___________ poses the greatest risk to workers because it is more common and more easily transmitted than other bloodborne diseases.
Answers
Answer: Hepatitis
Explanation: According to the center for disease control and prevention (CDC) HIV, hepatitis B and Hepatitis C are the most common bloodborne pathogens which workers are more susceptible to contract. According to CDC's the estimated risk of an HIV infection is 0.3 percent, 1 from 300 people. Hepatitis B has from 6 to 30 percent causing serious liver damage. And Hepatitis C has a risk between 2 and 4 percent
Related Questions
Which two factors do ergonomic principles consider a part of a job?
Answers
Answer:
mental stress, social stress, physical stress
travelling factors, relationship factors, environmental factors
Explanation:
Ergonomic principles consider a part of a job? =
mental stress, social stress, physical stress
travelling factors, relationship factors, environmental factors
describe the component of communication system with the help of diagram
Answers
Answer:
Solution
Communication:
The communication system is a system that describes the information exchange between two points. The process of transmission and reception of information is called communication.
Components of Communication:
The three essential components of a communication system are:
Transmitter:
The transmitter modulates the message signal.
Modulation is the process of converting a signal into a form suitable for transmission.
A transmitter is a telecommunications electrical device that generates radio waves so that data may be transferred or received through an antenna.
The transmitter may generate an alternating current of radio frequency, which is then applied to the antenna, which radiates it as radio waves.
Channel:
A communication channel is a physical transmission channel in telecommunications and computer networking.
A channel is a device that delivers data from one or more senders (or transmitters) to one or more receivers.
Or in other words, the channel is what connects the output of the transmitter to the receiver input.
Receiver:
The receiver does the demodulation. Demodulation is the process of recovering the correct message signal.
The received signal, which is picked up from the broadcast signal at the channel output, is processed by the receiver to reproduce the original message signal in a recognizable form for transmission.
A radio receiver, also known as an FM receiver, is a device that receives radio waves and converts the data carried by them into useable information.
The desired frequency waves are caught using an antenna

1) You are a digital media professional who wants to interview a senator as she stands on the steps of the capitol building. What kind of microphone would you select and why would you choose it ?
Answers
As a digital media professional, if I wanted to interview a senator as she stands on the steps of the Capitol building, I would select a directional or shotgun microphone.
A directional or shotgun microphone is a type of microphone that is designed to pick up sound primarily from one direction and reject sounds from other directions. This makes it ideal for outdoor interviews where there may be ambient noise, such as wind or traffic.
By using a directional or shotgun microphone, I can ensure that the senator's voice is captured clearly and with minimal background noise. This is important for the quality of the interview and for the audience's ability to hear and understand the senator's responses.
Additionally, a directional or shotgun microphone can be mounted on a boom pole, making it easy to position the microphone close to the senator's mouth without it being visible in the shot.
Overall, a directional or shotgun microphone would be the best choice for conducting an outdoor interview with a senator on the steps of the Capitol building due to its directional sensitivity, ability to reject ambient noise, and ease of positioning.
How does visualizing help you better understand a poem?
Answers
Read each question below. Then, using the drop-down menus, decide if it represents the purpose, construction, or support aspect of choosing a website host.
Will the website be built by a programmer at a company?
What type of content will be on the website?
Will the website be used to share family pictures or as a professional site for posting news?
Will customers be making secure transactions on the website?
How extensive of a control panel, or location of login and website control, will be needed?
Answers
Answer:
ConstructionPurposePurposeSupportConstructionExplanation:
Will the website be built by a programmer at a company? construction
What type of content will be on the website? purpose
Will the website be used to share family pictures or as a professional site for posting news? purpose
Will customers be making secure transactions on the website? support
How extensive of a control panel, or location of login and website control, will be needed? Construction
__________________________________________________
discarding ping packet reduces the risk that an attacker will find you on the internet
a. true
b. false
Answers
Answer:
Explanation:
The statement is false. Discarding ping packets does not reduce the risk of an attacker finding you on the internet.
Ping is a network utility used to test the reachability of a host on an Internet Protocol (IP) network. It sends an Internet Control Message Protocol (ICMP) Echo Request to the target host and waits for an ICMP Echo Reply. Discarding ping packets does not inherently enhance security or make you less visible to potential attackers. Attackers can employ various methods, such as port scanning or vulnerability scanning, to identify and target systems on the internet regardless of whether ping packets are discarded. Implementing robust network security measures, such as firewalls, intrusion detection systems, and access controls, is crucial for reducing the risk of attacks, rather than simply discarding ping packets.
Learn more about network click here:
https://brainly.in/question/13044019
#SPJ11
1. Create a naive Bayes model for this data set.
2. What prediction will the naive Bayes model return for the query q=(1,0,0)?
Answers
Answer:
import the GaussianNB class from the scikit-learn naive bayes module using the import statement;
from sklearn.naivebayes import GaussianNB
create the classifier,
clf = GaussianNB()
Then train or fit a section of the dataset (the training set) with the classifier, then predict the label of the test section of the dataset with the provided query "q".
trained = clf.fit( train_features, train_label)
predict = clf.predict(q)
Explanation:
The scikit-learn is a machine learning package in python used to create machine models from datasets. It has several classifiers and regressions algorithms.
The naive baye algorithm is a machine learning class in python used in supervised machine learning to create models used to predict a label given a set of features using a classifier.
____ is an OO programming language developed by Sun Microsystems that runs on top of the Web browser software
Answers
Java is an OO programming language developed by Sun Microsystems that runs on top of the Web browser software. Java is an extremely popular programming language that is used to create a wide range of applications and systems.
Java is an object-oriented programming language that is particularly well suited for developing internet applications. Java is a general-purpose programming language that has been used to create everything from desktop applications to mobile applications.
It is particularly well-suited for developing web applications due to its ability to run on top of web browsers. Java is known for its portability, security, and reliability. Java programs are executed within the Java Virtual Machine (JVM), which provides a layer of abstraction between the program and the underlying hardware.
This makes Java programs highly portable, meaning they can be executed on a wide range of systems without needing to be recompiled.
To learn more about web browser: https://brainly.com/question/22650550
#SPJ11
populating missing data with default values, correcting data inaccuracies, and summarizing overly detailed data is an aspect of the phase of the crisp-dm. question 17 options: a) data understanding b) evaluation c) data preparation d) modeling
Answers
Populating missing data values with default values, correcting data inaccuracies, and summarizing overly detailed data is a feature of the data preparation phase of the CRISP-DM. Hence, option (c) 'data preparation' is the correct answer.
The 'CRoss Industry Standard Process for Data Mining' (CRISP-DM) refers to a process model that functions as the base for a data science process. CRISP-DM is generally a methodology for understanding how business-related problems are solved with data-based solutions. CRISP-DM has six sequential phases:
Business understanding: Determining the needs of the business need.Data understanding: Collecting and analyzing data sets to accomplish the business project, or correct impute.Data preparation: Preparing/organizing final datasets by removing erroneous values as well as summarizing data details.Modeling: Evaluating various modeling techniques to choose one best.Evaluation: Accessing the results of multiple business models and selecting one that best works to meet business objectives.Deployment: Delivering the final result or output to the stakeholders.As per the above discussion, it is obvious that it is the data preparation phase of the CRISP-DM that corrects values with errors, replaces missing values with default data values, and summarizes overly detailed data.
You can leran more about CRISP-DM at
https://brainly.com/question/14991835
#SPJ4
In a while loop, the Boolean expression is tested Group of answer choices both before and after the loop is executed before the loop is executed after the loop is executed
Answers
The Boolean expression in a while loop is tested before the loop is executed.
In a while loop, the Boolean expression is tested before the loop is executed. This means that the condition is checked at the beginning of each iteration. If the condition evaluates to true, the loop body is executed. If the condition is false, the loop is skipped entirely, and the program continues with the next statement after the loop. This setup allows the loop to potentially execute multiple times as long as the condition remains true. If the condition becomes false during the execution of the loop, the program exits the loop and continues with the next statement after the loop.
Learn more about Boolean expression here:
https://brainly.com/question/29025171
#SPJ11
Data visualization cannot be used for which of the following? A. Revealing trends B. Correcting for sampling error C.Comparing groups D.Identifying correlations E. Highlighting key facts
Answers
Data visualization can be used for revealing trends, comparing groups, identifying correlations, and highlighting key facts. However, it may not be the best tool for correcting for sampling error. Sampling error occurs when a sample does not accurately represent the population being studied, and it can lead to inaccurate conclusions.
Data visualization is a powerful tool that helps in presenting complex information in a graphical format, making it easier to understand and interpret. However, it cannot be used for every aspect of data analysis. Among the options provided, data visualization cannot be used for B. Correcting for sampling error.
Sampling error occurs when the sample selected for a study does not accurately represent the population. Data visualization can reveal trends (A), compare groups (C), identify correlations (D), and highlight key facts (E), but it does not have the capability to correct sampling errors. To address sampling errors, researchers should consider using a larger sample size or adopting better sampling techniques to ensure that the sample is representative of the population. Analyzing and interpreting the data correctly is also crucial to minimize the impact of sampling errors on the conclusions drawn from the study.
Learn more about visualization here:
https://brainly.com/question/30541124
#SPJ11
combining strings. assign secretid with firstname, a space, and lastname. ex: if firstname is barry and lastname is allen, then output is: barry allen java
Answers
To combine strings in the given format of firstname, followed by a space, and then lastname, you can concatenate the strings and assign the result to secretid. For example, if firstname is "Barry" and lastname is "Allen," the output would be "Barry Allen."
To achieve the desired output format, you can use string concatenation in your programming language of choice. The specific implementation may vary depending on the programming language you are using, but the general approach remains the same.
Here's an example using Java:
String firstname = "Barry";
String lastname = "Allen";
String secretid = firstname + " " + lastname;
System.out.println(secretid);
In this Java example, we declare two string variables, firstname and lastname, with the respective values "Barry" and "Allen". Then, we concatenate the strings using the + operator, along with a space enclosed in double quotes, to separate the firstname and lastname. The result is assigned to the secretid variable. Finally, we print the secretid, which outputs "Barry Allen" as the combined string.
Learn more about Java here: https://brainly.com/question/12972062
#SPJ11
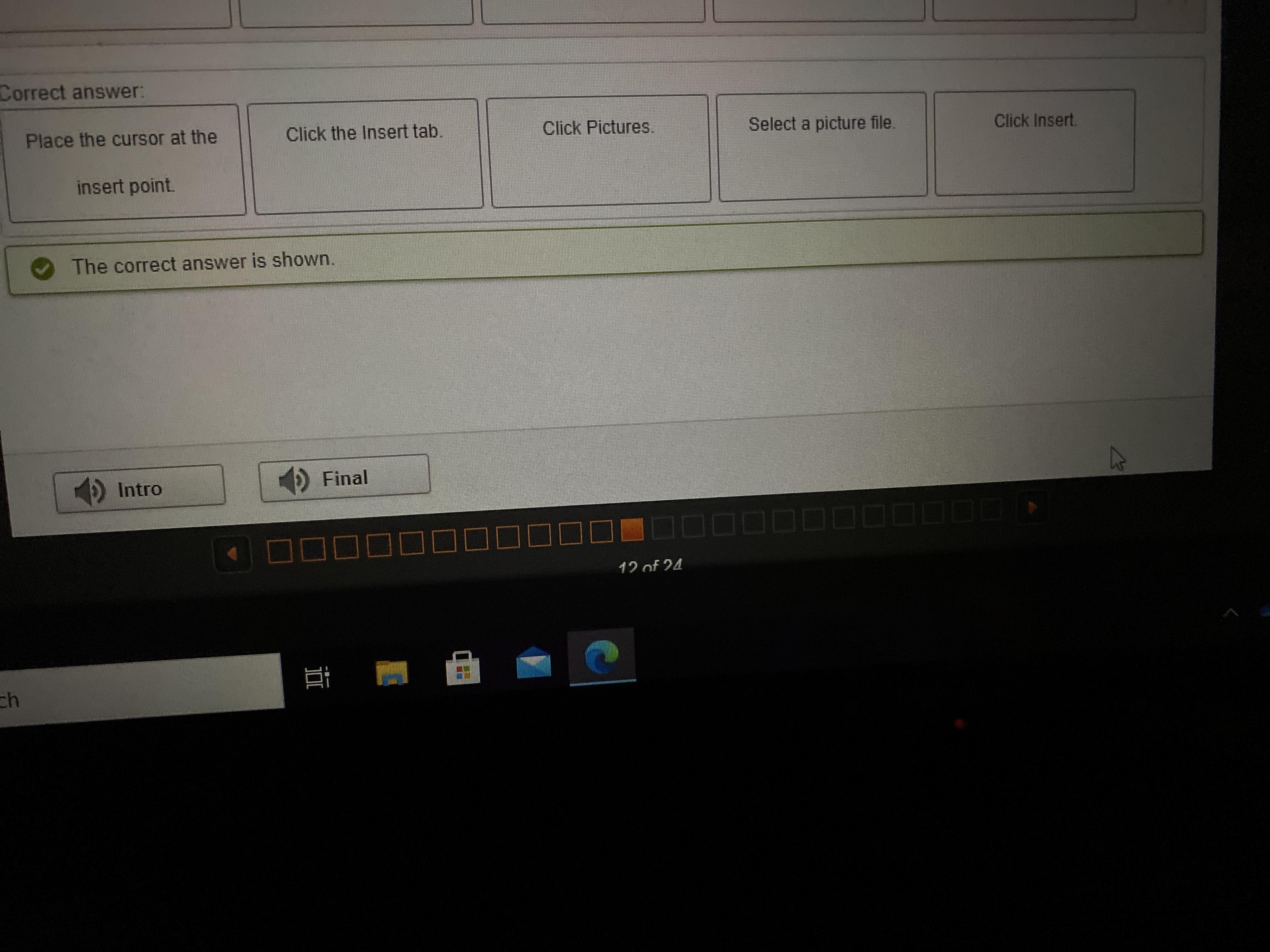
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
Licensing is best described as:
a. a nonequity method of international business in which an entrepreneur contracts his or her management techniques and skills to a (foreign) purchasing company.
b. a method that involves giving a foreign manufacturer the right to use a patent, technology, production process, or product in return for the payment of a royalty.
c. an equity partnership that involves selling patents to foreign governments.
d. a method of doing international business whereby a foreign entrepreneur supplies the manufacturing technology or infrastructure for a business and then turns it over to local owners.
Answers
The best description of licensing is: (b). a method that involves giving a foreign manufacturer the right to use a patent, technology, production process, or product in return for the payment of a royalty.
Licensing is a contractual agreement between the licensor (owner of the technology or product) and the licensee (foreign manufacturer) that allows the licensee to use the licensor's technology or product for a specified period of time in exchange for a fee or royalty payment. This method is commonly used by companies to expand their business globally without having to invest heavily in manufacturing facilities, research and development, and marketing in foreign countries.
To learn more about licensing; https://brainly.com/question/12928918
#SPJ11
(Java) Complete the method definition to output the hours given minutes.Output for sample program: 3.5public class HourToMinConv {public void outputMinutesAsHours(double origMinutes) {/* Your solution goes here */}public static void main (String [] args) {HourToMinConv timeConv = new HourToMinConv();// Will be run with 210.0, 3600.0, and 0.0.timeConv.outputMinutesAsHours(210.0);System.out.println("");}}
Answers
Structured Streaming introduces the idea of the output mode. Spark Structured Streaming needs a sink, as we already stated in our previous post. The result table's data is written according to the output mode.
The best way to read streaming data into a DataFrame is by what method?call readStream(). Using the read. stream() method in R. You can specify the specifics of the source, including the data format, schema, options, etc., in a manner similar to the read interface for creating static DataFrame.
Data output command: what is it?A data output command instructs the interface to transfer data from the bus into one of its registers in response. The data input command is the polar opposite of the data output command.
To know more about DataFrame visit:-
brainly.com/question/28190273
#SPJ4
Consider the following methods.
/* Precondition: a > 0 and b > 0 /
public static int methodOne(int a, int b)
{
int loopCount = 0;
for (int 1 = 0; 1 < a / b; i++)
{
loopCount++;
}
return loopCount:
}
/* Precondition: a > 0 and b > 0 /
public static int methodTwo(int a, int b)
{
int loopCount = 0;
int i = 0;
while (i < a)
{
loopCount++;
i += b;
}
return loopCount;
}
Which of the following best describes the condition sunder which methodOne and methodTwo return the same value??
A. when a and b are both even
B. when a and b are both odd
C. when a is even and b is odd
D. when a % b is equal to zero
E. when a % b is equal to one
Answers
Answer:
The correct answer is (D) when a % b is equal to zero.
Explanation:
In methodOne, the loop runs until i is less than a/b, incrementing the loop counter each time. This means that the loop runs a/b times.
In methodTwo, the loop runs until i is equal to or greater than a, incrementing the loop counter each time. At each iteration, i is increased by b. This means that the loop runs a/b times, the same number of times as in methodOne.
Therefore, the two methods will return the same value when they have run the same number of times, which occurs when the loop runs a/b times. This only occurs when a % b is equal to zero, which means that a is a multiple of b.
Of the following, if tatement, which one correctly execute three intruction if the condition i true? If (x < 0) a = b * 2; y = x; z = a – y; { if (x < 0) a = b * 2; y = x; z = a – y; } If{ (x < 0) a = b * 2; y = x; z = a – y ; } If (x < 0) { a = b * 2; y = x; z = a – y; }
Answers
Except for 1, all of the choices are accurate. If (x < 0) { a = b * 2; y = x; z = a – y; }.
What is an action to execute?Execute actions cover a wide range of options, such as grouping a subset of action, sending script commands, modifying database records, and setting variables to be used by subsequent actions.
What does the CPU "execute"?The CPU runs a program that is saved in main memory as a series of machine language instructions. It achieves this by continuously retrieving an instruction from memory, known as fetching it, and carrying it out, known as executing it.
To know more about execute visit:
https://brainly.com/question/14308171
#SPJ4
Paavo was reviewing a request by an executive for a new subnotebook computer. The executive said that he wanted USB OTG support and asked Paavo’s opinion regarding its security. What would Paavo tell him about USB OTG security
Answers
Answer:
Connecting a mobile device as a peripheral to an infected computer could allow malware to be sent to that device.
Explanation:
Since in the question it is mentioned that Paavo reviewed a request by an executive for subnotebook computer i.e new. but he needs to USB OTG support so it is a USB i.e on the go that links the devices from one device to another
Therefore by links the mobile device to the computer i.e infected that allows malware we called virus so that we are able to send it to that device. By this, he wants to tell about the USB OTG security
post the solve
Q.1 Write all the MATLAB command and show the results from the MATLAB program Solve the following systems of linear equations using matrices. 2y = 8z = 8 and -4x + 5y +9z = -9. x-2y+z=0,
Answers
The solution for the given system of linear equations is x= 3, y = -1, and z = 2.
As the given system of linear equations can be represented in matrix form as:
| 0 2 8 | | y | | 8 |
| -4 5 9 | x | y | = |-9 |
| 1 -2 1 | | z | | 0 |
MATLAB commands to solve the system of linear equations are:
1. Define the coefficient matrix and constant matrix:
>> A = [0 2 8; -4 5 9; 1 -2 1];
>> B = [8; -9; 0];
2. Solve for the variables using the command ‘\’ or ‘inv’:
>> X = A\B % using ‘\’ operator
X =
3.0000
-1.0000
2.0000
>> X = inv(A)*B % using ‘inv’ function
X =
3.0000
-1.0000
2.0000
Hence, the solution for the given system of linear equations is:
x = 3, y = -1, and z = 2.
Learn more about MATLAB: https://brainly.com/question/30641998
#SPJ11
Write the steps of applying background colour to the document?
Answers
Answer:
Select add color
Explanation:
depends the program u are using
What is the addressing system?
Answers
The addressing system is known to be one that is made up of hierarchical structure that establishes connections between addresses is an address system.
What is number addressing system?The numeric or IP address is made up of six numbers connected together, each of which is less than 256. IP addresses are constructed as four fields of eight bits each, separated by the use of a period.
Address ancestry in the levels of location addresses can be found using address systems.
Therefore, one can say that The addressing system is known to be one that is made up of hierarchical structure that establishes connections between addresses is an address system.
Learn more about addressing system from
https://brainly.com/question/1406940
#SPJ1
what are the uses of plotters
Answers
Answer:
Plotters are use to produce the hard copy of schematics and other similar applications They are mainly used for CAE applications.They can print on a wide variety of flat materialsHope it helps :)❤
Answer:
Plotters are used to print graphical output on paper. It interprets computer commands and makes line drawings on paper using multicolored automated pens. It is capable of producing graphs, drawings....
You are working to bring a healthcare facility into compliance with the Safety Data Sheet–related provisions of OSHA’s Hazard Communication Standard. You interview administrative personnel at the facility. You learn that the facility has compiled a list of all hazardous chemicals to which workers in the facility might be exposed. An SDS corresponding to each chemical on the list has been obtained and filed. For full compliance, you advise that this facility also must:
a. Verify the accuracy of all health hazard information contained in the SDS file
b. Ensure that the SDS file is readily available to all workers in their work areas, at all times
c. Review the SDS file, in order to compile a list of manufacturer emergency phone numbers
d. All of these are requirements under OSHA's HCS
e. None of these are requirements
Answers
Answer:
Option(b) is the correct answer to the given question .
Explanation:
By maintaining that the SDS file is easily accessible to all staff in their workplaces at any and all times. it gets the list of all dangerous substances that employees in the plant can be susceptible to has been collected also the SDS are obtained and filed that correlates to each chemicals in the list
All the others option are not correct way for the given question that's why these are incorrect option .Answer:
The answer is "Option b"
Explanation:
In OSHA Hazard digital natives, 29 CFR is the 1910.1200, section, which states the employer must retain copies of the datasheet.It provides data within workplaces with each toxic material and ensure the safety of the datasheet, which is easily available for employees.In various workplace areas throughout each change, that's why ensure all employees in their workplaces are always connected to the SDS register is the correct answer.How the evolution of the CPU has changed the computing environment of our present times?
Answers
Answer:
Explanation:
The evolution of the central processing unit (CPU) has had a profound impact on the computing environment of our present times. The CPU is the "brain" of the computer and has seen many improvements over the years, leading to significant changes in the computing environment. Some of these changes include:
Increased Processing Power: The increase in processing power has allowed computers to handle more complex tasks and applications. This has enabled the development of new technologies such as virtual reality, artificial intelligence, and big data analytics.
Improved Energy Efficiency: Modern CPUs are designed to consume less energy, which has allowed for the development of smaller and more portable computing devices, such as laptops and smartphones.
Increased Storage Capacity: The growth of data has necessitated an increase in storage capacity. CPUs have incorporated larger caches and improvements in memory management, which has allowed for the creation of more powerful computing systems.
Improved Graphics Processing: The integration of graphics processing units (GPUs) into CPUs has allowed for the development of more visually stunning applications and games.
Increased Connectivity: The advancement of the CPU has allowed for improved connectivity between devices and networks, enabling new forms of collaboration and communication, such as cloud computing and the Internet of Things (IoT).
Overall, the evolution of the CPU has brought about numerous changes in the computing environment, leading to a more powerful, efficient, and connected world. These advancements have created new opportunities for innovation, creativity, and productivity, and have greatly impacted many aspects of our daily lives.
which of the following protocols scales better within a cisco autonomous system?
Answers
In a Cisco autonomous system, the Interior Gateway Protocol (IGP) that scales better is the Open Shortest Path First (OSPF) protocol. OSPF is one of the most commonly used IGP protocols in large networks.
OSPF uses a link-state routing algorithm, which allows for fast convergence and provides loop-free network routing. OSPF also scales well because it can divide networks into smaller areas, which helps reduce the amount of routing information that needs to be exchanged within the network. OSPF scales better within a Cisco autonomous system because it can handle a large number of routers and networks.
OSPF is also highly flexible, as it can be configured to support multiple paths to a destination. This provides redundancy and increases network availability. OSPF is also capable of load balancing traffic over multiple paths to a destination. It can use a variety of metrics to determine the best path, including bandwidth, delay, cost, and others. OSPF is also highly configurable, as it can be tuned to optimize network performance.
Learn more about autonomous system: https://brainly.com/question/30240559
#SPJ11
According to a recent Experian survey of marketing
organizations, what percentage of organizations rely on ‘gut
feelings’ or ‘educated guesses’ to make business decisions based on
digital data
Answers
According to a recent Experian survey of marketing organizations, 42% of organizations rely on ‘gut feelings’ or ‘educated guesses’ to make business decisions based on digital data.In today's data-driven world, the role of data analytics and market research in decision-making is becoming increasingly important.
It is now common knowledge that data analytics can help businesses optimize their marketing campaigns and make better-informed decisions. Digital data can be leveraged to gain insights into customer behavior, preferences, and interests, and it can also be used to measure the effectiveness of marketing campaigns.However, despite the fact that many organizations have access to digital data and analytics tools, they are still not fully utilizing them to make informed business decisions. According to a recent Experian survey, 42% of organizations rely on "gut feelings" or "educated guesses" when making business decisions based on digital data. This is a worrying trend, as it means that businesses are not fully leveraging the power of data analytics to make data-driven decisions.
Moreover, the survey also found that only 39% of organizations regularly review their customer data to understand the needs and preferences of their customers. This suggests that many organizations are missing out on valuable insights that could help them to optimize their marketing campaigns and improve their customer experience.In conclusion, the Experian survey highlights the need for organizations to invest in data analytics and market research to make informed business decisions based on digital data. With the right tools and expertise, businesses can gain valuable insights into their customers' behavior and preferences, and use this information to optimize their marketing campaigns and improve their bottom line.
To know more about marketing organizations visit:
https://brainly.com/question/30096295
#SPJ11
Which of the following is not one of the top ten risks captured by Barry Boehm (the creator of the Spiral Model)
Group of answer choices
a. Software requirements and user needs never change
b. Personnel shortfalls
c. Unrealistic schedules and budgets
d. Shortfalls in externally furnished components
e. Developing the wrong software functions
f. Shortfalls in externally performed tasks
Answers
Among the given options, the answer isbSoftware requirements and user needs never change.Barry Boehm, the creator of the Spiral Model, identified the top ten risks in software development projects.
However, "Software requirements and user needs never change" is not one of the risks captured by Boehm. In fact, one of the fundamental principles in software development is that requirements and user needs are subject to change throughout the project lifecycle. This understanding led to the emergence of agile methodologies that emphasize flexibility and adaptability in response to evolving requirements. The other options, such as personnel shortfalls, unrealistic schedules and budgets, shortfalls in externally furnished components, developing the wrong software functions, and shortfalls in externally performed tasks, are among the risks highlighted by Boehm.
To learn more about requirements click on the link below:
brainly.com/question/18369405
#SPJ11
prim's and kruskal's algorithms to find the mst follows which of the algorithm paradigms? group of answer choices greedy approach brute force divide and conquer dynamic programming
Answers
Prim's and Kruskal's algorithms to find the MST follow which of the algorithm paradigms? The answer is the greedy approach. The Greedy Approach follows Prim's and Kruskal's algorithms to find the minimum spanning tree (MST). In Kruskal's algorithm, it selects the edges in ascending order of their weights.
The algorithm adds the edge only if it doesn't create a cycle. In Prim's algorithm, the algorithm starts with a vertex and adds edges with minimum weight to it. The algorithm keeps track of the vertices already visited. The algorithm continues until it visits all the vertices connected to the starting vertex.
Both Kruskal's algorithm and Prim's algorithm are greedy algorithms. The Greedy algorithms are the algorithms that make the most optimal choice at each step. They make the locally optimal choice in the hope that it will lead to globally optimal solutions.
To know more about Prim's algorithm visit:
https://brainly.com/question/32065965
#SPJ11
what is a program answer these question
of grade-6
Answers
a series of coded software instructions to control the operation of a computer or other machine.
Drag the tiles to the correct boxes to complete the pairs.
Match the effects with the result they have.
silky blur
grainy BMW effect
soft focus
zoom effect
blurs an image while maintaining sharp edges
simulates flow of water
shows motion lines around the main object
obtains a darker, textured finish
Answers
Done
Answer:
1 : blurs an image while maintaining sharp edges = soft focus
2: simulates flow of water = silky blur
3: shows motion lines around the main object = zoom effect
4: obtains a darker, textured finish = grainy B/W effect
Explanation:
