Create a bash shell script for a number guessing game. Here are the requirements: a. Your program generates a random number between 0 and 128 and keeps asking the user to guess the number until the user guesses it correctly. b. If the user guesses a number that is lower or higher than the number to be guessed then indicate that information to the user as a ‘low guess’ or a ‘high guess’ so that the user can get to the correct guess quicker. c. The program keeps track on number of guesses taken by the user to get to the correct guess. This is user’s score. d. Your program asks user for the name and adds user’s name and the score in a file that keeps track of the scores by various users. e. At the end of the game, the program displays the top 3 scores (lowest 3 scores) along with the name of the users to conclude the game. John 4 Sam 7 Tony 10
Answers
Answer:
Here is the bash shell script:
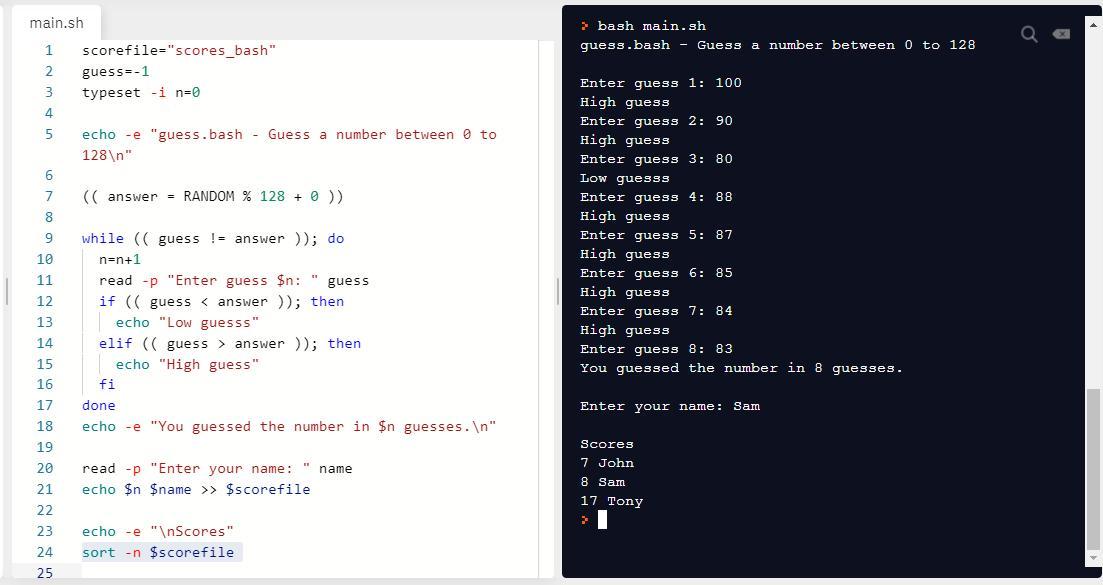
scorefile="scores_bash"
guess=-1
typeset -i n=0
echo -e "guess.bash - Guess a number between 0 to 128\n"
(( answer = RANDOM % 128 + 0 ))
while (( guess != answer )); do
n=n+1
read -p "Enter guess $n: " guess
if (( guess < answer )); then
echo "Low guesss"
elif (( guess > answer )); then
echo "High guess"
fi
done
echo -e "You guessed the number in $n guesses.\n"
read -p "Enter your name: " name
echo $n $name >> $scorefile
echo -e "\nScores"
sort -n $scorefile
Explanation:
The program creates a scorefile as scores_bash to store the names and scores. Next the program initializes the guess with -1. guess is used to store the guess made by user and n is used to store the number of trials user took to guess the correct number. Next the program prompts the user to: Guess a number between 0 to 128 and generates random numbers from 0 to 128 and store it into answer. Next the while loop keeps repeating until the user guesses the correct number. If the user guess is less than the correct answer then the program displays the message Low guess otherwise displays High guess. When the user guesses the correct number, the loop breaks and the message You guessed the number in $n guesses. is displayed where in place of $n the number of trials user take to guess the number is displayed. Next the user is asked to enter his name.
echo $n $name >> $scorefile statement adds the n which is the user score and name which is the names of user to the score file. sort -n $scorefile sorts the file in ascending order to display the lowest scores. The screenshot of program with its output is attached.
