a body performing Shm has a velacity of 12m/s when the displacement is 100mm the displacement
measured from the mid point calculate the frequency and amplitude of motion what is the acceleration when displacement is 75mm
Answers
Answer:
vjcyfuy
Explanation:
yjvjy
Related Questions
Design templates can be applied to presentations when _____.
they are opened
a new slide is added
all the slides are created
all of the above
none of the above
IT IS NOT WHEN A NEW S IS ADDED
Answers
Answer:
all of the above
Explanation:
The answer to this is all of the above. In the Microsoft Powerpoint software, you are able to add a design template as soon as you first open the software and begin creating your presentation. Aside from this, you can also add the design template you want to use when a new slide is added or all the slides have already been created. This is done by clicking on the Design tab in the top ribbon and choosing the desired template. From this tab, you are also able to select specific slides to which you want the design to be applied to.
Answer:
All of the above
Explanation:
EDG2021
The penalties for ignoring the requirements for protecting classified information when using social networking services are _________________ when using other media and methods of dissemination.
Answers
The penalties for ignoring the requirements for protecting classified information when using social networking services are the same when using other media and methods of dissemination.
The penalties are the same because it does not matter what the medium used, the effect is that classified information and confidential details have been left unguarded and exposed.
When in hold of such information, it is not okay to leave it unguarded or exposed. A person who is found guilty of disclosure of classified materials would face sanctions such as:
They would be given criminal sanctionsThey would face administrative sanctionsThey would also face civil litigationsRead more on https://brainly.com/question/17207229?referrer=searchResults
Adam is so good at playing arcade games that he will win at every game he plays. One fine day as he was walking on the street, he discovers an arcade store that pays real cash for every game that the player wins - however, the store will only pay out once per game. The store has some games for which they will pay winners, and each game has its own completion time and payout rate. Thrilled at the prospect of earning money for his talent, Adam walked into the store only to realize that the store closes in 2 hours (exactly 120 minutes). Knowing that he cannot play all the games in that time, he decides to pick the games that maximize his earnings
Sample game board at the arcade GAME COMPLETION TIME (in minutes) PAYOUT RATE Pac-man 90 400 Mortal Kombat 10 30 Super Tetris 25 100 Pump it Up 10 40 Street Fighter II 90 450 Speed Racer 10 40
An acceptable solution is the one where it still picks the best earnings even when the list of games or completion times or payout rates change.
Question:
Write code in Java/Scala/Python to help Adam pick the sequence(s) of games that earn him the most money?.
Then, assume you have a variable list of games and their payout rates. What is the best way to pick the games that earn you the most?
Input Explanation
The first line of input is always an integer denoting many lines to read after the first line. In our sample test case, we have 6 in the first line and 6 lines after the first line, each having a game, completion_time and payout_rate.
In each data line, the game, completion_time and payout_rate are separated by a ','(comma).
The games board may change but the store still closes in 120 minutes.
Input
6
Pac-man,80,400
Mortal Kombat,10,30
Super Tetris,25,100
Pump it Up,10,40
Street Fighter II,90,450
Speed Racer,10,40
Output Explanation
Print the game names that earn him the most into the standard output in alphabetical order
Output
Mortal Kombat
Pump it Up
Speed Racer
Street Fighter II
Answers
Answer:
ask it to ur teacher boiiiiii
Draw raw a program Flowchart that will be use to solve the value ofx im a quadratic equation +(x) = ax²tbxtc.
Answers
A program Flowchart that will be use to solve the value of x in a quadratic equation f(x) = ax²+bx+c.
Sure! Here's a basic flowchart to solve the value of x in a quadratic equation:
```Start
|
v
Input values of a, b, and c
|
v
Calculate discriminant (D) = b² - 4ac
|
v
If D < 0, No real solutions
|
v
If D = 0, x = -b / (2a)
|
v
If D > 0,
|
v
Calculate x1 = (-b + √D) / (2a)
|
v
Calculate x2 = (-b - √D) / (2a)
|
v
Output x1 and x2 as solutions
|
v
Stop
```In this flowchart, the program starts by taking input values of the coefficients a, b, and c. Then, it calculates the discriminant (D) using the formula D = b² - 4ac.
Next, it checks the value of the discriminant:
- If D is less than 0, it means there are no real solutions to the quadratic equation.
- If D is equal to 0, it means there is a single real solution, which can be calculated using the formula x = -b / (2a).
- If D is greater than 0, it means there are two distinct real solutions. The program calculates both solutions using the quadratic formula: x1 = (-b + √D) / (2a) and x2 = (-b - √D) / (2a).
Finally, the program outputs the solutions x1 and x2 as the result.
