e) Created in the system walkthough a) Models that describe processes without suggesting how they are conducted b) Coded logic models c) Models based upon implementing the if-then-else programming structure d) Developed by the infrastructure analyst
Answers
Answer:
d
Explanation:
Related Questions
Help please!, explain what is missing and what needs to be changed if anything.
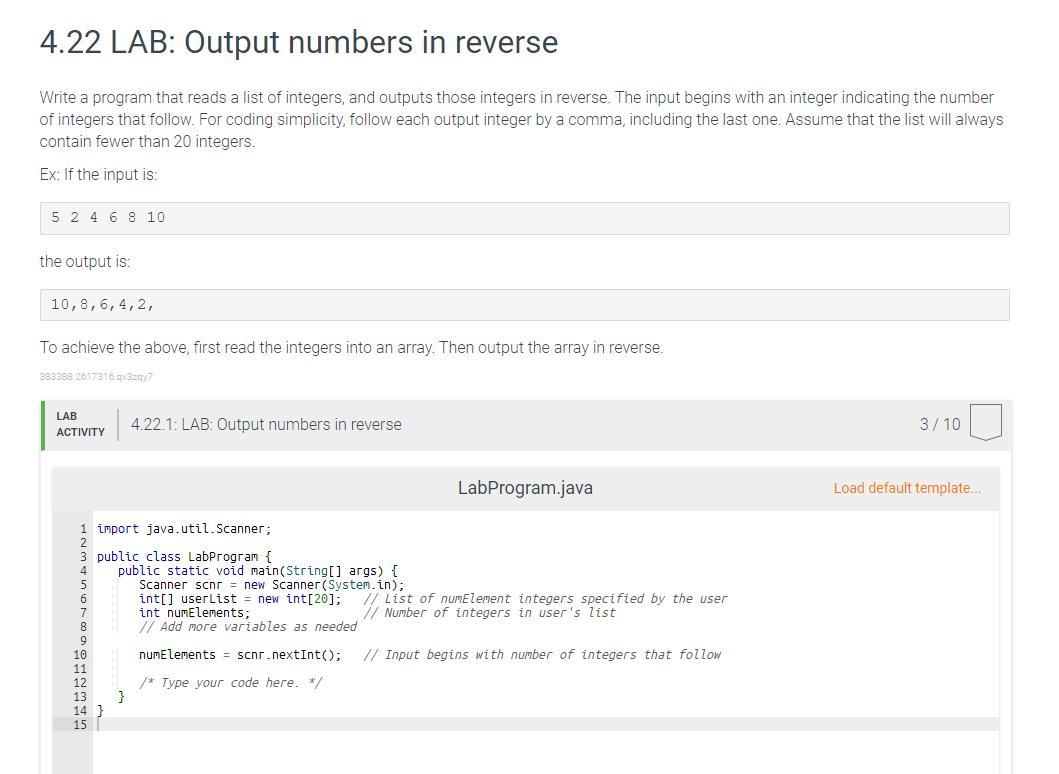
Answers
Using the computer language in JAVA to write a function code that output numbers in reverse
Writting the code in JAVA:import java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
int[] userList = new int[20];
int numElements;
numElements = scnr.nextInt();
for (int i = 0; i < numElements; ++i) {
userList[i] = scnr.nextInt();
}
for (int i = numElements - 1; i >= 0; --i) {
System.out.print(userList[i] + " ");
}
System.out.println();
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1


What Are AWS Consulting Services?
Answers
Answer:
The AWS Professional Services organization is a global team of experts that can help you realize your desired business outcomes when using the AWS Cloud.
Explanation:
We work together with your team and your chosen member of the AWS Partner Network (APN) to execute your enterprise cloud computing initiatives.
Answer:
The AWS Professional Services organization is a global team of experts that can help you realize your desired business outcomes when using the AWS Cloud.
Explanation:
We work together with your team and your chosen member of the AWS Partner Network (APN) to execute your enterprise cloud computing initiatives.
A footnote can be configured to take up a fixed number of ______ of text
Answers
Footnote just like endnotes can be formatted to have a fixed number of lines of texts.
