An airport is developing a computer simulation of air-traffic control that handles events such as landings and takeoffs. Each event has a time stamp that denotes the time when the event will occur. The simulation program needs to efficiently perform the following two fundamental operations:
• Insert an event with a given time stamp (that is, add a future event).
• Extract the event with smallest time stamp (that is, determine the next event to process).
Answers
By ensuring that events are processed in the order they are scheduled to occur, the simulation program can provide accurate and timely information to air-traffic controllers, enabling them to make informed decisions.
An airport's development of a computer simulation of air-traffic control is an excellent way to enhance the efficiency and safety of air travel. This simulation program should be able to handle different events such as landings and takeoffs and efficiently perform two fundamental operations. The first operation is to insert an event with a given time stamp, which means adding a future event. The second operation is to extract the event with the smallest time stamp, which means determining the next event to process.
To achieve this, the simulation program can utilize data structures such as priority queues to maintain events in a sorted order based on their time stamp. Inserting an event with a given time stamp can be done by adding it to the priority queue. The event with the smallest time stamp can be extracted from the priority queue, and the simulation program can process it accordingly.
Efficient handling of events is crucial in air-traffic control simulation, and a well-designed program can help reduce the chances of mishaps. By ensuring that events are processed in the order they are scheduled to occur, the simulation program can provide accurate and timely information to air-traffic controllers, enabling them to make informed decisions.
Learn more about computer simulation here:
https://brainly.com/question/31038498
#SPJ11
Related Questions
which shooting games is good for low end PC. CSGO or Valorant?
Answers
the best choice would be csgo
Search for one (1) published journal article related to STRATEGIC MARKETING (please include the reference of the searched journal article). From the searched article, make a comprehensive / complete journal article review that includes the following:
a. A brief summary of the article: purpose, issues/problems, procedures, and conclusions ;
b. Explain briefly two or three significant/interesting aspects (approaches, theories, methods, findings, implications) of the article
c. Present your personal opinions, comments or any criticisms of the article, including any flaws that you found in the article (e.g., omissions of important information, ambiguous text, illogical procedures, inappropriate methods/overstated conclusions and implications, etc.)
d. Discuss the relevance and importance of the article to strategic marketing including your own ideas on the contribution that the article makes to the field and any practical applications & research implications of the study.
Answers
I apologize, but as an AI text-based bot, I am unable to perform searches or access specific articles. However, I can provide you with a step-by-step guide on how to review a journal article related to strategic marketing. Here's how you can approach it:
a. Brief Summary:
- Begin by providing a concise summary of the article's purpose or objective.
- Identify the key issues or problems that the article addresses.
b. Significant/Interesting Aspects:
- Choose two or three noteworthy aspects of the article, such as unique approaches, theories, methods, findings, or implications.
- Explain why these aspects stood out to you and how they contribute to the field of strategic marketing.
c. Personal Opinions and Criticisms:
- Share your personal opinions on the article, focusing on its strengths and weaknesses.
- Highlight any flaws or omissions you found, such as missing information, ambiguous text, illogical procedures, inappropriate methods, overstated conclusions, or implications.
d. Relevance and Importance:
- Discuss the relevance and importance of the article to the field of strategic marketing.
- Share your own ideas on how the article contributes to the field.
To know more about approaches visit:
https://brainly.com/question/30967234
#SPJ11
You will be able to conduct a thorough journal article review.
1. Start by accessing academic databases or search engines such as Go ogle Scholar, JSTOR, or EBSCOhost.
2. Enter keywords related to strategic marketing, such as "strategic marketing," "marketing strategy," or "strategic management."
3. Filter your search results to display only journal articles by selecting the appropriate options in the search filters.
4. Skim through the article titles, abstracts, and keywords to find a relevant article that aligns with your interests.
5. Once you have found a suitable article, retrieve its reference information, including the author(s), title, journal name, publication year, volume, and page numbers.
