compare and contrast the leadership and leadership and management style of apple and Samsung
Answers
Answer:
Samsung's business model has focused on vertically integrating supply chains and ramping up production volume. Apple has made a business strategy of focusing on design and user experience while outsourcing elements such as manufacturing. The two companies have found themselves engaged in legal battles over intellectual property and patent fights.
Hope this helps!
Related Questions
With respect to iot security, what term is used to describe the digital and physical vulnerabilities of the iot hardware and software environment?
a. Traffic Congestion
b. Device Manipulation
c. Attack Surface
d. Environmental Monitoring
Answers
Answer: Answer Surface
Explanation:
You would use the _______ conditional formatting options when analyzing a worksheet in which you want to highlight the highest or lowest values compared to other cells in the selection.
Answers
Answer:
Top/bottom conditional formatting
Explanation:
The top/bottom conditional formatting automatically carries out the task of finding the highest, lowest and even average values.
Conditional formatting formatting gives one the opportunity to enhance reports and dashboards as they work on excel.
You use the too/bottom formatting to highlight cells whose values of highest in a dataset and lowest in a dataset
Write a C function arrayMinimum( ) that accepts an integer valued array a along with its size arraySize as parameters and returns the smallest array element.
Answers
Answer:
int arrayMinimum(int* arr, int arraySize){
int result = arr[0];
for (int i = 0; i < arraySize; i++){
if (arr[i] < result)
result = arr[i];
}
return result;
}
Explanation:
This function takes a integer array and it's size as parameters. It defines an integer variable result, which is initialized with the value of the first element of the array. The function then iterates through the array and checks if the current index's value is smaller than result. If it's smaller than result, it sets result to the element, if it isn't it continues at normal. At the end of the function, the function returns result, which represents the smallest array element.
Why is it essential to design an architecture before implementing the software? (1 point)
Designing the architecture first is important so future developers can use the architecture as a reference.
Designing the architecture first makes time use analysis for the product easier.
Architecture design beforehand is essential because it encapsulates the complete cost analysis before launch.
Having a designed architecture ensures things are planned well and allows for evaluation of and changes to the project before deployment.
Answers
The reason why it is essential to design an architecture before implementing the software is option d: Having a designed architecture ensures things are planned well and allows for evaluation of and changes to the project before deployment.
What is the importance of architectural design in software design?Architecture is known to be one that acts as the framework or the blueprint for any kind of system.
Note that it is one that tends to provide a form of an abstraction that can be used to handle the system complexity as well as set up some communication and coordination methods among parts.
Therefore, based on the above, one can say that The reason why it is essential to design an architecture before implementing the software is option d: Having a designed architecture ensures things are planned well and allows for evaluation of and changes to the project before deployment.
Learn more about architecture from
https://brainly.com/question/9760486
#SPJ1
Which three steps might be included in an algorithm for a digital thermostat?
✓ A. The thermostat uses the resistance detected to calculate the
temperature.
B. The thermostat sends an electrical signal to either the air
conditioner or the heater.
C. The thermostat measures electrical resistance with its thermistor.
O D. The thermostat automatically installs itself by wiring itself to the
house's electrical system.
Answers
Answer:
Explanation:
It certainly isn't D. It would cost a fortune to make that happen. It's not impossibe. Just impractical.
It's not A. Resistance is a floating physical thing present in the air.
B could be correct, but there is a better answer.
The answer is C. A thermistor is a resistance that is temperature sensitive.
Who developed and released the first Linux operating system? group of answer choices a) Andrew S Tannenbaum b) Richard Stallman c) Linus Torvalds d) Bill Gates
Answers
Answer:
c. ) Linus Torvalds
Explanation:
Linus Torvalds is the creator of the first Linux operating system. He developed and released the first Linux operating system.
Linus Torvalds was born on December 28, 1969, in Finland. The first version of the Linux operating system was released on the Internet in September 1991. It consisted of 88 files, totaling 231 kilobytes of code.
