arduino programming language is a simplified version of ______ which is maintained by arudino.cc
Answers
The arduino programming language is a simplified version of C++ which is maintained by arduino.cc.
The Arduino programming language is a simplified version of C++, which is maintained by Arduino.cc.
C++ is a general-purpose programming language that is widely used for developing a variety of software applications, including operating systems, video games, and embedded systems. It is a powerful language that allows for low-level memory manipulation and direct hardware access.
The Arduino programming language simplifies C++ by providing a set of pre-written libraries and functions that abstract away the low-level details of hardware communication. This makes it easier for beginners and non-programmers to get started with embedded systems development.
The Arduino programming language also includes a simplified syntax and a simplified version of the C++ standard library. The language is compiled using the GNU C++ compiler, which generates machine code that runs on the Arduino's microcontroller. The Arduino Integrated Development Environment (IDE) provides a user-friendly interface for writing, compiling, and uploading Arduino programs to the microcontroller.
Learn more about arduino programming language here:
https://brainly.com/question/12216796
#SPJ11
The Arduino programming language is a simplified version of C++, which is maintained by arduino.cc.
C++ is a high-level, object-oriented programming language that is widely used for developing applications that run on a variety of platforms, including desktop computers, servers, mobile devices, and embedded systems.
Arduino programming language is based on C++, but it has been modified and simplified to make it easier for beginners to learn and use.
The language has a streamlined syntax and includes libraries that provide easy access to the features of the Arduino hardware.
Libraries make it possible to interface with sensors, motors, and other components using simple commands, without the need for complex programming.
Despite its simplicity, the Arduino programming language is powerful enough to support a wide range of applications, from simple LED blinkers to advanced robotics projects.
It is a popular choice among hobbyists, students, and professionals who are interested in building and prototyping electronic devices and systems.
The Arduino.cc website provides a wealth of resources, including tutorials, forums, and documentation, to help users get started with the language and create their own projects.
For similar questions on Language
https://brainly.com/question/10585737
#SPJ11
Related Questions
a concern when performing regular backups of virtual servers from the host computer is that ____________________ files on a virtual server do not show that it has been backed up.
Answers
The main concern when performing regular backups of virtual servers from the host computer is that snapshot files on a virtual server do not show that it has been backed up.
Virtual machines (VMs) can be copied or moved to a new location in a process known as backup and restore in a virtual environment. Backing up a VM produces a snapshot of the VM, which includes files and other data that are stored on the VM's virtual disk. Snapshots are generated by backup applications, which are used to protect data against hardware or software failures, human error, or other unforeseen events.
When a snapshot is created, it is stored in the backup repository, and the data is compressed and encrypted to ensure that it is secure and protected. The primary concern when performing backups of virtual servers from the host computer is that snapshot files on a virtual server do not show that it has been backed up. This could result in a loss of data if a disaster or other event occurs that requires the data to be restored from the backup. To avoid this problem, it is important to regularly test your backup and restore process to ensure that your virtual servers are properly protected.
To know more about virtual server visit:
https://brainly.com/question/32287835
#SPJ11
Can you solve this challenging activity?

Answers
Answer:
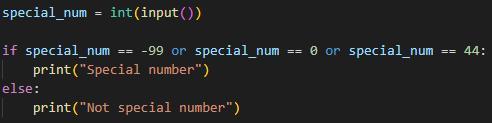
special_num = int(input())
if special_num == -99 or special_num == 0 or special_num == 44:
print("Special number")
else:
print("Not special number")
Explanation:
If “A” represents in binary 10011001, what will be the value of word “CAB”?
Answers
Answer:
01000011 01000001 01000010
Explanation:
You can convert to and from binary and the base-10 system typically used by humans. You can also convert to and from binary and hexadecimal where you need four digits of binary to represent one digit of hex. Converting to and from binary and octal is another possibility. It takes three binary digits to represent an octal digit. Binary 000 is octal digit 0.
For which of the following are music editors responsible? (Select all that apply).
editing a film’s score
structuring the soundtrack
shooting interiors
editing a film’s musical soundtrack
Answers
Answer:
A: structuring the soundtrack
B: editing a film's score
D: editing a films musical soundtrack
Explanation:
edg2021
(other test answers:
(all but "long-lasting shots of the characters speaking"
true (that film editors review footage and notes from director...)
computer graphics
it indicates an exterior shot of an urban street scene )

Q9. Complete the table with the name of the functions
1. Excel function to lookup data in a table organized
Vertically.
