for a range query, the hash index can significantly reduce the i/o costs compared to the b tree index T/F
Answers
False. Hash indexes are not suitable for range queries because they only support exact match lookups. On the other hand, B-tree indexes are optimized for range queries. They store the data in a sorted order, and each node in the B-tree contains multiple keys and pointers to child nodes.
By traversing the B-tree, a range query can quickly locate all the records that fall within a specified range of values. In contrast, a hash index uses a hash function to map keys to a specific location in memory. This makes hash indexes very efficient for exact match lookups, but they don't provide any ordering on the keys.
Therefore, it's not possible to perform a range query by traversing a hash index. Instead, a range query would require scanning the entire table, which can be very expensive in terms of I/O costs. In summary, B-tree indexes are the preferred choice for range queries because they support efficient traversal of the data in a sorted order. Hash indexes are better suited for exact match lookups but are not appropriate for range queries.
Learn more about hash index here-
https://brainly.com/question/29575888
#SPJ11
Related Questions
Type the correct answer in the box. Spell all words correctly. Define the term semiconductor. A semiconductor is a material that can carry an electric current between a ______and an insulator.
Answers
The correct answer to complete the sentence is conductor.
A semiconductor is a material that can carry an electric current between a conductor and an insulator.
What is a conductor?A conductor is a material which allows the easy passage or flow of electricity through it.
What is an insulator?Insulators are materials that do not allow the passage of electricity to pass through it.
Learn more about conductors and insulator:
https://brainly.com/question/11845176
what is computer give definition
Answers
Answer:
computer is
an electronic device for storing and processing data, typically in binary form, according to instructions given to it in a variable program.
Choose one answer for each statement, whether it is True or False:
a) CPU stands for Computer Processing Unit
b) The CPU processes all of the data and instructions that make a computer system work
c) The CPU carries out the fetch-decode-execute cycle
d) The clock speed, number of processor cores and cache size all affect CPU performance
Answers
b) true
c) true
d) true
execute or non-execute some of Javascript statements according to condition expression result.................
Answers
Answer:
execute
Explanation:
Computerized machines have taken the place of most __________.
A.
teachers
B.
IT specialists
C.
order clerks
D.
graphic designers
Answers
Answer:
B??
Explanation:
I feel like B. is the correct answer.
If i'm wrong plz let me know :>
Answer:
B
Explanation:
A(n) _____ is a computerized system by which subscribers are able to communicate to all other subscribers by sending a transmission to one address
Answers
Answer: Listerv
Explanation:
Create a flowchart that will accept 10 whole numbers one at a time and print the highest and the lowest. Use Switch.
Answers
I will create a sequence of steps that would accept 10 whole numbers one at a time and print the highest and the lowest in Java:
Import javax.swing.JOptionPane;
public class loop_exer2 {
public static void main(String agrs[])
{ String input; int trial=10, sc=0, h=0, l=0, test=0;
System.out.print("Scores: ");
for (int ctr=1;ctr<=10;ctr ) {
input=JOptionPane.showInputDialog("Enter the Scores [" trial "] trials "); sc=Integer.valueOf(input); System.out.print(sc ", ");
if(test==0){h=sc;l=sc;test=1;}
if(sc>h){h=sc;}
else if(sc>h){
h=sc; {
else if(sc<1) {
l=sc;
}
JOptionPane.showMessageDialog (null, "Highest score is:" h "Lowest score is:" l);
System.out.println();
System.out.println ("Highest score is: " h);
System.out.println ( "Lowest score is: "l);
}
}
What is a Flowchart?This refers to a diagram which is used to represent the various steps which a system uses to create a step by step solution.
From the above code, there is the command to accept whole numbers in String and then request for them one at a time and after the computation, display the highest and lowest numbers.
Read more about flowcharts here:
https://brainly.com/question/6532130
What causes the 'AnyConnect was not able to establish a connection to the specified secure gateway' Error Message?
Answers
Incorrect client settings you may encounter the Any Connect was unable to establish a connection to the specified secure gateway Windows error if the client and VPN connections are configured incorrectly.
