a.) Write a code statement to assign the value 7.3 to a variable with an identifier
timer.
Answers
The code segment that assigns value to the variable named timer is:
timer = 7.3
How to write the codeTo assign a value to a variable, we make use of the following syntax:
variable = value
In this case;
The variable is timer and the value is 7.3
Hence, the required code segment is: timer = 7.3
Read more about code segments at:
https://brainly.com/question/18430675
Related Questions
Select the correct answer.
Which device can be used for channeling feedback back into the control system’s input?
The device that channels feedback into the control system’s input is the
.
Answers
Answer:
Sensing elements.
Explanation:
Sensing elements are the device which connect channels feedback and return it to the control system input. There are many sensors used for feedback control such as Tachometer, Encoders, Accelerometers and rate gyroscopes.
Answer:
the correct answer is SENSOR
Explanation:
look at the picture hope this helps someone

Enumerate and discuss some common problems and their solutions in Power Generating Plants.
2.Enumerate and discuss some environmental issues in Power Generating Plants.
3.Cite and briefly discuss, at least 10 Latest Energy Laws in the Philippines.
Answers
Fuel Supply Disruptions: Power plants require a steady supply of fuel, such as coal, natural gas, or oil. Interruptions in fuel delivery can lead to power shortages. Diversifying fuel sources and establishing contingency plans can help mitigate this problem.
Environmental Impact: Power plants can contribute to air and water pollution, as well as greenhouse gas emissions. Implementing cleaner technologies, such as renewable energy sources and emissions control systems, can minimize environmental impact.
Waste Management: Power plants produce various types of waste, including ash, sludge, and byproducts from combustion processes. Proper waste management practices, including recycling and safe disposal, are crucial to prevent environmental contamination.
Regulatory Compliance: Power plants must adhere to strict regulations and standards related to safety, emissions, and operational practices. Regular audits and monitoring ensure compliance and minimize legal and financial risks.
Environmental issues in Power Generating Plants:
Air Pollution: Power plants emit pollutants, including sulfur dioxide, nitrogen oxides, and particulate matter, which contribute to air pollution and respiratory health issues. Implementing emission control technologies and transitioning to cleaner energy sources can help reduce air pollution.
Water Pollution: Power plants that rely on water for cooling purposes can impact aquatic ecosystems by discharging heated water or pollutants.
The latest energy laws in the Philippines include:
Renewable Energy Act of 2008 (Republic Act No. 9513): Promotes the development, utilization, and commercialization of renewable energy resources in the country.
Electric Power Industry Reform Act of 2001 (Republic Act No. 9136): Restructures the electric power industry, promotes competition, and protects consumer interests.
Biofuels Act of 2006 (Republic Act No. 9367): Promotes the use of biofuels as alternative sources of energy and reduces dependence on imported fossil fuels.
Learn more about Air Pollution here:
https://brainly.com/question/31023039
#SPJ11
What eventually terminates an internet worm is a lack of: a. Memory or storage space b. Time c. Internet bandwidth d. Processing power
Answers
The correct option is a. Memory or storage space.
Internet worms are self-replicating programs that can spread autonomously from computer to computer through networks. They are considered to be one of the most dangerous forms of malware because they can reproduce without the need for a host file or program to spread, potentially infecting a large number of devices in a short amount of time.However, there is a limit to how much space a worm can occupy before it consumes all available memory and storage space on a device. When this occurs, the worm will either crash or be unable to spread, effectively ending its propagation.In some cases, security experts may also be able to develop and deploy patches or updates to prevent the worm from infecting additional devices, effectively stopping its spread.
To know more about Memory or storage space click here,
https://brainly.com/question/31212947
#SPJ11
what is the importance of familiarizing and understanding the cells rows and format tools in the microsoft cell
Answers
Answer:
so you know the cell rows
Explanation:
duh
name two components required for wireless networking
(answer fastly)
Answers
Explanation:
User Devices. Users of wireless LANs operate a multitude of devices, such as PCs, laptops, and PDAs. ...
