III. FILL-IN THE BLANK (five points each)
11. Open divided scales have scales going in
directions.
12. There are
groups of scales.
13. The open divided scales have an
unit preceding zero.
14. The triangular scale can have up to
different scales on one piece of plastic.
15. The mechanical inch is divided into
equal parts.
Answers
Related Questions
If any one has mincraft on ps4 bedrock we can finish building a BIG city world all we need to put is a shop and money dispensers thx
Answers
Answer:
cool i want a ps5
Explanation:
helllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllo
Answers
Hi, I have to make this at least 20 characters long
1.
Question 1
An online gardening magazine wants to understand why its subscriber numbers have been increasing. What kind of reports can a data analyst provide to help answer that question? Select all that apply.
1 point
Reports that examine how a recent 50%-off sale affected the number of subscription purchases
Reports that describe how many customers shared positive comments about the gardening magazine on social media in the past year
Reports that compare past weather patterns to the number of people asking gardening questions to their social media
Reports that predict the success of sales leads to secure future subscribers
2.
Question 2
Fill in the blank: A doctor’s office has discovered that patients are waiting 20 minutes longer for their appointments than in past years. To help solve this problem, a data analyst could investigate how many nurses are on staff at a given time compared to the number of _____.
1 point
doctors on staff at the same time
negative comments about the wait times on social media
patients with appointments
doctors seeing new patients
3.
Question 3
Fill in the blank: In data analytics, a question is _____.
1 point
a subject to analyze
an obstacle or complication that needs to be worked out
a way to discover information
a topic to investigate
4.
Question 4
When working for a restaurant, a data analyst is asked to examine and report on the daily sales data from year to year to help with making more efficient staffing decisions. What is this an example of?
1 point
An issue
A business task
A breakthrough
A solution
5.
Question 5
What is the process of using facts to guide business strategy?
1 point
Data-driven decision-making
Data visualization
Data ethics
Data programming
6.
Question 6
At what point in the data analysis process should a data analyst consider fairness?
1 point
When conclusions are presented
When data collection begins
When data is being organized for reporting
When decisions are made based on the conclusions
7.
Question 7
Fill in the blank: _____ in data analytics is when the data analysis process does not create or reinforce bias.
1 point
Transparency
Consideration
Predictability
Fairness
8.
Question 8
A gym wants to start offering exercise classes. A data analyst plans to survey 10 people to determine which classes would be most popular. To ensure the data collected is fair, what steps should they take? Select all that apply.
1 point
Ensure participants represent a variety of profiles and backgrounds.
Survey only people who don’t currently go to the gym.
Collect data anonymously.
Increase the number of participants.
Answers
The correct options are:
Reports that examine how a recent 50%-off sale affected the number of subscription purchasespatients with appointmentsa way to discover informationA business taskData-driven decision-makingWhen conclusions are presentedFairnessa. Ensure participants represent a variety of profiles and backgrounds.c. Collect data anonymously.d. Increase the number of participants.What is the sentences about?This report looks at how many people bought subscriptions during a recent sale where everything was half price. This will show if the sale made more people subscribe and if it helped increase the number of subscribers.
The report can count how many nice comments people said and show if subscribers are happy and interested. This can help see if telling friends about the company has made more people become subscribers.
Learn more about gardening from
https://brainly.com/question/29001606
#SPJ1
Reports, investigating, fairness, data-driven decision-making, gym classes
Explanation:Question 1:A data analyst can provide the following reports to help understand why the subscriber numbers of an online gardening magazine have been increasing:
Reports that examine how a recent 50%-off sale affected the number of subscription purchasesReports that describe how many customers shared positive comments about the gardening magazine on social media in the past yearReports that compare past weather patterns to the number of people asking gardening questions on their social mediaReports that predict the success of sales leads to secure future subscribersQuestion 2:A data analyst could investigate the number of patients with appointments compared to the number of doctors on staff at a given time to help solve the problem of longer waiting times at a doctor's office.
