Vocabulary List
precipitate
descent
ascent
maneuver
contemplate
enveloped
nucleus
exertion
perilous
manifestly
perpendicular
predicament
Answers
.sjjejekeiwiwkkskskdidieiiei
Related Questions
This is r programming
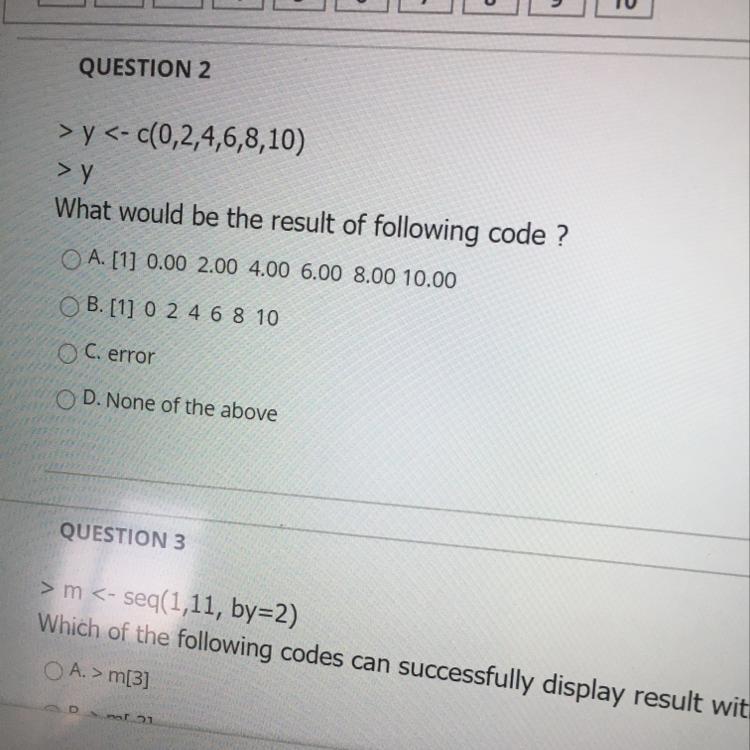
Answers
Answer:a
Explanation:
what is the answer i need them now pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls

Answers
Answer: Insert ribbon > table drop down menu
Explanation:
Answer:Insert ribbon > table drop down menu
Explanation:
1. What do you think is the most important event in the history of the internet? What event has had the biggest impact on your daily life?
Answers
Answer:
The biggest event in internet history was YuTubers punching each other in the face. Months of hype came to a peak Saturday for the self-declared “biggest event in internet history” a boxing match between two YuTube celebrities in Manchester, England.
Explanation:
There is no particular event but the whole journey till now which shaped my personality. Every person even if they are the worst has something good in them.
The impact it has had:
Developed into the globally used Internet which is now integrated into modern society and is seen as an essential for good quality of life.
FREE BRAINLIST FOR RIGHT ANSWER
Question 1(Multiple Choice Worth 5 points)
(03.03 LC)
Which type of chart or graph uses vertical bars to compare data?
Column chart
Line graph
Pie chart
Scatter chart
Answers
Answer:
Column Chart
Explanation:
what are some basic commands to remember in terminal? windows 10
please help if you know
Answers
Answer:
If you just need a few, maybe this can help.
Explanation:
Cat - The cat command means 'Concatenate'. It prints the contents of a file or files to stdout. It's frequently used in Linux commands.
Touch - Using the 'Touch' command, you can create a file, or possibly just modify or generate a timestamp.
Move - The 'mv' command stands for 'Move'. As the name says, we can use this command to move files and directories from one place to another.
Chsh - The chsh command changes a user's login shell attribute. If you want to change the shell of another user, execute the command with root permissions.
Sudo - 'Sudo', or 'super user do', is a command that allows you to elevate your user privileges while executing the command to administrator privileges.
Most files in Windows are associated with a specific program that is assigned to open the file by default. At times, remembering these associations can become confusing. You can remind yourself by entering the command assoc to display a full list of filename extensions and program associations. You can also extend the command to change file associations. For example, assoc .txt= will change the file association for text files to whatever program you enter after the equal sign. The assoc command itself will reveal both the extension names and program names, which will help you properly use this command.
In Windows 10, you can view a more user-friendly interface that also lets you change file type associations on the spot. Head to Settings (Windows + I) > Apps > Default apps > Choose default app by file type
2.Cipher
Deleting files on a mechanical hard drive doesn't really delete them at all. Instead, it marks the files as no longer accessible and the space they took up as free. The files remain recoverable until the system overwrites them with new data, which can take some time. The cipher command, however, lets you wipe a directory on an NTFS-formatted volume by writing random data to it. To wipe your C drive, for example, you'd use the cipher /w:d command, which will wipe free space on the drive. The command does not overwrite undeleted data, so you will not wipe out the files you need by running this command.
