What did the executive branch create?
Answers
The Convention's participants feared giving one individual an excessive amount of power. By incorporating a system of checks and balances into the Constitution, they ultimately created the executive branch, giving rise to our current system of a single President.
What did the executive branch do?The appointment of a President of the United States of America in Article II of the Constitution establishes the executive branch's powers. The first paragraph of Article II states:The executive Power will be held by the President of the United States of America. He will be elected[,] along with the Vice President, who will also be chosen for the same term, and hold office for a period of four years.The idea of a nation with a president who served a finite term was completely novel at the time the Constitution was created because the majority of the European nations were still monarchs. However, the restricted term was implemented in part as a response to the monarchy of Europe, where one person maintained entire power for an undetermined period of time.The President has certain authorities under Article II of the Constitution. In addition to being the Commander in Chief of the US Armed Forces, he or she can pardon US citizens who have committed crimes against the country, with the exception of impeachment, albeit these pardons must first be granted by Congress. As well as selecting Supreme Court justices, the President also appoints ambassadors. The President's whole scope of authority is outlined in Article II. Among other duties, the President must, among other things, inform Congress on the status of the Union on a regular basis and ensure that laws are faithfully carried out.To Learn more About executive branch refer to:
https://brainly.com/question/838027
#SPJ4
Related Questions
_____ are hand- or computer-created, single-sheet visuals intended to be attached to a wall or displayed on an easel.
Answers
Posters are hand- or computer-created, single-sheet visuals intended to be attached to a wall or displayed on an easel.
They are commonly used for advertising, marketing, informational, educational, or decorative purposes. Posters can be made using various materials, including paper, vinyl, fabric, or plastic, and can be printed using different printing techniques, such as offset printing, digital printing, or screen printing. Posters can come in various sizes, from small handbills to large billboard-sized prints. They can feature text, graphics, photographs, or a combination of all three, and can be designed in a wide range of styles, from minimalist to highly artistic.
Posters can be used for a variety of applications, such as promoting events, advertising products or services, informing the public about important issues, or as decorative elements in homes, offices, or public spaces.
Learn more about visuals here:
https://brainly.com/question/23995556
#SPJ11
In an environment that makes use of front-end data marts, the front-end data mart component in such an environment provides which type of business intelligence/reporting/analytics?
Answers
The front-end data mart component in an environment that makes use of front-end data marts provides ad-hoc analysis, reporting, and querying capabilities for business intelligence.
A front-end data mart is a sub-component of a data warehouse that contains a subset of an organization's data, which has been pre-summarized, aggregated, and filtered to address the specific information requirements of a particular business unit or department within the organization. :In an environment that makes use of front-end data marts, the front-end data mart component provides ad-hoc analysis, reporting, and querying capabilities for business intelligence. This is because it contains a subset of an organization's data, which has been pre-summarized, aggregated, and filtered to address the specific information requirements of a particular business unit or department within the organization. Front-end data marts are designed to be used by end-users and business analysts, rather than IT professionals or data scientists.
They are used to support operational decision-making, rather than strategic decision-making. Front-end data marts are typically created using data extraction, transformation, and loading (ETL) tools, which are used to extract data from one or more sources, transform it into a common format, and load it into the data mart. The data in a front-end data mart is organized into dimensions and measures, which are used to support ad-hoc analysis, reporting, and querying. Dimensions are the attributes or characteristics that describe the data, such as time, location, or product. Measures are the numeric values that are used to perform calculations or aggregations, such as sales, revenue, or profit. front-end data marts provide end-users and business analysts with the ad-hoc analysis, reporting, and querying capabilities they need to support operational decision-making.
To know more about front-end data visit:
https://brainly.com/question/19921481
#SPJ11
Helppppp meeeeee eee
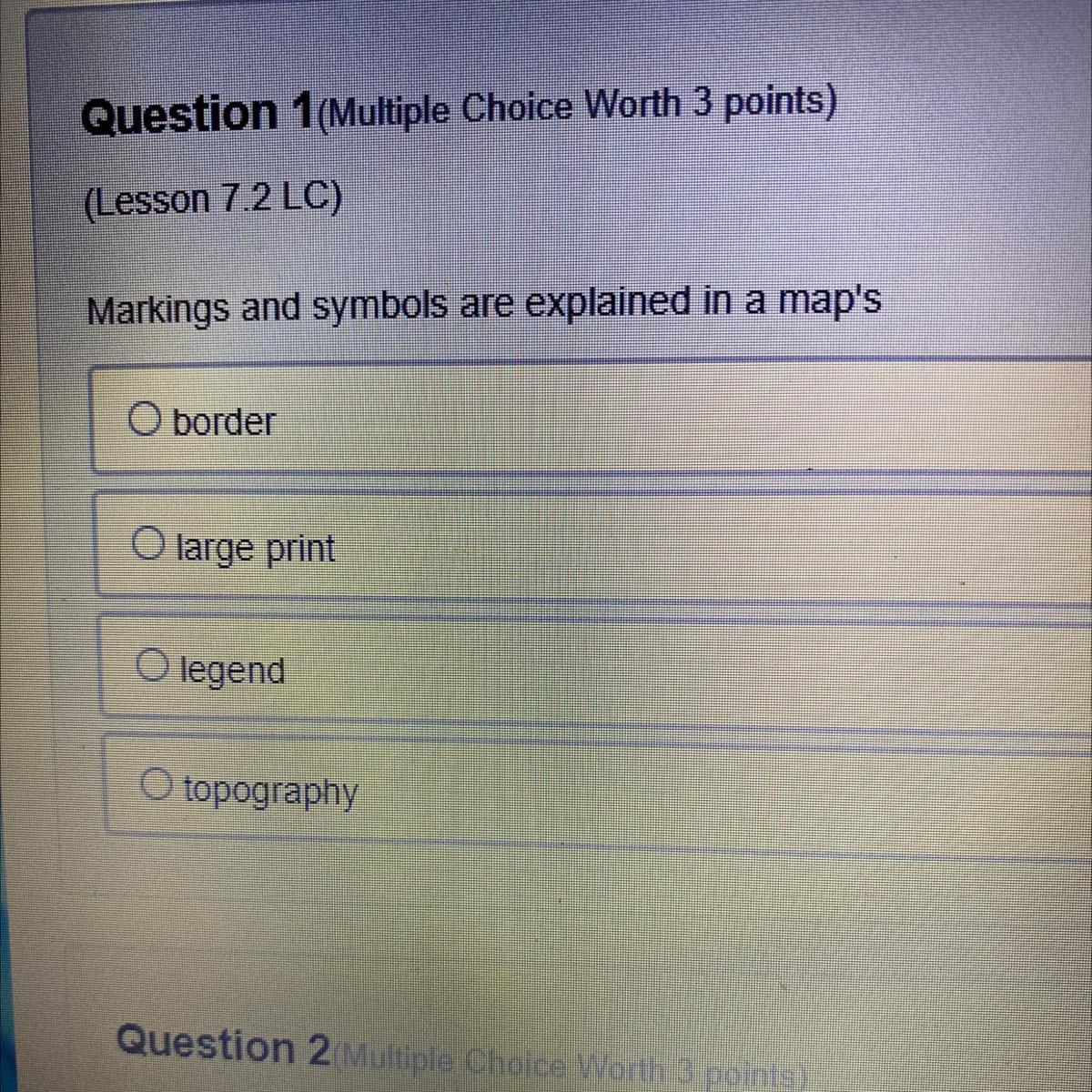
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
What is the final screen of computer called
Answers
Answer:
Monitor or display
Explanation:
Answer:
desktop is the correct answer. Please follow me and please mark my answer as a brainliest. ❤❤❤❤Peter took a selfie in his room. He was a wearing a light blue shirt. But he failed to realize that that shirt would clash in color with the light blue walls in his room. He wants to edit this photo using editing software. Which tool can Peter use to darken the background in his photo?
Answers
Answer:
A wand tool is to do that in an editing software.
Answer: Peter should use the burn tool
Martha is a network monitoring technician working on a firewall for her companyâs network. To filter traffic going through the firewall, she should
A) select Firewall first and Rules after
B) select the Floating icon on the firewall first
C) select WAN first and set firewall rules after
D) select Protocol first and Firewall after
Answers
She should (A) pick Firewall first, then Rules. Firewalls examine packets for malicious software or possible attacks that have previously been designated as known dangers. If a number of packets is reported & found to be a security concern, the firewall blocks it from accessing the network or accessing your computer.
What exactly are firewall filtering rules?
Network packets are allowed or denied by packet filtering firewalls depending on the following criteria:
The origin's IP address indicates where and how the packet is being transmitted from.
The packet's destination is the recipient IP address.
Protocols include data transmission mechanisms such as session and program protocols (TCP, UDP, ICMP).
To know more about computer click here
brainly.com/question/15709585
#SPJ4
Off distance grid cut off is characterized by which of the following.?
A. The top of the image is underexposed
B. Both sides of the image are underexposed
C. One side of the image is underexposed
D. The bottom of the image is underexposed
Answers
Off distance grid cut off is characterized by one side of the image being underexposed. Therefore, the correct answer is option C.The term "cut off" refers to a situation where the film, plate, or sensor area has failed to receive the entire image projection; the light from one or both edges of the camera lens does not reach it.
There is a partial loss of the visual data on one side of the resulting image. This issue is primarily seen in the case of aerial photographs that have been taken from a plane or other remote location where the camera is mounted and triggered automatically.In summary, the off distance grid cut off is a type of photographic error that is caused by one side of the image being underexposed.
To know more about characterized visit:
https://brainly.com/question/30241716
#SPJ11
Name of the best Android keyboard
Pls I need it asap!! For educational purpose
I need your Ideologies
Answers
I think Gboard is good, you can switch between languages quickly and you can translate in real time. Translation is not perfect, but it is the best translation available. Vocabulary and autocorrect is not bad too. You can change the background. It has some themes of its own, but you can always customise it with your own photo. It has instant gif, stickers and emoji options too. It also has a good collection of symbolic emojis like: *\0/*O_o(๑♡⌓♡๑)ᕙ( • ‿ • )ᕗ(☉。☉)!I cannot include all of them, they are in 100s.
But if you are looking for a solution for grammatical mistakes, then you may want to consider Grammarly.
\(\boxed{\underline{\bf \: ANSWER}}\)
Well, just like the person before me has answered ; I prefer Gboard, a keyboard provided by Go.ogle over all the other options ones available while using android. As you can see in the attached picture, I use Gboard & have been using it for quite a lot of years now as well. Gboard provides smooth surface for typing & there's glide technology as well. There's an option to pin your clipboard (which I find really helpful) & tons of built-in emojis, emoticons (this feature is not available in many), GIFs & so on. Also you can customize your keyboard by changing themes (you can either select one of the many backgrounds they have or choose one you like; in my case I have a blue scenery clipart as my background which matches my phone's overall theme). You can also use Gboard if you prefer to text in more than 1 language (this feature is available in many other keyboards as well though).
Now moving on, I would suggest the Samsung Keyboard too (that is, of you are using Samsung gadgets). The only reason I prefer Gboard over this keyboard is because you can't customize Samsung Keyboard (you can only choose White/Dark mode). Also, emoticons aren't available.
Then at last, there's the Grammarly Keyboard. This keyboard is really good if you are looking for writing essays, paragraphs or speeches as it catches all your grammar errors. But at times, it can be a bit too much & the keyboard is not overall smooth to use (at least for me).
So there, these 3 are the best keyboards for Android users.
_____
Hope it helps.
RainbowSalt2222

What are some details about the Elk cloner computer virus??
Answers
Marissa is designing a web page that features lessons on how to build cabinets. how can she make the page most engaging for the user?
A. by adding warm colors to make the content more fun to view.
B. by adding a short video demonstrating how to build cabinets.
C. by adding a variety of font types to make the text look appealing.
D. by adding a slideshow that displays pictures of built cabinets.
Answers
The IT manager has asked you to create four new VLANs for a new department. As you are going through the VLAN configurations, you find some VLANs numbered 1002-1005. However, they are not in use.What should you do with these VLANs?
Answers
When going through the VLAN configurations numbered 1002-1005 which are not in use. what to do? The best course of action is to remove VLANs numbered 1002-1005.
These VLANs are part of the default VLANs and are not usable for normal use. VLANs 1002 through 1005 are the FDDI defaults, Token Ring defaults, and FDDI and Token Ring defaults for VLAN 1, respectively. None of these VLANs may be removed.VLANs are created and deleted using the VLAN configuration subcommand of the switch. VLAN IDs range from 1 to 4094, and not all numbers are created equal. These numbers are reserved for special purposes or are predefined by the IEEE. VLANs that are not in use should be removed, and VLANs that are in use should not be removed to maintain a clean and concise VLAN configuration. For proper VLAN configuration, users must define the VLAN's name, description, and ID number. VLANs can also be added to other switch configurations such as interfaces, IP addressing, and security policies.
Learn more about VLAN here: https://brainly.com/question/28635096
#SPJ11
in the windows server 2016 interface, which type of tile displays content that changes dynamically?
Answers
In the Windows Server 2016 interface, "live tile" type of the tile displays content that changes dynamically.
In Windows Server 2016 interface, 'Live Tiles' are designed to show 'Live information' in the Start Menu. The purpose of the Live Tiles is to change the content dynamically. This automatically updating information could be users latest photos, calendar events, breaking news stories, or email messages.
Therefore this is stated that it is the type of Live Tiles in Windows Server 2016 interface that dynamically change or update contents to be displayed.
You can learn more about Windows Server at
https://brainly.com/question/14526761
#SPJ4
1. what are the steps for transforming a data model into a database design?
Answers
The process of transforming a data model into a database design involves include identifying entities and relationships, defining attributes and data types, establishing primary and foreign keys, normalizing the data, and considering performance and optimization factors.
The first step in transforming a data model into a database design is to identify entities and their relationships. This involves analyzing the requirements and determining the main entities and their associations. Entities represent real-world objects or concepts, while relationships define the connections between these entities.
The next step is to define attributes and data types for each entity. Attributes represent specific properties or characteristics of an entity, and data types determine the format and range of values for these attributes. This step helps in structuring the data properly and ensuring its integrity and consistency.
Once attributes are defined, the third step involves establishing primary and foreign keys. A primary key is a unique identifier for each entity instance, while foreign keys create relationships between entities. Primary and foreign keys help maintain data integrity and enable efficient querying and retrieval of information.
After defining keys, the next step is to normalize the data. Normalization is the process of organizing data into tables to eliminate redundancy and ensure data consistency. This step involves applying normalization rules to identify dependencies and create tables that minimize data duplication and update anomalies.
Lastly, during the transformation process, it is important to consider performance and optimization factors. This involves optimizing the database design for efficient storage, retrieval, and manipulation of data. Techniques such as indexing, partitioning, and denormalization may be employed to enhance performance based on the specific requirements of the application.
By following these steps, a data model can be effectively transformed into a well-designed and efficient database structure that meets the requirements of the intended application.
Learn more about database here:
https://brainly.com/question/30163202
#SPJ11
the type of layout which is used to achieve a smooth and rapid flow of large volumes of output is: group of answer choices a. process layout (functional layout) b. product layout (flow line layout) c. project layout (fixed-position layout) d. batch e. unit
Answers
The type of layout that is designed to achieve a smooth and rapid flow of large volumes of output is known as the product layout or flow line layout.
The type of layout which is used to achieve a smooth and rapid flow of large volumes of output is the product layout (flow line layout). In a product layout, the equipment and processes are arranged in a sequence that is optimized for the production of a particular product. This layout is often used in industries such as automotive manufacturing, where a large volume of products are produced using a standardized process. The layout allows for a continuous flow of materials and products, which can increase efficiency and productivity.
In a product layout, the production process is organized in a linear sequence, where each step of the process is designed to add value to the product. The layout is designed to minimize material handling and transportation time, reduce production lead times, and optimize the use of resources. This is achieved by positioning equipment, workstations, and materials in a way that allows for the most efficient and streamlined flow of products through the production process.
One of the key benefits of a product layout is its ability to handle a high volume of output with a low level of skill and training required for the workers. This is because the tasks are repetitive and specialized, which means that workers can be trained to perform a specific task and become highly proficient at it.
Another advantage of a product layout is that it can be easily scaled to increase production capacity. By adding more machines and workstations, the production output can be increased without significant changes to the layout or process.
Overall, the product layout is ideal for high-volume production of standardized products where efficiency, productivity, and cost-effectiveness are critical factors.
Learn more about manufacturing layout here:
https://brainly.com/question/13740503
#SPJ4
Describe how each command is used by matching the command to its purpose.
removes data fror
places it on the cli
Paste
cancels a previou
Undo
restores a previou
Copy
duplicates data a
clipboard
Cut
Redo
places data in its
Answers
Answer:
The correct answer to this question is given below in the explanation section.
Explanation:
The correct command matches its use are given below:
Paste Places data in its
Undo Cancel a previous
Copy Duplicates data on the clipboard
Cut Removes data for places it on the clipboard
Redo restores a previous
Paste term is used when you are placing copied data. Undo is used to cancel a previous action performed while Redo is used to restores a previously performed action. The copy is used to duplicate data on the clipboard while Cut is used to removes data for places/ to paste somewhere else.
What are the number of buttons on an average calculator?.
Answers
Answer:
56
Explanation:
There is 56
Pick the diagrams that are part of the UML set of diagrams.
Answers
The UML (Unified Modeling Language) set of diagrams includes several types of diagrams that are used for modeling different aspects of a software system.
Some of the most commonly used UML diagrams are:
1. Class diagram - This diagram shows the classes and their relationships in a software system. It is used to model the static structure of the system.
2. Use case diagram - This diagram shows the interactions between the system and its users. It is used to model the functional requirements of the system.
3. Sequence diagram - This diagram shows the interactions between the objects in the system over time. It is used to model the dynamic behavior of the system.
4. State diagram - This diagram shows the states that an object can be in and the transitions between them. It is used to model the behavior of an individual object.
5. Activity diagram - This diagram shows the activities that take place in the system and their relationships. It is used to model the workflow of the system.
The types of diagrams that are part of the UML set. Other types of diagrams include component diagrams, deployment diagrams, and communication diagrams, among others. Each type of diagram serves a specific purpose and is used to model a different aspect of the system. By using these diagrams, developers and stakeholders can gain a better understanding of the system and its behavior, and can communicate their ideas more effectively.
To know more about software system visit:
https://brainly.com/question/31228213
#SPJ11
name two different colors used in the python program file window.name the type of program content that has each color ......
whoever answer this correct i will rate them 5 stars and a like .....
please urgent
Answers
In the Python program window, black is used for code and syntax, while white is used as the background.
How is this so?1. Black - The color black is typically used for the program's code and syntax. It represents the actual Python code and includes keywords, functions, variables, and other programming constructs.
2. White - The color white is commonly used as the background color in the program window. It provides a clean and neutral backdrop for the code and makes it easier to read and understand.
Learn more about python program at:
https://brainly.com/question/26497128
#SPJ1
what is output?
x=2
y=3
print (x*y+2)
A. 4
B. 8
C. 2
D. 10
Answers
Answer:
The output is 8 so the answer is B
((2*3)+2)=(6+2)=8
The ________ is the biggest power consumer on a mobile computing device. display CPU memory module hard drive
Answers
Answer:
CPU (Central Processing Unit)
HOW DO I TURN THE CAPS LOCK OFF???? PLEASE HELP IT WONT STOP!!!!
Answers
Answer:
Press the caps lock key
Explanation:
In the first instance of multiple encryption plaintext is converted to __________using the encryption algorithm.
Answers
In the first instance of multiple encryption, plaintext is converted to ciphertext using the encryption algorithm.
Multiple encryption is the process of encrypting a message multiple times with different encryption keys or algorithms to enhance security. In the first round of encryption, the plaintext is transformed into ciphertext using an encryption algorithm, such as AES or RSA.
Multiple encryption involves encrypting the plaintext message more than once using different keys or algorithms. In the first instance, the plaintext is converted to ciphertext by applying an encryption algorithm. This ciphertext can then be encrypted further in subsequent instances to increase the security of the data.
To know more about Plaintext visit:-
https://brainly.com/question/30876277
#SPJ11
Python String Functions: Create a new Python Program called StringPractice. Prompt the user to input their name, then complete the following:
Length
• Print: “The length of your name is: [insert length here]”
Equals
• Test to see if the user typed in your name. If so, print an appropriate message
Really appreciate the help.
Answers
#Swap this value by your name. Mine is Hamza :)
my_name = "Hamza"
#Get input from user.
inp = input("What's your name?: ")
#Print the length of his/her name.
print("The length of your name is",len(inp),"characters.")
#Check if the input matches with my name?
#Using lower() method due to the case insensitive. Much important!!
if(inp.lower()==my_name.lower()):
print("My name is",my_name,"too! Nice to meet you then.")
What is the size of BIOS?
Answers
Answer:
The size of BIOS is 32 megabytes

Answer:
32 megabytes
Explanation:
1-5 Safety measures in the use of kitchen tools and equipment.
Answers
Answer:
Safety measures are as follows;
Explanation:
Hold the delicate instruments cautiously to use them.Require appropriate use of the equipment in the kitchen.Users should remove these defective instruments or discard of them.During and before use, check that perhaps the resources that will be used are indeed safe.In a cold and dry spot, all equipment must be kept.With _________ only one process may use a resource at a time and no process may access a resource unit that has been allocated to another process.
Answers
With Mutual exclusion only one process may use a resource at a time and no process may access a resource unit that has been allocated to another process. This helps in avoiding race conditions and ensures that the resources are accessed in a sequential manner by the processes.
In the operating system, resources are shared by multiple processes, and mutual exclusion is a technique used to handle the allocation of resources to avoid race conditions and deadlocks. Mutual exclusion ensures that only one process can access a resource at a time. It prevents two processes from accessing a shared resource at the same time. Mutual exclusion also ensures that a resource unit that has already been allocated to one process should not be allocated to another process until the first process completes its execution and releases the resource.
This technique helps in avoiding race conditions and ensures that the resources are accessed in a sequential manner by the processes. Mutual exclusion can be implemented using semaphores, locks, and monitors.Main answer: With Mutual exclusion only one process may use a resource at a time and no process may access a resource unit that has been allocated to another process.
To know more about access visit:
https://brainly.com/question/32238417
#SPJ11
which of the following is not a physical security mechanism?motion-activated camerasintegrated intrusion alarmsfirewall aclsperimeter fence detection
Answers
Firewall ACLs is not a physical security mechanism. Option D
What are firewall ACLs?Firewall Access Control Lists (ACLs) serve as a network security mechanism that governs and sifts through inbound and outbound traffic through predetermined regulations.
They are utilized in the networking layer and function within the digital domain, furnishing logical entry management to network assets.
Physical security measures such as motion-triggered cameras, integrated intrusion alarms, and perimeter fence detection systems are employed to oversee and safeguard physical areas by detecting and preventing unauthorized access or movement, thus reducing the likelihood of security breaches.
Learn more about firewall ACLs at: https://brainly.com/question/15006683
#SPJ4
How do I do this?
Someone Please help

Answers
Answer:
I am done solving there was a synthetic error very sorry I tried to help for 30mins
_____ is the process of using procedures from statistics and computer science to extract useful information from extremely large databases
Answers
The process of using procedures from statistics and computer science to extract useful information from extremely large databases is called data mining.
Data mining is the process of utilizing techniques from statistics and computer science to extract valuable insights and knowledge from vast and complex databases. It involves applying various algorithms, statistical models, and machine learning methods to discover patterns, relationships, and trends within the data. By examining large datasets, data mining aims to uncover hidden patterns, identify anomalies, and generate predictive models for decision-making and future forecasting. This iterative process involves data preprocessing, exploratory analysis, model building, and result interpretation. Data mining plays a crucial role in areas such as business intelligence, customer segmentation, fraud detection, market analysis, and personalized recommendations, enabling organizations to derive actionable insights from their data.
learn more about procedures here :
https://brainly.com/question/27176982
#SPJ11
Acute exacerbation of addison's disease can lead to ecg changes and cardiovascular collapse as a result of electrolyte imbalance secondary to:_________
Answers
Acute exacerbation of Addison's disease can lead to ECG changes and cardiovascular collapse as a result of electrolyte imbalance and also as a consequence of low blood volume due to the K retention and/or Na excretion.
What is Addison's disease?Addison's disease is a disorder associated with the faulty secretion of several hormones, which are fundamental to maintaining the homeostasis of the body (state of equilibrium) in normal conditions.
This disease (Addison's disease) is associated with electrocardiogram (ECG) changes due to arrhythmia caused by electrolyte imbalance issues, which is a process that depends on positive ion particles such as potassium K and sodium Na in normal concentration levels
In conclusion, acute exacerbation of Addison's disease can lead to ECG changes and cardiovascular collapse as a result of electrolyte imbalance and also as a consequence of low blood volume due to the K retention and/or Na excretion.
Learn more about Addison's disease here:
https://brainly.com/question/13840401
#SPJ1