How reliable and accurate is Wikipedia?
Answers
Eight of the nine entries were inaccurate, according to the study, and at least two of the nine Wikipedia articles had significant errors.
How accurate is the Wikipedia?Eight of the nine entries were inaccurate, according to the study, and at least two of the nine Wikipedia articles had significant errors.Wikipedia's overall accuracy percentage was 80%, whereas the other sources' accuracy rates ranged from 95% to 99%. The accuracy of the content is not guaranteed by the online encyclopedia. When scholars skip over the content to look at the references, citations, and sources given, it is regarded as a useful "beginning point." When evaluating the quality of papers, academics advise consulting trustworthy sources. It's also feasible that certain mistakes won't ever be corrected. An edit that corrects a mistake may potentially be later reversed. As a result, Wikipedia shouldn't be regarded as a sufficient source in and of itself.To learn more about Wikipedia refer to:
https://brainly.com/question/28848406
#SPJ4
Related Questions
For exchanging data between network devices and secondary storage, oss primarily use:____.
a. parallel transfer.
b. synchronous transfer.
c. asynchronous transfer.
Answers
The primary method used by operating systems (OSs) for exchanging data between network devices and secondary storage is asynchronous transfer.
Asynchronous transfer refers to the process where data is transferred at irregular intervals and is not synchronized with a clock signal. This method allows for more efficient data transfer as it does not require the sender and receiver to be synchronized. An asynchronous transfer is preferred because it allows for greater flexibility in data transfer and reduces the need for strict timing requirements. In contrast, parallel transfer involves sending multiple bits of data simultaneously over separate lines, which can be complex and costly to implement. Synchronous transfer, on the other hand, involves transmitting data in a synchronized manner with a clock signal, but this method can be less efficient for network devices and secondary storage.
In conclusion, operating systems primarily use asynchronous transfer for exchanging data between network devices and secondary storage due to its flexibility and efficiency.
To learn more asynchronous transfer visit:
brainly.com/question/32997269
#SPJ11
Define at least two ways in which correct network documentation will increase the effectiveness in troubleshooting and increasing employee morale.
Answers
The network documentation that increase effectiveness are:
Good and right documentation can save one's time in researching to fix consistent issues.Putting everything in order and all must follows the same processes and procedures, will help lower issues and errors.What is troubleshooting?Troubleshooting is known to be a kind of systematic method used in problem-solving that are linked to complex machines, electronics, computers and others.
Note that the network documentation that increase effectiveness are:
Good and right documentation can save one's time in researching to fix consistent issues.Putting everything in order and all must follows the same processes and procedures, will help lower issues and errors.Learn more about troubleshooting from
https://brainly.com/question/14394407
