Assuming int* new Dimensions; is already declared, which declaration will dynamically allocate an array of 5 integers? a. newDimensions[5] = (int*)malloc(sizeof(int)); b. newDimensions = (int*)malloc(5 * sizeof(int)); c. *newDimensions = (int*)malloc(5 * sizeof(int));
d. *newDimensions = (int * 5)malloc(sizeof(int));
Answers
The correct declaration that will dynamically allocate an array of 5 integers is option b. newDimensions = (int*)malloc(5 * sizeof(int)).
Memory for an array of 5 integers by multiplying the size of one integer by 5 and then allocating that amount of memory using malloc. Option a is incorrect because it only allocates memory for one integer and assigns it to the first element of the array. Option c is incorrect because it assigns the result of malloc directly to the pointer, which is not the correct way to allocate memory for an array. Option d is also incorrect because it uses invalid syntax for allocating memory.
newDimensions = (int*)malloc(5 * sizeof(int)); This declaration uses the malloc function to allocate memory for 5 integers, each with a size equal to sizeof(int), and assigns the resulting pointer to the previously declared int* newDimensions.
To know more about Array visit:
https://brainly.com/question/31605219
#SPJ11
Related Questions
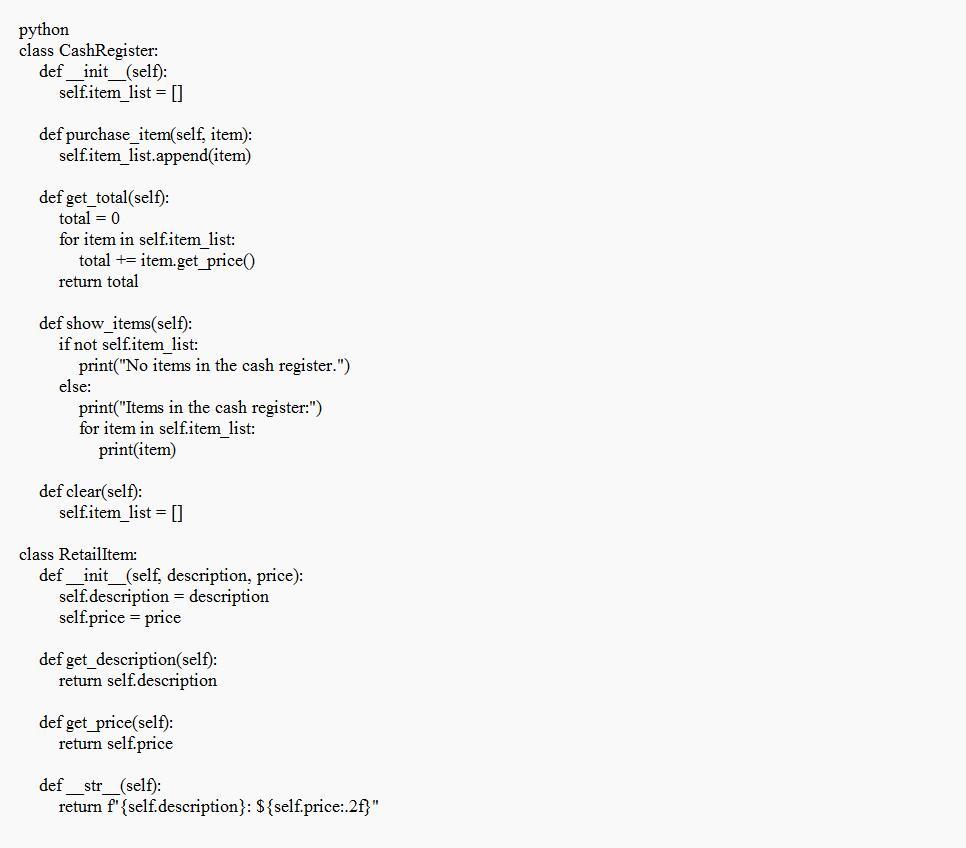
100 POINTS!!!! Write in python
10.8

Answers
A good example of the implementation of the Cash Register class that is known to have all the methods given in the question is attached below.
