Assuming the processor uses big-endian convention, what is the value of the following memory locations (place X in the blank if there is not enough information):Address 8-bit Data0x2000103A ____________0x20001039 ____________0x20001038 ____________0x20001037 ____________0x20001036 ____________0x20001035 ____________0x20001034 ____________0x20001033 ____________0x20001032 ____________0x20001031 ____________0x20001030 ____________0x2000102F ____________0x2000102E ____________0x2000102D ____________0x2000102C ____________0x2000102B ____________0x2000102A ____________0x20001029 ____________0x20001028 ____________0x20001027 ____________0x20001026 ____________0x20001025 ____________0x20001024 ____________
Answers
The byte ordering convention for each memory location is determined by the use of big-endian convention, where the most significant byte is stored at the lowest memory address. Without knowledge of the values stored at each location, the exact values of the memory locations cannot be determined.
How to determine memory byte ordering?To determine the values of the memory locations, we need to know the values stored at each location and the byte ordering convention being used. Since the processor is using big-endian convention, the most significant byte is stored at the lowest memory address.
Without information about the values stored at each location, we cannot determine the exact values of the memory locations. However, we can determine the order of the bytes at each location based on the big-endian convention.
Assuming each memory location stores a 32-bit (4-byte) value:
The value at address 0x2000103A is stored in the byte at address 0x2000103A, followed by the byte at address 0x20001039, then the byte at address 0x20001038, and finally the byte at address 0x20001037.
The value at address 0x20001036 is stored in the byte at address 0x20001036, followed by the byte at address 0x20001035, then the byte at address 0x20001034, and finally the byte at address 0x20001033.
The value at address 0x20001032 is stored in the byte at address 0x20001032, followed by the byte at address 0x20001031, then the byte at address 0x20001030, and finally the byte at address 0x2000102F.
The value at address 0x2000102E is stored in the byte at address 0x2000102E, followed by the byte at address 0x2000102D, then the byte at address 0x2000102C, and finally the byte at address 0x2000102B.
The value at address 0x20001028 is stored in the byte at address 0x20001028, followed by the byte at address 0x20001027, then the byte at address 0x20001026, and finally the byte at address 0x20001025.
Learn more about: Memory
brainly.com/question/14829385
#SPJ11
Related Questions
30 POINTS FOR THE CORRECT ANSWER
For this discussion, choose two different binding techniques, two different papers, and two different finishing techniques for a 24-page brochure. Describe the pros and cons of your choices and how it may impact your design and the setup of the document.
Answers
The chosen type of binding techniques are:
Saddle stitch binding. Hardcover or case binding.The papers type are:
Uncoated paper coated cover stockThe finishing techniques are:
Lamination Spot UV varnish.What are the pros and cons of my choices?Case binding is best because it is used in a lot of books were all the inside pages are known to be sewn together.
The Cons of case Binding is that it does not give room for one to lay books flat.
Saddle stitching is good because it can be used in small books that has fewer pages. Its limitations is that it only takes about 100 pages.
Learn more about binding techniques from
https://brainly.com/question/26052822
#SPJ1
Make a algorithm for a seat reservation for a specific seat in an auditorium using semaphore variables.
Answers
To create an algorithm for seat reservation in an auditorium using semaphore variables, we need to consider multiple steps. Here is a step-by-step explanation:
Start by initializing a semaphore variable with a value equal to the total number of available seats in the auditorium. This semaphore will keep track of the number of remaining seats. Before attempting to reserve a seat, check if there are any available seats. If the semaphore value is greater than zero, there are available seats.
Display the reserved seat: Once a seat is successfully reserved, display the seat number to the user. This will confirm their reservation. Release the semaphore: When the user finishes using the reserved seat, release it by incrementing the semaphore value by one. This will allow other users to reserve the seat.
To know more about algorithm visit:
https://brainly.com/question/33268466
#SPJ11
By using semaphore variables, this algorithm ensures that multiple individuals cannot reserve the same seat simultaneously. It guarantees mutual exclusion and avoids race conditions.
To create an algorithm for seat reservation in an auditorium using semaphore variables, you can follow these steps:
1. Define the semaphore variable: Initialize a semaphore variable called "seats" with the total number of available seats in the auditorium.