Question 3:In data analytics, a question is a topic to investigate.
Question 4:When a data analyst is asked to examine and report on the daily sales data from year to year to help with making more efficient staffing decisions for a restaurant, it is an example of a business task.
Question 5:The process of using facts to guide business strategy is called data-driven decision-making.
Question 6:A data analyst should consider fairness when conclusions are being presented during the data analysis process.
Question 7:Transparency in data analytics is when the data analysis process does not create or reinforce bias.
Question 8:To ensure the collected data is fair when surveying 10 people to determine popular classes for a gym, a data analyst should: ensure participants represent a variety of profiles and backgrounds, collect data anonymously, and increase the number of participants.
Learn more about Data analysis here:https://brainly.com/question/33332656
Quinton has been asked to analyze the TTPs of an attack that recently occurred and prepare an SOP to hunt for future treats. When researching the recent attack, Quinton discovered that after penetrating the system, the threat actor moved through the network using elevated credentials. Which technique was the threat actor using to move through the network?
Answers
There are different kinds of movement. The technique that was the threat actor using to move through the network is Lateral Movement.
Network Lateral Movement, is simply known as a method used by cyber attackers, or threat actors, to quickly move through a network as they search for the key data and assets that are the main hit or target of their attack work.
In this kind of movement, when an attacker do compromise or have the power or control of one asset within a network, it quickly transport or moves on from that device to others while still within the same network.
Examples of Lateral movement are:
Pass the hash (PtH) Pass the ticket (PtT) Exploitation of remote services, etc.See full question below
Quinton has been asked to analyze the TTPs of an attack that recently occurred and prepare an SOP to hunt for future treats. When researching the recent attack, Quinton discovered that after penetrating the system, the threat actor moved through the network using elevated credentials. Which technique was the threat actor using to move through the network?
A. Initial Compromise
B. Lateral movement
C. Privilege escalation
D. Data exfiltration
Learn more about Lateral movement from
https://brainly.com/question/1245899
Which number is equivalent to 72.5e-2?
0.725
72.5
7.25
7250
Answers
Answer:
.725
Explanation:
You are going back 2 spaces.
Answer:
0.725
Explanation:
Edge 2022

The Mac OS was the first to use a graphical user interface.
False
True
Answers
Hope this helps
joe Hubb does not have a secure workplace to do payroll and store confidential records in the store. He uses a space in his home exclusively for this purpose and documents the use thoroughly. What form is used to calculate his office in the home deduction
Answers
Answer:
Joe Hubb can use Form 8829 to calculate his office in the home deduction.
Explanation:
Based on the scenario, Joe is a self-employed taxpayer. Self-employed taxpayers who are filing IRS Schedule C, Profit or Loss from Business (as Sole Proprietorship) calculate their 'Expenses for Business Use of Home' on Form 8829. The expenses that are deductible include costs of electricity, heating, maintenance, cleaning supplies, and minor repairs, but only the business-use portions.
Where do charts get the data series names?
O data entries
O row labels
O column labels
O worksheet title
Answers
Answer:
B) Row labels
Explanation:

list different power options of computer
Answers
Answer:
1. System Standby
2. System Hibernation
3. System shutdown
4. System restart
name 3 supercomputers along with their cost, purpose and the country it is located.
Answers
Answer:
The three super computers are
a) Fujitsu Fugak
b) IBM Summit/IBM/Nvidia/Mellanox
c) Sunway TaihuLigh
Explanation:
Three super computers are as follows
a) Fujitsu Fugak - It is located in Kobe, Japan and its costs is ¥130 billion
b) IBM Summit/IBM/Nvidia/Mellanox - It is located in Oak Ridge, U.S. and it costs $325 million
c) Sunway TaihuLigh- It is located in Wuxi, China and it costs US$273 million
How do you remove the account. I made it w/Googol
Answers
It should be noted that to eradicate a account, follow these steps:
How to delete the accountBegin by accessing the Account page . Subsequently, log into the respective account you would like to remove. Locate and click on "Data & Personalization" tab adjacent to its left-hand menu.