Radio NICs. A major part of a wireless LAN includes a radio NIC that operates within the computer device and provides wireless connectivity.
or routers, repeaters, and access points
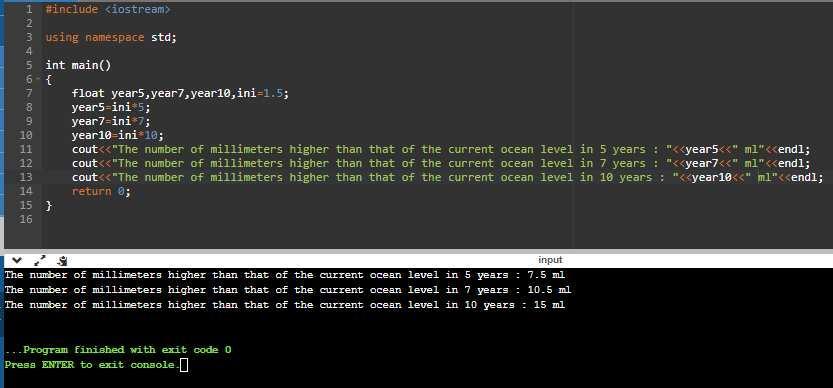
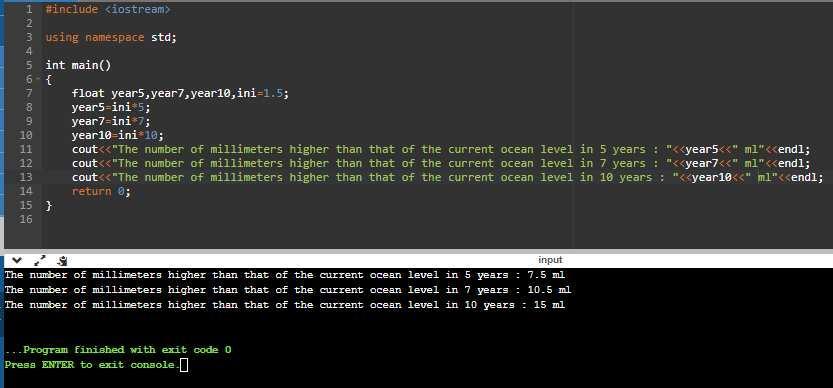
Ocean Levels
Assuming the ocean s level is currently rising at about 1.5 millimeters per year, write a program that displays:
* The number of millimeters higher than the current level that the ocean s level will be in 5 years.
* The number of millimeters higher than the current level that the ocean s level will be in 7 years..
* The number of millimeters higher than the current level that the ocean s level will be in 10 years.
Answers
The program is displayed in the images attached below:
#include <iostream>
using namespace std;
int main()
{
float year5,year7,year10,ini=1.5;
year5=ini*5;
year7=ini*7;
year10=ini*10;
cout<<"The number of millimeters higher than that of the current ocean level in 5 years: "<<year5<<" ml"<<endl;
cout<<"The number of millimeters higher than that of the current ocean level in 7 years: "<<year7<<" ml"<<endl;
cout<<"The number of millimeters higher than that of the current ocean level in 10 years: "<<year10<<" ml"<<endl;
return 0;
Learn more about programming here:
https://brainly.com/question/14368396
#SPJ4
How do you reference a property in the workspace tab for a script?
Answers
To reference a property in the workspace tab for a script, you need to follow these steps: identify, access, call and test.
1. Identify the property: Determine the specific property you want to reference within the workspace tab. This could be a variable, object, or function.
2. Access the workspace tab: Open the workspace tab where the property is located. The workspace tab usually consists of a script file, variables, and other elements that are a part of your project.
3. Use proper syntax: To reference the property, you will need to use the correct syntax for your programming language. For example, in JavaScript, you can access a property using the "objectName.propertyName" format.
4. Call the property: Once you have the proper syntax, you can call the property in your script. Ensure you are following any specific requirements or conventions of your programming language.
5. Test the reference: After referencing the property, test your script to ensure it works as intended. If there are any errors or issues, troubleshoot and make the necessary adjustments.
