computers usually remember the ip addresses of the websites that they've already visited. if this is the case, why do we need dns servers?
Answers
While computers do have the ability to remember IP addresses of websites they have visited, DNS servers play a crucial role such as
Human-Friendly NamesDynamic IP AddressesWhat is the ip addressesComputers remember IP addresses, but DNS servers provide human-friendly domain names. Users can use a domain name instead of an IP address (e.g. www.example.com instead of 192.168.0.1). DNS translates domain names to IP addresses.
Dynamic IP addresses change over time for websites and servers. DNS servers map domain names to IP addresses, ensuring access to websites despite IP changes. No DNS means knowing the new IP address every time it changes.
Learn more about ip addresses from
https://brainly.com/question/14219853
#SPJ1
Related Questions
The contents of a data file are as shown.
dog, 30, 6
dog, 45, 2
cat, 12, 3
22, cat, 15
This data is
O abstract
O incorrect
O structured
O unstructured
Answers
The contents of a data file is Unstructured data.
What are data file?This is known to be a computer file that is said to store data that are often used by a computer application or system. They are made up of input and output data.
Conclusively, The Unstructured data is said to be a collection of different kinds of data that are said to not be stored organized or a well-defined form.
Learn more about data file from
https://brainly.com/question/26125959
How many times will it tack when you fill 1 - liter of jar with water from the pond and uses 100 - milliliter cup to scoop water out of the pond and pour it into the jar
Answers
Answer:
10 times
Explanation:
Volume of a jar = 1 liter
Use 1 liter = 1000 milliliters to convert unit of volume of a jar to milliliter.
Therefore,
Volume of a jar = 1000 milliliters
Volume of cup = 100 milliliter
A 100 - milliliter cup is used to scoop water out of the pond and pour it into the 1 - liter of jar.
Number of times = \(\frac{1000}{100}=10\) times
If F=ma
m = 20
a = 5
What is the force?
a- 15
b- 25
c- 100
d- 4
Answers
Answer: C-100
Explanation:
m=20
a=5
20 x 5=100
List 4 differences between qualitative and quantitative data.
Answers
Answer:
Quantitative data is information about quantities, and therefore numbers, and qualitative data is descriptive, and regards phenomenon which can be observed but not measured, such as language.
Explanation:
Quantitative research is expressed in numbers and graphs. It is used to test or confirm theories and assumptions. This type of research can be used to establish generalizable facts about a topic.
Common quantitative methods include experiments, observations recorded as numbers, and surveys with closed-ended questions.
Qualitative research is expressed in words. It is used to understand concepts, thoughts or experiences. This type of research enables you to gather in-depth insights on topics that are not well understood.
Common qualitative methods include interviews with open-ended questions, observations described in words, and literature reviews that explore concepts and theories.
Suppose method1 is declared as
void method1 ( int a, float b )
Which of the following methods overloads method1?
Group of answer choices
void method2 ( int a, float b ).
void method2 ( float a, int b ).
void method1 ( float a, int b ).
void method1 ( int b, float a ).
Answers
Suppose method1 is declared as void method1 ( int a, float b ) to overload method1 using option C: void method1(float a, int b).
When two or more functions have the same name but differ in parameters, it's called function overloading. In this case, the method1 function is declared as void method1(int a, float b), so the only function that overloads it must have a different parameter list.
Option A, void method2(int a, float b), has the same parameter list as method1, so it does not overload it.
Option B, void method2(float a, int b), also has a different parameter list, but it has a different function name, so it doesn't overload method1 either.
Option D, void method1(int b, float a), has the same parameter types as method1, but the order of the parameters is different. However, the order of parameters does not affect the overloading, so it does not overload method1.
Therefore, only option C, void method1(float a, int b), overloads method1 because it has a different parameter list. When the compiler resolves which version of an overloaded function to call, it matches the argument types to the parameter types of each version and selects the most appropriate one.
To get a similar answer on overloads visit:
https://brainly.com/question/13566906
#SPJ11
What type of figurative language appears in the text?
Why does the author use figurative language rather than literal language?
How does the figurative language support the writer’s purpose?
How does figurative language help me to understand better the connotative and denotative meanings of unknown or difficult words and phrases?
What is the denotation, or literal meaning of this example of figurative language?
