I WILL GIVE BRAINLIEST TO WHO ANSWERS FIRIST AND CORRECT
How are blogs and wikis alike?
accessible 24/7
telecommunications technology
collaboration tool
available online
used for online dialog
increase business productivity
Answers
Answer:
accessible 24/7
available online
increase business productivity
telecommunications technology
Blogs and wikis alike because they are:
Accessible 24/7.Available online.Increase business productivity.Telecommunications technology.What are blogs?A blog is known to be a short word for “weblog”. This is known to be a kind of an online journal that is also said to be an informational website where one can get Infor on different subject.
Conclusively, Note that Blogs and wikis alike because they are Accessible 24/7 and one can get any information they want from it to increase business productivity.
Learn more about Blogs from
https://brainly.com/question/3653791
#SPJ2
Related Questions
A search engine is giving you too many sites that are not relevant to your topic, how cell phones change culture. Placing quotes around "cell phones change culture" gave only five results. What can you try next?
A.
change your key words
B.
use an advanced search
C.
use a search directory
D.
all of the above
PLease hurry
Answers
Answer:
all of the above
Explanation:
Answer:
D. all of the above
What are some of the restrictions to muscle wire?
Answers
Answer:
Muscle Wire is an extremely thin wire made from Nitinol (a nickel-titanium alloy) that is known for its ability to contract when an electric current is applied.Although thin and lightweight, one of the most amazing things about Muscle Wire is that they can lift many times their weight and are able to do 100 times more work per cycle than the human muscle. This material is easy to use, small in size, operates silently, has a high strength-to-weight ratio, and is easily activated using AC or DC power. This technology is ideal where mechanics require minimization, such as electronic textiles projects, robotics or nano-applications.Muscle Wire is an extremely thin wire made from Nitinol (a nickel-titanium alloy) that is known for its ability to contract when an electric current is applied.
One technique for coping with stress, known as _____, is to avoid thinking about or experiencing the situation that makes you stressed and to convince yourself to think positive thoughts instead.
Answers
One technique for coping with stress, known as Stress reliving is to avoid thinking about or experiencing the situation that makes you stressed and to convince yourself to think positive thoughts instead.
What is stress?Young people frequently have trouble learning how to handle stress. When stress is related to a catastrophic occurrence, such as a natural disaster, a family loss, school shootings, or community violence, youth can become especially overwhelmed.
Young people might feel better with stability and support from parents, carers, and instructors. When frightening or stressful situations occur in a child's life, worry is only natural.
By discussing these incidents with your kids, you can help them put frightening information into a more realistic context. Keep an eye on what your kids see and hear about stressful situations that occur in their life.
Therefore, One technique for coping with stress, known as Stress reliving is to avoid thinking about or experiencing the situation that makes you stressed and to convince yourself to think positive thoughts instead.
To learn more about stress, refer to the link:
https://brainly.com/question/25632718?
#SPJ1
If you had an idea for a new software company, what would be the best approach to help make it a successful business? develop a business plan to describe how to maintain and grow revenues go back to school to get a degree in IT business administration hire employees who understand the software development industry seek out financial support for venture capital, angel investors and grants
Answers
Answer:
(A). Develop a business plan to describe how to maintain and grow revenues
Explanation:
I got it right on edge2020.
If you had an idea for a new software company, develop a business plan to describe would be the best approach to help make it a successful business.
What is software company ?A business whose main offerings are different kinds of software, software technology, distribution, and software product creation is known as a software firm. They are what make up the software sector.
For corporations or customers, software development organizations create, create, and maintain apps, frameworks, or other software components.
Software may make your organization run more effectively in addition to enabling your computer hardware to execute crucial functions. Even new working methods can be developed with the correct software.
As a result, it is a vital company asset, and you should carefully select your software so that it meets your
Thus option A is correct.
To learn more about software company follow the link below;
https://brainly.com/question/10949949
#SPJ5
You cannot remember the address of Kayah’s website. What type of tool will help you
locate/find it by typing in keywords to look for it?