2. Is a function to sum cells that meet criteria.
3. Function to find the total number of entries in a
Column.
4. Runs a logical test and returns one value for a TRUE result, and another for a FALSE result
5. Excel function to lookup data in a table organized
Horizontally.
Answers
Answer:
1. VLOOKUP function.
2. SUMIF function.
3. COUNT function.
4. IF function.
5. HLOOKUP function.
Explanation:
Microsoft Excel is a software application or program designed and developed by Microsoft Inc., for analyzing and visualizing spreadsheet documents. There are different types of functions used in Microsoft Excel to perform specific tasks and these includes;
1. VLOOKUP function: it's an Excel function that avails end users the ability to lookup data in a table organized vertically. Thus, it's typically used for searching values in a column.
2. SUMIF function: it is an Excel function to sum cells that meet criteria such as text, dates and numbers. This function can be used with the following logical operators; <, >, and =.
3. COUNT function: it's an Excel function to find the total number of entries in a column. For example, to count the number of entries in B1:B15; COUNT(B2:B15).
4. IF function: runs a logical test and returns one value for a TRUE result, and another for a FALSE result. For example, to fail scores that are below 40; IF (A1 < 40, "Fail", "Pass").
5. HLOOKUP function: it's an Excel function that avails end users the ability to lookup data in a table organized horizontally. Thus, it's typically used for searching values in a column.
General requirements in this project, you will design and implement a system for a bank that has customers as users of the system, and bank accounts as products. You will need to establish a name for your business and the system. The system: a. Loads in data customers and accounts by reading input files and storing the data in arrays ; b. Processes transactions for customers; c. Updates bank accounts based on transactions; d. Writes the transactions to a file at the end of the program. Your project will use classes, methods, arrays, iteration, and text files. The system should have the following methods: login, reading files, writing to files, processing transactions (deposit, withdraw, display balances, and transfer between accounts)
Answers
They are outlined in a User Requirements Specification and can include, for example, ability to create various reports, view order history etc .
What is deposits?A deposit encompasses two different meanings. One kind of deposit involves a transfer of funds to another party for safekeeping. Using this definition, deposit refers to the money an investor transfers into a savings or checking account held at a bank or credit union.In this usage, the money deposited still belongs to the person or entity that deposited the money, and that person or entity can withdraw the money at any time, transfer it to another person’s account, or use the money to purchase goods.Often, a person must deposit a certain amount of money in order to open a new bank account, known as a minimum deposit. Depositing money into a typical checking account qualifies as a transaction deposit, which means that the funds are immediately available and liquid, without any delays.To learn more about transaction deposit refer to:
https://brainly.com/question/18529242
#SPJ4
Your cousin, a senior in high school, asks you to play a Jeopardy-style game with her to help prepare for her computer science exam next week. She gives you these two clues about a type of relational database key: No column values may be NULL, and columns may be combined to create a unique primary key. Which type of key is she referring to
Answers
Answer:
She is referring to composite primary key
Explanation:
Composite primary key comprises of several columns with each having column having its own individual uniqueness.
In a composite primary, all columns need to have some value as none of them can be null. Also, these individual columns are grouped to get a unique value.
You are part of a penetration testing team hired to test an organization's network security. The first phase of the test involves reconnaissance to discover which network services might be exposed to the Internet. Which tool should be used to complete this phase as quickly as possible
Answers
There are different phase of the test that involves reconnaissance The tool that should be used to complete this phase as quickly as possible is Port Scanner.
What is a reconnaissance phase? Reconnaissance is simply referred to as a preparatory phase. This is the phase where an hacker collect different information about a target before they launch an attack and is said to be completed in phases before they exploit the system vulnerabilities.The first phases of Reconnaissance is called dumpster diving. A port scan is a known to be a technique that hackers use to show or known the open doors or weak points in a network.