What is the Cash Register class?Based on the given program, It initiates three RetailItem instances that signify distinctive products that are available for procurement. The CashRegister object is updated with additional items through the purchase_item function.
The CashRegister's stored items can be viewed through the show_items method, while the get_total method computes and gives back the overall cost. Eventually, the internal list of items within the CashRegister is cleared utilizing the transparent approach.
Learn more about Cash Register class from
https://brainly.com/question/31655783
#SPJ1
See text below
8.
This exercise assumes you have created the RetailItem class for Programming Exer- cise 5. Create a Cash Register class that can be used with the RetailItem class. The Cash Register class should be able to internally keep a list of RetailItem objects. The class should have the following methods:
. A method named purchase_item that accepts a RetailItem object as an argument. Each time the purchase_item method is called, the RetailItem object that is passed as an argument should be added to the list.
. A method named get_total that returns the total price of all the RetailItem objects stored in the Cash Register object's internal list.
⚫ A method named show_items that displays data about the RetailItem objects stored in the Cash Register object's internal list.
⚫ A method named clear that should clear the CashRegister object's internal list.
Demonstrate the Cash Register class in a program that allows the user to select several items for purchase. When the user is ready to check out, the program should display a list of all the items he or she has selected for purchase, as well as the total price.

What makes these Pokémon special?
-Charizard
-Blastoise
-Charmander
-Ivysaur
-Missingno
First one to get it right gets Brainliest! If you get it right in the comments, I'll thank you on your profile!
Answers
Answer:
Charizard is a fire type dragon that is orange Blastoise is a big turtle that's water type Charmander is a fire type dinosaur the first evolution of Charizard Ivysaur is a grass type Turtle looking thing and the last one is a glitch
Answer:
i believe they are all based off of real amphibians and reptiles.
Explanation:
i really need brainliest if i got it wrong give me another try. i named my chameleon charmander so i really do love pokemon this is just such a specific question.
Q1. Which implementation of Network Access Control checks users' credentials to determine what level of access they should have to a top-secret file?
A. ACE
B. DAC
C. MAC
D. RBAC
Q2. Which physical access control uses a portable device that authenticates a person's identity electronically by storing some sort of personal information?
A. Infrared scanners
B. Hardware security tokens
C. Biometric devices
D. Keypads
Q3. Which implementation of Network Access Control grants access depending on a specific job role?
A. DAC
B. RBAC
C. MAC
D. PAC
Q4. Which implementation of Network Access Control is more relaxed, allowing users to determine file access privileges?
A. AAC
B. MAC
C. DAC
D. RBAC
Q5. Which type of access control sets the standard for the way security actions unfold?
A. Identity
B. Management
C. Physical
D. Technical
Answers
Answer:
1. MAC
2. Biometric Devices
3. RBAC
4. DAC
5. Management
Explanation:
Q.1) Option c) MAC
Q.2) Option c) Biometric devices
Q.3) Option b) RBAC
Q.4) Option c) DAC
Q.5) Option b) Management
What is MAC ?
The ability of individual resource owners to allow or refuse access to resource objects in a file system is constrained by the security measure known as mandatory access control (MAC).
What is a biometric device ?
An authentication and security identification tool is a biometric gadget.
What is RBAC ?
Role-based access control, often known as role-based security, is a method for only allowing authorized users to access a system.
What is DAC ?
The idea behind discretionary access control is to limit access to things based on who the subject is.
Therefore, MAC, biometric device, RBAC, DAC and Management access control sets are some of the measures for network security and access control.
You can learn more about network security from the given link
https://brainly.in/question/33317398
#SPJ2
In Outlook 2016, what happens when users begin to type in the To field the name of an email recipient to whom they frequently send messages? The recipient’s full email address appears in the field. The recipient’s full contact information appears in a window. The address book appears and presents names to choose from. The address book appears and presents addresses to choose from.
Answers
Answer:
The recipent's full email address appears in the field.
Explanation:
Answer:
The recipent's full email address appears in the field.
