For which programming task would you use a for loop?
Computing the average of a list of integers of unknown length
Counting the vowels in a document of unknown length
Generating a list of the anagrams in a word
Printing a specified number of integers in a list
Answers
Answer:
printing a specified number of integers in a list
Related Questions
Cheri needs to write a small program that interacts with the user. What step will allow her to do this?
Answers
Answer:
B. giving step by step directions
Explanation:
I did this as an assignment. Hope this helped :)
Which of the following replicates real-world events to save researchers time and money in planning for the future?
Augmented reality
Computer simulation
Problem-solving
Virtual reality
Pls answer quick.
Answers
Answer: Computer Simulation
Explanation: Computer Simulations save researchers time and money for the future because it allows them to recreate possible events that can happen in the real world (like diseases or natural disasters) in order for them to be prepared for something like that to actually happen and be able to research about it beforehand.
Why isn't my brainly post being answered?
Answers
Try deleting then reposting, it may not always pop up in new questions, I will have a look at the question anyway.
Hope this helps!
If you want the words “My puppy is a poodle” to appear in the interpreter. What code should you use?
A.
create "My puppy is a poodle"
B.
execute ("My puppy is a poodle")
C.
print("My puppy is a poodle")
D.
print "My puppy is a poodle"
Answers
Answer: Probably C
(also, C and D say the same thing)
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2
NO LINKS!! HELP!! ESSAY DUE TODAY!!!

Answers
Answer:
To the "Am not 13"
Explanation:
Amy Bernstein wrote a story, which is titled "I'm Not Thirteen Yet." The story is told from the perspective of one of the characters, making it a personal narrative. The story's author describes his personal experiences throughout the narrative. 'I had entered the world of teenagers, and I wasn't even one of them yet,' says the author, demonstrating that he is writing about his own experiences.
Is a poster the best media form to make a call to action to the government and major corporations? What other media forms could be effective?
Answers
Answer:
A Poster can be an effective media form to make a call to action to the government and major corporations, as it allows for visually impactful messaging. However, other media forms could also be effective, such as:
Social media campaigns: Utilize platforms like Twitt..er, Fa..cebook, or Ins..tagram for awareness and mobilization.Online petitions: Collect signatures and demonstrate public support.Video campaigns: Engage viewers emotionally through compelling videos.Mass media advertising: Utilize TV, radio, or print media for broader reach.Advocacy websites: Provide information, resources, and a platform for action.Public demonstrations and rallies: Gather supporters for visible advocacy.Answer:
Explanation:
Online petitions: Collect signatures and demonstrate public support.Video campaigns: Engage viewers emotionally through compelling videos.Mass media advertising: Utilize TV, radio, or print media for broader reach.Advocacy websites: Provide information, resources, and a platform for action.Public demonstrations and rallies: Gather supporters for visible advocacy.Which statements correctly compare and contrast the Cut and Copy commands in PowerPoint? Check all that apply.
O Both use galleries to carry out tasks.
O Both are options found in the mini toolbar.
O Both use the Paste command to move text.
O Only the Cut command removes the text from its location.
O Only the Copy command stores information on the clipboard.
Answers
Answer:
If there are only two options, they are:
--- Both are options found in the mini toolbar.
--- Only the Copy command stores information on the clipboard.
If there can be three options, they are:
--- Both are options found in the mini toolbar.
--- Only the Copy command stores information on the clipboard.
--- Only the Cut command removes the text from its location.
Which type of cyber crime offender requires the highest percentage of risk management in terms of computer monitoring?
A) Sex offenders
B) Identity thieves
C) Low-Risk offenders
D) hackers
Answers
Answer: D
Explanation: Hackers are the only type of cyber criminal that monitors your computer
How do the text feature help on the text?
Answers
Answer:
Text features help you locate important information in a text. Knowing the purpose of the text feature helps you decide at which text feature to look when you want to understand your text better. Organized by purpose, the chart identifies text features and how they help the reader.
Explanation:

Match List
Match each term to its definition.
Put responses in the correct input to answer the question.