What is VPN server?
There are numerous causes of common issues like Cisco AnyConnect VPN Login Failed. The most frequent root cause of this issue is the VPN client's failure to connect to the VPN server.
Among the causes of this include incorrect VPN configurations, firewall configuration issues, or issues with network connectivity. when attempting to access the Campus VPN services through a browser using the Web VPN gateway, the Cisco Any Connect software, or an incorrect or invalid login and password combination.
To learn more about Error Message from given link
brainly.com/question/15349056
#SPJ4
Which of the following specifies the format and appearance of page content on webpages?
A. URL
B. HTML
C. JavaScript
D. CSS
Answers
The option that specifies the format and appearance of page content on webpages is D. CSS.
CSS, which stands for Cascading Style Sheets, is a styling language used to describe the presentation of a document written in HTML. It allows web developers to control the layout, fonts, colors, and other visual aspects of webpages. By using CSS, you can separate the structure (HTML) from the presentation (CSS), making it easier to manage and update the styling of multiple webpages. CSS provides a wide range of selectors, properties, and values that enable precise control over the look and feel of web content, resulting in visually appealing and consistent designs across different devices and browsers.
Know more about webpages here:
https://brainly.com/question/12869455
#SPJ11
write a letter to your future self :”Imagining a world in 2030”.Be sure to mention things that you think your future self would probably be doing and experiencing in daily life. You may include your hobbies, your surroundings, the role of AI in your life, etc.
Answers
To write a letter to your future self, follow the steps:
Start with an introduction in the first paragraph.The next is what you want your future self to know in the second paragraph.The last is conclusion in the third paragraph.What is a Letter?A letter is known to be a form of a written message that passes information from a person to another.
Note that by following the steps above, one can be able to write a letter to your future self.
Learn more about letter from
https://brainly.com/question/24140747
#SPJ1
Match each of the following software categories to its primary use:
I. entertainment
II. enterprise resource planning
III. database
IV. video-editing
V. word processing
a. manage back end business functions
b. write and edit documents
c. play games
d. edit movies
e. keep track of clients
Answers
question 9 when examining the permissions on a file in linux you find the the first four bits are -rwx. what does this mean?
Answers
In Linux, file permissions are represented by a series of ten characters. The first character represents the file type, and the remaining nine characters represent the permissions for the owner, group, and others.
four characters of the permission string represent the read, write, and execute permissions for the owner of the file. In the case of "-rwx", this means that the owner has read, write, and execute permissions for the file.
The "r" character represents read permission, the "w" character represents write permission, and the "x" character represents execute permission. If a particular permission is not granted, it is represented by a "-" character.
So, in this case, the file is readable, writable, and executable by its owner, but the permissions for the group and others are not known based on the given information.
Learn more about information here:
https://brainly.com/question/3100288
#SPJ11
Emilee is watching an online video. The video is being sent to her laptop by a server over the Internet which splits the video into packets and sends them in the order they appear in the video. Which of the following is true about how the packets will arrive at her computer? *
Answers
Answer:
D. The packets may arrive out of order
Explanation:
The packets may arrive out of order, because some may take different pathways. Some paths being sorter and some being longer, causing a delay in when the packets are received.
The possibility of packet data arriving out of order is true.
When sending information from one computer to another through a server, the information being sent is called data and they are broken down into smaller chunks called packets.
These packets of data the move through internet severs along different pathways which are usually very different with unequal pathways.
Hence, data packets which travels through shorter pathways arrive their destination first before those on the longer trail.
Hence, packets are not always received in the order in which they were sent.
Explaining the other options :
Packets aren't sent back when they arrive out of order but are reassembled by the receiving computer. The fact that a certain data packet does not reach their destination does not mean all other data packet will not.Hence, the true statement is that data packet may arrive their destination out of order.
