Type the correct answer in the box. Spell all words correctly.
A language translator software works by recognizing the words a person is speaking and translating it into another language. Where will the system store the dictionary and semantic information?
The (?) stores the data such as dictionaries and semantic information necessary to make the translator work.
Answers
The correct answer in the box is as follows:
The knowledge base stores the data such as dictionaries and semantic information necessary to make the translator work.
What is the index of the knowledge base?The knowledge base possesses factual knowledge that is widely transmitted and acknowledged. It also incorporates heuristic knowledge that is exploratory and emanated from the conclusion.
Therefore, the word which is filled in the box is knowledge base.
To learn more about Semantic information, refer to the link:
https://brainly.com/question/15152462
#SPJ1
Related Questions
Shannon wants to work with renewable energy. She is researching what it would take to become a geochemist. A geochemist is someone who uses chemistry to study water and elements in it. What skill or ability well Shannon need to be the most effective in this position?
Answers
Answer:
Critical thinking
Explanation:
Shannon needs to be a Critical thinker to be effective in this position. Critical thinking has to do with giving deep and good thoughts while doing analysis, or assessment in other to come up with good judgements about a subject or topic.
Since she is going to be studying water and elements in it, she would be doing a lot of analysis and assessments and In other to do good in her field she must learn to think critically before arriving at her conclusions.
Answer:
Critical thinking
Explanation:
Shannon needs to be a Critical thinker to be effective in this position. Critical thinking has to do with giving deep and good thoughts while doing analysis, or assessment in other to come up with good judgements about a subject or topic.
Since she is going to be studying water and elements in it, she would be doing a lot of analysis and assessments and In other to do good in her field she must learn to think critically before arriving at her conclusions.
1. describe how a page fault is handled? 2. what are file attributes? 3. what operations can be performed on files and directories? why are some distinct? 4. compare and contrast sequential to direct access. 5. how is a tree-structured directory different from a acyclic-graph directory?
Answers
The way that page fault is handled is by:
Once the virtual address that produced the page fault is determined, the system verifies that the address is genuine and makes sure there are no issues with protection or access. The system checks to verify if a page frame is free if the virtual address is legitimate. The page replacement algorithm is used to remove a page if there are no empty frames.The operations that can be performed on files and directories are:
Open operationWrite operationRead operationRe-position or Seek operationDelete operationTruncate operationClose operationWhat is the compare and contrast sequential to direct access?Sequential access should start at the start and access each element one at a time. Any element may be directly accessed by using its index number or address to find it. There is direct access with arrays. CDs had direct access, but magnetic tape only has sequential access.
Therefore, one can say that direct access eliminates the need to browse the data in order. When data is retrieved sequentially, it is located by starting at one location and moving on to succeeding sites until it is.
Learn more about page fault from
https://brainly.com/question/29506246
#SPJ1
entry and exit time can be a significant physical limitation
Answers
As a physical restriction, entry and leave times are extremely important since they directly affect the potential danger of the enclosed location.
has fewer or more limited entry or departure options?limited or prohibited entry/exit options Any area where entry or exit requires unusual physical effort, such as crawling, climbing, twisting, being squeezed through a small aperture, following a long journey, or where the entrance may become blocked or secured to prevent opening from the inside.
What are the physical risks of a small space?Hazardous atmospheres, such as low oxygen levels, poisonous (toxic) air, or explosive atmospheres, can exist in enclosed places. These areas may also contain physical risks that could cause, for instance, workers to fall, be buried or crushed, or even drown.
To know more about physical restriction visit :-
https://brainly.com/question/19567256
#SPJ4
How many bits would be needed to count all of the students in class today?
10 students in the class
Answers
Answer:
If you have 12 students in class you will need 4 bits.
Nadia has inserted an image into a Word document and now would like to resize the image to fit the document better.
What is the quickest way to do this?
keyboard shortcut
sizing handles
context menu
sizing dialog box
Answers
What is the most important part of a state?
Answers
The most important part of a State is; Sovereignty
State SovereigntyThe most important part of the state is Sovereignty followed by other elements like population, government, and territory.
The reason for Sovereignty as the most important and most exclusive part of a state is because it is the basis upon which the state regulates all aspects of the life of the people living in that state.
Read more about State Sovereignty at; https://brainly.com/question/7226587
Which of the following is NOT an algorithm?
Following a recipe to bake a cake
Following an instruction booklet for a game
SHA-256
Rolling a pair of dice in monopoly
Answers
Answer:
d) rolling a pair of dice in monopoly
Explanation:
an algorithm is a process or set of rules followed in a particular order to perform a certain task. all of the other answers are a set of instructions that lead to something except for rolling a pair of dice. rolling a pair of dice can be a part of instruction but its not a process in itself.
hope this makes sense!
bruce frequently works with a large number of files. he notices that the larger the files get, the longer it takes to access them. he suspects that this problem of time consumption in accessing those files is related to the files being spread over the disk. he needs to store the files contiguously on the disk. which utility should he use to achieve this task?
Answers
Disk defragmenter utility should he use to achieve this task.
What is disk defragmenter?
Defragmentation is a procedure that lowers the level of fragmentation in file systems maintenance. It accomplishes this by dividing the mass storage device's file storage contents into the fewest possible continuous sections (fragments, extents).
In an effort to prevent fragmentation from returning, it also makes use of compaction to expand the areas of open space. Because they are frequently accessed in succession, several defragmentation tools attempt to keep smaller files within a single directory together.
The benefits of defragmentation and how it applies to file systems on mechanical disk drives (hard disk drives, floppy disk drives and optical disk media). When accessing fragmented files, the read/write heads of the hard drive move more slowly over the disk than when accessing the entire contents of a non-fragmented file sequentially without moving the heads to look for additional fragments.
Learn more about Defragmentation click here:
https://brainly.com/question/14254444
#SPJ4
Which of the following statements is false? a. As of Java SE 8, any interface containing only one method is known as a functional interface. b. There are many functional interfaces throughout the Java APIs. c. Functional interfaces are used extensively with Java SE 8â s new lambda capabilities. d. Anonymous methods provide a shorthand notation for creating lambdas.
Answers
Answer:
d. Anonymous methods provide a shorthand notation for creating lambdas.
Explanation:
Java SE 8, is Standard Edition of Java. It is a computing platform for deployment of portable code for servers. The statement that is not correct is anonymous method provide shorthand notation. Lambda expression are added in Java 8, which enables to treat functionality as method argument code or data. Lambda expression can be passed around as it is an object executed on demand.
Using the below variables, write a for loop that increases x by two for each i.
x=1; i=c(1:10)
Answers
Here is the for loop that increases x by two for each I that uses the below variables: x=1; i=c(1:10):` for (num in i){x = x + 2}`
What are variables? Variables are a way to save data in the computer memory (RAM) to use later. This data can be manipulated and updated during programming. They are assigned a value and can be referenced by the name given to them. There are different data types of variables, including integers, floating-point numbers, characters, strings, and Booleans. What is a loop? A loop is a programming function that allows a section of code to be repeated until a specific condition is met. It saves time and code by repeating sections of code that have the same output. Loops are useful when you need to perform the same action multiple times in a program, such as reading from a file, processing data, and validating user input. There are different types of loops, including loops, while loops, and do while loops.
Learn more about loop here: brainly.com/question/30494342
#SPJ11
You have a workbook with multiple worksheets and want an exact copy of one of the worksheets. How can you duplicate this sheet within the same workbook?.
Answers
To duplicate a sheet within the same workbook, hold down the Ctrl key, then click and drag the sheet's tab.
Microsoft ExcelMicrosoft Excel is a spreadsheet program that is used for data visualization and analysis tool. You can use Excel to store, organize, and analyze data.
Worksheet is a collection of cells organized in rows and columns found in Microsoft excel. A workbook is a collection of one or more spreadsheets, also called worksheets, in a single file.
To duplicate a sheet within the same workbook, hold down the Ctrl key, then click and drag the sheet's tab.
Find out more on Microsoft Excel at: https://brainly.com/question/1538272
compare and contrast science and technology
Answers
Answer:
Comparisons: Science and technology are always two things that are being constantly refined. They are also quite useful things to know in day to day life. However, technology depends on science. Science is more conceptual than technology; technology is a thing, while science is a concept of knowledge.
Need help fast this is do a 4

Answers
Answer:
I believe the answer is B.
i have the logger set to debug, and the appender set to error. what logs will i likely see in the log? choose all that apply
Answers
If the logger is set to debug and the appender is set to error, the logs that are likely to appear in the log include Debug and Error logs.
Logging refers to the process of recording the events that occur during the execution of a program or system. When a system or an application is running, logging records everything that occurs, including errors, status, and debug information. It helps to debug and identify issues that occur in the software. Loggers help in logging in to the system. The loggers determine the log level for the application to execute. The different levels of log levels include Error, Warning, Info, Debug, and Trace. Error log An error log is a log file that records all the significant errors that occur in a software system. It can help identify the root cause of an issue or bug and aid in debugging. In contrast to a warning message, an error message usually requires immediate attention, and the error needs to be resolved. Debug logThe Debug log records information that may help a developer identify issues with a piece of software. The Debug level records additional details about what happens in the code so that the developers can fix the problems that the software is experiencing. So if the logger is set to debug and the appender is set to error, the logs that are likely to appear in the log include Debug and Error logs.
Learn more about debug here:
https://brainly.com/question/13966274
#SPJ11
ways in which a computer are used in online resavation
Answers
Answer:
Explanation:
Modern GDSs typically also allow users to book hotel rooms, rental cars, airline tickets as well as other activities and tours. ... These are also used to relay computerized information for users in the hotel industry, making reservation and ensuring that the hotel is not overbooked.
subtract each element in origlist with the corresponding value in offsetamount. print each difference followed by a space. ex: if the input is: 4 5 10 12 2 4 7 3 the output i
Answers
Run a for loop after writing all the code specified in the question until the variable I is lower than the NUM VALS constant.
In other words, since the NUM VALS constant's value is 4, the for loop will be executed 4 times. Display the results by deducting offset. Amount from origList inside the for loop.
#include <stdio.h>
int main() {
const int NUM_VALS = 4;
int origList[NUM_VALS];
int offsetAmount[NUM_VALS];
int i;
origList[0] = 40;
origList[1] = 50;
origList[2] = 60;
origList[3] = 70;
offsetAmount[0] = 4;
offsetAmount[1] = 6;
offsetAmount[2] = 2;
offsetAmount[3] = 8;
for (i = 0; i < NUM_VALS; ++i) {
printf("%d ", origList[i] - offsetAmount[i]);
}
printf("\n");
return 0;
}
Learn more about Constant here-\
https://brainly.com/question/14159361
#SPJ4
Which code shows the correct version of the loop shown below?
It should print all the numbers in list a.

Answers
Answer:
The second program code segment must show the data in the same list being used ... loop, the function terminates by returning the number of correct answers.
Explanation:
The second program code segment must show the data in the same list being used ... loop, the function terminates by returning the number of correct answers.
What are the steps to debugging?
Answers
Answer:
The basic steps in debugging are:
Recognize that a bug exists.
Isolate the source of the bug.
Identify the cause of the bug.
Determine a fix for the bug.
Apply the fix and test it.
uestion
Question text
_ is not an object-oriented programming language
Answers
BASIC is not an object-oriented programming language Hence option 3 is correct.
What is object-oriented programming?Object-oriented programming (OOP) is a programming paradigm that focuses on using objects as the basic building blocks of software. In OOP, an object is an instance of a class, which defines a set of related data and behavior. An object contains data in the form of fields, and behavior in the form of methods.
BASIC is a procedural programming language that is not typically considered an object-oriented programming language. It does not provide built-in support for classes, objects, inheritance, and other key features of object-oriented programming.
In contrast, C++, Simula, and Java are all object-oriented programming languages that provide extensive support for classes, objects, inheritance, polymorphism, and other object-oriented programming concepts.
Read more about object-oriented programming here:
https://brainly.com/question/14078098
#SPJ1
See full text below
Which of the following is not an object oriented programming language?
1)C++
2)Simula
3)BASIC
4)Java
CALCULATE THE MECHANICAL ADVANTAGE (MA).
DATA: F= 135 kg; b= 4*a; L=15 m
Answers
The mechanical advantage (MA) of the lever system in this scenario can be calculated by dividing the length of the longer arm by the length of the shorter arm, resulting in an MA of 4.
To calculate the mechanical advantage (MA) of the lever system, we need to compare the lengths of the two arms. Let's denote the length of the shorter arm as 'a' and the length of the longer arm as 'b'.
Given that the longer arm is four times the length of the shorter arm, we can express it as b = 4a
The mechanical advantage of a lever system is calculated by dividing the length of the longer arm by the length of the shorter arm: MA = b / a.
Now, substituting the value of b in terms of a, we have: MA = (4a) / a.
Simplifying further, we get: MA = 4.
Therefore, the mechanical advantage of this lever system is 4. This means that for every unit of effort applied to the shorter arm, the lever system can lift a load that is four times heavier on the longer arm.
For more such question on system
https://brainly.com/question/12947584
#SPJ8
The complete question may be like:
A lever system is used to lift a load with a weight of 135 kg. The lever consists of two arms, with the length of one arm being four times the length of the other arm. The distance between the fulcrum and the shorter arm is 15 meters.
What is the mechanical advantage (MA) of this lever system?
In this scenario, the mechanical advantage of the lever system can be calculated by comparing the lengths of the two arms. The longer arm (b) is four times the length of the shorter arm (a), and the distance between the fulcrum and the shorter arm is given as 15 meters. By applying the appropriate formula for lever systems, the mechanical advantage (MA) can be determined.
Last two question, Let's go

Answers
For question 9, it's science
for question 10 it's the "world works"
A person with a kinesthetic learning style learns best by
a. reading and writing.
b. moving around and interacting with objects.
c. working with numbers and patterns.
d. independent study.
Answers
what does an "embedded video" mean
Answers
Answer:
simply linking to the video at another location and
Explanation:
Arthur Meiners is the production manager for Wheel-Rite, a small manufacturer of metal parts. Wheel-Rite sells 10,378 gear wheels each year. Wheel-Rite setup cost is $45 and maintenance cost is $0.60 per sprocket per year. Wheel-Rite can produce 493 gear wheels per day. The daily demand for the gear wheels is 51 units. Show your work.
1. What inventory management model should we use to solve this problem?
Model for discount purchases
Model Economic Quantity to Order
Model Economic Quantity to Produce
Model to handle dependent demand
2. What is the optimal amount of production? 3. What is the maximum inventory level of gear wheels that will be in the Wheel-Rite warehouse? 4. What is Wheel-Rite's annual setup cost? 5. What is the annual cost of maintaining Wheel-Rite?
Answers
2. To calculate the optimal amount of production using the EOQ model, we need the following information:
- Demand per year (D) = 10,378 gear wheels
- Setup cost (S)= $45
- Production rate per day (P) = 493 gear wheels
- Working days per year (W) = 365 (assuming no downtime)
The formula to calculate the EOQ is:
EOQ = sqrt((2 * D * S) / (P * (1 - (D / (P * W)))))
Plugging in the values:
EOQ = sqrt((2 * 10,378 * 45) / (493 * (1 - (10,378 / (493 * 365)))))
Calculating this equation will give you the optimal amount of production.
3. The maximum inventory level of gear wheels that will be in the Wheel-Rite warehouse can be calculated by multiplying the optimal amount of production (EOQ) by the number of production cycles in a year. The number of production cycles can be calculated by dividing the annual demand (D) by the optimal amount of production (EOQ) and rounding up to the nearest whole number.
Maximum inventory level = EOQ * ceil(D / EOQ)
4. Wheel-Rite's annual setup cost can be calculated by multiplying the setup cost (S) by the number of production cycles in a year.
Annual setup cost = S * ceil(D / EOQ)
5. Wheel-Rite's annual cost of maintaining inventory can be calculated by multiplying the holding cost per unit (which is the maintenance cost per sprocket per year) by the average inventory level. The average inventory level can be calculated by dividing the maximum inventory level by 2.
Annual cost of maintaining inventory = (Holding cost per unit) * (Average inventory level)
In this case, the holding cost per unit is $0.60 per sprocket per year, and the average inventory level can be calculated as (Maximum inventory level / 2).
Please note that you need the calculated EOQ value from question 2 to answer questions 3, 4, and 5.8
A(n) _____ is a computerized system by which subscribers are able to communicate to all other subscribers by sending a transmission to one address
Answers
Answer: Listerv
Explanation:
A power supply is an electrical transformer that regulates the electricity used by the computer. Select one: A. False B. True
Answers
Answer:
The Answer is B
Explanation:
The power supply converts AC current to DC current and protects the P.C. hardware from being fried from electrical surges. So it regulates electricity.
log the 'age' property of the 'person' object
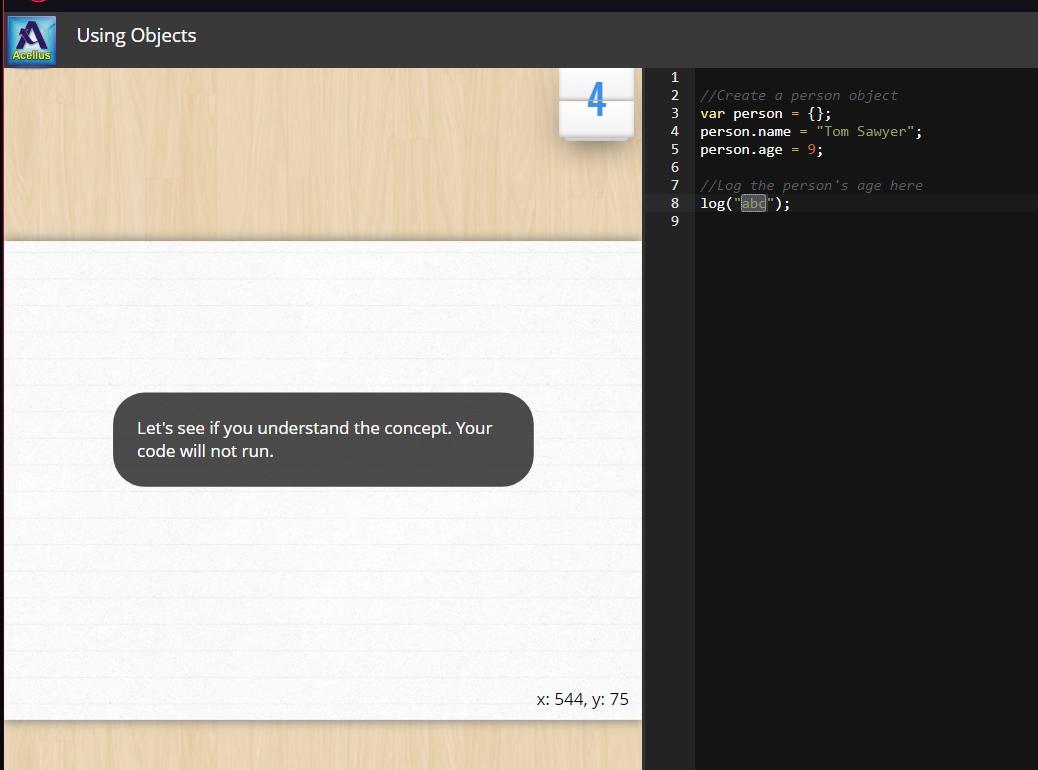
Answers
Answer:
vauwnwkwiauauwiajhwbwbw
20 Points and Brainliest!!!!!!
Select the correct answer.
