DEF is a small consulting firm with ten on-site employees and 10 to 12 part-time (off-site) software consultants. Currently, the network consists of 2 servers for internal business processes, 1 server that handles the call-in connections; 10 on-site wireless workstations/devices, and 2 printers. Respond to the following in a minimum of 175 words: Identify one network security strategy that would help this organization. Why did you choose this strategy over others
Answers
Answer:
What i would suggest for the organization is to use the Testing Infrastructure strategy. it is good for your consulting firm because it is less costly and provide security.
Explanation:
Solution
There are different network security strategy which is listed below:
Segment the network:
Segmentation in network is very useful for providing security.If any threat is occur only one segment is effected remaining are safe and it is less cost process. very useful for small organizations.
Test your infrastructure :
Testing infrastructure also very good technique.
Always we have to test our infrastructure whether threat is occur or not.
If any threat is happen we can detect that easily by testing our infrastructure.
Regularly update anti-virus software :
This is very useful for small organizations and it is less cost.with less cost we can provide security for all devices like computer,server,modems etc.
Frequently backup your critical data :
This is very good technique for crucial data.If we backup important data any time that will be useful if any attack is happen.
This is less costs and simple.
Change router default security settings :
Changing router password and settings also helpful for providing security.If we maintain same password and same settings for a long time that may lead to data hacking.It is cost less process very useful for small organizations.
Related Questions
Which behavior demonstrates courtesy toward others in the workplace?
working long hours to complete a work assignment
solving complex technical problems to get a project schedule back on track
asking a coworker about his or her annual review results
consulting with a coworker before intervening in one of his or her projects
Answers
The correct option is (d) consulting with a coworker before intervening in one of his or her projects.
It involves showing respect, consideration, and sensitivity toward others in your interactions, whether through words, actions, or attitudes.
Consulting with a coworker before intervening in their project is one way to demonstrate courtesy, but there are many other examples, such as listening actively, expressing gratitude, being punctual, using appropriate language, and avoiding gossip or negative comments.
This behavior shows that you value your coworker's input and respect their work, and are willing to work collaboratively rather than imposing your own ideas or solutions.
It also helps avoid potential conflicts or misunderstandings that could arise if you were to make changes to someone else's project without first discussing it with them.
Working long hours, solving complex technical problems, and asking about annual review results can all be positive behaviors, but they may not necessarily demonstrate courtesy toward others in the same way as consulting with a coworker.
The right answer is (d) consulting with a coworker before intervening in one of his or her projects.
For more questions on workplace courtesy, visit:
https://brainly.com/question/14962825
#SPJ11
Perfrom traceroute of an ip address in Australia
Answers
How to perform a typical traceroute on an IP address using CMD command is given below:
The StepsIn case you're striving to perform a traceroute operation on an IP address, either using Windows or Mac computer systems, the following guidelines will provide assistance.
Windows users may select the Windows key and R simultaneously, enter "cmd," hit Enter. In comparison, users operating with the Mac OS should navigate through Finder by visiting Applications -> Utilities and double-clicking Terminal.
To get started with the procedure, insert the word "traceroute," and proceed by entering the specific IP address that you desire to locate. Even if searching for information on 203.0.113.1, simply input "traceroute 203.0.113.1." At this stage, submit and wait until the validation is done.
This method ascertains the path taken by packets across the network. It indicates the number of jumps made, along with their response time at every stage. One aspect to bear in mind is some routers/firewalls may block access thereby leading to incomplete outcomes.
