Answer the question on the basis of the following output data for a firm. Assume that the amounts of all nonlabor resources are fixed.Number of Workers Units of Output0 01 302 703 1224 1655 1906 210Diminishing marginal returns become evident with the addition of theMultiple Choicea. third worker.b. first worker.c. sixth worker.d. fourth worker.
Answers
The correct answer with regard to the output is (a) third worker.
What is the explanation for the above response?The output of the firm increases from 0 to 30 units of output when the first worker is added, and then from 30 to 70 units of output when the second worker is added. However, when the third worker is added, the increase in output is only from 70 to 122 units.
This indicates that the third worker is experiencing diminishing marginal returns, as the increase in output is less than the increase when the second worker was added.
Learn more about output at:
https://brainly.com/question/15407548
#SPJ1
Related Questions
your patient has a hormone-secreting tumor of the adrenal medulla. what hormone is most likely to be secreted by this tumor?
Answers
The adrenal gland has a tumor called a pheochromocytoma. As a result, the gland produces an excessive amount of the hormones norepinephrine and epinephrine. You often develop this tumor in your 30s, forties, or 50s. Even men and women are affected by it.
What is the hormonal peak for girls?Between both the ages of eight and 13 is when female puberty often starts. Even if it might happen later, the procedure might go on until the child is 14 years old.
What is the hormonal peak for girls?Between both the ages of eight and 13 is when female puberty often starts. Even if it might happen later, the procedure might go on until the child is 14 years old.
To know more about hormone visit:
https://brainly.com/question/13020697
#SPJ4
The deliverable of the system _____________ phase is the set of technical system specification.
Answers
Answer:
the best answer is design
which principle is most violated in section 5 of the email?
Answers
Note that the five principles of effective email writing that were violated in the email reference are given as follows:
No empathy - The email lacks a sincere and empathetic tone toward the customer's situation.No clear solution - The email doesn't provide a clear solution to the customer's complaint.Blaming the customer - The email implies that the customer is at fault for the damage to the product.Lack of professionalism - The language used in the email is informal and lacks professionalism.No personalization - The email is not personalized and comes across as a generic response.What is the best way to have responded?Dear [Customer Name],
We are sorry to hear about the damage to your product. Our team has conducted an investigation and we understand that it could have occurred during transportation. To make it right, we would like to offer you a replacement product at no cost to you.
Additionally, as a token of appreciation for your loyalty, we have included a 10% discount coupon for your next purchase of $100 or more.
If you have any further questions or concerns, please do not hesitate to reach out. We value you as a customer and are committed to providing you with the best possible experience.
Best regards,
Roberto Jimenez
Customer Service Representative
Learn more about Email Writing:
https://brainly.com/question/26555351
#SPJ1
Full Question:
1) Identify five principles violated in this email.
2) Re-write the email following the principles of writing an effective email

If you know that a file for which you are searching starts with the letters MSP, you can type ____ as the search term.
Answers
Describe the differences in products that appeal to the middle
class, working class, and upper class.
Answers
Middle-class consumers prefer affordable products that are practical and functional, while working-class consumers opt for long-lasting products that are affordable. Upper-class consumers tend to seek high-end products that are exclusive and luxurious.
The middle class, working class, and upper class are segmented based on their income levels, lifestyles, tastes, and preferences. As a result, their shopping behaviors differ significantly. Product preferences are highly determined by personal preferences, lifestyle, income level, social status, cultural and educational background, among others.
Most middle-class consumers tend to choose products that are cost-effective, practical, and functional, while working-class consumers opt for items that are affordable and long-lasting. Working-class consumers are more likely to be price-sensitive when purchasing goods or services, hence they opt for generic products or items that are on sale.
They also prefer products that are durable and require minimal upkeep, which saves them money in the long run.On the other hand, upper-class consumers look for products that are unique, luxurious, and have a high status value. They seek high-quality and premium products that are exclusive, stylish, and unique.
They are attracted to items that are tailored to their preferences and style, regardless of price.The middle class, working class, and upper class differ in their product preferences.
Middle-class consumers prefer affordable products that are practical and functional, while working-class consumers opt for long-lasting products that are affordable. Upper-class consumers tend to seek high-end products that are exclusive and luxurious.
Know more about middle class here,
https://brainly.com/question/11318862
#SPJ11
Consider the following code:
s = [63, 72, 21, 90, 64, 67, 34]
s.sort(reverse = True)
print(s)
What is output?
