Because it is going to require so much time, effort, dedication, and typically money on your part, it is very important to find an educational program that suits you well. This lesson outlines six basic questions that you should be able to answer in order to find a program that is best for you. List three of these questions, and explain why each is important.
Answers
It is important to find an educational program that is right for you through in-depth research into the type of learning and discipline required in formal education, and whether these are compatible with your profile and needs.
Questions that can be asked to help a student find the best educational program for themselves and save time, effort, and money might be:
How is the curriculum of the institution formed?Will I be able to find a job after graduation?What types of grants are available? Importance of choosing the educational programIt is essential that there are student benefits in the learning system of each educational program. That's why it's important to choose the educational program that offers the greatest resources for learning through infrastructure, safety and student support.
Therefore, through basic questions the student can identify the best opportunities to search for an educational program that generates progress in their learning and social and professional development.
Find out more information about educational program here:
https://brainly.com/question/13798903
Related Questions
List some of the icons present in Microsoft Windows 7 desktops.
Answers
Answer:
Common desktop icons include Computer, your personal folder, Network, the Recycle Bin, Internet Explorer, and Control Panel.
Explanation:
Difference between software developer and software engineer.
Answers
Answer:
The core difference between the two jobs is that software developers are the creative force that deals with design and program implementation, while software engineers use the principles of engineering to build computer programs and applications.
Explanation:
Answer: The terms "software developer" and "software engineer" are often used interchangeably, but there are some subtle differences between the two roles.
Explanation: Here are some key differences:
Focus: A software developer typically focuses on the implementation of software code and applications based on design specifications, while a software engineer is involved in the entire software development lifecycle, including design, development, testing, deployment, and maintenance.Education and training: Software engineers usually have a broader education and training than software developers, with a strong foundation in computer science and software engineering principles. Software developers may have more specialized training in specific programming languages, frameworks, or technologies.Job responsibilities: Software engineers often take on more managerial or leadership responsibilities, such as project management, requirements analysis, and team leadership, while software developers typically focus more on writing and testing code.Professional standards: Software engineering is typically governed by professional standards and codes of ethics, which may not apply to software development. This reflects the more rigorous and disciplined approach to software engineering compared to software development.To learn more about software developer; https://brainly.com/question/3188992
Please! I need help matching this.
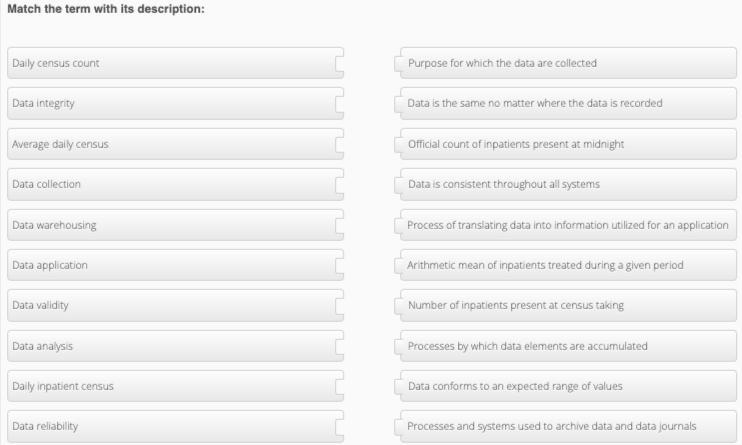
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
What ftp command uploads the filename from the current directory on the local computer to the current directory on the remote computer, and allows the use of wildcard metacharacters to specify the filename.
Answers
Answer:
The command is "put filename"
do anyone know why the technology is more Important in our live??
Answers
Answer:
In general technology makes our lives so much more simpler (full explanation below)
Explanation:
With technology, we have the tools available to us that make it easier to manage our day to day lives and exchange valuable information to our friends and family and other people. Technology is basically harnessing the tools, systems and techniques that are used to help us with problem solving or just making our lives better and easier to live in some way. In fact, technology has played a very significant role in how we live in the world and how we interact with everything around us in the environment today. Hope I helped!