Amara is designing a website to encourage people in a city to vote in local elections. She wants to include a web page that shows first-time voters the steps to follow to register and vote in the elections. How can Amara best use multimedia to show the voting process on the web page?
A.
by providing a paragraph of instructions with pictures
B.
by providing an audio file along with downloadable pictures
C.
by creating a brief animation with optional text instructions
D.
by creating a static slideshow of the steps showing just pictures
E.
by adding automatically playing audio with text instructions
Answers
Answer:
I think E, sorry if I'm wrong.
Answer:
I think it might be C
Explanation:
Design a program that gives simple math quizzes. The program should display two
random numbers that are to be added, an example is:
247
+ 129
The program should allow the student to enter the answer. If the answer is correct,
a message of congratulations should be displayed. If the answer is incorrect, a message showing the correct answer should be displayed.
In bash shell script, please.
Answers
Answer:
Explanation:
#!/bin/bash
# Generate two random numbers between 1 and 100
num1=$((1 + RANDOM % 100))
num2=$((1 + RANDOM % 100))
# Print the math problem
echo "$num1"
echo "+ $num2"
echo ""
# Read the user's answer
read -p "Enter your answer: " answer
# Calculate the correct answer
correct=$((num1 + num2))
# Check if the answer is correct
if [ "$answer" -eq "$correct" ]; then
echo "Congratulations, your answer is correct!"
else
echo "Sorry, the correct answer is $correct."
fi
Your name is Blake Jackson. You are the penetration tester for a small corporate network. After performing several SQL injection attract test on the corporate network, you have decided to see how secure your own online bank's web page is. In this lab, your task is to perform a simple SQL injection attack using the following information: Your bank's URL: MySecureOnlineBank Make an account query using your account number of: 90342 Answer Question 1. Perform a simple SQL attack using: 0 OR 1
Answers
Website developers and organizations take measures to prevent SQL injection attacks by implementing security best practices, such as parameterized queries or input validation. As a penetration tester, it is crucial to assess and report vulnerabilities responsibly, adhering to the defined scope and guidelines provided by your organization.
Performing a SQL injection attack on a website without proper authorization is illegal and unethical. It is essential to obtain explicit permission from the website owner and follow legal and ethical guidelines before conducting any security assessments or penetration testing.
If you are a penetration tester performing authorized tests on your online bank's web page, you should follow the guidelines and scope defined by your organization. Typically, penetration testing is conducted within a controlled environment with the necessary permissions and safeguards.
To answer your question and provide some guidance, a simple SQL injection attack using the provided information can be constructed as follows:
URL: MySecureOnlineBank
Account query using account number: 90342
SQL injection attack: 0 OR 1
In a vulnerable scenario, this SQL injection attack attempts to manipulate the SQL query to return unintended or unauthorized results. The "0 OR 1" payload aims to inject a condition that is always true, bypassing the original query's intended logic. The injected condition could potentially retrieve data from the database, even if it is not intended to be accessible.
However, it's important to note that website developers and organizations take measures to prevent SQL injection attacks by implementing security best practices, such as parameterized queries or input validation. As a penetration tester, it is crucial to assess and report vulnerabilities responsibly, adhering to the defined scope and guidelines provided by your organization.
Remember, unauthorized and unethical attempts to exploit security vulnerabilities can have legal consequences and may cause harm to individuals or organizations. Always ensure you have proper authorization and adhere to ethical standards when performing security assessments or penetration testing.
Learn more about validation here
https://brainly.com/question/32129966
#SPJ11