For more such questions on Flowchart,click on
https://brainly.com/question/6532130
#SPJ8
The Probable question may be:
Draw a program Flowchart that will be use to solve the value of x in a quadratic equation f(x) = ax²+bx+c.
Code an operation class called ArrayComputing that will ask user to enter a serials of integers with a loop until -99 is entered and after the input it will keep and display the greatest, the least, the sum and the average of the data entries (-99 is not counted as the data). And code a driver class called ArrayComputingApp to run and test the ArrayComputing class, separately.
Must use required/meaningful names for fields, variables, methods and classes.
Must use separate methods to perform each of specified tasks as described.
Must document each of your source code
Answers
Answer:
Explanation:
The following is written in Java and creates the ArrayComputing class. It uses the constructor to create the infinite loop that only breaks when the user enters a -99. After every input number it goes adding the correct values to the variables. Once it is done the user can call any of the getter methods to get the variable values as well as calculate the average.
import java.util.Scanner;
class ArrayComputingApp {
public static void main(String[] args) {
ArrayComputing arrayComputing = new ArrayComputing();
System.out.println("Average: " + arrayComputing.getAverage());
System.out.println("Greatest: " + arrayComputing.getGreatest());
System.out.println("Least: " + arrayComputing.getLeast());
System.out.println("Sum: " + arrayComputing.getSum());
}
}
class ArrayComputing {
int greatest, least, sum, average;
int count = 0;
Scanner in = new Scanner(System.in);
public ArrayComputing() {
while (true) {
System.out.println("Enter a number or -99 to exit: ");
int num = in.nextInt();
if (num == -99) {
break;
}
if (num > this.greatest) {
this.greatest = num;
}
if (this.count == 0) {
this.least = num;
} else {
if (num < this.least) {
this.least = num;
}
}
this.sum += num;
this.count += 1;
}
}
public int getAverage() {
this.average = sum / count;
return this.average;
}
public int getGreatest() {
return greatest;
}
public int getLeast() {
return least;
}
public int getSum() {
return sum;
}
}

Prompt the user to enter the time of the day. The user should enter d for daytime and n for nighttime. Configure a boolean variable to store if it is daytime (true) or nighttime (false). Use the boolean variable to store if it is daytime or nighttime and print if the temperature is ideal if it needs to be raised if it needs to be lowered, and by how much.
Answers
Answer:
Check the photos for the answers
Explanation:


On Earth, the pattern of daytime and nighttime repeat every day. This phenomenon takes place because of the rotation of the earth on its own axis. The rotation of the earth causes day and night on earth. The length of day and night varies on the seasons and it also varies according to the part of the earth.
What are rotation and the revolution of the earth?The rotation of the earth is one of the major movements of the earth which causes the day and night over the by the movement of the earth on its own axis. The rotation of the earth takes place from west to east direction.
Revolution is also one of the movements of the earth where the earth revolves around the sun and causes changes in season and also the duration of day and night due to its tilt over its axis.
Therefore, On Earth, the pattern of daytime and nighttime repeat every day. This phenomenon takes place because of the rotation of the earth on its own axis. The rotation of the earth causes day and night on earth. The length of day and night varies on the seasons and it also varies according to the part of the earth.
Learn more about the “revolution of the earth” here:
brainly.com/question/17731832
#SPJ2
Write and test a program that computes the area of a circle. This program should request a number representing a radius as input from the user. It should use the formula 3.14*radius**2 to compute the area and then output this result suitably labeled. Include screen shot of code.
