Create a function min_mid_max which takes a list as its formal parameter and returns a new list with the following characteristics: element 0 contains the minimum value • element 1 contains the middle value (not the median -- which would require an average if the list had an even number of elements). If the list is even (e.g. [1,2,3,4]) the 'middle' value will be the right value of the two possible choices (e.g. 3 rather than 2). • element 2 contains the maximum value Notes: • You can only use Python syntax shown so far (even if you know more) • You cannot use any math library (we have yet to see this) • You should use the function sorted. Remember the function sorted does not change its input, it returns a new list. • You should only need to call sorted one time. print(sorted(3,2,1])) • You can use the function int (another built in function) to help determine the index of the middle value. This function takes a floating point (or any kind of number) and converts it into an integer (e.g.print(int(4.32)). This will allow you to treat lists with an even number of elements the same as a list with a odd number of elements. • If min_mid_max is called with an empty list, return an empty list. • If min_mid_max is called with 1 item that item is the min, mid, and the max • If min_mid_max is called with 2 items, the mid and the max should be the same • No need to worry about the incoming list being the value None
Answers
Answer:
Follows are the code to this question:
def min_mid_max(myList):#defining a method min_mid_max that accept a list in parameter
if len(myList)==0:#defining if block that check list length equal to 0
return []#return empty list
s = sorted(myList)#defining variable s that uses the sorted method to sort the list
m = int(len(myList)/2)#defining mid variable that hold list mid value
return [s[0], s[m], s[-1]]#return list values
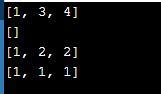
print(min_mid_max([1,2,3,4]))#use print function to call method
print(min_mid_max([]))#use print function to call method
print(min_mid_max([1, 2]))#use print function to call method
print(min_mid_max([1]))#use print function to call method
Output:
Please find the attached file.
Explanation:
In the given code, a method "min_mid_max" is defined, which accepts a list "myList" in parameter, inside the method if block is used, that check length of the list.
If it is equal to 0, it will return an empty list, otherwise, a variable "s" is declared, that use the sorted method to sort the list, and in the "m" variable, it holds the mid number of list and returns its value.
In the print method, we call the above method by passing a list in its parameter.
Related Questions
Many real world problems that we encounter including Information Systems problems are wicked in nature. The following statements are TRUE of the wickedness of these problems EXCEPT….
Answers
They have clear avenues for solutions that are simple to identify. Wicked problems lack precise problem descriptions, making them ambiguous, complex, and challenging to resolve.
What are some instances of wicked dilemmas in real life?Some of the most difficult and intricate problems of our time—many of which endanger human health—are referred to as "wicked." Examples of such wicked challenges include climate change, biodiversity loss, persistent poverty, the growing obesity pandemic, and food insecurity.
What constitutes a wicked example?adjective a cruel and evil deed In the play, she took on the role of the evil stepmother. After winning, she grinned viciously. Her caustic sense of humour is well recognised. She was a bad case.
To know more about Wicked problems visit:-
https://brainly.com/question/29854616
#SPJ1
Question:
Many real-world problems that we encounter, including Information Systems problems, are wicked in nature. The following statements are TRUE of the wickedness of these problems EXCEPT:
a) They have unclear problem definitions and no definitive solutions.
b) They have multiple and changing constraints.
c) They have well-defined solution paths that can be easily determined.
d) They require a unique approach to every problem instance.
Effects of disregarding to ignoring computer problems
Answers
-It can cause damage to essential computer hardware.
-It can also lead to electric shock circuit that may cause fire.
-Loss of information and data.

Increase the value of cell C30 by 15% using the cell referencing single MS Excel formula or function
Answers
To do this Excel formula, we must enter the following:
= C30 * 15% or = C30 * 1.15.
Assuming the value to increase is in cell C30, you can use the following formula in another cell to increase it by 15%:
=C30*1.15
This multiplies the value in cell C30 by 1.15, which is equivalent to adding 15%. The result will be displayed in the cell containing the formula.
Learn more about Excel formula at:
https://brainly.com/question/30324226
#SPJ1
Describe two reasons to use the Internet responsibly. Explain what might happen if the Internet use policies were broken at
your school.