2. Initialize the semaphore: Set the initial value of the semaphore variable to the total number of available seats.
3. Create a reservation process: Each individual who wants to reserve a seat must go through this process.
4. Enter the reservation process: Before entering the reservation process, the individual must acquire the semaphore by performing a "wait" operation. If the semaphore value is greater than zero, the individual can proceed. Otherwise, they must wait until a seat becomes available.
5. Reserve a seat: Once the individual acquires the semaphore, they can reserve a seat by selecting a specific seat and marking it as occupied.
6. Release the semaphore: After reserving the seat, the individual releases the semaphore by performing a "signal" operation, incrementing the semaphore value by one.
Learn more about semaphore variables:
https://brainly.com/question/32667739
#SPJ11
Walt has selected data in a worksheet and inserted a chart. However, the chart is inserted right on top of the data set, and he cannot see the data. How should Walt most efficiently fix this situation?
A) Cut and paste the chart to a different worksheet or to a different part of the current worksheet.
B) Delete the current chart and first select a blank sheet or space before inserting the chart again.
C) Right-click the chart and select Move Below Data Table from the menu list.
D) Click View and zoom into the worksheet so the chart is easily visible.
Answers
Answer:
Click View and zoom into the worksheet so the chart is easily visible.
Explanation:
Walt has entered data into a worksheet and added a chart, and the chart is inserted directly on top of the data set, and he cannot see the data, he should click View and zoom into the worksheet to make the chart more visible.
What is the worksheet?A worksheet is defined as a collection of cells that are organized in rows and columns. It is the working surface with which a user interact to enter data.
In the given case, Walt has entered upon collections into a worksheet and added a chart; however, the chart has been inserted directly on top of the data set, and he is unable to see the data, so he should click View and zoom into the worksheet to make the chart more visible.
Therefore, option D is correct.
Learn more about the worksheet, refer to:
https://brainly.com/question/13129393
#SPJ2
Malware that prevents authorized access until money is paid:___________
Answers
Answer: Malware that prevents authorized access until money is paid ransomware.
Explanation: Ransomware is a type of malware attack in which the attacker locks and encrypts the victim's data, important files and then demands a payment to unlock and decrypt the data.
I. Describe the recursive solution to the Towers of Hanoi puzzle
Answers
The Towers of Hanoi puzzle is a classic problem in computer science and mathematics that involves moving a stack of disks from one pole to another.
The problem is usually stated as follows: given three poles and a stack of n disks on one pole, move the stack to another pole, using the third pole as a temporary holding place, such that no disk is ever placed on top of a smaller disk.A recursive solution to this problem involves breaking it down into smaller sub-problems. Specifically, we can move n-1 disks from the starting pole to the auxiliary pole, using the destination pole as a temporary holding place. We then move the largest disk from the starting pole to the destination pole. Finally, we move the n-1 disks from the auxiliary pole to the destination pole, using the starting pole as a temporary holding place.This process is repeated recursively for each sub-problem until the base case of moving a single disk is reached. The recursive solution requires n-1 moves to solve the problem for n disks. The time complexity of the recursive solution is O(2^n), making it less efficient for larger values of n.
To learn more about Hanoi puzzle click the link below:
brainly.com/question/23446043
#SPJ4
The Glasses class represents a pair of eyeglasses. One of its instance variables is a Prescription object called script. The Prescription object has instance variables that stores the prescription for the left and right eye.
Which of the following constructors for the Glasses class correctly sets the script instance variable correctly? Assume any method calls are valid.
public Glasses(Prescription thePrescription){ script = new Prescription(thePrescription.getLeft(),thePrescription.getRight());}
Answers
Using the knowledge in computational language in python it is possible to write a code that class represents a pair of eyeglasses. One of its instance variables is a Prescription object called script.
