How did the change from water power to steam power influence British industries?
Steam engines meant the railroads could transport goods for trade.
Steam engines ensured that iron could be turned into steal.
Answers
Steam engines revolutionized British industries through improved transportation and increased industrial production.
What are the primary benefits of cloud computing for businesses?Steam engines revolutionized British industries by providing a more efficient and reliable source of power compared to water power. They had a significant impact in two key ways:
Transportation: Steam engines powered the development of railroads, enabling faster and more reliable transportation of goods. This facilitated the growth of trade and the expansion of markets, as goods could be transported more quickly and over longer distances. Industrial production: Steam engines powered machinery in factories, allowing for increased productivity and efficiency. This led to the mechanization of various industries, such as textiles, mining, and manufacturing. The availability of steam power enabled larger-scale production and the development of new technologies, contributing to the Industrial Revolution in Britain.Therefore, the shift from water power to steam power played a crucial role in transforming British industries, facilitating trade, improving transportation, and driving industrialization.
Learn more about British industries
brainly.com/question/887296
#SPJ11
Related Questions
Can someone help me on a 60 second ringtone :(

Answers
Answer:
If you have an apple phone, its as easy as importing it into Garage Band, cutting it to size, and exporting it as a ringtone or even a text tone. My text tone is now Megalovania.
A type of operating system embedded into devices, such as cars and consumer devices is called ____________."
Answers
Answer:
Embedded operating system
Explanation:
An operating system is a system software pre-installed on a computing device to manage or control software application, computer hardware and user processes.
This ultimately implies that, an operating system acts as an interface or intermediary between the computer end user and the hardware portion of the computer system (computer hardware) in the processing and execution of instructions.
Generally, there are different types of operating systems (OS) used for specific purposes and these are;
1. Batch Operating System.
2. Multitasking/Time Sharing OS.
3. Multiprocessing OS.
4. Network OS.
5. Mobile OS.
6. Single User OS.
7. Distributed OS.
8. Embedded or Real Time OS.
An embedded operating system (OS) is also referred to as Real Time OS and it can be defined as a specialized type of operating system designed and embedded into electronic devices, such as cars, automated teller machines (ATMs), traffic lights, digital televisions, point-of-sale (POS) machines, smart watches, digital camcorders, GPS navigation systems, etc. Thus, they're designed to perform specific function(s) or task(s) in microcontroller based electronic devices.
Some examples of embedded operating system (OS) are Arduino, Symbian, Windows mobile/CE, Unison OS, Raspberry PI, Nuttx, iOS, Palm OS, QNX, RTX, etc.
The Universal Serial Bus (USB) standard specifies that type A connectors can be attached to: (Select 2 answers)
Answers
The Universal Serial Bus (USB) standard specifies that Type A connectors can be attached to personal computers and USB hubs. Type A USB plugs are used to attach peripheral devices to a computer system in these situations
.A USB is a standard interface that is widely used in electronic devices, including computers, to transfer data between two devices. It was created to simplify the number of interfaces used on computers, and the standard has evolved over time to include more features that allow it to be used for a variety of purposes.
Type A USB connectors can be seen on the vast majority of USB cables and peripherals. They are the most common USB connector on the market, and most computers have Type A USB ports. They are used to connect a variety of devices, including external hard drives, keyboards, and mice, to computers or USB hubs. Type A USB connectors have been around for a long time and are widely supported. As a result, they have become the industry standard for USB connectors.
To know about Universal Serial Bus (USB) visit:
https://brainly.com/question/31365967
#SPJ11
Visit a shoot location for any video or film and observe the ongoing activities. Based on your observation, answer the following questions. If you’re unable to visit an actual shoot location, you can perform online or offline resources to answer the questions below.
What was the approximate size of the crew on the shoot? (Alternatively, what is the average crew size on a film shoot?)
What is the role of the director?
What is the role of a cameraman or cinematographer?
What is the role of the light technicians and assistants?
What does the makeup man do?
Was there a stylist on the shoot? What did he or she do?
Answers
Finding actual sites to act as the imaginary locations mentioned in a film's screenplay is known as location scouting. The correct setting aids the story and contributes to the creation of a believable world in films.