Explanation:
Simply, it simplifies our life making it better than ancient ages. Before, they used to walk using their limbs long distances to reach their destinations after getting exhausted or killed if the person was ill, however today everything has changed. Technology is exactly what human needs. For instance, if someone is going to die at any moment he can reach hospital in few seconds by the favor of technology (cars...)
Plus, Technology helps our lives to remain and become easier. ... Technology is considered to be extremely important in business because it provides faster and more efficient methods of getting a job done. For example, computer programs can be used in business to provide easier manufacturing of goods.
Hope this helps...
Have a great day.
Creates a table in MS Excel with each of the following accounts and indicates their effect on the expanded accounting equation The 1. in February 2020, Miguel Toro established a home rental business under the name Miguel's Rentals. During the month of March, the following transactions were recorded: o To open the business, he deposited $70,000 of his personal funds as an investment. He bought equipment for $5,000 in cash. O Purchased office supplies for $1,500 on credit. He received income from renting a property for $3,500 in cash. He paid for utilities for $800.00. He paid $1,200 of the equipment purchased on credit from the third transaction. O He received income from managing the rent of a building for $4,000 in cash. He provided a rental counseling service to a client for $3,000 on credit. He paid salaries of $1,500 to his secretary. He made a withdrawal of $500.00 for his personal use. O 0 0 O O 0 00
Answers
To create a table in MS Excel and indicate the effect of each account on the expanded accounting equation, you can follow these steps:
1. Open Microsoft Excel and create a new worksheet.
2. Label the columns as follows: Account, Assets, Liabilities, Owner's Equity.
3. Enter the following accounts in the "Account" column: Cash, Equipment, Office Supplies, Rental Income, Utilities Expense, Accounts Payable, Rental Counseling Service, Salaries Expense, Owner's Withdrawals.
4. Leave the Assets, Liabilities, and Owner's Equity columns blank for now.
Next, we will analyze each transaction and update the table accordingly:
Transaction 1: Miguel deposited $70,000 of his personal funds as an investment.
- Increase the Cash account by $70,000.
- Increase the Owner's Equity account by $70,000.
Transaction 2: Miguel bought equipment for $5,000 in cash.
- Increase the Equipment account by $5,000.
- Decrease the Cash account by $5,000.
Transaction 3: Miguel purchased office supplies for $1,500 on credit.
- Increase the Office Supplies account by $1,500.
- Increase the Accounts Payable (Liabilities) account by $1,500.
Transaction 4: Miguel received income from renting a property for $3,500 in cash.
- Increase the Cash account by $3,500.
- Increase the Rental Income account by $3,500.
Transaction 5: Miguel paid $800 for utilities.
- Decrease the Cash account by $800.
- Decrease the Utilities Expense account by $800.
Transaction 6: Miguel paid $1,200 of the equipment purchased on credit.
- Decrease the Accounts Payable (Liabilities) account by $1,200.
- Decrease the Equipment account by $1,200.
Transaction 7: Miguel received income from managing the rent of a building for $4,000 in cash.
- Increase the Cash account by $4,000.
- Increase the Rental Income account by $4,000.
Transaction 8: Miguel provided a rental counseling service to a client for $3,000 on credit.
- Increase the Rental Counseling Service account by $3,000.
- Increase the Accounts Payable (Liabilities) account by $3,000.
Transaction 9: Miguel paid $1,500 salaries to his secretary.
- Decrease the Cash account by $1,500.
- Decrease the Salaries Expense account by $1,500.
Transaction 10: Miguel made a withdrawal of $500 for his personal use.
- Decrease the Cash account by $500.
- Decrease the Owner's Equity account by $500.
Now, you can calculate the totals for the Assets, Liabilities, and Owner's Equity columns by summing the respective account values. The Assets column should include the totals of Cash, Equipment, and Office Supplies. The Liabilities column should include the total of Accounts Payable. The Owner's Equity column should include the total of Owner's Equity minus Owner's Withdrawals.
By creating this table and updating it with the effects of each transaction, you can track the changes in the expanded accounting equation (Assets = Liabilities + Owner's Equity) for Miguel's Rentals during the month of March.