Answers
Answer:
A search engine
Explanation:
View the pdf
How will future space flights be different for NASA?
Answers
Answer:
Explanation:
NASA's future will continue to be a story of human exploration, technology, and science. NASA will continue to be a global leader in scientific discovery, fostering opportunities to turn new knowledge into things that improve life here on Earth. ... Artist's concept, NASA's gateway in lunar orbit.
Answer:
NASA's future will continue to be a story of human exploration, technology, and ... changes on the global land surface at a scale where we can separate human ... Exploring deep space and three-year missions to Mars pose new challenges: ...
Explanation:
NASA's Artemis program aims to land another man and the first woman on the moon by 2024 and eventually establish sustainable space travel by 2028. The Artemis program is NASA's stepping stone to their ultimate goal of landing on Mars.
what is a turnaround documents.
A a letter
B a newspaper
C a machine readable document
D verify accuracy of information
Answers
Answer:
D
Explanation:
A turnaround document is a computer-generated form that is sent to a third party, who is supposed to fill in the document and return it to the issuer. The information on the form is then used as the basis for data entry back into the computer system.
Help Pleaseeee? Which tool is used to create the World Wide Web? A. HTML B. Web Coder C. Application Software D. JavaScript
Answers
The correct answer would be A, I did it and A was right. :)
What quality of an image is determined by the resolution?
Answers
Answer:
Image resolution is typically described in PPI, which refers to how many pixels are displayed per inch of an image. Higher resolutions mean that there more pixels per inch (PPI), resulting in more pixel information and creating a high-quality, crisp image.
Answer:
The answer is Clarity :)
Configure Switch Ports
You're configuring the switch ports on the Branch1 switch. You want to add an older server to switch port Fa0/6, which uses 10BaseT Ethernet. You also want to add a hub to switch port Fa0/7, which will be used in a lab for developers. The devices currently attached to the switch are shown in the diagram.
In this lab, your task is to:
Configure the switch port Fa0/6 to use 10 Mbps. Use the speed command to manually set the port speed.
Configure the switch port Fa0/7 to use half-duplex communications. Use the duplex command to set the duplex.
Make sure that ports Fa0/6 and Fa0/7 are enabled and can be used even though you haven't connected devices to those ports yet.
Disable the unused interfaces. Use the shutdown command to disable the interfaces. You can also use the interface range command to enter configuration mode for multiple ports at a time.
Fa0/4 and Fa0/5
Fa0/8 through Fa0/23
Gi0/1 and Gi0/2
Verify that all the remaining ports in use are enabled and configured to automatically detect speed and duplex settings. Use the show interface status command to check the configuration of the ports using a single list. Use this output to verify that all the other ports have the correct speed, duplex, and shutdown settings. If necessary, modify the configuration to correct any problems you find. The ports should have the following settings when you're finished:
InterfacesStatusDuplexSpeedFastEthernet0/1-3FastEthernet0/24Not shut downAutoAutoFastEthernet0/6Not shut downAuto10 MbpsFastEthernet0/7Not shut downHalfAutoFastEthernet0/4-5FastEthernet0/8-23GigabitEthernet0/1-2Administratively downHalfAuto
Save your changes to the startup-config file.
Answers
The Branch1 switch has a few requirements that need to be met.