What does filming on location entail?Location filming is simply shooting outside of a studio in the actual location where the story takes place. A soundstage is a space or building that is soundproof and utilized for the creation of movies and television shows.
How can I locate my shooting location?For assistance, get in touch with the film commission or your local government office. They can aid in locating potential shooting sites for your movie. For a list of locations that are offered to filmmakers, you may also check out location-scouting websites.
to know more about shooting here:
brainly.com/question/10922117
#SPJ1
explain the verbal method of communication
Answers
Answer:
verbal method of communication means using kaomji, emojis gifs and stickers although you know how to use the keyboard.
Answer:
The Verbal Communication is a type of oral communication wherein the message is transmitted through the spoken words. Explanation: Here the sender gives words to his feelings, thoughts, ideas and opinions and expresses them in the form of speeches, discussions, presentations, and conversations.
on a network such as the one illustrated in the accompanying figure, what kind of computer controls access to the hardware, software, and other resources on the network and provides a centralized storage area for programs, data, and information?
Answers
The computer that controls access to the hardware, software, and other resources on the network and provides a centralized storage area for programs, data, and information is called a server.
A server is a computer system designed to handle requests from other computers or devices (called clients) on a network. In a client-server architecture, the server is responsible for managing and distributing resources and services to clients. Some common types of servers include:
File servers: store and manage files that can be accessed by multiple clients on the network.Print servers: manage and distribute print jobs to printers on the network.Database servers: store, manage and retrieve data from databases.Web servers: host websites and serve web pages to clients upon request.Application servers: host applications and provide access to them for clients.Servers typically have more powerful hardware, larger storage capacity and are optimized for 24/7 operation compared to client computers. They play a crucial role in network infrastructure by providing centralized management and control of resources, as well as improved reliability, security, and scalability for networked computing environments.
To learn more about servers, use the link:
brainly.com/question/30168195
#SPJ4
Assume you are given an int variable named nPositive and a two-dimensional array of ints that has been created and assigned to a2d. Write some statements that compute the number of all the elements in the entire two-dimensional array that are greater than zero and assign the value to nPositive.
Answers
Answer:
public class Main
{
public static void main(String[] args) {
int nPositive = 0;
int[][] a2d = {{-7,28, 92}, {0,11,-55}, {109, -25, -733}};
for (int i = 0; i < a2d.length; i++) {
for(int j = 0; j < a2d[i].length; j++) {
if(a2d[i][j] > 0){
nPositive++;
}
}
}
System.out.println(nPositive);
}
}
Explanation:
*The code is in Java.
Initialize the nPositive as 0
Initialize a two dimensional array called a2d
Create a nested for loop to iterate through the array. If an element is greater than 0, increment the nPositive by 1
When the loop is done, print the nPositive
Answer:
const a2d = [[7,28, 92], [0,11,-55], [109, -25, -733]];
let nPositive = a2d.reduce((a,c) => a + c.filter(n => n>0).length, 0);
console.log(nPositive);
Explanation:
Just for fun, I want to share the solution in javascript when using the powerful list operations. It is worthwhile learning to understand function expressions and the very common map(), reduce() and filter() primitives!
a pneumatic lockout/tagout uses a _________ to prevent use .
Answers
Answer:
Lockable Valve
Explanation:
A pneumatic lockout/tagout typically uses a lockable valve to prevent the use of machinery or equipment.
Python plese help 4.2 projectstem
it keeps saying error
pet=input("What pet do you have? ")
c=1
while(pet!="rock"):
print("You have a " + pet + " with a total of " + str(c) + " pet(s)")
pet = input("What pet do you have?")
c = c + 1


Answers
Answer: while(pet!="stop"):
Explanation:
here was my code for that lesson
pet = input("What pet do you have? ")
total = 0
while pet!="stop":
total+=1
print("You have one " + pet + ". Total # of Pets: " + str(total))
pet = input("What pet do you have? ")
which new console should i buy Nintendo switch Xbox series x or a ps5
Answers
Answer:
you should buy the xbox series x, it has better quality and xbox is just better in general
Explanation:
Answer:
get the PS5 it showed off the gameplay and unreal engine 5 that I saw has better graphics.
meanwhile the new Xbox has shown one gameplay is halo but the graphics are not good . but I don't know how the new xbox 12tfop can't past the PS5 10.2 t fop
Soo 10.2 t fop is better than 12tfop.