#SPJ1
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
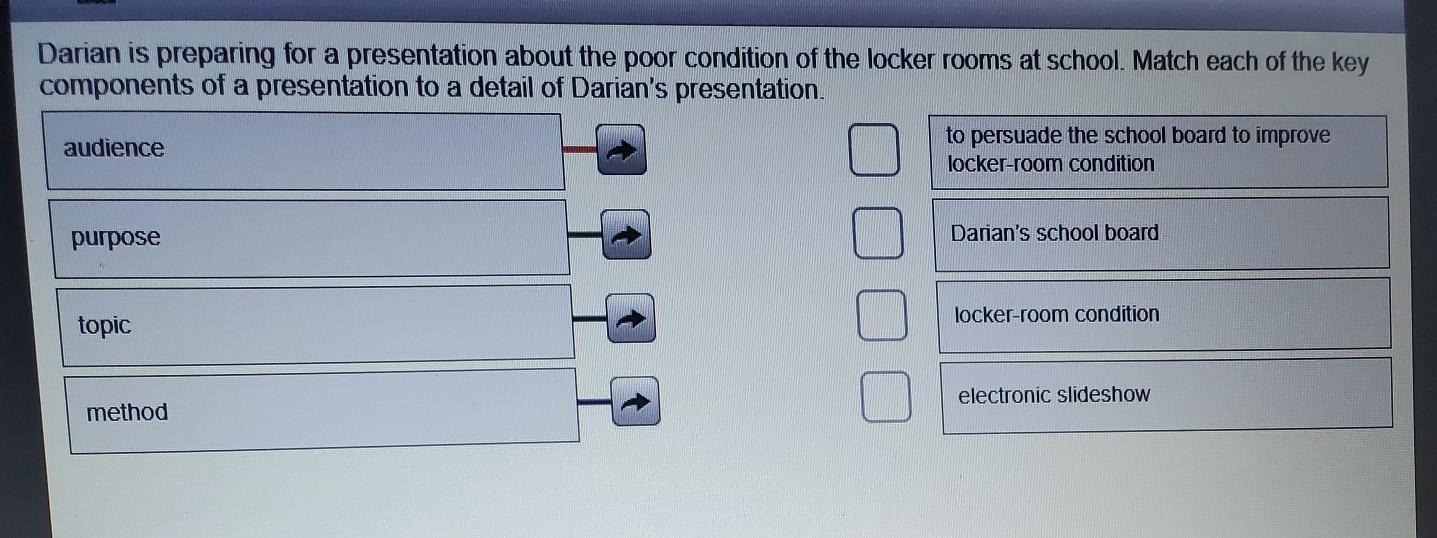
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
1. A teacher asked a student to capture and print out a one-slide presentation using MSWord, showing everything on the screen.
i) What keys or combination of keys can be used to carry out this operation ?
ii) Describe the procedures to be followed by the student in carrying out this operation?
iii) Describe the procedure to be followed by the student in carrying out this assignment using the keyboard.
b) A system Analyst was hired to set up a computer laboratory for Gan di Gan International School,
i.) Mention three hardware devices the analyst would need to set up the laboratory
ii) List two database applications likely to be recommended by the analyst
iii) State five Word Processing packages likely to be installed
Answers
The keyboard combinations that can be used to capture and print out a one-slide presentation using MSWord, showing everything on the screen is Function key + PrtScr
What is a Key Combination?This refers to the procedure that is used to combine two or more keys on the keyboard to execute a task.
Hence, we can see that the procedure that can be used to carry out the operation is:
Enter the screen you want to capture and printPress the Function key, followed by the PrtScr. Please note this can vary slightly, depending on the keyboard.The hardware devices that would be needed to be set up by the system analyst at a computer laboratory are:
System UnitLaptops/MonitorPower adaptersEthernet cables, etcThe database applications that can be recommended by the system analyst are:
MySQL, SQL ServerThe five word processing packages that are likely to be installed are:
G00..gle DocsMsWordMSOfficeDropbox PaperCorel WordPerfectRead more about word processing here:
https://brainly.com/question/985406
#SPJ1
1. Word Module 2 SAM Textbook Project
2. Word Module 2 SAM Training
3. Word Module 2 SAM End of Module Project 1
4. Word Module 2 SAM End of Module Project 2
5. Word Module 2 SAM Project A
6. Word Module 2 SAM Project B
Answers
The raise To Power Module of the program's calling error can be found in the real and integer values of the argument variables.
String should be spelled Sting. The set Double Module instead of returning an integer, does such. Access to local variables declared in the Main module is restricted to that module only. The raise To Power Module of the program's calling argument variables' real and integer values can be used to pinpoint the issue. Although the arguments for the raise To Power Module (Real value and Integer power) have been defined. The integer power is represented as "1.5," and the real value is supplied as "2." A real number, on the other hand, is a number with a fractional part. thus, a number without a fraction is considered an integer. 1.5 is a real number, whereas 2 is an integer. The parameters' contents when invoking raise To Power.
Learn more about The raise To Power Module here:
https://brainly.com/question/14866595
#SPJ4
What
ICT H/W
ст
are the Function numbering
•MS word
and bullets
Answers
The function of Bullets and numbering in MS Word is that Bulleted and numbered lists are known to be tool that often help a person to be able to simplify steps or items to any given reader readers.