Read more about Ip addresses here:
https://brainly.com/question/14219853
#SPJ1
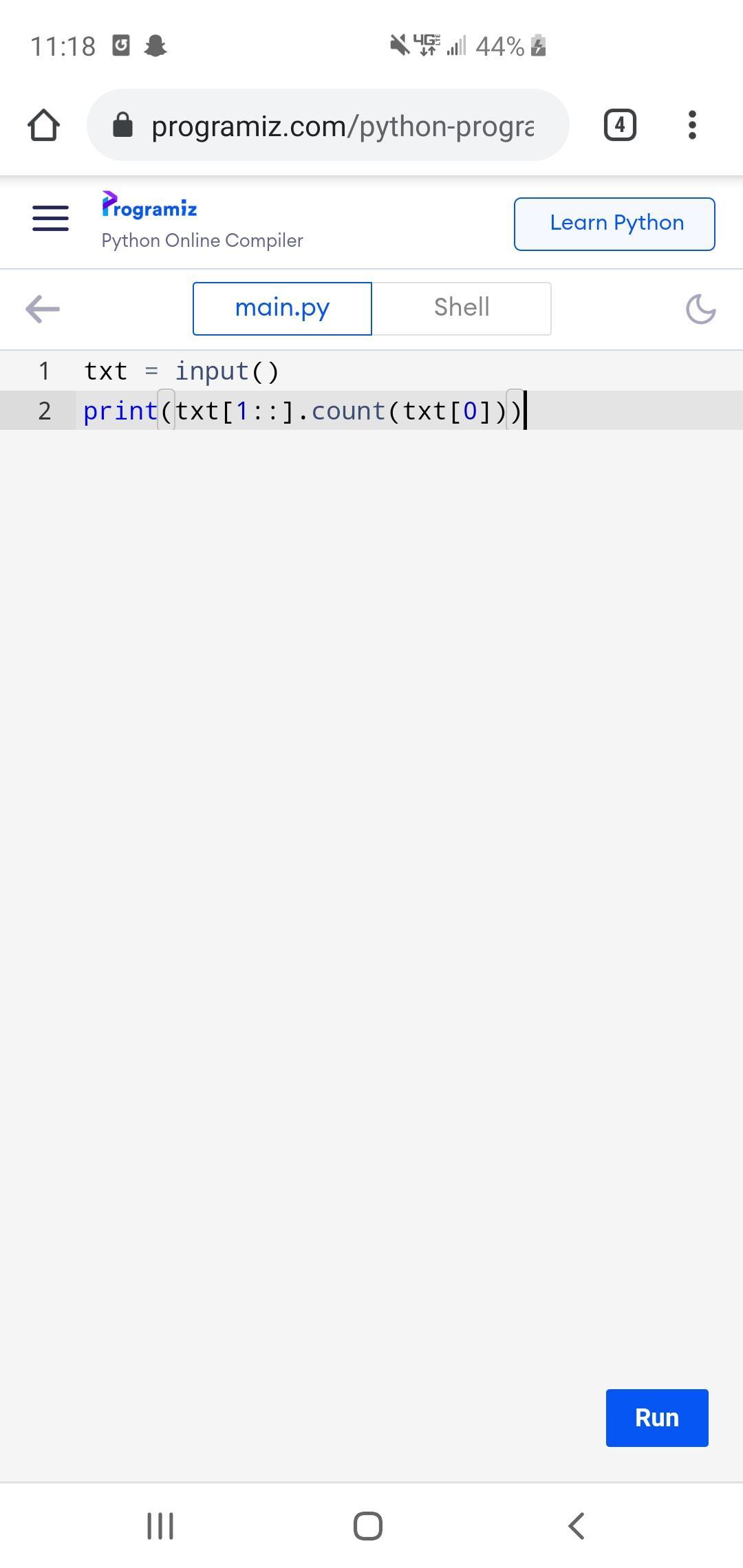
Write a program whose input is a string which contains a character and a phrase, and whose output indicates the number of times the character appears in the phrase.
Ex: If the input is:
n Monday
the output is:
1
Ex: If the input is:
z Today is Monday
the output is:
0
Ex: If the input is:
n It's a sunny day
the output is:
2
Case matters.
Ex: If the input is:
n Nobody
the output is:
0
n is different than N.