Explanation:
EDGE 2023
use semaphore to enforce mutual exclusion. t1 first uses and release resource a, and then uses and releases resource b. 1.1. define semaphores and their initial values. (2 points)
Answers
To enforce mutual exclusion for a scenario where t1 first uses and releases resource a and then uses and releases resource b, semaphores can be defined as follows:
- Semaphore a = 1 (initial value)
- Semaphore b = 1 (initial value)
In computer science, semaphores are a synchronization tool used to enforce mutual exclusion and coordinate access to shared resources in a concurrent system. A semaphore is essentially a variable that can be accessed by multiple threads or processes, and that can be used to control access to shared resources.
In the given scenario, t1 first uses and releases resource a, and then uses and releases resource b. To ensure that only one thread at a time can access each resource, semaphores can be defined as follows:
- Semaphore a = 1 (initial value): This semaphore will be used to control access to resource a. The initial value of 1 indicates that the resource is available and can be accessed by a single thread.
- Semaphore b = 1 (initial value): This semaphore will be used to control access to resource b. The initial value of 1 indicates that the resource is available and can be accessed by a single thread.
When t1 wants to access resource a, it will first wait on semaphore a to ensure that it is available. Once it has acquired semaphore a, t1 can safely access resource a. After it is done with resource a, t1 will release semaphore a to indicate that the resource is available again.
Similarly, when t1 wants to access resource b, it will first wait on semaphore b to ensure that it is available. Once it has acquired semaphore b, t1 can safely access resource b. After it is done with resource b, t1 will release semaphore b to indicate that the resource is available again. By using semaphores in this way, mutual exclusion is enforced, and only one thread at a time can access each resource.
To learn more about semaphores click here: brainly.com/question/13162814
#SPJ11
The way a student prepares for a test or reviews academic material is referred to as
a study environment.
study habits.
study hall.
a study schedule.The way a student prepares for a test or reviews academic material is referred to as
Answers
Answer:
study habits
Explanation:
Answer:
The Answer is Study Habits
Explanation:
Just got it right on edge
What us the category of logistics functional metrics that would be focused on individual activities within functtional areas and could be measured by customer returns and shipping accuracy?
Answers
The category of logistics functional metrics that would be focused on individual activities within functional areas and could be measured by customer returns and shipping accuracy is "Operational Efficiency Metrics."
Operational efficiency metrics in logistics focus on assessing the effectiveness and accuracy of specific activities within functional areas such as transportation, warehousing, and order fulfillment. Customer returns and shipping accuracy are two specific metrics that fall under this category. Customer returns measure the rate at which customers return products due to various reasons, while shipping accuracy evaluates the accuracy and correctness of order fulfillment and delivery processes. These metrics help organizations identify areas for improvement, optimize operational processes, and ensure customer satisfaction by monitoring the efficiency and effectiveness of individual logistics activities.
To know more about customer click the link below:
brainly.com/question/29215877
#SPJ11
Space Systems are shared and interconnected systems of computers, communications, people, and other support structures that
Answers
Answer:
Include command and control, tactical, intelligence, and commercial communications systems used to transmit DOD data
Explanation:
Space systems are a network of tools and people meant for the proper functioning of the a space sector of the security system and includes several dedicated and shared technologies and resources that are mainly outlined for efficient and economical usage.
Space systems facilitate systems public and private systems that require space to land based technologies.
Research the vulnerabilities called Heartbleed and Shellshock. Discuss how they affect a computer system.
Answers
Heartbleed and Shellshock are two separate vulnerabilities that affected computer systems in the past.
What are vulnerabilities?A hole or a weakness in the application is known as a vulnerability, which can be either a design flaw or an implementation error.
The widely-used OpenSSL cryptographic software library had a flaw called Heartbleed.
On the other side, Shellshock is a flaw in the Unix Bash shell, a command-line interface that is utilized by many Unix-based operating systems.
Both Heartbleed and Shellshock could have detrimental effects on the computer systems that were impacted.
Heartbleed was a vulnerability that gave attackers access to sensitive data from vulnerable systems, which they may have used to launch additional assaults or jeopardize the user's privacy.
Thus, it is crucial that computer systems are updated often with the most recent security patches in order to guard against these and other vulnerabilities.
For more details regarding vulnerabilities, visit:
https://brainly.com/question/30296040
#SPJ9
It's usually easier to change the design of a photo album slide show A.after you've created the presentation. B.before you've created the presentation. C.before you've planned out the presentation. D.after you've planned out the presentation but before creating it.