To know more about MS Excel, visit
https://brainly.com/question/30465081
#SPJ11
Besides syndicated data and publicly available data there are other useful sources for discovering marketing data. Identify some of the additional sources: Pew Research Center, World Bank Data, ____
Answers
World Bank Data,____and other government agencies, industry associations, trade publications, and market research firms can provide additional sources of marketing data.
What are some additional sources of marketing data besides syndicated data and publicly available data?Besides Pew Research Center and World Bank Data, some additional sources for discovering marketing data could include government agencies, such as the US Census Bureau, which provides a wide range of demographic and economic data at both the national and local level.
Other useful sources could include industry associations, which often gather and report on data related to specific industries or markets.
Additionally, social media platforms, can provide valuable insights into consumer preferences and behavior through their advertising and analytics tools.
Lastly, internal data sources, such as sales data, customer feedback, and website analytics can also provide valuable information for marketers looking to understand their target audience and improve their marketing efforts.
Learn more about sources
brainly.com/question/30071452
#SPJ11
You want to design a mouse that has gene imp1 knocked out only in sensory neurons (promoter: advillin). which do you need?
Answers
To design a mouse with the gene imp1 knocked out specifically in sensory neurons using the advillin promoter, you would need the following components and steps:
Gene Knockout Strategy: Develop a gene knockout strategy specific to imp1 in sensory neurons. This typically involves designing a targeting construct that contains a selectable marker, such as neomycin resistance gene, flanked by sequences homologous to the imp1 gene. This construct disrupts the imp1 gene when inserted into the genome through homologous recombination.
Advillin Promoter: Obtain the advillin promoter sequence, which is specific to sensory neurons, and ensure it is suitable for driving gene expression in mice.
Transgenic Mouse Generation: Generate transgenic mice by introducing the targeting construct containing the advillin promoter and selectable marker into embryonic stem cells through techniques such as pronuclear injection or gene targeting in embryonic stem cells. Select and breed mice that have successfully incorporated the construct into their genome.
Selective Breeding: Mate the transgenic mice with mice expressing the Cre recombinase enzyme under the control of the advillin promoter. This will allow for the excision of the imp1 gene specifically in sensory neurons.
Genotyping: Perform genotyping analysis on the offspring to identify mice with the desired knockout of imp1 in sensory neurons.
By following these steps, you can create a mouse model with the imp1 gene specifically knocked out in sensory neurons using the advillin promoter.
Learn more about promoter here
https://brainly.com/question/32878095
#SPJ11
Read the scenario and decide which type of banking service is the top priority for each
person.
1. Ja'Mychal is always on the go, and he uses his cell phone for just about everything. He's
heard about banks that have apps in which he can take a picture of a check he wants to
deposit, upload the picture to the app, and the money will be deposited to his account.
He feels this app will save him time instead of having to go to a bank branch to deposit
the money in person. He also wants to be able to see his bank balance through the app.
Which bankinſ service is Ja’Mychal most interested in?
2. Kyra has just began making money. Actually, she hasn't really started making money at
all. Instead, she receives an allowance each month from her parents, but she wants to
Pay Herself First. She knows in a year or so she will need some money to pay for car
insurance.
Which banking service is Kyra most interested in?
3. Sara is about to graduate high school. She has saved money the last few years while
working a part-time job. Her parents bought her a car when she turned 16, but her
younger brother is about to turn 16 and he
Answers
Answer:
1. internet banking service
2. savings service
Explanation:
The type of banking service which is suitable for each of the persons are stated below:
Internet banking serviceSavings serviceSavings ServiceWhat is a Bank?This is a place where people keep money and also perform financial transactions.
With this in mind, we can see that Michael is always on the go so he needs an internet banking service so he can make seamless transactions and because Kyra is still getting allowances, then she needs to get a savings service.
Read more about banking services here:
https://brainly.com/question/16657246
How is the OR (||) logical operator used?
PLS HURRY
Answers
Answer:
The answer is below
Explanation:
A logical operator is a symbol or word used to connect two or more expressions such that the value of the compound expression produced depends only on that of the original expressions and on the meaning of the operator. Common logical operators include AND, OR, and NOT.