Learn more about Scanner from
https://brainly.com/question/10097616
Lee has discovered what he thinks is a clever recursive strategy for printing the elements in a sequence (string, tuple, or list). He reasons that he can get at the first element in a sequence using the 0 index, and he can obtain a sequence of the rest of the elements by slicing from index 1. This strategy is realized in a function that expects just the sequence as an argument. If the sequence is not empty, the first element in the sequence is printed and then a recursive call is executed. On each recursive call, the sequence argument is sliced using the range 1:. Here is Lee’s function definition:
def printAll(seq):
if seq:
print(seq[0])
Answers
Lee's recursive printing strategy involves accessing the first element of a sequence using the 0 index and then making a recursive call to print the rest of the elements using slicing from index 1. The process continues until the sequence is empty, and all elements have been printed.
Lee's clever recursive strategy for printing the elements in a sequence involves using the 0 index to access the first element and slicing from index 1 to get the rest of the elements. The function definition for printAll(seq) is:```python
def printAll(seq):
if seq:
print(seq[0])
printAll(seq[1:])
```
This function works by:
1. Checking if the sequence is not empty.
2. Printing the first element of the sequence using the 0 index (seq[0]).
3. Making a recursive call to printAll() with the rest of the elements in the sequence, slicing from index 1 (seq[1:]).This process continues until the sequence is empty, at which point the recursion stops, and all elements of the sequence have been printed.
Learn more about recursive printing: https://brainly.com/question/30768149
#SPJ11
If you witness physical bullying and want to help, what should you consider first?
Answers
Answer:
confront the bully
Explanation:
If you witness physical bullying and want to help, you should consider first whether the person perpetrating bullying is struggling with something.
What is physical bullying?Physical bullying is the use of physical actions to intimidate and gain direct control. Physical activity is unwanted by the victim and can cause damage to the body or property. Some common types of violence enacted through physical bullying are hitting, Kicking, Pinching the Damage of property.
Ask them to refuse engaging emotionally. Set boundaries, don't engage with the abusive behavior, set consequences, and stick to them. Walk away if a boundary you set is crossed, or if you feel unsafe, leave. the place for some period. Talk to victim privately by setting a time aside, expressing your concern.
Offer any assistance, an ear to listen when they need it. Getting someone else involved might result in victim, be more open, to recognize the abuse, since including more people to express concern or witnessing the abuse, adds more value to the concern.
Thus, If you witness physical bullying and want to help, you should consider first whether the person perpetrating bullying is struggling with something.
Learn more about physical bullying on:
brainly.com/question/17505353
#SPJ3
Mr. Simmons has assigned a research project. Every student in the class will create a single page report about the recycling habits of an assigned state. The individual reports will then be combined to form a single 50 page reference manual. What can Mr. Simmons require each student use so that all page layouts follows a consistent style
Answers
Answer: template
Explanation:
In order for each student to have a page layout that follows a consistent style, then the students should have a template.
A template refers to a predesigned document that can be used can to create documents without having to think about formatting. When a template is used, the margin size, spacing, font style, etc are predetermined.
Which is not considered a defining characteristic of big data?
Answers
Big data is a term used to describe datasets that are so large and complex that traditional data processing methods and tools are inadequate to handle them.
It is characterized by the 3Vs - volume, velocity, and variety - and often requires advanced technologies and techniques to store, process, and analyze the data.One defining characteristic of big data is that it requires specialized tools and technologies to process and analyze the data efficiently. Another is that big data can come from a wide variety of sources, including social media, sensors, devices, and other sources, making it heterogeneous in nature. Additionally, big data is often unstructured or semi-structured, and it may require significant preprocessing to transform it into a usable format.Therefore, all of the above characteristics are defining characteristics of big data. None of them are excluded or not considered defining characteristics of big data.
To learn more about data click the link below:
brainly.com/question/15204133
#SPJ4
30 points for this.
Any the most secret proxy server sites like “math.renaissance-go . Tk”?
Answers
No, there are no most secret proxy server sites like “math.renaissance-go . Tk”
What is proxy server sitesA proxy server functions as a mediator, linking a client device (such as a computer or smartphone) to the internet. Sites operating as proxy servers, otherwise referred to as proxy websites or services, allow users to gain access to the internet using a proxy server.
By utilizing a proxy server site, your online activities are directed through the intermediary server before ultimately reaching your intended destination on the web.
Learn more about proxy server sites from
https://brainly.com/question/30785039
#SPJ1
In the address http://www.company.com/clients.html, which of the following is the top-level domain?