Footnotes are used to leave reference in the text for readers to make reference too and basically placed at the bottom of the page, although with a little formatting they can come in handy despite their limitations
Footnotes generally include the
Author name, The publication title,Publication date,Publisher information with the very first citation, and a Page number.For more information on footnotes and endnotes kindly visit
https://brainly.com/question/25365614
You are a knowledge engineer and have been assigned the task of developing a knowledge base for an expert system to advise on mortgage loan applications. What are some sample questions you would ask the loan manager at a bank?
Answers
As a knowledge engineer, it should be noted that some of the questions that should be asked include:
What do you expect in the loan application process?How is the loan going to be processed?What do you expect from the applicant to fund the loan?A knowledge engineer simply means an engineer that's engaged in the science of building advanced logic into the computer systems.
Since the knowledge engineer has been assigned the task of developing a knowledge base for an expert system to advise on mortgage loan applications, he should asks questions that will be vital for the loan process.
Learn more about engineers on:
https://brainly.com/question/4231170
TRUE/FALSE 75POINTS
1 Newspapers are forms of digital media
True
False
2 Moore's Law says that every two years the speed of computers doubles.
True
False
3 Web 2.0 is place where digital media is not just received but both created and shared.
True
False
4 click farms are interactive games for web2.0 users
true
false
5 Careers in digital media have drastically declined in recent years.
True
False
Answers
Newspapers are forms of digital media is a false statement.
Moore's Law says that every two years the speed of computers doubles is a true statementWeb 2.0 is place where digital media is not just received but both created and shared is a true statement.The click farms are interactive games for web2.0 users is a false statement.Careers in digital media have drastically declined in recent years is a false statement.What are the types of newspaper media?A newspaper is known to be a kind of a Print Media. Note that it is said to be the oldest media forms and they are known to be newspapers, magazines, journals and others.
Also, Moore's Law is said to be one that states that the amount of transistors on a processor chip will become a double portion every 18 month
Therefore, Newspapers are forms of digital media is a false statement.
Moore's Law says that every two years the speed of computers doubles is a true statementWeb 2.0 is place where digital media is not just received but both created and shared is a true statement.The click farms are interactive games for web2.0 users is a false statement.Careers in digital media have drastically declined in recent years is a false statement.Learn more about Newspapers from
https://brainly.com/question/26027924
#SPJ1
on a client server network clients and servers usually require what to communicate?
Answers
Answer:
A connectivity device. Your colleague, in describing the benefits of a client/server network, mentions that it's more scalable than a peer-to-peer network.
Explanation:
(4 marks)
(d) Outline the steps involved in inserting a picture from a file in a word processing document using
copy and past
Answers
Answer:
HELLO IAM LOKESH IAM NEW PLEASE SUPPORT ME
whats your favorite rocket leage carr???????????????????????????? comment if there is already 2 answers brainleist for first
Answers
Answer:
hello
Explanation:
Octane is my favorite
thx for the points
Upon returning from a year long working holiday, Alberta, the youngest of 4 sisters, announced her whirlwind marriage. Her 3 sisters, Carla, Paula, and Roberta,
were amazed by her husband's name.
• The 4 men are Albert, Carl, Paul, and Robert. Their last names are Albertson, Carlson, Paulson, and Robertson.
• No woman's husband has a first name that consists of her first name without the final "a"; no woman's last name consists of her first name without the final
"a" and with "son" on the end; and, no man's last name consists of his first name with "son" added at the end.
• Paul is not married to Roberta, and Robert is not married to Paula.
• No husband and wife have "bert" in both their first names, but there is a man who has "bert" in his first and last names.
Carl's last name is not Paulson.
Work out Alberta's husband's first and last name, as well as Carla's, Paula's, and Roberta's husbands' first and last name
Answers
The couples, considering the patterns in the problem, are listed as follows:
Carla and Robert Paulson.Paula and Albert Robertson.Alberta and Paul Carlson.Roberta and Carl Albertson.What are the couples?We use the information from the bullet points to find the couples.
