At the heart of every computing device is a(n) _______________, which is usually a single, thin wafer of silicon and tiny transistors.
Answers
Answer:
CPU
Explanation:
Central Processing UnitUnit
Related Questions
A system engineer enhances the security of a network by adding firewalls to both the external network and the internal company network. The firewalls are products of two separate companies. This is an example of what type of security control practice?
Answers
Answer:
Vendor diversity
Explanation:
Different cybersecurity companies maintain different codebases, which means an exploit that might poke holes in the security of one likely won't breach the other. In this situation, the network would still have an active and effective firewall from one vendor even as the exploit from the other vendor's firewall is being patched.
!!!!!16 POINTS!!!!Can a computer evaluate an expression to something between true and false? Can you write an expression to deal with a "maybe" answer?
DO NOT JUST ASWERE FOR POINTS OR YPU WILL BE REPORTED AND BLOCKED. IF YOU HAVE ANY QUESTION PLEASE ASK THE IN THE COMMENTS AND DO NOT ASWERE UNLESS YOU KNOW THE ANSWER TO THE PROBLEM, thanks.
Answers
Answer:
Yes a computer can evaluate between a true or false. x < 1, and if the condition is met, the value is true, else its false. A computer itself cannot handle any "maybe" expression, but with the influence of human opinion, in theory its possible. Chocolate cake < Vanilla cake, is an example. Entirely on opinion.
Shelley works in a dental office as an administrative assistant and uses a desktop computer for scheduling appointments. What type of keyboard is she most likely to use?.
Answers
according to the question A mechanical keyboard is the one that Shelley is most likely to utilize.
What is mechanical keyboard?In addition to a wide range of customization possibilities for look and feel, mechanical keyboards provide a noticeably more pleasant typing experience. They are also more robust and simple to fix.
With mechanical keyboards, signal transmission to your computer frequently just requires a half-press of a key, making typing quicker and simpler.
She is an assistant and makes use of a desktop computer to make reservations, hence a mechanical keyboard will be employed in this instance. She refused to utilize virtual keyboards, computers, or tablets. A mechanical keyboard is the one that Shelley is most likely to utilize.
To learn more about mechanical keyboard refer :
brainly.com/question/28866303
#SPJ4
company abc is buying computers for board members
Answers
Answer:
Not enough information.
Explanation:
_____ is a very short-range wireless connectivity technology designed for cell phones and credit cards.
Answers
The term that fills the blank space is NFC. NFC stands for Near Field Communication, which is a type of wireless connectivity technology designed for cell phones and credit cards that allows them to communicate with each other over short distances without requiring an internet connection or a Wi-Fi connection.
NFC technology has been around for a while, but it has only recently become more popular due to its inclusion in a number of modern smartphones. The reason for this is because NFC technology is a quick and easy way to share information between devices, such as contact information, photos, and videos. This makes it a very useful feature for people who are constantly on the go and need to stay connected with others.
To know more about technology visit:
https://brainly.com/question/9171028
#SPJ11
Which tab on the ribbon contains the command to open the header and footer dialog box where you can add footers, slide numbers and the date and time to slides?
Answers
1. Navigate to the Insert Tab.
2. MS Office 2021 has a separate group dedicated to Header And Footer.
What would you fix or improve in our current technology to make life better for all?
Answers
Which of the following candidates would most likely be hired as a graphic artist?
o a visual design artist with seven years of experience in advertising
a multimedia artist with five years of experience in multimedia design
O a recent college graduate with a degree in multimedia design
O a recent college graduate with a degree in film design
Answers
Answer:
a multimedia artist with five years of experience in multimedia design
Explanation:
how to create a code in pyton to ask the user to enter the number of switches and calculate the possible outcomes that can come from those many numbers of switches(on/off). Please help me with this
Answers
amount = int(input("How many switches? "))
if amount == 0:
print("There are no outcomes for 0 switches")
else:
print("With {} switch(es), there are {} outcomes.".format(amount, 2**amount))

Paige is writing about the progress her team made in setting up a new software system. in one detail, she tells that the team completed the testing phase. in another detail, she tells a second accomplishment the training program has started. what word would it be the best transition to connect the sentences about these two accomplishments
Answers
Answer:
Also
Explanation:
Just checked it in the system
Answer:
Also
Explanation:
CSCU EXAM TEST FINAL1-A software or hardware that checks information coming from the Internet and depending on the applied configuration settings either blocks it or allows it to pass through is called: a-Antivirus b-Firewall c-Antispyware d-Malware 2-A device designed to forward data packets between networks is called: Router 3-A computer network service that allows clients to make indirect network connections to other network services is called 4- Which of the following answers list the protocol and port number used by a spam filter
Answers
Answer:
1. Firewall.
2. Router.
3. Proxy.
4. SMTP, 25.
Explanation:
1. A firewall is a network security protocol that monitors and controls inbound and outbound traffic based on set aside security rules.
Generally, a firewall is used to control access to a computer or network, as it creates a barrier between a computer or a network and the internet in order to protect against unauthorized access. It is a security system pre-installed on most computers to essentially inspect data being transmitted to or from a computer.
Furthermore, firewalls are typically bidirectional, it checks all sent and received data and only allow authorized traffic through.
2. A router can be defined as a network device that is designed typically for forwarding data packets between two or more networks based on a well-defined routing protocol.
A routing protocol can be defined as a set of defined rules or algorithms used by routers to determine the communication paths unto which data should be exchanged between the source router and destination or host device.
3. A proxy can be defined as a computer network service designed to avail end users (clients) the ability to connect indirectly to other network services. For example, a reverse proxy is a type of server that is placed right in front of other servers such as a web server and forwards or routes the user's (client) requests to those servers sitting behind it. When properly configured, reverse proxy helps to ensure security, reliability and good performance of a network.
4. A spam filter can be defined as a software program designed to process all incoming electronic messages (e-mails) and prevents any unsolicited or unwanted mail (spam) from entering the inbox of a client.
Generally, a spam filter uses SMTP with port number 25 to carry out its services.
SMTP is an acronym for Simple Mail Transfer Protocol and it uses the standard port number of 25 to provide clients with requested services.
Computer 1 on network a, with the ip address of 10.1.1.8, wants to send a package to computer 2, with the ip address of 10.1.1.10. on which network is computer 2?
Answers
=65
SOLUTION:- According to the problem we have:-
Definition to approach the problem:- As To do these practical following steps should be done: 1. Start by stripping off about 2 inches of the plastic jacket off the end of the cable. Be very careful at this point, as to not nick or cut into the wires, which are inside. Doing so could alter the characteristics of your cable, or even worse render is useless. Check the wires, one more time for nicks or cuts. If there are any, just whack the whole end off, Thus by using above definition we have the value of the TTL once it reaches its destination will be
62+3
=62+3=(65)
Thus option B should be right there.
Explanation:Please refer to solution in this step.
Answer:
Thus option B should be right there.
=62+3=65
you can learn more through link below:
https://brainly.com/question/14291365#SPJ4
Which of the following statements is true? a Test generators eliminate the need for human testers. b Testers are poor programmers. c Test generators produce error free code. d Test generators are faster than human testers.
Answers
Answer:
d. Test generators are faster than human testers
Explanation:
Test generators are automated testing applications used for testing by making use of artificial intelligence such as bots to take the place of actual users of the software or system to operate the software and detect bugs as well as other primary issues related to the functioning of the tested application
The test generators making use of automated testing are able to run through a developed application in much less time than human testers with the capability to give an analysis of the collected data
Test generators are however test generators are not adequate for carrying out a customer validation program which also include going over documentation and assessing product perception
Therefore, the correct option is test generators are more faster when testing than human testers.
Hardware- The ______________ equipment that makes up the computer.
Answers
Answer:
It's like the stuff you can touch, the software is the stuff that runs in your computer
Explanation:
Hardware has those usb ports or whatever too (i think lol) good luck
Complete the sentence.
use only apps acquired from app stores.
PLEASE HELP
Answers
Answer:
that's a hard one maybe u should email ur teacher bc the punctuation on that is fine and it's not an incomplete sentence
B) What will be the value of the destination operand after each of the following instructions execute in sequence?
mov ax,var2 ; a.
mov ax,[var2+4] ; b.
mov ax,var3 ; c.
mov ax,[var3-2] ; d.