Missing Options from the question :
A. The packets will always be received in the order that they were sent
B. Either every packet will reach her computer or none of them will.
C. Packets that arrive out of order will be sent back to the server.
D. The packets may arrive out of order
Learn more : https://brainly.com/question/18729589?referrer=searchResults
In databases, null values are not equivalent to zero.a. Trueb. False
Answers
In databases, null values and zero values are not equivalent. A null value represents the absence of any value, while zero is a value. Null values are used to indicate missing or unknown data, whereas zero is a specific numerical value. In SQL, the comparison of null values with any other value or null value returns a null result.
For example, if we try to compare a null value with zero using the "=" operator, the result will be null, indicating that the comparison is unknown. To handle null values in databases, we can use the "IS NULL" or "IS NOT NULL" operators to check whether a value is null or not. In summary, null values are distinct from zero values in databases, and they should be treated differently in database operations.
.
Hi! I'm happy to help you with your question. The answer is:
a. True
In databases, null values are not equivalent to zero. Null values represent the absence of any value or data in a specific field, whereas zero is a numeric value. It is important to understand this distinction when working with databases, as treating null values and zero as equivalent may lead to incorrect results in queries or calculations.
To know more about null value visit:
https://brainly.com/question/30655755
#SPJ11
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
This and the next four questions go together and are worth a total of ten points. Consider the following first-order knowledge base: Vx Dog(x) A Wet(x) = Smelly(x) Dog(Snoopy) Which of the following sentences can be derived using only the Universal Instantiation inference rule? Dog(Snoopy) Smelly(Snoopy) Dog(Snoopy) A Wet(Snoopy) = Smelly(Snoopy) Dog(x1) A Wet(x1) = Smelly(x1) QUESTION 21 Consider the following first-order knowledge base: Vy Bird(Tweety) A [Birdiy) = Fliesty}] Which of the following sentences can be derived using only the Universal Instantiation inference rule? Bird(Tweety) A [Bird Tweety) = Flies(Tweety)] Bird(71) = Flies(1) Bird(Tweety) = Flies(Tweety) Flies(Tweety)
Answers
The first knowledge base's "Dog(Snoopy)" sentence may be produced using simply the Universal Instantiation inference rule. "Bird(Tweety)" is the sentence from the second knowledge base.
that can be obtained only using the Universal Instantiation inference rule. As "Dog(Snoopy)" is the only globally quantified statement in the initial knowledge base, it is the only sentence that can be derived using just the Universal Instantiation inference rule.
As "Bird(Tweety)" is the only globally quantified statement in the second knowledge base, it is the only sentence that can be generated using just the Universal Instantiation inference rule. Knowledge is frequently interpreted as factual awareness or as practical abilities, but it may also represent familiarity with things or circumstances. The term "knowledge of facts," also known as "propositional knowledge," refers to a real belief that may be distinguished from an opinion or educated guess by the use of evidence.
learn more about Knowledge here:
https://brainly.com/question/28025185
#SPJ4
+10 POINTS AND BRAINLIEST!! HELP ME PLEASE!!~~~
Which statement describes what happens when a user configures No Automatic Filtering in Junk Mail Options?
No messages will ever be blocked from the user’s mailbox.
Messages can still be blocked at the server level.
Messages cannot be blocked at the network firewall.
Most obvious spam messages will still reach the client computer.
Answers
Answer:
its D. most obvious spam messages will still reach the clients computer.
Explanation:
i got a 100 on the test on edge 2020.
Answer: D. Most obvious spam messages will still reach the client computer.
Explanation:
__________ are among the most important elements of internet security.
Answers
Encryption and firewalls are among the most important elements of Internet security. Encryption protects your data by scrambling it so that it can only be understood by someone with the key to decrypt it. Whereas, a firewall is a security feature that restricts access to your device and network
Encryption is the process of converting plaintext into ciphertext, making it unreadable without the appropriate key. This technology has the potential to keep your sensitive information safe from cybercriminals and other malicious individuals. Firewalls, on the other hand, can be hardware or software, and they function by examining the data passing through them and blocking anything that appears suspicious. Firewalls can provide an added layer of security to your network by allowing only authorized users to access it. The use of encryption and firewalls is critical to internet security. Without these measures in place, sensitive information such as personal data and financial details would be vulnerable to theft and misuse. Providing an additional layer of protection, encryption, and firewalls help to ensure that internet users are safe and secure. In conclusion, encryption and firewalls are essential components of internet security as they protect sensitive information and restrict unauthorized access to devices and networks.