Correct answers:
1
a value that can be passed to a function
2
a group of instructions that can be used to organize a program or perform a repeated task
3
a value that can be passed from a function back to the calling part of a program

Answers
Parameter - A value … function
Function - A group
Answer:
parameter: a value that can be passed to a function
function: a group of instructions that can be used to organize a program or perform a repeated task
return value: a value that can be passed from a function back to the calling part of a program
Explanation:
Open the NetBeans IDE and create a new project named MySizes.java. Your program should do the following:
Declare and initialize an int variable for the comparison expression (waist measurement).
Assign a value to the variable to be used as the customer’s response for the program.
Create a switch-case statement that includes three cases and a default statement. Use appropriate conditional operators ( =, >) to define the three case comparisons.
Create output lines for each case, stating the appropriate pant size.
Create a default statement if the customer waist measurement does not match any case.
Then, Create nested if statements that accomplishes the same results.
( I really need this for a project, it doesn't need to be correct it just needs to look like it is, this is in Java )
Answers
Explanation:
Open the NetBeans IDE and create a new project named MySizes.java. Your program should do the following:
Declare and initialize an int variable for the comparison expression (waist measurement).
Assign a value to the variable to be used as the customer’s response for the program.
Create a switch-case statement that includes three cases and a default statement. Use appropriate conditional operators ( =, >) to define the three case comparisons.
Create output lines for each case, stating the appropriate pant size.
Create a default statement if the customer waist measurement does not match any case.
Then, Create nested if statements that accomplishes the same results.
( I really need this for a project, it doesn't need to be correct it just needs to look like it is, this is in Java )
The commands available from a menu may change as a result of a user's actions. True False .
Answers
i guess it may depend on the context but if someone where to get in trouble they may get privileges taken away so i think the answer is true (not 100% sure)
Nascar has inserted an image into his document but needs the image to appear on its own line Which option should he choose?
Answers
Answer:
Explanation:
you want to first right click the picture and then click on wrap text then you want to press tight
Answer:
Top and Bottom
Explanation:
!!!!PLEASE HELP!!!!! You get to play journalist today. The topic of your story is one of the laws discussed in this lesson. You will select one of them to research. While researching, you will learn more about the law and will locate a case that went to court. Then you will write an unbiased article or broadcast describing the law and summarize the case and the stand of the parties involved. Be sure to review and abide by The Cannons of Journalism. Be sure to include:
a description of the law;
how the law relates to digital media;
one example of a case that went to court;
a discussion of the case and the parties involved; and
a summary of the outcome of the case.
Some helpful hints in finding a case are:
Search for “case law,” “court case examples,” and “case studies.”
Include the full name of the law and the acronym.
Discuss the impact these laws have on one or more media outlets in your community.
You will write your report as an article with at least 500 words that will be posted on an online news site or that a broadcast journalist will report on TV news.
Upload your 500-word story that describes one law, including how it relates to digital media, and summarizes a case that went to the courts and the stand of the parties involved.
Answers
Title: The Digital Privacy Act: Safeguarding Personal Information in the Digital Age
Date: [Insert Date]
Byline: [Your Name]
[City Name] - In an era of rapidly advancing technology and widespread digital connectivity, protecting personal information has become a paramount concern. The Digital Privacy Act, a legislation introduced to address these concerns, aims to safeguard individuals' privacy rights and regulate the handling of personal data in the digital realm.
The Digital Privacy Act, formally known as the Personal Information Protection and Electronic Documents Act (PIPEDA), was enacted in [Insert Year]. This federal law governs how private sector organizations collect, use, and disclose personal information in the course of commercial activities. It establishes rules and principles for obtaining consent, ensuring transparency, and safeguarding personal data from unauthorized access or disclosure.
In the realm of digital media, the Digital Privacy Act plays a crucial role in governing the practices of online platforms, social media networks, and e-commerce websites. It requires organizations to obtain informed consent when collecting personal information, inform individuals of the purpose for its collection, and implement appropriate security measures to protect sensitive data from breaches or unauthorized use.
One prominent case that exemplifies the intersection of the Digital Privacy Act and digital media is the landmark lawsuit of Doe v. SocialMediaCo. In this case, Jane Doe, a user of a popular social media platform, filed a complaint against the company for unauthorized disclosure of her personal information.
According to court documents, the plaintiff alleged that SocialMediaCo, without her consent, shared her private messages with third-party advertisers, resulting in a breach of her privacy. The case brought into focus the importance of user consent and the responsibility of online platforms in protecting personal information.