Now let's move on to writing a comprehensive journal article review, covering the requested aspects:
a. A brief summary of the article:
Provide a concise overview of the article, including its purpose, main issues or problems addressed, the research procedures followed, and the conclusions drawn by the authors.
b. Explain two or three significant/interesting aspects:
Identify and briefly explain the significant or interesting aspects of the article, such as novel approaches, theories, methods used, key findings, or practical implications derived from the study.
c. Personal opinions, comments, or criticisms:
Share your personal opinions about the article, highlighting any strengths or weaknesses you noticed. If you found any flaws, such as omissions of important information, ambiguous text, illogical procedures, inappropriate methods, or overstated conclusions, explain them in a constructive manner.
d. Discuss the relevance and importance of the article to strategic marketing:
Explain the relevance and importance of the article to the field of strategic marketing. Discuss how the article contributes to existing knowledge, potential practical applications, and any research implications it may have. Additionally, provide your own ideas on how the article expands the understanding of strategic marketing and its potential impact on the industry.
To know more about strategic marketing:
https://brainly.com/question/30582403
#SPJ11
When creating a new pivot table tyle, in the format cell dialog box, which tab change the ize and hape of the text?
Answers
When creating a new pivot table style and using the format cells dialogue box, the "Font" tab is used to change the size and shape of the text.
In the Font tab, you can adjust the following properties of the text:
Font: the typeface used for the textFont style: bold, italic, underline, strikethroughSize: the size of the textColor: the color of the textEffects: options such as shadow, outline, and small capsBy using the Font tab, you can quickly change the appearance of the text in your pivot table, such as making the text larger or smaller, bolding or italicizing it, or changing its color.
This can be useful for emphasizing important data or making the pivot table easier to read. It's worth noting that, depending on the software you are using, the options in the format Cell dialogue box may be different, but the Font tab is usually present to change the text formatting.
To learn more about Font tab, use the link:
brainly.com/question/15787410
#SPJ4
Apply the defined names Q1_Sales, Q2_Sales, Q3_Sales, and Q4_Sales to the formulas in the range B10:E10 in the Consolidated Sales worksheet.
Answers
To apply the defined names Q1_Sales, Q2_Sales, Q3_Sales, and Q4_Sales to the formulas in the range B10:E10 in the Consolidated Sales worksheet, follow these steps:
1. Select the range B10:E10 in the Consolidated Sales worksheet.
2. Go to the "Formulas" tab on the ribbon.
3. Click on the "Define Name" button in the "Defined Names" group.
4. In the "New Name" dialog box, enter the name Q1_Sales in the "Name" box.
5. Click on the "OK" button to apply the name to the selected range.
6. Repeat steps 4 and 5 for the names Q2_Sales, Q3_Sales, and Q4_Sales.
Once you have applied the defined names to the selected range, you can use them in formulas to refer to the corresponding cells. For example, you can use the formula =Q1_Sales+Q2_Sales+Q3_Sales+Q4_Sales to calculate the total sales for the year.
Learn more about Consolidated Sales worksheet:
https://brainly.com/question/30167580
#SPJ11
Does a Laser Printer use its beam to attach dry powdered ink to a sheet of paper?
Answers
Answer: A laser printer is different only in terms of ink heads. Hile Traditional Printers use physical contact to embed ink onto the paper laser jets use laser beams with inks to forms impressions into papers. They require no special paper to print. So probably not.
James Quinn (1991) defines strategy as the pattern that integrates an organization’s major goals, policies and actions into a cohesive whole.
What are the criteria for a good strategy?
List and discuss five different criteria.
(1 mark for each criteria and 1 mark for the corresponding and relevant discussion)
Answers
A good strategy should meet the following criteria: clarity, consistency, feasibility, flexibility, and alignment.