Answers
After each of the following instructions executes in sequence, the value of the destination operand will be: a.
The value of var2 is moved to ax.b. The value at memory address var2+4 is moved to ax.c. The value of var3 is moved to ax.d. The value at memory address var3-2 is moved to ax. The MOV instruction is used to move data from one location to another. MOV is a directive that is used in assembly language to move data from one location to another. It can be used to move both memory and immediate data. MOV is a simple instruction that moves a value from one place to another. In this case, it moves values between the registers and memory locations.
After each of the following instructions executes in sequence, the value of the destination operand will be the value of var2, the value at memory address var2+4, the value of var3, and the value at memory address var3-2, respectively.
To learn more about destination operand, visit:
https://brainly.com/question/29044380
#SPJ11
4.5 Code Practice
Write a loop that inputs words until the user enters STOP.
After each input, the program should number each entry and print in this format:
#1: You entered______
Can someone please help me with this because I so stuck
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
This program is written in C++.
#include <iostream>
using namespace std;
int main()
{
string word;// variable for taking user input
int cond;// to set condition true if user preses the stop and exit from loop
cout<<"Enter word: \n";
cin>>word;
do// start while loop
{
if(word=="stop" || word =="STOP" || word == "Stop")// if user enter word stop, then program exit
{
cond=0;
}
else//otherwise loop continue
{
cout<<" You Entered "+ word +"\n";
cout<<"Enter word: \n";
cin>>word;
cond=1;
}
}
while(cond == 1);// if user don't enter word "stop" loop run continuesly.
cout<<"Program exit";
return 0;
}
Answer:
word = input("Please enter the next word: ")
count = 0
while word != "DONE":
count += 1
print("#{}: You entered the word {}".format(count, word))
word = input("Please enter the next word: ")
print("A total of " + str(count) + " words were entered.")
Explanation:
Assuming this is python, this should help!
Data ________ is important because it establishes an organization's rules for sharing, disseminating, acquiring, standardizing, and classifying data.
Answers
Data protection policy is important because it establishes an organization's rules for acquiring, standardizing and disseminating data.
What is Data protection policy?These are policies adopted by organizations that help to ensure data is adequately protected.
When data isn't protected , it could get to the hands of criminals which could use it for different types of cybercrime and also to ensure compliance with data protection laws in the country.
Read more about Data protection policy here https://brainly.com/question/26493645
The deliverables from the coding, testing, and installation processes include: A. the creation of an analysis plan. B. structured descriptions and diagrams that outline the logic contained within each DFD process. C. the code, program documentation, test scenarios and test data, results of program and system testing, user guides, user training plan, and an installation and conversion plan. D. a database prototype. E. the creation of a document that will consolidate the information that must be considered when implementing a physically distributed systems design.
Answers
The deliverables from the coding, testing, and installation processes include C. the code, program documentation, test scenarios and test data,
Coding, testing, and installation processes are an important aspect of software development. Deliverables from the coding, testing, and installation processes include the following :The code Program documentation Test scenarios and test data Results of program and system testing User guides User training plan An installation and conversion plan The creation of an analysis plan is incorrect since analysis is part of the software development process but is not a deliverable from coding, testing, or installation processes.
The creation of a document that will consolidate the information that must be considered when implementing a physically distributed systems design is incorrect since this is related to distributed systems design and not coding, testing, or installation processes. A database prototype is incorrect since this is related to the development of a database and not coding, testing, or installation processes. Therefore, option C is the correct answer.
To know more about program visit:
https://brainly.com/question/33840330
#SPJ11
The most effective leaders treat everyone alike. True True False
Answers
Answer:
you have to have evidence they do that and on the question theirs no evidence so the answer would be false (as long as theirs no evidence)
Explanation:
Answer:
True
Explanation:
Write a program to print sum on first 10 natural numbers.
#include
int main()
{
int i, sum;
for(i=1;i<=10;++i);
{
sum =sum + i;
}
printf("The sum is = %d",sum);
}
Answers
A program that prints the sum on the first 10 natural numbers is:
int sum=0;int i=1;for(i=1; i <= 10 ; i++) // the value of i will be from 1 to 10{sum=sum+i; //each number will get added to the variable ‘sum’}System.out.println(sum); //What is a program?A computer program in a programming language is a set of instructions and commands written in a language that a computer can execute or understand.