When you run the cipher command by itself, it returns the encryption state of the current directory and the files it contains. Use cipher /e: to encrypt a file, cipher /c: to retrieve information about encrypted files, and cipher /d: to decrypt the selected file. Most of these commands are redundant with the Windows encryption tool BitLocker.
3.file Compare
You can use this command to identify differences in text between two files. It's particularly useful for writers and programmers trying to find small changes between two versions of a file. Simply type fc and then the directory path and file name of the two files you want to compare.
You can also extend the command in several ways. Typing /b compares only binary output, /c disregards the case of text in the comparison, and /l only compares ASCII text.
So, for example, you could use the following:
fc /l "C:\Program Files (x86)
The above command compares ASCII text in two Word documents.
4.Ipconfig
This command relays the IP address that your computer is currently using. However, if you're behind a router (like most computers today), you'll instead receive the local network address of the router.
Still, ipconfig is useful because of its extensions. ipconfig /release followed by ipconfig /renew can force your Windows PC into asking for a new IP address, which is useful if your computer claims one isn't available. You can also use ipconfig /flushdns to refresh your DNS address. These commands are great if the Windows network troubleshooter chokes, which does happen on occasion.
5.Netstat
Entering the command netstat -an will provide you with a list of currently open ports and related IP addresses. This command will also tell you what state the port is in; listening, established, or closed.
This is a great command for when you're trying to troubleshoot devices connected to your PC or when you fear a Trojan infected your system and you're trying to locate a malicious connection.
6.Ping
Sometimes, you need to know whether or not packets are making it to a specific networked device. That's where ping comes in handy.
Typing ping followed by an IP address or web domain will send a series of test packets to the specified address. If they arrive and are returned, you know the device is capable of communicating with your PC; if it fails, you know that there's something blocking communication between the device and your computer. This can help you decide if the root of the issue is an improper configuration or a failure of network hardware.
7.PathPing
This is a more advanced version of ping that's useful if there are multiple routers between your PC and the device you're testing. Like ping, you use this command by typing pathping followed by the IP address, but unlike ping, pathping also relays some information about the route the test packets take.
How does a resident virus differ from a non-resident virus? !!!25 POINTS!!!!!
A) Resident viruses simply disrupt operations while non-resident viruses will control hosts.
B)Resident viruses will control hosts while non-resident viruses simply disrupt operations.
C)Resident viruses find networks to infect while non-resident viruses load themselves into memory.
D)esident viruses load themselves into memory while non-resident viruses find networks to infect.
Answers
Answer:
The correct answer is **D)** Resident viruses load themselves into memory while non-resident viruses find networks to infect. A resident virus is a type of computer virus that’s deployed and resides within a computer’s random access memory (RAM). A non-resident computer virus, on the other hand, is a type of computer virus that doesn’t reside within a computer’s RAM. Non-resident computer viruses can still be deployed within RAM, but they don’t stay there.
What will be the result of the following lines of CSS?
body{
background-color:yellow;
}
A.
The background of the header will be yellow.
B.
The text will be highlighted yellow.
C.
The background of the body of the webpage will be yellow.
D.
The photo will change to a yellow box if the user clicks on the photo.
Answers
Answer:
C.
Explanation:
The correct option that explains the result of the given lines of CSS is:
C. The background of the body of the webpage will be yellow.
The CSS code provided sets the background color of the body element to yellow. The "body" selector targets the entire body of the webpage, and the "background-color" property sets the background color to yellow. This means that the background of the entire webpage will be displayed in yellow.
Answer:
C. The background of the body of the webpage will be yellow.
What is the study of computers and computing including their theoretical and algorithmic foundations, hardware and software, and their uses for processing information called?
Question 1 options:
Information Technology
Computer Science
Computer Engineering
Software Engineering
Answers
What two types of devices have a keyboard integrated into the screen?
Question 1 options:
laptops and smartphones
tablets and electric typewriters
typographers and tablets
tablets and smartphones
Answers
Answer:
tablets and smartphones
Explanation:
Have a good day!
THE FIRST PERSON THAT ANSWER THIS QUESTION GETS 18 POINTS AND BRAINLY!!!!!
You are creating an online form for a streaming music service. Users will need to enter at what point they want their contract to end. Which data type should you use?
Boolean
char
date
string
Answers
Answer:
data
Explanation:
PLEASE HELP ME Write a 150-word paragraph about five of the zaniest and/or most novel ways you’ve found online that people earn incomes. Keep in mind that the sites should not be corporate sites. We are looking for unique niches. Have fun. We think you will be surprised when you see what people are willing to pay for online.
