Charles Montesquieu believed that the
Legislative Branch should do what?
A. Make laws
B. Enforce laws
C. Interpret laws
elles sone. All Rights Resed.
Answers
Answer:
A. Make Laws
Explanation:
Montesquieu believed the ways to go about limiting the power of a monarch would be to split up power among 3 groups, Judicial, Legislative and Executive. The American Presidential system and Constitution used Montesquieu's writings as a foundation for their principles.
Judicial Interprets lawsLegislative Makes lawsExecutive Enforces LawRelated Questions
What area of the SP 800-100 management maintenance model addresses the actions of the content filter described here?
Answers
Answer:
Security planning, risk management, change management and configuration management.
Explanation:
Note: This question is not complete. The complete question is therefore provided before answering the question. See the attached pdf for the complete question.
The explanation of the answer is now given as follows:
Management maintenance model is a model that assist in the successful management of operations. It is a model with techniques and clear guidelines meant to be employed for attaining the aim of the organization.
SP 800-100 maintenance model is a model that handles the 13th information security areas like security planning, configuration management, governance of information security, incidence response, performance measures, change management, risk management, and among others.
The area of the SP 800-100 management maintenance model which addresses the actions of the content filter described in the question are:
a. Security planning: The security measures put in place is the email content filter which helps to prevent the executable files from attaching to emails. It should be noted that the function of the Security Planning section of SP 800-100 is to serve as a strategic plan that employed to give support to the IT plans and objectives of Sequential Label and Supply Company (SLS).
b. Risk Management: This is because the SLS greatly assist in reducing an accidental execution of dangerous software due to its prevention of executable email attachments.
c. Change management: This monitors the performance of the system continuously without stopping.
It should be noted that there is a need for the configuration of the system to meet the security requirement and also the needs of the user at the same time in such a way that the performance of either of the two is not compromised.
The configuration should meet both security and user needs without compromising the performance of either.
Do you use commas or periods in Terms Of Conditions?
For example,
in the following terms of conditions should be a comma or a period?
- Professionalism is required, (or period)
- You may not breach this document, (or period)
Furthermore, if a period is used, is the rest of the contract useless?
Answers
Answer:
yes u should use a period
Explanation:
What is one outcome of an integration point?
Answers
Answer:
What is one outcome of an integration point? It provides information to a system builder to potentially pivot the course of action. It bring several Kanban processes to conclusion. It supports SAFe budgeting milestones.
What do Dynamic-Link Library (DLL) files do?
Answers
The use of DLLs helps promote modularization of code, code reuse, efficient memory usage, and reduced disk space. So, the operating system and the programs load faster, run faster, and take less disk space on the computer.
Explanation:A dynamic link library (DLL) is a collection of small programs that larger programs can load when needed to complete specific tasks. The small program, called a DLL file, contains instructions that help the larger program handle what may not be a core function of the original program.
What would be an ideal scenario for using edge computing solutions?
Answers
An ideal scenario for using edge computing solutions will be a school computer lab with workstations connected to a local network. The correct option is C.
What is edge computing?The most typical places to find edge computing are in the transportation, industrial, energy, and even retail sectors.
The performant and scalable implementation model used by Akamai ensures that data and computation are not constrained by latency problems, which can negatively affect digital experiences.
Thanks to EdgeWorkers and EdgeKV, development teams can now focus on creating cutting-edge services and manage Akamai as code as a part of their digital infrastructure.
Thus, the correct option is C.
For more details regarding edge computing, visit:
https://brainly.com/question/28256857
#SPJ1
C programming 3.26 LAB: Leap year
A year in the modern Gregorian Calendar consists of 365 days. In reality, the earth takes longer to rotate around the sun. To account for the difference in time, every 4 years, a leap year takes place. A leap year is when a year has 366 days: An extra day, February 29th. The requirements for a given year to be a leap year are:
1) The year must be divisible by 4
2) If the year is a century year (1700, 1800, etc.), the year must be evenly divisible by 400; therefore, both 1700 and 1800 are not leap years
Some example leap years are 1600, 1712, and 2016.