Linux is an open-source operating system. An operating system is software that manages a system's hardware and resources. The Operating System sits between applications and hardware and makes the connections between all software and the physical resources that do the work.
Learn more about the Linux operating system at:
brainly.com/question/12853667
#SPJ4
which of the following file names would comply with a Windows operating system? .Budget2014 Budget_Proposal? Budget_Proposal_2014 Budget_Proposal/2014
Answers
Answer:
A and C
Explanation:
Based on my computers saving process, A and C both worked while B and D didn't. I tried all four names on a PowerPoint Presentation and only A and C saved.
This is assuming I read your options correctly, I tried the following
.Budget2014
Budget_Proposal?
Budget_Proposal_2014
Budget_Proposal/2014
i need help how do i fix this????
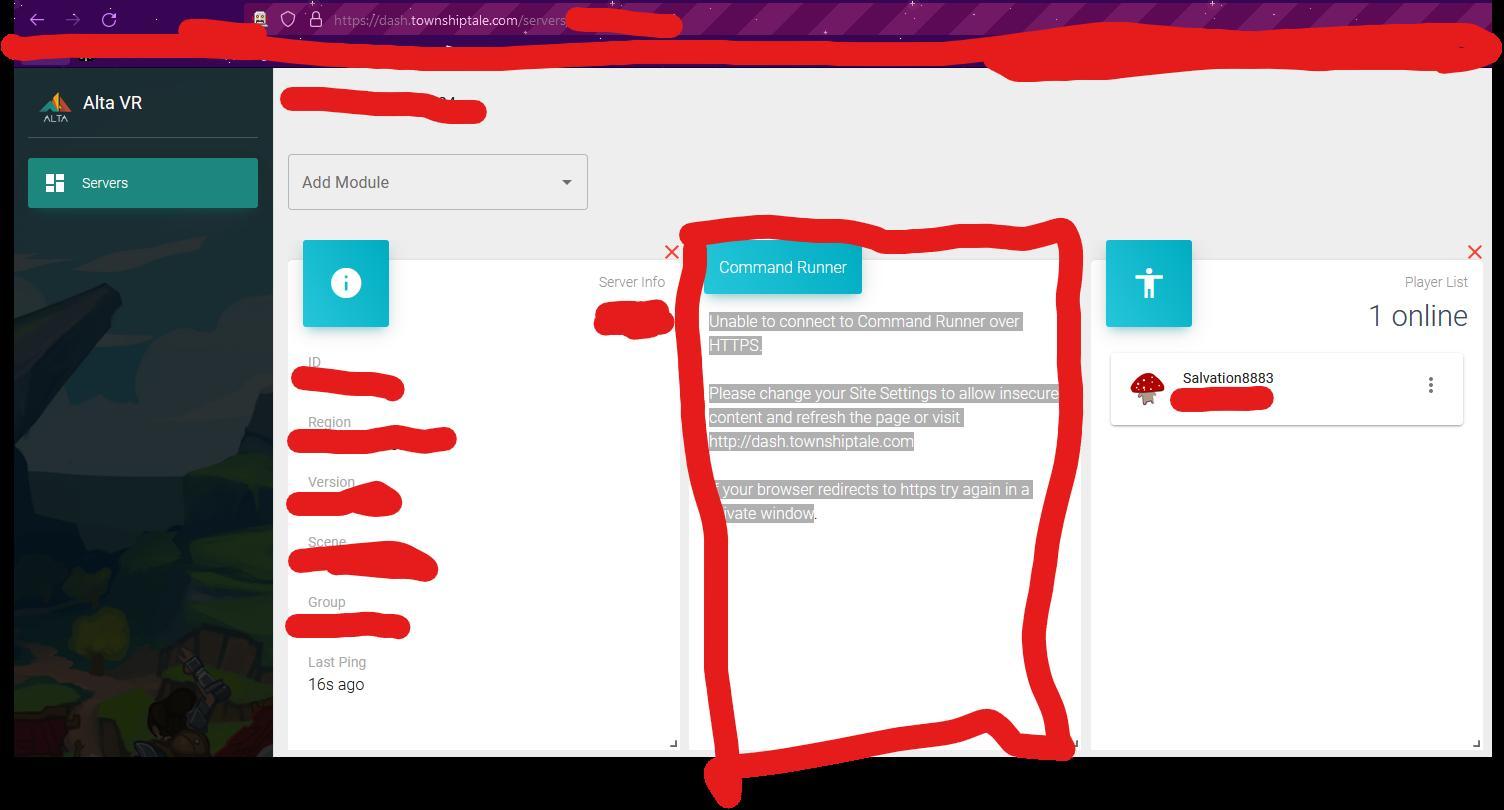
Answers
The error suggests enabling insecure content in the site settings or accessing the URL in a private window. Refreshing the page may also help.