Explain why this scenario could put an organization in jeopardy of losing some of its workforce.
Situation: The IT manager decides to add a new software application to replace an older albeit less efficient software application.
Answers
Answer:
Not educating its employees on the new software.
val = 50
def example():
val = 15
print (val)
print (val)
example()
print (val)
Answers
Answer:50
15
i dont know the 3rd number but hope it helped
Explanation:
Based on the given scenario above, the output will be 50, 15, 50. Check more about output below.
What are computer outputs?An output is known to be a kind of data that a computer is said to bring out after processing.
Based on the above, conclusively, looking at the programming code, we can say that the output will be 50, 15, 50.
Learn more about programming from
https://brainly.com/question/23275071
#SPJ2
1. The main objective of an infographic is to provide a compelling story through images and graphical elements while interpreting information. 2. You will create an infographic to mirror your Informat
Answers
An infographic is a visual communication tool that aims to present information in a compelling and easily understandable manner.
Both statements provide accurate descriptions of an infographic, but they highlight different aspects of its purpose and usage.
Statement 1: The main objective of an infographic is to provide a compelling story through images and graphical elements while interpreting information.
This statement emphasizes that the primary goal of an infographic is to visually communicate information in a compelling and engaging way.
Infographics use a combination of images, graphics, charts, and text to present data, facts, or concepts in a visually appealing and easily understandable format.
Statement 2: You will create an infographic to mirror your Informational Memo Report of the case you have worked on for this assignment.
This statement suggests the specific application of an infographic in the context of creating a visual representation of an informational memo report.
It implies that an infographic can be used as an alternative or supplementary medium to present the findings, analysis, and recommendations of a case study or research project.
By using an infographic, the creator can condense and simplify the content while still effectively conveying essential information and key insights.
In summary, an infographic is a visual communication tool that aims to present information in a compelling and easily understandable manner.
Know more about infographic:
https://brainly.com/question/29346066
#SPJ4
What is the name for the dynamic memory space that, unlike the stack, doesn't rely on
sequential ordering or organization?
A. Pointer
B. Heap
C. Pile
D. Load
Answers
The name for the dynamic memory space that, unlike the stack, doesn't rely on sequential ordering or organization is Heap. The Heap is a data structure that allows dynamic memory allocation.
The management of that memory is known as the Heap memory. It is also known as the dynamic memory allocation method. When the program execution begins, some memory is assigned to the program by the operating system, which is known as Stack Memory.
The Heap Memory is very flexible and allows the memory to be used whenever required and is less efficient than the Stack Memory. It takes a little more time for Heap Memory to locate the memory blocks and to allocate and deallocate memory. It is not sequential in nature, so the data allocation is not sequential.
To know more about dynamic visit:
https://brainly.com/question/29216876
#SPJ11
A malicious user launches in attack on a private network, and believe the attack has been successful. However, the target not work is not compromise. What security measure is it most likely using
Answers
This private network was successfully attacked but the target system has not been compromised. This indicates that the network is likely using an effective security measure to protect itself.
The most probable security controls in place would be:
Firewall: A firewall acts as a barrier between the private network and outside threats. It is inspecting traffic and blocking malicious access attempts. This is the most likely security measure preventing the attack from reaching its target.VPN: Using a virtual private network adds an extra layer of encryption and security over the network. Only authorized users with VPN access would be able to connect to the private network, shielding it from outsiders.Endpoint protection: Software like antivirus, anti-malware, and intrusion prevention systems installed on network devices and systems. These provide real-time scanning and can detect/block the attack before it infiltrates endpoints.Network monitoring: Tools are in place to actively monitor network activity, Ethernet/Wi-Fi connections, device communications, etc. Abnormal behavior would immediately flag the attack for inspection.User authentication: Strong password requirements, multi-factor authentication, biometrics or other verification ensures only authorized users can access the private network and systems. Attacker access was blocked at the login stage.In summary, the network is protected using a combination of controls like firewalls, VPN, endpoint security, monitoring and authentication. No single measure alone would prevent every attack, but together they are able to stop even sophisticated threats from compromising the network.
Please let me know if you have any other questions! I'm happy to explain anything in more detail.