Answers
Answer: You don't want to download any virus and Chat rooms with stranger can be harmful
Explanation: You can get a virus on your school device, get yourself in harmful situations and your passwords might not be safe
Upon returning from a year long working holiday, Alberta, the youngest of 4 sisters, announced her whirlwind marriage. Her 3 sisters, Carla, Paula, and Roberta,
were amazed by her husband's name.
• The 4 men are Albert, Carl, Paul, and Robert. Their last names are Albertson, Carlson, Paulson, and Robertson.
• No woman's husband has a first name that consists of her first name without the final "a"; no woman's last name consists of her first name without the final
"a" and with "son" on the end; and, no man's last name consists of his first name with "son" added at the end.
• Paul is not married to Roberta, and Robert is not married to Paula.
• No husband and wife have "bert" in both their first names, but there is a man who has "bert" in his first and last names.
Carl's last name is not Paulson.
Work out Alberta's husband's first and last name, as well as Carla's, Paula's, and Roberta's husbands' first and last name
Answers
The couples, considering the patterns in the problem, are listed as follows:
Carla and Robert Paulson.Paula and Albert Robertson.Alberta and Paul Carlson.Roberta and Carl Albertson.What are the couples?We use the information from the bullet points to find the couples.
The first information is:
No woman's husband has a first name that consists of her first name without the final "a".
Hence:
Alberta is married to either Carl, Paul or Robert.Carla is married to either Albert, Paul or Robert.Paula is married to either Albert, Carl or Robert.Roberta is married to either Albert, Carl or Paul.The second information is:
Paul is not married to Roberta, and Robert is not married to Paula.
Hence:
Roberta is married to either Albert or Carl.Paula is married to either Albert or Carl.No husband and wife have "bert" in both their first names, hence:
Roberta is married to Carl.Paula is married to Albert.Alberta is married to Paul.Carla is married to Robert.No woman's last name consists of her first name without the final "a" and with "son" on the end, and no man's last name consists of his first name with "son" added at the end, hence:
Roberta and Carl are either Albertson or Paulson.Paula and Albert are either Carlson or Robertson.Alberta and Paul are either Carlson or Robertson.Carla and Robert are either Albertson or Paulson.There is a man who has "bert" in his first and last names, hence either of these two can be couples.
Carla and Robert Albertson.Paula and Albert Robertson.Carl's last name is not Paulson, hence a couple is:
Carla and Robert Paulson.
Then Carla and Robert are Paulson, and the couples are:
Carla and Robert Paulson.Paula and Albert Robertson.Alberta and Paul Carlson.Roberta and Carl Albertson.More can be learned about patterns at https://brainly.com/question/18941199
#SPJ1
what are 3 software programs for mobile computing?
Answers
Answer:
1.Communication Devices
2.Mobile hardware
3.Mobile software and apps
(smartphones, laptop, etc)
Choose the correct option.
Which of the following infection types can send information on how you use your computer
to a third party without you realizing it?
Answers
Spyware accumulates your personal information and passes it on to curious third parties without your knowledge or consent.
Spyware is also learned for installing Trojan viruses.
What is spyware?
Spyware is a type of malicious software or malware that is established on a computing device without the end user's knowledge. It plagues the device, steals exposed information and internet usage data, and relays it to advertisers, data firms, or external users.
How do hackers utilize spyware?
Spyware monitors and logs computer use and activity. It celebrates the user's behavior and finds vulnerabilities that allows the hacker to see data and other personal details that you'd normally consider confidential or sensitive.
To learn more about Spyware, refer
https://brainly.com/question/7126046
#SPJ9
Discuss the impact of vision on your actions to keep a clean environment
Answers
Answer:
For healthy living a clean environment is crucial: The more you care about our environment, the more contaminants and toxins that have a detrimental effect on our health are polluted. Air pollution can lead, among other problems and diseases, to respiratory and cancer problems
Explanation:
Ensuring and improving the climate is an important resource for Irelanders. To safeguard against radiation and contamination damage our kin and the climate.
We have the vision:
A perfect environment to promote practical society and economy, which is sound and very secure.
Very few people are working to keep the environment clean. Although municipal authorities are responsible for making sure the environment is clean, the clean and green environment must also be supported.
Reasons Why We Should Care About the Environment
An essential part of human survival is the environment in which we live. I believe that people who don't care about the environment simply don't know how important it is for us all and how it doesn't directly affect them, which is why I want you to worry about the environment.
Earth Is Warming: We must do more to fight climate change for our children and our future. Yes, no single event trends. Yes, it is true. You can't ignore that now.
Biodiversity is essential: the diversity of plants, animals and the rest of our world is concerned with biodiversity. Habitat loss and degradation due, among other things, to human activity, climate change, and pollution could be negatively affected.
Which attitudes are most common among successful IT professionals?
O openness to learning new things and interest in technology
O emotional resilience and enjoyment of leadership positions
O tough-mindedness and a focus on financial gain
O empathetic and motivated by a concern for others
Answers
Answer:
O openness to learning new things and interest in technology
Explanation:
Successful IT professionals are always open to learn. The world of technology is rapidly evolving with new trends emerging with the passing of each day.
A successful IT professional must be open to learn in order to improve his skills. He must also be deeply interested in the world of technology so that he can effectively contribute to the development of new technology.
9
10
11
12
13
14
15
16
17
Which of the following is a shortcut used to copy selected or highlighted contents to
clipboard. (A) ctrl+A (B) ctrl+B (C) ctrl+Y (D) ctrrl+C
The shortcut use to open a new file / documents is ---(A) ctrl+K (B) ctrl+N (C) ctrl+M
(D) ctrrl+C
The best software for payroll calculation is --- (a) MS-Excel (b) CorelDraw (c) MS-
Access (d) MS-PowerPoint
GUI means: (a) graphical user input (b) graphical user interface (c) graphical user
internet (d) graphical used interface
Which of the following is an example of a word processing software: (a) CorelDraw (b)
WordPad (c) MS-Excel (d) Word Art
Which of the physical structure of the computer is NOT related --- (a) keyboard (b)
mouse (C) scanner (d) printer
Mouse, keyboard, system unit, printer, and speaker are best refers to: (a) components
(b) parts (c) hardware (d) software
Modern computer depending upon their application are classified as special purpose
computer and Purpose computer (a) new (b) original (c) all (d) general
The basic features of first generation computer is: (a) digital tube (b) vacuum tube (c)
valve tube (d) digital valve
Answers
The answers are in the order: D, B, A, B, D, C, C, D, B
Understanding computerA computer is an electronic device that accepts data, processes data to give information and finally store the data.
It is designed to receive, process, and output information, and can be programmed to perform a variety of tasks. Modern computers typically consist of hardware components, such as the central processing unit (CPU), memory, storage, and input/output devices like a keyboard and a monitor, as well as software components, such as the operating system and applications.
Computers have become an integral part of modern society and are used for a wide range of purposes, from personal use to business, education, and scientific research.
Learn more about computer shortcuts here:
https://brainly.com/question/30590269
#SPJ1
100pts!!!! It can be challenging to create algorithms that are not biased towards minority groups because machine learning works by _____. Select 2 options.
1. discarding outliers
2. excluding majorities
3. including outliers
4. discarding patterns
5. determining patterns
Answers
1. discarding outliers
2. excluding majorities
3. including outliers
4. discarding patterns
5. determining patterns
The program below is a salary calculator. It need to be modified to substract 30% to account for taxes, and 8% for retirement from the gross. Then print out the net amount earned.