Writting the code:oOfPrescriptions = 0
TotalCost = 0
def _init_(self, person, mcpNo, drug, refill, doctor, dCost, units):
self.pName = person
self.mcp = mcpNo
self.drugName = drug
self.noOfRefillsLeft = refill
self.dName = doctor
self.dUnitCost = dCost
self.noOfUnits = units
Prescription.NoOfPrescriptions += 1;
Prescription.TotalCost += self.computeCost()
def getPersonName(self):
return self.pName
def getNoOfRefillsLeft(self):
return self.noOfRefillsLeft
def refillThePrescription(self):
if self.noOfRefillsLeft < 1:
print("Sorry, there are no refills left.\n")
else:
self.noOfRefillsLeft -= 1
print("Refills left: %d\n" %self.noOfRefillsLeft)
def computeCost(self):
DISP_FEE = 0.15 * self.dUnitCost * self.noOfUnits
cost = self.dUnitCost * self.noOfUnits + DISP_FEE
return cost
def _str_(self):
return "Person's Name: " + self.pName + '\nMCP#: ' + self.mcp + "\nDoctor's Name: " + self.dName + "\nDrug: " + self.drugName + "\nRefills Left: %d"%self.noOfRefillsLeft + "\nTotal Bill: $%.2f\n"%(float(int(self.computeCost()*100))/100)
def main():
p1 = Prescription("Rolly Poll", "123 456 789", "Drug1", 3, "Dr. Peter", 2.5, 21)
p2 = Prescription("Henny Penny", "234 567 890", "Drug2", 1, "Dr. Pick", 1.95, 30)
print(p1)
print(p2)
p2.refillThePrescription()
p2.refillThePrescription()
print(p2)
print("Person's Name:", p1.getPersonName())
print("Number of refills left: %d"%p1.getNoOfRefillsLeft())
print()
print("Total number of prescription objects: %d"%p2.NoOfPrescriptions)
rint("Total Cost of all Prescripton Objects: $%.2f\n"%p2.TotalCost)
main()
See more about python at brainly.com/question/18502436
#SPJ1

50 points
Use of all dictnary functions with example easy explain in your own word..
Answers
The Dictionary function in programming is used to create a collection of key-value pairs, where each key maps to a specific value. It allows for efficient lookups and retrievals of values based on their associated keys, making it a useful data structure for tasks such as storing and retrieving configuration settings, representing and manipulating data, and more.
What is Dictionary Function in Programming?Note that the Dictionary function in programming is a data structure that allows you to store and retrieve values based on their associated keys.
It is used to create a collection of key-value pairs, where each key maps to a specific value. The function provides efficient and flexible methods for looking up and retrieving values based on their keys, making it a useful tool for tasks such as storing configuration settings, representing and manipulating data, and more.
Learn more about Dictionary Function:
https://brainly.com/question/14257789
#SPJ1
pls go to my account and answer my question
Answers
Answer:ok I couldn’t find the question do you mind maybe copy pasting it and asking it.
Explanation:
Answer:
ok
Explanation:
►Write
a python program that will convert Fahrenheit Temperature to Celsius and
Celsius Temperature to Fahrenheit
►Formulae
needed:
►°C
= (°F – 32) x 5/9
►°F
= (°C × 9/5) + 32
Answers
Answer:
import math
C_or_F = input("Enter C for Celcius or F for Farenheit: ")
if C_or_F == 'F':
F = int(input("Enter degrees in Fahrenheit: "))
Fahrenheit =(F-32)*(5/9)
print(Fahrenheit,"°")
if C_or_F == 'C':
C = int(input("Enter degrees in Celcius: "))
Celcius = (C*(9/5))+32
print (Celcius,"°")
Explanation:
The first input determines if it is Fahrenheit or Celcius. The second inputs determine how many degrees in that unit of temperature.
!!!!!16 POINTS!!!!Can a computer evaluate an expression to something between true and false? Can you write an expression to deal with a "maybe" answer?
DO NOT JUST ASWERE FOR POINTS OR YPU WILL BE REPORTED AND BLOCKED. IF YOU HAVE ANY QUESTION PLEASE ASK THE IN THE COMMENTS AND DO NOT ASWERE UNLESS YOU KNOW THE ANSWER TO THE PROBLEM, thanks.