People do make use of bulleted lists to be able to highlight some key pieces of their lessons.
What is numbering in MS Word?It is one that is often called the ordered list, number format, as well as the number list.
Note that the Bulleted and numbered lists are said to be tool that is often used in a given documents to put together and format text so as to be able to draw emphasis.
Hence, The function of Bullets and numbering in MS Word is that Bulleted and numbered lists are known to be tool that often help a person to be able to simplify steps or items to any given reader readers.
Learn more about numbering from
https://brainly.com/question/4509295
#SPJ1
A device receives a data link frame with data and processes and removes the Ethernet information. What information would be the next to be processed by the receiving device
Answers
The information that would be the next to be processed by the receiving device is: IP at the internet layer.
Internet protocol (IP)Internet protocol is a network protocol that help to transmit data to user device across the internet or network which inturn make it possible for user device to connect and communicate over the network.
Internet protocol at the internet layer is a TCP/IP software protocol which sole purpose is to transfer data packets across the internet after receiving and processing the data.
Inconclusion the information that would be the next to be processed by the receiving device is: IP at the internet layer.
Learn more about internet protocol here:https://brainly.com/question/17820678
What is a "Top-Level Domain Name"?
Answers
A top-level domain is known to be an aspect of a domain that quickly follows the last dot symbol that is seen in a domain name.
What is a "Top-Level Domain Name"?This is known to be the biggest level in terms of the hierarchical Domain Name System of the Internet.
Note that TLD (top-level domain) is said to be the most generic domain that is seen on the Internet's hierarchical DNS (domain name system) as A top-level domain is known to be an aspect of a domain that quickly follows the last dot symbol that is seen in a domain name.
Learn more about Domain Name from
https://brainly.com/question/13437432
#SPJ1
Question #4
Dropdown
Choose the correct term to complete the sentence.
The____A function removes the element with an index of zero.
a.leftpop
b. removeleft
c. popleft
d. leftremove
Answers
Answer: popleft
Explanation: Trust me bro
write a matlab program in a script file that finds a positive integer n such that the sum of all the integers 1 2 3 n is a number between 100 and 1,000 whose three digits are identical. as output, the program displays the integer n and the corresponding sum.
Answers
Answer:
%% Positive Integer between 100 and 1,000 with Identical Digits
% Initialize variables
n = 0;
sum = 0;
% Loop until an integer is found that meets the requirements
while sum < 100 || sum > 1000 || length(unique(num2str(sum))) ~= 1
n = n + 1;
sum = sum + n;
end
% Print the integer and corresponding sum
fprintf('The integer is %d and the sum is %d.\n', n, sum);
Which of the following is not a type of external data? a) Demographics b) Household c) Socioeconomic d) Promotion History Q8 Does a data warehouse? a) Improve data access b) Slow data access c) Makes
Answers
The answer to the first question is "d) Promotion History" as it is not typically categorized as a type of external data. Regarding the second question, a data warehouse is designed to improve data access rather than slow it down
External data refers to information that is obtained from sources outside of an organization. It provides valuable insights into external factors that can influence business operations and decision-making. The options provided in the question are all types of external data, except for "d) Promotion History." While demographic data, household data, and socioeconomic data are commonly used to understand consumer behavior, market trends, and target audience characteristics, promotion history typically falls under internal data. Promotion history refers to the records and data related to past promotional activities, campaigns, and strategies employed by the organization itself.
Moving on to the second question, a data warehouse is a centralized repository that is specifically designed to improve data access. It is a large-scale storage system that integrates data from various sources, such as transactional databases, spreadsheets, and external data feeds. The purpose of a data warehouse is to provide a structured and optimized environment for data storage, organization, and retrieval. By consolidating data into a single location, a data warehouse facilitates efficient access to information for analysis, reporting, and decision-making. It eliminates the need to query multiple systems and allows for faster and more streamlined data retrieval and analysis processes. Therefore, the correct answer to the question is "a) Improve data access."