Using the For Loop program, the variables of the first 10 natural numbers can be written as:
int sum=0;int i=1;for(i=1; i <= 10 ; i++) // the value of i will be from 1 to 10{sum=sum+i; //each number will get added to the variable ‘sum’}System.out.println(sum); //Learn more about writing a program here:
https://brainly.com/question/23275071
What is a benefit of the Name Manager feature?
A) add, edit, filter names you have created
B) add, edit, filter predetermined names for cells
C) create a name from a selection
D) rename a worksheet or a workbook
ANSWER: A
Answers
Answer:Its A
Explanation: edge2020
The benefit of the Name Manager feature is to add, edit, and filter names you have created. The correct option is A.
What is the Name Manager feature?The name manager feature is present in the ribbon present in the window of the tab. To open this, open click the formula tab. For instance, we sometimes utilize names rather than cell references when working with formulas in Excel.
The Name Manager allows us to add new references, update existing references, and delete references as well.
To interact with all declared names and table names in a worksheet, use the Name Manager dialog box. You could want to check for names with mistakes, confirm the reference and value of a name, see or update the descriptive comments, or figure out the scope, for instance.
Therefore, the correct option is A) add, edit, and filter the names you have created.
To learn more about the Name Manager feature, refer to the link:
https://brainly.com/question/27817373
#SPJ2
Authoring, maintaining or adding an article to an existing blog is called ___________
Answers
Answer:
"post"
I am not sure so, sorry about that
\(\rm \tiny \color{red}Authoring \: maintaining \: or \: adding \: an \: article \: to \: an \: existing \: blog \: is \: called\)
ANSWER:Authoring, maintaining or adding an article to an existing blog is called Post
\( \tt \small \color{green}by \: : \: denfor \\ \tt \: brainlyeveryday :)\)
:if you were giving a presentation there were 35 people in the room including yourself and you were to shake every person's hand in the room would you shake 35 hands. is it true or false?
Answers
Answer:
False, unless you were to shake your own hand.
Explanation:
Select the correct answer. Which important design element indicates that posters have proper visual balance of text and graphics? A- order B- focus C- visual grammar D-grid E- graphics
Answers
A key design component shows that posters have the right visual balance of text and pictures.
What design components specifically focus on visuals?The foundational aspects of a product's aesthetics include line, shape, negative/white space, volume, value, color, and texture. These are known as the elements of visual design. The principles of design, on the other hand, explain how these components can and should work together for the optimal outcomes.
What elements and principles of the artistic process are used in the creation of a poster's graphic design?Posters for each of the seven design principles—contrast, rhythm, unity, emphasis, pattern, movement, and balance—as well as the seven design elements—illustrate and explain value, color, form, shape, line, space, and texture.
To know more about posters visit:-
https://brainly.com/question/8242738
#SPJ1
One part of a development team has completed an algorithm. Why is it important to share it with others on the team? Choose all that apply. If it is easy to understand, no one will dispute what is included in the algorithm. It will give everyone else an opportunity to comment on the process described in the algorithm. It will serve as the starting point for all future activity. It communicates the consecutive instructions of the solution.
Answers
Answer: B,C,D
Explanation:
Answer:
the answer is B,C,D
Explanation:
thea has received a security alert that someone in london attempted to access the email account of sigrid, who had accessed it in los angeles one hour before. what feature determined an issue and send this alert to thea?
Answers
Impossible travel is the feature determined an issue and send this alert to Thea.
What is email?Email is defined as a form of communication that sends messages through computer networks using electronic devices. Email is a crucial medium for business communication since it is accessible, quick, inexpensive, and easy to replicate.
The best practices for access control involve actions where you must pay attention to upfront costs for various products, your preferred vendor, the setup of access control inside your organization, and the upkeep of the access control system as the business expands.
Thus, impossible travel is the feature determined an issue and send this alert to Thea.
To learn more about email, refer to the link below:
https://brainly.com/question/14380541
#SPJ1
On any given camera, a 50mm lens would create an image of a scene that would appear
enlarged compared to an image of the same scene created using a 25mm lens.