Answers
Answer:
A. after you've created the presentation.
Explanation:
A power point presentation is defined as a presentation program where one can create any presentation or design any layout like the photo album slide show to present it to others.
Once the album is created in the PowerPoint, it can be changed by going to the slide show and editing the content of the photo album of the slide show. Thus it is easier to make any changes in the design of the photo album slide show after the presentation have been created.
Conceptual note-taking is the act of writing down information in the order it is given. drawing attention to details with a marker or pen. adding main ideas and details to a graphic organizer. creating lists to organize homework and study time.
Answers
Answer:A
Explanation:Conceptual notetaking is the act of writing down information in the order it is given.
Conceptual note-taking is class of note-taking characterized with writing down in order, drawing of attention to details with a pen and adding of main ideas.
Conceptual note-taking is most useful when we need to show how the main ideas and details relate to each other.
Therefore, in short, the Conceptual note-taking basically focus on the concepts of the lecture, classwork etc
Learn more about this here
brainly.com/question/7321210
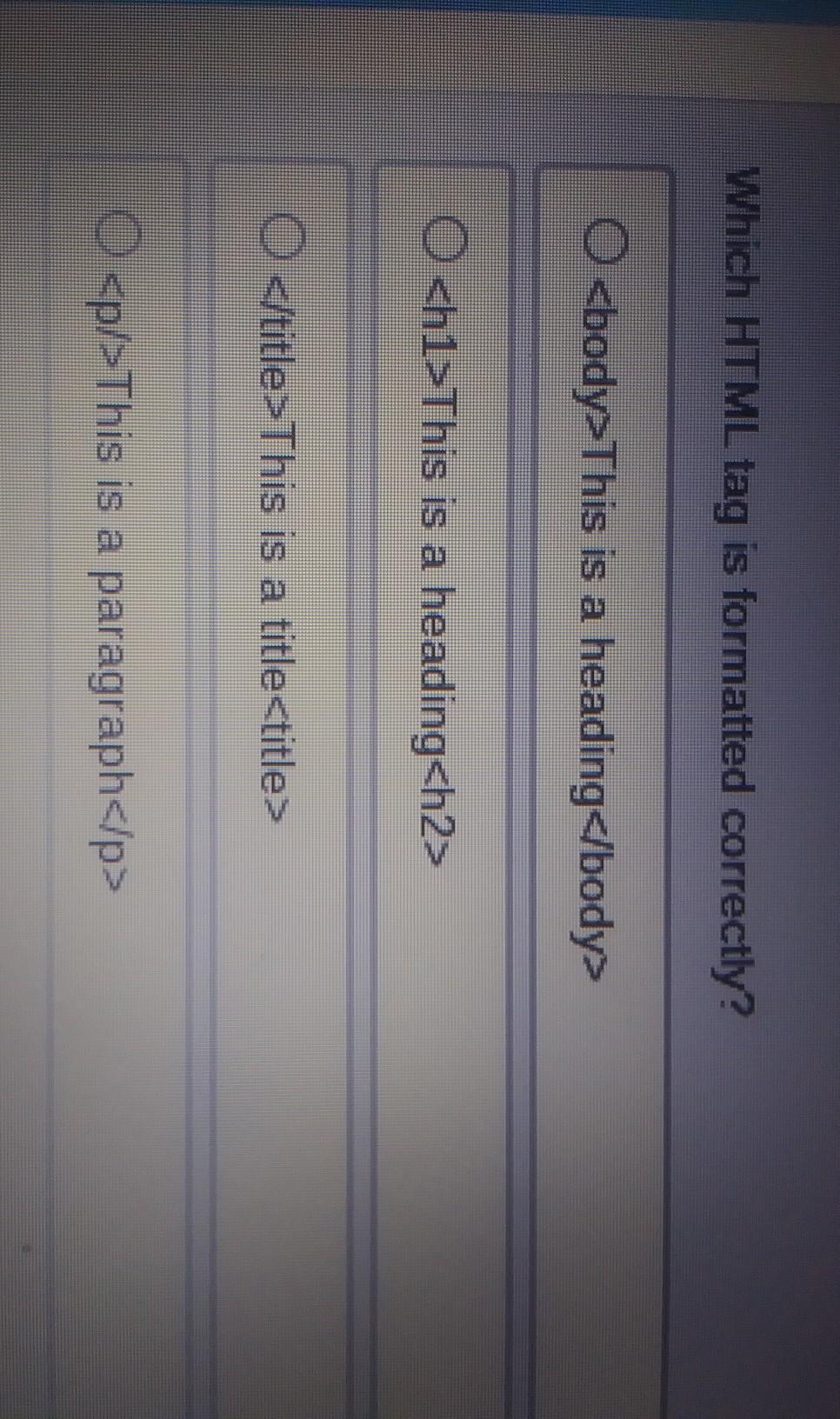
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
Baby Max begins to cry as soon as he sees his mother pick up her car keys. Max probably does this because he learned to associate the car keys with his mother leaving. This example demonstrates 1. modeling. 2. operant conditioning. 3. observational learning. 4. classical conditioning.