Answers
Answer:
Yes a computer can evaluate between a true or false. x < 1, and if the condition is met, the value is true, else its false. A computer itself cannot handle any "maybe" expression, but with the influence of human opinion, in theory its possible. Chocolate cake < Vanilla cake, is an example. Entirely on opinion.
What software controls a computer’s basic functions? the central processor the bios the motherboard the operating system
Answers
The operating system is the software that controls a computer's basic functions.
All computers require a master software program that help in managing the basic functions of the computer. This master software program is referred to as the operating system.
There are different kinds of operating systems such as Windows, macOS etc.
The operating system is itself a program that is fixed into a computer by a boot program. After its installation, the operating system has the capability to manage all the other programs and installations in a computer.
To learn more about operating system, click here:
https://brainly.com/question/1763761
#SPJ4
What are the most common malware types? How do you safeguard computer systems against malware? Why do you need to train users of computer systems to be vigilant about malware? What are some of the most recent malware attacks that you read or herd about in the news media?
Answers
Common Malware Types:
· Viruses
· Worms
· Trojans
· Ransomware
· Spyware
· Adware
Protections From Malware:
· Firewall Software
· Anti-Virus Software
In which of the following cases could a static variable be declared as something other than private?
Select one:
a. When it will be accessed by multiple objects.
b. When implementing static constants.
c. When declared inside a private method.
d. Static variables should never be declared as anything but private.
The correct answer is: When implementing static constants.
Answers
Static variables can be declared as public when they are used to (Option B) implement static constants. This is because static constants represent values that are shared among all instances of the class, so they can be accessed by multiple objects.
In which case could a static variable be declared as something other than private?Option B. When implementing static constants.Static variables are variables that retain their values even when the program exits or terminates. Generally, these variables are declared as private, meaning they can only be accessed and modified within the class or file where they are defined. However, in certain cases, such as when implementing static constants, static variables can be declared as something other than private.
Static constants are variables that are declared with the keyword “static”, and are used to store values that are constant throughout the program. These constants are often declared as public, meaning they can be accessed and modified by other classes or files. Since these constants are unchanging, their values don't need to be protected, so declaring them as something other than private is acceptable.
Learn more about Variables: https://brainly.com/question/25223322
#SPJ4
You are about to repair and change the resistor (small components),but the components are too small to solder and hold,what tool can help you hold the component so that you can replace it.
Answers
Answer:
Needle-nose pliers
Explanation:
Required
Tool used to hold small components
The device to do this is the needle nose pliers.
This device has several functions, but it is specifically designed to hold small components in the computer when the computer is being repaired.
Among the other functions are:
Picking small and tiny screwsCutting of wiresHold wires against the side of the computer caseConsider the following code, which is a portion of SomeClass. The instance variable is initialized by the constructor. The method is supposed to multiply the value passed as a parameter by the instance variable and update the value of the instance variable. However, there is a problem. Re-write this code, without renaming any variable names, to resolve the problem.
private int number;
public void multiplyNumbers(int number)
{
number = number * number;
System. Out. Println("The local variable is: " + number);
System. Out. Println("The instance variable is: " + number);
}
Answers
Use the knowledge of computational language in JAVA to write a code which is a portion of SomeClass.