Does anyone know how I can fix my computer and what is wrong?

Answers
Answer: What's wrong with it?
Explanation:
Restart your computer
Answer:
shut down all running programs and re-boot the computer, go one different device and try to search up other ways. if none of those work see a local technician.
what is the meaning of HML
Answers
Answer:
Explanation:
Hit my line
PLeeeeeaaase!!! Help!!!
1. Type the correct answer in the box. Spell all words correctly.
What is the output of 1101 x 10 == 11000 + 10?
The output of 1101 x 10 == 11000 + 10 is _______ .
2. Bob is searching for a website using the two words theory and practice. After several searches, he finds only one website that has both the words. Most of the other results have only one of the two words. Some results don’t have either of the two words. Which logic gate principle will help Bob find the most appropriate result?
The ______ logic gate principle will help Bob find the most appropriate result.
Answers
Answer:
1. Is simple,
1101 * 10 = 11010
11000 + 10 = 11010
Both equal the same thing so the output would be True.
As for 2. im sorry but I dont know this one. I dont know anything about logic gates(?)
Explanation:
Answer:
2. The AND logic gate principle will help Bob find the most appropriate result.
Explanation:

true or false? in developing the communication program, the medium refers to who will be delivering the message.
Answers
False. The medium refers to the channel or platform through which the message will be delivered.
What is communication program?A communication program is a type of software application or platform used to facilitate communication between users or groups. This can include email, text messaging, video conferencing, and other forms of digital communication. Communication programs often feature tools to help manage conversations and store data, as well as provide security and privacy controls. Many communication programs also integrate with other services and platforms, such as social media, to provide a more seamless experience. Communication programs can be used for a variety of purposes, from personal communication to business and team collaboration.
To learn more about communication program
https://brainly.com/question/26152499
#SPJ4
For this assignment, you will select a digital media career that you would be interested in pursuing. You will need to do some research to identify the right career for you. Next, you will research and discover what kind of training you will need to land your dream job. Finally, you will find available jobs in your career and select a job that you would want. After doing some research and some thinking, you will:
Select a career that is right for you. Write at least 150 words describing the career and why you believe it would be a good fit for you. Keep in mind your interests and talents.
Research and learn about what training the career requires. After you research, write at least 150 words describing the training. You can include what types of course you would take. How long the training program is, and how much it might cost you.
Finally, you will find a job! Research available jobs in your career and select a job you would want. Provide a copy of the job posting. You can snapshot this, copy and paste it, or copy it word for word. Make sure you include where you found the job posted. You will include at least 75 words on why you selected this particular position. Some helpful sites for job hunting are Indeed, Dice, Career Builder, and Monster.
Answers
A digital media career involves using technology to create and distribute various forms of digital content, such as video, audio, graphics, and multimedia. This can include roles such as graphic designers, web developers, social media specialists, digital marketers, and video producers.
How long the training program is, and how much it might cost you.To land a career in digital media, you will typically need a combination of technical skills and creativity, as well as a strong understanding of digital media platforms and technologies. Depending on the specific career path you choose, you may need to have skills in areas such as graphic design, web development, video editing, or social media management.
Training for a digital media career can vary depending on the specific path you choose, but often involves completing a degree or certificate program in a related field such as digital media, graphic design, or marketing. These programs can range in length from a few months to several years, and can cost anywhere from a few thousand dollars to tens of thousands of dollars.
Job opportunities in digital media can be found on job search sites such as Indeed, Dice, Career Builder, and Monster. One example of a job posting for a digital media position is:
Position: Social Media Specialist
Company: XYZ Digital Agency
Location: New York, NY
Job Type: Full-time
Responsibilities:Develop and execute social media strategies for client accounts
Create engaging social media content, including graphics and video
Monitor social media channels for trends and insights
Analyze social media metrics and adjust strategies as needed
Why I selected this particular position:
I am interested in pursuing a career in social media management, and this position seems like a good fit for my skills and interests. I am drawn to the opportunity to create engaging content and develop strategies to help clients achieve their social media goals. Additionally, the location and job type align with my preferences.