Answers
Answer: Disney and video games winning ratings can produced a vast amount of money, making into a job, that anyone could create for example becoming an actor or becoming a gamer.
we could go over the amount of time disney and other companies spent.
can someone describe how sampling is used to capture audio on a computer?
please make it easy I am struggling. Im in 7th.
Answers
Answer: Sampling is a method of converting an analogue audio signal into a digital signal.
Explanation:
While sampling a sound wave, the computer takes measurements of this sound wave at a regular interval called sampling interval. Each measurement is then saved as a number in binary format.
Hey can someone help?
What is something you do to judge the credibility of websites, videos, or information you come across online?
Answers
who want to go on scratch
I really need people to favorite and like my projects
Answers
Answer:
Sure
Explanation:
give me a random piece of Binary code to translate
Answers
Answer:
100110
Explanation:
Answer:
01001000 01000001 01001000 01000001 00100000 01000011 01001111 01001101 01010000 01010101 01010100 01000101 01010010 01010011 00100000 01010111 01001001 01001100 01001100 00100000 01010010 01010101 01001100 01000101 00100000 01010100 01001000 01000101 00100000 01010111 01001111 01010010 01001100 01000100
Give three examples of ethical or legal issues that an IT professional may encounter and the negative consequences of these issues.
Answers
Answer:
1. Private Informations being leaked.
2. Hackers that hacks accounts.
3. Computer Viruses obtained by clicking spam messages.
Explanation:
1. They can turn down the leaked informations by logging to it, legally.
2. IT Professionals could hack the hacker, or outsmart them.
3. Some people can stop Computer Viruses, but IT Professionals can prevent it much better than them.
I hope that my answer helped you. Thank you, and good luck.
The three examples of ethical or legal issues that an IT professional may encounter are:
Privacy violationsCybersecurity breachesIntellectual property violationsWhat are the negative consequences of the issues with IT professional?In Privacy violations: IT professionals may be faced with ethical dilemmas related to the collection, use, and protection of personal data. If personal data is not handled responsibly, it can lead to privacy violations, loss of trust, and potential legal consequences.
In Cybersecurity breaches: IT professionals are responsible for protecting the security of systems and data, and failure to do so can result in cybersecurity breaches that can have serious consequences, such as data loss, financial damage, and reputational harm.
Therefore, in Intellectual property violations: IT professionals may be faced with ethical issues related to the use of copyrighted or patented materials. If these materials are used without permission, it can result in legal consequences and damage to the reputation of the IT professional and their organization.
Learn more about IT professional from
https://brainly.com/question/6947486
#SPJ1
You need to find information about your system. Record the utility you used, then fill out the information you found in the table.
Device
Operating System
Utility Tool
RAM
Processor Type
Processor Speed
Answers
Answer:
utility tool, operating system and processor type, and processor speed
Explanation:
Answer:
Hello there!
Explanation:
So, assuming you are using Windows 7 and higher, I should be able to help you.
You will need two tools, one of them being control panel, and the other one being msinfo32.
Start off with control panel. Go down to your folder icon, go to it, and it should bring up an explorer window. If you see, This PC, or, My Computer, right click on it and go to properties.
This will show you what your computers specs are, the first image shown below is what you should see, or something like it, let's use my computers specs for an example.
Operating System, Windows 8.1 Pro.
RAM, 16.0 GB, 15.9 GB usable.
Processor and Speed, Intel R Core TM i5-4590 CPU 3.30GHz.
You've now completed 4 tasks. You'll want to close out of the control panel window and now on your keyboard, press the Windows key + R button at the same time. This should bring up a run box on the left hand side of your computer. In that run box, you need to type, msinfo32 . This will bring up a System Information Tool.
Instead of looking for Device, look for System Manufacturer and System Model. This will be around the top.
As mine is used for an example again.
System Manufacturer, Hewlett-Packard.
System Model, HP ProDesk 600 G1 SFF.
And there you go, and one last thing before you have an amazing day, the tools that you have used are Control Panel and msinfo32.
Have a wonderful day, and hope I helped you out.

If you created a variable called name, what data type would that value be? Group of answer choices a float a string a Boolean an integer
Answers
I think its an integer
Answer:
a float
Explanation:
THis took FOREVER! please go check it out, if you have seen my demo to this game, you will like the full version! https://scratch.mit.edu/projects/485122429/
Answers
Answer:
Sure! I'll comment in the comments of this answer on how it was <3
Answer:
The game is great good job!!
Explanation:
Which of the following describes a hardware error? Select 3 options.
-Nothing happens when you press the Power button on your desktop PC.
-Nothing happens when you press the spacebar on your keyboard, but the other keys are working.
-Every time you try to run your new game, it crashes after displaying the opening screen.
-The mouse pointer on-screen only moves horizontally, not vertically.