During the trial, the plaintiff argued that the actions of SocialMediaCo violated the provisions of the Digital Privacy Act. She contended that the company failed to obtain proper consent and did not adequately safeguard her personal data, leading to emotional distress and reputational harm.
On the other hand, SocialMediaCo maintained that their practices were in compliance with the Digital Privacy Act. They argued that users implicitly consented to the sharing of their information with third-party advertisers through the platform's terms of service agreement.
After careful deliberation, the court ruled in favor of Jane Doe, emphasizing the importance of explicit consent and the duty of organizations to protect user privacy. The court found SocialMediaCo liable for the unauthorized disclosure of personal information and awarded damages to the plaintiff.
The outcome of the case set a precedent for other digital media companies, reinforcing the need for stringent privacy practices and ensuring compliance with the Digital Privacy Act. It also served as a reminder to individuals about the importance of understanding privacy policies and exercising caution when sharing personal information online.
As we navigate the digital landscape, the Digital Privacy Act stands as a crucial safeguard, protecting individuals from the potential risks associated with the collection and use of personal data. It places the responsibility on organizations to respect privacy rights, obtain informed consent, and prioritize the security of sensitive information.
In an ever-evolving digital world, the Digital Privacy Act serves as a shield, empowering individuals to assert their rights and reinforcing the notion that personal information deserves protection, both offline and online.
I hope this helps. Cheers! ^^
Part 1: Compare the Websites
You are conducting research for a project about elephant sanctuaries. Compare the two websites using the 5 W’s criteria for reliability and validity. For each website, complete the 5 W’s Checklist.
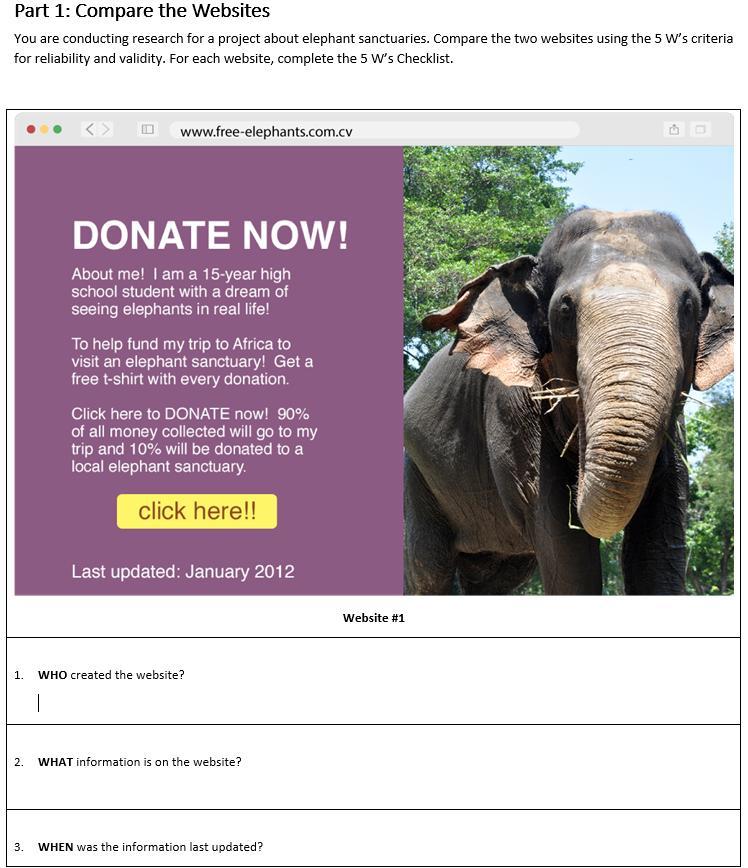




Answers
Answer:
WHO: a 15-year old high school student
WHAT: information about donating to a local elephant sanctuary and a trip
WHEN: January 2012
WHERE: www.free-elephants.com.cv
WHY: To help fund the student's trip to Africa to visit an elephant sanctuary
who: a 15-year-old high school student
what: information about donating to a local elephant sanctuary and a trip
when: January 2012
where: www.free-elephants.com.cv
why: To help fund the student's trip to Africa to visit an elephant sanctuary
(I made this up teehee) what anime is katski bakugo from
Answers
~ I already know this ~ who was the bits victim in five nights at freddys 4
___10 points___
Answers
Answer:
i dont know anything about them only that the bear is the ducks son and the duck is the fox mom.