Vince recently received the hash values of malicious software that several other firms in his industry found installed on their systems after a compromise. what term best describes this information?
Answers
A term which best describes the hash values of malicious software that several other firms in Vince's industry found installed on their systems after a compromise is: B. IoC.
What is a malware?A malware can be defined as any type of software program or file that is designed and developed to be intentionally harmful to the host computer, server, website, or network, especially for the purpose of wreaking havoc and destruction such as a Trojan, Rootkit, etc.
What is an IoC?An IoC is simply an abbreviation for indicator of compromise and it can be defined as an artifact which is found in an operating system (OS) or observed on a computer network, and as such serves as as forensic evidence of potential intrusions.
This ultimately implies that, an indicator of compromise (IoC) serves as a sign of malicious activity in an operating system (OS) or observed on a computer network.
In this context, we can reasonably infer and logically deduce that a terminology which best describes the hash values of malicious software that several other firms in Vince's industry found installed on their systems after a compromise is IoC.
Read more on indicator of compromise here: https://brainly.com/question/25521596
#SPJ1
Complete Question:
A. Vulnerability feed
B. IoC
C. TTP
D. RFC
Construct a JK flip-flop using a D flip-flop, a two-to-one-line multiplexer, and an inverter. Hint: Use the 2xl MUX to implement the input function for the D flip-flop just like you implemented the function in question 1. Basically, construct a truth table with inputs Q, J, and K and function Q(t+1). Use Q for selection, and express Q(t+1) in terms of J and K.
Answers
In order to create a JK flip-flop with a D flip-flop, an inverter, and a two-to-one-line multiplexer (MUX), the following instructions can be followed:
The InstructionsPrepare a truth table depicting the relationship between the inputs Q, J, and K, and their resultant output Q(t+1).
Implement the input function for the D flip-flop by utilizing the MUX, as done in the previous query.
Make sure to link the J input of the MUX with the J input of the JK flip-flop and the K input of the MUX with the K input of the JK flip-flop.
Link the output of the MUX to the D input of the D flip-flop.
Link the Q output of the D flip-flop to the input of the multiplexer.
One way to rephrase this statement is: Use an inverter to connect the feedback input of the MUX to the Q output of the D flip-flop.
This adaptation enables the JK flip-flop to operate according to the J and K inputs, in line with the truth table and feedback process.
Read more about multiplexers here:
https://brainly.com/question/30256586
#SPJ4
What is the scientific foundation for synchrotron technology
development?
Answers
The scientific foundation for synchrotron technology development is based on the principles of particle accelerators and the generation of synchrotron radiation through the interaction of charged particles with magnetic fields.
Synchrotron technology is based on the scientific principles of particle accelerators and the phenomenon of synchrotron radiation. Particle accelerators are devices that accelerate charged particles, such as electrons or protons, to high speeds using electric and magnetic fields. Synchrotron radiation is a type of electromagnetic radiation emitted when these charged particles are deflected by magnetic fields while moving at high velocities.
The scientific foundation for synchrotron technology development lies in understanding and harnessing the behavior of charged particles in magnetic fields to generate synchrotron radiation. Synchrotron radiation is highly intense and covers a wide range of wavelengths, from infrared to X-rays. This unique radiation has a number of applications in various scientific disciplines, including physics, chemistry, materials science, biology, and medicine.
Synchrotron facilities are built to house large-scale particle accelerators that generate and control the production of synchrotron radiation. These facilities enable researchers to utilize synchrotron radiation for a wide range of experiments and studies, such as structural analysis of materials, investigation of atomic and molecular processes, protein crystallography, medical imaging, and more.
In summary, the scientific foundation for synchrotron technology development lies in understanding particle acceleration and the generation of synchrotron radiation through the interaction of charged particles with magnetic fields. This knowledge is applied in the construction and operation of synchrotron facilities, enabling scientists to exploit the unique properties of synchrotron radiation for numerous scientific and technological advancements.