Related Questions
Which of the following is an application layer protocol? Select all that apply A) POP3 B) ARP C) SMTP D) DNS E) IPv6 F) HTTP G) TCP H) Vale 1) DHCP
Answers
An application layer protocol is a communication protocol that is used for communication between software applications on different networked computer systems. The following are application layer protocols:SMTP, HTTP, DHCP, and POP3.
SMTP (Simple Mail Transfer Protocol) is an application layer protocol that is used for sending and receiving email messages. SMTP is used to send email messages from a client email application to a mail server or from one mail server to another.
HTTP (Hypertext Transfer Protocol) is an application layer protocol that is used for accessing the World Wide Web. HTTP is used for retrieving web pages from web servers and for transmitting data from web servers to web clients.
DHCP (Dynamic Host Configuration Protocol) is an application layer protocol that is used for automatically assigning IP addresses to network devices. DHCP is used to assign IP addresses to computers, printers, and other network devices.
Therefore, the application layer protocols among the given options are SMTP, HTTP, DHCP, and POP3.
To know more about protocol visit:
https://brainly.com/question/28782148
#SPJ11
7.
"You win!" never displays. What line is responsible for this error?
1
var score
0
2
onEvent
"button2"
"click"
function
3
var score
score + 1
if
score
5
setText ("display", "You win!");
A. 1
B. 3
ОООО
C. 4
D. 5
Answers
Answer:
The answer is "4".
Explanation:
In this code, on line number 4, it will give the error message, and its correct solution can be defined as follows:
In this code, a variable "score" is declared, that holds a value that is 0, and in the next step, a method "onEvent" is declared that uses a method, and in the if block, it checks the "score" value that is less than 5 and it will print the message.
Write a python program to check whether the number is divisible by 7. If its divisible, print its divisible otherwise find previous number and the next number which is divisible by 7
Answers
f = int(input("Enter a number: "))
if(f%7==0):
print("It's divisible by 7.")
else:
if(f<7):
print("7")
else:
print(str(f-(f%7))+", "+str(f+(7-(f%7))))
quantum computing is implemented primarily with enterprise or isp servers.
Answers
Quantum computing is implemented primarily with enterprise servers.
Quantum computing is an innovative and upcoming area of computing that uses quantum-mechanical phenomena, such as superposition and entanglement, to perform computations. Quantum computers are distinct from traditional electronic computers, which rely on classical bits to encode and process data. Instead of using classical bits, quantum computers use quantum bits, or qubits, which can exist in various states at the same time.
Quantum computers may be classified into two types: analog and digital.
Digital quantum computers are more prevalent in current implementations and can be classified into two categories: gate-based and annealing.
Quantum computers, on the other hand, are not solely used by enterprises or ISPs. They are presently employed by government laboratories, research institutes, and corporations that have the resources and knowledge to use them.
To learn more about Quantum computing visit : https://brainly.com/question/15188300
#SPJ11
(100 points) analyze the provided network traffic files for a tcp connection and answer the following questions. one of the files is for the traffic with tcp cubic, and another for the traffic with tcp reno used as congestion control protocols. a. list all tcp options used by both end hosts. b. determine the minimum number of duplicate acks received before fast retransmits are triggered. c. when consecutive retransmissions are done with no other intervening packets from the same flow, what is the increase in the rto? d. what is the throughput (application data bytes/second) with each congestion control? explain why one is faster than the other.
Answers
TCP is dependable because it makes sure that every bit of data is transmitted completely and can be constructed by the receiver in the right sequence.
What is meant by Transmission Control Protocol?A network communication between applications is established and maintained according to the Transmission Control Protocol (TCP) standard. The Internet Protocol (IP), which specifies how computers send data packets to one another, works with TCP.
After the three-way handshake, TCP's connection-oriented architecture allows for two-way communication between two endpoints. TCP is dependable because it makes sure that every bit of data is transmitted completely and can be constructed by the receiver in the right sequence.
One of the key protocols in the Internet protocol family exists TCP (Transmission Control Protocol). It sits between the Application and Network Layers, which are utilized to deliver services with high reliability.