For more questions on script
https://brainly.com/question/26121358
#SPJ11
this absolute subtraction circuit has been implemented as a fully customized solution to the problem. is this design easily extendable to 32-bit inputs?
Answers
The 32-bit ALU 130 can perform any standard one- or two-operand operation, including pass, complement, twos complement, add, subtract, AND, NAND, OR, NOR, EXCLUSIVE-OR, and EXCLUSIVE-NOR.
How can I upgrade Windows from the 32-bit to the 64-bit edition?You must perform a hard disk reformat, install Windows 64-bit, and then reinstall all of the other software you previously had on your computer in order to upgrade from Windows 32-bit to Windows 64-bit.
What functions do the control unit (CU) and arithmetic logic unit (ALU) perform in a computer?Arithmetic and logical units, often known as ALUs, carry out operations like addition, subtraction, division, etc. CU stands for control unit, which is responsible for controlling computer functions.
To know more about 32-bit visit:-
https://brainly.com/question/30584706
#SPJ4
Why is the list constructor commonly used to find an index of an array element? Select an answer: .
a. index returns the array value for a particular index.
b. The array must be stripped of redundant information.
c. Arrays are not ordered. .
d. index only works with lists.
Answers
The list constructor is commonly used to find an index of an array element because it is a data structure that is an ordered sequence of items in Python programming.
This implies that the elements are arranged in a specific order and can be accessed using an index, and a list in Python is simply a collection of items that are separated by commas, with the whole list being surrounded by square brackets ([ ]).
Moreover, lists are mutable, which means that they can be modified after they have been created by adding, deleting, or modifying elements in the list.
In addition, the indexing of list elements begins at 0, which means that the first element in the list has an index of 0, the second has an index of 1, and so on. This makes it easy to find the index of a specific element in a list using the list constructor and the index() method, which returns the index of the first occurrence of the specified element in the list.If the element is not present in the list, it raises a ValueError. For instance, given a list
L = [10, 20, 30, 40, 50],
To know more about constructor visit:
https://brainly.com/question/13267120
#SPJ11
Which statement is most likely to be true of a self-driving vehicle rated at
automation level 2 (partial automation)?
A. The vehicle is mostly controlled by artificial intelligence.
B. The vehicle is completely controlled by a computer.
C. The driver's seat does not need to be occupied.
D. The vehicle may use artificial intelligence to stay in the correct
lane.
Answers
Answer:
i would select D.
Explanation:
Identify industries and career-based activities in which computer technology makes people's work easier or more efficient.
Answers
Answer:
Those helpful safety or convenience features in modern vehicles? They are all programmed!
Explanation:
PLSSS HELLLP!!! THE CROWN WILL BE REWARDED FOR THE CORRECT ANSWER!!!
When creating technical writing document, the author should consider _____. Choose all that apply.
Group of answer choices
the setting
the purpose
the audience
the imagery
the organization
Answers
Answer:
The audience
Explanation:
The correct option is - The audience
Reason -
When writing a technical document -
Always describe things in technical terms.
Write for your readers.
Describe things exactly as they're described to you by subject matter experts.
Technical writing :
Addresses particular readers.
Helps readers solve problems.
Is this a desktop or a computer, or are they the same thing

Answers
Answer:
Same thing.