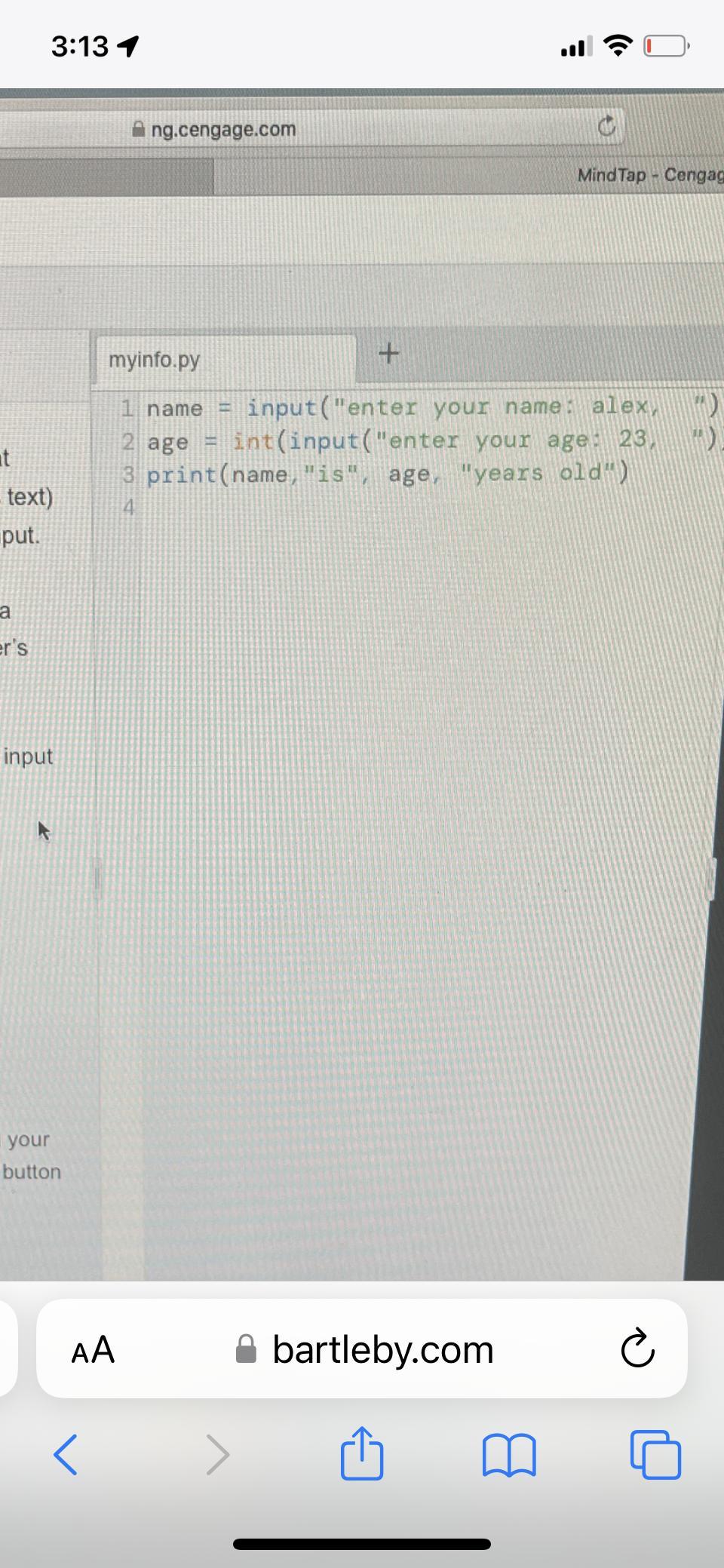
Answers
A program that computes the area of a circle is given below:
#include <stdio.h>
int main(void)
{
float radius, area;
printf("Enter radius of circle: ");
scanf("%f", &radius);
area = 3.14 * radius * radius;
printf("The area of the circle is: %.2f\n", area);
return 0;
}
What is program?A program is a set of instructions that tells a computer what to do. It is a set of commands that are written in a specific language or syntax, so that the computer can understand and execute them. Programs can range from a few simple commands to a complex system with millions of lines of code. Programs are written for a variety of purposes, including data processing, controlling hardware and software, developing websites, and more. Programs can also be used to create applications, games, and even artificial intelligence.
To learn more about program
https://brainly.com/question/30130277
#SPJ1
Trade Periodicals are usually highly scholarly resources
True
False
Answers
Answer:
False
Explanation:
Trade publications may be written by experts in a certain industry, but they are not considered scholarly, as they share general news, trends, and opinions, rather than advanced research, and are not peer-reviewed.
Exercise 8-3 Encapsulate
fruit = "banana"
count = 0
for char in fruit:
if char == "a":
count += 1
print(count)
This code takes the word "banana" and counts the number of "a"s. Modify this code so that it will count any letter the user wants in a string that they input. For example, if the user entered "How now brown cow" as the string, and asked to count the w's, the program would say 4.
Put the code in a function that takes two parameters-- the text and the letter to be searched for. Your header will look like def count_letters(p, let) This function will return the number of occurrences of the letter.
Use a main() function to get the phrase and the letter from the user and pass them to the count_letters(p,let) function. Store the returned letter count in a variable. Print "there are x occurrences of y in thephrase" in this function.
Screen capture of input box to enter numbeer 1
Answers
Answer:
python
Explanation:
def count_letters(p, let):
count = 0
for char in p:
if char == let:
count += 1
print(f"There are {count} occurrences of {let} in the phrase {p}")
def main():
the_phrase = input("What phrase to analyze?\n")
the_letter = input("What letter to count?\n")
count_letters(the_phrase, the_letter)
main()
Implement a binary search function in three substantially different programming languages. In each program (identical, except for the programming language), carry out the same 10,000,000 unsuccessful searches for eight different-sized arrays, namely arrays of sizes 128, 512, 2048, 8192, 32768, 131072, 524288, and 2,097,152. Measure in each of the three programs the time it takes to do the 10,000,000 searches for each of the eight arrays. Compare these timings to the theoretical timings the algorithm binary search provides. Are there differences between the three programs? Explain your timings and observations!!