Answers
Baby Max's behavior is an example of classical conditioning, which is a type of learning where an organism learns to associate two stimuli and responds.
In this case, Max associates the car keys with his mother leaving, and so he starts crying as soon as he sees them. Classical conditioning was first discovered by Ivan Pavlov, who noticed that his dogs started to salivate at the sound of a bell because they had learned to associate it with food. Similarly, Max has learned to associate the car keys with his mother leaving, and so he starts to cry as soon as he sees them. This type of learning is often automatic and involuntary, and it can be seen in a wide range of species, from humans to dogs to rats.
It's worth noting that classical conditioning is just one type of learning, and there are other types, such as operant conditioning and observational learning. Operant conditioning is when an organism learns to associate its behavior with its consequences, while observational learning is when an organism learns by watching others. In Max's case, however, classical conditioning is the most likely explanation for his behavior.
In conclusion, Max's behavior is an example of classical conditioning, which is a type of learning where an organism learns to associate two stimuli and responds to one of them in the same way it responds to the other. Max has learned to associate the car keys with his mother leaving, and so he starts crying as soon as he sees them.
Learn more about behavior :
https://brainly.com/question/8871012
#SPJ11
What does Spam mean in tech
Answers
Answer:
Spam is digital junk mail. They are unsolicited communications sent in bulk over the internet or through any electronic messaging system. For example, when you text someone "hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi" they will tell you "stop spamming!"
Answer:
Spam means Digit Junk Mail in tech context.
Explanation:
Spam is digital junk mail: unsolicited communications sent in bulk over the internet or through any electronic messaging system. It is unsolicited bulk messages, spamming is the act of sending these messages, and a person who engages the practice is a spammer. Most of the time, spamming is commercial in nature, and though the spam is bothersome, it isn’t necessarily malicious or fraudulent (though it can be).
What is a product line
Answers
Answer:
A group of products that are similar in many ways, but usually spec'd out uniquely to target different applications or customers.
I request that it is done in C++. Giving 100 points. To find the number of 100 dollar bills, 20 dollar bills, 10 dollar bills, 5 dollar bills, 1 dollar bills, quarters, dimes, nickels, and pennies that will make up an amount entered by the user.
Sample Output:
Enter Amount: 489.98
The number of 100 dollar bills: 4
The number of 20 dollar bills: 4
The number of 10 dollar bills: 0
The number of 5 dollar bills: 1
The number of 1 dollar bills: 4
The number of Quarters: 3
The number of Dimes: 2
The number of Nickels: 0
The number of Pennies: 3
I have this so far.(look at attachment)
Answers
A program that finds the number of 100 dollar bills, 20 dollar bills, 10 dollar bills, 5 dollar bills, 1 dollar bills, quarters, dimes, nickels, and pennies that will make up an amount entered by the user.