What is its connotation, or implied ideas and emotions?
How does figurative language help to create the mood, or the emotional atmosphere, of the text?
ASSIGNMENT
Think of your favorite book and answer the questions above as it pertains to the figurative language used in the book.
Answers
Answer:
In my favorite book, The Catcher in the Rye by J.D. Salinger, there are several examples of figurative language. For example, the protagonist Holden Caulfield often uses metaphors to convey feelings of alienation and loneliness, such as when he says "I felt like I was disappearing". He also uses similes to create vivid imagery, such as when he says "it was like I was surrounded by millions of little needles". He also makes use of alliteration to emphasize his points, such as when he says "it was that crazy kind of a laugh".
The author uses figurative language to create a more vivid and engaging narrative, as well as to emphasize certain themes, such as loneliness and alienation. It also helps to evoke specific emotions in the reader, such as sadness or empathy.
The denotation of the figurative language used in the book is the literal meaning of the words, such as when Holden Caulfield says "I felt like I was disappearing", which literally means he felt as if he was becoming invisible. The connotation of this phrase is that he feels isolated and alone, which is what the author is trying to convey.
Figurative language helps to create the mood or emotional atmosphere of a text by evoking certain feelings in the reader. In The Catcher in the Rye, Holden's use of figurative language helps to convey feelings of loneliness, alienation, and despair, which creates a melancholic and somber tone throughout the book.
List out the wrap to options.
Answers
It appears that you are requesting to know the Wrap Text Options in Microsoft word. Note that the options are indicated and explained below.
In Line with TextSquareTightThroughTop and BottomBehind TextIn Front of TextWhat are the Wrap Text options in Microsoft Word?In Microsoft Word, there are several options for wrapping text around an object or graphic. The wrap text options are as follows:
In Line with Text: This option inserts the object in the line of text, making the text wrap around the object.
Square: This option creates a square-shaped border around the object and wraps the text around the sides of the square.
Tight: This option wraps the text tightly around the contours of the object.
Through: This option allows the text to wrap around the object and appear in front of or behind the object as well.
Top and Bottom: This option creates a rectangular border around the object and wraps the text around the top and bottom edges of the rectangle.
Behind Text: This option places the object behind the text, with the text in front of the object and no wrapping.
In Front of Text: This option places the object in front of the text, with the text behind the object and no wrapping.
These options can be accessed by selecting an object or graphic in Microsoft Word and clicking on the "Wrap Text" button in the "Format" tab of the ribbon menu.
Learn more about Wrap Text Options:
https://brainly.com/question/30160011
#SPJ1
Full Question:
List out the Wrap Text Options in Microsoft Word
Suppose a computer using direct mapped cache has 232 byte of byte-addressable main memory, and a cache of 1024 blocks, where each cache block contains 32 bytes. How many blocks of main memory are there?
Answers
In direct mapped cache, each block of main memory can only be stored in one specific cache block. This means that if we have a 1024 block cache, we can only store 1024 blocks of main memory at any given time.
(2^32 bytes) / (32 bytes/block) = 134,217,728 blocksThis means that there are 134,217,728 blocks of main memory, but we can only store 1024 of them in the cache at any given time. This highlights the trade-off between the size of the cache and the size of the main memory - a larger cache can improve performance by storing more frequently accessed data, but it also comes at the cost of being able to store less of the overall memory.
For such more questions on block
https://brainly.com/question/14065401
#SPJ11
11.1.2 Ball and Paddle Code HS JavaScript
Overview
Add the ball and paddle. The ball should bounce around the screen. The paddle should move with the mouse.
Add Ball and Paddle
The first step is to add the ball to the center of the screen, and the paddle to the bottom of the screen. The dimensions of the paddle and its offset from the bottom of the screen are already constants in the starter code.
The next step is to get the paddle to move when you move the mouse. The paddle should be centered under the mouse, and should not go offscreen.
Move Paddle, Bounce Ball
The next step is to get the ball to bounce around the screen. We may have done this exact problem before…
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that Add the ball and paddle. The ball should bounce around the screen. The paddle should move with the mouse.