Learning Python
Answers
Explanation:
1
Ex: If the input is:
z Today is Monday
the output is:
0
Ex: If the input is:
n It's a sunny day
the output is:
2
Case matters.
Ex: If the input is:
n Nobody
the output is:
0
n is different than N.
Learning Python
I've included my code in the picture below. Best of luck.
Which programming language uses objects? C++ ALGOL Pascal BASIC
Answers
Answer:
C++
Explanation:
I am a c++ dev
Answer:
its A
C++
Explanation:
Youre amazing
b. Read in the data from the hours.csv file and call it “hours”. Make a histogram of the variable hours_studying. (Include the code to generate the histogram and the histogram itself in your lab report.) Comment on the symmetry or skew of the histogram.
c. Use the t.test() function that your used in lab to test the hypotheses to answer the question if this sample indicates a significant change in the number of hours spent studying. (Include your
R code and the output from t.test() in your lab report.)
i. What is the value of the test statistic?
ii. What is the p-value?
iii. Are the results significant at the α = 0. 05 level?
d. Write a conclusion for this test in APA format (as illustrated in lecture and lab).
Answers
After performing a one-sample t-test, it was determined that the test statistic held a value of t = 6.3775 (d.f.=63). The p-value calculated to be 1.128e-08, a figure insignificantly beneath the critical level of 0.05.
How to explain the StatisticsThis establishes that the resulting data holds significance, as confirmed by the α=0.05 criterion given that the p-value is inferior toward the stated limit.
The average weekly study time for the students in question resulted in M = 14.18 hours; this signifies statistical variance when contrasted with sigma distribution variable values equating to SD = 5.10 (t(63) = 6.38, p < .001, 95% CI [12.95, 16.39]). Consequently, the null hypothesis cannot be sustained and must therefore be rejected.
Learn more about statistic on
https://brainly.com/question/15525560
#SPJ1
Joseph owns a candy company and wants to show the popularity of his products across the United States. Which feature would best illustrate this argument? a 3D map a sparkline a trendline a data map
A 3D MAP
Answers
A data map would best illustrate the popularity of Joseph's candy products across the United States.
What is a Data Map?A data map is a visual representation of data that uses color coding or shading to show numerical values for specific regions or areas.
In this case, Joseph could use a data map to display sales data for each state, with darker colors representing higher sales figures. This would allow viewers to quickly and easily see which states have the highest and lowest sales of Joseph's candy products, and would provide a clear visual representation of the popularity of his products across the country.
Read more about data map here:
https://brainly.com/question/28416579
#SPJ1
Answer:
a) a 3-D map
Explanation:
got it right on edge
1) What is the first compartment of the 3 Sink Setup filled with?
O Multi-purpose detergent solution and water at least 110°F/37°C
O Baking soda solution and water at least 110°F/37°C
Isopropyl alcohol solution and water at least 110°F/37°C
Sanitizer solution and water at least 110°F/37°
Answers
The first compartment of the 3 Sink Setup is typically filled with option D: a Sanitizer solution and water at least 110°F/37°
What is the first compartment of the 3 Sink Setup filled with?The first part of the 3 Sink Setup is for cleaning and getting rid of germs. People often call it the spot where you sanitize things. In this compartment, we mix a special cleaning liquid with water to make a sanitizer solution. We suggest keeping the water in this area at least as warm as 110°F/37°C.
Sanitizer is used to get rid of germs on things like dishes and kitchen surfaces. It stops germs from spreading and makes sure food is safe.
Learn more about Sanitizer solution from
https://brainly.com/question/29551400
#SPJ1
Most operating system have GUI as part of the system, which is the following best describes an operating system GUI
Answers
A Graphical User Interface (GUI) is the component of an operating system that allows users to communicate with the system using graphical elements. GUIs are generally used to give end-users an efficient and intuitive way to interact with a computer.
They provide an easy-to-use interface that allows users to manipulate various objects on the screen with the use of a mouse, keyboard, or other input device.The primary function of an operating system GUI is to make it easier for users to interact with the system.