The first information is:
No woman's husband has a first name that consists of her first name without the final "a".
Hence:
Alberta is married to either Carl, Paul or Robert.Carla is married to either Albert, Paul or Robert.Paula is married to either Albert, Carl or Robert.Roberta is married to either Albert, Carl or Paul.The second information is:
Paul is not married to Roberta, and Robert is not married to Paula.
Hence:
Roberta is married to either Albert or Carl.Paula is married to either Albert or Carl.No husband and wife have "bert" in both their first names, hence:
Roberta is married to Carl.Paula is married to Albert.Alberta is married to Paul.Carla is married to Robert.No woman's last name consists of her first name without the final "a" and with "son" on the end, and no man's last name consists of his first name with "son" added at the end, hence:
Roberta and Carl are either Albertson or Paulson.Paula and Albert are either Carlson or Robertson.Alberta and Paul are either Carlson or Robertson.Carla and Robert are either Albertson or Paulson.There is a man who has "bert" in his first and last names, hence either of these two can be couples.
Carla and Robert Albertson.Paula and Albert Robertson.Carl's last name is not Paulson, hence a couple is:
Carla and Robert Paulson.
Then Carla and Robert are Paulson, and the couples are:
Carla and Robert Paulson.Paula and Albert Robertson.Alberta and Paul Carlson.Roberta and Carl Albertson.More can be learned about patterns at https://brainly.com/question/18941199
#SPJ1
In Microsoft windows which of the following typically happens by default when I file is double clicked
Answers
Answer:
when a file is double clicked it opens so you can see the file.
Explanation:
How many tasks should an effective to-do list have?
Answers
A to-do list is a straightforward yet effective tool for managing and arranging chores.
Thus, A to-do list can assist you in setting priorities for your time and concentrating your efforts on the most crucial tasks by detailing what has to be done. You can use to-do lists to keep track of your progress and make sure that everything gets done on time. To-do lists can also be distributed to others to encourage teamwork and guarantee that everyone is on the same page.
A to-do list is a vital tool for remaining organized and ensuring that all of your chores are accomplished, whether you're leading a team or managing a personal project.
This template can be used by an individual to keep track of their own tasks or by a team.
Thus, A to-do list is a straightforward yet effective tool for managing and arranging chores.
Learn more about To do list, refer to the link:
https://brainly.com/question/32132186
#SPJ1
A web administrator notices a few security vulnerabilities that need to be addressed on the company Intranet site. The portal must force a secure browsing connection, mitigate script injection, and prevent caching on shared client devices. Determine the secure options to set on the web server's response headers.
Answers
Answer: Set a Cache-Control header to 0 to prevent caching on client browsers. Set a Strict-Transport-Security header to 31536000 (1 year) to force the client to remember to only connect to the server with HTTP(S) secure. Lastly, set a Content Security Policy(CSP) HTTP header to tell the client what sources it can load scripts or images from and how to handle the execution of JS that is on the page which can allow to mitigate script injection.
Explanation:
Cache-Control is a server response header that controls how long a browser should have cache for before it becomes stale. Setting it 0 tells the browser that it should never cache.
Strict-Transport-Security is a server response header that tells the client that after the first initial visit; that the browser should remember to only connect to it via HTTPS for the time that was set by header.
Content Security Policy (CSP) is a policy and also a header that can be in the response of a server that explains to the browser the limitations of content that can be loaded. Examples include: images, videos, JS sources, etc. The policy can also tell the browser that only an ad analytics software should be the only script that can run thus mitigating any other scripts that may be injected onto the site.
how can you say that a painting is real?

Answers
Answer:Know the Artist. Prior to buying an artist's work, become familiar with their oeuvre. ...
Use a Magnifying Glass. Looking at the surface of a painting with a magnifying glass is one of the best ways to spot a print. ...
Turn the Painting Over.
Explanation:brainliest
See from the way they paint. You can see from the picture that its way different. Each artist has different way to paint. see the colour also
jss 1 computer text book
Answers
Note that the generation of computers that used integrated Circuit are called the Second Generation computers. (Option B)
What about Second Generation computers?Throughout the late 1950s and 1960s, a second-generation computer had circuit boards loaded with individual transistors and magnetic-core memory.