To learn more about TCP refer to:
https://brainly.com/question/17387945
#SPJ4
Omar wants to research additional information about asteroids. Complete the sentences to describe how he should use the Smart Lookup feature in PowerPoint. Step 1: He should ____________ the word asteroid. Step 2: He should navigate to the _________ tab. Step 3. He should go to the __________ command group. Step 4: He should turn on the Intelligent Services of PowerPoint in the pane. Step 5: He should click the ________ option to open links that contain information about asteroids. Please answer quickly! It is quite urgent
Answers
Answer:
Step 1: He should
✔ select
the word asteroid.
Step 2: He should navigate to the
✔ Review
tab.
Step 3. He should go to the
✔ Insights
command group.
Step 4: He should turn on the Intelligent Services of PowerPoint in the pane.
Step 5: He should click the
✔ Explore
option to open links that contain information about asteroids.
Explanation:
Edg2020
Omar should use the Smart Lookup feature in PowerPoint in several steps 1. Select, 2. Review, 3. Insights, 4. Explore.
What is the Smart Lookup feature in PowerPoint?The new Smart Lookup feature in PowerPoint 2016 for Windows is an option that shows up definitions, images, and other results from various online platforms about a word or phrase, right within PowerPoint.
There are four steps to use the Smart Lookup feature in PowerPoint:
Step 1: He should select the word asteroid.
Step 2: He should navigate to the Review tab.
Step 3. He should go to the Insights command group.
Step 4: He should turn on the Intelligent Services of PowerPoint in the pane.
Step 5: He should click the Explore option to open links that contain information about asteroids.
Therefore, he should use 1. Select, 2. Review, 3. Insights, 4. Explore.
Learn more about PowerPoint, here:
https://brainly.com/question/19238885
#SPJ2
With respect to iot security, what term is used to describe the digital and physical vulnerabilities of the iot hardware and software environment?
a. Traffic Congestion
b. Device Manipulation
c. Attack Surface
d. Environmental Monitoring
Answers
Answer: Answer Surface
Explanation:
7.2.6: First Character CodeHS
"Write a function called first_character that takes a string as a parameter and returns the first character.
Then, write another function called all_but_first_character that takes a string as a parameter and returns everything but the first character.
Test each of your functions on the string "hello" and print the results. Your output should be:"
Answers
def first_character(txt):
return txt[0]
def all_but_first_character(txt):
return txt[1::]
print(first_character("hello"))
print(all_but_first_character("hello"))
I wrote my code in python 3.8. I hope this helps.
Following are the Program to the given question:
Program Explanation:
Defining a two-method "first_character and all_but_first_character" that takes a string variable "t" into the parameter.In the first method, it returns the first character of the string.In the second method, it returns the string value except for the first character.At the last, we call both the methods.Program:
def first_character(t):#defining a method first_character that takes a string variable in parameter
return t[0]#using return keyword that return first character of string
def all_but_first_character(t):#defining a method all_but_first_character that takes a string variable in parameter
return t[1::]#using return keyword that return string except first character
print(first_character("hello"))#calling method
print(all_but_first_character("hello"))#calling method
Output:
Please find the attached file.
Learn more:
brainly.com/question/19168392

Example 1: Define a function that takes an argument. Call the function. Identify what code is the argument and what code is the parameter.
Example 2: Call your function from Example 1 three times with different kinds of arguments: a value, a variable, and an expression. Identify which kind of argument is which.
Example 3: Create a function with a local variable. Show what happens when you try to use that variable outside the function. Explain the results.
Example 4: Create a function that takes an argument. Give the function parameter a unique name. Show what happens when you try to use that parameter name outside the function. Explain the results.
Example 5: Show what happens when a variable defined outside a function has the same name as a local variable inside a function. Explain what happens to the value of each variable as the program runs
Answers
Examples of common errors when working with functions in C++ include using variables outside of their scope, naming conflicts between variables and parameters, and not properly passing arguments to functions.
What are some examples of common errors that can occur when working with functions in C++?In Example 1, the task is to define a function that takes an argument. The code that is passed into the function during the function call is the argument, and the code defined in the function header that receives the argument is the parameter.
In Example 2, the function from Example 1 is called three times with different kinds of arguments - a value, a variable, and an expression.
The argument passed as a value is a literal or constant, the argument passed as a variable is an existing variable, and the argument passed as an expression is a combination of literals, variables, and operators.