Write a program that takes in a year and determines whether that year is a leap year.
Ex: If the input is 1712, the output is:
1712 - leap year
Answers
The code below is in Java. It uses if else structure and modulo operator to check if a given year is a leap year or not. Recall that modulo operator is used to get the remainder of the division. ⇒ a % b = remainder.
What is C programming?The general-purpose programming language C is effective. The creation of software such as operating systems, databases, compilers, and other tools is possible with it. C is a great language for beginners to learn programming with.
These C tutorials will lead you step-by-step as you learn C programming.
Low-level memory access, a small collection of keywords, and a clean style are the fundamental characteristics of the C programming language, which makes it ideal for system programming like operating system or compiler development.
Therefore, The code below is in Java. It uses if else structure and modulo operator to check if a given year is a leap year or not. Recall that modulo operator is used to get the remainder of the division. ⇒ a % b = remainder.
To learn more about C programming, refer to the link:
https://brainly.com/question/10895516
#SPJ1
2. To publish your slide show as movie what should you click on first? (1 point)
O File
O Animations
O Slide Show
O View
Answers
To publish your slide show as movie we click on Slide show first.
What do you know about PPT?
A PowerPoint slideshow (PPT) is a presentation made using Microsoft software that enables users to include audio, visual, and audio/visual features. It is regarded as a multimedia technology that also serves as a tool for sharing and collaborating on content.
What is Slide show?
A slide show (slideshow) is a presentation of a series of still images (slides) on a projection screen or electronic display device, typically in a prearranged sequence.
To start your slide show, on the Slide Show tab, select Play From Beginning.To manage your slide show, go to the controls in the bottom-left cornerTo skip to any slide in the presentation, right-click the screen and select Go to Slide. Then, enter the slide number you want in the Slide box, and select OK.Learn more about SlideShow click here :
https://brainly.com/question/27363709
#SPJ1
Technical communicators view technology to be the most important aspect of their professional identity.
Question 7 options:
True
False
Answers
Answer:
false
Explanation:
technology is necessary but it's not the only thing that's important.
Read in a 3-character string from input into variable userCode. Declare a boolean variable isValid and set isValid to true if userCode only contains digits. Otherwise, set isValid to false.
Ex: If the input is 836, then the output is:
Passcode is valid
Note: Use getline(cin, userCode) to read the entire line from input into userCode.
in c++?
Answers
The program based on the information is given below.
How to write the programHere's a C++ code snippet that reads a 3-character string from input into variable userCode, checks if it only contains digits, and sets the boolean variable isValid accordingly:
#include <iostream>
#include <string>
using namespace std;
int main() {
string userCode;
bool isValid = true;
getline(cin, userCode); // read input into userCode
// check if userCode contains only digits
for (char c : userCode) {
if (!isdigit(c)) {
isValid = false;
break;
}
}
// output result based on isValid
if (isValid) {
cout << "Passcode is valid" << endl;
} else {
cout << "Passcode is not valid" << endl;
}
return 0;
}
Note that the code uses the isdigit function from the <cctype> library to check if each character in userCode is a digit.
Learn more about program on
https://brainly.com/question/1538272
#SPJ1
working with the tkinter(python) library
make the window you create always appear on top of other windows. You can do this with lift() or root.attributes('-topmost', ...), but this does not apply to full-screen windows. What can i do?
Answers
To make a tkinter window always appear on top of other windows, including full-screen windows, you must use the wm_attributes method with the topmost attribute set to True.
How can I make a tkinter window always appear on top of other windows?By using the wm_attributes method in tkinter and setting the topmost attribute to True, you can ensure that your tkinter window stays on top of other windows, even when they are in full-screen mode.
This attribute allows you to maintain the window's visibility and prominence regardless of the current state of other windows on your screen.
Read more about python
brainly.com/question/26497128
#SPJ1
what is the meaning of oneironaut and Oneironautics? pls help
Answers
Answer:
Such a traveller in a dream . Oneironauts refers to the ability to travel within a dream on a conscious basis. Such a traveller in a dream may be called an oneironaut.
lucid dreaming . Oneironauts (uncountable) lucid dreaming, the ability to explore dreams.