This is done by providing visual feedback and a simple way to access various system functions. GUIs can be customized to suit the user's preferences, which means that they can be tailored to meet the specific needs of different users.Some of the key features of a GUI include the use of windows, icons, menus, and buttons.
Windows are used to display information and applications, while icons are used to represent various objects or applications on the screen. Menus and buttons are used to provide users with a way to access various system functions, such as saving a file or printing a document.
The use of a GUI has become a standard feature of most operating systems. This is because GUIs make it easier for users to interact with computers, and they provide an efficient and intuitive way to access various system functions.
For more such questions on Graphical User Interface, click on:
https://brainly.com/question/28901718
#SPJ8
And office now has a total of 35 employees 11 were added last year the year prior there was a 500% increase in staff how many staff members were in the office before the increase
Answers
There were 5 staff members in the office before the increase.
To find the number of staff members in the office before the increase, we can work backward from the given information.
Let's start with the current total of 35 employees. It is stated that 11 employees were added last year.
Therefore, if we subtract 11 from the current total, we can determine the number of employees before the addition: 35 - 11 = 24.
Moving on to the information about the year prior, it states that there was a 500% increase in staff.
To calculate this, we need to find the original number of employees and then determine what 500% of that number is.
Let's assume the original number of employees before the increase was x.
If we had a 500% increase, it means the number of employees multiplied by 5. So, we can write the equation:
5 * x = 24
Dividing both sides of the equation by 5, we find:
x = 24 / 5 = 4.8
However, the number of employees cannot be a fraction or a decimal, so we round it to the nearest whole number.
Thus, before the increase, there were 5 employees in the office.
For more questions on staff members
https://brainly.com/question/30298095
#SPJ8
could someone teach me how to program it? Thanks you
Answers
Answer:
Did you read the pdf? Also I only know JAVAscript and scratch not Verilog
Explanation:
As you know computer system stores all types of data as stream of binary digits (0 and 1). This also includes the numbers having fractional values, where placement of radix point is also incorporated along with the binary representation of the value. There are different approaches available in the literature to store the numbers having fractional part. One such method, called Floating-point notation is discussed in your week 03 lessons. The floating point representation need to incorporate three things:
• Sign
• Mantissa
• Exponent
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-
point notation.
B. Determine the smallest (lowest) negative value which can be
incorporated/represented using the 8-bit floating point notation.
C. Determine the largest (highest) positive value which can be
incorporated/represented using the 8- bit floating point notation.
Answers
Answer:
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-point notation.
First, let's convert -9/2 to a decimal number: -9/2 = -4.5
Now, let's encode -4.5 using the 8-bit floating-point notation. We'll use the following format for 8-bit floating-point representation:
1 bit for the sign (S), 3 bits for the exponent (E), and 4 bits for the mantissa (M): SEEE MMMM
Sign bit: Since the number is negative, the sign bit is 1: 1
Mantissa and exponent: Convert -4.5 into binary and normalize it:
-4.5 in binary is -100.1. Normalize it to get the mantissa and exponent: -1.001 * 2^2
Mantissa (M): 001 (ignoring the leading 1 and taking the next 4 bits)
Exponent (E): To store the exponent (2) in 3 bits with a bias of 3, add the bias to the exponent: 2 + 3 = 5. Now, convert 5 to binary: 101
Now, put the sign, exponent, and mantissa together: 1101 0010
So, the 8-bit floating-point representation of -9/2 (-4.5) is 1101 0010.
B. Determine the smallest (lowest) negative value which can be incorporated/represented using the 8-bit floating-point notation.
To get the smallest negative value, we'll set the sign bit to 1 (negative), use the smallest possible exponent (excluding subnormal numbers), and the smallest mantissa:
Sign bit: 1
Exponent: Smallest exponent is 001 (biased by 3, so the actual exponent is -2)
Mantissa: Smallest mantissa is 0000
The 8-bit representation is 1001 0000. Converting this to decimal:
-1 * 2^{-2} * 1.0000 which is -0.25.