Explanation:
Linux is a powerful and free OS®️
-True
-False
Answers
Answer:
TRUEE
Explanation:
Which of the following statements tests if students have a grade of 70 or above, as
well as fewer than five absences? (5 points)
if (grade > 70 or daysAbsent <= 5):
if (grade > 70 and daysAbsent <= 5) :
if (grade >= 70 and daysAbsent <= 5):
if (grade >= 70 or daysAbsent <= 5) :
Answers
Let's try to find a relationship between Y and X in the graph
0 - 95
1 - 85
2 - 90
The following statements tests if students have a grade of 70 or above, as well as fewer than five absences. Between these three points we see that (95 + 85) / 2 = 90
3 - 80
4 - 70
5 - 75
What placed between the points?Between these three points we see that (80 + 70) / 2 = 75
Wese e that the difference between the value 2 and value 3 is : 90 - 80= 10
So, the sixth value will be 75 - 10 = 65
The seventh value is (75 + 65)/2 = 70
The seventh value will probably be 70
well as fewer than five absences if (grade > 70 or daysAbsent <= 5): if (grade > 70 and daysAbsent <= 5) : if (grade >= 70 and daysAbsent <= 5):if (grade >= 70 or daysAbsent <= 5)
Therefore, The following statements tests if students have a grade of 70 or above, as well as fewer than five absences. Between these three points we see that (95 + 85) / 2 = 90
3 - 80
4 - 70
5 - 75
Learn more about points on:
https://brainly.com/question/1590611
#SPJ1
mc qu. 33 mira reviews the data about users that her c... mira reviews the data about users that her company's website collects and uses that data to create targeted marketing materials. mira is using
Answers
Mira is using data analytics to review the data about users that her company's website collects and create targeted marketing materials.
Data analytics involves examining and interpreting data to uncover patterns, insights, and trends that can inform decision-making and improve business strategies. In this case, Mira is analyzing the user data collected by her company's website to gain a deeper understanding of user behavior, preferences, and demographics. By leveraging data analytics, Mira can identify patterns and correlations in the data that can help her create targeted marketing materials. This process involves segmenting the user base, identifying common characteristics among different user groups, and tailoring marketing messages and campaigns to specific segments. Data analytics enables Mira to make data-driven decisions, optimize marketing efforts, and improve overall customer engagement and satisfaction. It allows her to leverage the power of data to personalize marketing materials and enhance the effectiveness of her company's marketing strategies.
learn more about data analytics here:
https://brainly.com/question/23860654
#SPJ11
How does a security information and event management system (SIEM) in a SOC help the personnel fight against security threats
Answers
A security information and event management (SIEM) system in an SOC helps fight security threats by combining data from varying technology sources and analyzing logs in real time, which helps in managing resources to implement protective measures against threats.
Features of a SIEMThey are tools used to promote information security through the provision of reports that display malicious intrusion attempts and alerts that are triggered in case of violation of established rules for security.
Therefore, through SIEM tools there is greater analysis and collection of data that can impact information security, generating a better classification of threats and investigative capacity to carry out actions to combat system insecurities.
Find out more information about security information here:
https://brainly.com/question/26282951
Did you know that EddieVR is great at horror games
Answers
Answer:
In one of his most popular videos, EddieVR takes on the role of a ghost hunter and plays the horror-themed video game -Phasmophobia with his friends at 3 a.m.
Explanation:
Unit 9 Inheritance and Polymorphism FRQ (a) (b) (c) PENCIL AND PAPER ONLY. SHOW ALL YOUR WORK CLEARLY. REMEMBER THAT PROGRAM SEGMENTS ARE TO BE WRITTEN IN JAVA. Assume that the classes listed in the Java Quick Reference have been imported where appropriate. Unless otherwise noted in the question, assume that parameters in method calls are not null and that methods are called only when their preconditions are satisfied. In writing solutions for each question, you may use any of the accessible methods that are listed in classes defined in that question. Writing significant amounts of code that can be replaced by a call to one of these methods will not receive full credit. The following Book class is used to represent books and print information about each book. Each Book object has attributes for the book title and for the name of the book's author. public class Book private String title; private String author; public Book (String t, String a) title = t; author = a; public void printBookInfo() System.out.print(title + ", written by " + author); (a) The PictureBook class is a subclass of the Book class that has one additional attribute: a String variable named illustrator that is used to represent the name of the illustrator of a picture book. The PictureBook class also contains a printBookInfo method to print the title, writer, and illustrator of a picture book. Consider the