In order to configure switch ports on this switch, the following steps need to be taken:
Step 1: Configure the switch port Fa0/6 to use 10 Mbps On Branch1 switch, enter the configuration mode and configure the Fa0/6 port with the speed of 10 Mbps by using the following command:```
Branch1(config)#interface fa0/6
Branch1(config-if)#speed 10
```Step 2: Configure the switch port Fa0/7 to use half-duplex communicationsOn the same switch, enter the configuration mode and configure the Fa0/7 port with the duplex of half by using the following command:```
Branch1(config)#interface fa0/7
Branch1(config-if)#duplex half
```Step 3: Enable the switch ports Fa0/6 and Fa0/7Ensure that both ports are enabled and can be used even if they are not connected by using the following command:```
Branch1(config-if)#no shutdown
```Step 4: Disable the unused interfacesEnter the following command in the configuration mode to disable the following interfaces: Fa0/4 and Fa0/5, Fa0/8 through Fa0/23, Gi0/1 and Gi0/2```
Branch1(config)#interface range fa0/4 - 5, fa0/8 - 23, gi0/1 - 2
Branch1(config-if-range)#shutdown
```Step 5: Verify all the remaining ports in use are enabled and configured to automatically detect speed and duplex settingsVerify that all other ports are configured to automatically detect the speed and duplex settings by using the following command:```
Branch1#show interface status
```Step 6: Save your changesSave all changes to the startup-config file by using the following command:```
Branch1#copy running-config startup-config
```Therefore, this is how we configure switch ports.
Learn more about switches :
https://brainly.com/question/31853512
#SPJ11
what spreadsheet function enables you to put each of the colors in column g into a new, separate cell?
Answers
To put each of the colors in Column G into a new, separate cell, use SPLIT. SPLIT is a spreadsheet function that divides text around a specified character and puts each fragment into a new, separate cell.
What method would you employ to query a certain value from a spreadsheet column and return it?Vertical lookup, or VLOOKUP. delivers the value of a specific cell in the row that was found after searching down the first column of a range for a key. Horizontal lookup, or HLOOKUP returns the value of a specific cell in the column that contains the key after searching the first row of the range for the key.
What Excel functions are used to calculate the sum of values in columns or rows?Allow Excel to handle the math for you whenever you need to add a column or row of numbers. To total the numbers, choose a cell next to them, choose AutoSum from the Home menu, and then press Enter.
To know more about Excel visit:
https://brainly.com/question/17019765
#SPJ4
What happened to the badge system Brainly introduced the other day?
i went in my profile to see if there was more badges to earn (by this time i had earned the first three that were availible) and the tab for badges was gone, anyone know whats up?
Answers
Answer:
I don't know what happened to that system. I logged on today and saw it had disappeared too. I guess the badge system wasn't effective since many people earned them very quickly.
Explanation:
define computer network
Answers
Answer:
Explanation:
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other.
what is a sending device
Answers
Answer:
A sending device that initiates an instruction to transmit data, instruction, or. information. e.g., Computer A, which sends out signals to another computer. □ A communication device that converts the data, instructions, or information. from the sending device into signals that can be carried by a.
Answer:
A sending device is an object that gives instructions to transmit information.
i’m failing this class and i’m stuck on this one, this is the code from the last lesson:
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a":4, "b":3, "c":2, "d":1, "f":0}
if weighted == 1 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade])
else:
return"Invalid"
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes, 0 = no) "))))
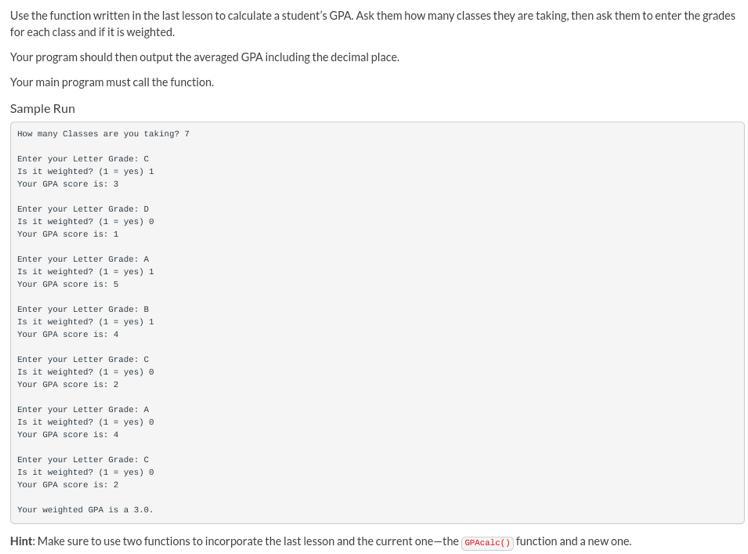
Answers
lst=([])
def avgGPA(lst1):
total = 0
count = 0
for x in lst:
if type(x) == int:
total += x
count += 1
return total/count
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
if weighted == 1 and grade in dictionary:
lst.append(dictionary[grade]+1)
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
lst.append(dictionary[grade])
return "Your GPA score is: " + str(dictionary[grade])
else:
lst.append("Invalid")
return "Invalid"
classes = int(input("How many Classes are you taking? "))
i = 0
while i < classes:
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes) "))))
i += 1
print("Your weighted GPA is a "+str(avgGPA(lst)))
If you need me to change any code, I'll do my best. I hope this helps!