A) .com
B) company.com
C) www
D) http
Answers
In the address http://www.company.com/clients.html, which of the following is the top-level domain is .com.
Which top level domain among the following is the most popular?Dot-coms swiftly took over as the top-level domain that people most frequently used as the internet's use and popularity continued to rise. net – Dot-nets, which stand for "network," were created for organizations that engage with network technologies, such as infrastructure providers or internet service providers (ISPs).
Which TLD is the ideal one?Commercial is the meaning of the dot com. People consider it reputable, trustworthy, and more memorable than other obscure domain extensions, making it one of the greatest TLD domains to utilize. According to a Growth Badger analysis, the.com TLD is the most reliable.
To know more about domain visit:-
https://brainly.com/question/14466182
#SPJ4
What statement best describes operating systems?
It’s possible for modern computers to function without operating systems.
Most operating systems are free or very inexpensive.
Operating systems are managed by the computer’s microprocessor (CPU).
Operating systems manage the computer’s random access memory (RAM).
Answers
The statement which best describes operating systems is: D. Operating systems manage the computer’s random access memory (RAM).
What is an operating system?An operating system (OS) can be defined as a system software that is pre-installed on a computing device to manage random access memory (RAM), software applications, computer hardware and user processes.
This ultimately implies that, an operating system (OS) acts as an interface (intermediary) between an end user and the hardware portion of the computer system (computer hardware) in the processing and execution of instructions, including the management of the random access memory (RAM).
Read more on software here: https://brainly.com/question/26324021
Answer:
Answer is D! :)
Explanation:
What is defined as the copying or extracting of existing listing information or keywords from a website, digital platform, or any form of social media of another licensee and using or altering that material and posting or displaying it for the benefit of the general public on another digital platform, form of social media, or in front of firewall on another website, without written or electronic permission and disclosure from the original listing licensee
Answers
The act of copying or extracting information or keywords from a website, digital platform, or social media of another licensee and using or altering it to post or display it for the public on another platform, social media or on a website that is behind a firewall is called content scraping.
The practice of content scraping is illegal and unethical. For this reason, it requires the written or electronic permission of the original listing licensee before posting or displaying on another digital platform, social media, or website.The copying of material or information without permission from the rightful owner is a violation of copyright laws. The original listing licensee could initiate legal action against anyone who violates copyright laws. Also, content scraping could lead to SEO (search engine optimization) problems for the website of the individual who engaged in such act.
Therefore, it is essential to obtain permission from the original licensee before displaying or posting content on another digital platform, social media, or website to avoid copyright infringement and potential legal action.Content scraping is also considered to be unethical and unprofessional. It is important to maintain honesty and integrity while performing business activities.
To know more about firewall visit:
https://brainly.com/question/31753709
#SPJ11
Which page layout is most commonly used for a website with a large navigation menu ?
Answers
Cartographer website navigation method consists of a single web page containing a list of hyperlinks representing all the pages in the website.
A cartographer is "a person who creates or produces maps," according to the Oxford Dictionary of English app. According to the online Merriam-Webster definition, a cartographer is "one who produces maps." Additionally, a cartographer is defined as "someone who makes or draws maps" in the online version of the Cambridge Dictionary.
The creation of maps, graphs, and other graphics, as well as the maintenance of their standardization for various project and technical reports.
Performs geographic analysis on the data after creating, recording, and/or digitally extracting geospatial or statistical data from a number of sources.
Learn more about cartographer on:
brainly.com/question/18151641
#SPJ1
Convert the folllowing binary number to decimal:00101
Answers
Answer:
5
Explanation:
Each digit in binary is worth double the amount compared to the number to the right of it. This means the rightmost number is 1, the second rightmost is 2, the third rightmost is 4, and so on.
If a digit has a 1 in the place, you add however much it is worth to the decimal count.
For example, this number has a 1 in the third rightmost. The third place here means a 4, so we add 4 to the count. It also has a 1 in the rightmost place, so we add 1 to the count.
Any digit with 0 is simply there to hold the place and can be ignored.
A bit confusing but hopefully you understand

What is the keyboard shortcut to show formulas in a worksheet (as opposed to the value)? OCTRL+S OCTRL + Z CTRL- There is no shortcut for showing formulas
Answers
CTRL + (tilde) is a keyboard shortcut to show formulas instead of values in Excel spreadsheets. It can be found in the upper-left corner of most keyboards, below the Escape key or just left of the 1 key.