following code segment. PictureBook myBook = new PictureBook ("Peter and Wendy", "J.M. Barrie", "F.D. Bedford"); myBook.printBookInfo(); The code segment is intended to print the following output. Peter and Wendy, written by J.M. Barrie and illustrated by F.D. Bedford Complete the PictureBook class below. Your implementation should conform to the example above. public class PictureBook extends Book (write your class using pencil in a separate page) Unit 9 Inheritance and Polymorphism FRQ (a) (b) (c) Consider the following books. • A book titled Frankenstein, written by Mary Shelley A picture book titled The Wonderful Wizard of Oz, written by L. Frank Baum and illustrated by W.W. Denslow The following code segment is intended to represent the two books described above as objects bookl and book2, respectively, and add them to the ArrayList myLibrary. ArrayList myLibrary = new ArrayList(); /* missing code */ myLibrary.add(bookl); my Library.add(book2); (b) Write a code segment that can be used to replace /* missing code */ so that bookl and book 2 will be correctly created and added to my Library. Assume that class PictureBook works as intended, regardless of what you wrote in part (a). (write your code segment using pencil in a separate page) The BookListing class is used to generate a descriptive listing for a book. The BookListing constructor takes a Book object and a double value as parameters and uses them to print information about the book, along with its price. Assume that book1 and book2 were created as specified in part (b). The following table demonstrates the intended behavior of the BookListing class using objects book1 and book2. Code Segment Result Printed BookListing listing1 = new BookListing (book1, 10.99); Frankenstein, written by Mary Shelley, $10.99 listingl.printDescription(); BookListing listing2 = new BookListing (book2, 12.99); The Wonderful Wizard of Oz, written by L. Frank Baum and illustrated by W.W. Denslow, $12.99 listing2.print Description(); (c) Complete the BookListing class below. Your implementation should conform to the examples. Assume that class PictureBook works as intended, regardless of what you wrote in part (a). public class BookListing (write your class using pencil in a separate page)
Answers
(a) The implementation of the PictureBook class:
typescript
Copy code
public class PictureBook extends Book {
private String illustrator;
public PictureBook(String t, String a, String i) {
super(t, a);
illustrator = i;
}
public void printBookInfo() {
System.out.print(title + ", written by " + author + " and illustrated by " + illustrator);
}
}
(b) The code segment that creates book1 and book2 and adds them to myLibrary:
csharp
Copy code
Book book1 = new Book("Frankenstein", "Mary Shelley");
PictureBook book2 = new PictureBook("The Wonderful Wizard of Oz", "L. Frank Baum", "W.W. Denslow");
myLibrary.add(book1);
myLibrary.add(book2);
(c) The implementation of the BookListing class:
csharp
Copy code
public class BookListing {
private Book book;
private double price;
public BookListing(Book b, double p) {
book = b;
price = p;
}
public void printDescription() {
book.printBookInfo();
System.out.println(", $" + price);
}
}
For more questions like Polymorphism visit the link below:
https://brainly.com/question/16344360
#SPJ11
which of the following best describes a code of ethics?
Answers
The code of ethics refers to the guide of principles that are required to help professionals so that they can conduct their business with integrity.
Organizations adopt code of ethics so that their members can be able to know the difference between what is considered right and what is wrong.Through code of ethics, employees can be judged in an organization when they do something that doesn't align with the ethical standards of the organization.
In conclusion, code of ethics is important as it shapes an organization in the right direction.
Read related link on:
https://brainly.com/question/21819443
The Ethics Code relates towards the guidance of principles that specialists need to help them perform their business with integrity.
It also included business ethics, a code of professional behavior as well as rules of ethics for employees.Organizations adopt an ethics code so that their representatives can understand the difference between what is wrong and what is right.Employees may be judged in an organization through an ethics code when they do anything that does not match the company's ethical standards.The code of ethics is important because it shapes an organization.Therefore, the final answer is "code of ethics".
Learn more:
brainly.com/question/13818432
Read the following code:
X = totalcost
print(x / 2)
What value will this code calculate? (5 points)
A. Double the total cost
B. Half the total cost
C. Quarter of the total cost
D. Two percent of the total cost
Answers
You carried out a PERT analysis of a very large activity-event network using only slightly skewed or symmetric beta distribution models for the activity durations. Your analysis yields a mean duration of 56.2 time units for the critical path with a variance of 3.4. What is your best estimate of the probability of successful project completion in 57 time units or less? Provide your answer as a number between 0 and 1 with 3 decimals (3 digits after the decimal point, for example: 0.123).
