Design a greedy algorithm for the following problem. You are given n distinct points and one line L on the plane and some constant r > 0. Each of the n points is within distance at most r of line L (as measured along the perpendicular). You are to place disks of radius R centered along line L such that every one of the n points lies within at least one disk. Your algorithm should run in O (n*log n) time and use a minimum number of disks to cover all n points
Answers
Given n distinct points and one line L on the plane, and some constant\(r > 0\). Each of the n points is within distance at most r of line L (as measured along the perpendicular).
We are to place disks of radius R centered along line L such that every one of the n points lies within at least one disk. Our algorithm should run in O(n*logn) time and use a minimum number of disks to cover all n points.
Algorithm :
1. Sort the given points by their x-coordinate
2. Choose the leftmost uncovered point, p.
3. Place a disk of radius R with its center at point p.
4. Mark all points covered by this disk as covered.
5. Repeat steps 2-4 until all points are covered.
The algorithm is clearly a greedy one, which selects the leftmost uncovered point at each stage to place a disk. Since each point is covered by the disk centered at its leftmost uncovered point, the algorithm guarantees the minimum number of disks needed to cover all n points.
The algorithm's time complexity is \(O(n*logn)\) since sorting the given points takes \(O(n*logn)\) time, and selecting the leftmost uncovered point for every disk takes O(n) time, which we do n times.
To know more about perpendicular visit:-
https://brainly.com/question/12746252
#SPJ11
Related Questions
A large part of Kelly's job with a software development company is to monitor the servers to ensure that they are not overloaded by the computers that are connected to them. Kelly holds the position of __________ in the organization. Infrastructure Manager Database Administrator Support Analyst Network Administrator
Answers
Kelly holds the position of Network Administrator in the software development company.
As a Network Administrator, Kelly is responsible for monitoring and managing the company's network infrastructure, including the servers. One of Kelly's key responsibilities is to ensure that the servers are not overloaded by the computers connected to them.
In this role, Kelly is tasked with implementing and maintaining network security measures, troubleshooting network issues, and optimizing network performance.
Kelly monitors network traffic and server performance to identify potential bottlenecks or signs of overload. By analyzing network usage patterns and implementing appropriate network management techniques, Kelly ensures that the servers operate smoothly and efficiently.
Furthermore, Kelly collaborates with other IT professionals, such as system administrators and database administrators, to ensure the overall stability and reliability of the company's infrastructure.
Kelly may also participate in the planning and implementation of network upgrades and expansions to support the growing needs of the organization.
Overall, as a Network Administrator, Kelly plays a crucial role in maintaining the stability, performance, and security of the company's network infrastructure, specifically focusing on preventing server overload caused by connected computers.
For more such questions on Network Administrator,click on
https://brainly.com/question/29462344
#SPJ8
describe the 802.11a standard, and detail some of its history and advantages / disadvantages versus other 802.11 standards.
Answers
The 802.11a standard was developed as an alternative to the congested 2.4GHz frequency band and is capable of higher speeds, greater security, and reliability, and is compatible with existing 802.11 devices. However, it does have some drawbacks including a lack of backward compatibility with older 802.11 devices, limited range, and increased power consumption.
The 802.11a standard is a wireless network communication standard created by the Institute of Electrical and Electronics Engineers (IEEE) in 1999. It operates on the 5 GHz frequency band, making it a high-speed option for data transmissions, as well as providing greater security and reliability compared to other 802.11 standards. It has a theoretical maximum data rate of 54 Mbps and supports up to 8 channels.
The 802.11a standard was developed as a response to the increasingly congested 2.4GHz frequency band, which the other 802.11 standards relied on. It was designed to offer much higher speeds than 802.11b while maintaining better security and reliability than 802.11g.
Advantages of the 802.11a standard include higher speed than other 802.11 standards, greater security and reliability, and compatibility with existing 802.11 devices. Disadvantages include the lack of backward compatibility with older 802.11 devices, limited range due to operating on the 5GHz frequency band, and increased power consumption.