How to write code that uses a file?To make it simpler the code is described as:
SomeClass
private int number;
public void subtractNumbers(int number)
{
number = number − number;
System.out.println("The local variable is: " + number);
System.out.println("The instance variable is: " + number);
}
See more about Java at brainly.com/question/2266606

Answer:
Correct code (For everyone confused):
private int number;
public void multiplyNumbers(int number) {
this.number = this.number * number;
System.out.println("The local variable is: " + number);
System.out.println("The instance variable is: " + this.number);
}
Explanation:
the this. command allows the instance variable of the class to be called instead of the variable in the constructor which as shown can stay the same while still changing the instance variable of the same name. Allowing for the code to be, say if int number was 5. Then the instance variable would be, 5 + 5, which would print:
The local variable is: 5
The instance variable is: 10
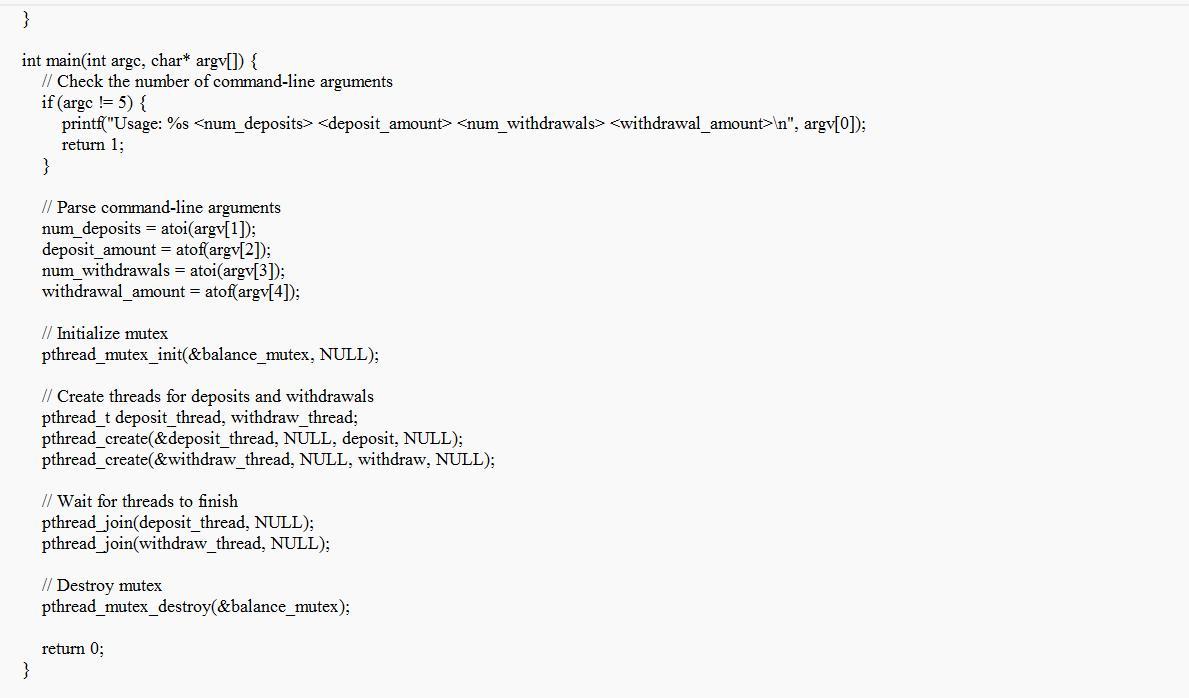
Using pthread library, write a program abc123-prog.c, which takes 4 command line arguments as follows (abc123 should be your abc123):
> ./abc123-prog a b c d
a int (# of deposits)
b double (amount of each deposit)
c int (# of withdrawals)
d double (amount of each withdrawal)
Answers
The example of a program written in C using the pthread library that takes 4 command-line arguments and performs deposits and withdrawals is given below
What is the program?In the code given, One is presuming that there are no limitations on performing deposits and withdrawals simultaneously. In practical situations, it may be necessary to use further synchronization techniques to maintain the accuracy of data and avoid situations in which multiple processes compete for resources.
So, this instance involves making three deposits of $100 and two withdrawals of $50. In order to securely conduct deposits and withdrawals in a multi-threaded environment, the program utilizes mutex locks to synchronize access to the balance variable.
Learn more about program from
https://brainly.com/question/26134656
#SPJ4


what is the answer???

Answers
Answer:
I think it should be C
Explanation:
A group of two or more computers that are link together.
How to use arrays in python as a counter ?
I need to write a program in python where a dice is rolled i have to track how many times each of the six digits(1,2,3,4,5,6) are rolled.
So how do i do that ?
Answers
Answer:
len is a built-in function that calls the given container object's __len__ member function to get the number of elements in the object.
Functions encased with double underscores are usually "special methods" implementing one of the standard interfaces in Python (container, number, etc). Special methods are used via syntactic sugar (object creation, container indexing and slicing, attribute access, built-in functions, etc.).
The method len() returns the number of elements in the list.
A database is an organized collection of ________ related data. group of answer choices logically badly loosely physically
Answers
A database is an organized collection of logically related data. It serves as a structured repository that allows for efficient storage, retrieval, and manipulation of information.