Explanation:
For which task is the WordArt gallery most useful?
making a list
creating a table
designing a title
Formatting a paragraph
Answers
The right to make others do things is referred to as _________.
a.
Power
b.
Authority
c.
Compliance
d.
Vision
Please select the best answer from the choices provided
Answers
Answer:
I think B hope its right
The correct option is b. authority.
The information regarding the authority is as follows:
It is the power or the right to give the orders. It is the power or right to make the decisions.Also, it is the right to make others for doing the things. In this, the decisions are carried out, rules & regulations are enforced by having the authority.Therefore we can conclude that the option b is correct.
Learn more: brainly.com/question/17429689
In what ways can information be slanted in a news report? List at least five ways.
Answers
Answer:
author, journalist and speaker/media trainer this is all I know so
author, journalist and speaker/media trainer
Author and journalist
How does a resident virus differ from a non-resident virus? !!!25 POINTS!!!!!
A) Resident viruses simply disrupt operations while non-resident viruses will control hosts.
B)Resident viruses will control hosts while non-resident viruses simply disrupt operations.
C)Resident viruses find networks to infect while non-resident viruses load themselves into memory.
D)esident viruses load themselves into memory while non-resident viruses find networks to infect.
Answers
Answer:
The correct answer is **D)** Resident viruses load themselves into memory while non-resident viruses find networks to infect. A resident virus is a type of computer virus that’s deployed and resides within a computer’s random access memory (RAM). A non-resident computer virus, on the other hand, is a type of computer virus that doesn’t reside within a computer’s RAM. Non-resident computer viruses can still be deployed within RAM, but they don’t stay there.
what software is my teacher using to do this and how can i stop her from doing this

Answers
Answer:
I’m not sure if you can only teachers can acess that
Explanation:
In 1 to 2 sentences, describe how to create a list with bullets
Answers
Answer:
To create a bulleted list:
Select the text you want to format as a list.
On the Home tab, click the drop-down arrow next to the Bullets command. A menu of bullet styles will appear.
Move the mouse over the various bullet styles. ...
The text will be formatted as a bulleted list.
Explanation:
~Hope this helps
Answer:
the person above is correct i got 100% give him brainly Est
Explanation:
Question: How do you file a complaint using a food restaurant? 100 POINTS WILL BE GIVEN INCLUDING BRAINLIEST
Answers
send it through the mail
Answer: Be prepared to provide the following information:
1.Your Name, Address and Phone Number (your information will remain anonymous to the restaurant)
2.Name of restaurant
3.Location/address of the restaurant
4.Date of incident
5.Nature of complaint
If you suspect you became ill from this incident. You will need to give specific information about the suspected foods that made you sick, as well as when your symptoms began, and what they were. In addition, you will need to give a 3-day food eating history.
Explanation
HELP ASAP!!!!!!!! GIVING 8 POINTS OR 16 POINTS FOR BRAINLIEST!!!!!!! Which of the following are goals of e-government? Check all of the boxes that apply.
(A) to have a secure website.
(B) to sell things online.
(C) to be able to protect the personal information of the other people who use the site.
(D) to make information about the government available.
(E) to be able to stop having meetings.
Answers
Why is a repeat command helpful when programming a turtle?
A. it gives input B. it engages memory C. it saves time when writing code D. it rotates objects
Answers
Answer:
C. it saves time when writing code
Explanation:
A repeat command (also known as a loop) is a programming statement that allows a block of code to be executed repeatedly for a specified number of times. When programming a turtle, a repeat command can be very helpful because it allows the same set of commands to be executed multiple times without having to write them out repeatedly. This can save a lot of time and make the code much shorter and easier to read.
For example, if a programmer wants a turtle to draw a square, instead of writing out the commands to move the turtle forward, turn right, move forward, turn right again, and so on, they can use a repeat command to tell the turtle to perform those same commands four times. This makes the code much more efficient and easier to read, and can help prevent errors that might occur if the programmer had to write out the same commands multiple times.