The Program#include<iostream>
using namespace std;
int main () {
double bill=0.0, twenty=0.0, ten=0.0, five=0.0, one=0.0, quarter=0.0, dime=0.0, nickel=0.0, penny=0.0, payment=0.0, cashBack=0.0;
// We need to gather a value for the bill.
while (bill==0) {
cout << "Please enter the amount of the bill (ex. $15.67): \n";
cin >> bill;
cout << "Your bill is "<< bill << ".\n";
}
do {
cout << "Please pay for bill by entering \nthe count of each dollar bill denomination and coin denomination.\n";
// Gathers an amount for each denomination and then gives it a value equal to its monetary value.
cout << "\nTwenty dollar bills:"; cin >> twenty;
twenty *= 20.00;
cout << "\nTen dollar bills:"; cin >> ten;
ten *= 10.00;
cout << "\nFive dollar bills:"; cin >> five;
five *= 5.00;
cout << "\nOne dollar bills:"; cin >> one;
one *= 1.00;
cout << "\nQuarters:"; cin >> quarter;
quarter *= .25;
cout << "\nDimes:"; cin << dime;
dime *= .10;
cout << "\nNickels:"; cin >> nickel;
nickel *= .05;
cout << "\nPennies:"; cin >> penny;
penny *= .01;
// Add the money together and assign the value to payment.
payment = twenty + ten + five + one + quarter + dime + nickel + penny;
cout << "\nYour payment totals: $" << payment << "\n";
if (payment < bill) {
cout << "\nYou didn't pay enough money to cover the bill. \nPlease re-enter your amount.\n";
// If payment isn't greater than bill then they're asked to reenter their money.
}
// Determine the amount of cash to give back and assign the value to cashBack.
cashBack = payment - bill;
} while (cashBack <= 0);
cout << "\nI owe you $" << cashBack <<"\n";
// Reset the values of each denomination to 0
twenty = 0;
ten = 0;
five = 0;
one = 0;
quarter = 0;
dime = 0;
nickel = 0;
penny = 0;
// These while loops will subtract the monetary value from cashBack and add a value of 1 each time it is looped.
while (cashBack >= 20) {
cashBack -= 20;
twenty += 1;
}
while (cashBack >= 10) {
cashBack -= 10;
ten += 1;
}
while (cashBack >= 5) {
cashBack -= 5;
five += 1;
}
while (cashBack >= 1) {
cashBack -= 1;
one += 1;
}
while (cashBack >= .25) {
cashBack -= .25;
quarter += 1;
}
while (cashBack >= .10) {
cashBack -= .10;
dime += 1;
}
while (cashBack >= .05) {
cashBack -= .05;
dime += 1;
}
while (cashBack >= .01) {
cashBack -= .01;
penny += 1;
}
// For each denomination that has a value greater than 0, the person is payed back the amount.
if (twenty > 0) {
cout << "\n" << twenty << " Twenty dollar bills.\n";
}
if (ten > 0) {
cout << "\n" << ten << " Ten dollar bills.\n";
}
if (five > 0) {
cout << "\n" << five << " Five dollar bills.\n";
}
if (one > 0) {
cout << "\n" << one << " One dollar bills.\n";
}
if (quarter > 0) {
cout << "\n" << quarter << " Quarters.\n";
}
if (dime > 0) {
cout << "\n" << dime << " Dimes.\n";
}
if (nickel > 0) {
cout << "\n" << nickel << " Nickels.\n";
}
if (penny > 0) {
cout << "\n" << penny << " Pennies.\n";
}
}
Read more about C++ programming here:
https://brainly.com/question/20339175
#SPJ1
PLEASE HELP GIVING 25 POINTS Sophia is leading a project to help clean up a local river in her area. She creates an online forum where participants can communicate with each other and read the goals of the project. She encourages people to post ideas on this forum and sets up weekly web-conferencing meetings to move the project along. Which qualities show that Sofia is an effective digital leader? Check all that apply. She holds useful online meetings. She encourages collaboration. She pursues her own ideas. She is comfortable with technology. She waits for others to take the lead. She takes action to complete the job.
Answers
Answer:
Sophia holds useful online meetings ...
Explanation:
Give brainly, sister.
Answer:
1 2 4 6
Explanation:
edge 2021
Two adjacent vertices can be part of the same MIS. True or False
Answers
The statement "Two adjacent vertices can be part of the same MIS" is false. A maximum independent set (MIS) is defined as a set of vertices in a graph such that no two vertices in the set are adjacent. In other words, each vertex in the MIS has no direct connections to any other vertex in the set. This is why it is called an independent set.