Learn more about Synchrotron here:
https://brainly.com/question/32410347
#SPJ11
TRUE/FALSE. the motherboard sits on elevated screw holes or spacers to keep it from touching the case
Answers
The motherboard sits on elevated screw holes or spacers to keep it from touching the case." the answer is: True. The motherboard indeed sits on elevated screw holes or spacers, which are designed to keep it from touching the case and prevent electrical shorts or damage to the components.
When assembling a computer, the motherboard is placed inside the case and secured with screws or standoffs into elevated screw holes or spacers. This creates a gap between the motherboard and the case, preventing direct contact. This is important to avoid electrical shorts and damage to the components. The elevated placement also helps ensure proper grounding by aligning the motherboard's grounding traces with the screw holes or spacers. Overall, the purpose of elevated screw holes or spacers is to protect the motherboard, prevent shorts, and maintain a reliable electrical ground.
Learn more about motherboard :
https://brainly.com/question/29981661
#SPJ11
what is the unusable, or inedible, part of a wheat kernel that provides a protective coating around the kernel?
Answers
The unusable or inedible part of the wheat kernel that forms a protective layer around the kernel is the husk.
What does wheat kernel mean?Wheat kernel is the seed from which a wheat plant grows. Each small seed contains three different parts that are separated during the milling process into flour. The endosperm accounts for approximately 83% of the kernel weight and is the source of the white endosperm meal.
What are wheat kernel used for?A kernel, also called wheat berry, is the seed from which the wheat plant grows. Rather than being returned to the ground, most of the grain produced is ground into flour and processed into delicious wheat products that can be enjoyed by consumers around the world.
To learn more about wheat visit:
https://brainly.com/question/7283637
#SPJ4
What is one benefit of using audio-visual technology to facilitate meetings over audio technology like the telephone
Answers
Audio-visual technology has one significant benefit that sets it apart from audio technology, such as the telephone, when it comes to facilitating meetings. In this case, the audio-visual technology is able to provide an excellent platform for enhancing communication.
One benefit of using audio-visual technology to facilitate meetings over audio technology such as the telephone is that it enhances communication. Audio-visual technology is one of the most popular technologies in the world today. It has been used in a wide range of fields such as education, entertainment, and business, among others. Audio-visual technology has revolutionized how people communicate with each other. The use of audio-visual technology in meetings enhances communication in many ways. Audio-visual technology makes it possible for people to see and hear each other in real-time, which means that it is possible to hold a virtual face-to-face meeting, even when the parties involved are in different locations. The technology is ideal for facilitating remote communication, making it possible to connect people who are not physically in the same place. This has made it possible for organizations to save on costs related to travel and accommodation. Additionally, the use of audio-visual technology in meetings has made it possible for people to share and view documents, slideshows, and videos, among other visual aids. This has helped to enhance the effectiveness of meetings. The use of audio-visual technology in meetings is highly beneficial, particularly when compared to audio technology such as the telephone. One benefit of using audio-visual technology in meetings is that it enhances communication. It makes it possible for people to see and hear each other in real-time and for visual aids to be shared and viewed.
To learn more about Audio-visual technology, visit:
https://brainly.com/question/28315438
#SPJ11
What is operating System? Graphically explain the categorias
of operating System. Also mention the type of operating
System you are using
in your home.
Answers
Answer:
.............................................................. ..........
Can a computer evaluate an expression to something between true and false? Can you write an expression to deal with a "maybe" answer?
Answers
Answer:
yes it can
Explanation:
Computers cannot evaluate an expression to be between true or false.
Expressions in computers are represented in boolean values; i.e. they can only take one of two values (either true or false, yes or no, 1 or 0, etc.)
Take for instance, the following expressions will be evaluated to true, because the expressions are true.
\(\mathbf{1 + 2 = 3}\).\(\mathbf{5>4}\).\(\mathbf{4 + 4 <10}\)The following expressions will be evaluated to false, because the expressions are false.
