What is the advantage of 2022 rogue’s available premium traffic?.
Answers
The Nissan Rogue has made a name for itself in the market due to its practicality, efficiency, and affordability. Nissan is taking things up a notch in 2022 with its all-new Rogue, which boasts cutting-edge features and equipment.
One of the most noteworthy features of the 2022 Nissan Rogue is its Premium Traffic system, which promises to make navigation even more straightforward. The Premium Traffic system in the 2022 Nissan Rogue offers a range of benefits that set it apart from the competition.One of the primary benefits of Nissan Rogue's Premium Traffic system is that it will assist the driver in avoiding traffic congestion, ensuring a quicker and more pleasant journey. This system gathers data from a variety of sources and displays it on the car's center display screen.
This feature will allow drivers to avoid traffic congestion, save time, and arrive at their destination more quickly and efficiently. The system also offers up-to-the-minute traffic updates, allowing the driver to avoid delays caused by roadworks, accidents, and other obstructions. In addition to these features, the Premium Traffic system offers users access to real-time weather data and other critical information to assist drivers in planning their journeys.
To know more about market visit:
https://brainly.com/question/15483550
#SPJ11
Related Questions
Which internet communication service can you use to speak to other users over the internet?.
Answers
Answer: VOIP or Voice over IP
Explanation: It uses internet protocols and your IP address to make video or voice calls, depending on the service, it might also use WebRTC
In polar rz format for coding, symbol '0' is represented by
Answers
In polar rz format for coding, symbol '0' is represented by a Negative voltage or by a Pulse is transmitted for half the duration.
What is Coding?Coding is the process of transforming ideas, solutions, and instructions into the language that the computer can understand, that is, binary-machine code. Coding is how humans are able to talk with computers.
Coding creates a set of instructions for computers to follow. These instructions determine what actions a computer can and cannot take. Coding allows programmers to build programs, such as websites and apps. Computer programmers can also tell computers how to process data in better, faster ways.
Learn more about Coding here,
https://brainly.com/question/10729181
#SPJ4
What is an Algorithm? (might not be in the chapter text). Give an example.
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
An algorithm is the list of a finite set of instructions and rules that a computer needs to do to complete a task in order to solve a problem.
In short, an algorithm is a series of instructions that are implemented step by step to solve a problem. For example, you could consider a pizza recipe an algorithm for making a pizza in an everyday life routine. But when you are talking about using algorithms in computation and in mathematics. It means that solving a problem using a series of steps step by step.
For example, your everyday tasks aligned on a google calendar and remind you about your tasks using the alarm, etc- how to implement this using set of instructions and rules- is an algorithm.
Solving a quadratic equation is another example of an algorithm.
Binary search, array sorting are an example of an algorithm in computation. Because these algorithms based on the execution of step-by-step instruction to solve a problem such as sorting a list of numbers etc.
Write code using the range function to add up the series 7, 14, 21, 28, 35,. 70 and print the resulting sum.
Answers
#declare variable to hold sum
sum=0
#loop from 7 to 70 by incrementing 7 each time using range function
for i in range(7,71,7):
sum+=i
#peint sum
print(sum)
In Python, how do you determine a list's range?The list of even numbers in the input range will be returned by the range() function. The values will be increased by 2 and will produce even numbers until stop-2 because the range() function's parameters are start = 2, stop = 20, and step = 2.
What formula is employed for range?Briefly stated, we have the following formula: Values at the extremes make up the range. The data set 4, 6, 10, 15, 18, for instance, has a range of 18-4 = 14, a maximum of 18, a minimum of 4, and a minimum of 4.