Explanation:
A hexadecimal input can have how many values
Answers
Answer: Unlike the decimal system representing numbers using 10 symbols, hexadecimal uses 16 distinct symbols, most often the symbols "0"–"9" to represent values 0 to 9, and "A" to "F" (or alternatively "a"–"f") to represent values from 10 to 15.
Explanation:
help asap !!!
which component of cpu controls the overall operation of computer..
Answers
Answer:
Control unit.
Explanation:
A scheduling computer system refers to an ability of the computer that typically allows one process to use the central processing unit (CPU) while another process is waiting for input-output (I/O), thus making a complete usage of any lost central processing unit (CPU) cycles in order to prevent redundancy.
Modern central processing units (CPUs) only require a few nanoseconds to execute any instruction when all operands are stored in its registers.
In terms of the scheduling metrics of a central processing unit (CPU), the time at which a job completes or is executed minus the time at which the job arrived in the system is known as turnaround time.
Generally, it is one of the scheduling metrics to select for optimum performance of the central processing unit (CPU).
The component of the central processing unit (CPU) that controls the overall operation of a computer is the control unit. It comprises of circuitry that makes use of electrical signals to direct the operations of all parts of the computer system. Also, it instructs the input and output device (I/O devices) and the arithmetic logic unit how to respond to informations sent to the processor.
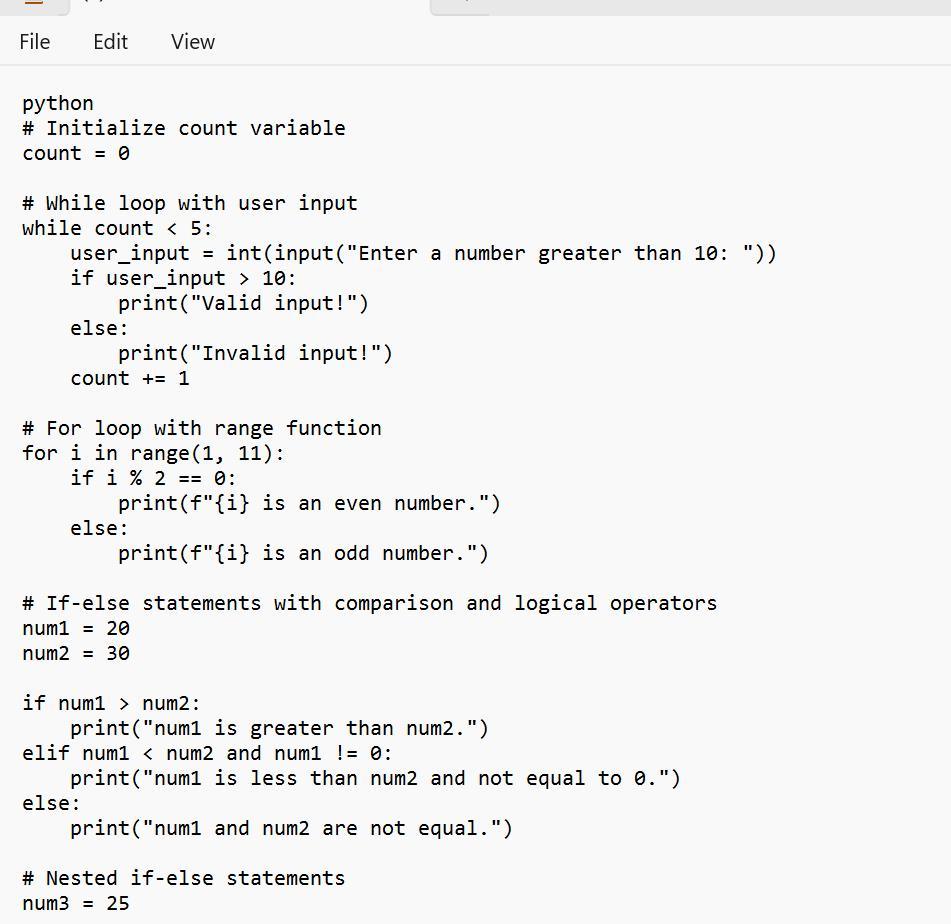
if-else AND if-elif-else
need at minimum two sets of if, one must contain elif
comparison operators
>, <, >=, <=, !=, ==
used at least three times
logical operator
and, or, not
used at least once
while loop AND for loop
both a while loop and a for loop must be used
while loop
based on user input
be sure to include / update your loop control variable
must include a count variable that counts how many times the while loop runs
for loop must include one version of the range function
range(x), range(x,y), or range(x,y,z)
comments
# this line describes the following code
comments are essential, make sure they are useful and informative (I do read them)
at least 40 lines of code
this includes appropriate whitespace and comments
python
Answers
Based on the image, one can see an example of Python code that is said to be able to meets the requirements that are given in the question:
What is the python?The code given is seen as a form of a Python script that tells more on the use of if-else as well as if-elif-else statements, also the use of comparison operators, logical operators, and others
Therefore, one need to know that the code is just a form of an example and it can or cannot not have a special functional purpose. It is one that is meant to tell more on the use of if-else, if-elif-else statements, etc.