These computers remained the standard design until the late 1960s, when integrated circuits appeared, resulting in the third-generation computer.
It was created in 1947 at Bell Labs by three people: William Shockley, Walter Houser Brattain, and John Bardeen.
Unlike the previous generation of computers, the second generation computers employed assembly language rather than binary machine language.
Learn more about second generation computers at:
https://brainly.com/question/31492021
#SPJ1
Full Question:
Which generation was used integrated Circuit?
answer choices
First Generation
Second Generation
Third Generation
Fourth Generation
Which of these options is an example of a nested structure?A.
for loop
B.
while loop
C.
if-then-else loop
D.
if else inside a for loop
Answers
Answer:
D. if else inside a for loop
Explanation:
We would like the set of points given in the following figure into 1D space. The set of points has been
generated using this instruction [X, y = make_moons(n_samples = 100)], where X are the 2D features
and y are the labels(blue or red).
How to do that while keeping separable data point with linear classification? Give the
mathematics and the full algorithm.
How to apply the SVM algorithm on this data without dimension reduction? Give the
mathematics and full algorithm.
Answers
One way to project the 2D data points onto a 1D space while preserving linear separability is through the use of a linear discriminant analysis (LDA) technique. LDA finds the linear combination of the original features that maximizes the separation between the different classes.
What is the mathematics in SVM algorithm?The mathematics behind LDA involve finding the eigenvectors of the within-class scatter matrix and the between-class scatter matrix and selecting the eigenvector that corresponds to the largest eigenvalue. The full algorithm for LDA can be outlined as follows:
Compute the mean vectors for each class
Compute the within-class scatter matrix (SW) and the between-class scatter matrix (SB)Compute the eigenvectors and eigenvalues of the matrix (SW⁻¹SB)Select the eigenvector that corresponds to the largest eigenvalue as the linear discriminantProject the original data onto the new 1D space using the linear discriminantRegarding the SVM algorithm, it can be applied directly to the original 2D data without the need for dimension reduction. The mathematics behind SVM involve finding the hyperplane that maximizes the margin, or the distance between the closest data points of each class, while also ensuring that the data points are correctly classified.
The full algorithm for SVM can be outlined as follows:
Select a kernel function (e.g. linear, polynomial, radial basis function)Train the model by solving the optimization problem that maximizes the marginUse the trained model to classify new data points by finding the hyperplane that separates the different classesIt is important to note that, in case of non-linearly separable data, SVM algorithm uses the kernel trick to map the original data into a higher dimensional space, where the data is linearly separable.Learn more about algorithm from
https://brainly.com/question/24953880
#SPJ1
What is the name of the big hole in the ground in Northern Arizona
Answers
Answer:
is that sink hole, I think it is
Write code that outputs variable numTickets. End with a new line (Java) output 2 and 5
Answers
Answer:
public class Main {
public static void main(String[] args) {
int numTickets = 2;
System.out.println(numTickets);
numTickets = 5;
System.out.println(numTickets);
}
}
Assume aList is a valid ArrayList containing the following string values:
apple, orange, grape, kiwi, watermelon, peach, banana
When the following statement executes, what does aList contain?
aList.set(3, "lemon");
A.apple, orange, grape, kiwi, lemon, peach, banana
B.apple, orange, grape, lemon, watermelon, peach, banana
C.apple, orange, grape, kiwi, lemon, watermelon, peach, banana
D.apple, orange, lemon, grape, kiwi, watermelon, peach, banana
E.apple, orange, grape, kiwi, watermelon, peach, banana, lemon, lemon, lemo
Answers
If aList is a valid ArrayList containing the given string values. Then, aList will contain B. apple, orange, grape, lemon, watermelon, peach, banana.
What is the reasoning behind this answer?
The statement aList.set(3, "lemon") replaces the element at index 3 in the list with the value "lemon". In this case, the element at index 3 is "kiwi", so after executing the statement, the list will contain "apple, orange, grape, lemon, watermelon, peach, banana".