Clarity means that the strategy should have a clear and well-defined purpose and direction, ensuring that everyone understands it. Consistency implies that the strategy should be aligned with the organization's goals and policies, creating a coherent and integrated approach. Feasibility means that the strategy should be realistic and achievable within the organization's resources and capabilities. Flexibility suggests that the strategy should be adaptable to changes in the internal and external environment, allowing for adjustments when needed. Alignment emphasizes the importance of aligning the strategy with the organization's culture, values, and stakeholders' expectations.
In summary, a good strategy should be clear, consistent, feasible, flexible, and aligned with the organization's goals, policies, and stakeholders' expectations. These criteria ensure that the strategy can effectively guide the organization towards its major goals and actions.
You can learn more about strategic criteria at
https://brainly.com/question/29340760
#SPJ11.
Can someone please help me with this question
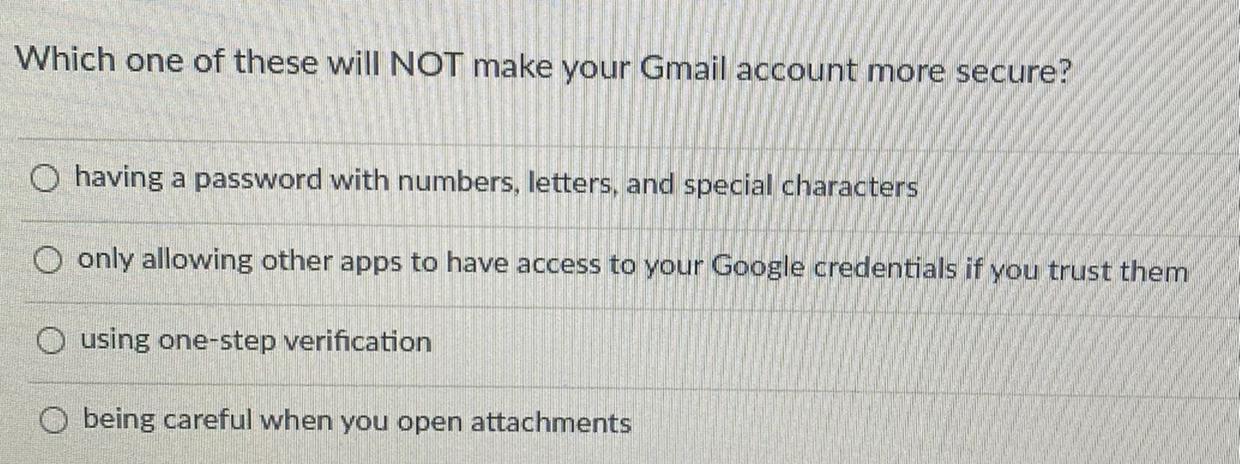
Answers
Answer:
being careful when you open attachments
Which option best describes the purpose of the Design step?
A. To implement user feedback into the game
B. To add characters and other elements to the game
C. To plan the game's structure and artwork
D. To write the framework of the game's code
Answers
The option that best describes the purpose of the Design step is option C. To plan the game's structure and artwork
Why does design mean?It is the act of making a plan or drawing for something that will later be built, particularly one that specifies what the end product will do and look like, is the definition of design. The plan or sketch produced as a result of this activity is referred to as a design.
Note that It brings cutting-edge solutions to life based on what actual consumers feel, think, and do. Empathize, Define, Ideate, Prototype, and Test are the five main phases of this human-centered design approach. The fact that these steps are only a guide should not be overlooked. 3
Hence, the Steps in the Engineering Design Process are: Establish criteria and constraints. Consider alternative solutions. Choose an approach. Develop a design proposal. Create a model or prototype. Define the problem. Research ideas and explore possibilities for your engineering design project.
Learn more about Design step from
https://brainly.com/question/2604531
#SPJ1
how to explain if the following is a valid set of java instructions: int mygrade = (assignment1 * 10); int assignment1 = 10;
Answers
Yes, this is a valid set of Java instructions. The first line declares a variable called mygrade' and assigns it the value of the product of the two variables 'assignment1' and 10. The second line declares a variable called 'assignment1' and assigns it the value of 10.
