the process in which new visual information constantly replaces old visual information in the sensory registers almost immediately, is called . group of answer choices b. masking c. the recency effect a. circumlocation d. chunking
Answers
The recency effect describes the mechanism by which fresh visual information quickly and continuously replaces old visual data within sensory registers.
What does the term "sensory" mean?Something related to feeling, or something you can physically feel, is described by the term sensory. You may have a sensory experience by inserting a knife into the a toaster, but you can also smell roses.
What kind of thing is sensory?Examples such sensory interaction include (1) savoring food with both taste and smell, (2) avoiding a road because a heavy car is visually approaching and blasting its horn, or (3) assembling a model boat using sight and touch.
To know more about Sensory visit:
https://brainly.com/question/9173579
#SPJ4
Related Questions
A screen on Evelyn's cell phone can hold an odd or an even number of apps. If she has an odd number of apps, how can she arrange them on 2 screens?
Answers
To arrange an odd number of apps on two screens, Evelyn can put (N-1)/2 apps on one screen and 1 app on the other.
When Evelyn has an odd number of apps on her cell phone, she may encounter a challenge when trying to arrange them on two screens evenly. However, with a little creativity and strategic placement, she can find a solution.
Let's assume Evelyn has N apps, where N is an odd number. She can begin by placing (N-1)/2 apps on one screen. This screen will hold the majority of the apps, as it can accommodate an even number of them. Now, Evelyn is left with one app to place.
To address this, she can choose one of the apps from the first screen and move it to the second screen, making it uneven. This action leaves her with (N-1)/2 - 1 apps on the first screen and 1 app on the second screen. While this setup is not perfectly even, it ensures that all the apps are accounted for on both screens.
Alternatively, if Evelyn desires a more balanced arrangement, she can distribute the apps differently. She can place (N+1)/2 apps on one screen and (N-1)/2 apps on the second screen. This configuration ensures that the number of apps on each screen differs by only one.
In either case, Evelyn can prioritize her most frequently used or essential apps on the first screen, making them easily accessible. The second screen can hold less frequently used or secondary apps.
By employing these strategies, Evelyn can overcome the challenge of arranging an odd number of apps on two screens, allowing for efficient organization and easy access to all her applications.
Learn more about Odd Apps
brainly.com/question/32284707
#SPJ11
Why we need to learn ict?
Answers
Answer:
Explanation: ICT stands for information and communication technology . As we know we are living in a world which is digital and with the passage of time it is going to get more digitalized , so there is demand of people who have computational skills.
we need to learn ICT cause it helps us to be smart .ICT helps in achieving a good knowledge of technology and make us future and job ready .
ICT tools help to get our education system digitalized and help to build an interactive environment for students
Which file format is most often used with the CMYK color model and allows the image to be increased or decreased in size with minimal loss in quality?
GIF
PNG
TIFF
JPEG
Answers
The file format that is most often used with the CMYK color model and allows the image to be increased or decreased in size with minimal loss in quality is option C: TIFF.
What is the purpose of a TIF file?Computer files called TIFFs, which stand for Tag Image File Format, are used to store raster graphics and image data. If you want to avoid lossy file formats, TIFFs, which are a favorite among photographers, are a useful option to keep high-quality photographs before editing.
Hence, With a high color depth of up to 32 bits per color component, the format supports both the RGB and CMYK color models. Transparencies, masks, and layers can also be stored. You may copy or save data without sacrificing quality thanks to lossless compression.
Learn more about file format from
https://brainly.com/question/24102638
#SPJ1
Similarities between Off-site and On-site
Answers
Answer:
As adjectives the difference between onsite and offsite
is that onsite is on or at a site while offsite is away from a main location; in a place not owned by a particular organisation.
Make a list of eleectric motors in your home
Answers
The list of electric motors in my home are:
The motor of the fan and that of microwave oven. The motor of the blender and the refrigerator .Which motors are used in homes?The common used one is known to be the Single-phase induction motors and they are known to be used in household applications based on the fact that they have a robust and simple kind of construction and they are known to be capable for being attached straight to the single-phase grid without the use of power converters.
Hence, The list of electric motors in my home are:
The motor of the fan and that of microwave oven. The motor of the blender and the refrigerator .Learn more about electric motors from
https://brainly.com/question/7645396
#SPJ1
3. Choose the statement that best describes a ray. A ray extends forever in both directions. B ray is a part of a line with two endpoints. C ray is an exact location. D ray has one endpoint and continues forever in the opposite direction.
Answers
Answer:
Ray is part of a line that starts at one point and extends forever in one direction.
Explanation:
In geometry, a ray can be defined as a part of a line that has a fixed starting point but no end-point. It can extend infinitely in one direction. On its way to infinity, a ray may pass through more than one point. The vertex of the angles is the starting point of the rays.
Extra
B. A part of a line with two endpoints?
line segment
A line segment has two endpoints. It contains these endpoints and all the points of the line between them. You can measure the length of a segment, but not of a line. A segment is named by its two endpoints, for example, ¯AB.
Answer:
Ray is part of a line that starts at one point and extends forever in one direction.
Explanation:
As heard in the cell phone history video case, who was the inventor of the cell phone that said for the first time, you were calling a person, not a place?.
Answers
Martin Cooper, a Motorola engineer who invented the handheld cellular phone, made the first-ever mobile phone call to make a fuss about his accomplishment.
What is a cell phone?A cellular phone is a type of telecommunications device that uses radio waves to communicate over a networked area (cells) and is served by a cell site or base station at a fixed location, allowing calls to be transmitted wirelessly over a long distance, to a fixed landline, or via the Internet.
Motorola engineer Martin Cooper created the first hand-held phone that could connect via Bell's AMPS. In 1984, Motorola introduced the DynaTAC.
It weighed more than a kilogram and was nicknamed "The Brick," but it quickly became a must-have accessory for wealthy financiers and entrepreneurs.
Thus, Martin Cooper is the one who was the inventor of the cell phone that said for the first time, you were calling a person, not a place.
For more details regarding cell phone, visit:
https://brainly.com/question/14272752
#SPJ1
Question 2: Did every packet arrive in the correct order? Describe what went wrong and whether your partner was able to read the message. If neither you nor your partner had an issue try sending another message.
Answers
Answer:
No, the packets did not arrive in the right order but the TCP protocol reordered the packets. The transmission took a while, but the message was finally delivered.
Explanation:
Packets are chunks of data from a data source or message transmitted from one computer device to another. Protocols like TCP or transmission control protocol and UDP (user datagram protocol) are used for data transfer, with TCP as the more reliable protocol (it checks for errors, retransmit lost packets, and reorders received packets in the destination device) and slow protocol.
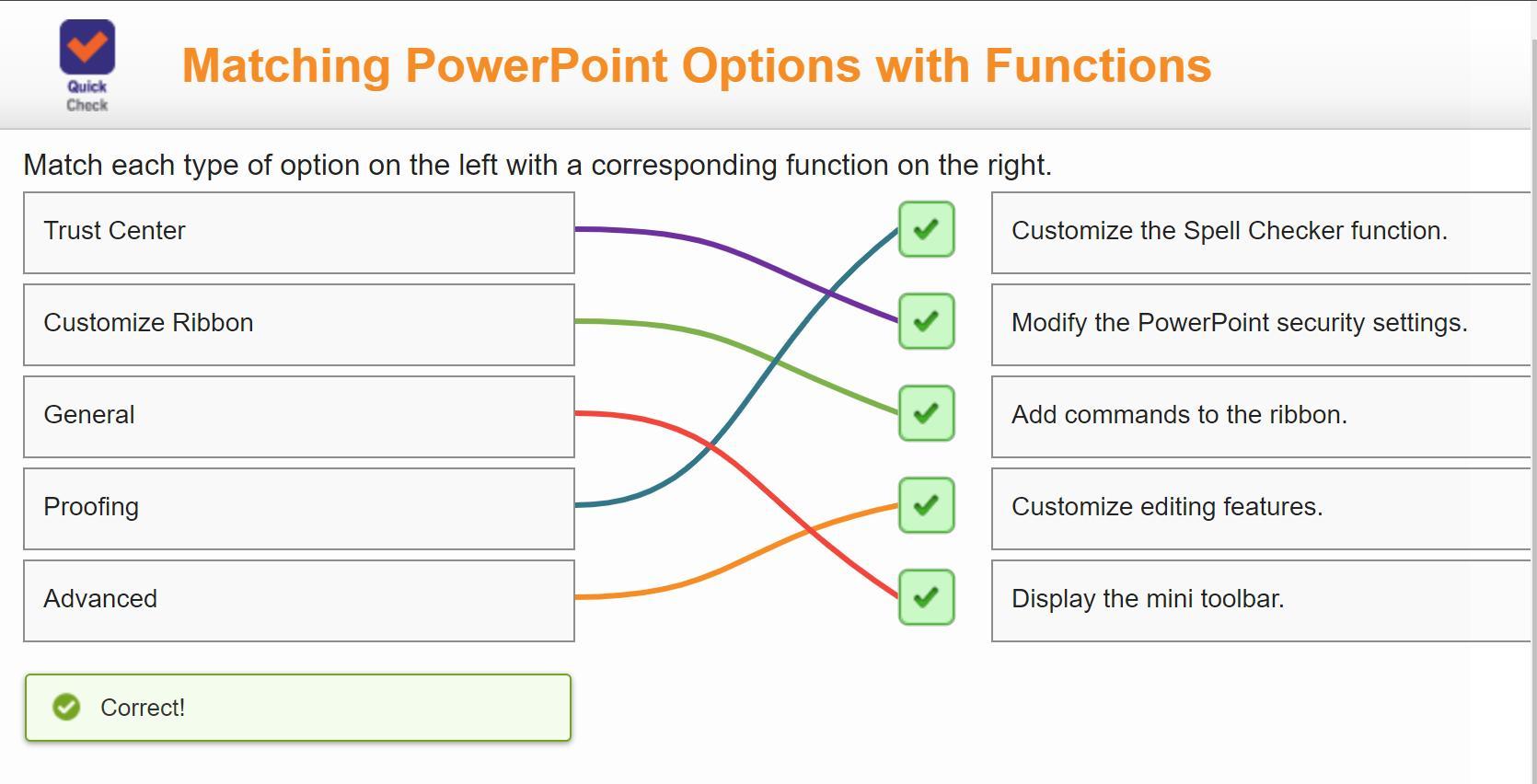
Match each type of option on the left with a corresponding function on the right.
Answers
Answer:
yes. the above is correct
Explanation: q posted
Answer: Anwer is correctly shown!!!!!!!!
Explanation:
HOPE IT HELPS Y'ALL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!

(03.02 LC)
How is customer service defined? (6 points)
A.
Aid provided to the elderly by neighbors
B.
Assistance provided by a company to people who buy or use its products or services
C.
Help given to students by classmates
D.
Support given to employees by managers and supervisors
Answers
Answer:
B.
Assistance provided by a company to people who buy or use its products or services
B.
Assistance provided by a company to people who buy or use its products or services
What statement best describes entrepreneurship?
Answers
Answer: D
Explanation:
Answer
Option: It requires creativity and ambition.
Hope this helps, have a wonderful day/night, stay safe, happy holidays, and merry Christmas!
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
the difficulty some units face adapting their mindset to vastly changed conditions on their third or fourth deployment to the same location is known as
Answers
Rotation problems are when some units have trouble changing their mentality to significantly different circumstances after their third or fourth deployment to the same region.
Is there a cross-agency staff group that promotes or fosters timely, collaborative working on a regular basis?An interagency staff group called the joint interagency coordination group (JIACG) helps civilian and military operations planners develop consistent, timely, and cooperative working relationships.
What fundamental tenets govern inter professional and interagency collaboration?These components include accountability, assertiveness, coordination, communication, cooperation, mutual trust, and respect. Students will be able to interact with one other, share experiences, and put these qualities into practice through a successful inter professional program.
To know more about Rotation visit:-
brainly.com/question/15085157
#SPJ4
question-
The difficulty some units face adapting their mindset to vastly changed conditions on their third or fourth deployment to the same location is known as _____ challenges.
recall that book ciphers do not necessarily require a full book to decode, but instead any written text, such as the declaration of independence. for the example discussed in class (the second beale cipher), we created the key by numbering words and taking the first letter. but we can also number characters themselves instead, making sure to skip spaces. the following is a message encrypted with a book cipher, using the text of this question as a key. what is the hidden message?
Answers
To decode this book cipher, we need to number each character in the text of this question. We should skip spaces while doing so. Once we have numbered all the characters.
we can match them with the numbers in the message to find the hidden message. Unfortunately, as the message has not been provided, we cannot determine the hidden message. However, it is important to note that book ciphers can be created using any written text as a key, including books, articles, and even social media posts. They can be difficult to crack if the key text is unknown, making them a popular choice for secret communication. A transposition cypher is a sort of encryption in which the letters of a message are shuffled or rearranged in accordance with a predetermined pattern or key, but the actual letters remain the same. This encryption technique aims book cipher to shuffle the original message's order, making it challenging for unauthorised parties to read or decode it. In conclusion, the transposition cypher is a method that involves rearrangement of letters in a message without changing the actual letters. Messages are encrypted using this technique, which increases their security and makes it more difficult for third parties to read them.
Learn more about book cipher here
https://brainly.com/question/31718003
#SPJ11
What was the biggest challenge you faced in getting to where you are today and how did you overcome it? Peer counseling
Answers
When stacking, interlocking rows should be used to minimize the risk of any becoming destabilized and falling.a. Trueb. False
Answers
The assertion is accurate. This is due to the fact that interlocking rows should always be used when stacking objects to reduce the possibility of any dropping and becoming unstable.
What must be kept secure by being piled in interlocking rows?Workers should do the following when stacking bags, sacks, and baled and bundled materials: To keep items safe, stack bags and bundles in rows that interlock one another.
What safety precautions apply to stacking?Use work gloves and boots when handling items, especially if there are sharp edges or heavier loads. Stack materials only in designated places. Never go close to doors, entry points, or fire escape routes. Place in packing and stack on a level surface.
To know more about stacking visit:-
brainly.com/question/14257345
#SPJ1
As part of a summer internship at UMD you are working on improving the ELMS website. You want to see if the new ELMS website with your modifications is effective. To do so, you track student engagement with a score that can range from 0 to 100 for a group 32 students who have agreed to participate in your study. You want to control for order by having half of the students interact with the old ELMS website first and then with the new one; the other half students do it in reverse order. You want to determine if engagement scores differ between the old and new ELMS website. Which of the following would you use as the appropriate hypothesis test? a. paired t-test b. chi-squared test c. two sample t-test d. two sample z-test ewe haven't covered the appropriate method for this test yet
Answers
The appropriate hypothesis test for determining if engagement scores differ between the old and new ELMS website is the paired t-test.
Which hypothesis test is suitable for comparing engagement scores between the old and new ELMS website?The appropriate hypothesis test in this scenario is the paired t-test. The study aims to compare the engagement scores of a group of 32 students who interact with both the old and new ELMS website, with half of them starting with the old website and the other half starting with the new website.
The paired t-test is suitable when analyzing dependent samples, where each participant is measured under two different conditions or treatments. In this case, the students' engagement scores are paired because they are measured before and after interacting with different versions of the ELMS website.
By using the paired t-test, the researchers can assess whether there is a significant difference in engagement scores within each participant, taking into account the order in which they interacted with the websites. This test allows for controlling the potential variability between individuals, as each participant serves as their own control.
Hypothesis testing, specifically the paired t-test, which is commonly used in research studies involving dependent samples. Understanding the appropriate statistical tests helps in drawing accurate conclusions and making informed decisions based on the data.
Learn more about hypothesis test
brainly.com/question/17099835
#SPJ11
what are the five elements of video production
sight, color, emotion, sound, motion
or
light, dark, air, greenery, location
??
Answers
the person or user associated in computer field is called
Answers
Explanation:
A computer programmer, sometimes called a software developer, a programmer or more recently a coder (especially in more informal contexts), is a person who creates computer software.
Answer:
computer technision because it's the person who fixes and maintenance of the computer and makes sure everything is running ok with it and has no bugs or viruses or spam.
What is the name of the character set created to allow
computers to represent other languages?
Answers
Answer:
UTF-8, which stands for Unicode Transformation Format – 8-bit.
Answer: ASCII
Explanation:
The ASCII character set is a 7-bit set of codes that allows 128 different characters.
If you found my answer useful then please mark me brainliest.
what is pirating means in technical terms?
Answers
Answer:
the illegal copying, distribution or use of software
Pirating refers to the unauthorized copying, distribution, or use of copyrighted material, such as software, music, movies, or books, without the permission of the copyright holder.
Here,
In technical terms pirating refers to the unauthorized copying, distribution, or use of copyrighted material.
This can include activities such as downloading or sharing copyrighted content without paying for it or using cracks to bypass licensing or copy protection mechanisms.
Pirating is considered illegal and unethical because it infringes upon the rights of the copyright holder and can result in legal consequences.
Know more about pirating,
https://brainly.com/question/29769277
#SPJ6
The keys to content marketing include
content that is shared sporadically.
content that is relevant to the target audience.
content that tries to reach everyone on social media.
content that includes coupons and discount offers.
Answers
The keys to content marketing are crucial for any business to succeed in the digital world. One of the most important aspects of content marketing is creating content that is relevant to the target audience. This means that businesses need to have a deep understanding of their customers and create content that resonates with them.
Another important factor in content marketing is creating content that is shared sporadically. This means that businesses should not flood their audience with too much content at once.
Instead, they should focus on creating high-quality content that is shareable and resonates with their audience. It is also important to note that businesses should not try to reach everyone on social media. This is because not everyone will be interested in their content.
Instead, businesses should focus on targeting their content to their specific audience to get the most engagement and results. Lastly, including coupons and discount offers in content can be an effective way to attract new customers and retain existing ones.
However, businesses should be careful not to rely too heavily on this strategy and ensure that their content is still relevant and valuable to their audience.
In summary, the keys to successful content marketing include creating content that is relevant to the target audience, shared sporadically, targeted to a specific audience, and includes value-additions like coupons and discount offers.
By following these strategies, businesses can create engaging and effective content that resonates with their audience and drives business results.
For more question on "Content Marketing" :
https://brainly.com/question/29991952
#SPJ11
Which is the best method for sending a word-processor document to another
person via e-mail?
Answers
Answer:
Attach the document to the e-mail message as a file attachment.
Hope this helps :)
What would happen if you fake a credit card number online on a website.
My 13 year old friend did that months ago and now he got a message saying his “chase account was locked due to suspicious activities”
I’m only asking because he’s freaking out
Answers
Which Data Storage Essentials solution should you recommend to a customer that needs simultaneous read and write access across two locations?
Answers
Multiple users Storage can simultaneously read and write to the same files using a distributed file system, which is accessible from multiple places. Customers who need to share data between many sites will find it to be the perfect solution as a result.
A distributed file system is a form of file system that offers simultaneous read and write access to the same files across several locations. Customers who need to share data between many sites will find it to be the perfect solution as a result. The widely used distributed file systems include Ceph, GlusterFS, and HDFS. Users may access their data anywhere, at any time, because to the highly available, dependable, and secure storage that these file systems are built to offer. When several places need simultaneous access to the same files, this is extremely helpful. Users can access the same data from anywhere using a distributed file system, regardless of where they are. This makes it possible to provide equal access for all users.
Learn more about data here-
brainly.com/question/11941925
#SPJ4
Which of the following programming languages were initially developed to teach programming techniques to students? Choose all that apply.
Answers
Answer:
BASIC programming language
Pascal programming language
Explanation:
C++ programming language
Java programming language
BASIC programming language
Pascal programming language
Answer:
it's C and D
Explanation:
What is the difference between the two worlds of video games identified in the video as Core video games and casual video game?
Answers
Answer:
Core videogames are more explicit.
Casual videogames are less explicit.
Answer:
The core is a lot of money
The casual is less of money
pretty sure
Explanation:
What does your car driver look like? Answer the following question.
1. How many minutes do you drive every day?
2. How long do you travel every day?
3. What trips could you make in any other way?
4. What are the risks / dangers of traveling by car?
Answers
Answer:
42 miami to pakistan
Explanation: buy
With _, phone calls are treated as just another kind of data. A. voice over internet protocol. B. chat rooms. C. teleconference. D. all choices are correct.
Answers
With voice over internet protocol/VoIP, phone calls are converted into digital data and transmitted over the internet.
So, the correct answer is A.
This allows for more efficient use of bandwidth and lower costs for communication.
Additionally, VoIP allows for advanced features such as video calling, call forwarding, and voicemail to email transcription. As such, VoIP has become increasingly popular in both personal and business settings.
So, if you're looking for a cost-effective and flexible way to communicate, VoIP might be the solution for you.
Hence, the answer of the question is A.
Learn more about VoIP at
https://brainly.com/question/14041634
#SPJ11
Files that are stored on your server are known as:
transferred files
remote files
root files
local files
Answers
Files that are stored on your server are known as: D. local files.
What is a file?A file can be defined as a computer resource or type of document that avails an end user the ability to save or record data as a single unit on a computer storage device.
What is a server?A server can be defined as a dedicated computer system that is designed and developed to provide specific services to other computer devices or programs, which are commonly referred to as the clients.
In Computer technology, local files simply refer to a terminology which is used to describe and connote all files that are stored on your server.
Read more on files here: brainly.com/question/6963153
#SPJ1