Writting the code:function setupBall(){
ball = new Circle(BALL_RADIUS);
ball.setPosition(getWidth()/2, getHeight()/2);
add(ball);
}
function setupPaddle(){
paddle = new Rectangle(PADDLE_WIDTH, PADDLE_HEIGHT);
paddle.setPosition(getWidth()/2 - paddle.getWidth()/2,
getHeight() - paddle.getHeight() - PADDLE_OFFSET);
add(paddle);
}
function getColorForRow(rowNum){
rowNum = rowNum % 8;
if(rowNum <= 1){
return Color.red;
}else if(rowNum > 1 && rowNum <= 3){
return Color.orange;
}else if(rowNum > 3 && rowNum <= 5){
return Color.green;
}else{
return Color.blue;
}
}
function drawBrick(x, y, color){
var brick = new Rectangle(BRICK_WIDTH, BRICK_HEIGHT);
brick.setPosition(x, y);
brick.setColor(color);
add(brick);
}
function drawRow(rowNum, yPos){
var xPos = BRICK_SPACING;
for(var i = 0; i < NUM_BRICKS_PER_ROW; i++){
drawBrick(xPos, yPos, getColorForRow(rowNum));
xPos += BRICK_WIDTH + BRICK_SPACING;
}
}
function drawBricks(){
var yPos = BRICK_TOP_OFFSET;
for(var i = 0; i < NUM_ROWS; i++){
drawRow(i, yPos);
yPos += BRICK_HEIGHT + BRICK_SPACING;
}
}
function setSpeeds(){
vx = Randomizer.nextInt(2, 7);
if(Randomizer.nextBoolean())
vx = -vx;
}
function setup(){
drawBricks();
setupPaddle();
setupBall();
setSpeeds();
}
See more about JAVA at brainly.com/question/18502436
#SPJ1

if two or more users are trying to update the database and the dbms is not releasing the locks to allow either user to continue, this is known as a(n) .
Answers
A deadlock occurs when two or more users are trying to update the database and the DBMS is not releasing the locks to allow either user to continue.
The dangers of deadlocks in a databaseA deadlock can cause major problems for a database, as it can prevent users from being able to access or update data. In some cases, a deadlock can even cause the database to crash.
This can happen if the users are trying to update the same data, or if they are trying to update different data but are using the same resources (such as locks).
Learn more about database at: https://brainly.com/question/17635431
#SPJ4
Assembly Program
⦁ Store the two 8 bit numbers in registers
⦁ compare them both
⦁ check if the value in the first register is greater than the other
⦁ if true print their sum
⦁ else subtract them
Answers
This program first stores two 8-bit numbers (42 and 23) in registers A and B, respectively. It then compares the values in registers A and B using the CMP instruction.
If A is greater than or equal to B, it jumps to the ADD label, where it adds the values in registers A and B, stores the result in register C, and calls the PRINT_SUM subroutine to print the sum to the console. If A is less than B, it subtracts the value in register B from the value in register A, stores the result in register C, and calls the PRINT_DIFF subroutine to print the difference to the console.
The PRINT_NUM subroutine is used to convert the sum or difference in register C to ASCII code and output it to the console. It uses the DIV instruction to divide the number in register A by 10, which stores the quotient in A and the remainder in B. It then converts the remainder and quotient to ASCII code by adding 48 to their values (since the ASCII code for '0' is 48) and outputs them to the console using the 0EH output port. Finally, it swaps the values in registers A and B so that the quotient is in A and the remainder is in B, and repeats the process to output the second digit of the number.
To know more about program visit :
https://brainly.com/question/11023419
#SPJ11
Uploading Your Work
Assignment Upload: Using PowerPoint
Active
Instructions
Click the links to open the resources below. These resources will help you complete the assignment. Once you have created your
file(s) and are ready to upload your assignment, click the Add Files button below and select each file from your desktop or network
folder. Upload each file separately.
Your work will not be submitted to your teacher until you click Submit.
Documents
Uploading Your Work Directions
Clip Art and Media Clips Student Guide
Animations and Photo Albums Student Guide
Customizing SmartArt Graphics and Tables Student Guide
Don’t know how to do this and could really use some help please!!!!!!!
Answers
Answer:
Easy all you have to do is upload one assignment at a time and follow all the other directions!
Explanation:
_Hope_this_helps! >O<
What is a way to prevent the download of viruses and other malicious code when checking your email?.
