The step of creating a storyboard should be done after you complete which step?
1filming
2writing the script
3casting the actors
4designing a set
Answers
Answer:
the step of creating a story board should be done after writing the script
Related Questions
Demonstrate how to assign a value to the third element of an array called finalGradeArray.
Answers
Answer:
It's really important that you say in which language you wanna do this. But like in python:
finalGradeArray.insert(2, "New value")
Explanation:
Question 1(Multiple Choice Worth 5 points)
(03.01 MC)
Which line of code will only allow a non-decimal point to be stored in a variable?
candyCost = int(input("How much is the candy?"))
candyCost = input("How much is the candy?")
candyCost = float(input("How much is the candy?"))
candyCost = str(input("How much is the candy?"))
Question 2(Multiple Choice Worth 5 points)
(03.01 MC)
Cheri's teacher asked her to write a program using the input() function. What will this allow her program to do?
Add comments to the code
Allow others to understand the code
Display a string on the screen
Make the program interactive
Question 3(Multiple Choice Worth 5 points)
(03.01 MC)
Jabari is writing a program which prompts a user for a value that is negative and has a decimal. Which function should he use?
float()
int()
print()
string()
Question 4(Multiple Choice Worth 5 points)
(03.01 LC)
In programming, what is a string?
A cable that connects a computer to hardware
A method of threading code into a computer
A system of organizing letters alphabetically
A way to store a sequence of letters, numbers, or symbols
Question 5(Multiple Choice Worth 5 points)
(03.01 LC)
Which function converts the user's input to a number without a decimal?
float()
int()
print()
string()
Answers
Answer:
b
Explanation:
it's not a c or d and now I have to make it 20 characters long so I will do this
A college campus uses robots to give students tours. The prospective students can ask the robot questions about life on campus. The robot allows the visiting student to choose which parts of campus to visit. What best describes the type of AI possessed by the robot?
weak AI
neural network AI
symbolic AI
Strong AI
Answers
The type of AI possessed by the robot in this scenario is Weak AI, also known as Narrow AI or Applied AI.
Weak AI is designed to perform a specific task, and it operates within a limited domain. The robot in this scenario is programmed to give tours of the campus and answer questions about life on campus. It does not have general intelligence, consciousness, or the ability to think and reason like a human being, and it cannot perform tasks outside of its programmed capabilities.
In contrast, Strong AI, also known as Artificial General Intelligence (AGI), is a theoretical form of AI that would possess human-like intelligence and the ability to reason and perform any intellectual task that a human can do. However, Strong AI does not currently exist.
Neural network AI and Symbolic AI are categories of techniques and approaches used in the development of AI, and they can be applied to both Weak AI and Strong AI systems. Neural network AI involves developing algorithms that are modeled after the structure and function of the human brain, while Symbolic AI involves creating AI systems based on a set of rules or symbols. However, the type of AI possessed by the robot in this scenario is more specifically described as Weak AI.
Please answer the question on engineering process

Answers
Answer: A
Explanation: If you don't Identify the problem the computer will act up and you will not be able to fix it if you don't identify the problem.
explanation:
help please im not sure what this means T^T

Answers
Answer:
14
Explanation:
Experts believe robots and AI will continue taking over many of the human jobs we know today. What changes should be made to K-12 education to ensure students are prepared for the future? What courses or skills should be added? WHat should be removed? Why?
Answers
Answer:
I think they should show one subject per month so students are more prepared
Answer: some changes that should be made are dresscode , some courses should be more sports . Nothing should be removed because the kids in the future need to learn more .
Explanation:
A bicycle is probably not a computer because it does not
have a screen
require electricity
use information to solve a problem
use the internet
Pls anwser quick
Answers
C programming 3.26 LAB: Leap year
A year in the modern Gregorian Calendar consists of 365 days. In reality, the earth takes longer to rotate around the sun. To account for the difference in time, every 4 years, a leap year takes place. A leap year is when a year has 366 days: An extra day, February 29th. The requirements for a given year to be a leap year are:
1) The year must be divisible by 4
2) If the year is a century year (1700, 1800, etc.), the year must be evenly divisible by 400; therefore, both 1700 and 1800 are not leap years
Some example leap years are 1600, 1712, and 2016.
Write a program that takes in a year and determines whether that year is a leap year.
Ex: If the input is 1712, the output is:
1712 - leap year
Answers
if year mod 100 equals 0
Check if year mod 400 equals 0 (if true, leap year, if not, not a leap year)
And if year mod 100 doesn’t equal 0
Check if year mod 4 equals 0 (if true, leap year, if not, not a leap year)
Sorry if this is a bit janky, if you need any further explanation please let me know.
How do you think computers have helped to improve documentation, support and services within the healthcare industry.
Answers
Computers are the excellent means for storage of patient related data.It is often necessary to maintain detailed records of the medical history of patients. Doctors often require the information about a patient's family history, physical ailments, already diagnosed diseases and prescribed medicines.
Answer:
It can help in many ways, like telling your phone that your there to tell the workers to get ready, you don't need to hire a worker cashier anymore but you will need power for it speakers and radios and lights can help you see inside of the area technology has helped us with many things.
Explanation:
Will the following boolean expression return True or False?

Answers
Answer:
the boolean expression returns false
Explanation:
because 10!==100
Ji-Woo is helping a supervisor create a database of all employees. The supervisor points out that there is more than one person with the same name, and there are concerns about their records getting confused. Ji-Woo explains that every database record will have a unique ____ to identify it.
A.
primary key
B.
query
C.
table
D.
field
Answers
Answer:
I think that option A is the correct answer.
Answer:
Explanation: Primary key
PLEASE HELP ME!!!!
You are creating a form on a website where the user will enter a “Y” for “yes” and an “N” for “no.” Which data type should you use to store the letter that the user enters?
*character
*string
*Boolean
*integer
Answers
Answer:
integer
Explanation:
Hey can someone help?
What is something you do to judge the credibility of websites, videos, or information you come across online?
Answers
How does binary code control the processes in a computer.
Answers
Binary systems employ the code to comprehend user input and operational instructions and to offer the user with an appropriate output.
What is binary system?Binary system is defined as a numbering system where each digit can only have one of two values—0 or 1—and which serves as the foundation for all binary code used in computing systems. These systems make use of this code to decipher user input and operational directives and provide the user with the desired result.
The binary is read from, say, disk and loaded into memory. The memory contents are then loaded into a processor local resister according to a directive issued by the processor logic to the memory controller. The CPU then interprets it as a command to execute.
Thus, binary systems employ the code to comprehend user input and operational instructions and to offer the user with an appropriate output.
To learn more about binary system, refer to the link below:
https://brainly.com/question/2824068
#SPJ2
If you want the words “My puppy is a poodle” to appear in the output box, what Python code should you use?
A.
create “My puppy is a poodle”
B.
execute (“My puppy is a poodle”)
C.
print(“My puppy is a poodle”)
D.
print “My puppy is a poodle”
Answers
Answer:
i think it is B hope it helps
Part 1: Compare the Websites
You are conducting research for a project about elephant sanctuaries. Compare the two websites using the 5 W’s criteria for reliability and validity. For each website, complete the 5 W’s Checklist.
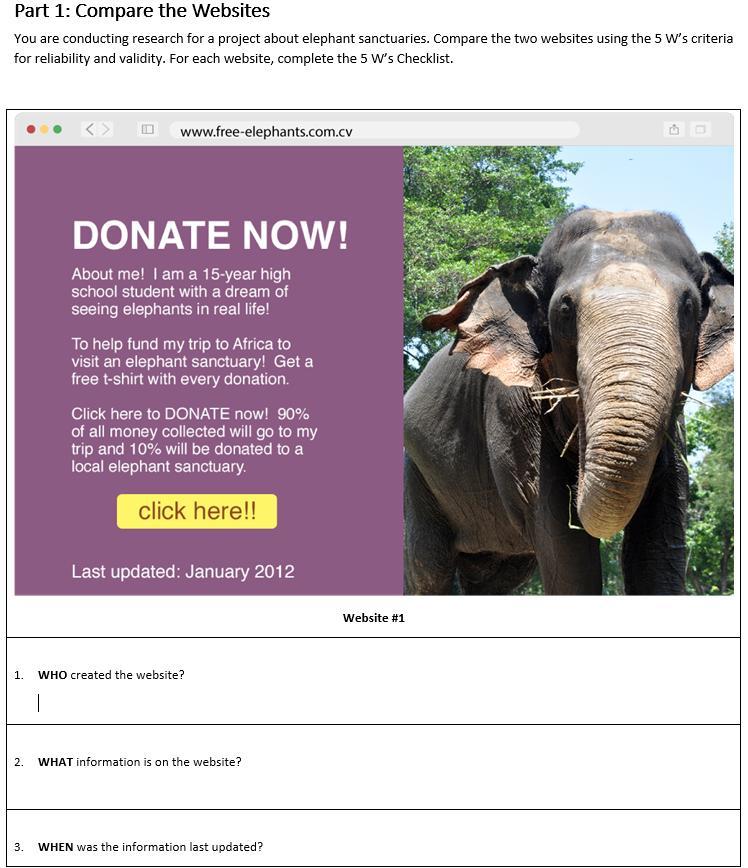




Answers
Answer:
WHO: a 15-year old high school student
WHAT: information about donating to a local elephant sanctuary and a trip
WHEN: January 2012
WHERE: www.free-elephants.com.cv
WHY: To help fund the student's trip to Africa to visit an elephant sanctuary
who: a 15-year-old high school student
what: information about donating to a local elephant sanctuary and a trip
when: January 2012
where: www.free-elephants.com.cv
why: To help fund the student's trip to Africa to visit an elephant sanctuary
In a minimum of 250 words, discuss the technological problems that can occur when consumers emphasize on speed over security.
Answers
1. Vulnerabilities and Breaches: Emphasizing speed often means sacrificing robust security measures. This can lead to vulnerabilities in software, applications, or systems that attackers can exploit. Without adequate security measures, data breaches become more likely, exposing sensitive information such as personal data, financial records, or trade secrets. The aftermath of a breach can be detrimental, including reputational damage, legal consequences, and financial losses.
2. Malware and Phishing Attacks: When speed takes precedence, consumers may overlook potential malware or phishing attacks. By rushing through security checks or bypassing cautionary measures, they inadvertently expose themselves to malicious software or fraudulent schemes. These attacks can compromise personal information, hijack devices, or gain unauthorized access to networks, resulting in financial losses and privacy violations.
3. Inadequate Authentication and Authorization: Speed-centric approaches might lead to weak or simplified authentication and authorization mechanisms. For instance, consumers may choose easy-to-guess passwords or reuse them across multiple platforms, making it easier for attackers to gain unauthorized access. Additionally, authorization processes may be rushed, granting excessive privileges or overlooking necessary access controls, creating opportunities for unauthorized users to exploit system vulnerabilities.
4. Neglected Updates and Patches: Prioritizing speed often means neglecting regular updates and patches for software and systems. By delaying or avoiding updates, consumers miss out on critical security fixes and vulnerability patches. Hackers actively exploit known vulnerabilities, and without timely updates, devices and systems remain exposed to these threats, making them easy targets.
5. Lack of Secure Development Practices: When speed becomes the primary concern, secure development practices might take a backseat. Security testing, code reviews, and quality assurance measures may be rushed or ignored, leading to the inclusion of vulnerabilities in the software or application itself. These vulnerabilities can be exploited by attackers to gain unauthorized access or execute malicious activities.
To mitigate these problems, it is essential to strike a balance between speed and security. Consumers should prioritize security measures such as using strong passwords, enabling multi-factor authentication, regularly updating software, and being cautious of suspicious links or emails. Service providers and developers must also prioritize security in their products and services by implementing secure coding practices, conducting thorough security assessments, and promptly addressing vulnerabilities. Ultimately, a comprehensive approach that values both speed and security is crucial for maintaining a safe and efficient technological ecosystem.
Explanation:
--> used brainly simplify :D
Consumers prioritizing speed over security can lead to several technological problems. This includes vulnerabilities and breaches where attackers can exploit weaknesses in software or systems. Malware and phishing attacks become more likely when security measures are overlooked. Weak or simplified authentication and authorization methods can make it easier for unauthorized users to gain access. Neglecting updates and patches leaves devices and systems vulnerable to known threats. Lastly, rushing through secure development practices may result in the inclusion of vulnerabilities in the software itself. To address these issues, consumers should use strong passwords, update their software regularly, and be cautious of suspicious links or emails. Service providers and developers should prioritize security by conducting thorough security assessments and promptly addressing vulnerabilities. Striking a balance between speed and security is crucial for a safe and efficient technological environment.
Which of these might be an example of an advertiser's target group?
A.People who have no access to media
B.people the advertisers know nothing about
C. People who watch a variety of TV shows
D. People who live in the same region of the country
Answers
An example of an advertiser's target group that "people the advertisers know nothing about". which is the correct answer would be option (B).
What is Advertiser?A corporation, organization, or individual who pays for advertising space or time to deliver a convincing commercial or message to the public is known as an advertiser. It is derived from the Latin word "annunciare", which means to announce or make known certain news.
Advertising is the technique of displaying advertisements. Advertisers use advertising to increase the consumption of their products or services by creating a "brand," which equates the name of the product or picture with particular traits in the minds of customers. Political parties, interest groups, religious organizations, and government agencies are examples of advertisers who can spend money to market other aspects of a product or service to the customer.
Thus, the example of an advertiser's target group that "people the advertisers know nothing about"
Hence, the correct answer would be option (B).
To learn more about the advertisements click here:
https://brainly.com/question/3163475
#SPJ5
how do you set up a go ogle account on a school computer?
Answers
Explanation: Click sign in, then Click use another account, after that put in the email and password for that account. You should now have a new account.
3 different ways that ultrasonic sensors can be used in everyday life.
Answers
Answer:
Ultrasonic Sensors Uses:
Anti-Collision DetectionPeople DetectionContouring or ProfilingPresence DetectionBox Sorting using a Multi-Transducer SystemEasy Control of Trash Collection VehiclesPallet Detection with ForkliftsBottle Counting on Drink Filling MachinesLearn more about Ultrasonic Sensors here
Visit —
https://brainly.in/question/19907919
https://brainly.ph/question/13809853
Hope my answer helps you ✌️
Mark BRAINLIEST
Ultrasonic retro-reflective sensors.
Ultrasonic through-beam sensors.
Question: How do you file a complaint using a food restaurant? 100 POINTS WILL BE GIVEN INCLUDING BRAINLIEST
Answers
send it through the mail
Answer: Be prepared to provide the following information:
1.Your Name, Address and Phone Number (your information will remain anonymous to the restaurant)
2.Name of restaurant
3.Location/address of the restaurant
4.Date of incident
5.Nature of complaint
If you suspect you became ill from this incident. You will need to give specific information about the suspected foods that made you sick, as well as when your symptoms began, and what they were. In addition, you will need to give a 3-day food eating history.
Explanation
NO LINKS!! HELP!! ESSAY DUE TODAY!!!

Answers
Answer:
To the "Am not 13"
Explanation:
Amy Bernstein wrote a story, which is titled "I'm Not Thirteen Yet." The story is told from the perspective of one of the characters, making it a personal narrative. The story's author describes his personal experiences throughout the narrative. 'I had entered the world of teenagers, and I wasn't even one of them yet,' says the author, demonstrating that he is writing about his own experiences.
ill give Brainliest!!!!! I REALLYYY NEED HELP
i have to do journals for computers, and its a free topic....... make a topic and give me a four sentence journal PLSSSS this question Worth 28 points too
Answers
Answer:
Topic: Alexander the great
Alexander was born in July 356 B.C. to Philip II and his wife, Queen Olympias.He was tutored by a philosopher named ‘Aristotle’,he taught Alexander about medicine, philosophy, morals, religion, logic, and art.His full name is ‘Alexander ||| of Macedon’.He died on June 323 B.C and people still don't know how he was killed.A lot of people say that he was killed by poison but nobody really has proof.But despite him being killed he was famous for being the King of Macedonia and conqueror of the Persian Empire. He was a great military leader in fact he is one of the BEST known
I think butterflies are one of the most underrated bugs. Butterflies are some of the most beautiful bugs, their pretty patterns distinguish them. They have some pretty top notch comoflage and defense mechanisms too. They migrate which makes them pretty wonderful too. I think we should work harder to protect them, when cars are driving down the road during migration season, thousands of innocent butterflies get killed.
what are some basic commands to remember in terminal? windows 10
please help if you know
Answers
Answer:
If you just need a few, maybe this can help.
Explanation:
Cat - The cat command means 'Concatenate'. It prints the contents of a file or files to stdout. It's frequently used in Linux commands.
Touch - Using the 'Touch' command, you can create a file, or possibly just modify or generate a timestamp.
Move - The 'mv' command stands for 'Move'. As the name says, we can use this command to move files and directories from one place to another.
Chsh - The chsh command changes a user's login shell attribute. If you want to change the shell of another user, execute the command with root permissions.
Sudo - 'Sudo', or 'super user do', is a command that allows you to elevate your user privileges while executing the command to administrator privileges.
Most files in Windows are associated with a specific program that is assigned to open the file by default. At times, remembering these associations can become confusing. You can remind yourself by entering the command assoc to display a full list of filename extensions and program associations. You can also extend the command to change file associations. For example, assoc .txt= will change the file association for text files to whatever program you enter after the equal sign. The assoc command itself will reveal both the extension names and program names, which will help you properly use this command.
In Windows 10, you can view a more user-friendly interface that also lets you change file type associations on the spot. Head to Settings (Windows + I) > Apps > Default apps > Choose default app by file type
2.Cipher
Deleting files on a mechanical hard drive doesn't really delete them at all. Instead, it marks the files as no longer accessible and the space they took up as free. The files remain recoverable until the system overwrites them with new data, which can take some time. The cipher command, however, lets you wipe a directory on an NTFS-formatted volume by writing random data to it. To wipe your C drive, for example, you'd use the cipher /w:d command, which will wipe free space on the drive. The command does not overwrite undeleted data, so you will not wipe out the files you need by running this command.
When you run the cipher command by itself, it returns the encryption state of the current directory and the files it contains. Use cipher /e: to encrypt a file, cipher /c: to retrieve information about encrypted files, and cipher /d: to decrypt the selected file. Most of these commands are redundant with the Windows encryption tool BitLocker.
3.file Compare
You can use this command to identify differences in text between two files. It's particularly useful for writers and programmers trying to find small changes between two versions of a file. Simply type fc and then the directory path and file name of the two files you want to compare.
You can also extend the command in several ways. Typing /b compares only binary output, /c disregards the case of text in the comparison, and /l only compares ASCII text.
So, for example, you could use the following:
fc /l "C:\Program Files (x86)
The above command compares ASCII text in two Word documents.
4.Ipconfig
This command relays the IP address that your computer is currently using. However, if you're behind a router (like most computers today), you'll instead receive the local network address of the router.
Still, ipconfig is useful because of its extensions. ipconfig /release followed by ipconfig /renew can force your Windows PC into asking for a new IP address, which is useful if your computer claims one isn't available. You can also use ipconfig /flushdns to refresh your DNS address. These commands are great if the Windows network troubleshooter chokes, which does happen on occasion.
5.Netstat
Entering the command netstat -an will provide you with a list of currently open ports and related IP addresses. This command will also tell you what state the port is in; listening, established, or closed.
This is a great command for when you're trying to troubleshoot devices connected to your PC or when you fear a Trojan infected your system and you're trying to locate a malicious connection.
6.Ping
Sometimes, you need to know whether or not packets are making it to a specific networked device. That's where ping comes in handy.
Typing ping followed by an IP address or web domain will send a series of test packets to the specified address. If they arrive and are returned, you know the device is capable of communicating with your PC; if it fails, you know that there's something blocking communication between the device and your computer. This can help you decide if the root of the issue is an improper configuration or a failure of network hardware.
7.PathPing
This is a more advanced version of ping that's useful if there are multiple routers between your PC and the device you're testing. Like ping, you use this command by typing pathping followed by the IP address, but unlike ping, pathping also relays some information about the route the test packets take.
What is the purpose of the PC troubleshooting process? Select two answers. BRAINLIEST to who gets it right

Answers
Answer:
identify...
solve...
Explanation:
Troubleshooting is a form of problem solving, often applied to repair failed products or processes on a machine or a system.
Answer:
Identify Problems and Fix Broken Components
Explanation:
"Critical troubleshooting will automatically fix things like corrupt settings that keep critical services from running, make adjustments to work with your hardware, or make other specific changes required for Windows to operate with the hardware, apps, and settings you've selected." Cited from Microsoft Support's Website
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain. ( USE C.E.R *Claim, Evidence, Reasoning* )
Answers
I think the pros of digital recordings outweigh the cons! I prefer digital audio recordings over analog audio recordings because analog recordings require more financing and preservation. Compared to digital recordings, analog recording equipment is more expensive and the tape deteriorates over time. Which to me personally, doesn't seem to be worth the amount of effort since it's such a process to go through. You can possibly go into debt due to that. Digital recording equipment, on the other hand, is more affordable. It's less time-consuming and although it does have its disadvantages, they're minor. Digital recordings can be stored online. Its data get corrupted? You can get it back! It won't cost you anything.
What do the Brainly points do? sorry im new here and i dont know how to internet rn .-.
also you get points for this i guess :)
Answers
Answer:
Hii, Welcome to brainly!
Explanation:
Basically, if you have points, you can ask your own questions. If you answer people's questions, you get points. You can also get leveled up by points. (or ranks) For example, Beginner is starts from 0 points and 0 brianliest. Then there's Helping Hand. You can get helping hand by having 100 points. Then there's Ambitious which starts off with 250 points. You can get Brainliest when you answer someone's question and they think you answered with the best answer. You also get points when you get Brainliest. One way to earn many points is by doing any challenges. The first challenge is to answer 5 questions in 48 hours/2 days and you get 50 points. There's a lot to learn about brainly i didn't cover all of it but i hope this helps!
HURRY 50 POINTS A human is needed to create the algorithms that computers use.
True
False
Answers
Answer:False
Explanation:Took the test before
Answer:
maybe false
Explanation:
While the economy of eastern Washington relies on farming, western Washington relies on technology.
True
False
Answers
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2