\(\mathbf{1 + 2 > 3}\).\(\mathbf{5=4}\).\(\mathbf{4 + 4 >10}\)The above highlights show that, a computer cannot evaluate expressions to another value other than true or false
Read more about computer expressions at:
https://brainly.com/question/17500565
what user groups are commonly used to assign privileges for group members to run applications as the administrator?
Answers
The user groups that are commonly used to assign privileges for group members to run applications as the administrator are the Administrators, Power Users, and Users groups
.What is a user group: A user group is a collection of user accounts that share similar requirements for system resource usage, security, and applications. User groups can be used to simplify user administration by allowing access and authorizations to be assigned to groups instead of individual users.In computing, what is an administrator?In computing, an administrator is a user who has complete control over a computer, network, or system. They can install and remove software, change system settings, and manage user accounts, among other things.What are applications?An application is a computer software designed to execute a specific task. Word processors, web browsers, and media players are examples of applications. Applications can be downloaded from the internet or installed from a CD-ROM or other storage media.
learn more about applications here:
https://brainly.com/question/31164894
#SPJ4
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
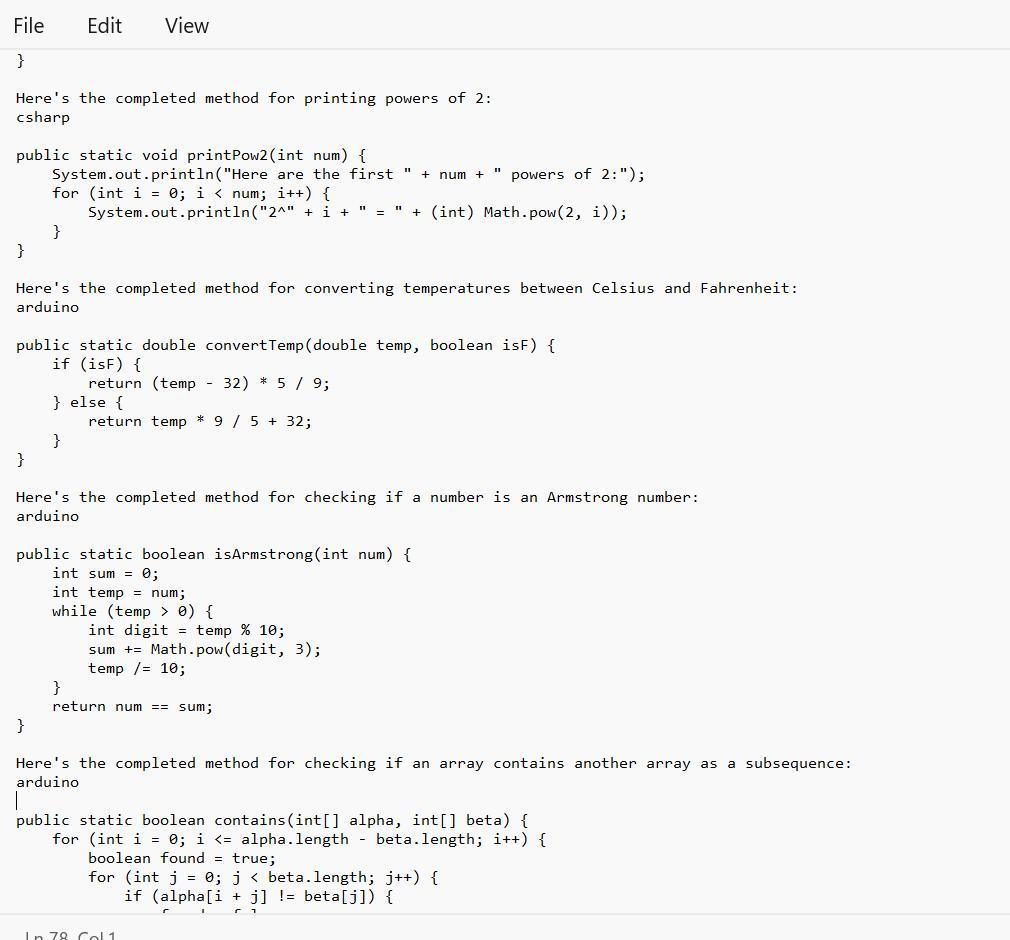
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


how do i auto-sum the values of two columns into a third column in excel?
Answers
To auto-sum the values of two columns into a third column in Excel, you can use the SUM formula. Here are the steps to do so:
Select the cell in the third column where you want the sum to appear.
Type the formula "=SUM(".
Select the first cell in the first column that you want to sum.
Hold the Shift key and select the corresponding cell in the second column.
Close the parentheses by typing ")".
Press Enter to calculate the sum.
Excel will calculate the sum of the selected range of cells and display the result in the cell where you entered the formula. The sum will automatically update if you change the values in the first or second column.
Alternatively, you can use the AutoSum feature in Excel, which automatically suggests the sum formula based on the adjacent cells. Here's how:
Select the cell directly below the values in the third column where you want the sum to appear.
Click on the "AutoSum" button (Σ) in the Excel toolbar.
Excel will automatically select the adjacent cells in the first and second columns.
Press Enter to calculate the sum.
The sum will be calculated and displayed in the selected cell, and it will update automatically if the values in the first or second column change.
learn more about "Excel":- https://brainly.com/question/24749457
#SPJ11
The CEO of CorpNet.xyz has hired your firm to obtain some passwords for their company. A senior IT network administrator, Oliver Lennon, is suspected of wrongdoing and suspects he is going to be fired from the company. The problem is that he changed many of the standard passwords known to only the top executives, and now he is the only one that knows them. Your company has completed the legal documents needed to protect you and the company. With the help of a CorpNet.xyz executive, you were allowed into the IT Admin's office after hours. You unplugged the keyboard from the back of the ITAdmin computer and placed a USB keylogger into the USB, then plugged the USB keyboard into the keylogger. After a week, the company executive lets you back into the IT Admin's office after hours again. In this lab, your task is to use the keylogger to recover the changed passwords as follows: Move the keyboard USB connector to a different USB port on ITAdmin. Remove the keylogger from ITAdmin. Move the consultant laptop from the Shelf to the Workspace. Plug the keylogger into the consultant laptop's USB drive. Use the SBK key combination to toggle the USB keylogger from keylogger mode to USB flash drive mode. Open the LOG.txt file and inspect the contents. Find the olennon account's password. Find the Administrator account's password. Answer the questions.
Answers
Answer:
The olennon account's password: See the attached file for this.
The Administrator account's password: 4Lm87Qde
Explanation:
Note: See the attached excel file for the olennon account's password as I was unable to save it here because I was instead getting the following message:
"Oh no! It seems that your answer contains swearwords. You can't add it!"
The olennon account's password and the Administrator account's password can be found as follows:
To see the rear of the computer, click Back from the menu bar above the computer.
Drag the USB Type A connector for the keyboard from the rear of the computer to another USB port on the machine.
Make sure the keyboard is plugged back in.
Expand System Cases on the shelf.
Add the Laptop to the Workspace by dragging it there.
To see the rear of the laptop, click Back from the menu above the laptop.
Drag the keylogger from the computer to the laptop's USB port.
Select Front from the menu above the laptop to see the front of the laptop.
Select Click to display Windows 10 on the laptop.
Toggle between keylogger and flash drive mode by pressing S + B + K.
To control what occurs with detachable drives, select Tap.
To view files, choose Open folder.
To open the file, double-click LOG.txt.
Select Answer Questions in the top right corner.
Respond to the questions.
Choose Score Lab as the option.
Therefore, we have:
The olennon account's password:
The Administrator account's password: 4Lm87Qde
1. Open the table in__
view.
2. Place the cursor in the Last Name column.
3. On the__ tab, in the Sort & Filter group, click __
Answers
2. Place the cursor in the last name column
3. On the create tab , in the sort a amp; filter group, click the toggle filter icon
What are your thoughts on the influence of AI on the overall progress of globalization? So far, globalization has been more beneficial to the developing countries than the developed. Do you think that may change in the future with the advances and expansion of AI in global business?