Learn more about python from
https://brainly.com/question/26497128
#SPJ1

PLEASE HELP WILL GIVE BRAINLIEST!!!’
What is a Path, and how do you know that it is filled and selected?
A Path is a series of (blank)
that you can join together. As you click a point in a curve, it changes color and becomes (blank).
Answers
Answer: What is a Path, and how do you know that it is filled and selected?
A Path is a series of curves that you can join together. As you click a point in a curve, it changes color and becomes black.
Maya has discovered that her computer is running slowly and not like it used to. She has decided to research why this might be. Which of the below is a good step for her to take in the research process?
A. Ask family and friends about their experiences.
B. Allow an unknown online person to remotely troubleshoot the problem.
C. Try every solution that can be found on the internet.
D. Turn off your computer’s firewall.
Answers
The good step for her to take in the research is to ask family and friends about their experiences option (A) is correct.
What is a computer?A computer is a digital electronic appliance that may be programmed to automatically perform a series of logical or mathematical operations. Programs are generic sequences of operations that can be carried out by modern computers. These apps give computers the capacity to carry out a broad range of tasks.
As we know,
Programs operating in the background are one of the most frequent causes of a slow computer.
TSRs and starting programs that launch automatically each time the computer boots should be removed or disabled.
Thus, the good step for her to take in the research is to ask family and friends about their experiences option (A) is correct.
Learn more about computers here:
https://brainly.com/question/21080395
#SPJ2
Deb needs to add borders on the cells and around the table she has inserted into her Word document.
Insert tab, Tables group
Table Tools Design contextual tab
Home tab, Page Layout
Home tab, Format group
Answers
Answer:
Design tab
Explanation:
Select the call or table that you will like to useThen select the design tabIn the group page background select Page Borders There you will have multiple choses for where you want your borderYou can even customize your border by pressing Custom Border at the bottom of the list for Page BordersAnswer:
Table tools design contextual tab
Explanation:
Write a procedure ConvertToBinary that takes an input as a number from 0 to 16 (including 0 but not 16) and converts it to a binary number. The binary number should be returned as a list.
Answers
Sure, here's an example of a Python function that converts a decimal number to binary and returns the result as a list:
def ConvertToBinary(decimal):
binary = []
while decimal > 0:
remainder = decimal % 2
binary.append(remainder)
decimal = decimal // 2
return binary[::-1]
The function takes in an input decimal which is a number between 0 and 16 (not including 16) and uses a while loop to repeatedly divide the decimal number by 2 and take the remainder. The remainders are then appended to a list binary. Since the remainders are appended to the list in reverse order, the result is reversed by slicing the list [-1::-1] to give the proper order.
You can also add a check to make sure that the input is within the required range:
def ConvertToBinary(decimal):
if decimal < 0 or decimal >= 16:
return None
binary = []
while decimal > 0:
remainder = decimal % 2
binary.append(remainder)
decimal = decimal // 2
return binary[::-1]
this way you can make sure that the input provided is within the allowed range.
