_____ is the process of bypassing the built-in limitations and protections of a mobile device. Group of answer choices D. Slicing B. Twisting C. Jailbreaking A. Cracking
Answers
Answer:
C
Explanation:
Jailbreaking is the process of bypassing the built-in limitations and protections of a mobile device
Related Questions
Internal combustion engines use hot expanding gasses to produce the engine's power. Technician A says that some engines use spark to ignite the gasses. Technician B says some engines use compression to ignite the gasses. Who is correct?
Answers
Answer:
Explanation:
Both are right.
Engines are divided into:
1) Internal combustion engines
2) Diesels
Jennifer turns on her laptop and hears a series of beeps. What do they probably indicate?.
Answers
Answer:
Hey, it's probably a bad Ram or a CPU/GPU problem.
In an interview, you were asked to explain the steps involved in a successful authentication by a radius server. How should you answer?.
Answers
Between a Network Access Server that wants to authenticate its links and a shared Authentication Server, RADIUS is a protocol for transferring authentication, authorization, and configuration information. Remote Authentication Dial In User Service is what RADIUS stands for. You can centralize user authentication and accounting with a Remote Authentication Dial-In User Service (RADIUS) server, a particular kind of server.
What is Server Authentication?
When a person or another server needs to prove their identity to an application, an authentication server is used to check their credentials.
The act of identifying a person or machine to confirm that they are who they claim to be is known as authentication.
To confirm this, an application or device could request a variety of IDs. Every identifier often belongs to one of these three groups:
a thing you are aware of Typically, it's a username and password or PIN. It is the most typical type of identification.Something you have – This includes tangible items you own, such a phone, key, etc.a quality you possess In this category, verification is done using biometric tools like fingerprint or retinal scans.The RADIUS server obtains the user credentials from the message and searches for a match in a user database if the Access-Request message employs a permitted authentication technique.
The RADIUS server can access the user database to obtain further information about the user if the user name and password match an entry in the database.
Additionally, it checks to determine if the configuration of the system contains an access policy or a profile that fits all the data it has about the user. The server replies if such a policy is present.
Learn more about Remote Authentication Dial In User Service click here:
https://brainly.com/question/15397099
#SPJ4
Which rule should be on the top line when creating conditional formatting?
the most important rule that marks it as lowest precedence
the most important rule that marks it as highest precedence
O the least important rule that marks it as highest precedence
the least important rule that marks it'as lowest precedence
Answers
Answer:
B
Explanation:
Final answer
Answer:
B) the most important rule that marks it as highest precedence
Explanation:
"Should be on the top line because it is the most important." -Edge narrator
Who can use empathetic listening?
counselors
psychiatrists
anyone
teachers
College Readiness
Answers
Using 20 sentences, as a student, why is it important to identify risk and hazard inside kitchen and home and business properties?
Answers
Answer:
The answer is below
Explanation:
Hazard is something or condition that can cause injury to individuals. If properties are not managed appropriately, the hazard can be inevitable. Every hazard comes with its own risk. And Risk of hazard is the degree to which hazard can affect individuals when exposed to hazards.
Identifying hazards in the surrounding are essential. Also, identifying the risk associated with hazards can't be overemphasized. Hence, the need to identifying both the hazards and the risks associated with it.
There are various reasons it is important to identify risks and hazards inside kitchen and home and business properties. They include the following reasons:
1. It is important to identify hazards in the kitchen, home, and business properties because they may cause injury.
2. Identifying hazards will make us know how to eliminate the hazards
3. When we identify hazards we can easily prevent its future occurrence
4. Identifying hazards in the kitchen such as a bad electric cooker can prevent potential electrical shock
5. When a hazard such as leaking gas is identified, we prevent potential fire outbreak
6. Identifying hazard early is a preventive measure and it is cheaper.
7. Failure to identify hazards in business properties will lead to a great loss of profits.
8. To identify the risk of hazards is the best way to eliminate the hazards.
9. Identifying the risk of hazards can make us anticipate and quickly remove the hazards effectively.
10. It is cheaper to eliminate the risk of hazards when identified than performing repairs after hazards have caused damages.
11. Understanding and identifying the risk of hazard can help save lives, whether kitchen, home, or in business properties.
12. Identifying the risk of hazards, can lead us to have a solution in place against the hazard.
The first time you save a file, there is no difference between theBlank Space __________ and Save As commands.
Answers
The first time you save a file, there is no difference between the Blank Space save and save as commands.
Which command is used to save a file?The command that is used to save a file is known as Ctrl+S. If a user wants to Save a file, he/she needs to press Ctrl+S to save an existing workbook in its current location.
Apart from this, you need to use Save As to save your workbook for the first time, in a different location, or to create a copy of your workbook in the same or another location.
The difference between Save and Save As is that Save permits a user to update a previously saved file with new content, whereas Save As permits a user to save a new file or an existing file to a new location with the same or different name.
Therefore, the first time you save a file, there is no difference between the Blank Space save and save as commands.
To learn more about Save commands, refer to the link:
https://brainly.com/question/26484162
#SPJ1
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
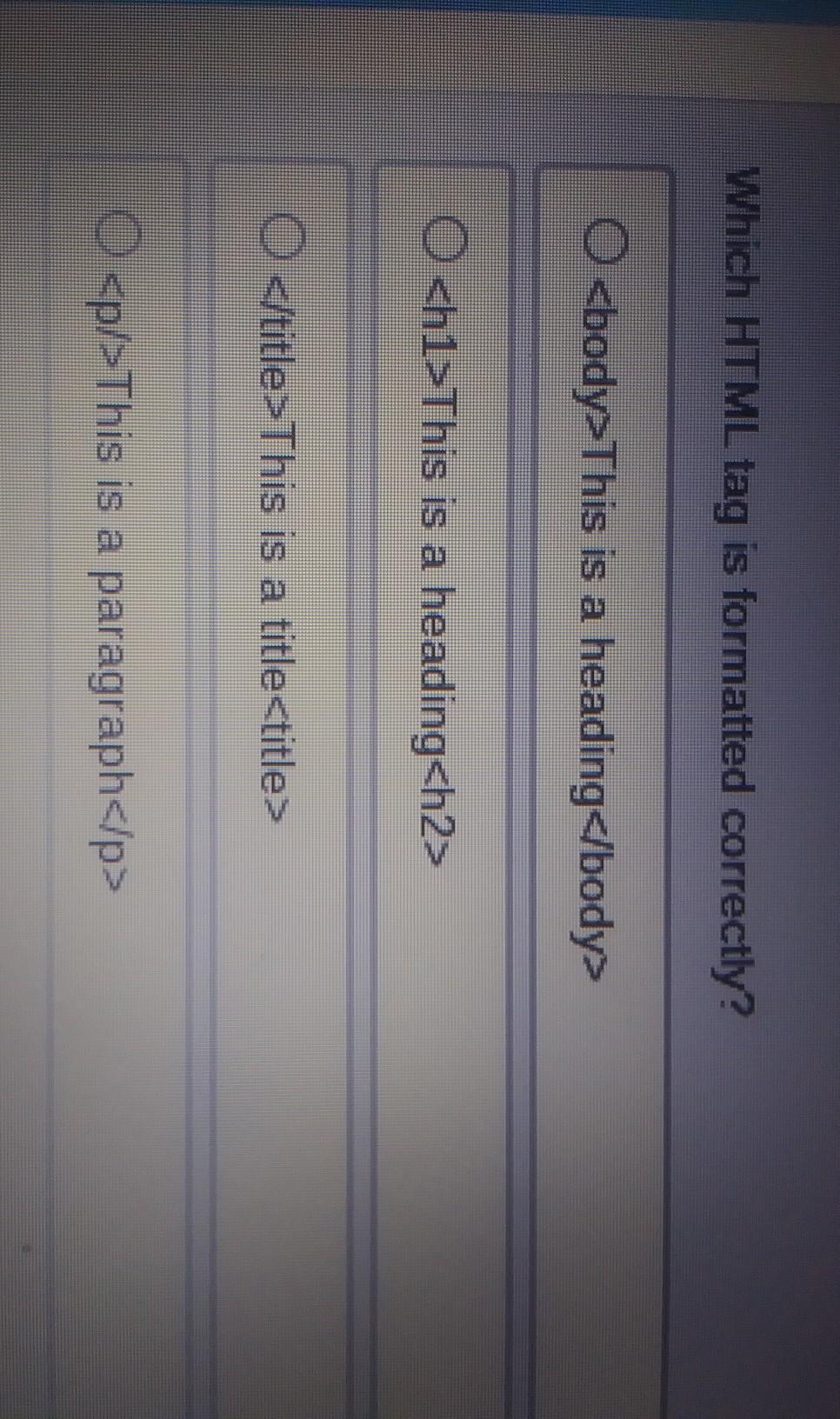
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
Explain all the steps of K means clustering algorithm with
Diagram and example.
Answers
The K-means clustering algorithm steps are :
Step 1: Choose the number of clusters (K).Step 2: Initialize cluster centroidsStep 3: Assign data points to clustersStep 4: Update cluster centroidsStep 5: Repeat steps 3 and 4 until convergence:Step 6: Output the clustersWhat is the clustering algorithm?K-means clustering is an unsupervised ML algorithm that partitions data into K clusters based on data point similarity.
In Steps: 1. Determine the requested number of clusters K that you be going to recognize in your dataset. This is a hyperparameter and needs expected predefined.
In Step 2, Randomly select K data points from the dataset as the primary cluster centroids. These centroids show the centers of the clusters.
Learn more about clustering algorithm from
https://brainly.com/question/29807099
#SPJ4
which type of valve is used to limit the flow of fluid in one direction only?
Answers
Another kind of flow-control valve is the check valve. A check valve's purpose is to restrict flow to one direction. The ability of flow check valve to regulate speed of air motors and cylinders is a relatively typical function.
What use does a check valve serve?Control valves are commonly employed in lines to prevent backflow. The flow can freely move one direction through a check valve, but if the flow changes, the piston will close to safeguard the pipes, other valves, pumps, etc.
Do we need a check valve?One of the most crucial parts of any pipeline system or fluid-moving application is the simple check valve. The delicate design conceals its serious intent.
To know more about check valve visit:
https://brainly.com/question/27876952
#SPJ4
As a pen test team member, you begin searching for IP ranges owned by the target organization and discover their network range. You also read job postings and news articles and visit the organization's website. Throughout the first week of the test, you also observe when employees come to and leave work, and you rummage through the trash outside the building for useful information. Which type of footprinting are you accomplishing
Answers
The activities described, including searching for IP ranges, reading job postings and news articles, visiting the organization's website, observing employee behavior, and rummaging through trash, are indicative of active footprinting. Active footprinting involves actively gathering information about a target organization through various methods, including direct interactions and observations.
The described activities align with the concept of active footprinting, which involves engaging in proactive efforts to gather information about a target organization. Here's an explanation of each activity and its relevance to active footprinting:
Searching for IP ranges owned by the target organization: This helps identify the network infrastructure and potential entry points for penetration testing.Reading job postings and news articles: Job postings can provide insights into the organization's technology stack, while news articles may reveal recent developments, partnerships, or vulnerabilities.Visiting the organization's website: Exploring the website helps gather information about the company's products, services, technologies used, and potentially hidden details such as employee names, email formats, or public-facing applications.Observing employee behavior: Monitoring when employees arrive and leave work can provide insights into their work patterns, potential access points, or times when the network may be less secure.Rummaging through trash outside the building: This unconventional method aims to find discarded documents or information that may be useful for understanding the organization's operations, infrastructure, or potential weak points.Overall, the combination of these activities indicates an active approach to footprinting, which involves actively seeking and gathering information about the target organization to assess its security posture and identify potential vulnerabilities that can be exploited during a penetration test.
Learn more about network here: https://brainly.com/question/30456221
#SPJ11
In the non-pipelined datapath, for an R-type instruction, all the needed values for control lines like ALUOp, ALUSrc, RegDst, and RegWrite, can be determined when the instruction appears from instruction memory.
True
False
Answers
True. The control lines for an R-type instruction in the non-pipelined datapath can be identified when the instruction arrives from instruction memory since all required values are taken directly from the instruction.
The exact register operands and the function code that designates the operation to be carried out by the ALU are not known until the instruction is in the register file, despite the fact that the opcode of the R-type instruction can be decoded to determine that it is an R-type instruction. As a result, in the non-pipelined datapath, it is not possible to establish the control lines for ALUOp, ALUSrc, RegDst, and RegWrite only from the instruction memory. The register operands and function code of the instruction, which are received from the register file, must be used to determine these values.
learn more about datapath here:
https://brainly.com/question/31359573
#SPJ11
my computer is acting weird, can you guys see what this picture is ?? should be Snoop

Answers
Answer:
yes it is snoop
Explanation:
great photo it is indeed snoop so you pc work
Answer:
yeah it comes out ok for me too, hope your computer isn't acting weird anymore for you.
Shruti has displayed the entire text of her document in uppercase. Name the property she must have used to
achieve the same.
Cyber tools
Answers
Can someone come and see if I have answered this question correctly? Please ...
if i have a mistake or somewhere i can go deeper can you correct me? Thank you

Answers
Answer:
presentation or visualization
Explain why Austin takes close-up pictures of whales and displays them in life-size? worth 50 points
Answers
The reason why Austin takes close - up pictures of and displays them in life - size is due to the fact that he wants to give viewers an indelible view or opinion of what a whale is.
It also to give whales a background to bring out unexplored thought and emotion in a lot of ways that has been yet to pursued .What are Whales?This is known to be Animals that are said to be mostly distributed and have a lot of group of aquatic placental marine mammals.
They are known to belong to an informal grouping as they belong to the order Cetartiodactyla.
Learn more about pictures from
https://brainly.com/question/25938417
Draw a flow chart that accepts mass and volume as input from the user. The flow chart should compute and display the density of the liquid.( Note: density = mass/volume ).
Answers
Answer:
See attachment for flowchart
Explanation:
The flowchart is represented by the following algorithm:
1. Start
2. Input Mass
3. Input Volume
4 Density = Mass/Volume
5. Print Density
6. Stop
The flowchart is explained by the algorithm above.
It starts by accepting input for Mass
Then it accepts input for Volume
Step 4 of the flowchart/algorithm calculated the Density using the following formula: Density = Mass/Volume
Step 5 prints the calculated Density
The flowchart stops execution afterwards
Note that the flowchart assumes that the user input is of number type (integer, float, double, etc.)

5. (5 points) Construct the truth table and determine whether the proposition is a tautology, contradie tion, or contingency PNP V-9)
Answers
The given statement is P ∨ ¬P. To evaluate whether the given statement is a tautology, contradiction or contingency, we construct a truth table. The truth table for the given statement is as follows: P¬PP ∨ ¬PTrue False False ∨ True True False True ∨ FalseTrue True False ∨ False False True .
The truth table above shows that the given statement P ∨ ¬P is a tautology. This means that the statement is true for all possible truth values of its propositional variables. Therefore, the statement is true regardless of the truth values of P and ¬P.Table for P ∨ ¬PP¬PP ∨ ¬PTrueFalseFalse ∨ True True True FalseTrue ∨ FalseTrueTrueFalse ∨ FalseFalseAs shown in the truth table, the given statement P ∨ ¬P is a tautology.
This implies that the statement is true for all possible truth values of its propositional variables. As a result, the statement is always true regardless of the truth values of P and ¬P.A tautology is a type of compound statement that is always true. It can be obtained by combining two or more simple statements using logical connectives. This means that the truth value of the tautology is always true irrespective of the truth values of the propositions it is composed of.
To know more about tautology visit :
https://brainly.com/question/29494426
#SPJ11
computer system allows three users to access the central computer simultaneously. Agents who attempt to use the system when it is full are denied access; no waiting is allowed. of 28 calls per hour. The service rate per line is 18 calls per hour. (a) What is the probability that 0,1,2, and 3 access lines will be in use? (Round your answers to four decimal places.) P(0)= P(1)= P(2)= P(3)= (b) What is the probability that an agent will be denied access to the system? (Round your answers to four decimal places.) p k
= (c) What is the average number of access lines in use? (Round your answers to two decimal places.) system have?
Answers
In the given computer system scenario, there are three access lines available for users to access the central computer simultaneously. The arrival rate of calls is 28 per hour, and the service rate per line is 18 calls per hour.
We are required to calculate the probabilities of different numbers of access lines being in use, the probability of an agent being denied access, and the average number of access lines in use.
(a) To calculate the probabilities of different numbers of access lines being in use, we can use the formula for the probability of having k lines in use in a system with three lines, given by P(k) = (1 - p) * p^(k-1), where p is the utilization factor. The utilization factor can be calculated as p = λ / μ, where λ is the arrival rate and μ is the service rate per line.
Using the given values, we can calculate the probabilities as follows:
P(0) = (1 - p) * p^2
P(1) = (1 - p) * p^0
P(2) = (1 - p) * p^1
P(3) = p^3
(b) The probability of an agent being denied access is equal to the probability of all three access lines being in use, which is P(3) = p^3.
(c) The average number of access lines in use can be calculated using the formula for the average number of customers in a system, given by L = λ / (μ - λ). In this case, since there are three lines available, the average number of access lines in use would be L / 3.
By plugging in the values and calculating the probabilities and average number of access lines, we can obtain specific numerical answers.
Learn more about arrival rate here :
https://brainly.com/question/29099684
#SPJ11
Which of the following functions can produce different results, depending on the value of a specified column?
a. NVL
b. DECODE
c. UPPER
d. SUBSTR
Answers
The function among the following functions which can produce different results, depending on the value of a specified column is DECODE.
The DECODE function is a powerful function for controlling output from a query. It operates like an IF-THEN-ELSE statement. The following are some of the capabilities of the DECODE function:DECODE can be used to add columns or expressions togetherDECODE can be used to substitute one value for anotherDECODE can be used to provide a default valueDECODE can be used to convert one value into anotherDECODE can be used to return a null valueThe DECODE function will work with any data type that can be compared. Numeric data types are returned as NUMBER data. Character data types are returned as VARCHAR2 data. If the values in the DECODE statement are all numeric, Oracle will compare the first value to the second value. If the values are character data, Oracle will compare the first value to the second value using an exact match.
Know more about DECODE here:
https://brainly.com/question/32231599
#SPJ11
The registers are the communication channels inside the computer.( true or false)
Answers
Registers are storage, not channels
suppose that you are going to connect the computers in your house or apartment. what media would you use? why? would this change if you were building a new house
Answers
To connect computers in your house or apartment, you can use two primary media options: wired (Ethernet) and wireless (Wi-Fi). The choice depends on your specific needs and requirements.
Ethernet involves using physical cables, such as Cat5e, Cat6, or Cat7, to connect devices directly to a router or a network switch. This method is reliable and provides faster, more stable connections. Ethernet is ideal for high-bandwidth activities, such as online gaming or media streaming, where latency and connection stability are crucial.
Wi-Fi, on the other hand, enables wireless connections between devices and the router. This method is more convenient and flexible, as it allows users to move freely within the Wi-Fi range without being tethered to a cable. However, Wi-Fi connections can be less stable and slower than Ethernet, as they are more susceptible to interference and congestion.
If you were building a new house, your choice might change depending on your needs and the design of the house. It would be a good idea to install Ethernet cables during the construction process, as this would allow for a future-proof and high-performance network. However, you may still want to include Wi-Fi capabilities for the convenience and flexibility it offers, particularly for mobile devices like smartphones and tablets.
In summary, the choice of media to connect computers in your house or apartment depends on factors like performance, convenience, and flexibility. Ethernet provides a reliable, fast connection, while Wi-Fi offers mobility and ease of use. When building a new house, consider incorporating both options to create a versatile and future-proof home network.
for such more question on flexibility
https://brainly.com/question/3829844
#SPJ11
The process by which information is encoded by its meaning is calledA) long-term potentiation.B) automatic processing.C) rehearsal.D) semantic encoding
Answers
Semantic encoding is the process of encoding information based on its meaning.
What does long-term memory encoding involve?Simply said, encoding is the act of transferring data from our working memory, or short-term memory, to our long-term memory. There are important techniques we can use to transfer information from our long-term memory back into working memory once it has been appropriately recorded.
What does information encoding entail?Encoding, storage, and retrieval are the three basic processes involved in memory. The process of committing information to memory is called encoding (the process by which information is recovered from memory).Visual, auditory, or semantic coding are all possible.
To know more about information visit:-
https://brainly.com/question/14879566
#SPJ4
The table button is present in the ……… tab.
Answers
Answer:
Insert
Explanation:
The table button is present in the Insert tab.
Refer to screenshot (MS Word)
Insert → Table → Insert Table or Draw Table

33. a client wants to send federal documents to another agency. what would be the best way to send a secure message with information? a. email b. usb c. sftp d. ftp
Answers
A client wants to send federal documents to another agency. The best way to send a secure message with information is SFTP (Option C)
What is SFTP?A secure file transmission protocol is SFTP (SSH File Transfer Protocol). It employs the SSH protocol. It supports all of SSH's security and authentication features.
As a file transfer protocol, SFTP has mostly superseded classic FTP, and it is rapidly overtaking FTP/S. It offers all of the capabilities of existing protocols, but more securely and reliably, and with a simpler configuration. There is no reason to utilize old protocols any longer.
Password eavesdropping and man-in-the-middle attacks are also prevented by SFTP. It secures the data's integrity through encryption and cryptographic hash algorithms, and it authenticates both the host and the user.
Learn more about SFTP:
https://brainly.com/question/28086395
#SPJ1
when you have constraints in place on columns, an error is returned if you try to violate the constraint rule
Answers
When constraints are set on columns in a database, an error will be returned if you try to violate the constraint rule. Constraints are used to enforce rules and maintain data integrity in a database.
These rules can include conditions such as unique values, not null values, and referential integrity. If a constraint is violated, such as trying to insert a duplicate value into a unique column or inserting a null value into a not null column, an error will be thrown by the database system.
The error message will provide information about the specific constraint that was violated and can help in identifying and resolving the issue. So, to summarize in a long answer, constraints on columns in a database prevent violations of the defined rules, and attempting to violate a constraint will result in an error being returned.
To know more about constraint rule visit :-
https://brainly.com/question/30547079
#SPJ11
Which of the following are causes of a run-time error. Choose all that apply.
A user enters a numeric value when a text value was expected.
A user enters text and numeric values.
A user enters a text value when a numeric value was expected.
A user enters a negative number when a positive number was expected.
Answers
Answer:
A C D
Explanation:
just did it
Answer:
A. A user enters a numeric value when a text value was expected.
C. A user enters a text value when a numeric value was expected.
D. A user enters a negative number when a positive number was expected.
Explanation:
Discuss the evolution of file system data processing and how it is helpful to understanding of the data access limitations that databases attempt to over come
Answers
Answer:
in times before the use of computers, technologist invented computers to function on disk operating systems, each computer was built to run a single, proprietary application, which had complete and exclusive control of the entire machine. the introduction and use of computer systems that can simply run more than one application required a mechanism to ensure that applications did not write over each other's data. developers of Application addressed this problem by adopting a single standard for distinguishing disk sectors in use from those that were free by marking them accordingly.With the introduction of a file system, applications do not have any business with the physical storage medium
The evolution of the file system gave a single level of indirection between applications and the disk the file systems originated out of the need for multiple applications to share the same storage medium. the evolution has lead to the ckean removal of data redundancy, Ease of maintenance of database,Reduced storage costs,increase in Data integrity and privacy.
Explanation:
You may need to use the appropriate appendix table or technology to answer this question.
Advertisers contract with internet service providers and search engines to place ads on websites. They pay a fee based on the number of potential customers who click on their ad. Unfortunately, click fraud—the practice of someone clicking on an ad solely for the purpose of driving up advertising revenue—has become a problem. Businessweek reports that 40 percent of advertisers claim they have been a victim of click fraud. Suppose a simple random sample of 360 advertisers will be taken to learn more about how they are affected by this practice. (Round your answers to four decimal places.)
(a)What is the probability that the sample proportion will be within ±0.04 of the population proportion experiencing click fraud?
(b)What is the probability that the sample proportion will be greater than 0.45?
Answers
To find the probability that the sample proportion will be within ±0.04 of the population proportion experiencing click fraud, we need to calculate the margin of error.
The margin of error is given by the formula:
Margin of Error = z * sqrt((p * (1-p)) / n)
Where:
- z is the z-score corresponding to the desired level of confidence (typically 1.96 for a 95% confidence level)
- p is the estimated population proportion experiencing click fraud (0.40 in this case)
- n is the sample size (360 in this case)
Calculating the margin of error:
Margin of Error = 1.96 * sqrt((0.40 * (1-0.40)) / 360)
Margin of Error ≈ 0.0359
The probability that the sample proportion will be within ±0.04 of the population proportion experiencing click fraud can be calculated as the sum of the probabilities within the range p ± margin of error.
P(p - 0.04 ≤ sample proportion ≤ p + 0.04) = P(p - 0.04 ≤ sample proportion) - P(p + 0.04 < sample proportion)
Using the standard normal distribution, we can calculate these probabilities.
P(p - 0.04 ≤ sample proportion) = P(z ≤ (sample proportion - p) / sqrt((p * (1-p)) / n))
P(p + 0.04 < sample proportion) = P(z ≤ (sample proportion - p) / sqrt((p * (1-p)) / n))
We use the z-score formula to convert the sample proportion into a standard normal distribution.
To know more about sample proportion visit :-
https://brainly.com/question/11461187
#SPJ11
A _________________ can also contain a single character or be entirely empty.
Answers
In Computer programming, a string can either contain a single character or be entirely empty.
The kinds of data type.In Computer programming, there are five (5) main recognized data types and these include the following:
Integer type (int).Character type (char).Floating point type (float).Boolean (bool)String (str)What is a string?A string is a data type which is typically used for data values that comprises ordered sequences of characters. Also, a string can either contain a single character or be entirely empty.
An example of a string in computer programming is "Hello world"
Read more on a string here: https://brainly.com/question/25619349