Answers
PERT (Program Evaluation and Review Technique) is a network analysis technique commonly used in project management.
It is particularly useful when there is a high level of uncertainty surrounding the duration of individual project activities. PERT uses probabilistic time estimates, which are duration estimates based on using optimistic, most likely, and pessimistic estimates of activity durations, or a three-point estimate.
These estimates help to identify the likelihood of meeting project deadlines and can assist project managers in developing effective project schedules and resource allocation plans. Overall, PERT is an important tool for managing complex projects with uncertain activity durations.
To know more about project management, refer to the link:
brainly.com/question/4475646#
#SPJ4
he core networks are generally comprised of fixed-line networks with switches, routers and servers. For the same reason as in Question 3, they need to be left running all the time to provide the service level agreement (SLA). However, there are some opportunities to reduce the energy consumption in the core network while keeping them running. a) Describe at least 2 methods that can be used to reduce the energy consumption in the core network, including the routing algorithm. (4 marks) b) A benchmarking model can be used to evaluate the energy cost of networking devices in the core network, to predict and compare the energy consumption of networking equipment via software tools, i. ii. Describe one of the benchmark schemes available in the literature. (2 marks) Identify at least 4 of the main parameters that should be measured and explain why these are important. (2 marks) Evaluate the accuracy of such a benchmark scheme. (2 marks)
Answers
a) Methods to reduce the energy consumption in the core network are as follows: Packet switching: This method sends the data in packets, and it is more efficient than sending the data in a whole.
The routing algorithms used in the packet switching method include shortest path, flooding, and broadcast. Therefore, this method reduces the energy consumption of the core network due to its routing algorithms.
Enhanced network architecture: It measures the effect of network architecture on the energy consumed.
The accuracy of the benchmark scheme is good because the benchmark model is used to determine the energy consumed by a device in the laboratory.
The laboratory tests and results are evaluated and published in peer-reviewed journals, which increases the benchmark scheme's accuracy.
To know more about network visit :
https://brainly.com/question/1167985
#SPJ11
in 100 word, tell me who is a significant public figure who has the job profile as a "set designer" and explain why
Answers
A significant public figure who holds the job profile of a set designer is Sarah Jones.
Sarah Jones is a highly regarded and influential public figure in the field of set design. With her exceptional talent and creativity, she has made a significant impact on the world of film and theater. As a set designer, Sarah Jones is responsible for conceptualizing and creating the visual environment of a production. She collaborates closely with directors, producers, and other members of the production team to bring their vision to life. Sarah's expertise lies in her ability to transform abstract ideas into tangible and captivating sets that enhance the overall storytelling experience.
Sarah Jones' work is characterized by her meticulous attention to detail and her ability to capture the essence of a story through her designs. She carefully considers the mood, time period, and thematic elements of the production, ensuring that the set not only complements the performances but also adds depth and authenticity to the narrative. Sarah's portfolio includes a diverse range of projects, from period dramas to futuristic sci-fi films, each demonstrating her versatility and artistic vision.
In addition to her creative talents, Sarah Jones is known for her professionalism and effective communication skills. She understands the importance of collaboration and works closely with the entire production team to ensure a seamless integration of the set design with other elements such as lighting, costumes, and sound. Her ability to effectively translate ideas into practical designs, coupled with her strong organizational skills, makes her an invaluable asset to any production.
Learn more about job profile
brainly.com/question/884776
#SPJ11
Searching for a particular value is an example of a process filter. The program below reads a character, and then searches for that character in input. Modify the filter so that it also reports the line number in which the character appears.
Answers
Searching for a particular value is an example of a process filter. The program below reads a character, and then searches for that character in input.
Modify the filter so that it also reports the line number in which the character appears.