What is ArrayList?
ArrayList is a dynamic data structure in Java that implements the List interface and provides resizable arrays to store elements. It is a commonly used collection for storing and manipulating a large number of elements, allowing to add, remove, access and modify elements by their index efficiently. ArrayList is also known for its flexibility, as it can store elements of any object type.
To learn more about ArrayList, visit: https://brainly.com/question/20464124
#SPJ4
The computer that is used in scientific research is ........
Answers
Answer:
supercomputers are the computer that is used in scientific research.
Answer:
super computer is the right answer
Posting pictures everyday of all the things you eat would most likely be considered
Answers
1. Write a program that asks the user to enter a string. The program should then print the following: (a) The total number of characters in the string (b) The string repeated 10 times (c) The first character of the string (remember that string indices start at 0) (d) The first three characters of the string (e) The last three characters of the string (f) The string backwards (g) The seventh character of the string if the string is long enough and a message otherwise (h) The string with its first and last characters removed (i) The string in all caps (j) The string with every a replaced with an e
Answers
Answer:
s = input("Enter a string: ")
print(len(s))
print(s*10)
print(s[0])
print(s[:3])
print(s[len(s)-3:])
print(s[::-1])
if len(s) >= 7:
print(s[6])
else:
print("The string is not long enough")
print(s[1:len(s)-1])
print(s.upper())
print(s.replace("a", "e"))
Explanation:
*The code is in Python.
Ask the user to enter a string
Use len method to get the total number of characters
Use "*" to repeat 10 times
Use index, 0, to get first character
Use slicing to get first three characters
Use slicing to get last three characters
Use slicing to get it in backwards
Check if the length is greater than or equal to 7. If it is, use index, 6. Otherwise, print a message.
Use slicing to remove first and last characters
Use upper method to get it in all caps
Use replace method to replace the "a" with the "e"
The program that ask the user to enter a string and print the (a) The total number of characters in the string (b) The string repeated 10 times (c) The first character of the string (remember that string indices start at 0) (d) The first three characters of the string (e) The last three characters of the string (f) The string backwards (g) The seventh character of the string if the string is long enough and a message otherwise (h) The string with its first and last characters removed (i) The string in all caps (j) The string with every a replaced with an e
is as follows:
x = str(input("please enter a string: "))
print(len(x))
print(x*10)
print(x[0])
print(x[0:3])
print(x[-3:])
print(x[::-1])
if len(x) >= 7:
print(x[6])
else:
print("The string is not up to length 7")
print(x[1:-1])
print(x.upper())
print(x.replace('a', 'e'))
The first line ask the user for a string input.
Print length of the user input
Print the user input ten times.
Print the first value of the user input
print the first three string
Print the last three string
Print the reverse of the string
if the length of the user input is greater than or equals to zero, then print the 7th term of the user input.
else it will print that the string length is not up to seven.
Remove the first and the last term of the user input and print the remaining user input.
print the uppercase of the user input.
Replace a with e in the user input.
learn more on python here: https://brainly.com/question/20202506?referrer=searchResults
Question 7 of 10
What is a good way to turn an interview into a human interest story?
A. By presenting two people as one
B. By making up some information
C. By presenting the whole interview
D. By identifying a key quotation
SUBMIT
Answers
The ultimate way to convert an interview into a riveting human interest story is by pinpointing the central citation or story that encapsulates the quintessence of the interviewee's predicament or outlook.
How can this be done?This can act as the keystone for your tale, and interned throughout to provide the narrative plot.
It is crucial to feature the full encounter, though solely including the most pertinent and stirring sections. It is never permissible to fabricate details or coalesce two figures together. In consequence, the emphasis should be on narrating a companionable and fascinating story that reveals the personae element of the interviewee's tale.
Read more about interviews here:
https://brainly.com/question/8846894
#SPJ1
What is cybersecurity? Cybersecurity refers to the protection of hardware?

Answers
Cybersecurity is the practice of safeguarding computer systems, networks, and mathematical data from unauthorized approach, theft, damage, or additional malicious attacks.