The smallest (lowest) negative value that can be represented using the 8-bit floating-point notation is -0.25.
C. Determine the largest (highest) positive value which can be incorporated/represented using the 8-bit floating-point notation.
To get the largest positive value, we'll set the sign bit to 0 (positive), use the largest possible exponent (excluding infinity), and the largest mantissa:
Sign bit: 0
Exponent: Largest exponent is 110 (biased by 3, so the actual exponent is 3)
Mantissa: Largest mantissa is 1111
The 8-bit representation is 0110 1111. Converting this to decimal:
1 * 2^3 * 1.1111 which is approximately 1 * 8 * 1.9375 = 15.5.
The largest (highest) positive value that can be represented using the 8-bit floating-point notation is 15.5.
Explanation:
Which of the following is NOT an element of critical thinking?
Answers
Answer:
implementing the first solution to a problem identified
Create a spreadsheet that lists the ten currencies you chose. For each currency, enter an amount and create a
formula to convert it to U.S. dollars. Make sure to include dollar signs in the appropriate cells.
Answers
Answer:
its a very lengthy one
Explanation:
A programmer created a piece of software and wants to publish it using a Creative Commons license. Which of the following is a direct benefit of publishing the software with this type of license? The programmer can specify the ways that other people are legally allowed to use and distribute the software.
Answers
A direct benefit of publishing the software with a Creative Commons license is that it allows the programmer to maintain copyright ownership while still giving others the right to use, share, and modify the software for free.
What is Software?
Software is a set of instructions that tell a computer how to perform a task. It can be used to facilitate tasks, automate processes, and create new programs. Software can be divided into two categories, system software and application software. System software includes operating systems and device drivers which manage and control the hardware and software applications of a computer system.
To know more about Software
https://brainly.com/question/28224061
#SPJ4
When using the ________ logical operator, both subexpressions must be false for the compound expression to be false. a. either or or and b. not c. or d. and
Answers
When using the and logical operator, both subexpressions must be false for the compound expression to be false
What are logical operators?A logical operator, also known as a boolean operator, is a symbol or keyword used in computer programming and logic to perform logical operations on one or more boolean values.
Boolean values are binary values that represent true or false, or in some cases, 1 or 0.
There are three common logical operators:
AND: Denoted by the symbol "&&" in many programming languages, the AND operator returns true if both operands are true, and false otherwise.
OR: Denoted by the symbol "||" in many programming languages, the OR operator returns true if at least one of the operands is true, and false otherwise.
NOT: Denoted by the symbol "!" in many programming languages, the NOT operator, also known as the negation operator, is a unary operator that takes a single boolean operand and reverses its logical value.
Learn more about logical operator at
https://brainly.com/question/15079913
#SPJ1
The____ feature in the Camera Raw dialog box can be used to bring out any deep colors in an image.
Answers
Answer: elg
Explanation:
The five types of personal computers are: desktops, laptops, tablets, smartphones, and
Answers
Answer:
microcomputers
Explanation:
For this question, assume all input comes from the keyboard, and all output goes to the screen. Include method prototypes and comments. The array should have room for 100 integers Write a complete Java program, including at least one comment in the main program and one in each method, to do the following Write a main program which will call the methods described below.(a) First the main program will read an integer (this integer is a parameter or header value) which it will callk Then the main program will call the method readdata( (see part 1 below) to read a set of data containing k values into an integer array which the main program will call x(b) The main program will call the method count5s) (see part 2 below), sending the x array (and k).(c) The main program will call the method sortarray() (see part 3 below) to sort the first k elements of the x array into descending order. The new values in the x array will be printed in the main prograrmDetails of the methods:1. Write a method called readdata() which receives two parameters, an integer n and an integer array arr The method will be sent a value for n. The method will read a set of n data items into the arr array. The method will print the set of data values as they are being read in2. Write a method called count5s) which receives two parameters, an integer n and an integer array v. The method will count how many of the first n elements of the v array are greater than 5, how many are less than 5 and how many are equal to 5 The method will print these values, with messages for each As an example: if the array holds the values 5 66 -4 5 1 -3, with n 6: there is 1 value greater than 5, there are 3 values less than 5, and there are 2 values equal to 5 3. Write a method called sortarray) which receives two parameters, an integer array w and an integer n giving the size of the array. The method will sort the first n elements of the w array into descending order. As an example, assume that method starts with these values in the w array: 5 66-4 5 1-3, with n = 6, Inside the method, these values will be sorted into descending order; the array will now hold 66 5 5 1 -3 -4
Answers
A group of comparable data elements kept in close proximity to one another in memory is called an array.