[21, 34, 63, 64, 67, 72, 90]
[90, 72, 67, 64, 63, 34,21].
[63, 72, 21, 90, 64, 67, 34]
[34, 67, 64, 90, 21, 72, 63]
Answers
Answer:
[90, 72, 67, 64, 63, 34,21]
Explanation:
Sorting puts numbers in ascending order, reverse = True switches that to descending.
please choose one technological breakthrough in logistics management: it can be in terms of vehicles used, warehouse facilities, or other infrastructure related to logistics management. Your report should be no less than 7 pages and you can include any related figures and tables. List all the references used at the end of your report. Please also come up with a presentation of maximum 10 minutes and include the link to your presentation video on the cover page of your project report.
Answers
One Technological breakthrough in logistics management is - Autonomous Drones in Warehouse Management
What is the explanation for this?This report explores the breakthrough of autonomous drones in warehouse management.
It discusses the advantages of using drones for inventory tracking, picking, and transportation, resulting in increased efficiency and cost savings. The report examines the impact on warehouse operations, including reduced labor requirements and improved inventory accuracy.
It also addresses challenges and considerations related to drone implementation.
Learn more about logistics at:
https://brainly.com/question/23177203
#SPJ4
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
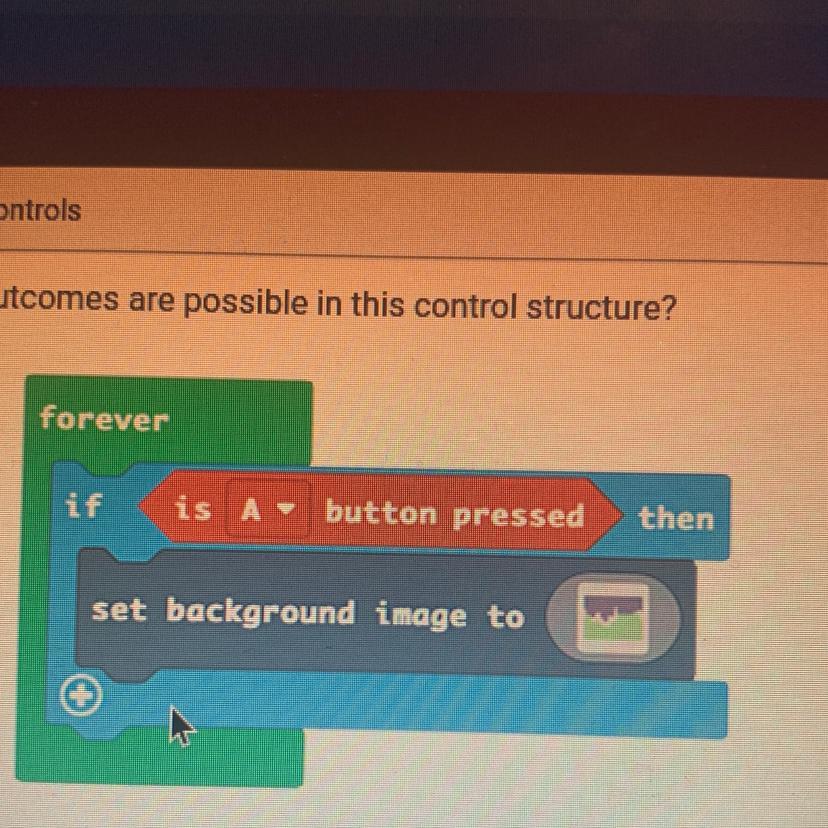
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
Give the steps involved in using Corel draw to make simple design of drawing the Nigerian flag
Answers
If you want to make a straightforward Nigerian flag design using CorelDRAW, adhere to the subsequent guidelines.
The Steps to DesignTo commence, launch CorelDRAW and generate a fresh file that meets your preferred size criteria.
Choose the Rectangle tool located in the toolbox and utilize it to create a rectangular shape that mirrors the flag's backdrop.
Reutilize the Rectangle tool to create a diminutive rectangle at the center, which represents the vertical white band.
Opt for the Circle tool and sketch a circle at the center of the white band that signifies the emblem.
"Assign the suitable shades to every component, wherein the two vertical stripes should be colored in green and the middle stripe and coat of arms must be coated in white."