James has a USB flash drive that he has used at work. The drive needs to be thrown away, but James wants to make sure that the data is no longer on the drive before he throws it away. What can James use to wipe the data clean?
a. Zero-fill utility
b. Format the drive
c. ATA Secure Erase
d. Smash the USB drive
Answers
Answer:
C. ATA Secure Erase
D. Smash the USB drive
Explanation:
Zero fill utility is a specialized way of formatting a storage device particularly secondary storage such as hard disk, flash drive e.t.c. In this process, the disk contents are overwritten with zeros. Once this has been done, undoing is essentially hard but possible. In most cases, this might just mean that the data content is corrupt and as such might still be recovered, maybe not in its pure entirety.
Formatting the drive on another hand does not essentially mean cleaning the drive and wiping off data. It just means that operating systems cannot see those data contents anymore. They are still present in the drive and can be recovered.
ATA Secure Erase is actually a way of completely and permanently erasing the content in a drive. Once the function has been done, undoing is not possible. Both the data content and even the data management table will be completely gone.
Smashing the USB drive is the surest way of cleaning data as that will permanently destroy the working components of the drive such as the memory chip. And once that happens then there's no drive let alone its contents.
Consider a two-by-three integer array t: a). Write a statement that declares and creates t. b). Write a nested for statement that initializes each element of t to zero. c). Write a nested for statement that inputs the values for the elements of t from the user. d). Write a series of statements that determines and displays the smallest value in t. e). Write a series of statements that displays the contents of t in tabular format. List the column indices as headings across the top, and list the row indices at the left of each row.
Answers
Answer:
The program in C++ is as follows:
#include <iostream>
using namespace std;
int main(){
int t[2][3];
for(int i = 0;i<2;i++){
for(int j = 0;j<3;j++){
t[i][i] = 0; } }
cout<<"Enter array elements: ";
for(int i = 0;i<2;i++){
for(int j = 0;j<3;j++){
cin>>t[i][j]; } }
int small = t[0][0];
for(int i = 0;i<2;i++){
for(int j = 0;j<3;j++){
if(small>t[i][j]){small = t[i][j];} } }
cout<<"Smallest: "<<small<<endl<<endl;
cout<<" \t0\t1\t2"<<endl;
cout<<" \t_\t_\t_"<<endl;
for(int i = 0;i<2;i++){
cout<<i<<"|\t";
for(int j = 0;j<3;j++){
cout<<t[i][j]<<"\t";
}
cout<<endl; }
return 0;
}
Explanation:
See attachment for complete source file where comments are used to explain each line
Which concept deals with connecting devices like smart refrigerators and smart thermostats to the internet?
1 point
IoT
IPv6
NAT
HTTP
Answers
The concept that deals with connecting devices like smart refrigerators and smart thermostats to the internet is the Internet of Things (IoT).
The correct answer to the given question is option A.
It is a network of interconnected devices and systems that can interact with each other through the internet, and it includes anything that can be connected to the internet, from smartphones to cars, homes, and even cities.
IoT is a revolutionary technology that has the potential to change the way we live and work. It is built on the foundation of the internet and relies on the Internet Protocol (IP) for communication between devices.
To enable IoT to operate on a global scale, IPv6 was developed. This protocol provides a large number of unique IP addresses that can accommodate the growing number of IoT devices that are being connected to the internet. Network Address Translation (NAT) is another concept that is used to connect devices to the internet. It is a technique that allows multiple devices to share a single public IP address.
Hypertext Transfer Protocol (HTTP) is the primary protocol used to transfer data over the internet. In summary, IoT is the concept that deals with connecting devices like smart refrigerators and smart thermostats to the internet.
For more such questions on Internet of Things, click on:
https://brainly.com/question/19995128
#SPJ8
A _____ address directs the frame to the next device along the network.
Answers
Answer:
When sending a frame to another device on a remote network, the device sending the frame will use the MAC address of the local router interface, which is the default gateway.