If two adjacent vertices were to be part of the same MIS, it would contradict the definition of an MIS because adjacent vertices have an edge connecting them. Therefore, if one vertex is in the MIS, its adjacent vertex cannot be included in the same MIS.
To illustrate this concept, let's consider a simple example of a graph with four vertices, A, B, C, and D. If A and B are adjacent vertices and part of the same MIS, then C and D cannot be in the MIS because they are adjacent to A and B. Therefore, an MIS in this graph could be either {A, C} or {B, D}.
In conclusion, two adjacent vertices cannot be part of the same MIS as an MIS is defined as a set of vertices with no direct connections to each other.
To learn more about, adjacent
https://brainly.com/question/31458050
#SPJ11
MIS:
False. Two adjacent vertices can be part of the same MIS.
ten(10) examples of wearables or wearable technologies?
Answers
Answer:read
Explanation:
airpods
headphones
earbuds
AirPods pro
watch
fitbit (type of watch that counts your miles) &you can say workout watch&
VR set
technology bracelet
smart glasses
Smart ring
__________, a level beyond vulnerability testing, is a set of security tests and evaluations that simulate attacks by a malicious external source (hacker).
Answers
According to security evaluation, Penetration testing is a level beyond vulnerability testing, a set of security tests and evaluations that simulate attacks by a malicious external source (hacker).
Penetration testing is often considered or described as ethical hacking. It involves the process of securing a firm or organization's cyber defenses.
The process of penetration testing or security testing includes assessing for exploitable vulnerabilities in networks, web apps, and user security.
Hence, in this case, it is concluded that the correct answer is Penetration testing.
Learn more about penetration testing here: https://brainly.com/question/13137421
which digits are used in digital computer?
Answers
Answer:
binary digits i.e. 0s and 1s
when considering the agile project management process, at the end of each iteration
Answers
When considering the agile project management process, at the end of each iteration "stakeholders and customers review progress and reevaluate priorities" (option D)
Who are the stakeholders in an agile project management process?Agile management is the application of Agile software development and Lean management ideas to different management activities, most notably product development.
Agile methodologies began to extend into other areas of activity with the publication of the Manifesto for Agile Software Development in 2001.
The project team, product owner, scrum master, and key organizational representatives are common stakeholders in an agile project management approach.
Learn more about agile project management at:
https://brainly.com/question/14318704
#SPJ1
Full Question:
When considering the agile project management process, at the end of each iteration
team members are released to work on other projects
product owner determines whether or not the project is complete
the Scrum master can terminate the project
stakeholders and customers review progress and reevaluate priorities
the Scrum master assigns daily tasks to team members
Define a function InspectVals() with no parameters that reads integers from input until integer -1 is read. The function returns true if all of the integers read before -1 are in the range 9000 to 10000 inclusive, otherwise, returns false.Ex: If the input is 9500 10030 -1, then the output is:
Answers
To define the function InspectVals() with no parameters, you can follow these steps:
1. Start by creating the function InspectVals() without any parameters.
2. Inside the function, initialize a variable called validRange to True. This variable will keep track of whether all the integers read before -1 are within the range of 9000 to 10000 (inclusive).
3. Use a while loop to continuously read integers from the input until -1 is encountered.
4. For each integer read, check if it falls within the range of 9000 to 10000 (inclusive).
- If the integer is within the range, continue to the next iteration of the loop.
- If the integer is outside the range, set validRange to False and break out of the loop.
5. After the loop finishes, return the value of validRange.
6. The function InspectVals() should now return True if all the integers read before -1 are within the range of 9000 to 10000 (inclusive), and `False` otherwise.
Here's an example implementation of the function `InspectVals()` in Python:
python
def InspectVals():
validRange = True
while True:
num = int(input())
if num == -1:
break
if num < 9000 or num > 10000:
validRange = False
break
return validRange
This function prompts the user to input integers until -1 is entered. It checks each integer to see if it falls within the range of 9000 to 10000 (inclusive). If any integer is outside this range, the function returns False. Otherwise, if all the integers are within the range, the function returns True.