Learn more about external data here : brainly.com/question/32220630
#SPJ11
which cytoskeletal element could be described as solid, thinner structures that are often organized into a branching network?
Answers
the cytoskeletal element could be described as solid, thinner structures that are often organized into a branching network is microfilaments
What is microfilaments?As they are made up of two entangled strands of the globular protein known as actin, microfilaments are also known as actin filaments. They are the tiniest filaments of the cytoskeleton and polymers of the protein actin. They are essential for muscle contraction, cell division, and cellular mobility.With a diameter ranging from 5 to 8 nanometers, microfilaments are the thinnest cytoskeleton filaments seen in the cytoplasm of eukaryotic cells. These filaments' polymers are robust and flexible, resisting buckling and crushing while providing support for the cell.Microfilaments are adaptable parts that are crucial to cytokinesis and the structure of a cell. The flexible filament layout of the framework makes it possible for it to aid in cell migration.To learn more about microfilament refer to:
https://brainly.com/question/1286389
#SPJ4
A _________ conversion involves shutting the old system off and turning the new system on at a certain point in time.
Answers
A direct conversion involves shutting the old system off and turning the new system on at a certain point in time.
What do you mean by direct conversion?
Implementing the new system while immediately ending the old one is known as direct conversion.
What is Conversion method?
The conversion procedure entails changing a company's single-entry accounting system to a double-entry one. Single-entry bookkeeping is a quick and easy approach for new small enterprises to record their revenue and expenses. The three accounts used in single-entry bookkeeping are the bank, cash, and personal.
What are the methods of conversion?
The four methods of conversion are −
Parallel ConversionDirect Cutover ConversionPilot ApproachPhase-In MethodLearn more about direct conversion method click here:
https://brainly.com/question/28366814
#SPJ4
Implement a 2-out-of-5 detector using the 8-to-1 multiplex. Definition of 2-out-of-5 detector: for a 5-input logic, if and only if 2 of inputs are ‘1’, the output will be true. You need to draw the schematics of your design and write down the design intermediate steps
Answers
To implement a 2-out-of-5 detector using an 8-to-1 multiplexer, we can use the following design steps:
Connect the five inputs (A, B, C, D, and E) to the eight data inputs of the 8-to-1 multiplexer (MUX).
Use two additional inputs (S0 and S1) to select which pair of inputs to compare. We can set up the MUX so that it selects two inputs at a time and compares them.
Use logic gates (AND and NOT) to determine if two of the selected inputs are '1'.
Connect the output of the logic gates to the MUX output.
The schematic diagram of the 2-out-of-5 detector using an 8-to-1 MUX is attached at last.
The truth table for the 2-out-of-5 detector using an 8-to-1 MUX is attached as image.
The X in the first row of the truth table represents "don't care" inputs, as all inputs are 0 and the output is always 0.
Thus, this circuit can be expanded to detect any 'M' out of 'N' combinations by adjusting the number of input lines and the selection inputs of the MUX accordingly.
For more details regarding multiplex, visit:
https://brainly.com/question/31462153
#SPJ1


n the most basic level, internet supports point to point asynchronous communication. true or false
Answers
In the most basic level, internet supports point to point asynchronous communication is false. In the most basic level, the internet supports point-to-point synchronous communication. So the statement is False.
Point-to-point communication refers to the direct transmission of data between two endpoints, such as a client and a server. Synchronous communication means that the sender and receiver are in sync and exchange data in real-time.
This is commonly seen in protocols like TCP (Transmission Control Protocol), where data is sent and acknowledged in a synchronized manner. Asynchronous communication, on the other hand, allows for non-real-time, independent data transmission and processing between endpoints.
While the internet can support both synchronous and asynchronous communication, its fundamental operation relies on point-to-point synchronous communication. Therefore, the statement is False.
To learn more about asynchronous communication: https://brainly.com/question/28412501
#SPJ11
Pasta is best if cooked and served immediately. What do you need to
do to follow this golden rule in presenting pasta dishes?
Answers
sprinkle a little bit of cheese on there, maybe add a few meatballs.
You wrote a program to allow the user to guess a number. Complete the code to get a number from the user.
# Get a guess from the user and update the number of guesses.
guess =
("Guess an integer from 1 to 10: ")
Help please
Answers
Answer:
input
Explanation:
I got it right on the quiz.
Answer: input
Explanation: Edge 2022
Which of the following numbers might this code generate: random.randint(1,9)?
0
10
11
1
Answers
Answer:
1
Explanation:
In Python programming language, the random.randint function is an abbreviation for random integers.
Basically, the random.randint is used for generating or creating a random integer numbers.
The syntax for this code can be written as;
A = random.randint(1,9)
Print ("Random number between 1 and 9 is % s" % (A))
Note, the numbers between 1 and 9 are 1, 2, 3, 4, 5, 6, 7, 8 and 9.
From the answer choices given (0, 1, 10 and 11), the only number that matches the requirement is 1.
Therefore, the number this code random.randint (1,9) might generate is 1.
Write an LMC program as follows instructions:
A) User to input a number (n)
B) Already store a number 113
C) Output number 113 in n times such as n=2, show 113
113.
D) add a comment with a details exp
Answers
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
The LMC program can be written as follows:
sql
Copy code
INP
STA 113
INP
LDA 113
OUT
SUB ONE
BRP LOOP
HLT
ONE DAT 1
Explanation:
A) The "INP" instruction is used to take input from the user and store it in the accumulator.
B) The "STA" instruction is used to store the number 113 in memory location 113.
C) The "INP" instruction is used to take input from the user again.
D) The "LDA" instruction loads the value from memory location 113 into the accumulator.
E) The "OUT" instruction outputs the value in the accumulator.
F) The "SUB" instruction subtracts 1 from the value in the accumulator.
G) The "BRP" instruction branches back to the "LOOP" label if the result of the subtraction is positive or zero.
H) The "HLT" instruction halts the program.
I) The "ONE" instruction defines a data value of 1.
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
To know more about LMC program visit :
https://brainly.com/question/14532071
#SPJ11
there are 5 key questions you should ask yourself before joining a new social media platform. which of the following are key questions? (choose two answers)
a.Is the platform being adopted by gen z and younger generations?
b.Does this platform integrate with my social media management software?
c.Is my audience on the platform?
d.Can I do things on this platform that I can’t do on my existing channels?
Answers
The key questions among the options provided are Is the platform being adopted by Gen Z and younger generations? Can I do things on this platform that I can't do on my existing channels?
These two questions are important considerations before joining a new social media platform. Here's whya. Is the platform being adopted by Gen Z and younger generationsUnderstanding the target demographics and user base of a social media platform is crucial. If the platform is popular among Gen Z and younger generations, it indicates a potential opportunity to reach and engage with a specific audience segment. Can I do things on this platform that I can't do on my existing channelsExploring unique features and functionalities offered by the new platform is important. If the platform allows for new and innovative ways to connect, share content, or engage with the audience, it can provide added value and differentiation from existing social media channels.Considering these questions helps assess the platform's relevance to your target audience and the potential for new opportunities and capabilities that align with your social media strategy.
To learn more about generations click on the link below:
brainly.com/question/32216009
#SPJ11
9
10
1
2
3
4
5
Which is a valid velocity reading for an object?
45 m/s
45 m/s north
O m/s south
0 m/s
Answers
Answer:
Maybe 45 m/s north I think I'm wrong
Answer:45 ms north
Explanation:
How would I search snowboarding outside of Minnesota in my browser?
Answers
The way to search for snowboarding outside of Minnesota in your browser is to use the search tool to type likely words such as Popular Downhill Skiing Destinations and then you will see different options to choose from.
What does browsing entail?When you're searching, you want to finish a task; when you're browsing, you can be seeking for ideas, entertainment, or just additional information. When you are searching, you are actively looking for solutions, whereas when you are browsing, you are merely viewing the results.