An unicast address directs the frame to the next device along the network.
What is network?
A computer network is a group of computers that share resources on or provided by network nodes. To communicate with one another, the computers use standard communication protocols across digital linkages. These linkages are made up of telecommunication network technologies that are based on physically wired, optical, and wireless radio-frequency means and can be configured in a number of network topologies.
The term "unicast" refers to communication in which a piece of information is transferred from one point to another. In this situation, there is only one sender and one receiver.
To learn more about network
https://brainly.com/question/28041042
#SPJ13
2. Which of the following would you keep in an office quick-list file?
O A. Your personal checking account number
O B. Equipment catalogs
OC. An instruction manual
O D. Commonly asked customer questions
Answers
Option D is correct . I would store frequently asked customer questions in an office quick-list file.
How can a list file be created?Navigate to the folder that contains the files you want to list using a computer or Windows Explorer. o Do not open the folder; you should be "one level" above it, allowing you to view the folder itself rather than its contents. Right-click the folder that contains the listed files by pressing and holding the SHIFT key.
The Java Runtime Environment (JRE) uses JAR files alongside LIST files that are associated with JAR files. Nonetheless, in the event that you're ready to open the Container document, you can utilize a word processor like Scratch pad, or one from our best free content tools list, to open the Rundown record to peruse its text contents.
To learn more about Java visit :
https://brainly.com/question/30354647
#SPJ1
In which of the following situations must you stop for a school bus with flashing red lights?
None of the choices are correct.
on a highway that is divided into two separate roadways if you are on the SAME roadway as the school bus
you never have to stop for a school bus as long as you slow down and proceed with caution until you have completely passed it
on a highway that is divided into two separate roadways if you are on the OPPOSITE roadway as the school bus
Answers
The correct answer is:
on a highway that is divided into two separate roadways if you are on the OPPOSITE roadway as the school busWhat happens when a school bus is flashing red lightsWhen a school bus has its flashing red lights activated and the stop sign extended, it is indicating that students are either boarding or exiting the bus. In most jurisdictions, drivers are required to stop when they are on the opposite side of a divided highway from the school bus. This is to ensure the safety of the students crossing the road.
It is crucial to follow the specific laws and regulations of your local jurisdiction regarding school bus safety, as they may vary.
Learn more about school bus at
https://brainly.com/question/30615345
#SPJ1
you make an api call using the aws command line interface (cli) to request credentials from aws security token service (aws sts). which of the following elements is needed to make this api call?
Answers
Answer:
To make an API call using the AWS Command Line Interface (CLI) to request credentials from AWS Security Token Service (AWS STS), you will need the following elements:
AWS CLI installed on your computer, you can install it by following the instruction from here: https://docs.aws.amazon.com/cli/latest/userguide/install-cliv2.html
Access keys for an AWS Identity and Access Management (IAM) user or role that has permissions to call the STS API. To get the access keys, you can create an IAM user with the proper permissions and then generate an access key and secret access key. https://docs.aws.amazon.com/general/latest/gr/aws-sec-cred-types.html#access-keys-and-secret-access-keys
The AWS CLI command for requesting temporary security credentials, which is "aws sts assume-role".
The ARN (Amazon Resource Name) of the IAM role you want to assume. The ARN is a unique identifier for the role and it will be in the format of "arn:aws:iam::account-id:role/role-name"
The duration of the session, which is the amount of time that the temporary security credentials are valid. It is expressed in seconds or as a duration string (for example, 1h, 12h, or 3600s).
Example:
aws sts assume-role --role-arn arn:aws:iam::1234567890:role/ExampleRole --role-session-name ExampleSession --duration-seconds 3600
This command requests temporary security credentials for the role "ExampleRole" with a session name "ExampleSession" and a duration of 3600 seconds (1 hour).
Once you have all these elements, you can make the API call using the command prompt or terminal, and the output will be the temporary security credentials (access key, secret access key, session token) that you can use to access AWS resources.
A customer uses an app to order pizza for delivery. Which component includes
aspects of the customer's interaction with an enterprise platform?