Read more on digital media career here https://brainly.com/question/29363025
#SPJ1
The application layer process that sends mail uses __________. When a client sends email, the client process connects with a server process on well-known port __________. A client retrieves email, however, using one of two application layer protocols: ________ or ________. With ________, mail is downloaded from the server to the client and then deleted on the server. The server starts the __________ service by passively listening on TCP port __________ for client connection requests. However, when a client connects to ta server running __________, copies of the messages are downloaded to the client applications. The original messages are kept on the server until they are manually deleted.
Answers
Answer:
1. SMTP.
2. 25.
3. POP.
4. IMAP.
5. POP.
6. POP.
7. 110.
8. IMAP-capable server.
Explanation:
The application layer process that sends mail uses Simple Mail Transfer Protocol (SMTP). When a client sends email, the client process connects with a server process on well-known port 25. A client retrieves email, however, using one of two application layer protocols: Post Office Protocol (POP) or Internet Message Access Protocol (IMAP). With POP, mail is downloaded from the server to the client and then deleted on the server. The server starts the POP service by passively listening on TCP port 110 for client connection requests. However, when a client connects to a server running IMAP, copies of the messages are downloaded to the client applications. The original messages are kept on the server until they are manually deleted.
Luminaires for fixed lighting installed in Class II, Division 2 locations shall be protected from physical damage by a suitable _____.
Answers
Given what we know, the protection for fixed lightings like the ones described in the question is by way of a guard or by location.
Why is protection necessary?Luminaires, as with all lighting solutions, can be dangerous if proper safety precautions are not taken. The precautions, in this case, include a safe installation location or the use of a guard to prevent damage to the lighting and subsequently to any nearby occupants of the location.
Therefore, we can confirm that Luminaires for fixed lighting installed in Class II, Division 2 locations shall be protected from physical damage by a suitable guard or by a safe location.
To learn more about Electrical safety visit:
https://brainly.com/question/14144270?referrer=searchResults
thin layer found directly under the crust that floats and moves around is called
Answers
The thin layer found directly under the crust that floats and moves around is called the lithosphere.
The lithosphere is the thin layer found directly under the Earth's crust that is responsible for the movement and floating of tectonic plates. It encompasses the rigid outermost layer of the Earth's surface, including the crust and the uppermost part of the mantle.
The lithosphere plays a crucial role in the process of plate tectonics, which drives the movement of continents, the formation of mountains, and the occurrence of earthquakes and volcanic activity. Understanding the composition and behavior of the lithosphere is essential for gaining insights into the dynamics of the Earth's geology and geophysics, and for studying the evolution of our planet's surface and its geological processes over time.
Learn more about lithosphere: https://brainly.com/question/10162846
#SPJ11
a cpu is equipped with a cache. accessing a word takes 40 clock cycles if the data is not in the cache and 5 clock cycles if the data is in the cache. what is the effective memory access time in clock cycles if the hit ratio is 80%?
Answers
The effective memory access time in clock cycles can be calculated by considering the hit ratio and the respective access times for cache hit and cache miss. In this scenario, with a hit ratio of 80% and access times of 40 clock cycles for a cache miss and 5 clock cycles for a cache hit, the effective memory access time is calculated as 12 clock cycles.
The effective memory access time can be calculated using the formula:
Effective Memory Access Time = Cache Hit Time + (Cache Miss Time * Miss Rate)
Given that the hit ratio is 80%, the miss rate is 20%. The cache hit time is 5 clock cycles, and the cache miss time is 40 clock cycles. Plugging in these values into the formula, we have:
Effective Memory Access Time = 5 + (40 * 0.20)
= 5 + 8
= 12
Therefore, the effective memory access time in clock cycles is 12.
To learn more about memory access time, refer:
brainly.com/question/31388776
#SPJ11
with cell b2 selected, set the width of column b to autofit.
Answers
Autofit is an important feature of Excel that allows the user to adjust the column width in an automated way.
The autofit feature helps users to fit the text data in a given cell to the column size. Therefore, with cell B2 selected, set the width of column B to autofit, the following procedures should be followed:
Step 1: Start by selecting the Home tab of the Excel sheet.