Answers
Answer:
Explanation:
The influence of AI on the overall progress of globalization is significant and multifaceted. AI technologies have the potential to reshape various aspects of global business and societal interactions. Here are a few key points to consider:
1. Automation and Efficiency: AI-driven automation can enhance productivity, optimize processes, and reduce costs for businesses across the globe. This can lead to increased efficiency in production, supply chains, and service delivery, benefiting both developed and developing countries.
2. Access to Information and Knowledge: AI-powered tools and platforms can facilitate the dissemination of information and knowledge on a global scale. This can bridge the knowledge gap and provide learning opportunities to individuals in developing countries, potentially narrowing the gap between developed and developing nations.
3. Economic Disruption and Job Transformation: The expansion of AI in global business may disrupt certain job sectors, particularly those involving repetitive or routine tasks. While this can lead to job displacement, it also creates opportunities for reskilling and upskilling the workforce. Adapting to these changes will be crucial for individuals and countries to ensure they can benefit from the evolving job market.
4. Technological Divide and Access: There is a concern that the advancement of AI could exacerbate the digital divide between developed and developing countries. Access to AI technologies, infrastructure, and resources can vary significantly, posing challenges for countries with limited resources to fully leverage AI's potential. Addressing this divide will be crucial to ensure equitable globalization and avoid further marginalization of certain regions.
5. Ethical Considerations: The ethical implications of AI, including privacy, bias, and accountability, need to be carefully addressed in the global context. International collaboration and regulation can play a significant role in ensuring responsible and inclusive deployment of AI technologies worldwide.
While globalization has historically had varying impacts on developed and developing countries, the future influence of AI on this trend is complex and uncertain. It will depend on how AI is harnessed, the policies and strategies implemented, and the capacity of countries to adapt and leverage AI for their development goals. A proactive and inclusive approach can help mitigate potential risks and maximize the benefits of AI in global business and globalization as a whole.
AI has been changing the face of globalization by its advances and expansion in global business. The influence of AI is expected to continue to shape globalization in the future.
AI and its technologies are becoming increasingly popular in different areas of globalization. These technologies offer cost-effective and efficient solutions that enable businesses to expand across borders. AI-powered business intelligence, predictive analytics, and automation technologies are allowing companies to streamline operations, reduce costs, and make more informed decisions. While AI may initially offer more benefits to developed countries, it is expected that developing countries will begin to adopt AI technologies more extensively as well. AI has the potential to help bridge the gap between developed and developing countries by improving access to information, resources, and opportunities. This will be especially beneficial in the areas of healthcare, education, and infrastructure development.
Know more about globalization, here:
https://brainly.com/question/30331929
#SPJ11
he primary key contained in the vendor master record is the ________.
Answers
The primary key contained in the vendor master record is the Vendor Number.
What is the Vendor Master Record?A Vendor Master Record (VMR) is a collection of vendor-specific data that is stored and maintained in SAP. The Vendor Master Record is used to keep track of the vendor's essential information, such as the vendor's name, address, bank information, payment terms, and other critical data. A master record is created for every vendor in the vendor master data.
Vendor Number, which is the primary key contained in the Vendor Master Record is the unique identification of each vendor. It's a six-digit numeric code assigned to vendors that identifies them in the SAP system. The Vendor Number helps identify a vendor's information in the vendor master record by searching for the vendor's record using the vendor number.
Learn more about Vendor Master Record (VMR) here: https://brainly.com/question/13650923
#SPJ11
The lifetime of a new 6S hard-drive follows a Uniform
distribution over the range of [1.5, 3.0 years]. A 6S hard-drive
has been used for 2 years and is still working. What is the
probability that it i
Answers
The given hard-drive has been used for 2 years and is still working. We are to find the probability that it is still working after 2 years. Let A denote the event that the hard-drive lasts beyond 2 years. Then we can write the probability of A as follows:P(A) = P(the lifetime of the hard-drive exceeds 2 years).By definition of Uniform distribution, the probability density function of the lifetime of the hard-drive is given by:
f(x) = 1/(b - a) if a ≤ x ≤ b; 0 otherwise.where a = 1.5 years and b = 3.0 years are the minimum and maximum possible lifetimes of the hard-drive, respectively. Since the probability density function is uniform, the probability of the hard-lifetime of a new 6S hard-drive follows a Uniform distribution over the range of [1.5, 3.0 years]. We are to find the probability that a 6S hard-drive, which has been used for 2 years and is still working, will continue to work beyond 2 years.Let X denote the lifetime of the hard-drive in years.