In Example 3, a function with a local variable is created. When this variable is used outside the function, a compilation error occurs because the variable only exists within the function's scope.
In Example 4, a function is created with a parameter that has a unique name. When attempting to use this parameter name outside the function, a compilation error occurs because the name only exists within the function's scope.
In Example 5, when a variable is defined outside a function with the same name as a local variable inside the function, the local variable takes precedence within the function's scope.
The value of the global variable remains unchanged while the local variable is in use, and the global variable can only be accessed once the local variable goes out of scope.
Learn more about common errors
brainly.com/question/31474055
#SPJ11
a team is designing a new user interface for a website and deciding between two formats for collaboration: an in-person brainstorming session using paper, markers, and post-its a digital document in a productivity software suite that allows for simultaneous editing and comment threads what would be the benefit of collaborating with the digital document?
Answers
Digital documents that support concurrent editing and commenting enable real-time collaboration, simple change tracking, and distant collaboration.
Compared to in-person brainstorming sessions, working together on a digital document has significant advantages. The first benefit is that it enables real-time collaboration, allowing team members to work on the document concurrently without the need for follow-up meetings or emails. Second, it makes it simple to track changes, which makes it simpler to maintain track of various document versions. Last but not least, digital documents enable remote collaboration, which is crucial in the modern workplace where many teams operate remotely. Collaboration is facilitated via comment threads in digital documents, which also make it simple for team members to communicate and provide input.
learn more about document here:
https://brainly.com/question/13406067
#SPJ4
Design thinking is another name for agile manifesto?
True or False?
Answers
(4, a) and (2, 5) are two points from a direct variation. What is a? Use the step-by-step process you just learned to solve this problem. Step 1: Set up the correct type of variation equation. y =
Answers
The value of a for point (4,a) in the direct variation is 10.
What is a direct variation?
The direct variation in mathematics is given as the equation relationship between the two numbers, where one is a constant multiple.
In the given problem, the variation equation is given as:
\(y=kx\)
Where k is a constant.
The value of k can be derived from point (2,5):
\(5=k2\\\\k=\dfrac{5}{2}\\\\ k=2.5\)
Substituting the values of k for the point (4,a):
\(a=2.5\;\times\;4\\a=10\)
The value of a for point (4,a) in the direct variation is 10.
Learn more about direct variation, here:
https://brainly.com/question/14254277
#SPJ1
Check ALL of the correct answers.
What would the following for loop print?
for i in range(2, 4):
print(i)
2
2
3
4.
1
Help now please
Answers
Answer:
2,3,4
Explanation:
Starts at two, goes to four. Thus it prints 2,3,4
Natalie is writing an

Answers
Answer:
A
The answer is A according to me because there are no match making 0 match.
designations at the end of file names such as .docx and .html are called
Answers
Answer:
Designations at the end of file names such as .docx and .html are called. File extensions.
Explanation:
Designations at the end of file names such as .docx and .html are called file extensions. A file name or file extension is a suffix that is added, to a computer file.
What are file extensions?The file type is identified by the extension, a three- or four-letter abbreviation. For instance, in a letter. The filename letter.docx has the extension.docx. Extensions are crucial since they inform your computer about the file's icon and the program that may open it.
The different types of file extensions are:
PEG (Joint Photographic Experts Group) PNG (Portable Network Graphics) SVG (Scalable Vector Graphics) PDF (Portable Document Format) GIF (Graphics Interchange Format) MP4 (Moving Picture Experts Group)Therefore, the file extensions are the designations that appear at the end of file names, such as.docx and.html.
To learn more about file extensions, refer to the link:
https://brainly.com/question/21419607
#SPJ5
when was pokemon movie 2000 release
Answers
Answer:
Pokemon movie released on 17 July 1999
ESXi Host Supports Following Discover Methods By ISCSI Target. (Choose Two) Static Dynamic Shared Non-Shared
Answers
The two discover methods supported by ESXi Host for iSCSI Target are Static and Dynamic. This allows the ESXi host to connect to the iSCSI target directly, without relying on any additional services.