What is a private window?A private window, also known as incognito mode, is a browsing mode that does not save any browsing history, cookies, or site data.
It is important to avoid insecure sites because they can be vulnerable to cyberattacks and put your personal information at risk. Insecure sites do not have a secure connection, which means that the data you enter on these sites, such as passwords or credit card information, can be intercepted by hackers. Browsing in a private window can help protect your online privacy and prevent your personal information from being exposed.
Also, using a trusted antivirus and firewall software can also help to protect against cyber threats.
Learn more about browsers at:
https://brainly.com/question/28504444
#SPJ1
Write a program that asks the user to enter a city name, and then prints Oh! CITY is a cool spot. Your program should repeat these steps until the user inputs Nope.
Sample Run:
Please enter a city name: (Nope to end) San Antonio
Oh! San Antonio is a cool spot.
Please enter a city name: (Nope to end) Los Angeles
Oh! Los Angeles is a cool spot.
Please enter a city name: (Nope to end) Portland
Oh! Portland is a cool spot.
Please enter a city name: (Nope to end) Miami
Oh! Miami is a cool spot.
Please enter a city name: (Nope to end) Nope
Answers
user_name = input("Please enter city name to run the program: ")
while( user_name != "Nope" ):
print("Nice to meet you ", user_name )
user_name = input("Please enter a name or type Nope to terminate the program: ")
I hope this helps!
Creating the model of a character is one of the first things a 3D artist will do.
True or false
Answers
Answer:
false
Explanation:
the character must first be drawn and designed
Answer:
True
Explanation:
I had this same question in my work, and after submitting it, I saw that the answer was true. I hope this was of good use to someone who had this question. Bye bye now :)))
Amazon.com purchases flat screen computer monitors from HP for $275.59 and sells them for $449.99. What is the amount of markup?
Answers
Answer: 82%
Explanation:
$ 449.99- $ 275.59= % 224.40
$ 224.40/ $ 275.59*100= 81.4253057078
explain three ways by which we can obtain data
Answers
Answer:
Here are some of the most common types of data collection used today.
Surveys. ...
Online Tracking. ...
Transactional Data Tracking. ...
Online Marketing Analytics. ...
Social Media Monitoring. ...
Collecting Subscription and Registration Data. ...
In-Store Traffic Monitoring.
Explanation:
what is the computational complexity of the recursive factorial method?
Answers
The recursive factorial method has a computational complexity of O(n), which means that it grows linearly with the size of the input. This is because each recursive call of the factorial function multiplies the current value by one less than the current value until it reaches 1
so it takes n multiplications to compute the factorial of n. In other words, the number of operations required to compute the factorial of n using the recursive method is proportional to n. This makes the recursive method less efficient than the iterative method for computing factorials, which has a computational complexity of O(1) because it only requires a fixed number of operations (n multiplications) regardless of the input size. However, the recursive method is often more intuitive and easier to understand, especially for small inputs.