Step 2: Choose the Format command group.
Step 3: Click on the AutoFit Column Width command. It will automatically adjust the width of column B so that the contents of cell B2 will fit within that column. For instance, the amount of text data in cell B2 will determine the column width that will be adjusted. However, if the data in the cell exceeds the maximum capacity of the column, then the extra text data will be cropped.
Therefore, when using Excel, the autofit feature is an essential tool to adjust the column width automatically and improve the efficiency of work. This feature helps to save time and produce an organized worksheet with presentable data.
Know more about the Autofit
https://brainly.com/question/32331452
#SPJ11
question 14 (1 point) which of the following statements is false? for decades, relational database management systems (rdbms) have been the standard in data processing. rdbms require unstructured data that fits into neat rectangular tables. as the size of the data and the number of tables and relationships increases, relational databases become more difficult to manipulate efficiently. in today's big-data world, nosql and newsql databases have emerged to deal with the kinds of data storage and processing demands that traditional relational databases cannot meet.
Answers
The false statement among the following options is "rdbms require unstructured data that fits into neat rectangular tables."
In reality, RDBMS or Relational Database Management Systems are designed to work with structured data that can fit into tables. This type of data is organized into rows and columns, where each row represents a single record and each column represents a specific attribute or field of that record.
The data in RDBMS is organized according to a set of rules or constraints called a schema, which defines the relationships between the tables and the data they contain. This schema helps ensure data consistency and integrity, and makes it easier to query and retrieve data from the database.
To know more about data visit:-
https://brainly.com/question/11941925
#SPJ11
50 POINTS!!!!!!!!!!!
Give at least two examples of how the transport layer is used.
Answers
Answer:
The transport layer is responsible for delivering data to the appropriate application process on the host computers. Some transport layer protocols, for example TCP, but not UDP, support virtual circuits, i.e. provide connection-oriented communication over an underlying packet-oriented datagram network.
Explanation:
Some transport layer protocols, for example TCP, but not UDP, support virtual circuits, i.e. provide connection-oriented communication over an underlying packet-oriented datagram network.
Answer:
1. The transport layer is responsible for delivering data to the appropriate application process on the host computers. and 2. Some transport layer protocols, for example TCP, but not UDP, support virtual circuits, i.e. provide connection-oriented communication over an underlying packet-oriented datagram network.
-CC
In order to ensure drive health, what command should you use to search for a repair file system error
Answers
What are 5 key terms that describe cloud computing
Answers
The 5 key terms that describe cloud computing are as follows:
1. Virtualization: Cloud computing heavily relies on virtualization, which enables the creation of virtual resources such as servers, storage, and networks.
This technology allows for the efficient allocation and utilization of physical hardware resources, enabling multiple virtual instances to run on a single physical machine.
2. Scalability: Cloud computing offers scalability, allowing users to easily scale up or down their resource usage based on their needs.
This flexibility ensures that businesses can handle increased demand or accommodate fluctuating workloads without the need for significant infrastructure investments.
3. Elasticity: Elasticity is closely related to scalability and refers to the ability of cloud resources to automatically adapt to workload changes.
It enables resources to be provisioned or deprovisioned dynamically, ensuring optimal performance and cost-efficiency.
4. Service Models: Cloud computing provides different service models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
These models offer varying levels of control and management, allowing users to choose the level of abstraction and responsibility that best suits their needs.
5. Multi-tenancy: Cloud computing often involves multi-tenancy, where multiple users or organizations share the same physical infrastructure and resources.
This enables cost-sharing and resource optimization, allowing cloud providers to serve numerous customers simultaneously while maintaining data isolation and security.
For more questions on SaaS, click on:
https://brainly.com/question/13615203
#SPJ8
What is the significance of the scientific method?
Answers
The scientific method is a widely accepted way of revising and rechecking the work of scientists to see if:
1. The answers match up
2. The experiment was performed correctly
3. The results are accurate
Through the scientific method, the probability is very high that things will not go wrong. The significance of this is that if the scientific method is not applied to an experiment, nobody knows the results. If nobody knows the results, there are many possible unintended consequences that could happen. Hope this helps!