What is Java ?Java is a programming language and computing platform first released by Sun Microsystems in 1995. It is used to develop and run programs on a variety of hardware, including desktop computers, servers, and mobile devices. Java has become one of the most popular programming languages due to its versatility, allowing developers to write code that can be used on different platforms. Java is a class-based, object-oriented language,
which means it is composed of classes that define objects and the methods that can be used to manipulate them. It is an interpreted language, meaning that the code is compiled into bytecode and then executed by the Java Virtual Machine (JVM). Java also has features such as garbage collection and memory management, which make it easier for developers to create reliable, efficient applications. Java is used in many applications, from web applications to enterprise software to Android apps.
To learn more about Java
https://brainly.com/question/26789430
#SPJ1
write the home cell of MS Excel.
Answers
Answer:
MS Excel
Explanation:
the communication model is a view that communication is merely a conduit for the transmission of information about the real world.
Answers
False. The communication model is a theoretical framework that describes the process of communication, including the exchange of messages between a sender and a receiver. It takes into account various factors that can influence communication, such as noise, feedback, and context, and recognizes that communication is not just about transmitting information, but also about creating meaning and building relationships between people.
#SPJ11
Which component of Exploit Guard helps prevent access to internet domains that may host phishing scams, exploits, and other malicious content?
Network protection
Answers
Network protection is the component of Exploit Guard that helps prevent access to internet domains that may host phishing scams, exploits, and other malicious content.
Exploit Guard is a set of advanced security features in Windows that provides enhanced protection against various types of cyber threats. One of its key components is network protection, which acts as a safeguard against accessing malicious internet domains.
When enabled, network protection monitors network traffic and analyzes the URLs or domain names being accessed by applications on a system. It compares these URLs against a list of known malicious domains or blacklists maintained by Microsoft, security organizations, or administrators.
By leveraging real-time threat intelligence and machine learning algorithms, network protection can identify and block attempts to access websites that are known to host phishing scams, exploit kits, malware, or other types of malicious content. This proactive approach helps to prevent users from inadvertently visiting dangerous websites and falling victim to online scams or malware infections.
Network protection operates at the network level, meaning it can block access to malicious domains across various applications and processes on a system. This ensures comprehensive protection, even if an application has vulnerabilities that could be exploited to bypass other security measures.
By actively monitoring and filtering network traffic, Exploit Guard's network protection component helps to create a safer browsing environment for users and mitigate the risks associated with accessing malicious internet domains.
Learn more about phishing scams
brainly.com/question/32404889
#SPJ11
Older Microsoft disk compression tools, such as DoubleSpace or ____, eliminate only slack disk space between files.
Answers
Use nested for-loops to have the turtle draw a snowflake of polygons. Use the variable turnamount to turn after each shape and the variable n for the sides of the polygon
Answers
An interlocking loop is referred to as nested loop . These are frequently utilized while working in two dimensions, such as when printing stars in rows and columns.
How do two for loops that are nested work?An inner loop encloses the body of an outer loop, creating a nested loop. In order for this to operate, the inner loop must be triggered by the outer loop's initial pass in order to begin working. The inner loop is then reactivated during the second transit of the outer loop.
The for loop may be nested, right?For loops that are nested are placed inside of one another. With each outer loop iteration, the inner loop is repeated.
To know more about nested for-loops visit :-
https://brainly.com/question/13971698
#SPJ4
plzzz help i need this today :(

Answers
Answer:
C
Explanation:
im doing begginer Python please explain the steps
Write code including a for loop to input 6 numbers of type float one by one and then
print out the position of the largest number. For example, if the numbers are 1.0, 2.5,
2.9, 3.1, 2.8, 1.7, then the number 4 is printed out because the largest number, 3.1,
is in the 4th position. You may assume in the code that exactly 6 numbers are to be
input.
Answers
Here's the step-by-step explanation of the code:
First, we initialize a variable max_number to store the largest number. We also initialize a variable max_position to store the position of the largest number.