Answers
Answer:
It is not permissible to access links or hyperlinked information such as buttons and images in email messages.
Explanation:
MyProgramming Lab
It needs to be as simple as possible. Each question is slightly different.
1. Given the lists list1 and list2, not necessarily of the same length, create a new list consisting of alternating elements of list1 and list2 (that is, the first element of list1 followed by the first element of list2 , followed by the second element of list1, followed by the second element of list2, and so on. Once the end of either list is reached, the remaining elements of the longer list is added to the end of the new list. For example, if list1 contained [1, 2, 3] and list2 contained [4, 5, 6, 7, 8], then the new list should contain [1, 4, 2, 5, 3, 6, 7, 8]. Associate the new list with the variable list3.
2. Given the lists list1 and list2 that are of the same length, create a new list consisting of the last element of list1 followed by the last element of list2, followed by the second to last element of list1, followed by the second to last element of list2, and so on (in other words the new list should consist of alternating elements of the reverse of list1 and list2). For example, if list1 contained [1, 2, 3] and list2 contained [4, 5, 6], then the new list should contain [3, 6, 2, 5, 1, 4]. Associate the new list with the variable list3.
3. Given the lists list1 and list2, not necessarily of the same length, create a new list consisting of alternating elements of list1 and list2 (that is, the first element of list1 followed by the first element of list2, followed by the second element of list1, followed by the second element of list2, and so on. Once the end of either list is reached, no additional elements are added. For example, if list1 contained [1, 2, 3] and list2 contained [4, 5, 6, 7, 8], then the new list should contain [1, 4, 2, 5, 3, 6]. Associate the new list with the variable list3.
Answers
Answer:
Explanation:
The following code is written in Python. It creates a method for each one of the questions asked and then tests all three with the same test case which can be seen in the picture attached below.
def alternating_list(lst1, lst2):
lst3 = []
for x in range(len(lst1)):
lst3.append(lst1[x])
try:
lst3.append(lst2[x])
except:
pass
if len(lst2) > len(lst1):
lst3.extend(lst2[len(lst1):])
return lst3
def reverse_alternating(lst1, lst2):
lst3 = []
if len(lst1) == len(lst2):
for x in range(len(lst1) - 1, -1, -1):
lst3.append(lst1[x])
lst3.append(lst2[x])
return lst3
def alternating_list_no_extra(lst1, lst2):
lst3 = []
max = 0
if len(lst1) > len(lst2):
max = len(lst2)
else:
max = len(lst1)
for x in range(max):
lst3.append(lst1[x])
try:
lst3.append(lst2[x])
except:
pass
return lst3

describe your programming experience, including specific languages and platforms used, and number of years of experience working with each of them.
Answers
The correct answer is Your knowledge of software development and how you have used it in practical settings are referred to as your "programming experience." It includes the.
To be able to generate code and test it quickly, you'll need at least 16GB of RAM and a multi-core processor to begin with. The project duration will be shorter as a result of your ability to execute and test code more quickly, allowing you to take on more work. Additionally, the quality of the keyboard is crucial. The underlying systems that run the devices or manage networks are created by software developers, as are the computer apps that let users perform particular activities. Analysts and testers for software quality assurance create and carry out software tests to find issues and understand how the product functions.
To learn more about software development click on the link below:
brainly.com/question/3188992
#SPJ4
Distinguish between the physical and logical views of data.
Describe how data is organized: characters, fields, records,
tables, and databases. Define key fields and how they are used to
integrate dat
Answers
Physical View vs. Logical View of Data: The physical view of data refers to how data is stored and organized at the physical level, such as the arrangement of data on disk or in memory.
It deals with the actual implementation and storage details. In contrast, the logical view of data focuses on how users perceive and interact with the data, regardless of its physical representation. It describes the conceptual organization and relationships between data elements.
In the physical view, data is stored in binary format using bits and bytes, organized into data blocks or pages on storage devices. It involves considerations like file structures, storage allocation, and access methods. Physical view optimizations aim to enhance data storage efficiency and performance.
On the other hand, the logical view represents data from the user's perspective. It involves defining data structures and relationships using models like the entity-relationship (ER) model or relational model. The logical view focuses on concepts such as tables, attributes, relationships, and constraints, enabling users to query and manipulate data without concerning themselves with the underlying physical storage details.
Data Organization: Characters, Fields, Records, Tables, and Databases:
Data is organized hierarchically into characters, fields, records, tables, and databases.
Characters: Characters are the basic building blocks of data and represent individual symbols, such as letters, numbers, or special characters. They are combined to form meaningful units of information.
Fields: Fields are logical units that group related characters together. They represent a single attribute or characteristic of an entity. For example, in a customer database, a field may represent the customer's name, age, or address.
Records: A record is a collection of related fields that represent a complete set of information about a specific entity or object. It represents a single instance or occurrence of an entity. For instance, a customer record may contain fields for name, address, phone number, and email.
Tables: Tables organize related records into a two-dimensional structure consisting of rows and columns. Each row represents a unique record, and each column represents a specific attribute or field. Tables provide a structured way to store and manage data, following a predefined schema or data model.
Databases: Databases are a collection of interrelated tables that are organized and managed as a single unit. They serve as repositories for storing and retrieving large volumes of data. Databases provide mechanisms for data integrity, security, and efficient data access through query languages like SQL (Structured Query Language).
Key Fields and their Role in Data Integration:
Key fields are specific fields within a table that uniquely identify each record. They play a crucial role in integrating data across multiple tables or databases. A key field ensures data consistency and enables the establishment of relationships between tables. There are different types of key fields:
Primary Key: A primary key is a unique identifier for a record within a table. It ensures the uniqueness and integrity of each record. The primary key serves as the main reference for accessing and manipulating data within a table.
Foreign Key: A foreign key is a field in a table that refers to the primary key of another table. It establishes a relationship between two tables by linking related records. Foreign keys enable data integration by allowing data to be shared and referenced across different tables.
By utilizing primary and foreign keys, data from multiple tables can be integrated based on common relationships. This integration allows for complex queries, data analysis, and retrieval of meaningful insights from interconnected data sources.
Learn more about memory here
https://brainly.com/question/28483224
#SPJ11
Describing Label Printing Options
What are some options when printing labels? Check all that apply.
random addresses
single label
handwritten label
full page of same label
Answers
Custom labels are printed using a variety of techniques in the label printing process. Some options when printing labels are Single label and Full page of same label.
What Is Label Printing?
Label printing is the process of creating personalized labels using different techniques. These techniques include wide-format printing, flexographic printing, and digital printing, all of which have an impact on how the label looks, feels, and serves its purpose.
Label Printing Today:
Flexographic printing has continued to advance and prosper up until the 1990s, when digital printing emerged as a brand-new method for producing labels. With the addition of inkjet technology, this process has advanced today, producing premium, full-color labels with a less time-consuming procedure and less waste.
To know more about Label Printing, visit: https://brainly.com/question/4676056
#SPJ9
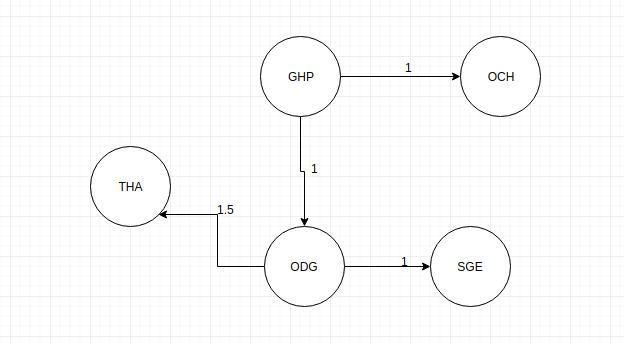
use prim's algorithm to find a minimal spanning tree for the times whose vertices are the hotels given in the distance chart. what is the total time for this spanning tree?
Answers
The greedy approach is the foundation of the Prim's algorithm. We choose the edge with the least weight at each step, assuming that the final node hasn't been reached yet.
The spanning tree would appear like this. All the names are written in shorthand. Kindly corelate.
What is spanning tree?
A spanning tree is a sub-graph of an undirected connected graph that contains all of the graph's vertices and the fewest number of edges possible between them. It is not a spanning tree if a vertex is missed. Weights may or may not be applied to the edges.
What is minimum spanning tree?
A minimum spanning tree is one in which the weight of the edges added together is as small as it can be.
To know more about spanning tree, check out:
https://brainly.com/question/13148966
#SPJ1
what is a web page and a website
Answers
Answer:
:)Explanation:
┬─┬ノ( º _ ºノ) ♪ ♬ ヾ(´︶`♡)ノ ♬ ♪
Asia is selling bracelets to raise money for the school's band trip. She needs to determine how much she has already raised and how many more bracelets she must sell. Which response best explains why a computer would perform this task better than a human?
Computers can perform calculations at unbelievable speeds.
Computers can think creatively.
Computers can replicate human tasks.
Computers don't require sleep.
Answers
Note that where Asia is selling bracelets to raise money for the school's band trip and she needs to determine how much she has already raised and how many more bracelets she must sell, the response that best explains why a computer would perform this task better than a human is: "Computers can perform calculations at unbelievable speeds." (Option A)
What is the speed of the fastest computer?Frontier, the fastest supercomputer on the TOP500 supercomputer list as of May 2022, with a LINPACK benchmark score of 1.102 ExaFlop/s, followed by Fugaku. The United States has five of the top ten, China has two, and Japan, Finland, and France each have one.
As of June 2022, China had 173 of the world's 500 most advanced and powerful, one-third more than its next competitor, the United States, which had an additional 128 supercomputers.
Learn more about computing speed:
https://brainly.com/question/2072717
#SPJ1
Write a program in java to input N numbers from the user in a Single Dimensional Array .Now, display only those numbers that are palindrome
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that input N numbers from the user in a Single Dimensional Array .
Writting the code:class GFG {
// Function to reverse a number n
static int reverse(int n)
{
int d = 0, s = 0;
while (n > 0) {
d = n % 10;
s = s * 10 + d;
n = n / 10;
}
return s;
}
// Function to check if a number n is
// palindrome
static boolean isPalin(int n)
{
// If n is equal to the reverse of n
// it is a palindrome
return n == reverse(n);
}
// Function to calculate sum of all array
// elements which are palindrome
static int sumOfArray(int[] arr, int n)
{
int s = 0;
for (int i = 0; i < n; i++) {
if ((arr[i] > 10) && isPalin(arr[i])) {
// summation of all palindrome numbers
// present in array
s += arr[i];
}
}
return s;
}
// Driver Code
public static void main(String[] args)
{
int n = 6;
int[] arr = { 12, 313, 11, 44, 9, 1 };
System.out.println(sumOfArray(arr, n));
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

how to make your phone flash when you get a notification
Answers
Answer:
If your talking about it turning on then go to notifications in the settings and turn on badges. If your talking about the flashlight on ur phone not possible.
Explanation:
PLEASE HELP ME! Sam was researching rocks and minerals. He thought the Web site looked unprofessional, so he looked for the author's information or credentials. He couldn't find any. Is this site reliable? A. Probably B. Probably not.
Answers
Answer:
B
Explanation:
If a site looks unprofessional and doesn't have any credentials, those are two signs that it's probably not very reliable.
PLEASE HELP! ILL GIVE BRAINLIEST!!!!!

Answers
Based on the above scenario, Redlan is supporting his company software.
What is customer support a software?Customer support software is known to be a kind of unified channels that are often used by firms that helps a person to communicate with their customers and others.
Conclusively, Redlan is supporting his company software and he is acting in the capacity of customer support.
Learn more about support software from
https://brainly.com/question/1538272
#SPJ1
What contains programming statement written in VB?
Answers
Answer:
A statement in Visual Basic is a complete instruction. It can contain keywords, operators, variables, constants, and expressions. Each statement belongs to one of the following three categories: Declaration statements, which name a variable, constant, or procedure and can also specify a data type.
Supply Chain strategy often optimizes supply chain networks for "average" performance. Explain why this is or is not the right approach? Edit View Insert Format Tools Table 12pt Paragraph BIU AQV T²V : When locating facilities in a network, the transportation economies about the potential facility location should be considered. What does this mean with respect to where the facility is located and how the network is configured? Edit View Insert Format Tools Table 12pt Paragraph ✓ B I U AV 2V T²V ⠀
Answers
Supply Chain strategy is essential in every organization that involves the planning and management of all activities involved in sourcing, procurement, conversion, and logistics. In doing so, the goal is to optimize supply chain networks for average performance.
It is the right approach to optimize supply chain networks for "average" performance because it helps the company attain its objectives and improve its performance. It makes the planning and management of activities in sourcing, procurement, conversion, and logistics more efficient by making use of resources at an optimal level. Also, this approach allows the company to maintain the right balance between supply and demand by producing enough products to meet the customers' demands. By doing so, the company reduces costs, increases efficiency, and enhances customer satisfaction. However, sometimes, optimizing supply chain networks for "average" performance may not be the right approach. This is because customers' preferences are not average. Also, different customers have different needs. Thus, optimizing the supply chain for an average performance level may result in dissatisfied customers who may opt to seek services from the competitors. Thus, it is essential to ensure that the optimization strategy considers the customers' needs and preferences, and a balance is achieved. In conclusion, optimizing the supply chain for average performance is the right approach in most cases. However, this approach should consider the customers' needs and preferences to achieve a balance between supply and demand. Therefore, when locating facilities in a network, transportation economies about the potential facility location should be considered. This means that the facility should be located in an area that is easily accessible to transportation. Additionally, the network should be configured in such a way that the facility is linked to other facilities in the supply chain network to allow for efficient transportation.
To learn more about Supply Chain strategy, visit:
https://brainly.com/question/27670727
#SPJ11
what do you think are the importance of making presentation to show your report summary
Answers
to show all the very cool information you learned.
(Mulitple choice) in the following list of attributes in an entity what type of normalization issue would exist if attribute 3 determined attribute 4?
Table 1 -
PK - Attribute 1
Attribute 2
Attribute 3
Attribute 4
Attribute 5
Answers:
A) 1st normal form
B) 2nd normal form
C) 3rd normal form
D) Boyce Codd Normal form
Answers
If attribute 3 determines attribute 4 in the given list of attributes, it indicates a normalization issue related to functional dependencies. The specific normalization issue would be addressed in the explanation.
The type of normalization issue that would exist if attribute 3 determines attribute 4 in the given entity is related to functional dependencies. Functional dependency occurs when the value of one attribute determines the value of another attribute in the same table.
In this case, if attribute 3 determines attribute 4, it implies that the value of attribute 4 can be uniquely determined based on the value of attribute 3. This violates the principles of normalization, specifically the second normal form (2NF).
The second normal form (2NF) requires that each non-key attribute in a table is functionally dependent on the entire primary key and not on any subset of the key. If attribute 3 determines attribute 4, it means that attribute 4 is functionally dependent on a subset of the key (attribute 3), which violates the 2NF.
Therefore, the correct answer would be B) 2nd normal form, as it represents the normalization issue where attribute 3 determines attribute 4, violating the principles of the 2NF.
Learn more about second normal form here:
https://brainly.com/question/32284517
#SPJ11
Select the correct answer. Richard wants to use a technology that allows the automation of manufacturing cars in his factory. What should Richard use? A. free software B. CAM C. rapid prototyping D. prototyping E. online tools
Answers
Answer:
The answer is B. CAM
Explanation:
Just answered this and got it correct.
CAM C. rapid prototyping is the correct option for Richard wants to use a technology that allows the automation of manufacturing cars in his factory.
What is prototyping?Prototyping is an iterative process in which design teams translate abstract ideas into tangible forms, which might range from paper to digital.
To capture design concepts and test them on people, teams create prototypes of varied degrees of quality. one can modify and validate designs with prototypes.
Thus, option B is correct.
For more details about prototyping, click here
https://brainly.com/question/24231598
#SPJ1
Question 1 Which portion of the PuTTY package allows you to perform file transfers using the SCP (Secure Copy) protocol?
Answers
There are different aspect of computing. The portion of the PuTTY package that allows you to perform file transfers using the SCP (Secure Copy) protocol is pscp.exe.
The pscp.exe tool commonly called the PuTTY Secure Copy Client is known to be the only portion of the Putty package that can let you copy files to and from remote computers through the use of the SCP.
Secure Copy (SCP) is simply defined as a computer command that one can use in Linux to copy files from one computer to another on a network. PuTTY is simply known to be a free implementation of SSH (and telnet) used for computer that running Microsoft Windows.
Learn more about the PuTTY package from
https://brainly.com/question/13171394