t/f. provisioning is the process of allocating all of the capacity of a virtual disk at the time of creation. this increases the performance of a disk at the cost of storage space efficiency.
Answers
It is true, becasue provisioning is the process of allocating all of the capacity of a virtual disk at the time of creation. This means that the entire virtual disk is reserved for a specific application or purpose, which can increase the performance of the disk.
However, this also means that all of the storage space is being used up, which can reduce storage space efficiency. Provisioning is indeed the process of allocating all of the capacity of a virtual disk at the time of creation. This is known as eager zeroed thick provisioning in some virtualization platforms.
Allocating all capacity upfront increases the performance of a disk because the storage space is pre-zeroed and reserved, eliminating the need to zero out blocks and allocate space during normal operation. However, this comes at the cost of storage space efficiency, as the entire capacity is reserved even if it's not fully utilized.
To know more about virtual disk visit:
https://brainly.com/question/30225114
#SPJ11
Related Questions
Which of the constraints listed below would be considered a physical constraint
-Materials
-Demand for product
-Timeline
-Cost
Answers
materials are the only physical thing
PLEASE HURRY!!! Fill in the word to complete the sentence. A _____ is a line ignored by Python during execution. Here is an example: # ask the user for the date
Answers
Answer:
Writing Single-Line Comments is the answer
Explanation:
This line is ignored by the Python interpreter. The output of this program will be the same as in Example 1. The interpreter ignores all the text after # .
50 POINTS
in Java
A palindrome is a word, phrase, or sequence that reads the same backward as forward, e.g., madam or nurses run.
In this program, ask the user to input some text and print out whether or not that text is a palindrome.
Create the Boolean method isPalindrome which determines if a String is a palindrome, which means it is the same forwards and backwards. It should return a boolean of whether or not it was a palindrome.
Create the method reverse which reverses a String and returns a new reversed String to be checked by isPalindrome.
Both methods should have the signature shown in the starter code.
Sample output:
Type in your text:
madam
Your word is a palindrome!
OR
Type in your text:
hello
Not a palindrome :(
Answers
import java.util.Scanner;
public class JavaApplication52 {
public static String reverse(String word){
String newWord = "";
for (int i = (word.length()-1); i >= 0; i--){
newWord += word.charAt(i);
}
return newWord;
}
public static boolean isPalindrome(String word){
if (word.equals(reverse(word))){
return true;
}
else{
return false;
}
}
public static void main(String[] args) {
Scanner scan = new Scanner(System.in);
System.out.println("Type in your text:");
String text = scan.nextLine();
if (isPalindrome(text) == true){
System.out.println("Your word is a palindrome!");
}
else{
System.out.println("Not a palindrome :(");
}
}
}
I hope this works!
An example of documentary evidence that might be presented at trial for a cyber crime is:
A. None of these choices.
B. data retrieved from slack space on a hard drive.
C. a cellular telephone.
D. a photocopy of a hacker’s spreadsheet of telephone numbers and e-mail addresses.
Answers
An example of documentary evidence that might be presented at trial for cybercrime is a photocopy of a hacker’s spreadsheet of telephone numbers and e-mail addresses. Thus, option D is correct.
What is the evidence?
Evidence is really the data used to attempt to support anything in a court of justice. Evidence is gathered from people, artifacts, and records. The only means through which the court may draw conclusions and reach a ruling is via the use of evidence.
According to the definition of information, it is the demonstration of any claim to be true. A hard copy of a hacker's worksheet with contact information and e-mail accounts is an illustration of documented evidence that might be used in court to prove a cybercrime. Therefore, option D is the correct option.
Learn more about evidence, here:
https://brainly.com/question/14370298
#SPJ2
What symbol should you look for to determine who owns the intellectual property of a website? the logo the web address the domain suffix the copyright symbol.
Answers
Answer:
the answer is d
Explanation:
took the test
Answer:
d
Explanation:
edge2023
Betta is taking up the hobby of knitting. How can she use typing to help her learn how to knit faster?
Answers
Typing can help Betta learn how to knit faster by allowing her to quickly search for tutorials, knitting patterns, and knitting tips online. She can also use typing to look up knitting terminology, abbreviations, and symbols. Additionally, typing can be used to save notes, helpful knitting tips, and important information Betta finds while researching. Finally, typing can be used to keep track of projects, yarn amounts, and other details related to her knitting.
Answer:
She can search up tutorials on how to knit.
Explanation:
I got an 5/5 Quiz 1.02 k12

Aking sense of the death, the social consolidation after a death occurs, and caring for the dying are all functions of the: Multiple choice question. Sociology of death. Determinants of death. Death system. Psychology of death
Answers
The Death System is responsible for understanding the death, the social consolidation after a death occurs, and caring for the dying as it is the functions of the Death System.
The Death System comprises funeral homes, hospitals, cemeteries, crematoria, and various other entities that work to address the needs of the dying, the deceased, and the bereaved.A good understanding of the Death System is critical since it will help in comprehending the ways in which death and dying can affect various sectors of society.
The sociology of death is the study of the social structure, processes, and culture that surrounds death and dying. The determinants of death are the factors that cause or contribute to an individual's death. The psychology of death is the study of the psychological and emotional responses to death and dying.
To know more about responsible visit:
https://brainly.com/question/28903029
#SPJ11
an ad-hoc query is . group of answer choices a question that can be answered from the database using sql a question about the data that requires a program to be written never useful in business intelligence scenarios a question that can be answered only by combining several sql queries
Answers
A question that can be answered from the database using SQL
What is SQLSQL (Structured Query Language) is a standard language for accessing and manipulating data stored in relational database management systems. It is used for inserting, updating, deleting, and retrieving data from databases. SQL also allows users to create, modify, and drop database objects such as tables, views, stored procedures, and triggers. SQL is used to define the data in a database and to create relationships among the data. It also allows users to control access to the data and to specify constraints on the data. SQL is a powerful language that can be used to query, analyze, and manage data stored in a relational database. It provides a flexible and efficient way to interact with data in a database, allowing users to quickly and easily retrieve and manipulate data.
To know more about SQL
https://brainly.com/question/20264930
#SPJ4
An ad-hoc query is b.) a question that can be answered from the database using SQL.
What is an ad-hoc query?
An ad-hoc query is a request for information that is made in an unplanned, impromptu manner. In the context of data management and database systems, an ad-hoc query refers to a query or search for information that is not predefined or programmed into a system, but rather created on the fly to meet a specific need or purpose.
In other words, an ad-hoc query is a query that is written by a user to retrieve specific data from a database or other data source, rather than using pre-built queries or reports. Ad-hoc queries are typically used to answer a specific question or to investigate a particular issue or problem.
Ad-hoc queries can be written in a variety of ways, including through the use of SQL (Structured Query Language) statements or other query languages, as well as through the use of ad-hoc reporting tools or data visualization software. The ability to perform ad-hoc queries is an important feature of many business intelligence and data analytics tools, as it allows users to quickly and easily access the information they need to make informed decisions.
To learn more about ad-hoc query, visit: https://brainly.com/question/29642925
#SPJ4
Which field in the contacts form is used to control the order in which contacts are displayed in the current view.
Answers
Answer: File as
Explanation:
A contact form is simply refered to as a web based form which is usually short and then published on the website which can be filled out by people in order to pass a message across to the person who owns the site.
The field in the contacts form that is used to control the order in which the contacts are displayed in the current view is "File As".
T/F A hierarchical network topology in which each device is connected to a central node, either directly or through one or more other devices, is also called a tree network.
Answers
True, a hierarchical network topology in which each device is connected to a central node, either directly or through one or more other devices, is also called a "tree network." A tree network is a combination of star and bus topologies, and it provides a balance between scalability and control.
Following is the procedure:
1. In a tree network, the central node, also known as the root, serves as the main point of connection for the entire network. This central node may be a server, a switch, or a hub.
2. Devices are connected to the central node either directly, forming a star topology, or through other devices using a bus topology.
3. In a hierarchical structure, the devices are arranged in levels or layers, with the central node at the top level. Each level of devices is connected to the next level down, forming branches of the tree.
4. Tree networks allow for easy expansion, as new devices can be added to the branches without disrupting the existing connections.
5. The hierarchical structure also provides efficient data management, as data can be easily passed from one level to another, eventually reaching the central node.
In summary, it is true that a hierarchical network topology, where each device is connected to a central node either directly or through other devices, is called a tree network. This topology combines the benefits of star and bus topologies, offering a balanced approach to network organization and scalability.
Learn more about tree network here:
https://brainly.com/question/15302102
#SPJ11
Pls help xD. In pseudocode or python code please. Will mark best answer brainliest. Thx

Answers
Answer:
I'm doing my best to send you my answer,
Explanation:
The coding will be below
Tell me 2-6 computer parts that are inside a computer.
Spam answers will not be accepted.
Answers
Answer:
Memory: enables a computer to store, at least temporarily, data and programs.
Mass storage device: allows a computer to permanently retain large amounts of data. Common mass storage devices include solid state drives (SSDs) or disk drives and tape drives.
Input device: usually a keyboard and mouse, the input device is the conduit through which data and instructions enter a computer.
Output device: a display screen, printer, or other device that lets you see what the computer has accomplished.
Central processing unit (CPU): the heart of the computer, this is the component that actually executes instructions.
Explanation:
Hardware- The ______________ equipment that makes up the computer.
Answers
Answer:
It's like the stuff you can touch, the software is the stuff that runs in your computer
Explanation:
Hardware has those usb ports or whatever too (i think lol) good luck
Eva needs to hire someone that has in-depth knowledge of all of her network devices and can keep her network running efficiently. Which of the
following professionals does Eva need to hire?
A. a network architect
B.a network security analyst
C.a network analyst
D. a network administrator
Answers
Answer:
D. A network administrator.Explanation:
A network administrator is responsible for the day-to-day operations of a computer network, including installing, configuring, and maintaining network devices, such as servers, routers, switches, and firewalls. They are knowledgeable about the technical aspects of a network and can troubleshoot and resolve issues as they arise. They are also responsible for ensuring that the network is secure, and that data is backed up and protected. Therefore, a network administrator would be the best fit for Eva's needs, as they have in-depth knowledge of network devices and can keep her network running efficiently.While network architects design and plan computer networks, network security analysts focus on protecting networks from cyber threats, and network analysts analyze and optimize network performance, they may not have the same level of day-to-day operational knowledge as a network administrator.
who is he can anyone help me

Answers
pls solve the problem i will give brainliest. and i need it due today.

Answers
Answer:
1024
Explanation:
by the south of north degree angles the power of two by The wind pressure which is 24 mph equals 1024
What are the best editing apps?
Answers
Answer:
Snapseed, Lightroom, Adobe Photoshop, Prisma, Bazaart, Photofox, VSCO and PicsArt.
Explanation:
Snapseed, Lightroom, Adobe Photoshop, Prisma, Bazaart, Photofox, VSCO and PicsArt are the best editing apps. Some of the apps are present as free while some of them are not available without paying money for it. These are the top best editing apps so you can use it anyone of it. Snapseed is free on iOS and Android whereas Lightroom needs $5 per month for full access. Adobe Photoshop is also free on iOS and Android.
Answer:
After effects or alight motion on mobile are pretty good
Explanation:
which of the following imposes the requirement to grant users access only to data or resources they need to perform assigned work tasks.
Answers
The need-to-know principle imposes the requirement to grant users access only to data or resources they need to perform assigned work tasks.
What is need-to-know principle?According to the "need-to-know" principle, a user should only have access to the data that their job function requires, regardless of their level of security clearance or other approvals.
In other words, both a need-to-know and permissions are required of a user. And in order for the User to perform its current role, there must be a strict link between that Need-to-Know and a legitimate requirement.
As you might infer from the wording, the need-to-know principle is typically upheld in governmental or military settings.
Sometimes, in non-military scenarios, you will also find a slightly different description that states, in weaker terms, that access to data must be periodically reviewed to ensure that users only access data they strictly need for legitimate reasons.
Learn more about data access
https://brainly.com/question/28033296
#SPJ4
Java Question-5 Declare and initialize two variables called first and second. Write a single statement that will print the message "first is " followed by the value of first, and then space, followed by "second = ", followed by the value of the second. Ex: first is 55 second = 123
Answers
import java.util.Scanner;
public class HelloWorld {
public static void main(String[] args) {
Scanner reader = new Scanner(System.in);
System.out.print("Enter two number: ");
int number1 = reader.nextInt();
int number2 = reader.nextInt();
// println() prints the following line to the output screen
System.out.println("The first is " + number1+" and second= "+number2);
}
}
Old systems can be useful when designing new computer software.
True or False
Answers
True
Computers represent color by combining the sub-colors red, green, and blue (rgb). Each sub-color's value can range from 0 to 255. Thus (255, 0, 0) is bright red, (130, 0, 130) is a medium purple, (0, 0, 0) is black, (255, 255, 255) is white, and (40, 40, 40) is a dark gray. (130, 50, 130) is a faded purple, due to the (50, 50, 50) gray part. (In other words, equal amounts of red, green, blue yield gray).
Answers
Answer:
Follows are the code to this question:
#include <iostream>//defining a header file
using namespace std; //using namespace
int main() //defining main method
{
int red,green,blue,s; //defining integer variable
cout<<"Enter value: \n ";//print message
cin>>red>>green>>blue; //input value
if(red<green && red<blue)//defining if block that checks red value
s=red;//store red variable value to s variable
else if(green<blue)//defining else if block that checks green value less then blue
s=green;//store green variable value in s variable
else//defining else block
s=blue; //store blue variable value in s variable
//calculating red, green, blue value
red=red-s;//store red value
green=green-s;//store green value
blue=blue-s;//store blue value
cout<<red<<" "<<green<<" "<<blue;
}
Output:
Enter value:
130
50
130
80 0 80
Explanation:
In the above code, inside the Main method, four integer variable "red, green, blue, and s" is defined, in which "red, green, and blue" is used for input the value from the user end.
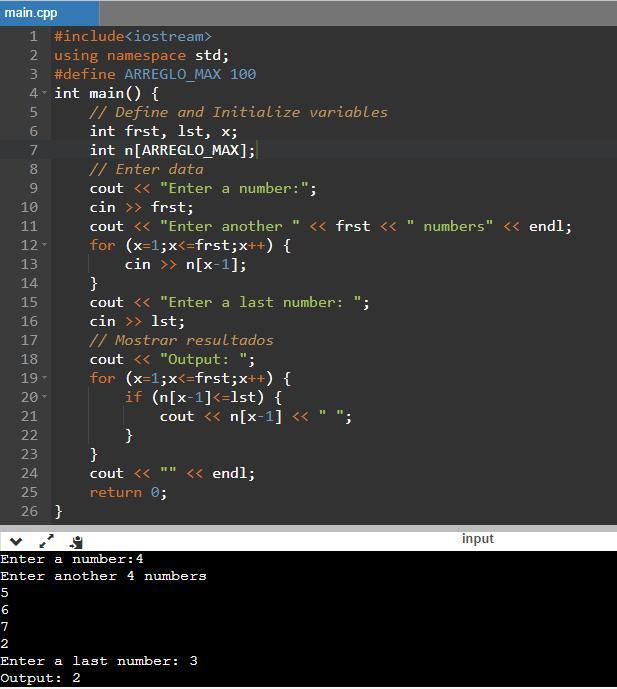
In the next step, a conditional statement is used, that checks the red variable value, if the condition is true, it will store its value in the "s" variable, otherwise, it will go to else if block.In this block, the green variable checks its value less than then blue variable value, if the condition is true, it will store the green value in the "s" variable, otherwise, it will goto else block.In this block, it will store the blue variable value in the "s" variable, and subtract the value of "red, green, and blue" value from "s" and store its value, and at the last, it will print its value.6.25 lab: output values below an amount - functions write a program that first gets a list of integers from input. the input begins with an integer indicating the number of integers that follow. then, get the last value from the input, and output all integers less than or equal to that value.
Answers
Program in C++ where the user creates a list of size indicated by the first element entered, then prints all numbers less than or equal to the last in the list.
Programs in C++ using list and arrays
#include<iostream>
using namespace std;
#define ARREGLO_MAX 100
int main() {
// Define and Initialize variablesint frst, lst, x;
int n[ARREGLO_MAX];
// Enter datacout << "Enter a number:";
cin >> frst;
cout << "Enter another " << frst << " numbers" << endl;
for (x=1;x<=frst;x++) {
cin >> n[x-1];
}
cout << "Enter a last number: ";
cin >> lst;
// Mostrar resultadoscout << "Output: ";
for (x=1;x<=frst;x++) {
if (n[x-1]<=lst) {
cout << n[x-1] << " ";
}
}
cout << "" << endl;
return 0;
}
To learn more about Programs in C++ using arrays see: https://brainly.com/question/15551918
#SPJ4
When you touch a warm picnic table , your hand becomes warmer. Explain how energy conservation applies to this situation
Answers
When you contact a warm picnic table, this transfer occurs because your hand has a lower surface temperature than the table, which allows the heat to pass from the table to your hand. You can see how this procedure conserves energy.
Why should we conserve energy?Energy conservation is essential for limiting climate change. It helps to replace non-renewable resources with renewable energy. When there are energy shortages, energy saving is frequently more cost-effective and environmentally friendly than increasing energy output.
What kind of energy is that?There are numerous shapes that energy can take. Examples of these energies include gravitational energy, mechanical energy, electrical energy, sound energy, chemical energy, nuclear or atomic energy, light energy, heat energy, and so on.
To know more about conserves energy visit:-
https://brainly.com/question/13949051
#SPJ1
which of the following is a constant time operation? question 5 options: finding the minimum value in an unsorted array finding the occurrence of a string in a sorted array finding the sum of two numbers input by the user concatenating two strings entered by the user
Answers
The operation that is a constant time operation from the given options is "concatenating two strings entered by the user". What is Constant Time Operation? An operation in computer science is said to be a constant time operation if the algorithm takes the same amount of time to execute irrespective of the size of the input. Here, from the given options, the operation that takes the same amount of time to execute irrespective of the size of the input is "concatenating two strings entered by the user".
Therefore, the correct option is: Concatenating two strings entered by the user.
#SPJ11
Learn more about constant time operation:
https://brainly.com/question/30186341
Drag the tiles to the correct boxes to complete the pairs.
Match the memory type with its function.
ROM
cache
RAM
hard drive
Functions
Memory Type
acts as a buffer between the CPU and main memory
arrowRight
contains data and instructions for current execution
arrowRight
stores data permanently
arrowRight
stores the program required to boot a computer
arrowRight
Next
Your welcome

Answers
Explanation :
which is not one of the four layers of a tcp stack? group of answer choices syn / ack packet physical network application
Answers
The term that is not one of the four layers of a TCP stack is "syn / ack packet." The four layers of a TCP stack are the application, transport, network, and physical layers.
The term that is not one of the four layers of a TCP stack is "syn/ack packet".
The four layers of a TCP stack are the physical layer, network layer, transport layer, and application layer.The physical layer deals with the actual transmission of data over a physical medium, while the network layer deals with routing and addressing of data packets. The transport layer manages the reliable delivery of data between applications, and the application layer deals with the specific protocols and processes that applications use to communicate with each other. The term "syn/ack packet" is actually a type of communication that occurs within the TCP protocol during the establishment of a connection, rather than being a layer in the stack itself. Thus, the term that is not one of the four layers of a TCP stack is "syn / ack packet." The four layers of a TCP stack are the application, transport, network, and physical layers.Know more about the TCP stack
https://brainly.com/question/17387945
#SPJ11
3.
Read the test again and write words which mean the following.
(a) The putting and keeping of things in a special place for use in the future
Answers
Answer:
File Or Folder I think it is
A web-based program that uses artificial intelligence techniques to automate tasks such as searches is called
Answers
A web-based program that uses artificial intelligence (AI) techniques to automate tasks such as web searches is called a: bot.
Artificial intelligence (AI) is also referred to as machine learning and it can be defined as a branch of computer science which involves the process of using computer algorithms to build a smart computer-controlled robot that is capable of automatically performing and handling tasks that are exclusively designed to be performed by humans or using human intelligence.
In the field of artificial intelligence (AI), a bot is an abbreviation for robot.
A bot is a web-based software program that assists an end user, or acts on his or her behalf, in the automatic performance of repetitive computer-related tasks such as web searches.
Read more: https://brainly.com/question/21656851
Eddie is working on a document that has only text. Which layout will he use to type the text? plato
Answers
Which file type is best for saving line art and animated images?
DOC
GIF
JPG
MP3
Answers
Hope this helps!!!
Answer:
GlF =Graphic interchange format is best for saving line art and animated images.
stay safe healthy and happy.