False
O
True
Answer this ASAP
Answers
Answer:
true
Explanation:
On any given camera, a 50mm lens would create an image of a scene that would appear enlarged compared to an image of the same scene created using a 25mm lens. This statement is True.
What is lens?The lens may be diverging or converging which forms an image enlarged or diminished in nature.
The lens of dimension 50mm will make larger image as compared to the image by the lens of 25mm.
Thus, the statement is true.
Learn more about lens.
https://brainly.com/question/14413099
#SPJ2
Ways of sharing information in traditional mode and u modern mode
Answers
The traditional ways of sharing information can be through physical acts of communication, which include talking and writing letters or sending and receiving texts in the form of transmitting e-mails.
we no longer actually rely on traditional modes of sharing information but use modern ways as they are faster and involve an active audience participating in the medium. social media and digital marketing are a few examples.
Books, newspapers, magazines, and radio are a few examples of traditional modes of sharing information. Internet, social media and blogging are a few examples of modern information-sharing methods.
To learn more about the topic:
https://brainly.com/question/1347779?referrer=searchResults
Complete questions-
what are the different ways of sharing information in traditional and modern modes?
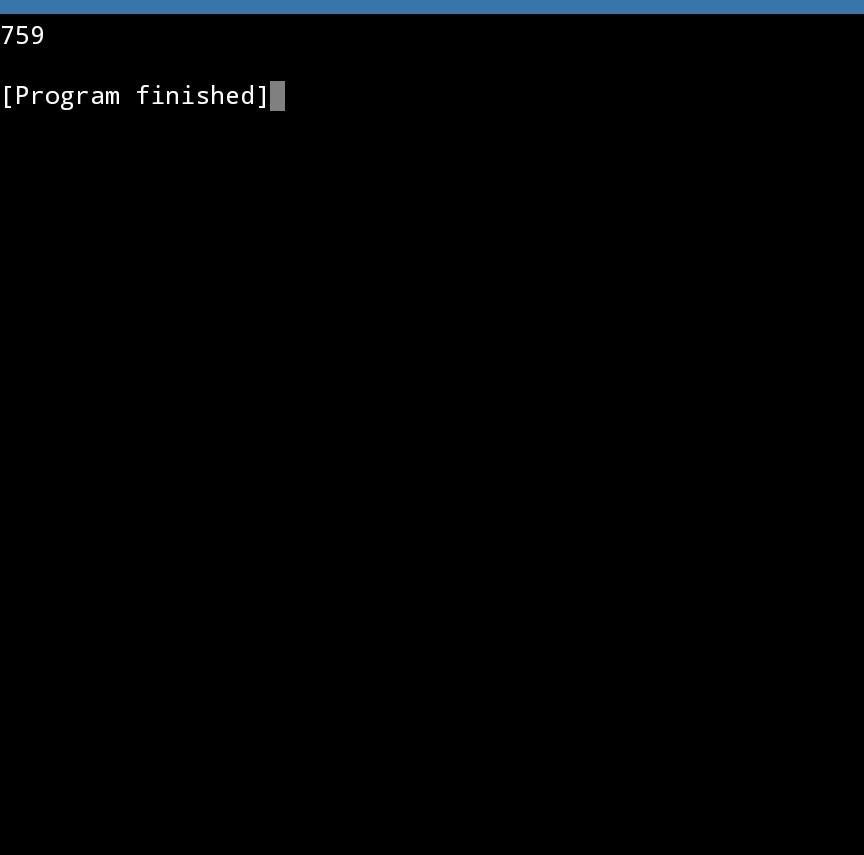
4.9 Code Practice: Question 1

Answers
total = 0
for x in range(3, 67, 3):
total += x
print(total)
I hope this helps!
The program sums all the values in a given range and assigns the total to the sum variable. The program is written in python 3 thus :
sum = 0
#initialize a sum variable, initialized as 0
for x in range(3, 67, 3):
#loop through the range taking a step of 3 after each iteration.
sum+= x
#add the iterated value to the sum variable after each iteration
print(sum)
#display the sum
A sample run of the program is attached
Learn more :https://brainly.com/question/14899725