Melinda is useing a BX cutter to prepare wire. What king of wire is she useing?
Answers
The type of wire Melinda is using is a type of armored cable that can be found in home wiring applications. This wire has a sheath that is comprised of interlocking metal armor. It is designed to be installed indoors and is available in a variety of gauges.
Armored cable is sometimes referred to as BX cable.The name "BX" is an abbreviation for "Brick X". This is due to the fact that the wire was initially used in the early 1900s as a replacement for knob-and-tube wiring, which was common in brick buildings.
Because BX wiring is covered in a metal sheath, it is considered more secure than other types of wiring.There are many different types of wire cutters, and each one is designed for a specific purpose.
BX cutters, like the one Melinda is using, are designed to cut through the metal sheath that encases BX cable. This is a necessary step when working with this type of wiring, as the metal sheath cannot be easily stripped away by hand.
With the help of BX cutters, Melinda can prepare her armored cable quickly and easily. This will allow her to complete her wiring project in a timely and efficient manner.
For more such questions on armored cable, click on:
https://brainly.com/question/30757851
#SPJ8
Related Questions
You want to use your Windows workstation to browse the websites on the internet. You use a broadband DSL connection to access the internet. Which network protocol must be installed on your workstation to do this
Answers
Answer:
IP
Explanation:
What was the biggest challenge you faced in getting to where you are today and how did you overcome it? Peer counseling
Answers
when the show spanning-tree vlan 33 command is issued on a switch, three ports are shown in the forwarding state. in which two port roles could these interfaces function while in the forwarding state?
Answers
When the "show spanning-tree vlan 33" command is issued on a switch and three ports are shown in the forwarding state, these interfaces can function in the following two port roles: Designated Port and Root Port.
When the "show spanning-tree vlan 33" command is issued on a switch, it displays information about the Spanning Tree Protocol (STP) status of ports assigned to VLAN 33. If three ports are shown in the forwarding state, these ports are actively forwarding data frames within the VLAN.In STP, each port on a switch can be assigned one of several port roles, depending on its configuration and the state of the network. The two port roles that could be assigned to the three forwarding interfaces are:
Root port: The forwarding interfaces on non-root switches are typically assigned the role of root port, which is responsible for forwarding data frames toward the root bridge.
Designated port: The forwarding interfaces on switches that are not the root bridge and are connected to other switches in the network are typically assigned the role of designated port. This port is responsible for forwarding data frames from non-root switches to the root bridge.
Learn more about interfaces about
https://brainly.com/question/14235253
#SPJ11
one more thing explain why this program would be better written using a function
look my previous q1
Answers
The key use is for mental chunking, to help you grasp what complex software does.
By naming a small function according to its outcome/overall purpose, you reduce the amount of stuff you need to mentally juggle.
It's one of the many tools available to divide and conquer complexity.
Same way as a TV is full of complex stuff, but you press on, and plug into the wall plus an aerial, hdmi and WiFi. You don't talk about how the inside works to make higher level discussions possible
consider the following instruction: lwi rt, rd(rs) interpretation: r[rt] <-mem[r[rs] r[rd]] highlight the path for executing the above instruction. this is a multiple choice question. which of the following paths is the correct answer for this? select the closest matching answer. please type in answer box from the below options(there are 4 options):
Answers
The correct paths of the given instruction is the option 3 in the figure given below.
Path analysis is a technique to identify and evaluate the effects of a collection of factors operating on a specific outcome via different causal routes. Path analysis is a forerunner to and subset of structural equation modeling.
What is R-Type instruction?
When all of the data values needed by an instruction are stored in registers, R instructions are employed. The format for all R-type instructions is OP rd, rs, rt. where the mnemonic for the specific instruction is "OP." The source registers are rs and rt, and the destination register is rd.
What Type of instruction is LW?
The instruction "lw" stands for "load word," and it loads (reads) a word of data from memory into a register. Consequently, the first operand (the destination) defines a register, and the second operand identifies a location in memory.
To learn more about Register click here:
brainly.com/question/28812407
#SPJ4
![consider the following instruction: lwi rt, rd(rs) interpretation: r[rt] <-mem[r[rs] r[rd]] highlight](https://i5t5.c14.e2-1.dev/h-images-qa/answers/attachments/cJyencpgRuKtzK24ycrvO2bvWvYyIhrH.png)
![consider the following instruction: lwi rt, rd(rs) interpretation: r[rt] <-mem[r[rs] r[rd]] highlight](https://i5t5.c14.e2-1.dev/h-images-qa/answers/attachments/8vvS0Am2VCuSVcbPWTGgD1yMVwhM6oTP.png)
![consider the following instruction: lwi rt, rd(rs) interpretation: r[rt] <-mem[r[rs] r[rd]] highlight](https://i5t5.c14.e2-1.dev/h-images-qa/answers/attachments/dlhHNWIudstKrva0bipXSJXl1MLCmT2E.png)
![consider the following instruction: lwi rt, rd(rs) interpretation: r[rt] <-mem[r[rs] r[rd]] highlight](https://i5t5.c14.e2-1.dev/h-images-qa/answers/attachments/XumJ72cSZrS4tptGSQEGjQjqtZGdGgOA.png)
what does the first number in a zip code represent?
Answers
so.. the answer is “ The first digit in a ZIP code represents a defined group of U.S. states. “
hope this helps!!
Use the drop-down menus to complete the steps for using the Go To feature.
1. Press the shortcut key of F5 ✓
2. Type the
✓in the
3. Hit OK or select Special for more options.
✓box.
4
Answers
Answer:
Explanation:
. Select "Go To Special" from the "Go To" dialog box.
5. Choose the type of cell you want to go to, such as a blank cell or a cell with an error, or select "OK" to go to the default type of cell, which is a blank cell.
6.Click "OK" to go to the selected cell or range of cells.
what is adb command???
Answers
Answer:
Android Debug Bridge (adb) is a versatile command-line tool that lets you communicate with a device. The adb command facilitates a variety of device actions, such as installing and debugging apps, and it provides access to a Unix shell that you can use to run a variety of commands on a device.
Explanation:
I hope this helps!!write a function reverse which takes a string as an argument, reverses the string and returns the reversed string. note; you should not return a string that you created inside the reverse function!
Answers
String:- String is a collection of a set of characters terminated by a null character.
So, the required code in Python is
def reverse(string):
str_list = list(string) # convert string to a list of characters
length = len(str_list)
for i in range(length//2):
str_list[i], str_list[length-i-1] = str_list[length-i-1], str_list[i] # swap characters at i and length-i-1
return ''.join(str_list)
def reverse(string):
str_list = list(string) # convert string to a list of characters
length = len(str_list)
for i in range(length//2):
str_list[i], str_list[length-i-1] = str_list[length-i-1], str_list[i] # swap characters at i and length-i-1
return ''.join(str_list)
reverse() that takes a string as an argument, reverses the string and returns the reversed string without creating a new string.
Learn more about string
brainly.com/question/32072600
How many worksheets display in the Excel window when you create a new blank workbook?
(I'm genuinely confused on if it's 1, or 3.)
A. 3
B. 1
C. 2
D. 4
Answers
In Excel, when you create a new blank workbook, there is only one worksheet displayed. If you need more, you'd have to create them yourself. (Option B)
what is excel worksheet?A worksheet (sometimes known as a spreadsheet) is made up of cells into which data may be entered and calculated. Columns and rows are used to order the cells. A workbook always has a worksheet. A workbook may contain several worksheeks. Consider it a book.
To find the worksheet, go to the Home tab, Cells group, Insert, and then Insert Sheet. Tip: You may also right-click the sheet tabs you want to insert and select Insert. Click Worksheet on the General tab, and then OK.
Learn more about worksheet at:
https://brainly.com/question/13129393
#SPJ1
Helppppp meeeeee eee
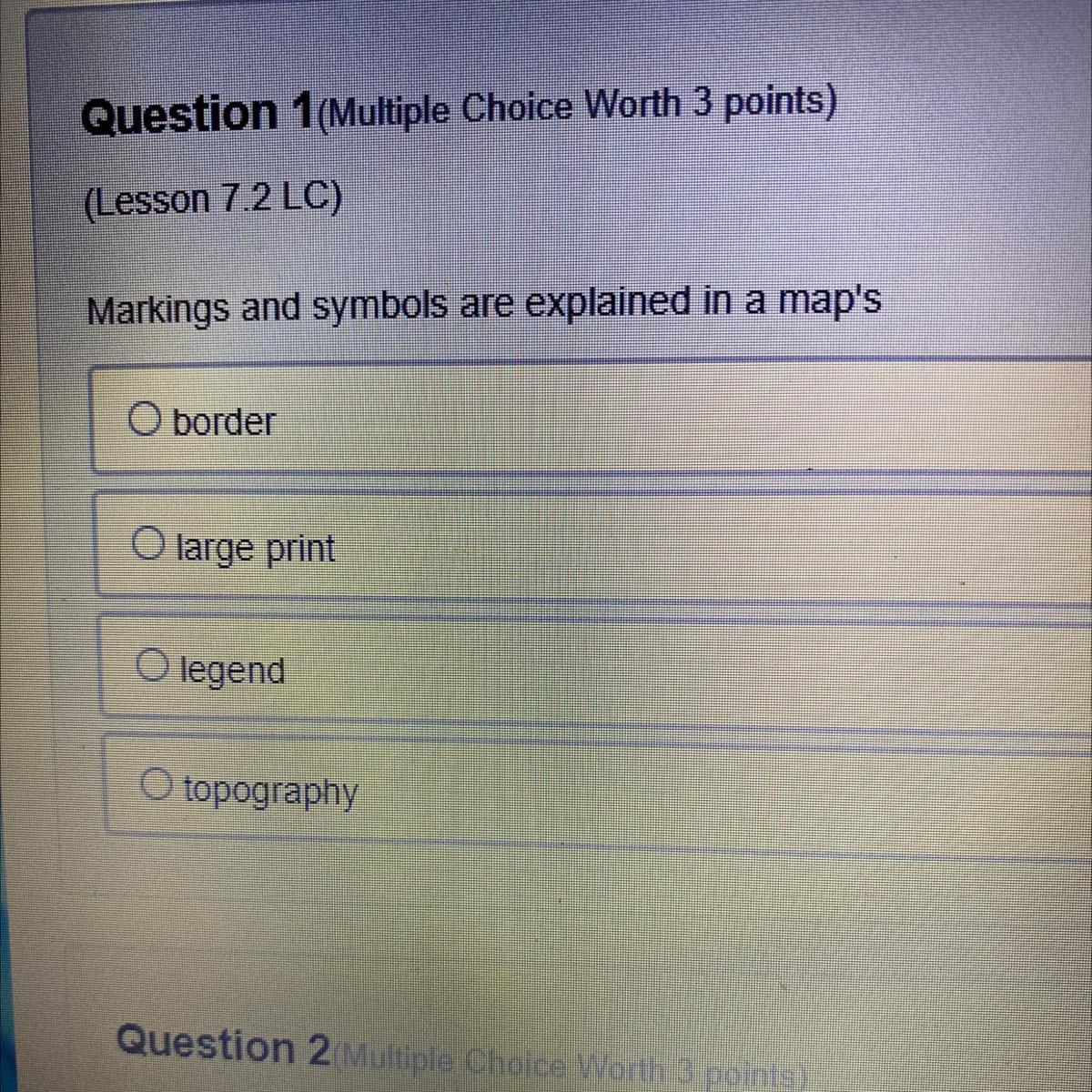
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
Which memory do computers use to read information that has been previously
loaded?
A.Hard drive
B.RAM
C.ROM
D.Virtual memory
Answers
The answer to your question is
b) RAM
When designing a security-in-depth strategy, security measures such as firewalls, vpns and sll would be examples of what type of control?.
Answers
In the designing of a security-in-depth strategy, security measures such as VPNs, SSL, and firewalls are examples of security controls.
Security controls are primarily developed to protect information systems from potenial security risks. Security controls are countermeasures and parameters that safeguard information systems against malicious security threats. Given the vast growing rate of cyberattacks, data security controls are considered vital secuirty meusre today more than ever. VPNs, SSL, and firewalls are some examples of security control.
VPNs: Virtual Private Networks (VPNs) establish a private and secure online connection to the Internet. With VPNs data traffic, IP address, and location of users remain hidden.
SSL: Secure Socket Layer (SSL) establishes an encrypted connection between a server and a client - such as a website and a browser. SSL authenticates the identity of a website and enables an encrypted connection.
Firewalls: A firewall refers to a network security device that monitors and filters outgoing and incoming network traffic based on preset security rules.
You can learn more about Security Controls at
https://brainly.com/question/27960062
#SPJ4
Question :the ubiquitous nature of mobile phones today brings tremendous convenience to our lives, but will misuse of new improvements to this technology result in the loss of that convenience? for instance, camera phones are now banned in many fitness centers, park restrooms, and other similar facilities because some people have used them inappropriately to take compromising photos, and mobile phones are banned in many classrooms because of the disruption of constant text messaging and the use of the phone by dishonest students to cheat on exams. do you think these reactions to mobile phone misuse are justified? is there another way to ensure the appropriate use of mobile phones without banning their use for all individuals? should there be more stringent consequences for those who use technology for illegal or unethical purposes?
Answers
The prevalence of mobile phones has revolutionized the way we communicate and access information. They have become an integral part of our daily lives and have made our lives more convenient in many ways. However, there are also negative consequences associated with their use, such as the misuse of new improvements in technology.
In recent years, we have seen an increase in inappropriate behavior with the use of camera phones and mobile phones, leading to the banning of their use in certain places and situations.The ban on camera phones in fitness centers, park restrooms, and other similar facilities is justified to a certain extent. This is because some individuals have used these devices to take compromising photos of others without their consent. This behavior is not only unethical but also a violation of privacy and can lead to emotional distress for the victim. Therefore, it is important to implement measures that protect individuals' privacy and safety in such settings.
Similarly, mobile phones are banned in many classrooms to prevent cheating during exams and the disruption of constant text messaging. This is understandable because the inappropriate use of mobile phones can affect the quality of education and create an unfair advantage for some students. Therefore, it is important to ensure that students are not using their mobile phones during class time.
To know more about technology visit:
brainly.com/question/26594591
#SPJ11
A rounded-down integer solution can result in a less than optimal solution to an integer programming problem. True False
Answers
Answer:
True, this is because rounding down an integer can cause the solution to be farther away from the optimal solution.
Question 7 what are some of the shortcomings of antivirus software today? check all that apply.
Answers
Answer:
Modern day anti-viruses have a few shortcomings:
1.) False detections. Anti-viruses use a set of algorithms to determine whether or not a application or library contains harmful code such as trojans or rats. But sometimes an anti-virus will flag a file it thinks is dangerous when the file is harmless.
2.) Disk space. Any file or executable takes up disk space in order to exist on your computer; anti-viruses are no exception to this. Anti-viruses may take up a large amount of space on your drive.
3.) Slows down computer. Anti-viruses are constantly loaded into memory to protect your computer. Due to this, they impact your computer's performance.
4.) Don't always work. Any dedicated virus creator will try find a way to bypass anti-viruses and sometimes may succeed. This makes anti-viruses completely useless when it comes to viruses that can bypass them.
They will choose the design team on 2 April. (change this into passive voice)
Answers
Answer:
On 2 April the design team would be choosen by them
The different parts of a video game won't mesh if the designers don't?

Answers
Answer:
Collaborate
Explanation:
I dont know to much about this particular subject, but Collaborate means to come together in agreement. If they can do that they should come together. If they dont collaborate, then it wouldnt come together.
I apologize if this is incorrect
All of the following statements about MapReduce are true EXCEPT: MapReduce handles the complexities of network communication. MapReduce is a general-purpose execution engine. MapReduce handles parallel programming. MapReduce runs without fault tolerance.
Answers
Answer:
The correct option is;
MapReduce runs without fault tolerance
Explanation:
Map Reduce is a technique of processing or a framework of software, that is geared towards managing, sorting and handling large data by working in the Map and Reduce phases where the map function involves the dividing, filtering and sorting of the data and mapping of the split data while the reduce method involves the rearranging, summary activities having the data reduced.
please help with this question

Answers
Answer:
whats the problem/question?
Explanation:
1) Lux Corporation has issued 2,500 shares of common stock and 500 shares of preferred stock for a lump sum of $95,000 cash.Instructions (a) Give the entry for the issuance assuming the par value of the common stock was $8 and the fair value $28, and the par value of the preferred stock was $35 and the fair value $65. (Each valuation is on a per share basis and there are ready markets for each stock.) (b) Give the entry for the issuance assuming the same facts as (a) above except the preferred stock has no ready market and the common stock has a fair value of $30 per share.
Answers
The journal entry for Lux Corporation's issuance of 2,500 shares of common stock and 500 shares of preferred stock, assuming common stock par value of $8 and fair value of $28, and preferred stock par value of $35 and fair value of $65, would be:
Common Stock: $70,000
Paid-in Capital in Excess of Par: $62,500
Preferred Stock: $30,000
In the first step, we determine the total par value of the common stock and the preferred stock by multiplying the number of shares issued by their respective par values. For the common stock, it would be 2,500 shares x $8 = $20,000, and for the preferred stock, it would be 500 shares x $35 = $17,500.In the second step, we calculate the amount of paid-in capital in excess of par for each stock. This is done by subtracting the par value from the fair value of each stock. For the common stock, it would be $28 - $8 = $20 per share, and since 2,500 shares were issued, the total amount would be $20 x 2,500 = $50,000. For the preferred stock, it would be $65 - $35 = $30 per share, and since 500 shares were issued, the total amount would be $30 x 500 = $15,000.Finally, we record the journal entry by debiting the appropriate accounts and crediting the corresponding accounts. The common stock and preferred stock accounts are debited for their respective par values, while the paid-in capital in excess of par accounts are credited for the difference between the fair value and par value of each stock.Learn more about common stock
brainly.com/question/11453024
#SPJ11
How to Find an IP Address in Command Prompt
Answers
First, click on your Start Menu and type cmd in the search box and press enter. A black and white window will open where you will type ipconfig /all and press enter. There is a space between the command ipconfig and the switch of /all. Your IP address will be the IPv4 address.
Definition of IP AddressesInternet Protocol address (or abbreviated IP address) is a numeric label assigned to each device connected to a computer network that uses Internet Protocol for communication. An IP address has two main functions: host or network interface identification and location addressing.
Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, due to the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for IP addresses, was standardized in 1998. IPv6 deployments have been ongoing since the mid-2000s.
IP addresses are written and displayed in human-readable notation, such as 172.16.254.1 in IPv4, and 2001:db8:0:1234:0:567:8:1 in IPv6. The address routing prefix size is specified in CIDR notation by suffixing the address with a significant number of bits, eg, 192.168.1.15/24, which is equivalent to the historically used subnet mask 255.255.255.0.
The IP address space is managed globally by the Internet Assigned Numbers Authority (IANA), and by five regional Internet registrars (RIR) who are responsible in designated areas for assignment to local Internet registries, such as Internet service providers, and other end users. IPv4 addresses were distributed by IANA to RIRs in blocks of approximately 16.8 million addresses each, but have exhausted at IANA's level since 2011. Only one of the RIRs still has a supply for local assignments in Africa. Some IPv4 addresses are reserved for private networks and are not globally unique.
Learn more about IP address at https://brainly.com/question/16011753.
#SPJ4
N Sistema tecnológico es: * A). Es un sistema que se usa solo en computadoras B) Es todo lo referente a tecnología como computadoras y celulares C) Es un conjunto de elementos y procesos que interactúan entre sí, para lograr la fabricación de un producto o servicios y que a su vez satisface necesidades sociales. D )Elaborar un producto con materiales Resistentes para las personas.
Answers
Answer:
C) Es un conjunto de elementos y procesos que interactúan entre sí, para lograr la fabricación de un producto o servicios y que a su vez satisface necesidades sociales.
Explanation:
Un sistema tecnológico se define como un conjunto de elementos y procesos que interactúan entre sí, para lograr la fabricación de un producto o servicio y que a su vez satisface necesidades sociales.
Por lo tanto, todos los dispositivos y máquinas que utilizamos para lograr varios fines pueden clasificarse como dispositivos tecnológicos.
Por ejemplo, un teléfono inteligente es un ejemplo típico de un sistema tecnológico.
Answer:
c
Explanation:
Sukant's professor asks her to take over his online class while he is away because she is an effective digital communicator.
Which of Sukant's traits show that she understands netiquette? Check all that apply.
a) She listens to others and is friendly in her messages.
b) She posts messages that avoid slang and text language.
c) She is the smartest in the class and overshadows others.
d) She is always studying, so she is slow to respond to messages.
e) She respects the privacy of others and avoids cyberbullying.
Answers
Answer:
b is the right answer. she posts messages that avoid slang and text language
What temperature is most commonly used in autoclaves to sterilize growth media and other devices prior to experimentation
Answers
Answer:
The most effective temparature used in autoclave is 121°C
Which of the following best describes top down design?
a. gathering small solutions to related subproblems into a complete solution
b. refining a particular solution into one that is more abstract
c. decomposing a general solution into more concrete solutions to subproblems
d. converting modules into subproblems
e. converting classes into objects
Answers
Decomposing a general solution into more concrete solutions to subproblems best describes top down design. The correct answer is option C.
Option c best describes top-down design. Top-down design involves breaking down a complex problem or system into smaller, more manageable subproblems. It starts with a high-level or general solution and decomposes it into more concrete solutions for each subproblem.
This approach allows for a systematic and organized design process, where the focus is on understanding the overall structure and then gradually refining and addressing the specific details of the subproblems.
By decomposing the general solution into smaller components, top-down design promotes modularity and separation of concerns, making the development process more efficient and maintainable.
Hence, option C is the right choice.
To know more about top down design, visit https://brainly.com/question/20357037
#SPJ11
Which securities protects networks from intruders? *
Application security
Network security
Information security
Operational security
Answers
Answer:
I think it is network security
Explanation:
Heard in an ad before :T
Answer:
Use Kika Clipboard to make paste easypneumonoultramicroscopicsilicovolcanoconiosis
In Unix
How would you complete the following command (that is missing
part _____) so that the results would be saved to a file called
file3.
paste -d: file1 file2 ___________
Answers
To complete the command "paste -d: file1 file2 ___________" in Unix, so that the results would be saved to a file called file3, you need to use the redirection symbol > as shown below:paste -d: file1 file2 > file3
Explanation:In Unix, the "paste" command is used to merge two files line by line. The "-d" option specifies the delimiter character to be used for separating the fields from the two files. In the given command, ":" has been specified as the delimiter, so the fields from file1 and file2 will be separated by a colon.In order to save the output of this command to a file called file3, we use the redirection symbol ">", which redirects the output from the standard output (the terminal, by default) to a file instead. Therefore, "paste -d: file1 file2 > file3" command will merge the contents of file1 and file2, separate them with a colon and save the output to a file called file3.
Conclusion:So, in order to complete the given command in Unix, we need to add the redirection symbol ">", followed by the name of the output file we want to save the results to. Hence, the completed command will look like "paste -d: file1 file2 > file3".
To know more about command visit:
brainly.com/question/32329589
#SPJ11
Why do we have to watch a video to get answers?
Answers
Answer:
The videos contain the answers.
Explanation:
Hey there!
Watching a video can help understand the concept better. If you watch the video, you will learn more. It's also a benefit to watch a video. For many people who can't understand, they can learn by watching the video. So this is a good way to understand things better: watching a video.
Hope this helps!
select the name, creaturetype, creaturesubtype, gender, and appearance from litcharacters for creatures who have made 5 or more appearances (this includes characters that have made 5 appearances). order ascending by the character id. what is the first entry?
Answers
I'm sorry, but as an I don't have access to a specific database or its data. Therefore, I cannot retrieve the first entry from the "litcharacters" table as requested.
To obtain the first entry from the "litcharacters" table with the given conditions, you would need to execute a SQL query on the database that contains the table. The query would look something like this:
SELECT name, creaturetype, creaturesubtype, gender, appearance
FROM litcharacters
WHERE appearance >= 5
ORDER BY character_id ASC
LIMIT 1;
Executing this query on the appropriate database would give you the first entry from the "litcharacters" table that meets the criteria of having 5 or more appearances.
Learn more about database here
https://brainly.com/question/24027204
#SPJ11