We use a for loop to iterate 6 times since we want to input 6 numbers. In each iteration, we prompt the user to enter a number using the input() function.
Inside the loop, we convert the user input to a float using the float() function and store it in a variable number.
We then check if number is greater than the current max_number. If it is, we update max_number to the value of number and update max_position to the current iteration index plus 1 (since the index starts from 0 but we want the position to start from 1).
After the loop finishes, we print out the value of max_position using the print() function.
Here's the code:
python
Copy code
max_number = float('-inf') # Initialize the largest number as negative infinity
max_position = 0 # Initialize the position of the largest number
for i in range(6):
number = float(input("Enter a number: "))
if number > max_number:
max_number = number
max_position = i + 1
print("The position of the largest number is:", max_position)
When you run the code, it will prompt you to enter 6 numbers one by one. After entering the numbers, it will print out the position of the largest number among the entered numbers.
Learn more about code here:
https://brainly.com/question/31228987
#SPJ11
Yelena has created timings within her slide show, and she wants to verify that each slide has the correct timing. In which view in PowerPoint can she do this? a. Normal view b. Outline view c. Slide Master view d. Slide Sorter view
Answers
Yelena has created timings within her slide show, and she wants to verify that each slide has the correct timing in the Slide Sorter view in PowerPoint.
The correct answer to the given question is option d.
Viewing the Slide Show in Power Point.The default view of the presentation is in Normal view. In this view, we can add content and make modifications to the slides. However, we can also view the slides in various other ways. Let's have a look at each view:
Normal view: This view is the default view and is the view in which we can add and modify the slide content. We can also add and modify slide animations and transitions here.
Outline view: In this view, we can view the text content of the presentation in outline form, which makes it easy to organize the presentation.
Slide Sorter view: This view allows us to view all the slides in the presentation simultaneously, which makes it easy to rearrange the slides or change their timings.Notes Page view: In this view, we can view the speaker notes associated with each slide.
Slide Master view: In this view, we can create and modify slide layouts and templates.The Slide Sorter view allows us to see all the slides in the presentation at once, so it is the best view to use to verify the timings for each slide. We can use the controls at the bottom of the Slide Sorter view to modify the timing of each slide.
For more such questions on PowerPoint, click on:
https://brainly.com/question/28220859
#SPJ8
originally positioned as a replacement to tape, which method of backup is seen as being part of a more sophisticated backup strategy?
Answers
Originally positioned as a replacement to tape, the method of backup seen as being part of a more sophisticated backup strategy is disk-to-disk (D2D) backups. The method of backup that is seen as being part of a more sophisticated backup strategy is disk backup.
Disk backup, also known as hard drive backup, is a type of backup that involves copying data from a computer's hard drive to another disk or drive. This method of backup is faster and more reliable than tape backup, which was originally used for data backup. Additionally, disk backup allows for easier and quicker data retrieval, making it a more sophisticated backup strategy.
Learn more about disk-to-disk: https://brainly.com/question/27960878
#SPJ11
How did the invention of an airplane totally change people’s views of the world?
Answers
Queries are a very useful object in a database, please explain why.
Answers
Answer:
they tell the producer what to do to make their website better
Explanation:
if (learningtocode === 'fun') { print('coding is awesome!'); print('i want to solve more puzzles!'); }
Answers
Assuming the variable learningtocode is equal to 'fun', the code will print "coding is awesome!" and "i want to solve more puzzles!".
This is because the code is written in JavaScript and uses an if statement to check whether the value of the variable learningtocode is equal to 'fun'. If it is, then the two print statements inside the curly braces will be executed. The first print statement will output "coding is awesome!", while the second print statement will output "i want to solve more puzzles!". This code is an example of using conditional logic in programming to execute different actions based on certain conditions.
Lean more about learningtocode here;
https://brainly.com/question/20714866
#SPJ11
A(n) ____________________ is a software tool that examines and reports about vulnerabilities on local and remote hosts.