What is an array ?The first k items of the x array will be sorted into descending order by the main program by calling the function sortarray(). An array is a group of memory regions, or "boxes," each of which has the same identification and stores a single piece of data. A single data type must be present in every element of an array. Think of a situation where a scoreboard for a game needs to keep track of ten scores.
It is the most basic data structure because each data element may be immediately retrieved by using only its index number.
Therefore the correct answer is option C ) The main program will call the method sortarray() (see part 3 below) to sort the first k elements of the x array into descending order.
To learn more about array refer to :
brainly.com/question/29537583
#SPJ4
An __________ hard drive is a hard disk drive just like the one inside your, where you can store any kind of file.
Answers
An external hard drive is a hard disk drive just like the one inside your computer, where you can store any kind of file.
These drives come in various sizes, ranging from small portable drives that can fit in your pocket to larger desktop-sized drives with higher storage capacities. They often offer greater storage capacity than what is available internally in laptops or desktop computers, making them useful for backups, archiving data, or expanding storage capacity.
Overall, external hard drives are a convenient and flexible solution for expanding storage capacity and ensuring the safety and accessibility of your files.
What are some random fun facts about Technology?
Answers
Answer:
i do not know
Explanation:
but it helps to communication
5. What are Excel cell references by default?
Relative references
Absolute references
Mixed references
Cell references must be assigned
Answers
Answer: relative references
Explanation:
By default, all cell references are RELATIVE REFERENCES. When copied across multiple cells, they change based on the relative position of rows and columns. For example, if you copy the formula =A1+B1 from row 1 to row 2, the formula will become =A2+B2.
1.16 LAB: Input and formatted output: Right-facing arrow
Given two input integers for an arrow body and arrowhead (respectively), print a right-facing arrow.
Ex: If the input is:
0 1
the output is:
1
11
0000111
00001111
0000111
11
1
Answers
The program is an illustration of a sequential program.
What are sequential programs?Sequential programs are programs that do not require loops and conditional statements
The actual programThe program in Python, where comments are used to explain each line is as follows:
#This gets input for the first integer
a = int(input())
#This gets input for the second integer
b = int(input())
#The next 7 lines print the arrow head
print(b)
print(str(b)*2)
print(str(a)*4+""+str(b)*3)
print(str(a)*4+""+str(b)*4)
print(str(a)*4+""+str(b)*3)
print(str(b)*2)
print(b)
Read more about sequential programs at:
brainly.com/question/17970226
some context free languages are undecidable
Answers
Select the correct answer.
Kelly is trying to access her company fashion website through the wireless network. Even after repeated attempts, she is unable to access the
website. What must have probably happened?
ОА.
ОВ.
The network is under a war driving attack.
The network is under an eavesdropping attack.
The network is under a denial of service attack.
Ос.
OD
The network is under a frame injection attack.
The network is under a domain name cracking attack.
ОЕ.
Reset
Next
1 Edmentum. All rights reserved.
Answers
algorithm that has been coded into something that can be run by a machine.