Afterward, drag your attention to the section titled: "Download, delete, or make a plan for your data," from where you can select "Delete a service or your account". Carry out procedures instructed on that landed page to verify the account's removal. Be it known deleting an account implies permanent eradication of every information.
Learn more about account on
https://brainly.com/question/26181559
#SPJ1
Need help with this python question I’m stuck



Answers
It should be noted that the program based on the information is given below
How to depict the programdef classify_interstate_highway(highway_number):
"""Classifies an interstate highway as primary or auxiliary, and if auxiliary, indicates what primary highway it serves. Also indicates if the (primary) highway runs north/south or east/west.
Args:
highway_number: The number of the interstate highway.
Returns:
A tuple of three elements:
* The type of the highway ('primary' or 'auxiliary').
* If the highway is auxiliary, the number of the primary highway it serves.
* The direction of travel of the primary highway ('north/south' or 'east/west').
Raises:
ValueError: If the highway number is not a valid interstate highway number.
"""
if not isinstance(highway_number, int):
raise ValueError('highway_number must be an integer')
if highway_number < 1 or highway_number > 999:
raise ValueError('highway_number must be between 1 and 999')
if highway_number < 100:
type_ = 'primary'
direction = 'north/south' if highway_number % 2 == 1 else 'east/west'
else:
type_ = 'auxiliary'
primary_number = highway_number % 100
direction = 'north/south' if primary_number % 2 == 1 else 'east/west'
return type_, primary_number, direction
def main():
highway_number = input('Enter an interstate highway number: ')
type_, primary_number, direction = classify_interstate_highway(highway_number)
print('I-{} is {}'.format(highway_number, type_))
if type_ == 'auxiliary':
print('It serves I-{}'.format(primary_number))
print('It runs {}'.format(direction))
if __name__ == '__main__':
main()
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
how do you fill different data into different cells at a time in Excel
Answers
The way that you fill different data into different cells at a time in Excel are:
Click on one or a lot of cells that you want to make use of as the basis that is needed for filling additional cells. For a set such as 1, 2, 3, 4, 5..., make sure to type 1 and 2 into the 1st two cells. Then pull the fill handle .If required, select Auto Fill Options. and select the option you want.How do you make a group of cells auto-fill?The first thing to do is to place the mouse pointer over the cell's bottom right corner and hold it there until a black + symbol appears. Drag the + symbol over the cells you wish to fill in while clicking and holding down the left mouse button. Additionally, the AutoFill tool rightly fills up the series for you.
Note that Excel data entering can be automated and this can be done by: On the Data tab, select "Data Validation," then click "Data Validation." In the Allow box, select "List." Enter your list items in the Source box, separating them with commas. To add the list, click "OK." If you wish to copy the list along the column, use the Fill Handle.
Learn more about Excel from
https://brainly.com/question/25879801
#SPJ1
If you determine that the hard drive is experiencing excessive use but the Windows Experience Index reports that memory is the system bottleneck, which component do you upgrade first: memory or the hard drive? Why?
Answers
The reason why is it is good to use an Upgrade memory is because low amounts of memory can lead to much use of the hard drive and based n the fact that it is not costly to upgrade memory than to upgrade the hard drive.
What is upgrading memory?This is known to b an act done so as to improve the performance of a computer.
It is often known as a RAM or system memory upgrade. An upgrade implies that one is adding memory modules along with the ones that were there or replacing the old ones. It is less costly when compared to hard drive upgrade.
Learn more about Upgrade memory from
https://brainly.com/question/13196228
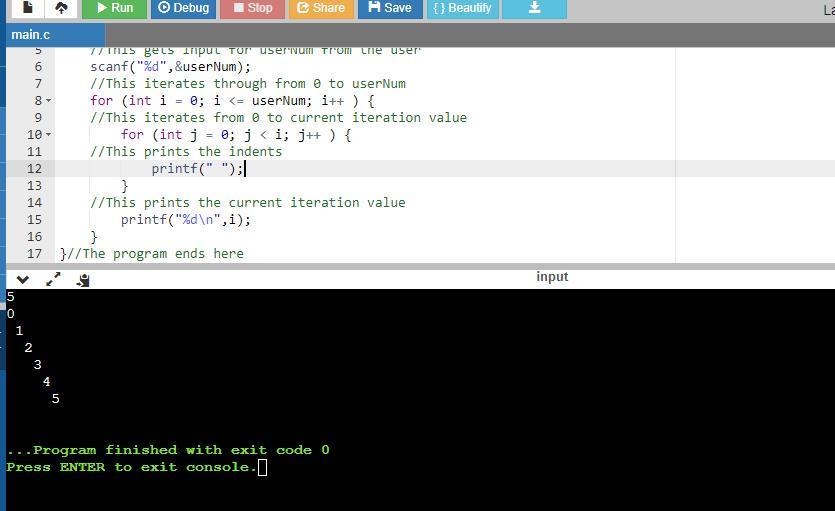
In C language. Print numbers 0, 1, 2, ..., userNum as shown, with each number indented by that number of spaces. For each printed line, print the
leading spaces, then the number, and then a newline. Hint: Use i and j as loop variables (initialize i and j explicitly). Note: Avoid any
other spaces like spaces after the printed number. Ex: userNum = 3 prints:
Answers
The program uses loops to print the numbers from 0 to the user input.
It also uses loops to print the indented space before each iteration value.
The program in C where comments are used to explain each line is as follows:
#include <stdio.h>
int main(){
//This declares userNum as integer
int userNum;
//This gets input for userNum from the user
scanf("%d",&userNum);
//This iterates through from 0 to userNum
for (int i = 0; i <= userNum; i++ ) {
//This iterates from 0 to current iteration value
for (int j = 0; j < i; j++ ) {
//This prints the indents
printf(" "); }
//This prints the current iteration value
printf("%d\n",i); }
}//The program ends here
At the end of the program, the program outputs the indent, followed by the iteration value and a new line.
See attachment for the program sample run
Read more about loops at:
https://brainly.com/question/21751160
True or False? As an abstract data type, trees can represent more complex relationships than linear types.
One such example would be a heirarchy of data items.
1) True
2) False
???
Answers
Answer:
True.
Explanation:
The hierarchy is the complex data about the trees.
Which number system is based on 1s and 0s? Binary Decimal Digital Whole
Answers
Answer:
6.78
Explanation:
Answer:
Binary Number System
Explanation:
binary number is a number expressed in base 2 numeral system for binary numeral system, a method of mathematical expression which uses only two systems: typically 0 and 1.
Find the following series of 8,88,888,8888,88888
Answers
the sum to n terms of the sequence 8, 88, 888, 8888,..... is 80/80(10ⁿ-1) -8/9n
How is this so?The nth terms is solved as follows
Sⁿ =8+88+888+8888+......+n terms
= 8/9 [9+99+999+9999+....to n terms]
= 8/9 [(10−1)+(10² −1+(10³ −1)+(10⁴ −1+....to n terms]
= 8/9 [(10+(10²+(10³ .....n terms) - (1 + 1 + 1 + ....n terms)
= 8/9 [(10(10ⁿ-1))/(10-1) - n] [Sun of GP= a(rⁿ-1)/(r-1) when r > 1]
= 8/9 [ 10 (10ⁿ -1)/9) -n]
= 80/81(10ⁿ -1) -8/9n
Thus, it is correct to state that 80/81(10ⁿ -1) -8/9n
Learn more about Series:
https://brainly.com/question/26263191
#SPJ1
Full Question:
Find the sum to n terms of the sequence 8, 88, 888, 8888,
Assume a fully associative write-back cache with many cache entries that starts empty. Below is sequence of eight memory operations (The address is in square brackets):
Read Mem[300];
Write Mem[100];
Write Mem[100];
Read Mem[200];
Write Mem[200];
Read Mem[100];
Write Mem[100];
Write Mem[100];
Answers
Answer:
Please mark me the brainliest
We can use the following steps to simulate the given sequence of memory operations in a fully associative write-back cache:
Explanation:
1. Read Mem[300]:
- The cache is empty, so we have a cache miss and bring the block containing Mem[300] into the cache.
- The block is now in the cache.
2. Write Mem[100]:
- The cache currently only contains a block for Mem[300], so we have a cache miss and bring the block containing Mem[100] into the cache.
- The block is now in the cache.
- The value of Mem[100] in the cache is updated with the new value.
3. Write Mem[100]:
- The block containing Mem[100] is already in the cache, so we have a cache hit.
- The value of Mem[100] in the cache is updated with the new value.
- Note that this write operation is redundant, since the value of Mem[100] was already updated in step 2.
4. Read Mem[200]:
- The block containing Mem[200] is not in the cache, so we have a cache miss and bring the block into the cache.
- The block is now in the cache.
5. Write Mem[200]:
- The block containing Mem[200] is already in the cache, so we have a cache hit.
- The value of Mem[200] in the cache is updated with the new value.
6. Read Mem[100]:
- The block containing Mem[100] is already in the cache, so we have a cache hit.
- The value of Mem[100] in the cache is not changed.
7. Write Mem[100]:
- The block containing Mem[100] is already in the cache, so we have a cache hit.
- The value of Mem[100] in the cache is updated with the new value.
8. Write Mem[100]:
- The block containing Mem[100] is already in the cache, so we have a cache hit.
- The value of Mem[100] in the cache is updated with the new value.
- Note that this write operation is redundant, since the value of Mem[100] was already updated in step 7.
At the end of these operations, the cache contains blocks for Mem[200] and Mem[100], with the value of Mem[200] being the most recent value written to that address. The value of Mem[100] in the cache is the same as the value written in step 8.
Below functions flatten the nested list of integers (List[List[int]]) into a single list and remove duplicates by leaving only the first occurrences. When the total number of elements is N, choose the one that correctly compares the time complexity with respect to N of each function.
f1 = f3 < f2
f1 = f2 < f3
f3 < f1 = f2
f3 < f1 < f2
f1 = f2 = f3
![Below functions flatten the nested list of integers (List[List[int]]) into a single list and remove duplicates](https://i5t5.c14.e2-1.dev/h-images-qa/contents/attachments/7SabddIpXbmIZVUz3Vbha6czJ9luF36Q.png)
Answers
The time complexities of the functions is (a) f1 = f3 < f2
How to compare the time complexities?The time complexities of the functions are dependent on the loops and conditional statements in the function.
From the given code, we have the following highlights:
Function f1: 2 loops and 1 conditional statementFunction f2: 2 loops and 1 conditional statement in the second loopFunction f3: 2 loops and 1 conditional statementConsidering the function f2
The conditional statement in the second loop implies that the conditional statement would be executed several times as long as the loop is valid.
This means that:
f2 > f1 and f2 > f3
Functions f1 and f3 have equal loops and conditional statement.
This means that
f1 = f3
So, we have:
f2 > f1 = f3
Rewrite as:
f1 = f3 < f2
Hence, the time complexities of the functions is (a) f1 = f3 < f2
Read more about time complexities at:
https://brainly.com/question/15549566
#SPJ1
Please help!
Which of the following statements provides the most accurate assessment of the current legal situation as it pertains to cyberbullying?
.
.
A- The current laws are adequate to deal with cyberbullying, but they are not being properly enforced.
The current laws are adequate to deal with cyberbullying, but they are not being properly enforced.
B- The current laws are not yet adequate to deal with cyberbullying, and the existing laws are difficult to enforce.
The current laws are not yet adequate to deal with cyberbullying, and the existing laws are difficult to enforce.
C- The current laws are more than adequate to deal with cyberbullying, and they are being fully enforced.
The current laws are more than adequate to deal with cyberbullying, and they are being fully enforced.
D- The current laws are not adequate to deal with cyberbullying, but the existing laws are plentiful and easy to enforce.
Answers
I got it right ……..!3$:&/‘sbs
................. are used to summarize data (option) (a) report (b) action
Answers
i think report is right for the question
Is it possible to compare 2 pre-packaged versions in cpi?
Answers
Yes, it is possible to compare two pre-packaged versions in the Consumer Price Index (CPI), but it can be challenging due to certain limitations of the index.
The CPI is designed to measure changes in the overall price level of a basket of goods and services consumed by households.
It focuses on broad categories and representative items within those categories, rather than specific versions of products.
When it comes to pre-packaged versions of products, there can be variations in size, quality, branding, and other attributes that may affect their prices differently.
These variations make direct comparisons complex within the framework of the CPI.
To compare two specific pre-packaged versions within the CPI, it would require detailed data on their specific characteristics and how they align with the representative item in the CPI basket.
This level of granularity may not be readily available in the public domain or within the CPI methodology.
For more questions on Consumer Price Index
https://brainly.com/question/8416975
#SPJ8
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

To specify the data sets you want to see for your particular user, you create or select a
d
Select one:
a. Filter
b. View
c. Switch
d. Scope
Answers
Answer:
B
Explanation:
Nathan takes a close-up photography of a sticky cone of cotton candy. What element of art is he trying to use?
A.
emphasis
B.
foreground, middleground, and background
C.
texture
D.
value
Answers
Answer:
C. texture
Explanation:
Nathan is likely trying to use the element of art known as texture in his close-up photography of a sticky cone of cotton candy. Texture refers to the surface quality or feel of an object, and can be visual or tactile. In Nathan's case, he is likely trying to capture the unique visual texture of the cotton candy, highlighting its soft, fluffy appearance and sticky, sugary surface.
Create a conditional expression that evaluates to string "negative" if userVal is less than 0, and "non-negative" otherwise. Ex: If userVal is -9, out
Answers
Answer:
import java.util.Scanner;
public class Main
{
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
System.out.print("Enter a number: ");
int userVal = input.nextInt();
String aString;
if(userVal < 0)
aString = "negative";
else
aString = "non-negative";
System.out.println(aString);
}
}
Explanation:
Ask the user to enter a number and set it to userVal
Check the value of userVal. If it is smaller than 0, set the string as "negative". If it is not, set it as "non-negative"
Print the string
some context free languages are undecidable
Answers
The way a system can differentiate between two applications attempting to send and receive information via the network is through the use of what
Answers
Answer:
Processes
Explanation:
Given that Process is a term in computer networking that defines the program moving between two systems.
This is carried out through what is known as interprocess communication. Here, Processes differentiate between two applications by ensuring the sending process identifies the receiving process.
This is done by identifying the name or address of the host computer and then again identify the identifier that defines the identity of the receiving process on the destination host.
Hence, The way a system can differentiate between two applications attempting to send and receive information via the network is through the use of PROCESSES
email is suitable for which of the following types of messages in business? (choose every correct answer.)
Answers
Email is suitable for Informational, Promotional , Transactional , Networking.
What is Email
Email (short for "electronic mail") is a method of exchanging digital messages from an author to one or more recipients. Email is sent through a network of computers using a protocol called SMTP (Simple Mail Transfer Protocol). Email messages can contain text, files, images, or other attachments sent as a single block of data. Since its inception in the early 1970s, email has evolved into one of the most widely used forms of digital communication. It is used for a variety of purposes, including business communication, personal correspondence, and sharing of information and files.
To know more about Email
https://brainly.com/question/29444693
#SPJ4