Then X follows the Uniform distribution with a = 1.5 and b = 3.0. Thus, the probability density function of X is given by:f(x) = 1/(b - a) if a ≤ x ≤ b; 0 otherwise.Substituting the given values, we get:f(x) = 1/(3.0 - 1.5) = 1/1.5 if 1.5 ≤ x ≤ 3.0; 0 the integral is taken over the interval [2, 3] (since we want to find the probability that the hard-drive lasts beyond 2 years). Hence,P(A) = ∫f(x) dx = ∫1/1.5 dx = x/1.5 between the limits x = 2 and x = 3= [3/1.5] - [2/1.5] = 2/3Thus, the probability that a 6S hard-drive, which has been used for 2 years and is still working, will continue to work beyond 2 years is 2/3.
To know more about Uniform distribution visit:
brainly.com/question/13941002
#SPJ11
Convert totalDays to months, weeks, and days, finding the maximum number of months, then weeks, then days.
Ex: If the input is 223, the output is:
Months: 7
Weeks: 1
Days: 6
Note: Assume a month has 30 days. A week has 7 days.
#include
using namespace std;
int main() {
int totalDays;
int numMonths;
int numWeeks;
int numDays;
cin >> totalDays;
cout << "Months: " << numMonths << endl;
cout << "Weeks: " << numWeeks << endl;
cout << "Days: " << numDays << endl;
return 0;
}
Answers
Here is a C++ program to convert totalDays to months, weeks, and days, finding the maximum number of months, then weeks, then days:
#include <iostream>
using namespace std;
int main() {
int totalDays; // variable to store the input of total days
int numMonths; // variable to store the number of months
int numWeeks; // variable to store the number of weeks
int numDays; // variable to store the number of days
cin >> totalDays; // get input from user for total days
numMonths = totalDays / 30; // calculate the number of months by dividing totalDays by 30
totalDays -= numMonths * 30; // subtract the number of days already accounted for by months from totalDays
numWeeks = totalDays / 7; // calculate the number of weeks by dividing remaining totalDays by 7
totalDays -= numWeeks * 7; // subtract the number of days already accounted for by weeks from totalDays
numDays = totalDays; // set the remaining totalDays to numDays
cout << "Months: " << numMonths << endl; // output the number of months
cout << "Weeks: " << numWeeks << endl; // output the number of weeks
cout << "Days: " << numDays << endl; // output the number of days
return 0; // indicate successful completion of program
}
This program takes an input of totalDays and then calculates the number of months, weeks, and days that this represents, finding the maximum number of months, then weeks, then days. It assumes that a month has 30 days and a week has 7 days. The program then outputs the calculated number of months, weeks, and days.
Learn more about C++ strings : https://brainly.com/question/30392694
#SPJ11
What are some positive and negative impacts of computer science changing how we work, where we work and when we work?
Answers
Answer:
Using those tools, computer science allows us to predict hurricanes, tornadoes, or even the outbreak of a potentially fatal disease. It can even be used to predict human behavior, which can help prevent crimes. Computer science can provide us with some life-saving tools and work.
Explanation:
True or False: Python code can include a script that returns the operating system platform
your code is running on with the .sys
Answers
True
import sys
print(sys.platfom)
This will print, to the console, which type of platform is running.
Which of the following is the necessary equipment in order for skilled hackers working from within a
corrections facility to gain access to store account information? (Select all that apply.)
Internet connection
password detectors
computer
PIN detectors
Answers
The necessary equipment for skilled hackers working from within a corrections facility to gain access to store account information includes an Internet connection and a computer.
How is this so?An Internet connection is essential for hackers to connect to the target system and retrieve/store account information.
A computer is needed to perform the hacking activities and execute the necessary tools and techniques. Password detectors and PIN detectors are not mentioned as necessary equipment in this context.
Learn more about hackers at:
https://brainly.com/question/23294592
#SPJ1