1. algorithm
2. event
2. program
Answers
.13 LAB: Library book sorting Two sorted lists have been created, one implemented using a linked list (LinkedListLibrary linkedListLibrary) and the other implemented using the built-in Vector class (VectorLibrary vectorLibrary). Each list contains 100 books (title, ISBN number, author), sorted in ascending order by ISBN number. Complete main() by inserting a new book into each list using the respective LinkedListLibrary and VectorLibrary InsertSorted() methods and outputting the number of operations the computer must perform to insert the new book. Each InsertSorted() returns the number of operations the computer performs. Ex: If the input is:
Answers
Answer:
linkedListOperations = linkedListLibrary.InsertSorted(currNode, linkedListOperations); // this is right
linkedListLibrary.InsertSorted(currNode, linkedListOperations); // half right, it count how much operation but it doesn't store it anywhere in main.
vectorOperations = vectorLibrary.InsertSorted(tempBook, vectorOperations); // this is right
vectorLibrary.InsertSorted(tempBook, vectorOperations); // half right, it count how much operation but it doesn't store it anywhere in main.
cout << "Number of linked list operations: " << linkedListOperations << endl;
cout << "Number of vector operations: " << vectorOperations << endl;
Explanation:
The first, you are calling InsertSorted with linkedListLibrary and than you can store the number of operation inside the "linkedListOperations" variable. Then you do the same with vectorLibrary.
Which of the following is true about Main Content (MC)? Select all that apply.
True
False
Main Content should be created with time, effort, and expertise, and should not be copied from another source.
True
False
Main Content (MC) may include links on the page.
True
False
Main Content (MC) does not include features like search boxes.
True
False
High quality Main Content (MC) allows the page to achieve its purpose well.
Answers
True - Main Material should not be plagiarised and should be written with care, skill, and knowledge.
What are some examples of web content from the list below?Product brochures, user guides, slide shows, white papers, business reports, case studies, fact sheets, ebooks, webinars, and podcasts are a few examples.
Which of the following might lead you to doubt the reliability of an online source?Facts that cannot be confirmed or that are contradicted in other sources are two examples of signs that information may not be accurate. The sources that were consulted are well recognised to be biassed or unreliable. The bibliography of the sources utilised is insufficient or absent.
To know more about sheets visit:-
https://brainly.com/question/29952073
#SPJ1
Help ?i need help please

Answers
EVALUATING A HUMAN RIGHTS CAMPAIGN • Identify an organization (name) and the human right that they are campaigning for. (1+2=3) • Describe (their) FOUR possible objectives of the campaign (4x2=8) • Discuss THREE actions that you may take to get involved in a campaign (3x2=6) Evaluate the success of the campaign (indicate their successes, challenges, failures) (3x2=6) [44] 4. RECOMMENDATIONS Recommend, at least TWO practical ways by which the campaign could be assisted to ensure its successes. (2x2=4) 5. CONCLUSION In your conclusion, summarize the significance of key findings made out of your evaluation and suggest about what could be done about the findings (1x3=3)
Answers
With regards to the human rights campaign, Amnesty International's campaign for freedom of expression plays a vital role, with successes, challenges, and room for improvement through collaboration and engagement.
The explanation1. The Organization is Amnesty International
Human Right is Freedom of Expression
2. Objectives is Raise awareness, advocate for release of imprisoned individuals, lobby for protective laws, mobilize public support.
3. Actions is Join as member/volunteer, sign petitions, attend protests.
4. Evaluation is Successes include increased awareness and releases, challenges faced from governments and limited resources, failures in changing repressive laws.
5. Recommendations is Collaborate with organizations, engage influencers to amplify impact.
Conclusion - Amnesty International's campaign for freedom of expression plays a vital role, with successes, challenges, and room for improvement through collaboration and engagement.
Learn more about Human rights campaign at:
https://brainly.com/question/31728557
#SPJ1
A LinkedIn profile is required to be able to share your work experience and qualifications with potential employers.
True
False
Answers
Answer:
False
Explanation:
A LinkedIn profile is not required.