You need to add security for your wireless network. You would like to use the most secure method. Which method should you implement?.
Answers
Disabling SSID broadcast is the greatest practice to take to increase security for wireless networks.
What is network?a chain, group, or system that is interconnected or associated in some way. a system of interconnected computers and devices that can communicate with one another. 4. a collection of radio or television stations connected by a radio relay or wire.
The best method to implement to add security for wireless network is disabled SSID broadcast.
By turning off the SSID broadcast, the router stops broadcasting the name of the wireless network, rendering it undetectable to users.
This only prevents the name from appearing on device lists for neighboring networks, though. Since users still require the network, it is still in existence.
Hence, disabled SSID broadcast is correct option.
To know more about Network on:
https://brainly.com/question/15002514
#SPJ12
Rita used information from a blog that someone else wrote. What should she do?
Select all answers that apply.
Rita should use the information and hope that no one recognizes where it came from.
Rita should ask the original author for approval to use the information.
Rita should ask her teacher for approval to use the information.
Rita should give the author credit for their intellectual property by citing the source.
Answers
Answer:
rita should either ask the original author for permission to use her blog, but the best answer woyuld be that she should site her sources.
Explanation:
Which statement about analog and digital images is true?.
Answers
The statement which is true about analog and digital images is: Option B; Sampling an analog image more frequently produces a digital image with a better representation.
Analog and Digital ImagesAn analog image is defined as a type of image with a matrix of pixels that is stored in binary form whereby the tone is depicted by continuous variations such as Photograph, Television images, X-ray images, artistic paintings e.t.c
Now, a digital image converts an analogue image to a digital image or converts a digital image to an analog image. This means that digital images are more powerful and provide a better representation than analog images.
Looking at the options the inky correct one is option B.
The statements are missing and they are;
A) With advances in technology, digital images look exactly like the analog images they represent.
B) Sampling an analog image more frequently produces a digital image with a better representation.
C) Analog images come from data that is measured at regular intervals.
D) Digital images come from data that is measures continuously
Read more about analog and digital images at; https://brainly.com/question/17239524
You are working as a project manager. One of the web developers regularly creates dynamic pages with a half dozen parameters. Another developer regularly complains that this will harm the project’s search rankings. How would you handle this dispute?
Answers
From the planning stage up to the deployment of such initiatives live online, web project managers oversee their creation.They oversee teams that build websites, work with stakeholders to determine the scope of web-based projects, and produce project status report.
What techniques are used to raise search rankings?