To know more about computational visit:
https://brainly.com/question/31064105
#SPJ11
How do you check to see if the user entered more than one character? Complete the code.
letter = input("Enter a letter: ")
if _____ > 1:
print("\nPlease guess a single letter.\n")
letter.len()
length(letter)
letter.length()
len(letter)
Answers
Answer:
1len(letter)
Explanation:
JUST GOT IT RIGHT
The code is letter = input("Enter a letter: ") if len(letter) > 1:print("\nPlease guess a single letter.\n")
What is code?There are four kinds of coding:
Data compression (or source coding)Error control (or channel coding)Cryptographic coding.Line coding.The description of a code is a set of rules or a method of communication, often with erratically assigned numbers and letters given specific definitions.
An illustration of code is the state's vehicle laws. An example of code is a made-up vocabulary that two children use to articulate to each other.The total numeral of computer languages to exist is approximately 9,000, though there are 50 that are the most famous programming languages in use today.To learn more about code, refer to:
https://brainly.com/question/25605883
#SPJ2
Multiple
Choice
What will be the output?
class num:
def __init__(self,a):
self. number = a
def_mul__(self, b)
return self.number + b.number
numA = num(5)
numB = num(10)
product = numA * numb
print(product)
50
O 5
an error statement
15

Answers
Answer:
15
Explanation:
Edge 2021

lsa package is not signed as expected. this can cause unexpected behavior with credential guard.
Answers
The LSA provides heterogeneous credential management to connect to networks and databases that are not made by Microsoft.
What distinguishes credential guard from LSA protection?Only trustworthy, privileged programs and processes are permitted access to user secrets or credentials when Credential Guard is enabled. Windows keeps credentials in the Local Security Authority (LSA), a process running in memory, when Credential Guard is not activated.
Credential Guard: Does it safeguard LSA secrets?The operating system's LSA process communicates with a new component known as the isolated LSA process that stores and safeguards those secrets when Windows Defender Credential Guard is enabled.
Credential Guard: Is it required?At this time, it is not advised to enable Windows Defender Credential Guard on domain controllers. On domain controllers, Windows Defender Credential Guard can interfere with the compatibility of some applications without adding any additional protection.
To know more about credential guard visit:
https://brainly.com/question/28902859
#SPJ4
power steering belts should be checked for all of the following EXCEPT
Answers
You did not list the options.
(in c++):
Output "Valid" if input's length is less than or equal to 7. Otherwise, output "Invalid".
Ex: If input is test123, output:
Valid
Recall string's length() returns the length of the string. Ex: myString.length()

Answers
The program is an illustration of string manipulations
What are string manipulations?String manipulations include calculating the lengths of strings and also performing several operations on the string
The actual programThe complete program in C++ is as follows:
#include <iostream>
using namespace std;
int main(){
string passwordStr;
cin>>passwordStr;
if(passwordStr.length() <= 7){
cout<<"Valid";
}
else{
cout<<"Invalid";
}
return 0;
}
Read more string manipulation at:
https://brainly.com/question/14284563
what is database management?
Answers
Answer:
Database management is the process of organizing, storing, retrieving, and protecting data using a database management system (DBMS). The DBMS is a software application that enables users to interact with the database and manage data efficiently.
Database management involves designing the database schema, creating tables and fields, defining relationships between tables, and ensuring data integrity by enforcing constraints and validation rules. It also involves querying the database using SQL or other programming languages, updating or deleting data, and creating reports or visualizations of data.
3.
(gnicnahnE nife eengin stenmpoleved). The
fingernails upgrade your capacity to scratch and isolated, for example, pages in a book or hairs
on your head. An individual can likewise go through their fingernails to nini
Answers
The minerals having hardness of 3 or lower and can be scratched by a fingernail are:
Gypsum. Scratched by fingernail
Calcite. Very easily scratched by nail
Fluorite. Easily scratched by nail. ...