```import java.util.Scanner;
public class Main{
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
char ch = scanner.next().charAt(0);
String input = "Searching for a particular value is an example of a process filter.";
boolean found = false;
for(int i=0;i<=input.length()-1;i++) {
if(input.charAt(i) == ch) {
found = true;
System.out.println("Character "+ch+" found in input at line number "+i); break;
}
}
if(!found) {
System.out.println("Character "+ch+" not found in input");
}
}
}```
In the above code, we have initialized the character variable named "ch" which will hold the character that we want to search in the given input string. After this, we have taken input from the user and initialized the String variable named "input" which will hold the string in which we will search for the given character.
The for loop is used to iterate through the length of the input string from 0 to length-1. We have used if statement to check whether the character at i-th position of input string is equal to the character we want to search. If it is true, we will set the boolean variable named "found" to true and print the message "Character " + ch + " found in input at line number " + i".
The line number is i+1, as the line starts at 1 and not 0.If we do not find the character in the input string, we will set the boolean variable named "found" to false and print the message "Character " + ch + " not found in input".
By modifying the above code, we have added the line number in which the character appears in the given input string. This will help us to identify the location of the character in the input string and improve the efficiency of our program.
To know more about boolean variable :
brainly.com/question/32316270
#SPJ11
:) y’all are so nice for helping me ty , but any idea what this is?

Answers
Answer:
Best way is 3
Worst way is the rest
Explanation:
Answer:
the answer is 3
you are configuring a network in which remote access clients will access the network using different entry points such as through wifi and vpn. you need a convenient authentication system to handle this. which of the following is a good choice?
a. S-CHAP b. Kerberos c. PAP
Answers
Kerberos would be a good choice for this scenario.
Kerberos provides a centralized authentication system that allows remote access clients to access the network securely using different entry points such as through WiFi and VPN. It also provides strong encryption to ensure the security of the authentication process. S-CHAP and PAP are not as secure or convenient for this scenario.
Learn more about authentication system: https://brainly.com/question/30699179
#SPJ11
question 4 you are working with a database table that contains data about music artists. the table is named artist. you want to review all the columns in the table. you write the sql query below. add a from clause that will retrieve the data from the artist table. 12 select * reset how many columns are in the artist table? 1 point 8 2 5 9
Answers
Add "FROM artist" to the SQL query in order to retrieve all columns from the "artist" table. The information provided makes it impossible to estimate how many columns there are.
How many columns are there in the table of artists?It has the artist id and name columns. The integer column with unique values that serves as this table's primary key is called artist id.
What is the name of an artist's table?When used in its original form, a drawing board (also known as a drawing table, drafting table, or architect's table) is a type of multipurpose desk that can be used for any kind of drawing, writing, or spontaneous sketching on a large sheet of paper, for reading a large format book or other oversized document, or for precisely drafting.
To know more about SQL visit:-
brainly.com/question/13068613
#SPJ1
Jack knows how to use word processors, spreadsheets, and presentation software. He also has a basic knowledge of hardware, software, and the Internet. Given this information, it can be concluded that Jack has _____ literacy.
Answers
Answer: computer literacy
Given the above information, it can be concluded that Jack has computer literacy.
What is Computer literacy?This is known to be defined as given knowledge and ability that a person has in the area of the use of computers and its related technology in an efficient manner.
Note that Given the above information, it can be concluded that Jack has computer literacy.
Learn more about computer literacy from
https://brainly.com/question/20892559
#SPJ6
Write a function called replace_elem that takes an array and two values and uses the simple search algorithm to replace all instances of the first value with the second value.
I NEED THIS SOON
Answers
The replace_elem program is an illustration of functions, whose execution is carried out when the function name is evoked or called.
The main programThe program written in Python, where comments are used to explain each action is as follows:
#This defines the function
def replace_elem(myList, a, b):
#This iterates through the list elements
for i in range(0,len(myList)):
#The following if condition replaces the element
if(myList[i] == a):
myList[i] = b
#This prints the new list elements
print(myList)
Read more about python programs at:
https://brainly.com/question/26497128