Static Discovery Method: In the Static Discovery Method, the ESXi Host is configured with the iSCSI target IP address manually. The target IP address is entered in the iSCSI software adapter properties, and the ESXi Host connects to the target whenever it boots or when the iSCSI software adapter is rescanned. Dynamic Discovery Method: In the Dynamic Discovery Method, the ESXi Host discovers the iSCSI target automatically using the iSCSI target IP address or DNS name. The iSCSI target is identified using the iSCSI Qualified Name (IQN) or Extended Unique Identifier (EUI). The ESXi Host then establishes a connection with the iSCSI target and logs in.
Shared: A Shared iSCSI Target is accessible by multiple ESXi Hosts, and each ESXi Host can access the same data on the iSCSI Target. Non-Shared: A Non-Shared iSCSI Target is accessible by a single ESXi Host, and the data on the iSCSI Target is not shared with other ESXi Hosts.
To know more about connect visit:
https://brainly.com/question/28337373
#SPJ11
MS Word
6.What adds artistic effects to the picture to make it more look like a sketch or painting.?
7. It improves the brightness, contrast or sharpness of the picture.
Answers
The thing that adds artistic effects to the picture to make it more look like a sketch or painting is:
To add artistic effects to a picture to make it look like a sketch or painting, you can use photo editing software or an app that has filters or effects that mimic the look of a sketch or painting. Some popular options for this include Adobe Photoshop, GIMP, and Prisma.How do one improve brightness?To improve the brightness, contrast, or sharpness of a picture, you can also use photo editing software or an app.
These tools typically have features such as brightness/contrast adjustments, sharpening filters, and other image enhancement tools that allow you to fine-tune the appearance of your photo.
Therefore, Some popular options for this include Adobe Photoshop, GIMP, and Lightroom. You can also use these tools to adjust the color balance, saturation, and other aspects of the image to achieve the desired look.
Learn more about brightness from
https://brainly.com/question/2824108
#SPJ1
name at least two actions that you might take if you were to see a large animal on the right shoulder of the road in front of you
Answers
Answer:
Explanation:
Scan the road ahead from shoulder to shoulder. If you see an animal on or near the road, slow down and pass carefully as they may suddenly bolt onto the road. Many areas of the province have animal crossing signs which warn drivers of the danger of large animals (such as moose, deer or cattle) crossing the roads
mark me brillianst
which of the following returns the book handcranked computers in the results?
Answers
The query that would return the book "HANDCRANKED COMPUTERS" in the results is:c: SELECT * FROM books WHERE title LIKE 'H_N_C%';
What is the returnsThe LIKE operator in SQL is used to find specific patterns in a WHERE statement. You can find things that match a pattern by using special symbols called wildcard characters.
The symbol '%' can stand for any group of letters or numbers. This question looks for anything that starts with "H", then "N", and ends with "C" by using a symbol (%) that stands for any letter or number. The symbol % can stand for any letters or numbers. It will find any title that begins with "H", has some letters or numbers in the middle, and ends with "N", then "C".
Learn more about COMPUTERS from
https://brainly.com/question/24540334
#SPJ4
Which of the following returns the book HANDCRANKED COMPUTERS in the results?
SELECT * FROM books WHERE title = 'H_N_%';
SELECT * FROM books WHERE title LIKE "H_N_C%";
SELECT * FROM books WHERE title LIKE 'H_N_C%';
SELECT * FROM books WHERE title LIKE '_H%';
An electric toothbrush costs $56, including a 40% price markup. What was the cost for the store to purchase the electric toothbrush?.
Answers
An electric toothbrush costs $56, including a 40% price markup. The cost for the store to purchase is $22.40. The correct option is A.
What is the percentage?A percentage is a figure or ratio that can be written as a fraction of one hundred or as a relative value denoting one-hundredth of any amount.
Given that the cost of an electric toothbrush = $ 56
And, The price of markup = 40%
Now,
Since, The cost of an electric toothbrush = $ 56
And, The price of markup = 40%
So, The cost for the store to purchase the electric toothbrush is;
(40% of $56)
(40/100 x 56) = $22.4
Therefore, the cost for the store to purchase the electric toothbrush is $22.40. The correct option is A.