import java.util.Scanner;
public class Salary {
public static void main(String [] args) {
Scanner scnr = new Scanner(System.in);
int hourlyWage;
int weeklyHours;
int weeklySalary;
int overtimeHours;
final int WEEKLY_LIMIT = 40;
System.out.println("Enter hourly wage: ");
hourlyWage = scnr.nextInt();
// FIXME: Get user input value for weeklyHours
weeklyHours = 40;
if (weeklyHours <= WEEKLY_LIMIT) {
weeklySalary = weeklyHours * hourlyWage;
}
else {
overtimeHours = weeklyHours - WEEKLY_LIMIT;
weeklySalary = (int)((hourlyWage * WEEKLY_LIMIT) +
(hourlyWage * overtimeHours * 1.5));
}
System.out.print("Weekly salary is: " + weeklySalary);
}
}
Answers
Here's how we can modify the program:
import java.util.Scanner;
public class Salary {
public static void main(String [] args) {
Scanner scnr = new Scanner(System.in);
double hourlyWage;
int weeklyHours;double grossPay;
double netPay;
int overtimeHours;
final double TAX_RATE = 0.3;
final double RETIREMENT_BENEFITS = 0.08;
final int WEEKLY_LIMIT = 40;
System.out.println("Enter hourly wage: ");
hourlyWage = scnr.nextDouble();
System.out.println("Enter weekly hours: ");
weeklyHours = scnr.nextInt();
if (weeklyHours <= WEEKLY_LIMIT) {
grossPay = weeklyHours * hourlyWage;
}
else {
overtimeHours = weeklyHours - WEEKLY_LIMIT;
grossPay = (hourlyWage * WEEKLY_LIMIT) +(hourlyWage * overtimeHours * 1.5);
}
netPay = grossPay - (grossPay * TAX_RATE) - (grossPay * RETIREMENT_BENEFITS);
System.out.println("Net pay is: " + netPay);
}}
In the above modified program, we have changed the datatype of hourlyWage, grossPay, and netPay to double as it's always better to use double for financial calculations.We have added two more variables TAX_RATE and RETIREMENT_BENEFITS which will be used to calculate the taxes and retirement benefits.The user can now input the weekly hours.
The program will calculate the gross pay using the formula Gross Pay = Hourly Wage * Weekly Hours.If weekly hours are less than or equal to the weekly limit, we calculate the gross pay using the formula Gross Pay = Weekly Hours * Hourly Wage.
Otherwise, we will calculate the overtime hours, and use the formula Gross Pay = (Hourly Wage * Weekly Limit) +(Hourly Wage * Overtime Hours * 1.5).Finally, we calculate the net pay using the formula Net Pay = Gross Pay - Taxes - Retirement Benefits. The program then prints out the net amount earned.
For more such questions on java, click on:
https://brainly.com/question/29966819
#SPJ8
How will Excel summarize the data to create PivotTables? summarize by row but not by column summarize by column but not by row summarize by individual cells summarize by row and by column
Answers
Answer:
D. summarize by row and by column
Answer:
D.
Explanation:
You learn that in a previous security breach at GearUp, a disgruntled employee destroyed the encryption key that had been used to protect data. How will you prevent a similar data safeguard problem at GearOn
Answers
Answer:
The data can be safeguarded using key escrow procedure.
Explanation:
Key escrow basically means to store the cryptographic key in an "escrow" by a reputable trusted third party. The copy of the encryption key is kept with the third party. In case the cryptographic key gets lost or destroyed, then the key escrow service helps to access the encrypted data. It also manages the access control to the key in case the key gets lost. So this way in case of security breach at GearOn the key escrow service can be used to re-implement or access the key easily.
list the factors that influenced the advancement of AI in recent years
Answers
Answer:
In any case, there are 5 factors which are driving the development of Artificial Intelligent and other technologies of Big Data, ML, etc.
Next-Generation Computing Architecture. ...
Open Data. ...
Growth in Deep Neural Networks. ...
Legal and Ethical Issues. ...
Historical Datasets.
python best hashing algorithm for passwords with mysql
Answers
Answer: So you Wait a minute I do believe that mysql is a sql cracking suit but you would need to build a hashing suit or you could use passlib.hash.mysql41 so you are looking to crack some stuff ok look at the file I sent.
Explanation:

3.Personal Information Class
Design a class that holds the following personal data: name, address, age, and phone number. Write appropriate accessor and mutator methods. Demonstrate the class by writing a java
program that creates three instances of it. One instance should hold your information, and
the other two should hold your friends' or family members' information.