For example, if the input is 9500 10030 -1, the function will return True since both 9500 and 10030 are within the specified range.
learn more about function:
https://brainly.com/question/29631554
#SPJ11
Amazon describes their web services platform like this: Amazon Web Services (AWS) is a highly reliable, scalable, low-cost infrastructure platform in the cloud that powers hundreds of thousands of enterprise, start-up and public sector business with organizations in over 190 countries around the world. What does it mean for the platform to be scalable? Choose 1 answer: Choose 1 answer: (Choice A) A It is distributed across multiple data centers. (Choice B) B It can process requests for users located anywhere in the world. (Choice C) C It is relatively inexpensive for high amounts of usage. (Choice D) D It continues operating when experiencing traffic surges.
Answers
Answer:
A scalable platform enables organizations to solve large-scale business problems through the high-performance processing of massive data volumes
Explanation:
How is life complicated without electronics
Answers
Answer:
life is complicated without electronics
Explanation:
because we wont know the weather or if anything know anything about and we would mostly not know anything
Ashley wrote this paragraph:
Gabe is a hardworking art student. He painted his family history on the fence in front of his home. First, he painted his great-grandfather, who had invented a new kind of long-lasting glue. Then, Gabe added his grandfather, dad, mother, and sisters to the mural. The purple and pink flowers that his mother liked are in the background.
Which would be the best concluding sentence?
A. However, Gabe also earns money loading groceries at the supermarket.
B. Finally, Gabe painted the tree that his dad had planted when they moved into the house.
C. In addition, Gabe does well in school.
D. On the other hand, Gabe forgot to include a painting of his favorite dog.
Answers
Answer:
B
Explanation:
The best concluding sentence is finally, Gabe painted the tree that his dad had planted when they moved into the house.
What does concluding sentences do?The role of concluding sentences do is known to entails the act of summarizing the given clues or points and also ending of any passage.
Note that The best concluding sentence is finally, Gabe painted the tree that his dad had planted when they moved into the house as it is one that can give the best summary of what the passage is about.
Learn more about concluding sentence from
https://brainly.com/question/5427622
#SPJ2
what type of movement does the output produce
Answers
These effects include filters, delay, distortion, reverb, compressor, and more.
Solve using the standard algorithm 758 x 92
Answers
The answer to the following problem using Standard Algorithm is 69,739. See the explanation below and the attached image.
How do you perform a standard Algorithm?A standard Algorithm means that you do the multiplication by hand. Traditional methods or standard algorithms involve multiplying numbers and ordering the result by bit value. Here are the steps to do long multiplication manually:
Arrange the numbers on top of each other and put the values in the columns. The number with the most digits is usually placed at the top as the multiplier.Start from one digit in the bottom digit, multiply by the last digit in the top digitWrite your answer under the equal signIf the answer is greater than nine, enter the number one as the answer and indicate the level numberContinue from right to left. Multiply one digit in the bottom digit by the next digit to the left of the top digit. If you carry a number with you, add it to the result and write the answer under the equal sign. If you must wear it again, please do. As you multiply ones by each digit of the top digit, move to the digit at the level of the bottom digit.Multiply as above, but this time write the answer on a new line and move one digit to the left. After multiplying, draw another answer line below the answer numbers in the last row.Add your column of numbers from right to left using long addition and carry as you would normally do long addition.Learn more about Standard Algorithm:
https://brainly.com/question/28626488
#SPJ1

What is ur Favorite Musical Artist
Answers
Answer:
dani
Explanation:
to store three different strings using three variables and print the string aftet concatenation
Answers
Answer:
Explanation:
Certainly! Here's an example of how you can store three different strings using three variables and then concatenate them to print the resulting string:
```csharp
using System;
class Program
{
static void Main(string[] args)
{
string string1 = "Hello";
string string2 = "there";
string string3 = "world";
string result = string1 + " " + string2 + " " + string3;
Console.WriteLine(result);
}
}
```
In this example, we declare three string variables `string1`, `string2`, and `string3` to store the three different strings. Then, we use the concatenation operator `+` to combine the strings together with spaces in between. The resulting string is stored in the `result` variable. Finally, we use `Console.WriteLine()` to print the concatenated string to the console, which would display "Hello there world".