You can learn more about wireless standard at: brainly.com/question/13068619
#SPJ11
• Assignment. Python Programming
Cornerstone Hospital has
strike due
a
to
the reant inflation. The
Hospital is looking for Volunteers to work. Create
able to
program that is
to enter their
their name, age
work in
group of nußes
* The
in
$ allow the user
would want to
Program should be able to display the
of categories (1. Sate
a
and category they
menn
3. Tollets 4 Maternit
2. Pharmacy 3. Toilets 4
I
name, aga ad categories should be saved
arrays for later
access of data. [25]
Answers
Sure, here's an example Python program that allows the user to enter their name, age, and the category they would like to work in as a volunteer at Cornerstone Hospital. The program also saves the data in arrays for later access:
# Initialize empty arrays for name, age, and category data
name_data = []
age_data = []
category_data = []
# Define function to get user input for name, age, and category
def get_user_input():
name = input("Enter your name: ")
age = input("Enter your age: ")
category = input("Enter the category you would like to work in (1. State, 2. Pharmacy, 3. Toilets, 4. Maternity): ")
return name, age, category
# Define function to display the categories
def display_categories():
print("Categories: ")
print("1. State")
print("2. Pharmacy")
print("3. Toilets")
print("4. Maternity")
# Get user input and append to data arrays
name, age, category = get_user_input()
name_data.append(name)
age_data.append(age)
category_data.append(category)
# Display categories and user input
display_categories()
print("Name: ", name_data[0])
print("Age: ", age_data[0])
print("Category: ", category_data[0])
This program initializes empty arrays for name, age, and category data. It then defines a function get_user_input() that prompts the user to enter their name, age, and the category they would like to work in. Another function display_categories() displays the categories for the user to choose from.
The program then gets user input using get_user_input() and appends the input to the data arrays. Finally, the program displays the categories and the user input using display_categories() and array indexing.
Note that this is just an example program and can be modified to suit your specific needs.
describe how there has been a reduction of employment in offices, as workers' jobs have been
replaced by computers in a number of fields (e.g. payroll workers, typing pools, car production
workers)
Answers
Answer:
Automation is the term you are looking for. When we automate things in a business, it can reduce the amount of manual input needed to complete tasks. With the reduced need of manual input, this leads to many jobs being unnecessary. Furthermore, automation can be significantly more efficient in handling repetative tasks.
One major example of this is a stock brokerage room. In the 1980's, you'd see many people with phones, calling and making trades with other brokers. It would be loud, cluttered and a mess. However, nowadays all of these trades are done at incredibly fast speeds by computers with relatively small input from humans.
Fill in the blank: a data-storytelling narrative connects the data to the project _____.
Answers
A data-storytelling narrative connects the data to the project insights. The correct option is b.
What is data?Data is a measure of collection and accumulation that is preserved and documented for future information collection. Data comes in many varieties.
Information files are saved in an electronic computer, and everything that occurs on a computer is entered in its representation. The speed is the velocity of data that is traveling from one place to another place over the internet in calculators.
Therefore, the correct option is b, insights.
To learn more about data, refer to the link:
https://brainly.com/question/14759353
#SPJ1
The question is incomplete. Your most probably complete question is given below:
point objectives
insights
tasks
stakeholders
relevez le rôle principal de la peau dans l,organime humain. je suis bloquée aidez moi metci
Answers
Answer:
language?
Explanation:
If one of the resistors is turned off (I.e. , a light bulb goes out), what happens to the other resistors (light bulbs) in the circuit? Do they remain on? (I.e., lit)?
Answers
Answer:
No, they don't remain on because If any of bulbs in a series circuit is turned off from its socket, then it is observed that the other bulbs immediately go out. In order for the devices in a series circuit to work, each device must work. If one goes out, they all go out.