Learn more about Internet security: https://brainly.com/question/28004913
#SPJ11
________ are programs that attach themselves to legitimate programs. Group of answer choices Direct-propagation worms Worms Payloads Viruses
Answers
Answer:
Worms / Viruses / Trojan Horse Virus
Explanation:
A worm is a standalone program that can self-replicate and spread over a network. Unlike a virus, a worm spreads by exploiting a vulnerability in the infected system or through email as an attachment masquerading as a legitimate file.
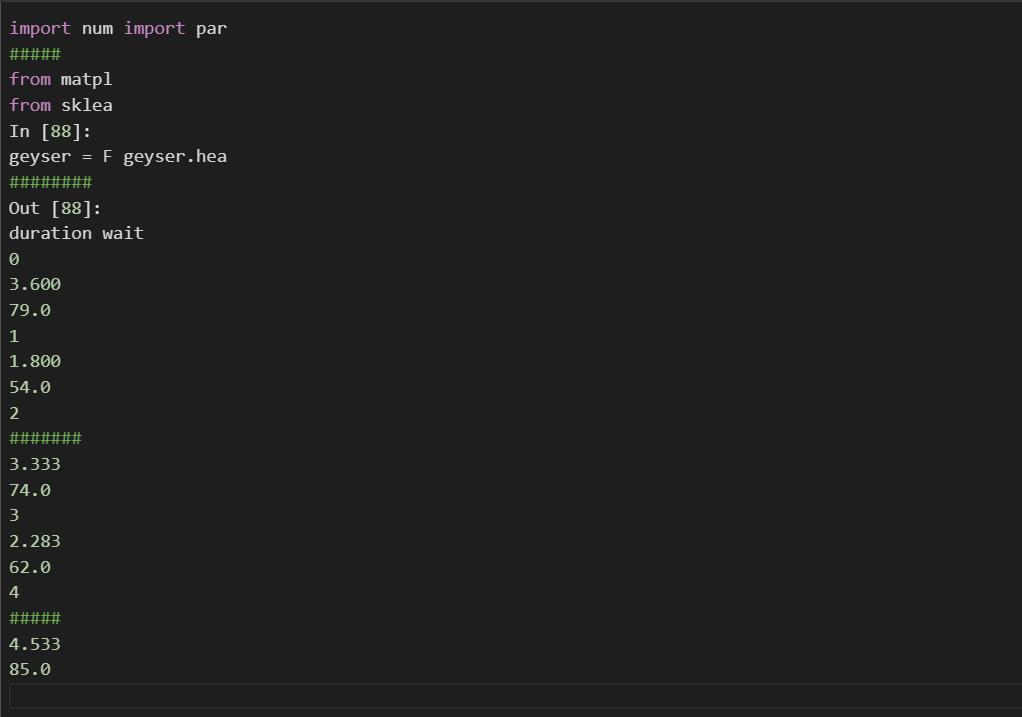
task-4: compute the eruption duration in standard units and append it as a new column named duration (standard units) to the dataframe geyser. also, compute the waiting times in standard units and append it as a new column named wait (standard units) to the dataframe geyser. after appending the 2 new columns successfully, print the first 5 rows of the dataframe geyser to the output.
Answers
Using the knowledge in computational language in C++ it is possible to write a code that compute the eruption duration in standard units and append it as a new column named duration.
Writting the code:import num import par
#####aa
from matpl
from sklea
In [88]:
geyser = F geyser.hea
########
Out [88]:
duration wait
0
3.600
79.0
1
1.800
54.0
2
#######
3.333
74.0
3
2.283
62.0
4
#####
4.533
85.0
What is matplotlib and example?Matplotlib is a cross-platform, data visualization and graphical plotting library for Python and its numerical extension NumPy. As such, it offers a viable open source alternative to MATLAB. Developers can also use matplotlib's APIs (Application Programming Interfaces) to embed plots in GUI applications.