How is a database logically arranged?The logical organization of a database involves designing tables, establishing relationships between them, and defining constraints to ensure data integrity.
The relationships between the tables enable users to access and query the data based on various criteria. By structuring the data logically, databases facilitate effective data management, scalability, and data consistency.
Read more about databases here:
https://brainly.com/question/518894
#SPJ4
which of the following environments utilizes dummy data and is most likely to be installed locally on a system that allows code to be assessed directly and modified easily with each build? a. production b. test c. staging
Answers
The environments that utilizes dummy data and is most likely to be installed locally on a system that allows code to be assessed directly and modified easily with each build is option b. test.
Why is a test environment necessary?Before delivering the program to the user, the testing teams examine its effectiveness and quality in the test environment. It can test a particular section of an application using various data setups and configurations. It is a crucial component of the agile development process.
In a QA environment, intended users can test the finished Waveset application while your upgrade procedure is tested against data, hardware, and software that closely resembles the Production environment.
Therefore, The testing teams evaluate the application's or program's quality in a test environment. This enables computer programmers to find and correct any issues that might affect how well the application functions or the user experience.
Learn more about test environments from
https://brainly.com/question/21902774
#SPJ1
what is the main digestive function of the pancreas?
Answers
The main digestive function of the pancreas is the production and secretion of digestive enzymes. These enzymes play a crucial role in breaking down various components of food, such as carbohydrates, proteins, and fats, to facilitate their absorption and utilization by the body.
The pancreas produces and releases digestive enzymes into the small intestine, where the majority of the digestive process takes place. The two main types of digestive enzymes produced by the pancreas are:
1. Pancreatic amylase: This enzyme helps in the digestion of carbohydrates. It breaks down complex carbohydrates, such as starch and glycogen, into simpler sugars like glucose, which can be readily absorbed by the body.
2. Pancreatic proteases: These enzymes assist in the breakdown of proteins. The pancreas produces several proteases, including trypsinogen, chymotrypsinogen, and procarboxypeptidase. These enzymes are initially secreted in their inactive forms and are activated within the small intestine. Once activated, they break down proteins into smaller peptides and amino acids, which can be absorbed and utilized by the body.
In addition to these primary enzymes, the pancreas also produces lipases, which are responsible for the digestion of fats. Lipases break down dietary fats into fatty acids and glycerol, which can be absorbed by the intestinal lining and transported throughout the body for energy production and other functions.
Overall, the pancreas plays a vital role in the digestion and absorption of nutrients by producing and releasing digestive enzymes that help break down carbohydrates, proteins, and fats in the small intestine, enabling their utilization by the body.
Learn more about the pancreas and digestive enzymes: https://brainly.com/question/29735070
#SPJ11
Does the following cause a data hazard for the 5-stage MIPS pipeline? i1: add $s3, $s3, $s4
Yes
No
Answers
Yes, the instruction "add $s3, $s3, $s4" may cause a data hazard for the 5-stage MIPS pipeline if the value of register $s4 is needed in the subsequent instruction(s) before the addition operation is completed.
This can lead to pipeline stalls and decreased performance. To avoid data hazards, techniques such as forwarding or delaying instructions can be used. Data refers to any set of values, facts, or statistics that are collected, analyzed, and interpreted for the purpose of gaining knowledge or making decisions. Data can be structured or unstructured and can come in various forms such as text, images, audio, and video. With the advent of technology, data is being generated at an unprecedented rate, and its management and analysis have become a crucial component of many industries. The field of data science has emerged to deal with the processing and analysis of large and complex data sets using techniques such as machine learning and data visualization. Data is used in many applications, including scientific research, business intelligence, healthcare, social media, and more.