Write a step by step flowchart algorithm solution to solve the following,
A manager gets paid double the waiter tariff per hour. Enter the number of hours worked, the worker tarrif per hour and the code indicatig the type of worker (W= waiter, M= manager). If the code is M(manager) the tariff paid per hour must be doubled. Calculate and display the payment.
Answers
The step by step flowchart algorithm solution to solve the given scenario is in the explanation part.
What is algorithm?A procedure for solving a problem or performing a computation is referred to as an algorithm.
Algorithms are a precise set of instructions that perform specified actions in either hardware or software-based routines. Algorithms are widely used in all areas of information technology.
Here is a step by step flowchart algorithm to solve the problem:
StartDeclare and initialize variables: hoursWorked, workerTariff, paymentInput hoursWorked, workerTariff, and workerTypeIf workerType = "M", then set workerTariff = workerTariff * 2Calculate payment as hoursWorked * workerTariffOutput paymentStopThus, this way, one can make the required flowchart algorithm.
For more details regarding algorithm, visit:
https://brainly.com/question/22984934
#SPJ1
make a story that ends in ´ I have never found such a kind person ever since´
Answers
Lol I know this isn’t that good , but you can change it up or add stuff.
3.1.1 What type of goods are car radio and remote control.
Answers
Answer:
Radio Controlled cars .
What is the difference in the outputs that you get when you use the following operators =; == ; and ===.
Answers
Note that the = operator is used for assignment, while == is used for equality comparison. The === operator checks for strict equality, including type.
What is the rationale for the above response?The = operator assigns a value to a variable. The == operator compares values, converting types if necessary. The === operator checks for strict equality, comparing values and types. Using the appropriate operator is important for accurate comparisons and avoiding unexpected behavior in code.
Operators are important in programming as they enable the computation and manipulation of data, facilitating complex logic and functionality.
Learn more about operators:
https://brainly.com/question/29949119
#SPJ1
power steering belts should be checked for all of the following EXCEPT
Answers
You did not list the options.
The four general techniques that firewalls use to control access and enforce the site's security policy are: service control, direction control, user control, and __________ control .
Answers
The four general techniques that firewalls use to control access and enforce the site's security policy are: service control, direction control, user control, and behavior control.
Firewalls are an important tool in protecting computer networks from unauthorized access and malicious attacks. They work by monitoring and controlling the flow of network traffic between the internal network and the outside world, allowing only authorized traffic to pass through and blocking all other traffic.
Firewalls typically use four general techniques to control access and enforce the site's security policy: service control, direction control, user control, and behavior control. Service control refers to the ability of the firewall to control access to specific network services, such as email, web browsing, or file sharing. Direction control refers to the ability of the firewall to control the direction of network traffic, such as inbound or outbound traffic.
To know more about firewalls visit :-
https://brainly.com/question/13379896
#SPJ11
Which file in the /usr/lib/systemd/system/ directory is text-based and used to start the services that support multiple users and support networking
Answers
The file in the /usr/lib/systemd/system/ directory that is text-based and used to start the services that support multiple users and networking is typically named "multi-user.target". This target file defines the dependencies and configuration for services that are essential for a multi-user environment and networking functionality.
Multi-user.target is a systemd target file that defines a system state or runlevel in which the system is configured to support multiple users and networking. It is responsible for starting essential services and dependencies required for a multi-user environment.
When the system boots into the multi-user target, it ensures that services such as network managers, login managers, and other user-related services are started.
The multi-user.target file specifies the order in which these services should be started and provides the necessary configuration for managing user sessions and network connectivity in a multi-user system.
Learn more about "multi-user.target" here:
brainly.com/question/30621406
#SPJ4
What is the name of the device that allows you to speak and hear the voice of a distant person?
Answers
The device that allows you to speak and hear the voice of a distant person is called a telephone.
What is telephone ?Telephone is a device used for communication over a distance. It consists of a transmitter, which converts sound into an electrical signal, and a receiver, which converts the electrical signal back into sound. When two people speak on a telephone, their voices are transmitted through a network of wires and switching systems, allowing them to communicate without being in the same room. The telephone has been an integral part of communication since its invention in the late 19th century, and remains a vital tool for communication today.
