Look both _____before you cross a street and i want to see how much of yall know it
Answers
Answer:
Ways
Explanation:
Look both ways
Related Questions
PLS HELP I HAVE 1 MINUTE LEFT!!! 50 POINTS Which statements are accurate? Select three options.
The more switches you have, the more 1s and Os you get.
The more switches you have, the smaller the bits can be.
The more switches you have, the more complex the data can be.
The more switches you have, the more bits you can have.
The more switches you have, the fewer bits you can have.
Answers
Answer:
MORE BITS
Explanation:
Think about a career you would like to have 10 years from now.
What role does technology play into this career?
Why is technology beneficial?
Will mark brainliest
Answers
Answer: Scientist
Explanation: Scientists use technology to record data, as well as using technology to study different things, for example scientists use computers to track DNA.
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
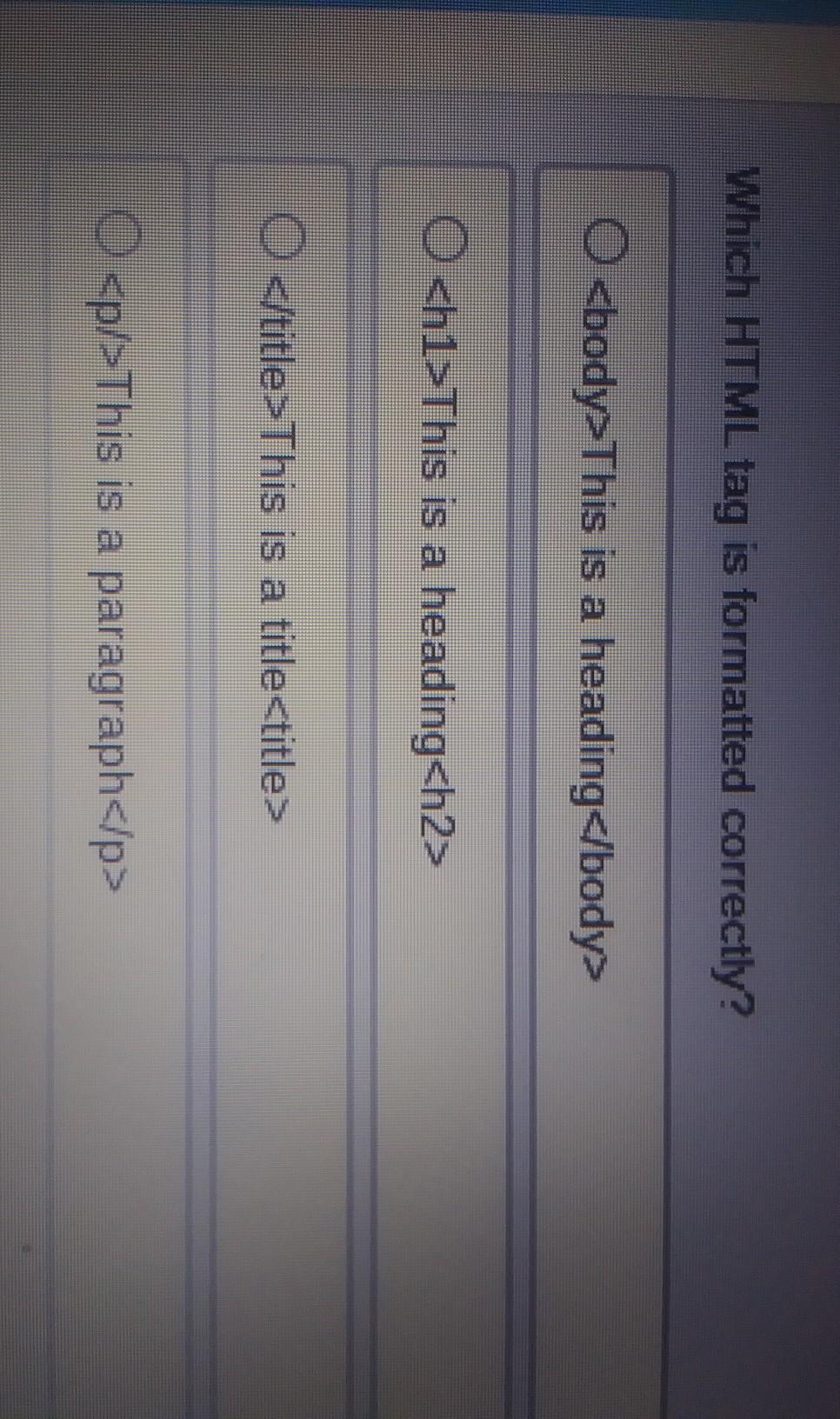
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
public class TurtleTest {
public static void main(String[] args) {
int distance; // line 1
World window; // 2
Turtle turtle1; // 3
window = new World(); // 4
turtle1 = new Turtle(window); // 5
turtle1.forward(100); // 6
turtle1.turnLeft(); // line 7
}
}
ANSWER THESE QUESTIONS HERE:
Examine line 1’s variable declaration.
What is the name of the variable being declared in line 1?
What is the data type of the variable being declared?
Is it a primitive data type or a class data type?
Examine line 2’s variable declaration.
What is the name of the variable being declared in line 2?
What is the data type of the variable being declared?
Is it a primitive data type or a class data type?
There are three variable declarations in the above code segment. What is the data type of the third variable?
In lines 4 and 5, a new object was assigned to a reference variable.
What type of object was created by the fourth line of code?
What type of object was created by the fifth line of code?
What keyword was used in lines 4 and 5 to create the new objects?
What is the argument on line 5?
Consider lines 6 and 7.
Based on the context, what do you think lines 6 and 7 will cause to happen?
Which words caused these actions to happen?
How would you categorize these words in terms of Java / programming?
Answers
Line 1’s variable declaration The name of the variable being declared in line 1 is "distance".The data type of the variable being declared is "int".It is a primitive data type.
Line 2’s variable declaration The name of the variable being declared in line 2 is "window".The data type of the variable being declared is "World".It is a class data type.The data type of the third variable is "Turtle".Type of object createdThe fourth line of code creates a "World" object.
The fifth line of code creates a "Turtle" object. The "new" keyword was used in lines 4 and 5 to create the new objects. The argument on line 5 is "window". Based on the context, lines 6 and 7 will cause the turtle to move forward by 100 units and then turn left by 90 degrees. The words "forward" and "turnLeft" caused these actions to happen. These words can be categorized as Java method calls or function calls.
To know more about variable visit:
https://brainly.com/question/15078630
#SPJ11
When do you not have to cite information you put on your website?
Answers
Answer:
You do not have to cite information you put on your website if the information is considered to be common knowledge. Common knowledge is information that is widely known and accepted by the general public, and does not require a citation because it is not original to the person presenting it.
Examples of common knowledge include well-known facts, such as the date of the Declaration of Independence, the capital of the United States, and the laws of physics. These facts are widely known and accepted, and do not require a citation because they are not original to the person presenting them.
However, if you use information on your website that is not considered to be common knowledge, you must provide a citation. This includes original research, ideas, data, or other information that is not widely known or accepted. By providing a citation, you are giving credit to the original source of the information and allowing others to verify the accuracy of the information.
Overall, you do not have to cite information you put on your website if the information is considered to be common knowledge, but you must provide a citation for any information that is not widely known or accepted.
What tag would you enter to link the text “White House" to the URL
http://www.whitehouse.gov?*
Answers
Answer:
3.<a href="http://www.whitehouse.gov" target="_blank">White House</a>
Explanation:
The exact question is as follows :
To find - What tag would you enter to link the text “White House" to the URL
http://www.whitehouse.gov with the destination document displayed in a new unnamed browser window?
1.<a ="http://www.whitehouse.gov" target="_blank">White House</a link>
2.<a href="ftp://www.whitehouse.gov" target="_blank">White House</a>
3.<a href="http://www.whitehouse.gov" target="_blank">White House</a>
4.<link="http://www.whitehouse.gov" target="_blank">White House</link>
The correct option is - 3.<a href="http://www.whitehouse.gov" target="_blank">White House</a>

Where is a Pivot Table inserted?
a. Next to the last column of data in your worksheet
b. Below the last row of data in your worksheet
c. It depends on whether you select to insert the Pivot Table in the current worksheet or a new worksheet
d. Above the first row of data in your worksheet
Answers
The Create PivotTable dialog box will prompt you to create a Pivot Table on an Existing Worksheet if you insert one on a data-filled worksheet. One of the options in the Create PivotTable dialog box is this one.
Utilized in spreadsheet applications like Excel, OpenOffice.org Calc, and Ggle Sheets is a data summarization tool called a pivot table. Sorting, counting, and totaling data in a table are its primary uses. In order to create a report, you can summarize the data in a variety of ways using a pivot table.
The dialog box for "Create PivotTable":
In Excel, a new pivot table can be created using the dialog box labeled "Create PivotTable."
Learn more about PivotTable at
brainly.com/question/18410166
#SPJ4
upon intercepting the assigned radial, the controller advises you that you are on the airway and to 'resume own navigation.' this phrase means that
Answers
This phrase means that you are to assume responsibility for your own navigation.
The correct option is B.
What are fundamental navigational skills?Always position the map so that it is towards the ground. Before you really need to use the compass, practise using it. While out on the stroll, keep the map and compass nearby. Regularly check your location to be aware of where you are.
The navigation system contains what?An apparatus that ascertains a vehicle's location and the path to a specific location is a navigation system. The navigation system in the automobile directs the driver to make a left or right turn at a specific intersection. To identify the present location and direction of the car, the navigation system makes use of GPS signals.
To know more about navigation system visit:
https://brainly.com/question/13894678
#SPJ4
I understand that the question you are looking for is:
Upon intercepting the assigned radial, the controller advises you that you are on the airway and to "RESUME OWN NAVIGATION.'' This phrase means that.
A) you are still in radar contact, but must make position reports.
B) you are to assume responsibility for your own navigation.
C) radar services are terminated and you will be responsible for position reports.
consider a hash table with open addressing that evaluates the load factor before adding a new element. if the load factor is larger than 50%, the table is resized by doubling the table capacity (the number of possible elements). then the existing elements are rehashed and inserted into the new table, followed by the new element. assuming an initial hash table capacity of 2 with 0 elements, what is the table capacity after adding 11 elements? group of answer choices 16 32 11 22
Answers
After adding 11 elements, the Hash tables capacity is 32.
Hash tables are used to store elements in an efficient and structured manner. They work by providing a hash value for each key inserted, which is then used to locate the corresponding element's position. Consider a hash table with open addressing that evaluates the load factor before adding a new element. If the load factor is larger than 50%, the table is resized by doubling the table capacity (the number of possible elements). Then the existing elements are rehashed and inserted into the new table, followed by the new element.The hash table capacity is first initialized to 2 with 0 elements, which means the current load factor is 0. Suppose the hash function is h(x) = x mod 2, which will be used to locate the position for the element 'x' in the hash table. Now let's add 11 elements to this hash table. They are:0, 1, 2, 3, 4, 5, 6, 7, 8, 9, and 10. To determine the table capacity after adding these elements, we need to calculate the load factor after each element is added. The load factor is calculated as follows:load factor = number of elements / table capacityInitially, the load factor is zero because the table is empty. After the first element (0) is added, the load factor is 1/2 = 0.5. Since this is equal to the maximum load factor (50%), the table capacity is doubled to 4 (i.e., 2 x 2), and the existing element (0) is rehashed and inserted into the new table. After adding the first element (0), the hash table now looks like this:Hash table with 1 elementThe second element (1) is then added to the hash table, and the load factor becomes 2/4 = 0.5. This is again equal to the maximum load factor, so the table capacity is doubled to 8 (i.e., 2 x 4), and the existing elements (0 and 1) are rehashed and inserted into the new table, followed by the new element (1). After adding the second element (1), the hash table now looks like this:Hash table with 2 elementsSimilarly, after adding the third element (2), the load factor becomes 3/8 = 0.375, which is less than the maximum load factor. Hence, the table remains unchanged. The hash table now looks like this:Hash table with 3 elementsAfter adding the fourth element (3), the load factor becomes 4/8 = 0.5, which is equal to the maximum load factor. Therefore, the table capacity is doubled to 16 (i.e., 2 x 8), and the existing elements (0, 1, 2, and 3) are rehashed and inserted into the new table, followed by the new element (3). The hash table now looks like this:Hash table with 4 elementsAfter adding the fifth element (4), the load factor becomes 5/16 = 0.3125, which is less than the maximum load factor. Hence, the table remains unchanged. The hash table now looks like this:Hash table with 5 elementsAfter adding the sixth element (5), the load factor becomes 6/16 = 0.375, which is less than the maximum load factor. Hence, the table remains unchanged. The hash table now looks like this:Hash table with 6 elementsAfter adding the seventh element (6), the load factor becomes 7/16 = 0.4375, which is less than the maximum load factor. Hence, the table remains unchanged. The hash table now looks like this:Hash table with 7 elementsAfter adding the eighth element (7), the load factor becomes 8/16 = 0.5, which is equal to the maximum load factor. Therefore, the table capacity is doubled to 32 (i.e., 2 x 16), and the existing elements (0, 1, 2, 3, 4, 5, 6, and 7) are rehashed and inserted into the new table, followed by the new element (7). The hash table now looks like this:Hash table with 8 elementsAfter adding the ninth element (8), the load factor becomes 9/32 = 0.28125, which is less than the maximum load factor. Hence, the table remains unchanged. The hash table now looks like this:Hash table with 9 elementsAfter adding the tenth element (9), the load factor becomes 10/32 = 0.3125, which is less than the maximum load factor. Hence, the table remains unchanged. The hash table now looks like this:Hash table with 10 elementsFinally, after adding the eleventh element (10), the load factor becomes 11/32 = 0.34375, which is less than the maximum load factor. Hence, the table remains unchanged. The hash table now looks like this:Hash table with 11 elementsTherefore, the table capacity after adding 11 elements is 32.
learn more about Hash tables here:
https://brainly.com/question/29970427
#SPJ4
____ is a practice used to illegally obtain sensitive information such as credit card numbers, account numbers, and passwords. group of answer choices
Answers
The practice you are referring to is called "phishing." Phishing is a method used by cybercriminals to illegally obtain sensitive information such as credit card numbers, account numbers, and passwords.
These criminals often disguise themselves as trustworthy entities, such as banks or online retailers, in order to trick individuals into revealing their personal information.
Here's how phishing typically works:
1. The attacker sends an email or message that appears to be from a legitimate source, such as a bank or social media platform.
2. The email or message usually includes a link to a fake website that closely resembles the legitimate website.
3. When the user clicks on the link and enters their personal information (such as login credentials or credit card details) on the fake website, the attacker captures this information.
4. The attacker can then use this stolen information for various illegal purposes, such as identity theft or financial fraud.
It's important to be cautious and vigilant when interacting online to protect yourself from phishing attempts. Always double-check the sender's email address or message, as well as the website's URL, to ensure their authenticity. Additionally, be wary of any requests for personal information or urgent actions that seem suspicious or out of the ordinary.
To know more about Phishing, visit:
https://brainly.com/question/32858536
#SPJ11
which of the following attack is also known as dns spoofing? domain hijacking dns poisoning dns hijacking universal resource locator (url) redirection
Answers
The attack that is also known as DNS spoofing is DNS poisoning.
DNS spoofing is the practice of tampering with the domain name system (DNS) server's domain name-to-IP address mapping or domain name-to-service mapping in an unauthorized manner, thereby diverting Internet traffic away from its intended destination or terminating it altogether.
DNS poisoning, also known as DNS cache poisoning, is an attack in which false information is inserted into the cache of a DNS resolver. Instead of returning the requested IP address for a domain name, the attacker's IP address is returned by the resolver.
DNS hijacking is a process of redirecting the queries of the domain name system (DNS) server to a malevolent domain name server (DNS), which is known as a rogue DNS.
URL redirection is a process of forwarding one URL to a different URL. It's also known as URL forwarding, domain redirection, or domain forwarding.
Domain hijacking is a technique used by hackers to acquire the domain names of other people or companies for their gain. By accessing the domain owner's account or exploiting security holes in the domain name system (DNS), hijackers can alter the DNS records to redirect traffic to their own website, a phishing site, or a spam site.
You can learn more about DNS poisoning at: brainly.com/question/30163079
#SPJ11
Which of the following types of digital evidence can be pulled from both a computer and a portable device?
Images
Text history
GPS coordinates
phone call data
Answers
The types of digital evidence that can be pulled from both a computer and a portable device are:
Text historyImagesGPS coordinatesWhat type of evidence can be identified and collected from digital devices?These are known to be Evidence that can be obtained Digitally. They includes:
Computer documentsEmailsText and instant messages,TransactionsImages Internet histories, etc.The above are all examples of information that can be obtained from electronic devices and can be used very well as evidence.
Therefore, The types of digital evidence that can be pulled from both a computer and a portable device are:
Text historyImagesGPS coordinatesLearn more about digital evidence from
https://brainly.com/question/18566188
#SPJ1
Answer:
(A) Images
Explanation:
Got it right on my quiz.
The attachment should help you understand why its Images.

Click to review the online content. Then answer the question(s) below. using complete sentences. Scroll down to view additional
questions.
Memory Matters
Explain the difference between occasional forgetfulness and Alzheimer's disease.
Answers
Answer:
The answer is below
Explanation:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.
Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.
Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Answer:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Explanation:
got 100% on edg
log in by swiping your id card is an application of
a. Encryption
b. Authorization
c. Authentication
d. Trusted network
Answers
Answer: c. Authentication
Explanation:
Answer:
The correct answer is
\(c. \: Authentication\)
how to find the first derivative of a titration curve in excel
Answers
To find the first derivative of a titration curve in Excel, you can use the numerical differentiation technique.
Here's a step-by-step guide:
Open your Excel spreadsheet and ensure that your titration curve data is in two columns: one column for the volume of titrant added and another column for the corresponding pH or other measured parameter.
Create a new column next to your data and label it "First Derivative" or something similar.
In the first row of the "First Derivative" column, enter the formula to calculate the numerical derivative. You can use the central difference formula for numerical differentiation:
=(B3-B1)/(A3-A1)
Here, B3 and B1 represent the pH values in the adjacent cells, and A3 and A1 represent the corresponding volumes of titrant added. Adjust the cell references according to your data range.
Know more about Excel spreadsheet here:
https://brainly.com/question/29987837
#SPJ11
Why is the third hand on a watch called second hand?
Answers
Answer: it is called the "second hand (because it measured the secondary minute divisions of the hour), which was shortened to "second" hand. The convention of the hands moving clockwise evolved in imitation of the sundial.
Explanation:
ASKING AGAIN CAUSE I GOT A WEIRD LINK
HTML5 allows web pages authors to place a/an _________ element around a block-level element that contains child elements
a. nav
b. div
c. h1
d. a
Answers
Answer:
A. Nav
Explanation:
....,..........
Which of the following sorting algorithms is the most inefficient?
A) Merge Sort
B) Bubble Sort
C) Selection Sort
D) Insertion Sort
Answers
Answer:
Bubble Sort
Explanation:
Bubble sort, sometimes referred to as sinking sort, is a simple sorting algorithm that repeatedly steps through the list, compares adjacent elements and swaps them if they are in the wrong order. The pass through the list is repeated until the list is sorted.
the selection of the short-run rate of blank______ (with existing plant and equipment) is the production decision.
Answers
The selection of the short-run rate of output (with existing plant and equipment) is the production decision.
What is production?
Production is the process of converting raw materials into usable goods. The term "production" can also refer to the production of services. Production refers to the process of combining resources to create something useful or valuable.
It is the process of transforming natural resources and raw materials into finished goods that can be sold for a profit. Production decisions are concerned with the management of resources to produce the desired output.
The selection of the short-run rate of output (with existing plant and equipment) is the production decision. The rate of output refers to the number of units of a good or service that a company produces in a given time period. In the short run, a company can only adjust its production level by changing the amount of labor and other variable inputs used while keeping the level of fixed inputs constant.
Therefore, the selection of the short-run rate of output (with existing plant and equipment) is the production decision.
Learn more about Production:https://brainly.com/question/16755022
#SPJ11
How is a limit register used for protecting main memory?
Answers
A limit register is used for protecting main memory by defining the range of addresses that a program can access.
The limit register stores the highest legal memory address for a program, and the processor compares each memory access with the limit register to ensure that it falls within the legal range. If a program attempts to access memory outside the allowed range, the processor generates a trap or interrupt to prevent the program from accessing unauthorized memory.
This mechanism helps to prevent buffer overflow attacks, which occur when a program tries to write data beyond the bounds of an allocated buffer, potentially overwriting critical system data or code. By limiting a program's access to a specific range of memory, the limit register can help protect against such attacks and improve system security.
You can learn more about register at
https://brainly.com/question/28941399
#SPJ11
a restricted computer lab at a college has been set up with local authentication. students are able to log in but do not have internet access. you check the network settings on one of the computers and it has an ip address of 169.254.1.10. what is the problem?
Answers
The problem with the restricted computer lab at the college is likely due to an Automatic Private IP Addressing (APIPA) issue.
What's APIPA issue?When a computer with IP address 169.254.1.10 is unable to obtain a valid IP address from the Dynamic Host Configuration Protocol (DHCP) server, it automatically assigns itself an APIPA address within the range of 169.254.0.1 to 169.254.255.254.
This indicates that the computer is not properly connected to the network and, therefore, lacks internet access.
The issue could be caused by a faulty DHCP server, incorrect network settings, or a physical disconnection in the network infrastructure.
To resolve the problem, the network administrator should check the DHCP server configuration, ensure proper network settings on the student computers, and verify the network connections, such as cables and switches.
Once these steps are taken, the computers should be able to receive valid IP addresses and regain internet access.
Learn more about APIPA address at
https://brainly.com/question/30750169
#SPJ11
You have to insert the author's name at the bottom of all the pages of an article
prepared in the word processor. Which of the following tools is the most suitable
for this?
a) Footer
b) Merge Cells
c) Insert Rows
d) Header
Answers
Answer:
Footer
Explanation:
Which of these purchases is most likely to be paid for with a credit card
A. Soda
B. Lotto ticket
C. Parking fee
D. Plane ticket
Answers
Answer:
plane ticket?
Explanation:
What is Chromolithography and did it help logo design?
Answers
Answer:
Yes, Chromolithography help logo design. The further explanation is given below.
Explanation:
Chromolithography would be a process by which multi-color designs or prints are made. This style of color printing originated from those in the lithography procedure, and now it encompasses a variety of color-printed lithography. A printing technology procedure that uses completely separate printing utensils to add each color of the components.And the above response is the right one.
contoh ralat sintaks
Answers
T/F with a cell in edit mode, you can edit part of the contents directly in the cell and keep part, such as correcting a spelling error.
Answers
True (T).With a cell in edit mode, you can edit part of the contents directly in the cell and keep part, such as correcting a spelling error. While typing into a cell, if you click elsewhere in the worksheet, that's called canceling the edit of the cell. If you press the Enter key, the edit is finished, and the content of the cell is changed. If you press the Esc key, the cell's content remains the same and the edit is canceled.
With a cell in edit mode, you can indeed edit part of the contents directly within the cell while keeping the remaining content intact. This allows for making specific changes or corrections within the cell without overwriting or modifying the entire contents.
For example, if you have a cell with the text "The quick browwn fox jumps over the lazy dog," and you notice a spelling error in "brown," you can activate the cell's edit mode and directly modify only the misspelled word without retyping the entire sentence. Once you make the necessary correction, you can exit the edit mode, and the modified part will reflect the updated content while the rest of the text remains unchanged.
Learn more about edit mode
https://brainly.com/question/1250224
#SPJ11
print a test page what is the answer.
Answers
Answer:
The keys "Ctrl" and "P"
Jason is creating a web page for his school's basketball team. He just finished creating his storyboard. Which tool should he use to start coding?
Storyboard
Text editor
Web browser
Word processing document
You must check the box below prior to sub
Answers
Jason should use a text editor
Answer:
text editor
Explanation:
what is the extension of a Microsoft access database 2013
Answers
Answer:
Access Database (2007, 2010, 2013, 2016)..accdb
Answer:
.accdb
Explanation:
.accdb is the extension of Microsoft Access Database 2013
personal professionalism is only important when you have a full-time job.
true or false?
Answers
Answer: True
Explanation: just cuz