If you follow these suggestions, your website will become more search engine optimized and will rank better in search engine results (SEO).Publish Knowledgeable, Useful Content.Update Your Content Frequently.facts about facts.possess a link-worthy website.Use alt tags.Workplace Conflict Resolution Techniques.Talk about it with the other person.Pay more attention to events and behavior than to individuals.Take note of everything.Determine the points of agreement and disagreement.Prioritize the problem areas first.Make a plan to resolve each issue.Put your plan into action and profit from your victory.Project managers are in charge of overseeing the planning, execution, monitoring, control, and closure of projects.They are accountable for the project's overall scope, team and resources, budget, and success or failure at the end of the process.Due to the agility of the Agile methodology, projects are broken into cycles or sprints.This enables development leads to design challenging launches by dividing various project life cycle stages while taking on a significant quantity of additional labor.We can use CSS to change the page's background color each time a user clicks a button.Using JavaScript, we can ask the user for their name, and the website will then dynamically display it.A dynamic list page: This page functions as a menu from which users can access the product pages and presents a list of all your products.It appears as "Collection Name" in your website's Pages section.To learn more about search rankings. refer
https://brainly.com/question/14024902
#SPJ1
when a picture is downloaded off the internet and then posted to social media, can the social media platform tell it was downloaded off the internet
Answers
write a scheme program that prompts a user for year n, and then checks if year n is a leap year. test your program
Answers
Scheme program that prompts the user for a year and checks if it is a leap year:
(define (is-leap-year? year)
(cond ((= (mod year 4) 0)
(if (= (mod year 100) 0)
(= (mod year 400) 0)
#t))
(else #f)))
(display "Enter a year: ")
(define year (read))
(if (is-leap-year? year)
(display year)
(display "is a leap year.")
(newline)
(display year)
(display "is not a leap year.")
(newline))
To test the program, you can run it in a Scheme interpreter or compiler, and it will prompt you to enter a year. After entering a year, it will display whether the entered year is a leap year or not.
For example, if you enter the year 2024, the program will output:
2024 is a leap year.
And if you enter the year 2023, the program will output:
2023 is not a leap year.
You can try running the program with different years to test its functionality.
Learn more about Scheme interpreter here:
https://brainly.com/question/31107007
#SPJ11
Employing the use of a(n)
will help you manage a STEM project.
Answers
Answer:
technicians
Explanation:
the answer is technicians. in my freshmen year we made flash cards and i still have them so i remember it.
Answer: technicians
Explanation:
my teacher told me and I passed so its right
bitcoin is designed such that the attacker cannot reverse or tamper with the transactions. explain how, referencing its technical design features as needed.
Answers
Answer: -=-
;;;;;;;;;;;;;-----;;;;;;;;;;;;;;;;;;;
the most common source of database failures in organizations is: group of answer choices inadequate budget. lack of planning. failure to implement a strong database administration function. inadequate hardware.
Answers
Inadequate database administration is the most frequent cause of database failures in businesses.
The correct option is D.
What do database failures entail?The inability of a database to carry out the required transaction or data loss from the database are both considered failures. Each type of failure that a DBMS is susceptible to requires a unique management strategy.
What types of database failures are typical?Hardware issues Memory faults, disc crashes, faulty sectors, disc full errors, and other issues with the hardware can occur. Inadequate (poor) quality control during manufacture, overloading (using components with insufficient capacity), and mechanical component wearout can also be blamed for hardware failures.
To know more about database failures visit:
https://brainly.com/question/14536748
#SPJ4
The most common source of database failures in organizations is:
A) lack of planning.
B) inadequate budget.
C) inadequate hardware.
D) failure to implement a strong database administration function.
write a short note on mail bombing
Answers
Explanation:
A mail bomb is the sending of a massive amount of e-mail to a specific person or system. A huge amount of mail may simply fill up the recipient's disk space on the server or, in some cases, may be too much for a server to handle and may cause the server to stop functioning. In the past, mail bombs have been used to "punish" Internet users who have been egregious violators of netiquette (for example, people using e-mail for undesired advertising, or spam).