It works by converting sound waves into electrical signals which are sent over a telephone line, and then converted back into sound waves at the other end.
To learn more about telephone.
https://brainly.com/question/28039913
#SPJ4
anaconda is an installation program that's used by fedora, rhel, and other distributions. which of the following does anaconda perform? (select three.
Answers
Identifies the computer's hardware, Creates a file system and Provides a user interface with guided installation steps does anaconda perform.
What a user interface means?The user interface of a device is the point of interaction and communication between humans and computers. Desktop monitors, keyboards, mice, and other pointing devices may fall under this category. It also describes how a user interacts with a website or program.
The user interface is the point of interaction and communication between people and computers on a gadget, website, or app. Desktop graphics, keyboards, mice, and display screens are a few examples of this.
Thus, the options are written.
For more information about user interface, click here:
https://brainly.com/question/15704118
#SPJ1
In computer security, the term "Dumpster diving" is used to describe a practice of sifting through trash for discarded documents containing sensitive data. Found documents containing names and surnames of the employees along with the information about positions held in the company and other data can be used to facilitate social engineering attacks. Having the documents shredded or incinerated before disposal makes dumpster diving less effective and mitigates the risk of social engineering attacks.A. TrueB. False
Answers
Answer:
TRUE
Hope this helps ;)
Which snippet of code is in XML?

Answers
Answer:
The top left
Explanation: It uses XML Syntax
Answer: Bottom left '<cd>'
Explanation:
PLAYTO i got it right
Helppppp meeeeee eee
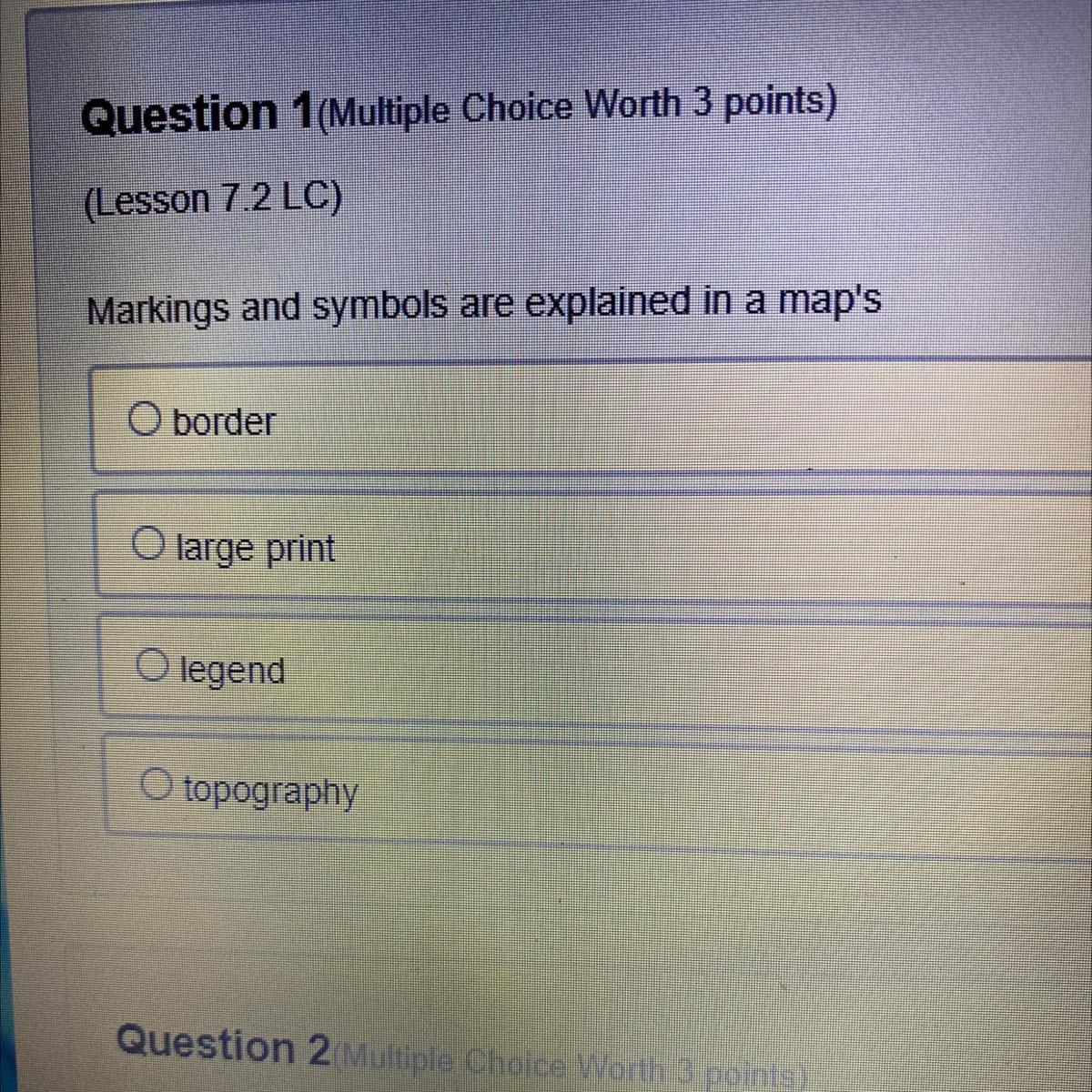
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
write any five sources of information for foreign employment.
Answers
Hope this helped!
what is the fan-out for a multi-level index where index entries are 32 bytes and index blocks are 10 kilobytes?
Answers
Approximately 300 is the fan-out for a multi-level index where index entries are 32 bytes and
index blocks are 10 kilobytes.
What is fan-out?
The number of gate inputs in digital electronics that are driven by a single logic gate's output is known as the fan-out. Logic gates are typically connected to create more complicated circuits in designs.
The largest number of identical-type gate inputs that can be connected to an output securely serves as a gauge for an output's load-driving capacity.
Therefore, Approximately 300 is the fan-out for a multi-level index where index entries are 32 bytes and index blocks are 10 kilobytes.
You can learn more about Logic gates from the given link:
https://brainly.com/question/9913122
#SPJ4
a content-filtering technique where the software that performs the filtering task is placed on individual users' computers is called
Answers
The content-filtering technique where the software that performs the filtering task is placed on individual users' computers is called client-based filtering.
Content filtering can be done in several ways. It can be done by blocking specific sites, keywords, or IP addresses. It can also be done using a content filter, which can be server-based or client-based.
The filtering technique in which filtering is performed by installing filtering software on individual users' computers is known as client-based filtering.
Client-based filtering is a content-filtering technique in which filtering software is installed on individual users' computers. The client-based filtering approach has some advantages over the server-based filtering approach.
It provides more control over user access to the internet and can be configured to filter content based on user profiles. In addition, client-based filtering can be used to enforce internet usage policies in a corporate or educational setting
Client-based filtering is a content-filtering technique in which filtering software is installed on individual users' computers.
It is a useful technique in a corporate or educational setting because it provides more control over user access to the internet and can be configured to filter content based on user profiles.
To know more about content-filtering visit:
https://brainly.com/question/31217498
#SPJ11
You have a computer that is connected to the internet through a NAT router. You want to use a private addressing scheme for your computer. Which of the following IP addresses could you assign to the computer? (Select all that apply.)10.0.12.15192.168.12.25332.188.99.10127.0.0.1240.12.188.1224.15.166.12172.18.188.67
Answers
IP addresses that you could provide the machine are 192.168.12.253, 172.18.188.67, and 10.0.12.15.
Can we use a private IP address in a private network?One public IP address is required to access the Internet, but we can utilize a private IP address on our private network. Through a single public address, NAT enables numerous devices to access the Internet.
Can all computers on my Home Network connect to the Internet?All computers on your home network can connect to the internet. You attempt to use your home computer's IP address from your office at work but are unable to connect to the server.
To know more about IP visit:-
brainly.com/question/17387945
#SPJ4
Write code which takes a user input of a String and an integer. The code should print each letter of the String the number of times the user inputted in reverse order.
Sample run:
Input a String:
code
Input an integer:
3
eeedddoooccc
Note: Write In Java
Thank You...
Answers
import java.util.Scanner;
public class JavaApplication70 {
public static void main(String[] args) {
Scanner scan = new Scanner(System.in);
System.out.println("Input a String:");
String txt = scan.nextLine();
System.out.println("Input an integer:");
int num = scan.nextInt();
String newTxt = "";
int w = 0;
for (int i = txt.length()-1; i >= 0; i--){
char c = txt.charAt(i);
while (w < num){
newTxt += c;
w++;
}
w = 0;
}
System.out.println(newTxt);
}
}
I hope this helps!
Following are the java program to input string:
Program Explanation:
Import package. Defining a class Main. Inside the class, the main method is defined. Inside the main method two String variable "val, next", and three integer variable "n,x, j" is defined. In the next step, a scanner class object is declared that inputs string and integer variable value. After input value a loop is defined that holds a sting value and define a while loop that seprate the value and calculate its value and print its value.Program:
import java.util.*;//import package
public class Main //defining a class Main
{
public static void main(String[] ar)//defining a main method
{
String val,next="";//defining a String variable
int n,x=0,j;//defining an integer variable
Scanner bd = new Scanner(System.in);//defining a Scanner class object to input value
System.out.println("Input a String:");//print message
val= bd.nextLine();//input String value
System.out.println("Input an integer:");//print message
n = bd.nextInt();//input integer value
for (j = val.length()-1; j >= 0; j--)//defining a for loop that calculate a value
{
char c = val.charAt(j);//defining a char variable that holds character value of string
while (x < n)//defining loop for compare value
{
next += c;//incrementing the character value
x++;//incrementing integer value
}
x = 0;
}
System.out.println(next);//print value
}
}
Output:
Please find the attached file.
Learn more:
brainly.com/question/18844825

Help please!! I want to make an account on Brainly for my math work but it keeps giving me the same error message: "Sorry, we were not able to complete you registration at this time." I have tried multiple usernames, emails, ages, browsers, and N O T H I N G works. Please help :,(
Answers
Answer:
You can contact the brainly support team on this one and be rest assured help is on it way brainly.com/contact/index
Explanation:
Hey there?,
I understand how bad things can get when you cant make headway and the help needed is very urgent.
Now on this issues kindly contact via brainly.com/contact/index and you will get help on whatever problems you are faced with.
Furthermore, whenever you are challenged with any online technical issues, kindly lookup for the contact detail of their support team and mail them directly and be sure to get direct response soonest.
Should you need further assistance you can ask and I will guide you.
Participating in pi planning enables teams to gain alignment and commitment around a clear set of what?
Answers
Participating in pi planning enables teams to gain alignment and commitment around a clear set of prioritized objectives.
What is planning?Planning is a form of management function, that involves thinking regarding the activities or project to be done in other to decide beforehand on things to do.
It also involves how the task or assignment is carried out to get a specified result.
Human resource to be used, materials and possible time frame are involved in planning. It is on of the major objectives in effective business or project management.
Therefore,
Participating in pi planning enables teams to gain alignment and commitment around a clear set of prioritized objectives.
Learn more on Planning below
https://brainly.com/question/25453419
#SPJ1
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
hellllllllllp i need hlel dad
Answers
Edhesive intro to CompSci Test 7 answers pls
Answers
Answer:
nothing
Explanation:
nothing
You need to manage a process in the foreground by pressing Ctrl+C on the keyboard. Which signal code is sent to the process?