Learn more about Data here:
https://brainly.com/question/24267807
#SPJ11
Consider the following lines of code which create several LinkedNode objects:
String o0 = "Red";
String o1 = "Green";
String o2 = "Blue";
String o3 = "Yellow";
LinkedNode sln0 = new LinkedNode(o0);
LinkedNode sln1 = new LinkedNode(o1);
LinkedNode sln2 = new LinkedNode(o2);
LinkedNode sln3 = new LinkedNode(o3);
Draw the linked list that would be produced by the following snippets of code:
a. sln1.next = sln3;
sln2.next = sln0;
sln3.next = sln2;
b. sln0.next = sln3;
sln2.next = sln3;
sln3.next = sln1;
Answers
For the given snippets of code, let's visualize the resulting linked list -
sln1.next = sln3;
sln2.next = sln0;
sln3.next = sln2;
How is this so?The resulting linked list would look like -
sln1 -> sln3 -> sln2 -> sln0
The next pointer of sln1 points to sln3, the next pointer of sln3 points to sln2, and the next pointer of sln2 points to sln0.
This forms a chain in the linked list.
Learn more about code at:
https://brainly.com/question/26134656
#SPJ4
Website defacement occurs when attackers take over a computer and produce false web pages. A. TRUE B. FALSE
Answers
Website defacement occurs when attackers take over a computer and produce false web pages is B. FALSE.
The statement that website defacement occurs when attackers take over a computer and produce false web pages is actually false. This can be done through the modification of the HTML code, the insertion of malicious scripts, or by adding content to the website.
It is important to note that website defacement can occur due to different reasons. For example, it can be an act of vandalism, where the attacker wants to show off their skills or send a message. Alternatively, it can be a more malicious act, where the attacker wants to harm the reputation of the website, steal sensitive data, or install malware.
While it is true that attackers can use compromised computers to carry out website defacement, it is not a necessary condition for this to occur. An attacker can deface a website from any computer, as long as they have access to the website's login credentials or can exploit vulnerabilities in the website's software. Therefore, the correct answer is option B.
know more about malware here:
https://brainly.com/question/399317
#SPJ11
Please give answers between 500 words.
What have been the major issues and benefits in
Electronic Data Interchanges (EDI) and Web-Based/Internet
Tools?
Answers
The major issues and benefits of electronic data interchange (EDI) and web-based/Internet tools, such as compatibility and standardization, privacy, cost, dependence on internet connectivity, etc.,
One of the challenges of EDI is that it is ensuring compatibility between different systems and also establishing standardized formats for data exchange. It requires agreement and coordination among trading partners in order to ensure the seamless communication, while there are many benefits that include EDI and web-based tools that enable faster and more efficient exchange of information, eliminating manual processes, paperwork, and potential errors. Real-time data exchange improves operational efficiency and enables faster decision-making. Apart from this, there are many other benefits to these.
Learn more about EDI here
https://brainly.com/question/29755779
#SPJ4
what style is used for double spacing
Answers
Datawriter
Create a File object using "data.txt" as the argument to its constructor. Store the reference to the new File object in a variable of type File.
Will mark brainliest
Answers
Answer:
Explanation:
Write a program in Python which prints your name, surname and class.
Answers
Answer:
print(name + "\n" + surname + "\n" + class)
Explanation:
not enough information is given but this will print those three variables with a newline between each.
___ testing may begin before the program is 100% complete in order to test particular sections of code in a reply to discreet functions or modules
A. Dynamic.
B. Static.
C. Visual.
D. Gray-box.
Answers
Gray-box testing may begin before the program is 100% complete in order to test particular sections of code in a reply to discreet functions or modules. Hence option d is correct.
What is the testingGray-box experiment is a type of operating system experiment where the exploratory has prejudiced information of the within operation of the system being proven.
It connects ingredients of two together vital and static experiment approaches. In silver-box experiment, the exploratory has approach to some news about the within form or law of the spreadsheet but does not have full information or perceptibility into the exercise analyses.
Read more about Gray-box. testing here:
https://brainly.com/question/29590079
#SPJ1
Identify the correct characteristics of Python numbers. Check all that apply.
1. Python numbers can be large integers.
2. Python numbers can be complex values such as 12B16cd.
3. Python numbers can be floating-point numbers.
4. Python numbers have numeric values.
5. Python numbers are created automatically.
Answers
Answer:
The answers are 1, 2, 3, and 4
Explanation:
i just did it on edge
Answer:
The answers are 1, 2, 3, and 4
Explanation:
im simply good