What is cybersecurity?It involves the use of differing technologies, processes, and practices to secure digital maneuvers, networks, and data from a wide range of dangers, including cybercrime, cyber-spying, cyber-terrorism, and different forms of malicious endeavor.
While cybersecurity does involve protecting fittings, it also involves looking after software, networks, and digital dossier. In addition to protecting against external warnings, etc.
Learn more about cybersecurity from
https://brainly.com/question/28004913
#SPJ1
How many NOTS points are added to your record for not completely stopping at a stop sign?
Answers
In some jurisdictions, failing to stop at a stop sign can result in a citation for running a stop sign or a similar violation. In other jurisdictions, it may be categorized as a failure to obey traffic signals or a similar violation. The number of NOTS points added to your record, if any, will depend on the specific violation charged and the point system used by the jurisdiction in question.
It's important to note that NOTS points are used to track and measure the driving record of a driver, and they may impact insurance rates and license status. It's always a good idea to familiarize yourself with the laws and regulations in your area and drive safely to reduce the risk of violations and penalties.
problem description IT
Answers
In IT, a problem description refers to a clear and concise explanation of an issue or challenge that needs to be resolved within a technology system or application.
How is this so?It involves providing relevant details about the symptoms, impact, and context of the problem.
A well-written problem description outlines the specific errors, failures, or undesired behavior observed and provides enough information for IT professionals to analyze and identify potential solutions.
A comprehensive problem description is crucial for effective troubleshooting and problem-solving in the IT field.
Learn more about Problem Description at:
https://brainly.com/question/25923602
#SPJ1
what is data abstraction and data independence?
Answers
Data abstraction and data independence are two key concepts in computer science and database management systems. They are closely related and aim to improve the efficiency, flexibility, and maintainability of data management.
What is data abstraction and data independence?The definitions of these two are:
Data Abstraction:
Data abstraction refers to the process of hiding the implementation details of data and providing a simplified view or interface to interact with it. It allows users to focus on the essential aspects of data without being concerned about the underlying complexities. In programming languages, data abstraction is often achieved through the use of abstract data types (ADTs) or classes.
By abstracting data, programmers can create high-level representations of data entities, defining their properties and operations.
Data Independence:
Data independence refers to the ability to modify the data storage structures and organization without affecting the higher-level applications or programs that use the data. It allows for changes to be made to the database system without requiring corresponding modifications to the applications that rely on that data. Data independence provides flexibility, scalability, and ease of maintenance in database systems.
Learn more about data at:
https://brainly.com/question/179886
#SPJ1
Which of the following are types of computer hardware? Select all that apply.
Keyboard
Hard drive
Ram
No answer text provided.
Firefox
O Microsoft Windows
Answers
Answer:
hard drive
Explanation:
ram : software
key board :in put
IMPORTANCIAS de las ticc
Answers
Las TIC permiten a las empresas comunicarse, compartir informacion y recopilar datos de manera mas rapida, barata y eficiente. Esto reduce los costos operativos, mejora la productividad y aumenta la competitividad en el mercado.
What is comunicarse ?Comunicarse is the Spanish verb meaning "to communicate." It is used to describe the act of exchanging ideas, thoughts, information, or feelings between two or more people. Communication can be verbal or nonverbal, or a combination of both. It is an important part of interpersonal relationships and can be used to build trust and understanding.
Communication also helps us to connect with other people and create meaningful relationships. Through communication, we can learn about each other and develop meaningful connections. By communicating effectively, we can resolve conflicts, share ideas, and make decisions. Comunicarse is an important tool for fostering healthy relationships and better understanding.
To learn more about comunicarse
https://brainly.com/question/24540334
#SPJ1
what is similarity and difference between cluster computing and hadoop ecosystem?
Answers
Answer:
A cluster is simply a combination of many computers designed to work together as one system. A Hadoop cluster is, therefore, a cluster of computers used at Hadoop. Hadoop clusters are designed specifically for analyzing and storing large amounts of unstructured data in distributed file systems.