To learn more about percentages, refer to the link:
https://brainly.com/question/28751082
#SPJ1
The question is incomplete. Your most probably complete question is given below:
A) $22.40
B) $30.00
C) $40.00
D) $64.80
Which code is easier to learn, Python or C++. And which one is better than the other in your opinion
Answers
Choose the option that best matches the description given. The older term, social service, referred to advancing human welfare. The new term, meaning to provide for the needs of various people and groups, is ____.
A. social assistance
B.social welfare
C.social media
For everyone that doesn't wanna watch the ads, The answer is A, social assistance.
Answers
Answer:
Social Assistance
Explanation:
Provision and disbursement of intervention in other to palliate the suffering and want of an individual, group or community can be described as rendering social assistance. Assistance which also means helping people fulfill their needs could be offered by the government, non-governmental organizations or individuals personnels. Rendering social assistance could be in the form of cash or gift offerings, provision of food for the hungry, shelter for the homeless, medical interventions for the sick and catering for other touch points of the needy.
Answer:
Social Assistance
Explanation:
Which action would best help a school improve equity for its students?
O A. Provide classes on economics and investing
O B. Focus interventions on the students with disabilities
O C. Make the classes easier so everyone can get an A
O D. Provide all students with what they need to be successful
SUBMIT
Answers
D, the first two focus on two specific aspects and the third wouldn’t help i’m the long run.
you want to provide scalability for an application installed on an nlb cluster composed of several servers. which filtering mode should you use?
Answers
The same version of Windows Server 2016 must be used by all servers. An Active Directory domain must be joined by all servers. Hardware components must be the same across all servers.
A Network Load Balancing (NLB) cluster's settings can be changed using the Set-NlbCluster cmdlet. The cluster operating mode, cluster name, and cluster primary IP address are among the setup adjustments you can make. The most recent copy of the cluster database, which contains information about the setup and condition of the cluster, is kept in the quorum resource. On all active nodes, a failover cluster keeps a consistent, updated copy of the cluster database. Resources, sometimes known as physical or logical units, can be hosted by a node. The same subnet must have at least one IP address for each machine.
Learn more about server here-
https://brainly.com/question/7007432
#SPJ4
Suppose we are using a three-message mutual authentication protocol, andAlice initiates contact with Bob. Suppose we wish Bob to be a stateless server, and thereforeit is inconvenient to require him to remember the challenge he sent to Alice. Lets modify theexchange so that Alice sends the challenge back to Bob, along with the encrypted challenge. So the protocol is:Step 1: Alice send a message [I’m Alice] to Bob. Step 2: Bob sends a random number, R. Step 3: Alice sends a message [R,KAlice−Bob{R}]. Is this protocol secure?
Answers
No, this protocol is not secure. A secure mutual authentication protocol must, among other things, support mutual authentication, which allows both parties to confirm the identities of one another.
Due to the fact that Bob cannot recall the challenge he gave to Alice, he is unable to confirm Alice's identity using this protocol. As a result, an attacker can read Alice and Bob's messages and then pretend to be Alice to Bob by simply playing back the message that Alice originally sent.
This problem can be resolved by changing the protocol so that Bob sends a challenge along with the random number R, and Alice must respond with the challenge as well. This way, Bob can verify Alice's identity by checking if the challenge in Alice's response matches the one he sent earlier.
For such more question on protocol:
https://brainly.com/question/8156649
#SPJ11
longest string write a program that takes two strings and returns the longest string. if they are the same length then return the second string. ex. if the input is: almond pistachio the output is: pistachio
Answers
Below is the program in Python that takes two strings and returns the longest string. If they are the same length, then it returns the second string.
def longest_string(str1, str2):
if len(str1) =
= len(str2):
return str2
elif len(str1) > len(str2):
return str1
else:
return str2
print(longest_string("almond", "pistachio"))
The output of this program would be "pistachio" because it is the longest string. If the two strings had been the same length, the output would have been the second string which, in this case, is "pistachio".
The program above uses a simple if-else statement to compare the lengths of the two input strings. If the two strings have the same length, it returns the second string, otherwise, it returns the string with the longest length.
The "len" function in Python is used to find the length of the string. This function takes the string as input and returns the length of the string as an integer. In the program, we use this function to find the lengths of the two input strings.