Feldspars. ...
Quartz.
Mineral is "a naturally occurring inorganic element or compound having an.
Orderly internal structure and characteristic chemical composition, crystal form, and physical. properties."
Minerals differ from rocks, which are naturally occurring solids composed of one or more minerals.
Minerals are important for your body to stay healthy.
Your body uses minerals for many different jobs, including keeping your bones, muscles, heart, and brain working properly. Minerals are also important for making enzymes and hormones. There are two kinds of minerals: macro-minerals and trace minerals.
Learn more about minerals here:
brainly.com/question/1202700
#SPJ4
Please help with task!!! Computer Science

Answers
Answer:
for (int i = 0; i < a[].length; i++) {
for (int j = 0; j < a[][].length; j++) {
if (a[i][j] > 7)
return a[i][j];
}
}
Explanation:
A nested for-loop can iterate through every row and column and then perform the comparison, returning it if the condition is met.
__________________ is a technique can be beneficial when driving next to parked vehicles or approaching signal lights or intersections.
Covering the brake
Using your handbrake
Slipping the clutch
Drifting
Answers
Answer:
Covering the brakeis a technique can be beneficial when driving next to parked vehicles or approaching signal lights or intersections
Covering the brakes is a beneficial driving technique for driving next to parked vehicles o while approaching the signal lights.
What is driving technique?The appropriate and standard ways keeping the legal functions in mind while driving a vehicle is known as an ethical driving technique.
While driving, when a parked vehicle is in the way or at the time of approaching the signals or intersections on the roads, it is the best advisable to cover the brakes of the vehicles.
Hence, option A holds true regarding the driving technique.
Learn more about driving technique here:
https://brainly.com/question/9854106
#SPJ2
Henry has created a software product that manages a database of company clients. He wants to install the software on a client's computer, which has an operating system that does not support the software. What can Henry do to run the software on the client's computer?
Answers
Answer:
The answer is " Run the software on the original web browser practically".
Explanation:
The Virtual servers enable you to run programming not programmed to the devices. Let's all presume which Henry's software will operate on computers but not on the mac. Since Mac is unable to run this software, it can practically install Linux on MC and install this.
The several common software applications such as parallels, VMware, and Virtual machines could be practically used during mac to install windows. Its platform operating system from a macOS software perspective is a true physical computer with almost everything set.Where is a Pivot Table inserted?
a. Next to the last column of data in your worksheet
b. Below the last row of data in your worksheet
c. It depends on whether you select to insert the Pivot Table in the current worksheet or a new worksheet
d. Above the first row of data in your worksheet
Answers
The Create PivotTable dialog box will prompt you to create a Pivot Table on an Existing Worksheet if you insert one on a data-filled worksheet. One of the options in the Create PivotTable dialog box is this one.
Utilized in spreadsheet applications like Excel, OpenOffice.org Calc, and Ggle Sheets is a data summarization tool called a pivot table. Sorting, counting, and totaling data in a table are its primary uses. In order to create a report, you can summarize the data in a variety of ways using a pivot table.
The dialog box for "Create PivotTable":
In Excel, a new pivot table can be created using the dialog box labeled "Create PivotTable."
Learn more about PivotTable at
brainly.com/question/18410166
#SPJ4
A company notices their software is prone to buffer overflow attacks. They choose a popular development environment, Microsoft Visual Studio, to help avoid future attacks. What development environment feature would most help the company avoid future buffer overflows
Answers
Answer:
Compiler Option
Explanation: These help prevent buffer overflow attacks
Jenny is working on a laptop computer and has noticed that the computer is not running very fast. She looks and realizes that the laptop supports 8 GB of RAM and that the computer is only running 4 GB of RAM. Jenny would like to add 4 more GB of RAM. She opens the computer and finds that there is an open slot for RAM. She checks the other module and determines that the module has 204 pins. What module should Jenny order? a. SO-DIMM DDR b. SO-DIMM DDR 2 c. SO-DIMM DDR 3 d. SO-DIMM DDR 4
A friend has asked you to help him find out if his computer is capable of overclocking. How can you direct him? Select all that apply.
a. Show him how to find System Summary data in the System Information utility in Windows and then do online research.
b. Show him how to access BIOS/UEFI setup and browse through the screens.
c. Explain to your friend that overclocking is not a recommended best practice.
d. Show him how to open the computer case, read the brand and model of his motherboard, and then do online research.
Answers
Answer:
1. She Should Order C. SO-DIMM DDR 3
2. a. Show him how to find System Summary data in the System Information utility in Windows and then do online research.
Explanation:
Jenny should order a SO-DIMM DDR3 module.
To determine overclocking capability, access BIOS/UEFI setup and research or check system information.
What is the explantion of the above?For Jenny's situation -
Jenny should order a SO-DIMM DDR3 module since she mentioned that the laptop supports 8 GB of RAM and the computer is currently running 4 GB of RAM. DDR3 is the most likely type that would be compatible with a laptop supporting 8 GB of RAM.
For the friend's situation -
To help the friend determine if his computer is capable of overclocking, the following options can be suggested -
a. Show him how to find System Summary data in the System Information utility in Windows and then do online research.
b. Show him how to access BIOS/UEFI setup and browse through the screens.
c. Explain to your friend that overclocking is not a recommended best practice.
Option d is not necessary for determining overclocking capability, as the brand and model of the motherboard alone may not provide sufficient information.
Learn more about BIOS at:
https://brainly.com/question/1604274
#SPJ6
Fill in the blank: A keyword set to _____ match type will display your ad if the search term contains the same order of the words, but it can also contain additional words.
Answers
A keyword set to broad match type will display your ad if the search term contains the same order of the words.
Definition of Broad MatchBroad match is a keyword match type used by search engines to help ads determine variable terms that are eligible to match their keyword by providing a wide range of keyword searches which has relation or similarities to a particular keyword.
Broad match generally help campaigns by ads to improve the performance to a great extent.
Other types of keyword match types available to users are:
modified broad match phrase matchexact matchnegative match.See related answer where broad match is applied: https://brainly.com/question/15849818
which is the following career pathway for human services
Answers
The career pathway for human services includes:
Consumer servicesCounseling and mental health services, etc.What are career pathways?This is known to be the likely career choices that one can make based on a specific field.
Note that the career pathways within the human services cluster are:
Consumer services.Counseling and mental health services.Early childhood development and services.Family and community services.Personal care services.Learn more about career pathway from
https://brainly.com/question/9719007
#SPJ1
Justify the following statement: " Diversity should exist in the workplace."
Answers
Answer:
Explanation:
Diversity should exist in the workplace because if everyone working together had the exact same views, there wouldn't be any growth and learning of new ways to expand ideas.Answer:
Diversity should exist in the workplace because if everyone working together had the exact same views, there wouldn't be any growth and learning of new ways to expand ideas.
Explanation:
e d g e
how much mutable intelligibility does there have to be before a language is considered different quora
Answers
The concept of mutual intelligibility refers to the ability of speakers of one language to understand and communicate with speakers of another language without prior knowledge or learning.
When considering whether languages are different or not, linguists often look at the level of mutual intelligibility between them. A higher degree of mutual intelligibility means that the languages are more similar, while a lower degree indicates that they are more distinct. There is no specific threshold of mutual intelligibility that determines when a language is considered different. Instead, it depends on various factors such as phonology, vocabulary, and grammar.
In summary, the classification of languages as different or not depends on the degree of mutual intelligibility between them. There is no fixed percentage or benchmark for determining this, as it varies depending on multiple linguistic factors.
To learn more about mutual intelligibility, visit:
https://brainly.com/question/28489482
#SPJ11