Answers
~frestoripongetosarangeou
A consumer orders pizza for delivery via an app. The element of the data component covers how a customer interacts with an enterprise platform
What is the data component?A data component is a tool that provides information on the activities taking place on a certain enterprise platform. This application also aids in keeping track of the available inventory.
In this approach, customers place their orders through a smartphone app.
Therefore, while ordering pizza the consumer uses the data component.
To know more about the Data component, visit the link below:
https://brainly.com/question/27976243
#SPJ2
Question 10 of 10
What should you do to make your MakeCode micro:bit program respond to a
false start?
OA. Scrap the program and start over from the beginning with different
users.
OB. Use the input variable block to replace the "true" value in the If-
then condition.
C. Create a Boolean variable and control structure to make the
program skip the rest of the reaction test.
OD. Drag the entire "reaction Time" equation back into the set
reaction Time to block.
Answers
The thing you would have to do to make your MakeCode micro:bit program respond to a false start is B. Use the input variable block to replace the "true" value in the If- then condition.
What is a False Start?This refers to the term that is used in programming circles and terms to show the start of a variable or program without all the required things available,
Hence, it can be seen that in order to make your given program in MakeCode micro:bit program respond to a false start, you would have set the value of the variables false_start which means replacing the true value in the conditional statement to false, which means that no time elapsed
Read more about false starts here:
https://brainly.com/question/10818465
#SPJ1
Tunes up and maintains your PC, with anti-spyware, privacy protection, and system cleaning functions. A _ _ _ n _ _ _ S _ _ _e _ C _ _ _
Answers
Tunes up and maintains your PC, with anti-spyware, privacy protection, and system cleaning functions is all-in-one PC optimizer"
How do one maintains their PC?An all-in-one PC optimizer improves computer performance and security by optimizing settings and configuration. Tasks like defragmenting hard drive, optimizing startup, managing resources efficiently can be done.
Anti-spyware has tools to detect and remove malicious software. Protect your computer and privacy with this feature. System cleaning involves removing browser history, temporary files, cookies, and shredding sensitive data.
Learn more about privacy protection from
https://brainly.com/question/31211416
#SPJ1
A backup operator wants to perform a backup to enhance the RTO and RPO in a highly time- and storage-efficient way that has no impact on production systems. Which of the following backup types should the operator use?
A. Tape
B. Full
C. Image
D. Snapshot
Answers
In this scenario, the backup operator should consider using the option D-"Snapshot" backup type.
A snapshot backup captures the state and data of a system or storage device at a specific point in time, without interrupting or impacting the production systems.
Snapshots are highly time- and storage-efficient because they only store the changes made since the last snapshot, rather than creating a complete copy of all data.
This significantly reduces the amount of storage space required and minimizes the backup window.
Moreover, snapshots provide an enhanced Recovery Time Objective (RTO) and Recovery Point Objective (RPO) as they can be quickly restored to the exact point in time when the snapshot was taken.
This allows for efficient recovery in case of data loss or system failure, ensuring minimal downtime and data loss.
Therefore, to achieve a highly time- and storage-efficient backup solution with no impact on production systems, the backup operator should utilize the "Snapshot" backup type.
For more questions on Recovery Time Objective, click on:
https://brainly.com/question/31844116
#SPJ8
A(n) ________ event is an alert that is generated when the gossip traffic enables a platform to conclude that an attack is under way
A. PEP
B. DDI
C. IDEP
D. IDME
Answers
Answer:
B. DDI
Explanation:
A(n) DDI event is an alert that is produce or invoke when the gossip traffic allow a platform to conclude that an attack or potential attack is under way.
A device driver is a computer program that operates or controls a particular type of device that is attached to a computer system.
A driver provides or supply a software interface to hardware devices which enable the operating systems and other computer programs to access hardware functions without needing to know the exact details in respect of the hardware being used.
DDI means Device Driver Interface
A driver relate or communicate with the device via the computer bus or communications subsystem to which the hardware is connected. Whenever a calling program invokes a routine in the driver, the driver will subsequently transmit commands to the device.