Answers
A vulnerability scanner is a software tool that examines and reports vulnerabilities on local and remote hosts.
A vulnerability scanner is designed to identify weaknesses or flaws in computer systems, networks, or applications that could be exploited by attackers. It scans the system or network for known vulnerabilities and provides a detailed report on the findings.
Here's how a vulnerability scanner works:
1. Scanning: The vulnerability scanner scans the system or network, searching for vulnerabilities such as missing patches, misconfigurations, weak passwords, or outdated software.
2. Identification: When a vulnerability is found, the scanner identifies the specific issue and provides details about its severity, impact, and recommended actions to mitigate the risk.
3. Reporting: After the scanning process is complete, the vulnerability scanner generates a report that includes a list of vulnerabilities discovered, their severity levels, and suggested remediation steps. This report helps system administrators or IT teams prioritize and address the identified vulnerabilities.
4. Remediation: Once the vulnerabilities are identified, the necessary actions can be taken to fix or mitigate them. This may involve applying patches, updating software, reconfiguring settings, or strengthening security measures.
By using a vulnerability scanner, organizations can proactively identify and address security weaknesses before they can be exploited by malicious actors. Regular scanning and remediation can help ensure the security and integrity of computer systems, networks, and applications.
Overall, a vulnerability scanner is a valuable software tool for assessing the security posture of systems and networks by identifying and reporting vulnerabilities.
To know more about the word vulnerability, visit:
https://brainly.com/question/30296040
#SPJ11
Your _______ can help block inappropriate content online.
1. web browser
2. Password
Answers
Answer:
web browser.
Explanation:
yea let me go post my password to block content (sarcasm)
i need help debugging this code
public challenge 1_2b
{
/* fix all the errors in this code */
public static void main(String[] args)
{
System.out.print("Baby");
System.out.print("Shark");
System.out.print("Do Doo Do Do Do Doo");
}
}
Answers
Jack decides to apply a style to the vocabulary terms in his report. In the first section, he includes the vocabulary word "telescope.” The James Webb Telescope The James Webb Telescope, called Webb or JWST, is more powerful than the Hubble Space Telescope. A telescope is a tool used to view faraway objects. The Webb will have the ability to look at the first galaxies that formed the universe. It will also be able to look into dust clouds and observe how stars and planetary systems form. Which style did Jack use on the vocabulary words in his report?
strong
intense strong
emphasis
intense emphasis
Answers
Answer:
intense emphasis
Explanation:
I got it right
Answer:
D. intense emphasis
Explanation:
I just answered the question
edge 2021
The _____________ is the address of a piece of data.
Answers
Answer:
Question 1:
Ans: index
Index is a unique position to identify a particular value in an array.
Question 2:
Ans: Element
Element is the individual value present in the array. An array is used to store one or more element.
Question 3
Ans: String
We can find from the question that the value is enclosed within "" (double quotes). So, the value added to the array is string. Any value that is enclosed within double quotes are termed as string.
Question 4:
Indexes are always int. Array index are never float. This is because, it represent the position.
Question 5:
The output will be 3. The reason is there are 3 values appended to the array "stuff" in the given piece of program.
Question 6:
The given code is an example of initializer list. Price is a list variable where the values are initialized.
Explanation:
let us consider a simple 20. m2 rooftop installation of crystalline-silicon (c-si) pv modules. remember that pv modules are rated to receive 1.0 kw/m2 of solar radiation. assuming peak solar irradiance of 1.0 kw/m2, what would the peak output of this system be (in kw) if the modules are 18% efficient? [2 points]
Answers
The peak output of the system would be 18% * 20 kW = <<18*.01*20=3.6>>3.6 kW. Thus, the peak output of this system be \boxed{3.6} (in kw) if the modules are 18% efficient.
PV modules are photovoltaic modules, which are units made up of multiple photovoltaic cells. These modules are used to convert sunlight into electricity. They are a key component in solar power systems, and are often used to power homes and businesses. The electricity generated by PV modules can be used immediately, or it can be stored in a battery for later use.
If a 20 square meter rooftop installation receives 1.0 kW/m^2 of solar radiation, the total amount of solar radiation it receives is 20 * 1.0 = <<20*1.0=20>>20 kW.
Since the modules are 18% efficient, the peak output of the system would be 18% * 20 kW = <<18*.01*20=3.6>>3.6 kW. Answer: \boxed{3.6}.
Learn more about peak output, here https://brainly.com/question/13937812
#SPJ4
Compulsory Task 2 Follow these steps: A simple rule to determine whether a year is a leap year is to test whether it is a multiple of 4. • Create a program called task2.py. • Write a program to input a year and a number of years. • Then determine and display which of those years were or will be leap years. What year do you want to start with? 1994 How many years do you want to check? 8 1994 isn't a leap year 1995 isn't a leap year 1996 is a leap year 1997 isn't a leap year 1998 isn't a leap year 1999 isn't a leap year 2000 is a leap year 2001 isn't a leap year • Compile, save and run your file.
Answers
Here's an example implementation of the task2.py program in Python:
def is_leap_year(year):
if year % 4 == 0:
if year % 100 == 0:
if year % 400 == 0:
return True
else:
return False
else:
return True
else:
return False
start_year = int(input("What year do you want to start with? "))
num_years = int(input("How many years do you want to check? "))
for i in range(num_years):
current_year = start_year + i
if is_leap_year(current_year):
print(current_year, "is a leap year")
else:
print(current_year, "isn't a leap year")
The program defines a function is_leap_year() that checks if a given year is a leap year according to the given rule. It then prompts the user to enter the starting year and the number of years to check.
Using a loop, it iterates over the specified range of years, calls the is_leap_year() function for each year, and prints the appropriate message indicating whether the year is a leap year or not.
You can compile and run this program using a Python interpreter or IDE. After running the program, you can enter the starting year (e.g., 1994) and the number of years to check (e.g., 8), and the program will display the leap years for the specified range.
you can learn more about program at: brainly.com/question/31163921
#SPJ11
write a function called reverseletters that takes an input phrase consisting of a single word and reverses the sequence of letters between the first letter and last letter. the input phrase could be a character vector of any length. restrictions: the function may not use loops. ex: >> sout
Answers
The implementation of the reverseletters function in Python is as follows:
def reverseletters(input_phrase):
if len(input_phrase) <= 2:
return input_phrase
return input_phrase[0] + input_phrase[-2:0:-1] + input_phrase[-1]
input_phrase = "hello world"
output_phrase = reverseletters(input_phrase)
print(output_phrase)
Explanation:
This function first checks if the length of the input phrase is less than or equal to 2, in which case the phrase is returned unchanged. Otherwise, it returns the first letter of the input phrase (input_phrase[0]) followed by the reversed sequence of letters between the last letter and the second letter (input_phrase[-2:0:-1]) and finally followed by the last letter of the input phrase (input_phrase[-1]). This implementation assumes that the input phrase consists of a single word with no spaces in the middle. If the input phrase contains spaces or punctuation, the function will not behave correctly.
To know more about function click here:
https://brainly.com/question/31219120
#SPJ11
me dicen cómo hacer este programa en lenguaje C?:
"leer 10 numeros enteros y decir cuantos terminan en 7"
yo no se cómo hacerlo, por el momento se me ocurre esto, pero no se si esta bien encaminado:
#include <stdio.h>
#include <stdlib.h>
int main()
{
int i,num,cont=0;
for(i=0;i<=10;i++)
{
printf("ingrese un numero:");
scanf("%d", &num);
}
if(i%num==7)
cont=cont+1;
else
{
printf("ingrese un numero:");
}
printf("la cantidad de numeros que terminan en 7 es: %d", cont);
return 0;
}
Answers
Answer:
Wut tha h-
Explanation:
Im not rude lol.