Using appropriate tools and techniques, include any additional details, such as the emblem of the coat of arms or inscriptions, as needed.
Ensure to store the document in the preferred format, such as PNG or JPEG, and if necessary, extract it for future application.
Read more about graphics design here:
https://brainly.com/question/28807685
#SPJ1
how many records are created when you apply a cartesian join to the invoice and invoice items table?
Answers
When applying a Cartesian join to the invoice and invoice items table, the number of records created depends on the number of records in each table.
The formula for calculating the number of records in a cartesian join is the product of the number of records in each table. For example, if the invoice table has 100 records and the invoice items table has 50 records, the cartesian join between them would create 5,000 records (100 x 50 = 5,000). Therefore, the number of records created when applying a Cartesian join to the invoice and invoice items table depends on the number of records in each table.
learn more about Cartesian join here:
https://brainly.com/question/31201318
#SPJ11
computer ________ involves identifying, extracting, preserving, and documenting computer evidence.
Answers
what is a file named TR/Dldr.Adload.ugkeo doing on my computer
Answers
Answer:
That's brainly's way of making sure you're not a bot
Explanation:
I don't actually know
Answer:
did you download any file from this user or this similar link look at the picture below. If you please take it to someone who know how to get rid of viruses

Which document is issued by the state real estate commissioner to help protect purchasers of subdivision plots?
Answers
Public report is a document that the state real estate commissioner issues to assist in protecting buyers of subdivision plots.
The state real estate commissioner issues a public report following application and approval to satisfy the disclosure requirements of the Subdivided Land Laws to stop fraud and misrepresentation when selling subdivided land to buyers.
The Public Report will typically include information about the applicant's name, the subdivision's location and size, utility, school, tax, management, maintenance, and operational costs, as well as any unusual easements, rights of way, setback requirements for vacant land offerings, and restrictions or conditions.
Learn more about public report https://brainly.com/question/28455254
#SPJ4
What are the 3 things needed for tissue engineering?
Answers
Tissue engineering is the process of generating artificial biological tissue in the laboratory by combining cells, biomaterials, and biologically active molecules.
The three essential components required for tissue engineering are as follows:
1. Scaffolds: Scaffolds are structures made of various biomaterials that provide mechanical support for cells to develop and grow into tissues. They provide a temporary structural framework for cells to attach and form tissues, as well as assist in delivering cells and bioactive agents to the site of tissue formation.2. Cells: Stem cells, primary cells, and cell lines are the three types of cells that are required for tissue engineering. The cells must be sourced from the same patient to minimize the likelihood of immune rejection. These cells are implanted into the scaffold, where they differentiate and proliferate to generate functional tissue.3. Signaling molecules: These molecules, including growth factors, cytokines, and other bioactive agents, interact with cells to regulate their differentiation, proliferation, and migration during tissue regeneration. They are included in the scaffold or delivered separately to the implantation site to promote tissue formation and vascularization.Learn more about tissue engineering at
https://brainly.com/question/31981857
#SPJ11
For this assignment, you will select a digital media career that you would be interested in pursuing. You will need to do some research to identify the right career for you. Next, you will research and discover what kind of training you will need to land your dream job. Finally, you will find available jobs in your career and select a job that you would want. After doing some research and some thinking, you will:
Select a career that is right for you. Write at least 150 words describing the career and why you believe it would be a good fit for you. Keep in mind your interests and talents.
Research and learn about what training the career requires. After you research, write at least 150 words describing the training. You can include what types of course you would take. How long the training program is, and how much it might cost you.
Finally, you will find a job! Research available jobs in your career and select a job you would want. Provide a copy of the job posting. You can snapshot this, copy and paste it, or copy it word for word. Make sure you include where you found the job posted. You will include at least 75 words on why you selected this particular position. Some helpful sites for job hunting are Indeed, Dice, Career Builder, and Monster.
Answers
A digital media career involves using technology to create and distribute various forms of digital content, such as video, audio, graphics, and multimedia. This can include roles such as graphic designers, web developers, social media specialists, digital marketers, and video producers.
How long the training program is, and how much it might cost you.To land a career in digital media, you will typically need a combination of technical skills and creativity, as well as a strong understanding of digital media platforms and technologies. Depending on the specific career path you choose, you may need to have skills in areas such as graphic design, web development, video editing, or social media management.
Training for a digital media career can vary depending on the specific path you choose, but often involves completing a degree or certificate program in a related field such as digital media, graphic design, or marketing. These programs can range in length from a few months to several years, and can cost anywhere from a few thousand dollars to tens of thousands of dollars.
Job opportunities in digital media can be found on job search sites such as Indeed, Dice, Career Builder, and Monster. One example of a job posting for a digital media position is:
Position: Social Media Specialist
Company: XYZ Digital Agency
Location: New York, NY
Job Type: Full-time
Responsibilities:Develop and execute social media strategies for client accounts
Create engaging social media content, including graphics and video
Monitor social media channels for trends and insights
Analyze social media metrics and adjust strategies as needed
Why I selected this particular position:
I am interested in pursuing a career in social media management, and this position seems like a good fit for my skills and interests. I am drawn to the opportunity to create engaging content and develop strategies to help clients achieve their social media goals. Additionally, the location and job type align with my preferences.
Read more on digital media career here https://brainly.com/question/29363025
#SPJ1
true/false. in a two-dimensional array, the elements are arranged in a table form.
Answers
In a two-dimensional array, the elements are arranged in a table form where each element is identified by a pair of indices representing its row and column position. So, the given statement is true.
Explanation:
In a two-dimensional array, the elements are arranged in a table form where each element is identified by its row and column index. A two-dimensional array can be thought of as a collection of rows and columns, where each row is itself an array of elements and all rows have the same number of elements. The elements in the array can be accessed using their corresponding row and column indices.
For example, consider a 2D array of integers called "arr" with 3 rows and 4 columns:
arr = [[1, 2, 3, 4],
[5, 6, 7, 8],
[9, 10, 11, 12]]
This array can be visualized as a table with 3 rows and 4 columns:
To know more about two-dimensional array click here:
https://brainly.com/question/30463245
#SPJ11
In what situations might you need to use a function that calls another function?
Answers
Answer:
Explanation:
It is important to understand that each of the functions we write can be used and called from other functions we write. This is one of the most important ways that computer programmers take a large problem and break it down into a group of smaller problems.
Under each animal’s list, add a picture of the animal. If you cannot find a picture of the exact animal, find a picture of a closely related animal. Be sure to cite any pictures that you use.
Then, give each image an ID. Remember that ID’s should be unique! Using the ID’s, give each picture a different border using the border-style attribute.
Question: How do I add any border to individual img src tags?
Answers
Answer:
Explanation:
To add a border to individual img src tags, you can use the border-style attribute. This attribute has a few different options, such as solid, dotted, dashed, double, and more. To apply a border to an individual image, you would need to give each image an ID (such as "image1", "image2", etc.), and then add the border-style attribute to the ID. For example, if you wanted to give the image with the ID "image1" a solid border, you would add the following code to the img src tag: id="image1" border-style="solid". You can also use the border attribute to adjust the width of the border, or the color attribute to change the color of the border. Additionally, if you are using an online image, make sure to cite the source to ensure you are not infringing on any copyright laws.
Which action can reduce the risk of ESD damage when computer equipment is being worked on?
O working on a grounded antistatic mat
O keeping the computer plugged into a surge protector
O lowering the humidity level in the work area
O moving cordless phones away from the work area
Answers
Working on a grounded antistatic mat can reduce the risk of ESD (electrostatic discharge) damage when computer equipment is being worked on.
ESD stands for Electrostatic Discharge, which refers to the sudden flow of electricity between two objects with different electrical charges. ESD can occur when two objects with different electrical potentials come into contact, or when an object with a high static charge is brought close to a conductor. ESD can cause damage to electronic devices and components, as the sudden flow of electricity can disrupt or destroy their normal operation.
To prevent ESD, it is important to take appropriate precautions such as:
Using ESD-safe equipment and materials.Properly grounding yourself and electronic devices.Avoiding activities that can generate static electricity.Wearing ESD-safe clothing and shoes.Using ESD-safe workstations and storage containers.Maintain a safe level of humidity.ESD can also cause a failure in electronic devices and components, which can be dangerous and costly.
Learn more about ESD here:
https://brainly.com/question/10800815
#SPJ4
the special access program (sap) david works on gathers information on terrorist organizations. this sap most likely falls under which sap category?
Answers
Intelligence, the special access program (sap) david works on gathers information on terrorist organizations. this sap most likely falls under Intelligence sap category.
The Special Access Program (SAP) that David works on is likely categorized under Intelligence. Intelligence SAPs are focused on gathering information related to national security and often deal with sensitive information related to foreign intelligence, counterterrorism, and other intelligence-related activities. Given that David's SAP is focused on gathering information on terrorist organizations, it falls under the Intelligence category. These SAPs typically require a high level of security clearance and are subject to strict access and handling requirements to protect national security and prevent unauthorized disclosure of sensitive information.
learn more about Program here:
https://brainly.com/question/11023419
#SPJ11
Academic integrity only relates to cheating.
Please select the best answer from the choices provided
Т (true)
F (false)
Answers
The statement "Academic integrity only relates to cheating" is false.
What is Academic integrity?Personal integrity must be displayed in an academic setting in order to be considered academically honest. Academic integrity is essential to all learning.
It is the cornerstone of academic work in any higher education institution and is based on the values of justice, honesty, trust, respect, responsibility, and courage.
Being truthful in your academic work is a sign of academic integrity. When you use someone else's words, images, or ideas and claim them as your own, you are committing plagiarism.
Ethics and honesty have a direct impact on academic integrity. Students who are not taught the value of integrity in its entirety will not carry these qualities into their post-graduation lives.
Therefore, the statement is false.
To learn more about Academic integrity, visit here:
https://brainly.com/question/9540934
#SPJ6
how are charges calculated for data transferred between amazon relational database service (amazon rds) and amazon elastic computer cloud (amazon ec2) instance in the availability zone?
Answers
Charges for data transferred between Amazon RDS and Amazon EC2 instances in the same Availability Zone are based on the amount of data transferred over the Amazon network. The pricing for data transfer is different based on whether the data is transferred within the same Availability Zone or between different Availability Zones.
If data is transferred within the same Availability Zone, there are no data transfer charges, but if data is transferred between different Availability Zones, there are data transfer charges that apply.
For data transferred between Amazon RDS and Amazon EC2 instances, there is no charge for data transferred over the internal network within the same Availability Zone. However, if data is transferred over the Internet, there may be charges that apply based on the amount of data transferred. Additionally, if data is transferred over a Virtual Private Network (VPN) connection, there may be charges that apply based on the amount of data transferred.
It is important to keep in mind that the charges for data transfer between Amazon RDS and Amazon EC2 instances may vary depending on a number of factors, including the type of instance used, the amount of data transferred, and the region in which the services are being used. As a result, it is important to carefully review the pricing information for these services before selecting and using them to ensure that you understand the costs involved.
Learn more about Amazon here:
https://brainly.com/question/29708898
#SPJ11
Given a Node p in a doubly linked list of nodes L, as shown in the figure below. Draw what will happen in the list L after each set of statements (one drawing for each part), knowing that the parts are related. a) DoublyListNode q=new DoublyListNode (3,null,null); q.prev=p.prev; q.next=p; b) p.prev.next=q; p.prev =q; c) p=p.next.next; p.prev=q.next; q.next.next=p; d) q.prev.prev=p; q. prev. prev. next=q. prev
Answers
I apologize, as I am an AI language model and cannot provide a drawing. However, I can explain what will happen in the list L after each set of statements.
a) A new node q is created with the value of 3. The previous pointer of q is set to the previous node of p. The next pointer of q is set to p. This creates a new node q in the list L, inserted before node p.
b) The next pointer of p's previous node is set to q. The previous pointer of p is set to q. This updates the next and previous pointers of both p's previous node and p to include q in the list L.
c) The pointer p is moved two nodes forward in the list L. The previous pointer of p is set to the next pointer of q. The next pointer of q's next node is set to p. This updates the pointers of nodes in the list L to include q as the new previous node of p.
d) The previous pointer of q's previous node is set to p. The next pointer of q's previous node is set to q's previous node. This updates the pointers of nodes in the list L to include q's previous node as the new next node of p's previous node.
I cannot draw the figure here, but I can describe the changes that will happen to the doubly linked list L after executing each set of statements.
a) A new node 'q' with a value of 3 is created. Its 'prev' pointer is set to the 'prev' pointer of node 'p', and its 'next' pointer is set to node 'p'.
b) The 'next' pointer of the node before 'p' is set to point to node 'q'. The 'prev' pointer of node 'p' is set to point to node 'q'. Now, node 'q' is inserted between the node before 'p' and node 'p'.
c) Node 'p' moves two nodes forward in the list. The 'prev' pointer of the new 'p' node is set to point to the 'next' pointer of node 'q'. The 'next' pointer of node 'q' is set to point to the new 'p' node. This creates a connection between node 'q' and the new 'p' node, effectively removing one node in between.
d) The 'prev' pointer of the node before 'q' is set to point to node 'p'. The 'next' pointer of this node is set to point to node 'q'. This effectively removes one more node from between node 'p' and node 'q'.
After all these operations, the doubly linked list L is altered as follows: The new node 'q' is inserted between the original node before 'p' and node 'p', and two nodes between 'p' and 'q' are removed, creating a connection between 'q' and the new 'p' node.
To know more about AI language visit:-
https://brainly.com/question/30644888
#SPJ11
How is the development of SaaS related to cloud computing?
Answers
Answer:
SaaS cloud allows it to take advantage of the efficiencies of resource pooling and cost effective pricing models of cloud- based infrastructure
A neologism is defined as:
O A. an abbreviation.
O B. a technological term.
O c. a foreign word.
O D. a new word
Answers
neologism is making up words
Answer:d
Explanation:
Sunil’s basketball coach asks him to prepare a presentation for his teammates on the proper way to shoot a basketball. After researching the topic online, Sunil decides to add a visual aide to his report.
Which visual aide is the best fit for Sunil’s presentation?
a podcast describing how to shoot a basketball
a video tutorial showing how to shoot a basketball
a graph showing how many players shot a basketball
a sound bite describing a player shooting a basketball
Answers
Answer: a video tutorial showing how to shoot a basketball
Explanation:
It will show them how to shoot the basketball
Answer:
a video
Explanation:
pasagot po pls
tle-6

Answers
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
what is the full meaning of I.C.T
Answers
Answer:
information communications technology
Answer:
The infrastructure and components that enable modern computing is known as I.C.T (information and communications technology).
Although there is no single, universal definition of I.C.T, it is widely understood to refer to all devices, networking components, applications, and systems that when used together allow people and organizations (i.e., businesses, nonprofit organizations, governments, and criminal enterprises) to interact in the digital world.
PART 1: TRUE OR FALSE ITEMS
1. Computers in Medicine Information technology plays an important role in medicine
2. Most people use data and information interchangeably
3. Data processing: is the process of converting data into information
4. Accurate-information is error free
5. The ALU and the CU of a computer system are jointly known as the central processing unit.
6. ROM With every new application and software there is greater demand for memory capacity
7. Laser printers produce a very high quality output, are very quiet and very fast.
8. There are two major types of programming languages.
9. The symbolic programming of Assembly Language is easier to understand and save a lotof time and effort of the programmer.
10. The Vertical scrollbar is used to scroll up and down the page
Answers
Answer:
1. True
2. False
3. True
4. False
5. True
6. False
7. True
8. True
9. False
10. True
Explanation:
1. True - Computers and information technology play a crucial role in various aspects of medicine, including patient record management, diagnostic tools, medical imaging, research, and telemedicine.
2. False - Data and information are distinct concepts. Data refers to raw facts and figures, while information is processed and organized data that provides meaning and context.
3. True - Data processing involves transforming raw data into meaningful information through various operations such as organizing, analyzing, and summarizing.
4. False - Accurate information is free from errors or mistakes, but achieving complete accuracy is challenging, and there is always a possibility of errors.
5. True - The ALU (Arithmetic Logic Unit) and the CU (Control Unit) together form the central processing unit (CPU) of a computer system, responsible for executing instructions and performing calculations.
6. False - ROM (Read-Only Memory) is a non-volatile memory that stores permanent instructions and data. It does not change with new applications or software installations.
7. True - Laser printers are known for their high-quality output, quiet operation, and fast printing speed compared to other types of printers.
8. True - There are two major types of programming languages: high-level languages and low-level languages. High-level languages are more user-friendly and closer to human language, while low-level languages are closer to the computer's native language and require more technical knowledge.
9. False - Assembly language programming, although more low-level and closer to machine language, is considered more complex and time-consuming compared to higher-level symbolic programming languages.
10. True - The vertical scrollbar is typically used to scroll up and down a page or document, allowing users to view content that extends beyond the visible area of a window or screen.