An application program known as a browser offers a way to see and engage with all of the content on the World Wide Web. Web pages, movies, and photos are included in this.
Note that by typing key words using your browser such as snowboarding, you will see defferent result.
Learn more about Browser search from
https://brainly.com/question/22650550
#SPJ1
what happens to the fractional part when a division is performed on two integer variables? group of answer choices two integers cannot be used in division; at least one of the operands should be a floating-point number. the fractional part is discarded. the fractional part is rounded off to the nearest integer value. instead of using an integer division, you should use the modulus operator to perform floating-point division.
Answers
When dividing two integer variables, the fractional portion is ignored by integer division.
Integer variables are what?Variables with an integer value requirement are known as integer variables (0, 1, 2,). Binary variables are a particular class of integer variables. The only possible values for binary variables are 0 and 1. They are numerical variables that can only have a value of one.
What kind of variable has an integer format?In a single declaration, you can declare a field as an integers and give it a value. For instance: age is 10 int; This example would declare the age variable as such an integer and give it the number of 10.
To know more about integer variable visit:
https://brainly.com/question/27855584
#SPJ4
Using technologies increase the time needed to complete a task is beneficial
True
False
Answers
Answer:
True
Explanation:
The advent of technology has given human to achieve a whole lot more in a rather short period of time when compared to the period where the major tool of engagement and task is Manual. With technology, aside from having the ability to complete task faster, we can achieve more accurate result and a lot attractive output. All these in very little time. Technology has helped industries grow multiple times faster thus increasing input, yield and productivity. The tedious nature of having to work manually has also been expunged with repetitive task now being programmed and automated.
Write the steps for viewing tab stops in a word document. Hurry pleasee!!
Answers
Then click tabs button
Set the tab stops position> chose alignment and leader options and the click set and ok
pls answer fast ........

Answers
Answer:
1,048,576 rows on MS excel worksheet
what does MAN stand for??
what does wAN stand for?
Name the largest computer network?
Which computer network is limited with in the room?
What is internet works?
What is home networks?
Arrange the computer network on the basic of their size?
Answers
Explanation:
1. MAN : Metropolitan Area Network.
2. WAN: Wide Area Network.
3. The Internet is the world's largest computer network.
4. Local Area Network is limited with in the room. 5. Data sent over the Internet is called a message, but before message gets sent, they're broken up into tinier parts called packets.
6.A home network or home area network is a type of computer network that facilities communication among devices within the close vicinity of a home.
Sorry I don't know the answer of last question.
I am so sorry.
rotate object while holding the shift key. what does it do?
Answers
Answer:
It rotates it 45 degrees in a direction
Benefits of donating computer equipment include Select all that apply. A. extending the useful ife of the device B. heiping someone who can't afford a new deviceC. keeping e-waste out of landfills D. avoiding having the device waste space in your homeloflice
Answers
Benefits of donating computer equipment include:
B. helping someone who can't afford a new deviceC. keeping e-waste out of landfills D. avoiding having the device waste space in your home officeWhat is a Donation?This refers to the term that is used to define the act of giving a thing out to someone else who usually needs it more as a form of helping them or emancipation.
Hence, it can be seen that when it comes to computer equipments, donations can be made and this helps the person to prevent e-waste and also help someone else.
Read more about donations here:
https://brainly.com/question/13933075
#SPJ1
A wireless MAN (WMAN) is a metropolitan area network that uses __________ to transmit and receive data
Answers
A wireless MAN (WMAN) is a metropolitan area network that uses radio waves or other wireless communication technologies to transmit and receive data.
A wireless metropolitan area network (WMAN) is a type of network that connects devices over a geographic area, typically covering a city or town. Unlike traditional wired networks, which use physical cables to transmit data, WMANs use wireless communication technologies such as radio waves, microwave, or infrared signals to transmit and receive data.
WMANs can be used for a variety of applications, such as providing internet connectivity to homes and businesses, supporting public safety communications, and enabling mobile workforce productivity.
Learn more about wireless MAN: https://brainly.com/question/14616612
#SPJ11