t/f, a distributed unit of work allows a single sql update statement to update data at more than one location.
Answers
The statement "a distributed unit of work allows a single SQL update statement to update data at more than one location" is true. A distributed unit of work refers to a system where multiple processes, possibly running on different computers or databases, collaborate to complete a single task.
In the context of SQL, a distributed unit of work enables a single SQL update statement to make changes to data stored in different locations, such as multiple databases or servers. This is accomplished through the use of distributed transactions, which coordinate the updates across all the involved systems to ensure data consistency and integrity.
Learn more about SQL update visit:
https://brainly.com/question/30624532
#SPJ11
Related Questions
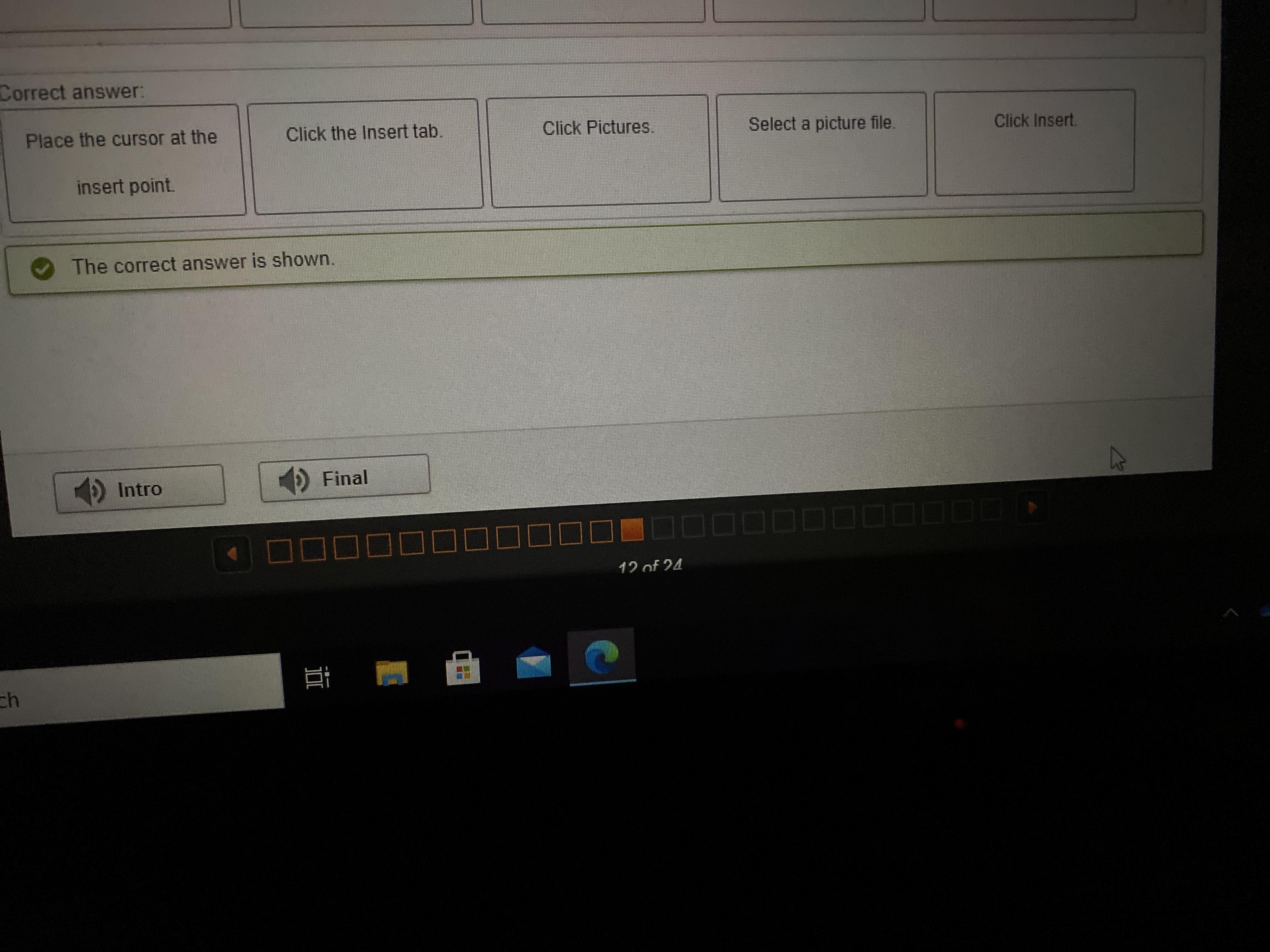
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
A computer configured to use DHCP cannot locate a DHCP server. Automatic Private IP Address (APIPA) will assign which of the following addresses? a) 172.16.1.25 b) 192.168.1.25 c)169.254.1.25 d)10.16.1.25
Answers
If a computer configured to use DHCP cannot locate a DHCP server, it will automatically assign an Automatic Private IP Address (APIPA).
An APIPA address falls within the range of 169.254.0.1 to 169.254.255.254. Therefore, the correct answer to the given question is option c) 169.254.1.25. It is important to note that an APIPA address is only used as a temporary solution until a DHCP server can be located and assigned a proper IP address. It is not recommended to rely on APIPA addresses for an extended period of time, as they can cause connectivity issues with other devices on the network.
To know more about DHCP visit:
https://brainly.com/question/8458316
#SPJ11
Apply following forecasting approaches for "Outstanding Debt Annual" spreadsheet and find the best method by comparing Mean Absolute Percentage Error (MAPE).
a) Naive Forecast
b) Moving Average (select a random k value)
c) Weighted Moving Average (select a random k value and random weights)
d) Exponential Smoothing Method with smoothing constant 0.3
e) Optimum Exponential Smoothing Constant Approach (Excel Solver must be used).
f) Linear Projection Method
g) Upper management also would like to know if MAPE is the best forecast accuracy measure or not. Pick one of the methods above and calculate Mean Square Error (MSE) for that method and then, compare the MAPE and MSE. Which forecast accuracy measure must be used?
Answers
The best method for forecasting "Outstanding Debt Annual" on the spreadsheet can be determined by comparing the Mean Absolute Percentage Error (MAPE) of different forecasting approaches. Here are the steps to find the best method:
1. Naive Forecast: Start by calculating the difference between each data point and the previous one. Take the average of these differences to get the Naive Forecast.
2. Moving Average: Choose a random value for k, which represents the number of periods to include in the average. Calculate the moving average by taking the sum of the previous k periods and dividing it by k.
3. Weighted Moving Average: Select random values for both k and the weights. Multiply each data point by its corresponding weight, sum the results, and divide by the sum of the weights.
4. Exponential Smoothing Method: Use a smoothing constant of 0.3 to calculate the forecast. Start with the first data point as the initial forecast and then update it using the formula: Forecast(t) = Forecast(t-1) + 0.3 * (Actual(t-1) - Forecast(t-1)).
5. Optimum Exponential Smoothing Constant Approach: Use Excel Solver to find the optimal smoothing constant that minimizes the MAPE.
6. Linear Projection Method: Fit a linear trendline to the data and use it to forecast future values.
To determine the best forecast accuracy measure, calculate the Mean Square Error (MSE) for one of the methods above. Then compare the MAPE and MSE. The forecast accuracy measure that should be used depends on the specific needs and preferences of upper management. If they prioritize the absolute percentage error, then MAPE is suitable. However, if they want to consider the magnitude of errors, MSE is more appropriate.
In conclusion, by comparing the MAPE of different forecasting approaches and calculating the MSE for one method, you can determine the best forecasting method for "Outstanding Debt Annual" on the spreadsheet. The choice between MAPE and MSE depends on the management's preference.
To learn more about debt, click here:
brainly.com/question/25035804
#SPJ11
Its made up of a small memory chips on a card that can hold data in an electronic format
Answers
The chip can allow you to have more data and more pictures so your phone does not become slow and messages and apps and more.
What are two common high-bandwidth fiber-optic media standards? (Choose two.)
SONET
SDH
ANSI
ATM
Answers
Two common high-bandwidth fiber-optic media standards are SONET and SDH.
SONET stands for Synchronous Optical Network and is a standard developed in North America, while SDH stands for Synchronous Digital Hierarchy and is the European equivalent.
Both standards were developed to provide a standardized way of transmitting large amounts of data over fiber-optic networks. SONET and SDH are similar in many ways and both use a synchronous transport mechanism, which means that they maintain a constant data rate. This makes them ideal for applications that require high bandwidth, such as video streaming and large file transfers. They also both use time-division multiplexing (TDM), which enables multiple signals to be transmitted simultaneously over the same fiber-optic cable.Despite their similarities, there are some differences between the two standards. For example, SONET has a slightly higher data rate than SDH and is used predominantly in North America, while SDH is more commonly used in Europe. Additionally, SONET uses optical carrier (OC) levels to indicate different data rates, while SDH uses synchronous transport module (STM) levels.In summary, SONET and SDH are two common high-bandwidth fiber-optic media standards that enable large amounts of data to be transmitted quickly and efficiently over fiber-optic networks.Know more about the fiber-optic media
https://brainly.com/question/29990631
#SPJ11
studocu implementation of a static environment (grid) using an array or other data structure that will represent the above grid. a function/method to determine what action to take. the decision should be based upon markov decision process. consideration of reward policy that incorporates the action costs in addition to any prizes or penalties that may be awarded. a function/method to calculate the optimal policy when a blocked state is encountered. a function/method to calculate the optimal policy when the fire state is encountered. a function/method to test if the desired goal is achieved or not.
Answers
The function will return true if the agent has successfully reached the fire state and false otherwise. The success of the agent's current policy will be tested by running multiple simulation trials.
Implementation of a static environment using an array or other data structure that will represent the grid: It's easy to use a two-dimensional integer array to represent the grid of cells. Consider using 0 to represent empty cells, 1 to represent cells containing obstacles, and 2 to represent cells containing fire. Consider the use of the following code to instantiate and populate the grid array in a new function named initialize_ environment(): int[][] grid = new int[5][5];grid[0] = new int[] {0, 1, 0, 0, 0};grid[1] = new int[] {0, 1, 1, 0, 0};grid[2] = new int[] {0, 0, 0, 0, 2};grid[3] = new int[] {0, 1, 1, 1, 1};grid[4] = new int[] {0, 0, 0, 0, 0};This creates a 5 by 5 grid with obstacles in the 2nd row and two obstacles in the 3rd column, with the goal represented by the fire at location (2,4). A function/method to determine what action to take:You can use the Markov Decision Process to determine what action to take based on the current state of the grid. The Q-learning algorithm is commonly used to make decisions based on Markov Decision Process. The function named get_next_action() should utilize the Q-learning algorithm to make the appropriate decision based on the state of the grid. A function/method to calculate the optimal policy when a blocked state is encountered:When the agent encounters a blocked state, the agent must be able to learn from its experience and adapt its decision-making process to avoid making the same error again. The optimal policy will be recalculated, taking into account the obstacles encountered during the previous attempt, using a function named update_policy_when_blocked(). A function/method to calculate the optimal policy when the fire state is encountered:When the agent encounters a fire state, the agent must be able to learn from its experience and adjust its decision-making process accordingly to avoid further risk of harm to the agent. The optimal policy will be recalculated, taking into account the obstacles encountered during the previous attempt, using a function named update_policy_when_fire(). A function/method to test if the desired goal is achieved or not:To test if the agent has accomplished its goal, use a function named test_goal().
Learn more about static
brainly.com/question/26609519
#SPJ11
what should you do if an online friend asked to meet you after school?
ᵖˡˢˢˢˢ...
Answers
Answer:
I'm going to agree if they had some decision when we meet to each other because I want to meet them in personal.
Explanation:
That's my own opinion
i am looking for some code to write 1,1,1 to 1,1,20 then switch to 1,2,1 to 1,2,20 all the way up to 20,20,20. any info would help alot thanks.
Answers
Answer:
press [Alt]+[F3] to open the create new building block dialog box. AutoText is listed in the Quick Parts dropdown, which is in the Text group on the insert tab.
it is not possible to nest boolean logical functions for a logical test in the logical_test argument of the if function in excel.
Answers
it is not possible to nest boolean logical functions for a logical test in the logical_test argument of the if function in excel.
This Statement is FALSE.
What is excel?Microsoft Excel is a spreadsheet developed by Microsoft for Windows, macOS, Android and iOS. It features calculation or computation capabilities, graphing tools, pivot tables, and a macro programming language called Visual Basic for Applications (VBA). Excel forms part of the Microsoft 365 suite of software.
Microsoft Excel has the basic features of all spreadsheets, using a grid of cells arranged in numbered rows and letter-named columns to organize data manipulations like arithmetic operations. It has a battery of supplied functions to answer statistical, engineering, and financial needs.
In addition, it can display data as line graphs, histograms and charts, and with a very limited three-dimensional graphical display. It allows sectioning of data to view its dependencies on various factors for different perspectives (using pivot tables and the scenario manager).
Learn more about Microsoft Excel
https://brainly.com/question/24202382
#SPJ4
Prompt
Explain three strategies you can use to take better notes.
Answers
Answer:
1. Use phrases not full sentences
2. Put your notes in categories
3. Take notes in your own words
Explanation:
It's right
When opening and closing a security container, complete the _____.
a. SF 701
b. SF 700
c. SF 702
d. SF 703
Answers
Option c is correct. SF 702 is the answer to this question. SF 702 is used to open and close security containers. Track security containers.
The security container can be opened and closed at any time. However, if possible, security containers should only be opened for privacy and security reasons. Security containers should use all possible safeguards such as guard protection, password protection, fingerprint protection, etc. Standard Form (SF 702) – Security Container Inspection Sheet. A standard form (SF 702 Security Container Sheet) tracks who opens, closes, and inspects security containers containing sensitive information.
SF 702 or "Security Container Check Sheet" is used to record the opening and closing of the data carrier. An area check is carried out in the SF 701 after the daily check is finished. The
SF 702 must be stored and disposed of according to a component records management program. SF 702 will be stored in the NDC until the next conformance inspection by a higher level control center.
Know more about information here:
https://brainly.com/question/29244533
#SPJ4
you have just downloaded a game onto your laptop. when you are not using the device, it unexpectedly downloads new content. which of these is the most likely cause of the issue
Answers
Answer:
deceptive software installed with the game.
Explanation:
Question 5: Which category best represents: a student has a friend who's
parent is a teacher at their school. The student uses his friend to obtain the
teachers username and password. Grades end up getting changed in the
digital grading system and it is soon discovered that the teacher also has the
same password in their family's online banking system.
A. illegal file sharing
B. software pirating
C. cyber bullying
D. identity theft
E. it's just not right or responsible.
Answers
Answer:
E
Explanation:
it's not right and it is also irresponsible and the teacher shouldn't have used that as her bank details and also that student's mother is Bankrupt by now
What is another name for a conditional statement?
a
an "if-then" statement
b
a "or-else" statement
c
an "either-or" statement
d
a "you-should" statement
Answers
Answer:
an "if-then" statement
Explanation:
2 Conditional Statement Another name for an IF-THEN statement is a CONDITIONAL STATEMENT. Every conditional has 2 parts. The part following the “IF” is called the HYPOTHESIS, and the part following the “then” is called the CONCLUSION.
Answer:
above me
Explanation:
stop looking
i said stop
so you want something don't you?
fine scroll down and I'll tell you something ;)
get rick rolled :)
"e"
How are the waterfall and agile methods of software development similar?
Answers
The waterfall and agile methods of software development are similar in that they both aim to develop software in an organized and efficient manner. However, they differ in the approach they take to achieve this goal.
The waterfall method is a linear, sequential method of software development. It follows a defined process with distinct phases, such as requirements gathering, design, implementation, testing, and maintenance. Each phase must be completed before the next phase can begin, and changes to the software are not allowed once a phase is completed.
On the other hand, Agile method is an iterative and incremental approach to software development. It emphasizes on flexibility, collaboration, and customer satisfaction. Agile method encourages regular inspection and adaptation, allowing for changes and improvements to be made throughout the development process. Agile methodologies, such as Scrum and Kanban, follow an incremental approach, where the software is developed in small chunks called iterations or sprints.
Both Waterfall and Agile approach have their own advantages and disadvantages and are suitable for different types of projects and teams. It is important to choose a method that aligns with the specific needs and goals of the project and the team.
To use the shortcut for inserting a row,_____
on the row number and choose Insert.
Right-click
Double-click
Shift-click
Click
Answers
The fundamental rule for testing functions requires that every function be tested in an already fully tested and debugged program. How can this be accomplished? a. Impossible! The main function must have all the functions it calls attached to get it to compile and run properly. b. The main function is tested with stub functions replacing each function. c. Write drivers for the stub functions to test them. d. Add each non-stub function in turn for testing. e. Write drivers for the function implementations one at a time to test them independently.
Answers
Option c, write drivers for the stub functions to test them, is the most appropriate answer.
How can this be accomplished?This approach is commonly known as unit testing and is a crucial step in ensuring that a program operates correctly. This involves creating a separate piece of code that calls and tests each function individually before integrating them into the main function. By doing so, any errors can be identified and resolved before they affect the overall functionality of the program. Once each function has been thoroughly tested, they can be integrated into the main function and tested as a whole to ensure the program operates as intended. This method is a fundamental rule for testing functions and helps to ensure that a program is fully tested and debugged before being released to users.
Using this method of testing functions is a fundamental rule for ensuring that a program is fully tested and debugged before it is released to users. It is important to note that the testing process should be ongoing and should continue throughout the development process to ensure that any changes made to the program do not introduce new errors or issues. By following these testing principles, developers can create software that is reliable, efficient, and meets the needs of its users.
To know more about test functions visit:
https://brainly.com/question/13384053
#SPJ11
Assume the int variables i ,lo , hi , and result have been declared and that lo and hi have been initialized.
Assume further that result has been initialized to the value 0.
Write a for loop that adds the integers from lo up through hi (inclusive), and stores the result in result.
Do not declare any additional variables --
use only i,lo,hi.
------------------------
import java.util.Scanner;
public class forloop_add{
public static void main(String args[]) {
int i,lo=1,hi=3,result=0;
Scanner scanner =new Scanner(System.in);
System.out.println("Enter the lower limit:");
lo=scanner.nextInt();
System.out.println("Enter the upper limit:");
hi=scanner.nextInt();
///{
//write your code here
//start
//end
///}
System.out.println("Result:"+result);
}
}
Answers
Answer:
I don't get this question, what is the point of initializing lo and hi if you're gonna read an input of both later, which is gonna override?
Explanation:
A camera detector has an array of 4096 by 2048 pixels and uses a colour depth of 16.
Calculate the size of an image taken by this camera; give your answer in MiB.
Answers
The size of an image taken by this camera is approximately 16 MiB.
How to calculate the size of an image?To calculate the size of the image taken by the camera, we need to know the total number of bits in the image.
The number of pixels in the image is:
4096 pixels × 2048 pixels = 8,388,608 pixels
The colour depth is 16, which means that each pixel can be represented by 16 bits. Therefore, the total number of bits in the image is:
8,388,608 pixels × 16 bits per pixel = 134,217,728 bits
To convert bits to mebibytes (MiB), we divide by 8 and then by 1,048,576:
134,217,728 bits ÷ 8 bits per byte ÷ 1,048,576 bytes per MiB = 16 MiB (rounded to two decimal places)
Learn more about cameras at:
https://brainly.com/question/26320121
#SPJ1
Required information The following information applies to the questions displayed below. John bought 1,000 shares of Intel stock on October 18, 2014, for $30 per share plus a $750 commission he paid to his broker. On December 12, 2017, he sells the shares for $42.50 per share. He also incurs a $1,000 fee for this transaction. a. What is John's adjusted basis in the 1,000 shares of Intel stock? Adjusted basis
Answers
John's adjusted basis in the 1,000 shares of Intel stock is $30,750.
To calculate John's adjusted basis in the 1,000 shares of Intel stock, we need to consider the initial purchase price, any commissions paid, and any transaction fees incurred. Here's the breakdown:
Purchase price of 1,000 shares of Intel stock: $30 per share
Total purchase price (excluding commission): $30 x 1,000 = $30,000
Commission paid to broker: $750
Adjusted basis (including commission): $30,000 + $750 = $30,750
When John sells the shares, the adjusted basis is used to calculate the capital gain or loss. If the selling price per share is greater than the adjusted basis, it results in a capital gain, and if it is less, it results in a capital loss.
Selling price of 1,000 shares of Intel stock: $42.50 per share
Total selling price: $42.50 x 1,000 = $42,500
Transaction fee: $1,000
Net proceeds from the sale: $42,500 - $1,000 = $41,500
To determine the capital gain or loss, we subtract the adjusted basis from the net proceeds:
Capital gain/loss: $41,500 - $30,750 = $10,750
In this case, since the selling price is higher than the adjusted basis, John has a capital gain of $10,750.
Learn more about Intel stock here:-
https://brainly.com/question/32518230
#SPJ11
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
to sum all the elements of a two-dimensional array, you can use a pair of nested if statements to add the contents of each element to the accumulator. question 93 options: true false
Answers
The sum of each element in the 2D array can be calculated by looping through the matrix and adding up the elements.
Reference elements are set to null, and the default values for members of numeric arrays are set to zero. Because a jagged array is an array of arrays, its elements are reference types and have null initialization. A n-element array's index ranges from 0 to n-1 and starts at zero. A type for a 2D array is one with two pairs of square brackets, like int[][] or String. Both the number of rows and the number of columns are specified using the new operator for 2D arrays. The components of a 2D array are arranged in rows and columns.
Learn more about array here-
https://brainly.com/question/19570024
#SPJ4
pLZ PLZ PLZ HELP I HAVE SO MANY MISSING ASSINMENTS. why is physical security so important and necessary for both personal users and businesses?
Answers
i. Suresh participated in a 100m race and won a prize. This motivated him to go for practice every morning. What type
of Motivation is this?
a) None of these
b) Internal
c) Intermediate
d) External
ii. Rekha gets up at 5 am and goes for her dance classes. Then she comes home and finishes her homework before going
to school. This an example of ________.
a) Self Motivation
b) None of these
c) Self Awareness
d) Self Regulation
iii. The file name and file name extension are separated by a ________.
a) semicolon
b) none of these
c) period
d) comma
Answers
2. D - Self Motivation
3. C - period, (word.doc)
At least 3 facts I learned about our Amazon Volunteer or their career experience:
Answers
Answer:
Amazon's Global Month of Volunteering includes hundreds of partners. Tens of thousands of employees around the world are coming together to support over 400 organizations in their local communities.
Which of the following numbers is of type
real?
(A)
-37
(B)
14.375
15
(D)
375
Answers
Answer:
all are real numbers
Explanation:
im a bit confused if there is only one answer, as real numbers are any numbers that can be shown on the number line, whether it be a decimal or negative.
At least that is what I remember
Describe a state space in which iterative deepening search performs much worse than
depth-first search (for example, O(n^2) vs. O(n)).
A state in which the iterative deepening search preforms worse than depth-first search would be one in which there is a single goal and each state has only 1 successor. This will make it so that the depth-first search will find the goal much quicker than the iterative deepening search.
Answers
Actually, the statement "a state in which the iterative deepening search performs worse than depth-first search would be one in which there is a single goal and each state has only 1 successor" is incorrect.
In fact, iterative deepening search is guaranteed to find the shallowest goal node in a tree, whereas depth-first search may not even find the shallowest goal node if it explores a deep branch before exploring a shallow one. Therefore, it is impossible for iterative deepening search to perform much worse than depth-first search in a state space where the goal is shallow.
However, there are state spaces in which iterative deepening search can perform much worse than depth-first search. For example, consider a state space where there are many paths to the goal state, but most of them are very long and only a few of them are short. In this case, depth-first search may find one of the short paths quickly, while iterative deepening search will explore many long paths before eventually finding a short one. This can result in iterative deepening search taking much longer than depth-first search, even though both algorithms eventually find the goal.
To know more about iterative click here:
brainly.com/question/6019026
#SPJ4
The data cache is where the data read from the database data files are stored _____ the data have been read or _____ the data are written to the database data files.
Answers
Data is known to have cache. The data cache is where the data read from the database data files are stored after the data have been read or before the data are written to the database data files.
Cached data are simply called too be the information that is saved on one's computer or mobile devices after a person have visited or accessed a website.
A lot of Developers often make use of cached data to boast their online experience. A considerable number of consumers often want a website to load within two and three seconds.
Learn more from
https://brainly.com/question/23708299
Pepsi or Coke B)
Or other
Answers
Answer:
Out of Pepsi or Coke, I gotta go with Coke, but in general any soda I would choose Orange Fanta.
Answer:
I prefer cream soda dr. pepper. But out of Pepsi and Coke, I'd choose Coke but I don't really like either.
Explanation:
Who invented the television and what year did color come out? Explain
Answers
The television was not invented by a single person, but its development involved contributions from several inventors and engineers.
How is this so?Philo Farnsworth is often credited as one of the key inventors of television, as he successfully demonstrated the first working electronic television system in 1927.
As for color television, it was first introduced commercially in the United States in 1953 by RCA.
The introduction of color television marked a significant milestone in broadcasting, enhancing the viewing experience for audiences worldwide.
Learn more about television at:
https://brainly.com/question/12079773
#SPJ1