Answers
Here's an example Java class that holds personal data and provides accessor and mutator methods:
public class PersonalData {
private String name;
private String address;
private int age;
private String phoneNumber;
public PersonalData(String name, String address, int age, String phoneNumber) {
this.name = name;
this.address = address;
this.age = age;
this.phoneNumber = phoneNumber;
}
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
public String getAddress() {
return address;
}
public void setAddress(String address) {
this.address = address;
}
public int getAge() {
return age;
}
public void setAge(int age) {
this.age = age;
}
public String getPhoneNumber() {
return phoneNumber;
}
public void setPhoneNumber(String phoneNumber) {
this.phoneNumber = phoneNumber;
}
}
And here's an example Java program that creates three instances of this class:
public class PersonalDataDemo {
public static void main(String[] args) {
PersonalData myData = new PersonalData("John Smith", "123 Main St, Anytown USA", 35, "555-1234");
PersonalData friend1Data = new PersonalData("Jane Doe", "456 Oak St, Anytown USA", 28, "555-5678");
PersonalData friend2Data = new PersonalData("Bob Johnson", "789 Elm St, Anytown USA", 42, "555-9012");
System.out.println("My personal data:");
System.out.println("Name: " + myData.getName());
System.out.println("Address: " + myData.getAddress());
System.out.println("Age: " + myData.getAge());
System.out.println("Phone number: " + myData.getPhoneNumber());
System.out.println();
System.out.println("Friend 1's personal data:");
System.out.println("Name: " + friend1Data.getName());
System.out.println("Address: " + friend1Data.getAddress());
System.out.println("Age: " + friend1Data.getAge());
System.out.println("Phone number: " + friend1Data.getPhoneNumber());
System.out.println();
System.out.println("Friend 2's personal data:");
System.out.println("Name: " + friend2Data.getName());
System.out.println("Address: " + friend2Data.getAddress());
System.out.println("Age: " + friend2Data.getAge());
System.out.println("Phone number: " + friend2Data.getPhoneNumber());
}
}
The above mentioned codes are the answers.
For more questions on Java, visit:
https://brainly.com/question/26789430
#SPJ11
what is logic unit of a computer processing unit
Answers
Answer:
Arithmetic logic unit
Explanation:
An arithmetic logic unit (ALU) is a digital circuit used to perform arithmetic and logic operations. It represents the fundamental building block of the central processing unit (CPU) of a computer. Modern CPUs contain very powerful and complex ALUs. In addition to ALUs, modern CPUs contain a control unit (CU).
If you have an array of 100 sorted elements, and you search for a value that does not exist in the array using a binary search, approximately how many comparisons will have to be done?
a)7
b)100
c)50
Answers
Answer:
50
Explanation:
as binary search will search the array by dividing it into two halves till it find the value.
aapke question about computer keyboard
Answers
Explanation:
A computer keyboard is an input device that allows a person to enter letters, numbers, and other symbols (these are called characters in a keyboard) into a computer. It is one of the most used input devices for computers. Using a keyboard to enter lots of data is called typing
Change the screen resolution so you can view more information on your screen. Use the resolution that enables you to fit the most information on the screen while still being able to read the display.
Use the space below to indicate your screen resolution and to describe the steps you used to do this.
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
My laptop's current screen resolution is (1366 by 768 recommended). When you change your screen resolution, your pc automatically suggests the recommended screen resolution that helps you to view more information on your screen and enable you to fit the most information on the screen while still being able to read the display.
To change the screen resolution, you need to go through from the following steps:
Right-click on empty space of desktop.As you right-click, a list of options will open, select "display setting" among themA new setting window will get open, at the left of the window, among given option, click on the first option i.e "display"The content of the display setting gets open in the right area of the window. scroll down and find the "Scale and Layout"under scale and layout, you can change your screen resolution while selecting the different screen resolution. However, it is good to select the recommended screen resolution based on your screen size.a place where people study space
Answers
Answer:
a place where people study space is a Spacey agent
Crashes involving new teen drivers are only caused by poor skills.
True
False
Answers
When should you create an outline?
OA. While you are creating your slides
OB. Before you create your first slide
O C. After you create your last slide
O D. After you have presented your slide presentation
Help need help now please!!!!!!!!
Answers
Answer:custom slide show
Explanation:
You have recently subscribed to an online data analytics magazine. You really enjoyed an article and want to share it in the discussion forum. Which of the following would be appropriate in a post?
A. Including an advertisement for how to subscribe to the data analytics magazine.
B. Checking your post for typos or grammatical errors.
C. Giving credit to the original author.
D. Including your own thoughts about the article.
Answers
Select All that apply
Answer:
These are the things that are would be appropriate in a post.
B. Checking your post for typos or grammatical errors.
C. Giving credit to the original author.
D. Including your own thoughts about the article.
Explanation:
The correct answer options B, C, and D" According to unofficial online or internet usage it is believed that sharing informative articles is a reasonable use of a website forum as much the credit goes back to the actual or original author. Also, it is believed that posts should be suitable for data analytics checked for typos and grammatical errors.
What is the difference between copy- paste and cut-paste
Answers
Answer:
Copy/ Paste - In the case of Copy/paste, the text you have copied will appear on both the locations i.e the source from where you copied the text and the target where you have pasted the text.
Cut/paste- In the case of Copy/paste, the text you have copied will appear on only one location i.e the target where you have pasted the text. The text will get deleted from the original position
A(n) ___loop is a special loop that is used when a definite number of loop iterations is required.
O a. for
O b. do...while
O c. else
O d. while
Answers
Answer: A
Explanation:
for is used when you're talking in terms of repeating loops for a finite number of times.
do... while is used when describing something to do while a variable is equal to something, else is used when a variable isn't what was defined in a while statement, and while is used when you want something to repeat while a variable is equal to something.
Given a variable s that contains a non-empty string, write some statements that use a while loop to assign the number of lower-case vowels ("a","e","i","o","u") in the string to a variable vowel_count.
Answers
Answer:
Following is the program in the python language
s="Hellooo" #string initialization
k=0 # variable declaration
vowel_count=0 #variable declaration
while k<len(s): #iterating the loop
c1=s[k] #store in the c1 variable
if c1=='a' or c1=='e' or c1=='i' or c1=='o' or c1=='u': #check the condition
vowel_count= vowel_count +1; # increment the variable vowel_count
k = k+1
print(vowel_count) #display
Output:
4
Explanation:
Following is the description of program
Create the string "s" and store some characters on them.Declared the variable "k" and initialized 0 on them .Declared the variable "vowel-count" and initialized 0 on them .Iterating the while loop ,inside that loop we shifted the string "s" into the " c1" variable and checking the condition in the if block by using or operator if the condition is true then it increment the "vowel_count" variable by 1 .Finally outside the loop we print the value of "vowel_count".The following code appears in a sort function. Will this function sort in increasing order (smallest first) or decreasing order (largest first)? Explain your answer if (list[index] < list[index + 1]) { temp = list [index]; list[ index] = list [index +1]; list[index +1] = temp; }
Answers
A sort function sorts in an ascending or desceding order
The true statement is that the function would sort in decreasing order.
What is a sort function?A sort function is a code segment that is used to reorder a list in ascending or descending order, when called or evoked
The order of the sort functionThe code segment is given as:
if (list[index] < list[index + 1]) {
temp = list [index];
list[ index] = list [index +1];
list[index +1] = temp;
}
In the above code, we can see that the code compares a list element with the next element on the list, and the larger value comes to the front
This means that the sort function sorts in decreasing order
Read more about code segments at:
https://brainly.com/question/16397886
**** Write in a Pseudocode form to compute sum of first ten prime numbers
Answers
Here's one way to write pseudocode to compute the sum of the first ten prime numbers:
The Pseudocodeset count to 0
set sum to 0
set num to 2 // start with the first prime number
while count < 10:
is_prime = true // assume num is prime unless proven otherwise
for i from 2 to num - 1:
if num % i == 0:
is_prime = false
break // num is not prime, so stop checking
if is_prime:
sum = sum + num
count = count + 1
num = num + 1 // check the next number
print sum
This pseudocode initializes a counter and a sum variable to zero, and then iterates through numbers until it finds 10 primes. For each number, it checks if it is prime by iterating through all the smaller numbers and checking if any divide it evenly. If the number is prime, it adds it to the sum and increments the counter. Finally, it prints the sum of the first 10 primes.
Read more about pseudocode here:
https://brainly.com/question/26905120
#SPJ1