Write a program that calculates and prints the bill for a cellular telephone company. The company offers two types of service: Regular and Premium. The rates vary, depending on the type of service. The rates are computed as follows: Regular service: $10. 00 The first 50 minutes are free. Any minutes over 50 are $0. 20 per minute. Premium service: $25. 00 The first 75 minutes from 6:00 a. M. To 6:00 p. M. Are free and minutes over 75 between these times are $0. 10 per minute. The first 100 minutes from 6:00 p. M. To 6:00 a. M. Are free and minutes over 100 are $0. 05 per minute
Answers
To calculate and print the bill for a cellular telephone company that offers two types of service, regular and premium, you can use the following program:
#include <iostream>
int main() {
// Regular service
double regular_cost = 10.00;
int regular_free_minutes = 50;
double regular_extra_minutes_cost = 0.20;
// Premium service
double premium_cost = 25.00;
int premium_daytime_free_minutes = 75;
double premium_daytime_extra_minutes_cost = 0.10;
int premium_nighttime_free_minutes = 100;
double premium_nighttime_extra_minutes_cost = 0.05;
// Read in the total number of minutes used
int minutes_used;
std::cout << "Enter the total number of minutes used: ";
std::cin >> minutes_used;
// Calculate the bill for regular service
double regular_bill = regular_cost;
if (minutes_used > regular_free_minutes) {
regular_bill += (minutes_used - regular_free_minutes) * regular_extra_minutes_cost;
}
// Calculate the bill for premium service
double premium_bill = premium_cost;
if (minutes_used > premium_daytime_free_minutes) {
premium_bill += (minutes_used - premium_daytime_free_minutes) * premium_daytime_extra_minutes_cost;
}
if (minutes_used > premium_nighttime_free_minutes) {
premium_bill += (minutes_used - premium_nighttime_free_minutes) * premium_nighttime_extra_minutes_cost;
}
// Print the bills
std::cout << "Regular service bill: $" << regular_bill << std::endl;
std::cout << "Premium service bill: $" << premium_bill << std::endl;
return 0;
}
Learn more about programming:
https://brainly.com/question/26134656
#SPJ4


What is meaning of lunch bar
Answers
A lunch bar is a restaurant where the public may purchase cold meals in containers, cold wrapped sandwiches, drinks, or items retrieved through coin operated compartments for consumption on or off the premises.
One of the files is substr.awk. Your job is to edit this file so it will output all of the character sequences of a certain length found in a text input file. Another file is wordlist.txt, which is a text file containing about 60,000 English words, one word per line. Here are the first lines of wordlist.txt:
a
aardvark
aardwolf
ab
aba
abaca
abacist
Answers
The `substr.awk` file is responsible for outputting all the character sequences of a particular length, found in a text input file. Below is how to edit it to output all of the character sequences of a specific length:
```
#!/usr/bin/awk -fBEGIN {
length = 3 # Change this value to the desired length of the character sequences
}
{
for (i=1; i<=length; i++) {
for (j=1; j<=length-i+1; j++) {
print substr ($0, j, i);
}
}
}
```
For instance, if you need to output all the 4-letter character sequences, replace `length = 3` with `length = 4`. And here is a sample of how to use `wordlist.txt` to obtain all the 4-letter words:`awk 'length($0) == 4' wordlist.txt` This command will print all the words in `wordlist.txt` that have a length of 4 characters.
Learn more about character sequences: https://brainly.com/question/32352749
#SPJ11
which two oci virtual cloud network network firewall features can be used to control traffic
Answers
The two OCI virtual cloud network firewall features that can be used to control traffic are Security Lists and Network Security Groups.
Security Lists are used to control traffic at the subnet level, whereas Network Security Groups are used to control traffic at the instance level. Both of these features allow for granular control over traffic flow within the cloud network, helping to ensure the security and integrity of the infrastructure.
Security Lists : Security rules are used to define which types of traffic are allowed to flow in and out of a subnet in a VCN. Security rules are stateful, which means that they allow return traffic that matches the outbound traffic that was allowed. Security rules can be defined based on IP protocol, source and destination IP addresses, source and destination port ranges, and the direction of traffic flow (inbound or outbound).
Network Security Groups: Network security groups are used to define a set of security rules that can be applied to one or more resources in a VCN. A network security group acts as a virtual firewall that controls inbound and outbound traffic to and from the resources that are associated with the group. Network security groups are stateful and can be used to restrict traffic based on source and destination IP addresses, source and destination port ranges, and the direction of traffic flow (inbound or outbound).
To know more about OCI, visit:
https://brainly.com/question/31140085
#SPJ11
who are bill Gates customers?
Answers
Bill Gates has customers from Microsoft.
Your answer is Microsoft!
Answer:
Microsoft people! The people who buy pcs and xboxs
Explanation: