the infosec assessment methodology (iam) was developed by which of the following?
Answers
Answer:
It was made available commercially in 2001. NSA developed the IAM to give organizations that provide INFOSEC assessments a repeatable framework for conducting organizational types of assessments as well as provide assessment consumers appropriate information on what to look for in an assessment provider.
Related Questions
Explain what Tom should do in the following scenario, and why.
Situation: Tom is writing a program that will be used to store car descriptions for all cars in the dealership. He already has code for a public class name CarDetails.
Answers
Answer:
Tom should most definitely continue writing his program, and its good that he has a code for a public class name. Tom should keep going with the project and see what others think, if they approve then its truly ready. Because In order to write the rest of his program that he wants, he needs to continue what he's doing.
Explanation:
To answer the research question "How am I going to find the information I need on the tople?" the best thing Georgia should
do first is
get on her computer to search the topic
make a list of the books she could use.
ask her teacher for specific suggestions.
make a list of relevant sources to check out
Answers
Answer:
The correct option is D)
Explanation:
To get information about a research topic the first thing to do is make a list of relevant sources.
Georgias sources would depend on the type of research she has been asked to conduct.
If it's primary research, she would collect information from:
Her own experienceHer own observationthe Information she gathers personally from other peopleIf it is secondary research, she can look at
books (hard copy, e-copy)journals (online, offline)online (blogs, videos, websites etc)Whilst looking online, it is important to stick to authoritative sources as it is possible for anyone to publish anything online.
Examples of reliable sources are:
Journals from Industry AssociationsBureaus of StatisticsGlobal Research CompaniesHigher Institutions e.t.c.Cheers!
Answer:
D
Explanation:
Edge 2021
Which of these is NOT an example of application software?
1Points
A
An operating system
B
A word processor
C
An email platform
D
A video game
Answers
Answer:
A, an operating system.
The rest are applications that runs on an operating system.
a_______helps us to see the relationship between different parts of data
Answers
Answer:
Data label........
..
which of the following is an example of a method for managing whole ecosystems and habitats? a. species survival plans (ssps) b. captive breeding c. mapping biodiversity hotspots d. cloning
Answers
c. mapping biodiversity hotspots. Mapping biodiversity hotspots is an example of a method for managing whole ecosystems and habitats. Biodiversity hotspots are regions.
that contain a high number of endemic species and are under significant threat due to human activities. By identifying and mapping these hotspots, conservation efforts can be targeted to protect and manage the entire ecosystem within those regions.
Mapping biodiversity hotspots involves assessing various factors such as species richness, endemism, habitat loss, and threat levels. This information helps conservationists and policymakers prioritize areas for protection, restoration, and sustainable management. It allows for the implementation of strategies and initiatives to preserve entire ecosystems and habitats, rather than focusing solely on individual species or specific locations.
Learn more about hotspots here:
https://brainly.com/question/29762821
#SPJ11
What is a form of data cleaning and transformation?
Select one:
a. building pivot tables, crosstabs, charts, or graphs
b. Entering a good header for each field
c. deleting columns or adding calculations to an Excel spreadsheet
d. building VLOOKUP or XLOOKUP functions to bring in data from other worksheets
Answers
The form of data cleaning and transformation is option c. deleting columns or adding calculations to an Excel spreadsheet
What is a form of data cleaning and transformation?Information cleaning and change include different strategies to get ready crude information for examination or encourage handling. Erasing superfluous columns or including calculations to an Exceed expectations spreadsheet are common activities taken amid the information cleaning and change handle.
By expelling unessential or excess columns, you'll be able streamline the dataset and center on the important data. Including calculations permits you to infer modern factors or perform information changes to upgrade examination.
Learn more about data cleaning from
https://brainly.com/question/29376448
#SPJ1
What is a small file deposited on a hard drive by a website containing information about customers and their web activities?.
Answers
Answer:
Cookies.
Explanation:
It is a small text file that a website can place on your computer's hard drive to collect information about your activities on the site or to allow the site to remember information about you and your activities.
Write a program that takes a decimal number from the user and then prints the integer part and the decimal part separately. For example, if the user enters 2.718, the program prints: Integer part = 2 and decimal part = .718 in python
Answers
Answer:
Explanation:
The following was coded in Python as requested. It is a function that takes in a number as a parameter. It then uses the Python built-in math class as well as the modf() method to split the whole number and the decimal, these are saved in two variables called frac and whole. These variables are printed at the end of the program. The program has been tested and the output can be seen below.
import math
def seperateInt(number):
frac, whole = math.modf(number)
print("Whole number: " + str(math.floor(whole)))
print("Decimals number: " + str(frac))

Which range of cells represents the Lookup Table for finding which award each student received? Which lookup function would you use to fill C2:C7? What is your lookup value for student C?.
Answers
To find award of each student recieved we use VLOOKUP function.
What is VLOOKUP Function ?VLOOKUP stated as 'Vertical Lookup' is a simplest functional form that makes excel to search a certain value in the column ie. Table Array in order to return values from different columns in that same row.
We use VLOOKUP when we need to find values in table or a range by given row.
Learn more about VLOOKUP here :https://brainly.com/question/14042837
Answer: First one is A (E7:F12)
Second one is Vlookup
Third one is 6
Explanation:
Just did the class in Alt Ed, sorry im late
Which of the following statements are true about the Internet?
1 - The Internet connects devices and networks all over the world
II - The Internet helps people collaborate to solve problems
III - The Internet helps people communicate
IV - There are no negative consequences of the Internet, it is purely positive
Answers
What is computer task bar
Answers
Answer:
It is a bar where you can see all of your tasks or pinned items.
Explanation:
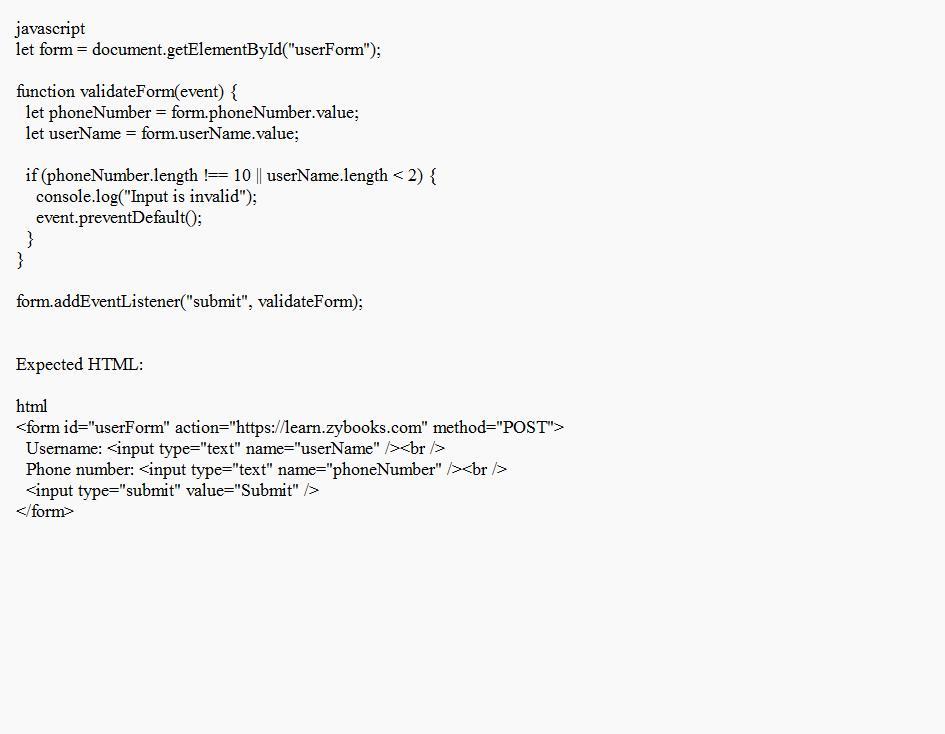
Update the validateForm() function to verify the phone number is exactly 10 characters long and the username is at least 2 characters long. Display "Input is invalid" in the console log if the phone number and username do not meet the requirements. Use the preventDefault() function to avoid submitting the form when the input is invalid. SHOW EXPECTED HTML JavaScript Ooo van WN 1 kform id="userForm" action="https://learn.zybooks.com" method="POST">
Username: 5 6
Phone number: 8 9
11 10 Update the validateForm() function to verify the phone number is exactly 10 characters long and the username is at least 2 characters long. Display "Input is invalid" in the console log if the phone number and username do not meet the requirements. Use the preventDefault() function to avoid submitting the form when the input is invalid. SHOW EXPECTED HTML JavaScript min 009 1 let form = document.getElementById("userForm"); 2 3 function validateForm(event) { let phoneNumber = form. phoneNumber.value; let userName = form.userName.value; \* Your solution goes here / 6 7 9} 10 11 form.addEventListener("submit", validateForm); 12Answers
The updated version of the validateForm() function that verifies the phone number and that is exactly 10 characters long and the username is at least 2 characters long is shown below.
What is the validateForm() function?By the use of the addEventListener() method, the submit event of the form is now linked to the validateForm() function in the updated code. Within the function, it obtains the inputted telephone number and user identification values.
Also, it verifies whether the phone number comprises precisely ten characters, and if the username contains a minimum of two characters. If the requirements are not fulfilled, the console displays the message "Input is invalid" and triggers the event.
Learn more about JavaScript from
https://brainly.com/question/16698901
#SPJ4
which of the following file names would comply with a Windows operating system? .Budget2014 Budget_Proposal? Budget_Proposal_2014 Budget_Proposal/2014
Answers
Answer:
A and C
Explanation:
Based on my computers saving process, A and C both worked while B and D didn't. I tried all four names on a PowerPoint Presentation and only A and C saved.
This is assuming I read your options correctly, I tried the following
.Budget2014
Budget_Proposal?
Budget_Proposal_2014
Budget_Proposal/2014
What is a good title for and about me project
Answers
Answer: MODERN TECHNOLOGY
Explanation: I don't know what your project is about, but I would assume since this is computer science that it is about technology.
Amazon.com purchases flat screen computer monitors from HP for $275.59 and sells them for $449.99. What is the amount of markup?
Answers
Answer: 82%
Explanation:
$ 449.99- $ 275.59= % 224.40
$ 224.40/ $ 275.59*100= 81.4253057078
Which of the following is a strategy used to enhance communication in a presentation?
A) using as few slides as possible by increasing the amount of information on each slide
B) using bullets to break up text and to highlight important talking points
C) using a large variety of backgrounds colors and slide transitions
D) using images to fill up unused space on each slide
Answers
A strategy which is used to enhance communication in a presentation is: B. using bullets to break up text and to highlight important talking points.
What is a presentation?A presentation refers to an act that involves the process of speaking to an audience, in order to formally explain an idea, subject matter, piece of work, topic, product, or project, especially through the use of multimedia resources or samples.
Generally, a strategy which can be used by a teacher or presenter to enhance communication in a presentation is by using bullets to break up text while highlighting important talking points.
Read more on presentation here: brainly.com/question/11827791
Roger is getting a $5,000 loan. Which option will allow Roger to pay off the loan and keep his payments under $100?
Answers
Explain the emerging trends in microcomputer technology in relation to size
Answers
Microcomputers, also known as personal computers, have come a long way since their inception in the 1970s. The emerging trends in microcomputer technology have been primarily focused on reducing the size of the devices while still maintaining their computing power. These trends have been driven by the need for portability, convenience, and efficiency.
One of the emerging trends in microcomputer technology is the development of smaller and thinner devices. Manufacturers are working towards creating devices that are not only portable but also lightweight.
This trend has been made possible by the advancements in miniaturization of computer components such as processors, storage devices, and batteries.
Another trend is the development of flexible and foldable displays that can be used in microcomputers. These displays are lightweight, thin, and durable, making them ideal for portable devices.
The use of flexible displays has allowed for the development of foldable laptops, tablets, and even smartphones. The emergence of Artificial Intelligence (AI) and Machine Learning (ML) has also had an impact on microcomputer technology.
Many microcomputers now come equipped with AI and ML capabilities, enabling them to process data faster and more efficiently.
This has led to the development of devices that can analyze and learn from data, which has many applications in industries such as healthcare, finance, and retail.
The trend towards reducing the size of microcomputers has also led to the development of wearable technology such as smartwatches and fitness trackers.
These devices are small, lightweight, and can be worn on the body, making them convenient for users who need to monitor their health or track their fitness.
In conclusion, the emerging trends in microcomputer technology are focused on reducing the size of devices while still maintaining their computing power. These trends are driven by the need for portability, convenience, and efficiency.
Manufacturers are working towards creating devices that are smaller, thinner, and more flexible. The use of AI and ML capabilities has also contributed to the development of more efficient devices.
The future of microcomputer technology is exciting, and we can expect to see even more advancements in the coming years.
For more questionon "Microcomputer Technology" :
https://brainly.com/question/30610552
#SPJ11
What is the ICD-10 code for a UTI?
Answers
0 Unknown location for urinary tract infection. If required, use extra codes (B95–B98) to identify the infectious agent.
What is ICD-10 and why is it important?This Organization for World Health (WHO) created ICD-10, its tenth revision of a International Disease Classification (ICD) (WHO). ICD is the world standard for reporting illnesses and medical problems and serves as the cornerstone for identifying health trends.
What is ICD-10 code example?An extension is used with a laceration code, as seen in ICD-10-CM code S31. 623A, Meniscal tear involving foreign entity of abdominal wall, layer neurons region with penetration into peritoneal, initial encounter. Take note that the complete code explanation is written out in ICD-10-CM.
To know more about ICD-10 visit:
brainly.com/question/14819864
#SPJ4
a possible attack on your combination-lock is a brute-force attack in which every possible input combination is tried. given the original design with a combination of three numbers between 0 and 15, how many possible input combinations exist? how about for the modified design with a combination of four numbers?
Answers
For the original design with a combination of three numbers between 0 and 15, there are 16 possible options for each number (0, 1, 2, 3, ..., 15). Therefore, there are a total of 16 x 16 x 16 = 4,096 possible input combinations.
For the modified design with a combination of four numbers between 0 and 15, there are also 16 possible options for each number. Therefore, there are a total of 16 x 16 x 16 x 16 = 65,536 possible input combinations.
Brute-force attack on the design
A brute-force attack on the original design would require trying all 4,096 possible input combinations, which could take a significant amount of time. However, a brute-force attack on the modified design would require trying all 65,536 possible input combinations, which would take even longer. Therefore, it's important to choose a strong combination lock with a design that makes brute-force attacks as difficult as possible.
To know more about Brute-force visit
https://brainly.com/question/28119068
#SPJ11
By placing you cursor over any value in a Pivot Table, it will display the: Cell format Cell information Cell address Defined Name
Answers
By placing your cursor over any value in a Pivot Table, it will display the cell information.
A pivot table is a table of statistics that summarizes the data of a more comprehensive table. It is used to categorize, sort, group, and summarize large amounts of data. It enables data in a spreadsheet to be compared, analyzed, and used to generate reports.
A Pivot Table has the following components:
Values: Numeric values that are summed, counted, or averaged.
Columns: Fields that are located in the horizontal area of the pivot table.
Rows: Fields that are placed in the vertical area of the pivot table.
Filters: Fields that are used to filter the data that are displayed in the pivot table.
Subtotals: Intermediate calculations performed for each field.
Cell Information is a feature in Excel that displays data about the cell you're looking at in a small box next to the cell. The cell information tool can show you the formula or format of the cell, as well as the cell reference, column, and row. When you hover over a value in a pivot table, Excel displays the cell information, which includes the underlying data and summary functions used in the pivot table.
Learn more about Pivot Table: https://brainly.com/question/29786921
#SPJ11
Plzz help me!!!! I don’t know the answer and I rlly need it FAST

Answers
Answer:
I think it's keyword explorer
Which of the following types of auditing requires access to source code?
Question options:
1. Use Case Testing
2. Code Review
In order for a subject to be _____, the system must first ____ the subject and then record the subject's actions.
Question options:
1. accountable, identify
2. accountable, authorize
Answers
The correct options are 2 for both the cases i.e., Code Review is the type of auditing requires access to source code and in the second question, for subject to be accountable the system must first be authorized.
What is a system in computer terms?A computer system is made up of carefully chosen hardware components that work well with the software components or programs that operate on the computer. The main element of software is the operating system, which oversees and provides services for other computer programs.
What function does system software serve?The computer itself is managed by system software. It functions in the background to maintain the computer's core functions so that users can access higher-level application software to perform particular tasks. In essence, system software provides a framework for using application software.
To know more about system visit-
brainly.com/question/14583494
#SPJ4
what type of open source programming language is python
Answers
Answer:
Python is developed under an OSI-approved open source license, making it freely usable and distributable, even for commercial use. Python's license is administered by the Python Software Foundation.
Explanation:
g00gle
_____ advice executes regardless of the means by which a join point exits (normal or exceptional return).
Answers
After advice executes regardless of the means by which a join point exits (normal or exceptional return).
What type of advice gets executes by join point exits?"After advice" executes regardless of the means by which a join point exits (normal or exceptional return). This means that after advice will run regardless of whether the join point completes successfully or encounters an error. It is useful for performing actions that should always take place, such as logging or resource cleanup.
Therefore, the "after" advice is designed to run after the join point completes its execution, ensuring that it runs no matter the outcome of the join point's execution.
To know more about After advice
visit:
https://brainly.com/question/31816650
#SPJ11
software programs that work without direct human intervention to carry out specific tasks for individual users, business processes, or software applications, are called
Answers
Intelligent agents are software programs that operate without direct human input to complete specified tasks for individual users, corporate processes, or software applications.
A software package includes a number of computer programs as well as related documentation and data. In contrast, hardware is what the system is made of and what actually does the work.
Executable code, which is the most basic form of programming, is made up of machine language instructions that are supported by a single processor, most often a central processing unit (CPU) or a graphics processing unit (GPU). Machine language is made up of collections of binary values that represent instructions for the processor to change the state of the computer from its previous state. An instruction, for instance, might have an effect that the user cannot see directly, such as altering the value kept in a particular storage place in the computer. Another option for instruction is to use one of the various input or output operations.
Learn more about software here:
https://brainly.com/question/2919814
#SPJ4
why womt this code work????
Answers
Answer: There is no code to look at.
Explanation:
Please comment your code.
What is the best definition of a database?
O a well-structured organization of data
O an email application that also sorts data
O a presentation software that handles data
O a task manager that provides storage for data
Answers
Answer: The answer is A
a well-structured organization of data
Explanation: i just took it :)
The carbon-14 isotope is important because it allows scientists to determine the ___________ of an organic sample.
Answers
Answer:
radiocarbon dating and radiolabeling, to detect specific bacteria
Explanation:
from google: Carbon-14, which is radioactive, is the isotope used in radiocarbon dating and radiolabeling. … medically important radioactive isotope is carbon-14, which is used in a breath test to detect the ulcer-causing bacteria Heliobacter pylori.
A__ is a part of a GUI that allows a specific type of interaction with the user.
O application
O
event
O subroutine
O widget
Answers
The part of a graphic user interface (GUI) that allows a specific type of interaction with an end user is: D. widget.
What is a widget?A widget is sometimes referred to as a gadget and it can be defined as a software application that is designed and developed as a part (element) of a graphic user interface (GUI) to display specific information or provide an end user with a specific way to interact with the computer's operating system (OS) or program.
The examples of a widget.In Computer science, there are different types of widget and these include the following:
Search box widgetsClock widgetsWeather widgetsCalculator widgetsStock market widgetsIn conclusion, the part of a graphic user interface (GUI) that allows a specific type of interaction with an end user is a widget.
Read more on widget here: https://brainly.com/question/7498108
Answer:
widget
Explanation:
got it right on edge