The keyboard shortcut to show formulas in a worksheet (as opposed to the value) is `CTRL + ~` (tilde).When working with Excel spreadsheets, you might want to display the formulas instead of the values in your cells. This could be done by using the "Show Formulas" button. But, if you're doing this frequently, it's easier to use a keyboard shortcut. To do this, press `CTRL + ~` (tilde) and it will show all of the formulas in your spreadsheet instead of the values.
The tilde symbol, ~, can be found in the upper-left corner of most keyboards. It is usually located below the Escape key or just left of the 1 key. It's worth noting that pressing the `CTRL + ~` (tilde) keyboard shortcut again will switch back to displaying the values.
To know more about Excel spreadsheets Visit:
https://brainly.com/question/10541795
#SPJ11
What is an example of a composite key in a database table?
InvoiceID
CustomerID
ProductID
OrderID + ProductID
Answers
Answer:
b
Explanation:
OrderID + ProductID is an example of a composite key in a database table. The correct option is 4.
What is composite key?A composite key is a key in a database table that consists of two or more columns that uniquely identify each row.
In a database table, a composite key is the combination of OrderID and ProductID in a table that tracks sales transactions.
Because a single order can contain multiple products and multiple orders can contain the same product, neither column can uniquely identify a row by itself.
However, by combining the two columns, each row can be uniquely identified, ensuring that the data is accurate and complete.
Similarly, a combination of CustomerID and ProductID might be used in a sales system to track the products purchased by each customer.
Thus, the correct option is 4.
For more details regarding composite key, visit:
https://brainly.com/question/10167757
#SPJ3
Who wrote Hamlet?
Brainliest for the right answer
Answers
Answer:
William Shakespeare wrote hamlet
Explanation:
what is system analyst explain the role of system analyst
Answers
Answer:
A system analyst is a person that works to optimize user experience with programs.
Explanation:
A system analyst is somebody that analyzes how well a software or hardware system fits the business needs of their employer or of a client.
They basically look at how a software functions and determines what needs to be fixed in order to better their software for consumers.
in the source data worksheet sort the data alphabetically by customerid and then by product.
Answers
To sort the data alphabetically by the customer ID and then by-product in the source data worksheet, follow these steps:
1. Open the source data worksheet in your spreadsheet software.
2. Click on any cell within the data range you want to sort.
3. Navigate to your spreadsheet software's "Data" tab or menu.
4. Click the "Sort" button or option to open the Sort dialog box.
5. In the Sort dialog box, select "Customer ID" from the first drop-down list under "Sort by" or "Column."
6. Choose "A to Z" or "Ascending" to sort alphabetically.
7. Click on the "Add Level" or "Then by" button to add another sorting criterion.
8. Select "product" from the second drop-down list.
9. Choose "A to Z" or "Ascending" to sort alphabetically.
10. Click "OK" to apply the sorting.
Your data in the source data worksheet is sorted alphabetically by the customer ID and then by product.
Learn more about Worksheet here: brainly.com/question/13129393.
#SPJ11
write an algorithm using pseudocode to input three different numbers, multiply the two larger numbers together and output the result. Use the variables: Number 1, Number 2 and Number 3 for you numbers
Answers
Answer:
Pseudocode is a simply way to write algorithm to any code in English. It is not a coding language.
Explanation:
Here is a pseudocode method that takes three different numbers as input, multiplies the two bigger values, and outputs the result using the variables 1, 2, and 3:
Pseudocode algorithm:
Request that the user enter 1.Take note of and save the value of Number 1.Request entry of Number 2 from the user.Take note of and save the value of Number 2.Request that the user enter 3.Read the value of Number 3 and note it down.Compare the two on the list.Step 10 is to be taken if Number 1 is greater than Number 2. If not, move on to step 11.Contrast numbers 1 and 3.Multiplying Numbers 1 and 2 and storing the result will indicate whether Number 2 is greater than Number 3.To learn more about pseudocode,
brainly.com/question/27986919
Find out how to print the below pattern in python and also come up with pseudocode,
you have to use for loop for this, you can use a for loop inside the outer for loop.
You can't use operator like " *" in python , only use print statement to print the below pattern. Find out how to print in 5 lines one by one in python , there is a way to print one line then next
X
XXX
XXXXX
XXXXXXX
XXXXXXXXX
Answers
Answer:
for i in range(5):
for j in range(2*i + 1):
print("*", end="")
print()
Explanation:
for row index going from 0 to 5
for column index going from 0 to 2*row index + 1
print * suppressing new line
print a new line to move to next row
What is output by the following code?
C = 1
sum = 0
while (c< 10):
C=C+2
sum = sum + c
print (sum)
Answers
The output of the code is 17. The output is simply what happens once all of the code is completed, the end result. It is what is entered into the console after all of the calculations have been completed.
What is Python ?Python is a general-purpose, high-level programming language. Its design philosophy prioritises code readability by employing significant indentation. Python is garbage-collected and dynamically typed. It is compatible with a variety of programming paradigms, including structured, object-oriented, and functional programming.
It is compatible with a variety of programming paradigms, including structured, object-oriented, and functional programming. Because of its extensive standard library, it is frequently referred to as a "batteries included" language.
Guido van Rossum began developing Python as a successor to the ABC programming language in the late 1980s, and it was first released in 1991 as Python 0.9.0.
To find out output let first write the question:
C=1
sum = 0
while(C<10):
C=C+3
sum=sum + C
print(sum)
Now Focus on
while(C<10):
C=C+2
sum=sum + C
The value of C is initially 1
C=1+2
Sum= 0+3
In second loop the value of C will become 3
c=3+3
sum=3+6
In third loop the value of C will be 6
c=6+2
sum=9+8
so the answer is 9+8 = 17
To learn more about Python refer :
https://brainly.com/question/26497128
#SPJ1
Across revisions of the Diagnostic and Statistical Manual, _____ has been removed entirely, while _____ has been renamed.
Answers
that homosexuality has been removed entirely from the Diagnostic and Statistical Manual (DSM), while gender identity disorder has been renamed to gender dysphoria.
this is that homosexuality was once considered a mental disorder, but it was removed in 1973 due to increasing pressure from the LGBTQ+ community and scientific evidence showing that it is not a mental illness. In contrast, gender identity disorder was renamed to gender dysphoria in the DSM-5 in 2013 to reflect a shift in understanding of the condition as a distress related to incongruence between one's gender identity and sex assigned at birth, rather than a disorder in and of itself. In conclusion, the DSM has undergone revisions that reflect changing societal attitudes and scientific understanding of mental health conditions.
In the revisions of the Diagnostic and Statistical Manual of Mental Disorders (DSM), homosexuality was removed entirely as a mental disorder in 1973, during the publication of the DSM-III. On the other hand, Gender Identity Disorder, which was included in previous versions, was renamed to Gender Dysphoria in the DSM-5, published in 2013, to better reflect the condition and reduce stigma.
Across the DSM revisions, homosexuality has been removed, while Gender Identity Disorder has been renamed to Gender Dysphoria.
For more information on homosexuality kindly visit to
https://brainly.com/question/28145496
#SPJ11
What is the something in the computer can be in the form of a tables, reports and graphs etc.
Answers
the very bottom window in wireshark shows the actual data was submitted when the ping was executed. what do you observe about the content and numeric format of the data shown in this bottom window when you click on the destination, source and type lines in the middle window?
Answers
Within Wireshark, the collected data is decoded and presented in individual packet form for study. The most popular packet sniffer worldwide is called Wireshark.
What is the purpose of Wireshark?A network protocol analyzer, such as Wireshark, is a program that records packets from a network connection, such as one connecting your computer to your home office or the internet. In a typical Ethernet network, a discrete unit of data is referred to as a packet. The most popular packet sniffer worldwide is called Wireshark.There are literally hundreds of developers who contribute code to Wireshark, and their programming backgrounds range from expert networking professionals to complete novices, increasing the likelihood that new problems may enter the system. As a result, compared to most other programs, Wireshark is more susceptible to attacks.To learn more about Wireshark refer to:
https://brainly.com/question/13261433
#SPJ4
30 pts!
Explain how Moore's law presumes everyone will have access to the Internet.
Answers
Answer:
Moore's law predicts that this trend will continue into the foreseeable future.
Explanation:
Moore's Law refers to Moore's perception that the number of transistors on a microchip doubles every two years, though the cost of computers is halved.