In the code below, what's the final value of the variable x?
var x = 8;
x = x - 6;
x = x * 3;
Answers
Answer:
First equation x=4
second equation x=3
Explanation:
The question is telling us that 'X' is equal to 8. It's another way of representing this number using X as the variable replacing it.
We input 8 instead of the X to solve the equation, and here in the picture, you can see where I went from there.
Do the same thing for the other equation.
I hope this helps :)

Related Questions
solution identification, understand the process methods and information that are in the diagnostic process
Answers
The process of diagnosing involves a way to identify and understand problems or issues in a step-by-step way.
What is the diagnostic process?The way one can figure out what's wrong with something can be different depending on what it is (like a medical problem or a broken machine), but there are usually some basic steps and parts that we follow.
Getting Information: In this step, you gather important information and details about the problem or situation. This could mean talking to a patient about their health history, checking what kind of symptoms they have, or finding out details about a problem with a machine.
Learn more about diagnostic process from
https://brainly.com/question/3787717
#SPJ1
Question 1 (1 point)
Jenna has created a wizard class. She has used the class to build two wizard objects
a
in her game. Which programming term describes the objects that Jenna built using
the wizard class?
A. Occurrences
B. Subclasses
C. Instances
D. Methods
Answers
Answer:
Subclasses
Explanation:
It's B for Plato students, took this not that long ago!
What is the value of alpha at the end of the loop?
alpha = 1;
loopCount = 1;
while (loopCount <= 3)
{
alpha = alpha + 10;
loopCount++;
}
a
10
b
21
c
31
d
1
e
3
PLEASE HELP NEED ANWSER FAST THANK YOU
Answers
Answer:
answer is D
Explanation:
Because alpha equal to 1
a really excellent way of getting you started on setting up a workbook to perform a useful function.
Answers
Templates a really excellent way of getting you started on setting up a workbook to perform a useful function.
What is the workbook about?One excellent way to get started on setting up a workbook to perform a useful function is to begin by defining the problem you are trying to solve or the goal you want to achieve. This will help you determine the necessary inputs, outputs, and calculations required to accomplish your objective.
Once you have a clear understanding of your goal, you can start designing your workbook by creating a plan and organizing your data into logical categories.
Next, you can start building the necessary formulas and functions to perform the required calculations and operations. This might involve using built-in functions such as SUM, AVERAGE, or IF, or creating custom formulas to perform more complex calculations.
Read more about workbook here:
https://brainly.com/question/27960083
#SPJ1
In North America, power cords must use a plug compatible with which of the following standards?
Answers
Answer:
NEMA 5-15
Explanation:
I hope this helps
In which views can a user add comments to a presentation? Check all that apply.
Outline view
Normal view
Protected view
Slide Sorter view
Notes Page view
Answers
Note that the view that a user can add comments to in a presentation ar:
Normal View;(Option B) and
Notes Page View. (Option E).
How are the above views defined?
Microsoft PowerPoint affords users three possible approaches for adding comments to their presentations: Normal view, Notes Page veiw, and Slide Show view via pointer annotations.
In Normal view, users can create straightforward slide-specific feedback by selecting a slide and clicking the "New Comment" buton in the Comments section.
Meanwhile, Notes Page view enables users to enter more detailed feedback by adding notes specifically for each slide's notes section.
Learn more about presentations:
https://brainly.com/question/649397
#SPJ1
Answer: outline & normal view
Explanation:
Which of the following methods should you use to configure dynamic libraries on a Linux system? (Select TWO).
Answers
The methods listed below ought to be used to configure dynamic libraries on a Linux system:
(A) Modify /etc/ld.so.conf to add the path of the libraries.
(B) Use the LD_LIBRARY_PATH environment variable to specify additional directories to search for library files.
What is a Linux system?A Unix-like operating system (OS) for desktops, servers, mainframes, mobile devices, and embedded devices, Linux is open-source and user-developed.
One of the most broadly supported operating systems, it is supported on almost all popular computing platforms, including x86, ARM, and SPARC.
Windows OS is a for-profit operating system, whereas Linux is an open-source alternative.
In contrast to Windows, which lacks access to the source code, Linux allows users to modify the code as needed.
On a Linux system, the following techniques should be used to configure dynamic libraries:
(A) Modify /etc/ld.so.conf to add the path of the libraries.
(B) Use the LD_LIBRARY_PATH environment variable to specify additional directories to search for library files.
Therefore, the methods listed below ought to be used to configure dynamic libraries on a Linux system:
(A) Modify /etc/ld.so.conf to add the path of the libraries.
(B) Use the LD_LIBRARY_PATH environment variable to specify additional directories to search for library files.
Know more about a Linux system here:
https://brainly.com/question/29773084
#SPJ4
Complete question:
Which of the following methods should you use to configure dynamic libraries on a Linux system? (Select TWO).
(A) Modify /etc/ld.so.conf to add the path of the libraries.
(B) Use the LD_LIBRARY_PATH environment variable to specify additional directories to search for library files.
data is information, information is Data, comparison of both
Answers
Answer:
"Data is raw, unorganized facts that need to be processed. Data can be something simple and seemingly random and useless until it is organized. When data is processed, organized, structured or presented in a given context so as to make it useful, it is called information. Each student's test score is one piece of data. "
Data is defined as facts or figures, or information that's stored in or used by a computer. An example of data is information collected for a research paper. An example of data is an email.
Hope this Helps
Mark Brainiest
In the screenshot of Filezilla shown below, what is the purpose of the windows outlined in red?
Please help. I'm SO confused. I used my resources to help me try to find the answer but sadly I couldn't find anything.
A.
Shows connection status
B.
Shows files on FTP site
C.
Shows files on local computer
D.
Shows file transfer status

Answers
How do you think productivity software like Microsoft Office might be useful in the healthcare field?
Answers
Microsoft Office offers several applications that are widely used in the healthcare field. Here are some of the common uses of Microsoft Office in healthcare:
Microsoft Word: It is extensively used in healthcare for creating and formatting documents such as patient reports, medical records, and referral letters.Microsoft Excel: It is used for data analysis, tracking patient records, managing inventory, financial calculations, and creating charts or graphs for a visual representation of data.Microsoft PowerPoint: PowerPoint is commonly used in healthcare for creating presentations, training materials, educational content, and reports.Learn more about Microsoft Office, here:
https://brainly.com/question/15131211
#SPJ1
For each of the cache modifications that we could perform, select whether it will increase, decrease, have no effect, or have an unknown effect on the parameter. An unknown effect means that it could either decrease or increase the parameter in question. No effect also includes marginal or very little effect When answering for multilevel caching, answer based on the caching system as a whole. Improvement Hit Rate Cache Access Time Average Memory Access Time Increase Cache Size (C) Increase Increase Increase Increase Associativity(K) Increase Increase [ Select ] Increase Block Size(b) Decrease Increase [ Select ] Use Multilevel Caching Increase
Answers
The question above is related to the effects of modifications related to the Computer Cache.
What is a Computer Cache?A computer cache is a technical name for the part of the computer called the CPU Cache Memory. It may also be referred to as the temporary memory.
Usually, it serves the purpose of allowing the computer to access information faster than it would normally take to get them directly from the hard drive.
See the results below for what happens when certain modifications to the Cache are made:
Increase in Cache Size = Increase in Computer PerformanceIncrease in Associativity (K) = Increase in Computer Performance, especially of memory system and processor.Increase in Block Size = Increase in overall performance, especially where many and various sizes of files are concernedThe Use of Multi-level Caching = Decreased Performance.Learn more about Computer Cache at:
https://brainly.com/question/3406184
Need help with this python question I’m stuck



Answers
It should be noted that the program based on the information is given below
How to depict the programdef classify_interstate_highway(highway_number):
"""Classifies an interstate highway as primary or auxiliary, and if auxiliary, indicates what primary highway it serves. Also indicates if the (primary) highway runs north/south or east/west.
Args:
highway_number: The number of the interstate highway.
Returns:
A tuple of three elements:
* The type of the highway ('primary' or 'auxiliary').
* If the highway is auxiliary, the number of the primary highway it serves.
* The direction of travel of the primary highway ('north/south' or 'east/west').
Raises:
ValueError: If the highway number is not a valid interstate highway number.
"""
if not isinstance(highway_number, int):
raise ValueError('highway_number must be an integer')
if highway_number < 1 or highway_number > 999:
raise ValueError('highway_number must be between 1 and 999')
if highway_number < 100:
type_ = 'primary'
direction = 'north/south' if highway_number % 2 == 1 else 'east/west'
else:
type_ = 'auxiliary'
primary_number = highway_number % 100
direction = 'north/south' if primary_number % 2 == 1 else 'east/west'
return type_, primary_number, direction
def main():
highway_number = input('Enter an interstate highway number: ')
type_, primary_number, direction = classify_interstate_highway(highway_number)
print('I-{} is {}'.format(highway_number, type_))
if type_ == 'auxiliary':
print('It serves I-{}'.format(primary_number))
print('It runs {}'.format(direction))
if __name__ == '__main__':
main()
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
When the InfoSec management team’s goals and objectives differ from those of the IT and general management communities, what items should be considered for the resolution, and who should be involved and provide an example of a situation where such a conflict might exist
Answers
phone holder 2 questions
Ronaldo wants to determine if employees would prefer having bagels or
donuts at morning meetings. Which method would be best to collect this
information?
Answers
Answer:
surveys and questionnaires
Answer:
Survey
Explanation:
There are many different LAN technologies (Wifi, Ethernet, etc) that can be incompatible with each other in terms of how they exchange data. How is it possible then, that any source host can still send information to any destination host when connected in an internet? Explain the two important components of this process.
Answers
Answer:
Explanation:
The two most important parts of this process are simply sending and receiving the data. When a network sends data, the system breaks the data into smaller pieces called Packets. The system then checks if the network that the packets are being sent to exists, if so the packets are sent to that network. When the receiving network's router receives these packets it reconstructs all of the packets received into the final data in the format that the final LAN system can read and sends it to the appropriate device.
Deb needs to add borders on the cells and around the table she has inserted into her Word document.
Insert tab, Tables group
Table Tools Design contextual tab
Home tab, Page Layout
Home tab, Format group
Answers
Answer:
Design tab
Explanation:
Select the call or table that you will like to useThen select the design tabIn the group page background select Page Borders There you will have multiple choses for where you want your borderYou can even customize your border by pressing Custom Border at the bottom of the list for Page BordersAnswer:
Table tools design contextual tab
Explanation:
pls tell me the answer pls i need the answer

Answers
Answer:
focus
Explanation:
specialize means concentrate on and become expert in a particular subject or skill.
Joseline is trying out a new piece of photography equipment that she recently purchased that helps to steady a camera with one single leg instead of three. What type of equipment is Joseline trying out?
A. multi-pod
B. tripod
C. semi-pod
D. monopod
Answers
Joseline trying out tripod .A camera-supporting three-legged stand is known as a tripod. For stability, cameras are fixed on tripods, sometimes known as "sticks." In tripods, the fluid head is used. The camera may now tilt up and down in addition to pan left and right.
What tools are employed in photography?You will need a camera with manual settings and the ability to change lenses, a tripod, a camera case, and a good SD card if you're a newbie photographer who wants to control the visual impacts of photography. The affordable photography gear listed below will help you get started in 2021.A monopod, which is a one-legged camera support system for precise and stable shooting, is also known as a unipod.A camera-supporting three-legged stand is known as a tripod. For stability, cameras are fixed on tripods, sometimes known as "sticks." In tripods, the fluid head is used. The camera may now tilt up and down in addition to pan left and right.To learn more about tripod refer to:
https://brainly.com/question/27526669
#SPJ1
Answer:
monopod
Explanation:
Which symbol is present on the home row of the keyboard?
A.
apostrophe
B.
question mark
C.
comma
D. period
Answers
Answer:
the answer is A. an apostrophe
Answer:
A I took the test
Explanation:
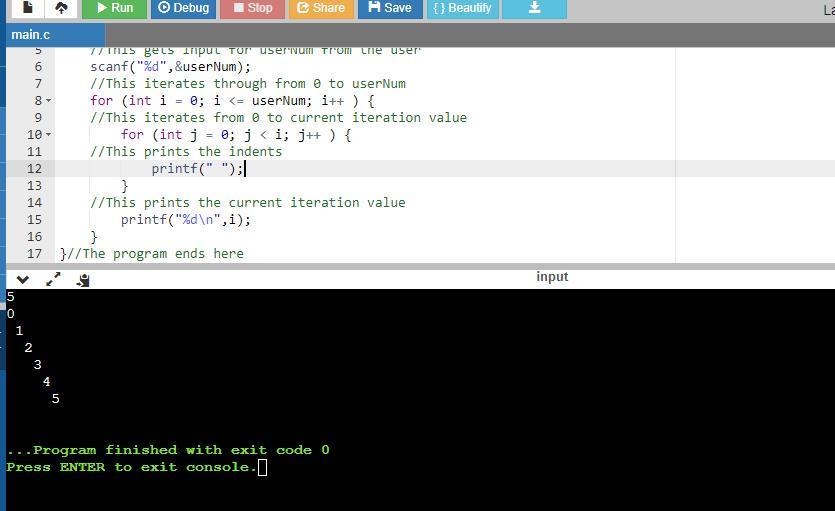
In C language. Print numbers 0, 1, 2, ..., userNum as shown, with each number indented by that number of spaces. For each printed line, print the
leading spaces, then the number, and then a newline. Hint: Use i and j as loop variables (initialize i and j explicitly). Note: Avoid any
other spaces like spaces after the printed number. Ex: userNum = 3 prints:
Answers
The program uses loops to print the numbers from 0 to the user input.
It also uses loops to print the indented space before each iteration value.
The program in C where comments are used to explain each line is as follows:
#include <stdio.h>
int main(){
//This declares userNum as integer
int userNum;
//This gets input for userNum from the user
scanf("%d",&userNum);
//This iterates through from 0 to userNum
for (int i = 0; i <= userNum; i++ ) {
//This iterates from 0 to current iteration value
for (int j = 0; j < i; j++ ) {
//This prints the indents
printf(" "); }
//This prints the current iteration value
printf("%d\n",i); }
}//The program ends here
At the end of the program, the program outputs the indent, followed by the iteration value and a new line.
See attachment for the program sample run
Read more about loops at:
https://brainly.com/question/21751160
What is the primary purpose of a namespace?
Answers
Answer:
A namespace ensures that all of a given set of objects have unique names so that they can be easily identified.
Explanation:
Answer:
A namespace ensures that all of a given set of objects have unique names so that they can be easily identified.
Explanation:
seven and two eighths minus five and one eighth equals?
Answers
Answer: 2.125
Explanation
Rewrite the following pseudocode to include two more scores, 99 and 87. start num myScores[10] = 78,95,84,92,88,85,94,89,97,82 num counter = 0 num highest = 0 while counter < 10 if myScores[counter] > highest then highest = myScores[counter] endif counter = counter + 1 endwhile output highest stop
Answers
start
num myScores[12] = 78,95,84,92,88,85,94,89,97,82,99,87
num counter = 0
num highest = 0
while counter < 12
if myScores[counter] > highest then
highest = myScores[counter]
endif
counter = counter + 1
endwhile
output highest
stop
Alani downloads a game called Kandy Krush from the app store. The app prompts her to enter her Social Security number (SSN) before playing. Alani asks her friend for advice. Which advice should her friend give
Answers
Answer:
"The game shouldn't need your SSN to be playable; don't enter it."
Explanation:
The game shouldn't need your SSN to be playable; don't enter it."
What is SSN?A numerical identification code known as a Social Security number (SSN) is given to residents and citizens of the United States in order to track income and calculate benefits.
As a component of The New Deal, the SSN was established in 1936 to offer benefits for retirement and disability. The SSN was first created to track earnings and offer benefits. Today, it is also utilized for other things including tracking credit reports and identifying people for tax purposes.
In the US, people are required to provide their SSN in order to open bank accounts, apply for government benefits, get credit, make large purchases, and more.
Therefore, The game shouldn't need your SSN to be playable; don't enter it."
To learn more about SSN, refer to the link:
https://brainly.com/question/2040269?
#SPJ5
mini practical tasks students can preform in a digital classroom?
Answers
Answer:
virtual scavenger hunt
Explanation:
if you do zoom you could a a scavenger hunt
during each round the teacher will announce a item you must search for around your house
as soon as the teacher says the item you have to turn your camera. and search the first person to come back turn Thier camera on and show the item wins 5-10 points
it keeps going untill someone ends up with 70-100 points and then they win! hope this helps
Write pseudocode for a new implementation o BFS that uses an adiacencv matrix instead of an aclacency nst.Find the time complexity of this new version and compare it to the version seen in class. Under what circumstances are they equally efficient?
Answers
Pseudocode for the new implementation of BFS using an adjacency matrix:
```
BFS(adjacency_matrix, start_node):
Create a queue and enqueue the start_node
Create a visited array and mark the start_node as visited
While the queue is not empty:
Dequeue a node from the queue
Process the node
For each adjacent node in the adjacency matrix:
If the adjacent node is not visited:
Mark the adjacent node as visited
Enqueue the adjacent node
```
The time complexity of this new version of BFS using an adjacency matrix is O(V^2), where V is the number of vertices. This is because we need to iterate over each element in the adjacency matrix to check the connections between nodes. In the worst case, we may need to visit every entry in the matrix, resulting in a quadratic time complexity.
In comparison, the version of BFS seen in class using an adjacency list has a time complexity of O(V + E), where V is the number of vertices and E is the number of edges. This version is more efficient because it only visits the nodes and edges that are present in the graph, rather than iterating over all possible connections as in the adjacency matrix implementation.
The two versions are equally efficient when the graph is dense and the number of edges approaches the maximum possible value of V^2. In this scenario, the time complexity of both implementations becomes similar, as the number of iterations required in the adjacency matrix version is comparable to the number of edges in the adjacency list version. However, in most practical cases, where the graph is sparse (fewer edges compared to the total possible connections), the adjacency list version is more efficient.
For more such answers on Pseudocode
https://brainly.com/question/24953880
#SPJ8
The security administrator for Corp.com. You are explaining to your CIO the value of credentialed scanning over non-credentialed scanning. In credentialed scanning, policy compliance plugins give you which advantage?
Answers
In credentialed scanning, policy compliance plugins give you an advantage known as option C: Customized auditing.
What does auditing serve to accomplish?The goal of an audit is to determine if the financial report's information, taken as a whole, accurately depicts the organization's financial situation as of a particular date. For instance, is the balance sheet accurately recording the organization's assets and liabilities?
Therefore since the goal of such a tailored audit, aside from cost and time savings, so, it is to present an objective overall picture of your supplier's organization in all pertinent disciplines, allowing you to better target risk areas and allocate control resources where they are most needed.
Learn more about Customized auditing from
https://brainly.com/question/7890421
#SPJ1
See full question below
The security administrator for Corp.com. You are explaining to your CIO the value of credentialed scanning over non-credentialed scanning. In credentialed scanning, policy compliance plugins give you which advantage?
More accurate results
Safer scanning
Customized auditing
Active scanning
79.1% complete question an attacker used an exploit to steal information from a mobile device, which allowed the attacker to circumvent the authentication process. which of the following attacks was used to exploit the mobile device?
Answers
The attack used could be a variety of attacks, such as a phishing attack, or an exploit that takes advantage of a vulnerability in the mobile device's operating system in authentication process.
What is authentication process?Authentication is the process of verifying the identity of a user or device. It is used to ensure that the person or device attempting to access a system is legitimate. Authentication is typically done through a username and password combination, but can also include biometric data such as fingerprints, retinal scans, or facial recognition. Authentication can also be done through two-factor authentication, which adds an additional layer of security by requiring a second form of identity verification such as a security code sent via text message. Authentication is essential for protecting sensitive data and maintaining system security.
To learn more about authentication process
https://brainly.com/question/13615355
#SPJ4
Make sure your animal_list.py program prints the following things, in this order:
The list of animals 1.0
The number of animals in the list 1.0
The number of dogs in the list 1.0
The list reversed 1.0
The list sorted alphabetically 1.0
The list of animals with “bear” added to the end 1.0
The list of animals with “lion” added at the beginning 1.0
The list of animals after “elephant” is removed 1.0
The bear being removed, and the list of animals with "bear" removed 1.0
The lion being removed, and the list of animals with "lion" removed
Need the code promise brainliest plus 100 points
Answers
Answer:#Animal List animals = ["monkey","dog","cat","elephant","armadillo"]print("These are the animals in the:\n",animals)print("The number of animals in the list:\n", len(animals))print("The number of dogs in the list:\n",animals.count("dog"))animals.reverse()print("The list reversed:\n",animals)animals.sort()print("Here's the list sorted alphabetically:\n",animals)animals.append("bear")print("The new list of animals:\n",animals)
Explanation:
Given two regular expressions r1 and r2, construct a decision procedure to determine whether the language of r1 is contained in the language r2; that is, the language of r1 is a subset of the language of r2.
Answers
Answer:
Test if L(M1-2) is empty.
Construct FA M2-1 from M1 and M2 which recognizes the language L(>M2) - L(>M1).
COMMENT: note we use the algorithm that is instrumental in proving that regular languages are closed with respect to the set difference operator.
Test if L(M2-1) is empty.
Answer yes if and only if both answers were yes.
Explanation:
An algorithm must be guaranteed to halt after a finite number of steps.
Each step of the algorithm must be well specified (deterministic rather than non-deterministic).
Three basic problems:
Given an FA M and an input x, does M accept x?
Is x in L(M)
Given an FA M, is there a string that it accepts?
Is L(M) the empty set?
Given an FA M, is L(M) finite?
Algorithm for determining if M accepts x.
Simply execute M on x.
Output yes if we end up at an accepting state.
This algorithm clearly halts after a finite number of steps, and it is well specified.
This algorithm is also clearly correct.
Testing if L(M) is empty.
Incorrect "Algorithm"
Simulate M on all strings x.
Output yes if and only if all strings are rejected.
The "algorithm" is well specified, and it is also clearly correct.
However, this is not an algorithm because there are an infinite number of strings to simulate M on, and thus it is not guaranteed to halt in a finite amount of time.
COMMENT: Note we use the algorithm for the first problem as a subroutine; you must think in this fashion to solve the problems we will ask.
Correct Algorithm
Simulate M on all strings of length between 0 and n-1 where M has n states.
Output no if and only if all strings are rejected.
Otherwise output yes.
This algorithm clearly halts after a finite number of steps, and it is well specified.
The correctness of the algorithm follows from the fact that if M accepts any strings, it must accept one of length at most n-1.
Suppose this is not true; that is, L(M) is not empty but the shortest string accepted by M has a length of at least n.
Let x be the shortest string accepted by M where |x| > n-1.
Using the Pumping Lemma, we know that there must be a "loop" in x which can be pumped 0 times to create a shorter string in L.
This is a contradiction and the result follows.
COMMENT: There are more efficient algorithms, but we won't get into that.
Testing if L(M) is finite
Incorrect "Algorithm"
Simulate M on all strings x.
Output yes if and only if there are a finite number of yes answers.
This "algorithm" is well specified and correct.
However, this is not an algorithm because there are an infinite number of strings to simulate M on, and thus it is not guaranteed to halt in a finite amount of time.
COMMENT: Note we again use the algorithm for the first problem as a subroutine.
Correct Algorithm
Simulate M on all strings of length between n and 2n-1 where M has n states.
Output yes if and only if no string is accepted.
Otherwise output no.
This algorithm clearly halts after a finite number of steps, and it is well specified.
The correctness of the algorithm follows from the fact that if M accepts an infinite number of strings, it must accept one of length between n and 2n-1.
This builds on the idea that if M accepts an infinite number of strings, there must be a "loop" that can be pumped.
This loop must have length at most n.
When we pump it 0 times, we have a string of length less than n.
When we pump it once, we increase the length of the string by at most n so we cannot exceed 2n-1. The problem is we might not exceed n-1 yet.
The key is we can keep pumping it and at some point, its length must exceed n-1, and in the step it does, it cannot jump past 2n-1 since the size of the loop is at most n.
This proof is not totally correct, but it captures the key idea.
COMMENT: There again are more efficient algorithms, but we won't get into that.
Other problems we can solve using these basic algorithms (and other algorithms we've seen earlier this chapter) as subroutines.
COMMENT: many of these algorithms depend on your understanding of basic set operations such as set complement, set difference, set union, etc.
Given a regular expression r, is Lr finite?
Convert r to an equivalent FA M.
COMMENT: note we use the two algorithms for converting a regular expression to an NFA and then an NFA to an FA.
Test if L(M) is finite.
Output the answer to the above test.
Given two FAs M1 and M2, is L(M1) = L(M2)?
Construct FA M1-2 from M1 and M2 which recognizes the language L(>M1) - L(>M2).
COMMENT: note we use the algorithm that is instrumental in proving that regular languages are closed with respect to the set difference operator.
Test if L(M1-2) is empty.
Construct FA M2-1 from M1 and M2 which recognizes the language L(>M2) - L(>M1).
COMMENT: note we use the algorithm that is instrumental in proving that regular languages are closed with respect to the set difference operator.
Test if L(M2-1) is empty.
Answer yes if and only if both answers were yes.