Answers
Answer:
The code to this question can be defined as follows:
Explanation:
C language code:
#include <stdio.h>//defining header file
int binarySearch(int x[], int l, int y, int z)//defining method binarySearch that accepts four integer parameter
{
if (y >= l)//defining if block that check r value is greater the l
{
int m= l + (y - l)/2; //defining if block that holds mid value of array
if (x[m] == z)//use if block that check value in array
return m;// return array value
if (x[m] > z) //defining if block that check array value greater then x value
return binarySearch(x, l, m-1, z);//use return keyword to call method
return binarySearch(x, m+1, y, z);// in else it use return keyword to call method
}
return -1;//return value -1
}
int main()//defining main method
{
int x[] = {2, 3, 4, 10, 40};//defining array that hold integer values
int n = sizeof(x)/ sizeof(x[0]);//use n variable to hold its size value
int z = 10;//defining x varaiable that hold integer value
int r= binarySearch(x, 0, n-1, z);//use r varaiable to hold method return value
if(r== -1) //defining if block that check its value equal to -1
printf("Number is not foud in array ");//print message
else
printf("Number is present at %d position", r);//print value
return 0;
}
C++ language code:
#include <iostream>// header file
using namespace std;
int binarySearch(int x[], int l, int y, int z)//defining method binarySearch that accepts four integer parameter
{
if (y >= l)//defining if block that check r value is greater the l
{
int m= l + (y - l)/2; //defining if block that holds mid value of array
if (x[m] == z)//use if block that check value in array
return m;// return array value
if (x[m] > z) //defining if block that check array value greater then x value
return binarySearch(x, l, m-1, z);//use return keyword to call method
return binarySearch(x, m+1, y, z);// in else it use return keyword to call method
}
return -1;//return value -1
}
int main()//defining main method
{
int x[] = {2, 3, 4, 10, 40};//defining array that hold integer values
int n = sizeof(x)/ sizeof(x[0]);//use n variable to hold its size value
int z = 10;//defining x varaiable that hold integer value
int r= binarySearch(x, 0, n-1, z);//use r varaiable to hold method return value
if(r== -1) //defining if block that check its value equal to -1
cout<<"Number is not foud in array ";//print message
else
cout<<"Number is present at position "<< r;//print value
return 0;
}
Python language code:
def binarySearch (a, x, r, y):#defining a method binarySearch
if r >= x:#defining if block that checks r is greater than equal to x
m = x + (r - x)//2#defining m variable that hold mid value
if a[m] == y:#use if that check its input value equal y
return m#return m value
elif a[m] > y:#use array that check its value greaterthan y
return binarySearch(a,x, m-1, y) #use return keyword to call method
else:#defining else block
return binarySearch(a, m+1, r, y)#use return keyword to call method
else: #defining else block
return -1#return value -1
a = [ 2, 3, 4, 10, 40 ]#defining list a that holds value
y = 10#defining integer variable
r = binarySearch(a, 0, len(a)-1, y)#defining r variable that holds method value
if r != -1:#use if that check r is not equal to -1
print ("Number is available at ", r," position")#print value
else:#else block
print ("Number is not available in array")#print message
Can someone help me fix my code for this question? got pretty far but now i'm stuck on the syntax error.
In this lab, you use what you have learned about parallel arrays to complete a partially completed C++ program. The program should:
Either print the name and price for a coffee add-in from the Jumpin’ Jive Coffee Shop
Or it should print the message Sorry, we do not carry that.
Read the problem description carefully before you begin. The file provided for this lab includes the necessary variable declarations and input statements. You need to write the part of the program that searches for the name of the coffee add-in(s) and either prints the name and price of the add-in or prints the error message if the add-in is not found. Comments in the code tell you where to write your statements.
Instructions
Study the prewritten code to make sure you understand it.
Write the code that searches the array for the name of the add-in ordered by the customer.
Write the code that prints the name and price of the add-in or the error message, and then write the code that prints the cost of the total order.
Execute the program by clicking the Run button at the bottom of the screen. Use the following data:
Cream
Caramel
Whiskey
chocolate
Chocolate
Cinnamon
Vanilla
The Gdb one is what i have so far but i can't figure out what i'm doing wrong as far as syntax.


Answers
To be able to complete the code that can be used to searching a coffee add-in in an array as well as printing its name and price, look at the example of the implementation in C++ that is given below
What is the syntax error?In the code that is known to be given, one can declare as well as initialize two arrays - addIns that can be used for saving the names of coffee add-ins, as well as the prices for saving of the prices of the all of the corresponding add-ins.
Therefore, We can be able to collect input from a given customer for the coffee add-in they need to order. Finally, we can be able to make use of an if-else statement to be able to print the name and price of all ofthe add-i.
Learn more about syntax error from
https://brainly.com/question/28957248
#SPJ1


Which of the following characterizes how an enabled security program might react to a new program installation on a computer system?
It might alert you to space requirement excesses.
It might report an error or tell you that the file is corrupted.
It might protect the new installation from getting viruses.
It might automatically set a restore point for the computer system.
Answers
Answer:
It might automatically set a restore point for the computer system
Answer:
It might report an error or tell you that the file is corrupted.
Explanation:
You are a systems analyst. Many a time have you heard friends and colleagues complaining that their jobs and businesses are being negatively impacted by e-commerce. As a systems analyst, you decide to research whether this is true or not. Examine the impact of e-commerce on trade and employment/unemployment, and present your findings as a research essay.
Answers
E-commerce, the online buying and selling of goods and services, has significantly impacted trade, employment, and unemployment. This research essay provides a comprehensive analysis of its effects.
What happens with e-commerceContrary to popular belief, e-commerce has led to the growth and expansion of trade by breaking down geographical barriers and providing access to global markets for businesses, particularly SMEs. It has also created job opportunities in areas such as operations, logistics, customer service, web development, and digital marketing.
While certain sectors have experienced disruption, traditional businesses can adapt and benefit from e-commerce by adopting omni-channel strategies. The retail industry, in particular, has undergone significant transformation. E-commerce has empowered small businesses, allowing them to compete with larger enterprises and fostered entrepreneurial growth and innovation. However, there have been job displacements in some areas, necessitating individuals to transition and acquire new skills.
Read mroe on e-commerce here https://brainly.com/question/29115983
#SPJ1
Numbering exception conditions, which often uses hierarchical numbering, in a fully developed use case description is helpful to _______. a. tie the exception condition to a processing step b. show which exception conditions are subordinate to other exceptions c. provide an identifier for each exception condition d. tie exception conditions to other diagrams or descriptions
Answers
Answer:
a) tie the exception condition to a processing step
Explanation:
Numbering exception conditions, in a fully developed use case description is helpful to tie the exception condition to a processing step
The fully developed use case description is useful for the documentation of the context, purpose, description, conditions, and workflow of each use case. Activity diagrams give a graphical image of the use case workflow and serve the purpose of illustrating the alternative paths through a business process.
Which common online presentation medium do people use to present their own articles?
A. news portal
B. company website
C. photo-sharing website
D. weblog
Answers
Edhisive 3.5 code practice
Answers
Answer:
x = int(input("What grade are you in? "))
if (x == 9):
print ("Freshman")
elif (x == 10):
print("Sophomore")
elif (x == 11):
print ("Junior")
elif (x == 12):
print("Senior")
else:
print ("Not in High School")
Explanation:
A security architect at a large, multinational organization is concerned about the complexities and overhead of managing multiple encryption keys securely in a multicloud provider environment. The security architect is looking for a solution with reduced latency to allow the incorporation of the organization's existing keys and to maintain consistent, centralized control and management regardless of the data location. Which of the following would best meet the architects objectives
a. trusted platform module
b. IaaS
c. HSMaaS
d. PaaS
Answers
Answer:
a. trusted platform module
i thinks it will help you
Explanation:
What are TWO examples of soft skills?
computer programming
o responsibility
certification
communication
troubleshooting
Answers
What characteristics are common among operating systems? List types of operating systems, and examples of each. How does the device affect the functionality of an operating system?
Answers
The operating system (OS) controls all of the computer's software and hardware. It manages files, memory, and processes, handles input and output, and controls peripheral devices like disk drives and printers.
What are the characteristics of OS?The fundamental software applications running on that hardware enable unauthorized users to interact with the equipment because instructions can be sent and results can be obtained.Developers provide technology that may be compatible, mismatched, or completely incompatible with several other OS categories across multiple versions of the same similar OS.The operating systems are frequently 32-Bit and 64-Bit in two different versions.Types of Operating System:Distributed OS .
Batch processing OS.
Time sharing OS.
To learn more about operating system refer to :
https://brainly.com/question/22811693
#SPJ1
1. If you were on Earth and wanted to call someone via the radio on the moon, and they immediately sent a message back as soon as they received your message, how long from when you sent your message would you get a response
Answers
Answer:
About 2.5 seconds.
Explanation:
The speed of radio waves is 299,750 km/s whereas the distance between moon and earth is 384,400 km. By dividing speed of radio waves over the distance of moon and earth, we get 1.22 seconds of time from one side or in other words the person on the moon receives message in 1.22 seconds from the earth and the person on the earth receives a response from the moon in also 1.2 seconds so total time taken by the sender in receiving response from the moon is 2.5 to 3 seconds.
A partition is the _____.
an application that makes an operating system easier to use, also known as a shell
section of a hard drive
the core of an operating system that controls the basic functions
software that can be downloaded from the Internet at no cost
Answers
Different types of users in a managed network, what they do, their classification based on tasks
Answers
In a managed network,, skilled can be miscellaneous types of consumers accompanying various roles and blames.
What is the network?Administrators are being the reason for directing and upholding the network infrastructure. Their tasks involve network arrangement, freedom management, consumer approach control, listening network performance, and mechanically alter issues.
Administrators have high-ranking approach and control over the network. Network Engineers: Network engineers devote effort to something designing, achieving, and claiming the network foundation.
Learn more about network from
https://brainly.com/question/1326000
#SPJ1
Click this link to view O*NET’s Work Contexts section for Librarians.
It describes the physical and social elements common to this work. Note that common contexts are listed toward the top, and less common contexts are listed toward the bottom. According to O*NET, what are common work contexts for Librarians? Check all that apply.
face-to-face discussions
pace determined by speed of equipment
cramped work space, awkward positions
indoors, environmentally controlled
telephone and electronic mail
freedom to make decisions
Answers
Answer:
1. b,d,f 2. a,b,c,f 3. b,c,e,f 4. a,c 5. a,b,c,e 6. a,b,c
7. d,e,f 8. a,b,e,f 9. a,c,d 10. b,d,f 11. c,e,f 12. a,c,e,f
Explanation:
all the answers to Finance Workplaces and Tasks Assignment 100%
Answer:
1, 4, 5, 6
Explanation:
the only options that are on the website
How do the interests of carriers differ from the interests of websites? What are the implications for websites from a value chain perspective?
Answers
Answer:
Explained below.
Explanation:
- The interest of the carriers has it's major focus on the process of getting funds from both individual customers and corporate entities that run the websites. However, the interest of websites’ has it's major focus on the process of generating funds in form of subscriptions or funds gotten from paid adverts from both individual customers and corporate entities.
- In terms of value chain perspectives; the websites experience far more pressure to keep fresh and exciting features and services on their platform while carriers don't experience that but only experience having to compete with innovations being done by their existing competitors to remain leaders in the field.
What features do web development tools provide?
Web development tools come with several features to ease the process of building websites. Templates allow you to
experiment with a ___
Plug-ins allow you to___
Answers
Explanation: platolivesmattertooyk?
how to identify the significant accounts, disclosures, and relevant assertions in auditing long-lived assets.
Answers
To identify the significant accounts, disclosures, and relevant assertions in auditing long-lived assets are as follows:
How do you calculate the Long-Lived assets?
Upon recognition, a long-lived asset is either reported under the cost model at its historical cost less accumulated depreciation (amortisation) and less any impairment or under the revaluation model at its fair value.
Why are long-lived assets are depreciated?
Long-term assets must be depreciated throughout the period of their useful lives, much like most other types of assets. It is because a long-term asset is not anticipated to produce benefits indefinitely.
The long-lived assets are also called Non-current assets, and they contain both tangible and intangible assets and are utilised throughout several operational cycles.
-Tangible assets are things with a physical shape. • Equipment, structures, and land.
-Intangible assets have a form that is not physical. • Copyrights, patents, trademarks, and brand recognition.
Hence, the significant accounts, closures and relevant assertions are identified by the above steps.
To learn more about the long-lived assets from the given link
https://brainly.com/question/26718741
#SPJ1
flowchart is written using english language.
true or false
Answers
the answer is true hope it helps
WHICH OF THE FOLLOWING TASKS ARE PART OF THE SOFTWARE EVALUATION PROCESS?
TESTERS...
Answers
With regard to software evaulation, note that the correct options are -
Testers check that the code is implemented according to the specification document.A specification document is created.Any issues with the software are logged as bugs.Bugs are resolved by developers.How is this so?The tasks that are part of the software evaluation process include -
Testers check that the code is implemented according to the specification document.A specification document is created.Any issues with the software are logged as bugs.Bugs are resolved by developers.Tasks not directly related to the software evaluation process are -
Software developers writing code line by line.Creating a design for the software program.Learn more about software evaluation at:
https://brainly.com/question/28271917
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
Choose all that apply: Which of the following tasks are part of the software evaluation process?
testers check that the code is implemented according to the specification document
an specification document is created
software developers write code line by line
any issues with the software are logged as bugs
bugs are resolved by developers
a design for the software program is created
In this c++ assignment, add an undo feature to a list of strings.
Here's a working class called Stringlist that implements a simple string list as a dynamic array. Stringlist_test.cpp has tests for all the methods in Stringlist.
Stringlist has one unimplemented method:
// Undoes the last operation that modified the list. Returns true if a
// change was undone, false otherwise.
//
bool undo()
{
cout << "Stringlist::undo: not yet implemented\n";
return false;
}
Your job is to implement undo, thus making Stringlist an undoable list.
Your implementation must follow these rules:
Do not delete any methods, or change the signatures of any methods, in Stringlist. You can change the implementation of existing methods if necessary. But they should still work the same way: your finished version of Stringlist with undo implement must still pass all the tests in Stringlist_test.cpp.
You can add other helper methods (public or private), functions, and classes/structs to Stringlist.h if you need them.
You must implement undo() using a private stack that is accessible only inside the Stringlist class. Implement the stack yourself as a linked list. Do not use arrays, vectors, or any other data structure for your stack.
Do not use any other #includes or #pragmas in Stringlist.h other than the ones already there.
When it's done, you'll be able to write code like this:
#include "Stringlist.h"
#include
using namespace std;
int main() {
Stringlist lst;
cout << lst << endl; // {}
lst.insert_back("one");
lst.insert_back("two");
lst.insert_back("three");
cout << lst << endl; // {"one", "two", "three"}
lst.undo();
cout << lst << endl; // {"one", "two"}
lst.undo();
cout << lst << endl; // {"one"}
lst.undo();
cout << lst << endl; // {}
}
Designing the Undo Stack
As mentioned above, you must implement undo() using at least one private stack implemented as a linked list inside the Stringlist class. You can modify Stringlist only as described at the start of this assignment.
examples of how specific methods should work.
Undoing insert_before
In code:
// lst == {"dog", "cat", "tree"}
lst.insert_before(3, "hat");
// lst == {"dog", "cat", "tree", "hat"}
lst.undo();
// lst == {"dog", "cat", "tree"}
lst.insert_before(1, "shoe");
// lst == {"dog", "shoe", "cat", "tree"}
lst.undo();
// lst == {"dog", "cat", "tree"}
Undoing set
For set, suppose that lst is {"yellow", "green", "red", "orange"}, and so lst.get(2) returns "red". If you call lst.set(2, "cow"), then you should push the operation set location 2 to "red" onto the undo stack, and then over-write location 2 with "cow".
In code:
// lst == {"yellow", "green", "red", "orange"}
lst.set(2, "cow");
// lst == {"yellow", "green", "cow", "orange"}
lst.undo();
// lst == {"yellow", "green", "red", "orange"}
Undoing remove_at
For remove_at
In code:
// lst == {"dog", "cat", "tree"}
lst.remove_at(1);
// lst == {"dog", "tree"}
lst.undo();
// lst == {"dog", "cat", "tree"}
Undoing operator=
For operator=,
In code:
// lst1 == {"dog", "cat", "tree"}
// lst2 == {"yellow", "green", "red", "orange"}
lst1 = lst2;
// lst1 == {"yellow", "green", "red", "orange"}
// lst2 == {"yellow", "green", "red", "orange"}
lst1.undo();
// lst1 == {"dog", "cat", "tree"}
// lst2 == {"yellow", "green", "red", "orange"}
As this shows, when you undo operator=, the entire list of strings is restored in one call to undo().
Important notes:
If lst1 and lst2 are different objects, then when lst2 is assigned to lst1 just the underlying string array of lst2 is copied to lst1. The lst1 undo stack is updated so that it can undo the assignment. The undo stack of lst2 is not copied, and lst2 is not modified in any away.
Self-assignment is when you assign a list to itself, e.g. lst1 = lst1;. In this case, nothing happens to lst1. Both its string data and undo stack are left as-is.
Undoing remove_all
For remove_all,
In code:
// lst == {"dog", "cat", "tree"}
lst.remove_all();
// lst == {}
lst.undo();
// lst == {"dog", "cat", "tree"}
Note that it should work the same way when lst is empty:
// lst == {}
lst.remove_all();
// lst == {}
lst.undo();
// lst == {}
Undoing Other Methods
undo() should undoall the other methods in Stringlist that are marked as "undoable" in the source code comments.
As mentioned above, undo() is not undoable. There is no "re-do" feature in this assignment.
Each method in Stringlist.h marked "undoable" should work correctly with undo(). This also includes the correct behaviour for the Stringlist copy constructor (which should not copy the undo stack).
The markers tests should run correctly, including with no memory leaks according to valgrind.
Answers
To implement the undo feature in the Stringlist class, you will need to modify the existing class and add a private stack implemented as a linked list. Here are the steps to follow:
How to write the program code1. In the Stringlist class in Stringlist.h, add a private struct called `UndoNode` to represent each node in the undo stack. Each node should store the necessary information to undo an operation (e.g., the method name, the arguments, and any other relevant data).
```cpp
private:
struct UndoNode {
std::string method; // The method name
// Add other necessary data for the specific method being undone
// ...
UndoNode* next; // Pointer to the next node in the stack
UndoNode(const std::string& m) : method(m), next(nullptr) {}
};
```
2. Add a private member variable `undoStack` of type `UndoNode*` to the Stringlist class to keep track of the undo stack.
```cpp
private:
// Other private member variables
UndoNode* undoStack;
```
3. Modify the undoable methods in the Stringlist class to push the necessary information onto the undo stack before performing the operation. For example, in the `insert_before` method:
```cpp
void insert_before(size_t index, const std::string& str) {
// Push the operation onto the undo stack
UndoNode* undoNode = new UndoNode("insert_before");
// Add necessary data to the undoNode (e.g., index and str)
// ...
// Perform the actual operation
// ...
// Add the undoNode to the top of the stack
undoNode->next = undoStack;
undoStack = undoNode;
}
```
4. Implement the `undo` method to pop the top node from the undo stack and perform the undo operation based on the stored information. You will need to handle each operation individually in the `undo` method.
```cpp
bool undo() {
if (undoStack == nullptr) {
std::cout << "Undo stack is empty." << std::endl;
return false;
}
UndoNode* undoNode = undoStack;
undoStack = undoStack->next;
// Perform the undo operation based on the stored information in undoNode
if (undoNode->method == "insert_before") {
// Undo the insert_before operation
// ...
} else if (undoNode->method == "set") {
// Undo the set operation
// ...
}
// Handle other operations...
delete undoNode;
return true;
}
```
Remember to handle memory deallocation appropriately and update other methods marked as "undoable" accordingly.
Read more on Java codes here https://brainly.com/question/25458754
#SPJ1
6-Write a BNF description of the precedence and associativity rules defined for the expressions in Problem 9 - chapter 7 of the textbook . Assume the only operands are the names a,b,c,d, and e.
Answers
The BNF description, or BNF Grammar, of the precedence and associativity rules are
\(<identifier>\text{ }::=a|b|c|d|e\)
\(<operand>\text{ }::=\text{ }NUMBER\text{ }|\text{ }<Identifier>\)
\(<factor>\text{ }::=\text{ }<operand>|\text{ }-<operand>|\text{ }(<expression>)\)
\(<power>\text{ }:=\text{ }<factor>\text{ }|\text{ }<factor>\text{**} <power>\)
\(<term>\text{ }::=\text{ }<power>\text{ }\\|\text{ }<term>*<power>\text{ }\\|\text{ }<term>/<power>\\\\<expression>\text{ }::=\text{ }<term>\text{ }\\|\text{ }<expression>+<term>\text{ }\\|\text{ }<expression>-<term>\)
BNF, or Backus-Naur Form, is a notation for expressing the syntax of languages. It is made up of a set of derivation rules. For each rule, the Left-Hand-Side specifies a nonterminal symbol, while the Right-Hand-side consists of a sequence of either terminal, or nonterminal symbols.
To define precedence in BNF, note that the rules have to be defined so that:
A negation or bracket matches first, as seen in the nonterminal rule for factorA power matches next, as seen in the rule defining a factorA multiplication, or division expression matches next, as seen in the rule defining a termFinally, addition, or subtraction match, as seen in the rule defining an expression.To make sure that the expression is properly grouped, or associativity is taken into account,
Since powers associate to the right (that is, \(x \text{**} y\text{**}z=x \text{**} (y\text{**}z)\text{ and not }(x \text{**} y)\text{**}z\)), the rule defining power does this\(<power>\text{ }:=\text{ }<factor>\text{ }|\text{ }<factor>\text{**} <power>\)
and not
\(<power>\text{ }:=\text{ }<factor>\text{ }|\text{ }<power>\text{**}<factor>\)
Since multiplication/division are left associative (that is, \(x \text{*} y\text{*}z=(x \text{*} y)\text{*}z\)), the rule defining a term takes this into account by specifying its recursion on the right of the operators like so;\(<term>\text{ }::=\text{ }<power>\text{ }\\|\text{ }<term>*<power>\text{ }\\|\text{ }<term>/<power>\)
Also, addition and subtraction are left associative (that is, \(x \text{+} y\text{+}z=(x \text{+} y)\text{+}z\)), the rule defining an expression takes this into account as seen below\(<expression>\text{ }::=\text{ }<term>\text{ }\\|\text{ }<expression>+<term>\text{ }\\|\text{ }<expression>-<term>\)
Learn more about BNF grammars here: https://brainly.com/question/13668912