Answer:
c
Explanation:
A large company has extensive downtown office space with many conference rooms. To lower their electric bill, the company has installed a new system that automatically turns off the heat and lights in a conference room when no one is in the room. What is the simplest explanation for how the system works?
A camera in each room is connected to the security desk. When the officer on duty sees that a room is empty, they turn off the heat and lights in that room.
A small robotic device on wheels knows the building layout. It roams the offices, peeking into each conference room to see if anyone is using it. If not, the robot turns off the lights and heat.
A sensor detects and reports on movement in the room. If there is no movement for a few minutes, the system assumes the room is empty and turns off the heat and lights.
Every hour, the system emits a loud sound in each room. Pressing a large red button in the middle of the table turns off the sound in that room. If nobody does so within 30 seconds, the system turns off the heat and lights.
Answers
The simplest explanation for how the system works is option C: a sensor detects and reports on movement in the conference room. If there is no movement for a few minutes, the system assumes the room is empty and turns off the heat and lights.
What is the office space about?The system that automatically turns off the heat and lights in a conference room when no one is in the room is commonly referred to as an occupancy sensor. An occupancy sensor uses various technologies, such as infrared or ultrasonic, to detect the presence or absence of people in a room.
Therefore, Once the sensor detects that no one is in the conference room, it sends a signal to the control system, which then turns off the heat and lights. When someone enters the room again, the sensor detects their presence and sends a signal to turn the heat and lights back on. This system is designed to save energy by ensuring that heating and lighting are only used when needed.
Learn more about office space from
https://brainly.com/question/28885269
#SPJ1
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain. ( USE C.E.R *Claim, Evidence, Reasoning* )
Answers
I think the pros of digital recordings outweigh the cons! I prefer digital audio recordings over analog audio recordings because analog recordings require more financing and preservation. Compared to digital recordings, analog recording equipment is more expensive and the tape deteriorates over time. Which to me personally, doesn't seem to be worth the amount of effort since it's such a process to go through. You can possibly go into debt due to that. Digital recording equipment, on the other hand, is more affordable. It's less time-consuming and although it does have its disadvantages, they're minor. Digital recordings can be stored online. Its data get corrupted? You can get it back! It won't cost you anything.
Question 1 (1 point)
This geographic network type has data transmitted securely through a private tunnel over an unsecure network?
Question 1 options:
Local Area Network
Virtual Private Network
Wide Area Network
Personal Area Network
Question 2 (1 point)
Which networking device learns all ports and then sends incoming data to selected ports on the same network?
Question 2 options:
Hub
Router
Wireless Router
Switch
Question 3 (1 point)
Which topology type has all devices directly connected to a centralized hub or switch?
Question 3 options:
Bus
Tree
Star
Ring
Question 4 (1 point)
Which topology type allows data to travel through the network in either one direction or both directions at the same time?
Question 4 options:
Mesh
Bus
Star
Ring or Dual Ring
Question 5 (1 point)
Which geographical network type has a distance of 33 feet to 10 meters?
Question 5 options:
Metropolitan Area Network
Personal Area Network
Local Area Network
Wide Area Network
Question 6 (1 point)
Which networking devices forward incoming data between computer networks
Select 2 correct answer(s)
Question 6 options:
Hub
Switch
Router
Wireless router
Question 7 (1 point)
The wireless router functions the same at a router but can also act as a wireless access point.
Question 7 options:
True
False
Question 8 (1 point)
Which networking device broadcasts all incoming data to all active ports on the same network?
Question 8 options:
Router
Switch
Hub
Wireless Router
Question 9 (1 point)
Which type of network shares information and devices but has no centralized control?
Question 9 options:
Peer to Peer
Client/Server
Wide Area Network
Storage Area Network
Question 10 (1 point)
Which geographic network type has a distance of 5 to 50 kilometers and typically uses fiber optics for increased speed?
Question 10 options:
Wide Area Network
Personal Area Network
Local Area Network
Metropolitan Area Network
Answers
Answer:
I'm not 100% on the answers . . .
Explanation:
1. A, 2. C, 3. D, 4. A, 5. D, 6. A & B, 7. False, 8. D, 9. D, 10. D