See more about C++ at https://brainly.com/question/29632676
#SPJ1
6.3 code practice edhisive
You should see the following code in your programming environment:
Import simplegui
Def draw_handler(canvas):
# your code goes here
Frame = simplegui.creat_frame(‘Testing’ , 600, 600)
Frame.set_canvas_background(“Black”)
Frame.set_draw_handler(draw_handler)
Frame.start()
Use the code above to write a program that, when run, draws 1000 points at random locations on a frame as it runs. For an added challenge, have the 1000 points be in different, random colors.
Answers
Answer:
import simplegui
import random
def draw_handler(canvas):
for x in range(1000):
colorList = ["Yellow", "Red", "Purple", "White", "Green", "Blue", "Pink", "Orange"]
c = random.choice(colorList)
x = random.randint(1,600)
y = random.randint(1,600)
canvas.draw_point([x, y], c)
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("Black")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
I used a for loop, setting my range to 1000 which is how you create exactly 1000 points. Next, I defined my color array, my x randint value, and my y randint value. I set both the x and y randint values to 1 - 600 since the frame is 600x600. The rest is pretty self explanatory.
Alright Brainly I need you to ask me some random funny questions PLZ THANK YOU
Answers
Answer:
ok bet
Explanation:
if a king farts, is it a noble gas?
Write a function named spell_name that takes in a string name as parameter, and returns a list where each character in the name is an item in the list. In your main program, call this function and print the returned list.
For example:
spell_name("Jessica") should return ['J', 'e', 's', 's', 'i', 'c', 'a']
Be sure to:
include comments for all functions that you create.
validate any user inputs using try-except-else-finally and/or if-else.
validate all parameters passed to functions you write using try-except-else-finally and/or if-else.
(30 points)
Answers
"""
Takes in a string name as parameter, and returns a list where each character in the name is an item in the list.
"""
# Create an empty list to store the characters of the name
name_list = []
# Iterate over each character in the name and append it to the list
for char in name:
name_list.append(char)
# Return the list of characters
return name_list
# Ask the user for input
name = input("Please enter a name: ")
# Call the spell_name function and print the returned list
try:
name_list = spell_name(name)
print(name_list)
except:
print("Error: invalid input")
Where are 'if' and 'else' statements shown when printing a document in a word processor?
Answer the question and then your task is to:
Write an algorithm or sequence of instructions that include the IF statement for the document being printed.
Answers
Explanation:
cpt price
Question at position 5 a mathematician develops a program to solve systems of linear equations. When they use distributed computing techniques to run the program on two computers in parallel, they find a speedup of 2. In this case, what does a speedup of 2 indicate? a mathematician develops a program to solve systems of linear equations. When they use distributed computing techniques to run the program on two computers in parallel, they find a speedup of 2. In this case, what does a speedup of 2 indicate? the program completed in two minutes less time with two computers versus one computer. The program completed in half the time with two computers versus one computer. The program completed in twice as much time with two computers versus one computer. The program completed in two minutes more time with two computers versus one computer
Answers
A speedup of 2 means that the program completed in half the time with two computers versus one computer. Speedup is a measure of how much faster a program runs on multiple processors compared to a single processor, and a speedup of 2 indicates that the program runs twice as fast on two processors as it does on a single processor.
What does speedup of 2 indicateA speedup of 2 in this case indicates that the program completed in half the time with two computers versus one computer. Speedup is a measure of how much faster a program runs when executed on multiple processors compared to a single processor. A speedup of 2 means that the program runs twice as fast on two processors than on a single processor. In other words, if the program takes T time to complete on a single processor, it takes T/2 time to complete on two processors.
Learn more on processor here;
https://brainly.com/question/474553
#SPJ1
What is Sectigo RSA Organization Validation Secure Server CA?
