Pip is configured with locations that require tls/ssl.
Answers
If Pip is configured with locations that require TLS/SSL, it will automatically verify the SSL/TLS certificates for those locations before downloading the packages. In simple words, Pip checks the SSL/TLS certificate of the package sources before it downloads the packages to make sure they are safe and secure.
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols that provide secure communication between two devices or endpoints. SSL/TLS protocols ensure that the data transmitted over the internet is encrypted and secure against eavesdropping and tampering by a third party.If Pip is configured with locations that require TLS/SSL, then it will use the https protocol instead of the insecure http protocol to fetch packages from the package sources.
The https protocol ensures that the communication between the server and client is secure by using SSL/TLS encryption.
To know more about TLS/SSL visit:
https://brainly.com/question/32248529
#SPJ11
Related Questions
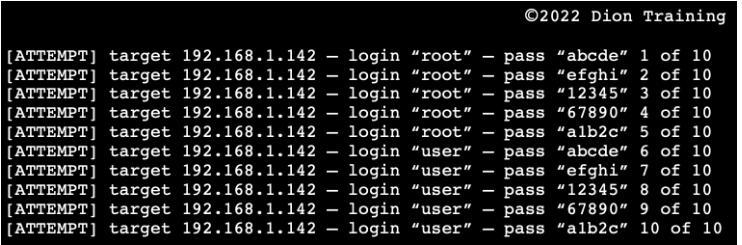
You walked up behind a penetration tester in your organization and saw the following output on their Kali Linux terminal:
Answers
A type of test which the penetration tester is currently conducting is brute force login attempt of a remote service on 192.168.1.142.
What is a penetration test?A penetration test can be defined as a cybersecurity technique that simulates a cyber attack against an end user's computer system, so as to scan, identify, test and check for exploitable vulnerabilities in the following:
Operating systemWeb softwareHost deviceNetworkThis ultimately implies that, a penetration test avails a tester the ability to exploit a weakness and potential security threats on a test network as a privileged user, during vulnerability assessments of the system.
In this scenario, we can infer and logically deduce that a type of test which the penetration tester is currently conducting is brute force login attempt of a remote service on 192.168.1.142.
Read more on penetration test here: https://brainly.com/question/25813524
#SPJ1
Complete Question:
You walked up behind a penetration tester in your organization and saw the following output on their Kali Linux terminal: What type of test is the penetration tester currently conducting?
Oregon Law - Nail TechVentilation by natural or mechanical methods which removes or exhaust fumes, vapors or dust to prevent hazardous conditions from occurring. Allow the free flow of air in a room in proportion to the size and capacity of the room
Answers
According to the Oregon Law, the ventilation can be provided either by natural or mechanical methods, and it should be efficient enough to remove or exhaust fumes, vapors or dust.
As per the Occupational Safety and Health Administration (OSHA), ventilation is a necessary means to control the risks of inhaling hazardous chemicals or dust in the workplace. Therefore, a nail salon must be adequately ventilated to minimize the health risks associated with nail care products and ensure that nail techs and their clients are not exposed to harmful substances. To achieve this, the Oregon Law recommends two types of ventilation- natural and mechanical. Natural ventilation- It is a system of ventilating a room that involves the flow of air through open windows, doors, and other openings in the room's walls. It is an inexpensive way to provide ventilation in a workplace. Mechanical ventilation- It is a system of ventilating a room that uses mechanical devices to move air in and out of a room.
Learn more about Ventilation visit:
https://brainly.com/question/11471552
#SPJ11
FILL THE BLANK. the term systems development life cycle (sdlc) describes the life of an information system from conception to _____
Answers
The term Systems Development Life Cycle (SDLC) describes the life of an information system from conception to deployment or implementation.
The Systems Development Life Cycle (SDLC) is a structured approach used in software development and information system management. It encompasses various phases, including requirements gathering, system design, development, testing, deployment, and maintenance.
The last phase of the SDLC is the deployment or implementation stage, where the developed system is installed and made operational. This involves activities like data conversion, user training, system integration, and finalizing hardware and software configurations. Once the system is successfully deployed, it enters the maintenance phase, where ongoing support and enhancements are provided. The completion of the SDLC is marked by the deployment or implementation stage, ensuring that the developed system is ready for use by its intended users.
Learn more about Systems Development Life Cycle here:
https://brainly.com/question/14804328
#SPJ11
write a BASIC program that will calculate the square root of all numbers from 20 to 64
Answers
Here's an example of a BASIC program that calculates the square root of numbers from 20 to 64:
10 FOR I = 20 TO 64
20 S = SQR(I)
30 PRINT "The square root of "; I; " is "; S
40 NEXT I
This program uses a FOR loop to iterate through the numbers from 20 to 64. For each number, it calculates the square root using the SQR function and then prints out the result using the PRINT statement. The program uses a variable S to store the square root value.
hannes complains that his computer is always giving error messages, the file names and folder names are garbled, and there is an odd noise coming from his computer tower. which hardware device do you suspect is causing the problem?
Answers
Answer:
It could be the hard disk drive (HDD)
Write a program to input 6 numbers. After each number is input, print the smallest of the numbers entered so far.
Answers
Python is frequently considered as one of the simplest programming languages to learn for novices. Python is a wonderful place to start if you're interested in learning a programming language. Additionally, one of the most popular uses of it
Explain about the Python?The def keyword in Python is used to define a function; it is prefixed with a user-supplied function name to construct a user-defined function.
Using our understanding of Python's computational language, we can write the following code in this exercise:
The enclosed image contains the code.
The Python can be written as:
Input ("Enter a number:"): num1 = int
Printing "Largest:" plus str(num1)
Number 2 is equal to int("Enter a number: ");)
If NUM2 > NUM1:
if not: print("Largest: " + str(num2)
num3 = int(input("Enter a number: ")) print("Largest: " + str(num1))
num4 = int(input("Enter a number: ")) print("Largest: " + str(max(num1, num2, num3)))
num5 = int(input("Enter a number: ")) print("Largest: " + str(max(num1, num2, num3, num4)))
num6 = int(input("Enter a number: ")) print("Largest: " + str(max(num1, num2, num3, num4, num5))
The largest is "Largest:" + str(max(num1, num2, num3, num4, num5, num6))
To learn more about Python refer to:
https://brainly.com/question/26497128
#SPJ4
deals with ensuring that data is protected against unauthorized access, and if the data are accessed by an authorized user, that the data are used only for an authorized purpose. question 3 options: a) integrity b) confidentiality c) compliance d) availability
Answers
The answer to your question is "confidentiality."
Confidentiality deals with ensuring that data is protected against unauthorized access, and if the data are accessed by an authorized user, that the data are used only for an authorized purpose. Confidentiality is a critical aspect of data protection, and it involves implementing various security measures to prevent unauthorized access to sensitive information.
One of the key ways to ensure confidentiality is by implementing strong access control policies that limit access to sensitive data only to authorized personnel. Encryption is another crucial technique that can be used to protect data by ensuring that even if it falls into the wrong hands, it cannot be read or understood without the encryption key.
In addition to these measures, organizations need to implement robust security protocols, such as firewalls and intrusion detection systems, to prevent cyberattacks that could compromise data confidentiality. Data backups and disaster recovery plans are also essential in ensuring that data can be recovered in case of a breach or other incident.
Overall, ensuring data confidentiality is vital for protecting sensitive information from unauthorized access and misuse. Organizations must implement various security measures to safeguard their data and maintain the trust of their customers and stakeholders.
Learn more about stakeholders here: https://brainly.com/question/30241824
#SPJ11
Preset arrangements of panels organized to make particular tasks easier are called:
Answers
The workspaces are the arrangements of panel that are organized for making the task to operate more easier.
What are workspaces?The workspaces can be understood as the arrangements of desktops in a large organization to reduce the clutter of work and make the work to operate more easier.
The workspaces can be well organized email of the entire organization, a cloud based system of entire organization for easy access and working.
Learn more about workspaces, here:
https://brainly.com/question/24946752
#SPJ1
2.3 Code Practice: Question 1
Answers
Answer:
a=int(input("Enter a numerator: "))
b=int(input("Enter a divisor: "))
quotient=a/b
remainder=a%b
print("Quotient is: " + str(int(quotient)))
print("Remainder is: " + str(int(remainder)))
Explanation:
Hope this helps lovely :)
Answer:
Answer is in explanation
Explanation:
num = int(input("Enter Numerator "))
den = int(input("Enter Denominator "))
one=int(num/den)
two=int(num%den)
print(one + two)
a query retrieves specific data from one or more tables to answer a question.
Answers
A query retrieves specific data from one or more tables to answer a question, which might include information about clients, items, or orders, for instance.
A database can have more than 100 tables with countless records that can be obtained using the SQL query language to generate queries. Queries are an essential component of any database system because they enable the user to communicate with the database and obtain the desired information in a structured way.
A user can specify the data they want to extract by writing a query that extracts it from one or more tables. When creating a query, the user specifies which tables will be queried and which fields will be returned. Query results can be manipulated or used as the basis for further queries. SQL is one of the most widely used query languages, and it can be used to create complicated queries, make modifications to data, and create database objects.
To know more about instance visit:
https://brainly.com/question/30039280
#SPJ11
Why is cyberbullying so devastating to many people beyond just the victim?
Answers
Answer: If the situation goes undetected, it can lead to serious situations, self-harm, and damaged relationships. According to Superintendent Alex Geordan, some common long-term effects of cyberbullying include depression, low self-esteem, unhealthy addictions, trust issues, and poor mental health.
How can we solve mental stress?
Hello can anyone answer
Answers
Answer:
Please don't delete it. Because other people did!
Explanation:
Use guided meditation, Practice deep breathing, Maintain physical exercise and good nutrition!
By making yourself comfortable around your environment.I know it can be hard but try making yourself feel distracted from stress.Have a break from what you are doing and take your time to heal.
Explanation:
what process involves placing one pdu inside of another pdu?
Answers
Answer: encapsulation
Explanation: When a message is placed inside of another message, this is known as encapsulation. On networks, encapsulation takes place when one protocol data unit is carried inside of the data field of the next lower protocol data unit.
When a message is placed inside of another message, this is known as encapsulation.
What is Encapsulation?Encapsulation is one of the fundamental concepts of object-oriented programming (OOP). Encapsulation, as it is defined, is the idea of combining data itself with methods that operate on it into a single entity, much like a class in Java.
This concept is widely used to conceal the internal representation or state of an entity.
The fundamental idea of this system is straightforward. For example, you might possess some characteristic that is concealed from view from the exterior of an item.
Encapsulation is a technique for preventing direct user access to some object components, preventing users from seeing the state values for all of an object's variables.
Therefore, When a message is placed inside of another message, this is known as encapsulation.
To learn more about Encapsulation, refer to the link:
brainly.com/question/29563804
#SPJ5
Question: Alex wants to identify the number of a policies he has soldof a specified type. Calculate this information as follows:
a. in cell K8 beginto enter a formula using the DCOUNTA function
b. Based on the headers and data in the client's table, and using structured references, count the number of values in the Policy type column that match the criteria in the range j5:j6
Excel Worksheet the CTC Casuality Insurance Managing Formulas Data and Tables project
Answers
To calculate the number of policies Alex has sold of a specified type, we can use the DCOUNTA function in Excel. Here's how you can do it step-by-step:
1. Start by entering the formula in cell K8.
2. In the formula, use the DCOUNTA function, which counts the number of non-empty cells in a column that meet specific criteria.
3. Based on the headers and data in the client's table, use structured references to specify the criteria for the count.
4. The criteria range is J5:J6, which means we will be looking for matches in the Policy type column
Let's break down the formula:
- DCOUNTA is the function we are using to count the values.
- Table1[#All] refers to the entire table where the data is located.
To know more about DCOUNTA visit:
https://brainly.com/question/33596251
#SPJ11
Melanie needs to ensure that readers are able to locate specific sections within a document easily. What should she include in
the document?
concordance
index
table of contents
bibliography
Answers
Answer:
according to me,she should include an index
Answer:
index
Explanation:
Which of the following best describes the average amount of stored data per user for the first eight years of the application existence
Answers
The option that best describes the average amount of stored data per user for the first eight years of the application existence is memory.
What is RAM memory?The memory of a system is known to bee RAM which is Random Access Memory.
Conclusively, This is known to be a part of system hardware where operating system (OS), and data are saved. The option that best describes the average amount of stored data per user for the first eight years of the application existence is memory.
Learn more about data from
https://brainly.com/question/19243813
#SPJ1
Which of the following do not describe net neutrality?
a.
Access to all data on the internet is equal
b.
Certain services are faster than others on the internet
c.
All services are equal on the internet and they compete on quality
d.
ISPs don’t provide more bandwidth to preferred services
Answers
The answer is b. Certain services are faster than others on the internet.
What is Net neutralityNet neutrality is the principle that all internet traffic should be treated equally, without discrimination or favoritism towards certain websites, applications, or services.
Option a is correct as it describes the principle of net neutrality. Option c is also correct as it emphasizes that all services compete on quality rather than having an unfair advantage due to special treatment by ISPs
Read more on Net neutrality here https://brainly.com/question/13165766
#SPJ1
A set of small databases where data are collected, processed, and stored on multiple computers within a network is a A. centralized database. B. high-impact process. C. distributed database. D. flat file database.
Answers
A set of small databases where data are collected, processed, and stored on multiple computers within a network is called a distributed database. So, option C is correct.
A distributed database is a type of database that is spread across multiple computers or sites within a network. Each computer or site in the network maintains a subset of the overall database, and data can be accessed and processed by any computer in the network.
The advantage of a distributed database is that it allows for greater scalability and reliability than a centralized database.
With a centralized database, all data is stored on a single computer or server, which can be a single point of failure. In contrast, with a distributed database, the data is distributed across multiple computers, which can help to improve the reliability and availability of the system.
Additionally, a distributed database can be more easily scaled by adding additional computers to the network, whereas a centralized database can become a bottleneck as the amount of data and users increases.
However, managing a distributed database can be more complex than managing a centralized database, as data must be synchronized and maintained across multiple computers. This requires specialized software and protocols to ensure that data is consistent and up-to-date across the entire network.
This type of database offers advantages in terms of scalability and reliability but requires specialized management to ensure consistency and synchronization of data across the network.
So, option C is correct.
Learn more about database:
https://brainly.com/question/31446078
#SPJ11
If you spend time on social media, you probably see many infographics. How can you determine whether the information contained in them is trustworthy? When you create infographics, what can you do to make it more likely that the viewer will trust you?
Answers
Answer:
Provide sources.
Explanation:
Providing sources for your infographic would be the best I can think of.
Either a direct quote, a source for a graph, etc.
based on the turing test, all commercial artificial intelligence systems are a long way from showing any significant intelligence. true false
Answers
This is a true statement. The Turing Test is a measure of a machine's ability to exhibit intelligent behavior that is indistinguishable from that of a human.
While commercial artificial intelligence systems have come a long way in recent years, they still have a long way to go before they can pass the Turing Test and demonstrate true intelligence. While many AI systems are capable of performing complex tasks such as natural language processing and image recognition, they lack the ability to truly understand context and nuance. In addition, AI systems are limited by their programming and the data they are trained on, which can lead to errors and biases. Therefore, it is true that all commercial artificial intelligence systems are still a long way from showing any significant intelligence as measured by the Turing Test.
To know more about Turing Test visit:
https://brainly.com/question/28240243
#SPJ11
what is the primary reason why emergency services communications (phone or radio) are recorded?
Answers
The answer states that, if necessary, communications may be included in a legal record.
What does the term "communications" mean?Transmit and receive messages through both verbal and non-verbal means is the process of communication. The goal of communication is to create understanding amongst two or more people by sharing data in the shape of thoughts, views, and ideas in a two-way fashion.
What do jobs in communications do?These experts create and preserve a company's engagement with the general public. They develop social media strategy, manage information production, maintain public relationships, and create news releases. At reduced ranks, they could narrow their attention to only one facet of a company's communication plan.
To know more about Communications visit :
https://brainly.com/question/15059972
#SPJ4
Write a program in java to input N numbers from the user in a Single Dimensional Array .Now, display only those numbers that are palindrome
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that input N numbers from the user in a Single Dimensional Array .
Writting the code:class GFG {
// Function to reverse a number n
static int reverse(int n)
{
int d = 0, s = 0;
while (n > 0) {
d = n % 10;
s = s * 10 + d;
n = n / 10;
}
return s;
}
// Function to check if a number n is
// palindrome
static boolean isPalin(int n)
{
// If n is equal to the reverse of n
// it is a palindrome
return n == reverse(n);
}
// Function to calculate sum of all array
// elements which are palindrome
static int sumOfArray(int[] arr, int n)
{
int s = 0;
for (int i = 0; i < n; i++) {
if ((arr[i] > 10) && isPalin(arr[i])) {
// summation of all palindrome numbers
// present in array
s += arr[i];
}
}
return s;
}
// Driver Code
public static void main(String[] args)
{
int n = 6;
int[] arr = { 12, 313, 11, 44, 9, 1 };
System.out.println(sumOfArray(arr, n));
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Hey, if anyone is familiar with python coding I would be appreciative of some troubleshooting help on some code.
I am trying to get a proper decimal response on a division question and can't get anything except 0 or 0.0 when I convert result3 to a float. My question is how do I get a PROPER decimal response on this, and thank you.
the code :
numy1=(8)
numy2=(13)
numy3=((numy2)-(numy1))
result3=(numy3)/(numy1)
print (result3)
#the proper answer should be 0.625
Answers
I downloaded your ide and it seems you just need to turn your initial numy1 and numy2 to floats.
numy1 = float(8)
numy2 = float(13)
numy3 = numy2 - numy1
result3 = numy3 / numy1
print(result3)
This will print out your desired result.
6. Before cleaning your electronics, you should turn off the power to the device.
True
False
Answers
Answer:
True
Explanation:
If you leave the device on while cleaning, you risk electrocution.
Answer:
true to prevent damage or a nasty shock, you need to turn off power to your machine. For computers, you should power down and then unplug the device. You'll also want to unplug the individual monitors. Unplug laptops and remove their batteries if your model allows for this to be done. Explanation:
Write: In paragraph 137, why does Norma use "us" over and over again?
Answers
In paragraph 137 of Button, Button by Richard Matheson, Norma used 'us' over and over again because she wanted to stress the fact that her request was not born out of selfishness.
Why did Norma use the word, 'us' repeatedly?After the conversation that Norma had with Arthur the night before, she could not help but believe that Arthur considered her to be a selfish person.
In her quest to prove that her request was not just for her but also for Arthur, she used the word 'us' over and over again. This was meant to demonstrate the fact that her intention was selfless and she was working for the good of two of them.
Learn more about Button, Button by Richard Matheson here:
https://brainly.com/question/24581622
#SPJ1
Part of host hardening is to reduce the attack surface.
what configuration changes does reducing the attack surface involve?
removing unwanted and unnecessary software
disabling unused os features and services
closing unnecessary network ports
all of the above
Answers
The configuration changes that reducing the attack surface involves include removing unwanted and unnecessary software, disabling unused OS features and services, and closing unnecessary network ports. By doing so, the server is less susceptible to attacks.
1. Removing unwanted and unnecessary software: The more software you have installed on your server, the more attack vectors are available. This software may contain vulnerabilities that attackers can exploit.
2. Disabling unused OS features and services: Operating systems come with various features and services, not all of which are required. These features and services provide attack vectors that attackers can use. Disabling these unused features and services reduces the attack surface.
3. Closing unnecessary network ports: Open network ports provide attackers with a way to gain access to the server. Reducing the number of open ports reduces the attack surface. Administrators should close any ports that are not necessary for the server to function. It is important to ensure that necessary ports remain open and that firewalls are configured correctly.
To know more about unnecessary visit:
https://brainly.com/question/32207934
#SPJ11
Hello,
Please help me make an introduction about Salesforce, its main
features, and who uses Salesforce for a written proposal. Thank
you.
Answers
It offers a range of features and functionalities that help organizations manage their customer interactions and streamline their sales, marketing, and customer service processes.
Contact and Account Management: Salesforce allows users to store and manage customer data, including contact details, communication history, and account information. This helps businesses keep track of their interactions with customers and provides a centralized database for easy access and analysis.
Sales and Opportunity Management: Salesforce provides tools for managing the entire sales process, from lead generation to closing deals. Users can track leads, manage sales opportunities, forecast revenue, and generate reports to analyze sales performance.
To know more about opportunities visit:
https://brainly.com/question/14893179
#SPJ11
What is the total running time of counting from 1 to n in binary if the time needed to add 1 to the current number i is proportional to the number of bits in the binary expansion of i that must change in going from i to i + 1?
Answers
The running time would be about 67minutes
A photograph is created by what?
-silver
-shutters
-light
-mirrors
Answers
Answer:
Mirrors and light maybe
Explanation:
Answer
Light.
Explaination
A photo is created when light falls in a photo–sensitive surface usually from an electronic image sensor.
define computer network
Answers
Answer:
Explanation:
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other.