-After a recent Windows update, you can no longer access the internet on your laptop.
Answers
Answer: opinion 4 and 5
Explanation:
Answer:
Nothing happens when you press the Power button on your desktop PC.
The mouse pointer on-screen only moves horizontally, not vertically.
Nothing happens when you press the spacebar on your keyboard, but the other keys are working.
Explanation:
Edge 2023

Match the letter with the feature it represents.
Put responses in the correct input to answer the question.
slide pane
menu bar
drawing toolbar
slide (normal) view
task pane
formatting toolbar
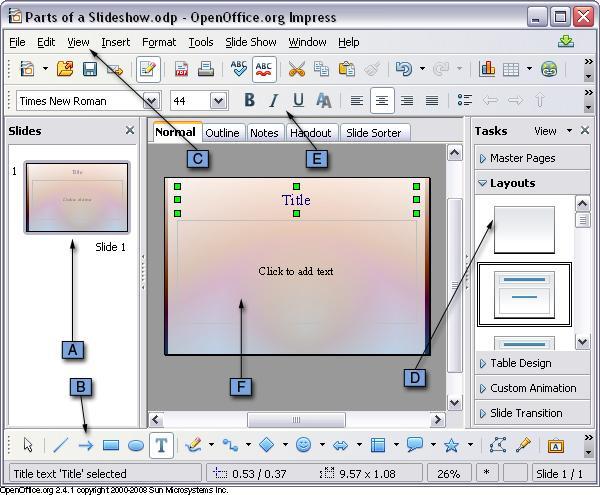
Answers
B is drawing toolbar
C is menu bar
D is task pane
E is formatting toolbar
F is slide normal view
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2
How can you have a safe browsing experience?
Enable JavaScript in your web browser.
Select the option to delete cookies when you close the browser.
Click pop-up advertisements to download software.
Enable automatic download of software whenever the vendor offers a new update.
Disable automatic completion of username and passwords.
Answers
Answer: Disable automatic completion of username and passwords or Select the option to delete cookies when you close the browser.
Explanation: The rest aren't safe. If it's a one choice go with Disable automatic completion of username and passwords
Organisms are classified as producers or consumers acorrding to the way they
A)obtain
B)release wastes
C)produce offspring
D)move from place to place
Answers
as the rest are irrelevant to the given options and cannot be classified as release waste produce offspring or move from place to place are classifications of biotic or abiotic
Select the correct answer.
What is Hypertext Transfer Protocol?
A.
the language used to build web pages
B.
a set of rules that allows for exchange of information on the web
C.
the language used by computers to exchange information on the web
D.
a set of rules that defines what search engines can do
Answers
I dont really know sorry
Write an algorithm for a program which inputs the lengths a, b and c of the three
sides of a triangle. The program then determines whether the triangle is right-angled
and prints out a message to say whether or not the triangle is right angled. You may assume that a is the longest side. The triangle is right-angled if a2 = b2 + c2
I’m really stuck with this and need help asap
Answers
Hello,
Answer:
--//Triangles AlgorithmDeclare the variables of the side of each triangle, in this case, a, b, and c, and input them.
If a^2 == b^2 + c^2
display "This triangle IS right-angled."
Else
display "This triangle is NOT right-angled
Explanation:
The meaning of the word "algorithm" in this situation would be the coding of the program that you are assigned to create. I'll use Python in this. Display, in this case, will mean "print"
Answer:
Triangles algorithm
IF a^2 == b^2 + c^2
then display is to the right
IF it is anything else then display not to the right.
Experts believe robots and AI will continue taking over many of the human jobs we know today. What changes should be made to K-12 education to ensure students are prepared for the future? What courses or skills should be added? WHat should be removed? Why?
Answers
Answer:
I think they should show one subject per month so students are more prepared
Answer: some changes that should be made are dresscode , some courses should be more sports . Nothing should be removed because the kids in the future need to learn more .
Explanation:
A bicycle is probably not a computer because it does not
have a screen
require electricity
use information to solve a problem
use the internet
Pls anwser quick
Answers
In 3–5 sentences, describe how technology helps business professionals to be more efficient.
business and computer science
Answers
Technology helps business professionals, keep more organized, communicate better, and effectively keeps businesses secure. Technology helps keep employee information and business paper work more organized using computers and software; while making it easier to communicate with employee's using e-mail and memo's.
if wrong sry :(
Answer:business and computer science
teck computer
What feature did the 32X add to the Sega Genesis?
A. It allowed the console to run 32 games per cartridge.
B. It allowed the console to run 32-bit cartridges.
C. It added 32 color schemes to the games playable on the console.
D. It increased the graphic quality of the games by 32 times.
Answers
Answer:
I think it is D
Explanation:
It is because the older generation of game run games in far worse graphic quality than Sega mega drive