Answers
It enables clients (internet users) and a website (server) to securely exchange a secret encryption key for the purpose of secure communication. However, the client must first confirm the identity of the server before keys may be exchanged.
Who is secure server?Secure servers are ones that shield communication from unauthorised recipients using the secure sockets layer protocol. Secure servers, often known as SSL servers, use cryptography, or encrypted and decrypted communication, to connect to other Web servers and Web browsers.
DigiCert ECC Secure Server CA: What is it?An intermediate SSL certificate is provided by the DigiCert certificate authority and is called the DigiCert ECC Secure Server CA Certificate (CA). It is an intermediary certificate that connects the DigiCert root certificates to your SSL server certificate.
To know more about Secure Server visit:
https://brainly.com/question/11179161
#SPJ4
1 Think about the five steps to writing an algorithm. Why is each step necessary?
2 Why is it important to be precise when writing computer code?
3 Some problems are better solved by a computer and some are better solved by humans. How do you know when a problem should be solved by a computer or by a person?
Answers
Answer and Explanation:
1. The steps in writing an algorithm include:
Step 1: obtain description of problem
Step 2: Analyze the problem. ...
Step 3: Develop a high-level algorithm.
Step 4: Refine the algorithm by adding more detail. ...
Step 5: Review the algorithm
In describing our problem we aim to define our problem and know exactly what problem we are looking to solve. We analyze and breakdown this problem to know where it begins and ends and therefore be able to understand it and develop algorithm to solve it. A high level algorithm is developed to fInd the main part of the problem and leave the details for later . We refine our algorithm and give more detail to further algorithm. We go ahead to review our algorithm to be sure it would solve the problem and ask questions like does it solve the problem and how much? Can the algorithm be simplified?
2. Computers are machines and therefore only understand instructions in the form of code languages. Coding must be precise because there is particular syntax and semantics in computer coding languages which if not followed cannot be understood by the computer
3. When a problem is repetitive and tedious at same time, it should be coded into computer programs and therefore automated
…..is the smallest size in audio files
Answers
Answer:
Wav files can be 16 bit,8 kHz (i.e 128 k bits per second) while mp3 could be compressed to 16 kbits per second. Typically wav is x10 larger than mpg. This is ratio is highly content specific. Wav is a raw format, while mp3 is a compressed format for audio.
Explanation:
Answer:
Wav files can be 16 bit,8 kHz (i.e 128 k bits per second) while mp3 could be compressed to 16 kbits per second. Typically wav is x10 larger than mpg. This is ratio is highly content specific. Wav is a raw format, while mp3 is a compressed format for audio.
What is the key sequence to copy the first 4 lines and paste it at the end of the file?
Answers
Press Ctrl+C after selecting the text you want to copy. Press Ctrl+V while holding down the cursor to paste the copied text.
What comes first in the copy and paste process for a slide?Select the slide you wish to copy from the thumbnail pane, then hit Ctrl+C on your keyboard. Move to the location in the thumbnail pane where you wish to paste the slide, then hit Ctrl+P on your keyboard.
What comes first in the copying process of a segment?The secret to copying a line segment is to open your compass to that segment's length, then mark off another segment of that length using that amount of opening.
To know more about copy visit:-
https://brainly.com/question/24297734
#SPJ4
excel is an example of an application software, as opposed to the operating system, which is a secondary level of an application software? true or false
Answers
It is accurate what is said. The operating system is a lower-level of application program, whereas excel is an example of application software.
What are some examples of application software?An application program, often known as a software application, application, or app, is a type of computer program used by end users that is created to do a particular purpose that is unrelated to the operation of the computer. Examples include accountancy software, media players, and word processors. When a person interacts directly with application software (App), it can carry out specified tasks for them. The only goal of application software is to assist the user in carrying out specific tasks. Applications software that is often used includes media players, office productivity suites, data management systems, and security programs. Examples include the typical mobile applications we use every day.To learn more about application software, refer to:
https://brainly.com/question/28224061