To know more about program visit:
https://brainly.com/question/30589888
#SPJ11
Intro to Java CODING assignment
PLEASE HELP

Answers
Answer:
Here's a Python program that can determine if a sentence is a pangram or a perfect pangram based on the given input format:
import string
def is_pangram(sentence):
# Convert the sentence to lowercase and remove all non-alphabetic characters
sentence = sentence.lower().replace(" ", "").replace(".", "").replace(":", "").replace("\"", "")
# Create a set of unique characters in the sentence
unique_chars = set(sentence)
# Check if the set of unique characters contains all 26 letters of the alphabet
if len(unique_chars) == 26:
return True
else:
return False
def is_perfect_pangram(sentence):
# Convert the sentence to lowercase and remove all non-alphabetic characters
sentence = sentence.lower().replace(" ", "").replace(".", "").replace(":", "").replace("\"", "")
# Create a set of unique characters in the sentence
unique_chars = set(sentence)
# Check if the set of unique characters contains all 26 letters of the alphabet
if len(unique_chars) == 26 and len(sentence) == 26:
return True
else:
return False
# Input sentences from the text file
sentences = [
"THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG.",
"ALL YOUR BASE ARE BELONG TO US: SOMEONE SET US UP THE BOMB.",
"\"NOW FAX A QUIZ TO JACK!\" MY BRAVE GHOST PLED.",
"QUICK HIJINX SWIFTLY REVAMPED THE GAZEBO.",
"NEW JOB: FIX MR GLUCK'S HAZY TV, PDQ.",
"LOREM IPSUM DOLOR SIT AMET CONSECTETUR ADIPISCING ELIT.",
"PACK MY BOX WITH FIVE DOZEN LIQUOR JUGS."
]
# Iterate through the input sentences
for sentence in sentences:
# Check if the sentence is a perfect pangram
if is_perfect_pangram(sentence):
print("PERFECT:", sentence)
# Check if the sentence is a pangram
elif is_pangram(sentence):
print("PANGRAM:", sentence)
# If neither, print NEITHER
else:
print("NEITHER:", sentence)
This program uses two functions is_pangram() and is_perfect_pangram() to check if a sentence is a pangram or a perfect pangram, respectively. It then iterates through the input sentences and prints the appropriate output based on the pangram status of each sentence.
what is the period of a wave that has a frequency of 30hz
A. 0.03 s
B. 3 s
C. 30 s
D. 0.3 s
Answers
A 0.03s hope this helps
0.03 s is the period of a wave that has a frequency of 30hz. Thus, option A is correct.
How Period of wave and its frequency are closely related?Period of wave and its frequency are closely related. Period is the inverse of frequency. The period of a wave is the time taken for a number of waves to pass through a particular point. The frequency of a wave is the number of waves that passes through a point at a particular time.
An electromagnetic spectrum can be defined as a range of frequencies and wavelengths into which an electromagnetic wave is distributed into.In Science, the electromagnetic spectrum is composed of the following types of energy from highest to lowest frequency and shortest to longest wavelength and these are Gamma rays, X-rays and electromagnetic wave.
An ocean wave is generally classified as a mechanical wave while both visible light and x-rays are electromagnetic waves. A wave can be defined as a disturbance in a medium that progressively transfers (transports) energy from a source to another location, especially without the transportation of mass (matter).
Therefore, 0.03 s is the period of a wave that has a frequency of 30hz. Thus, option A is correct.
Learn more about frequency on:
https://brainly.com/question/5102661
#SPJ2
wendy is considering the use of a vulnerability scanner in her organization. what is the proper role of a vulnerability scanner?
Answers
Wendy is considering the use of a vulnerability scanner in her organization. The proper role of a vulnerability scanner is that they locate known security holes.
What is vulnerability scanner?
Vulnerability scanning, also known colloquially as 'vuln scan,' is an automated process for proactively detecting network, application, and security flaws. Vulnerability scanning is typically performed by an organization's IT department or a third-party security service provider. This scan is also used by attackers looking for points of entry into your network.
Detecting and classifying system flaws in networks, communications equipment, and computers is part of the scanning process. In addition to identifying security flaws, vulnerability scans forecast how effective countermeasures will be in the event of a threat or attack.
To learn more about vulnerability scanner, visit: https://brainly.com/question/9239001
#SPJ4