To know more about variable visit :-
https://brainly.com/question/17344045
#SPJ4
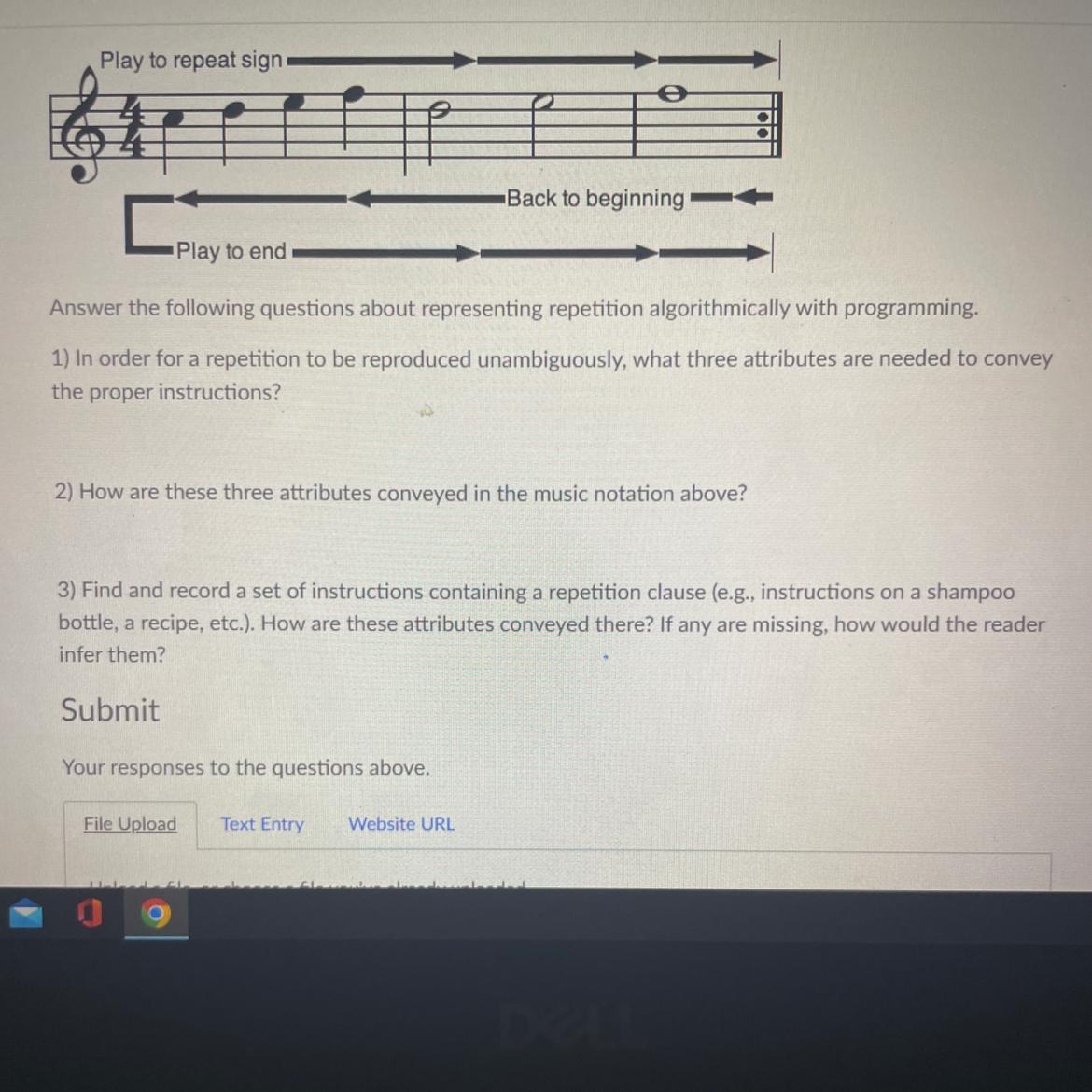
Play to end-
Back to beginning
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
The connection of your smartphone to your wireless headset is an example of a(n) ____.
Answers
The connection of your smartphone to your wireless headset is an example of a personal area network.
What is an illustration of a personal area network?One of the most common real-world instances of a PAN is the relationship between a Bluetooth earpiece and a smartphone. PANs can also secure laptops, tablets, printers, keyboards, and other computerized gizmos.
What are the elements of personal area network?
Features of WPAN :
Low cost, Small or No infrastructure setup.Short range transmission.Small confidential network , use anywhere.Wide spectrum of devices.Low energy consumption.No complicated connectivity.
To learn more about personal area network, refer
https://brainly.com/question/14704303
#SPJ4
What is the answer to this A term career is usually applied to a Someone please HEEEEEEEEEELP MEEEEEEE. THX
Answers
Answer:
Position that allows for professional growth and advancement
The term career is used in a number of ways but is usually applied to means the same thing: a position that allows for professional growth and advancement. It relates to a person’s occupation or profession and his journey of life, learning (training or formal education) and work.
Answer:
Position that allows for professional growth and advancement
Explanation:
a p e x
A charity is keeping track of donations for one month. The director would like to create a report that groups data by week. Each group will contain donations collected on each day of the week. Which type of calculated figure should the director use to display a cumulative total beneath each group?
running sum
sum
grand total
percentage
Answers
The calculated figure that the director should use to display a cumulative total beneath each group is option A: "running sum".
Which type of calculated figure is this?A "running sum" is used by the director to display cumulative totals beneath each group. It accumulates the values of a field over time or across a grouping.
Director groups donations weekly and displays total for each day using running sum to calculate and add up amount as days progress. Director groups donations weekly by creating a running sum field that adds daily totals until end of the week. Cumulative totals for each day of the week displayed in report.
Learn more about sum from
https://brainly.com/question/25734188
#SPJ1
The Link Layer in the TCP/IP Model corresponds to the and Layers of the OSI Reference Model. A) Transport; Physical. B) Physical; Data Link.
Answers
The link layer in the TCP/IP Model corresponds to the Transport and Physical layer of the OSI Model.
What is link layer?The Internet protocol suite, or IOS, is the networking architecture of the Internet, and the link layer is the lowest layer in computer networking. The set of procedures and communication standards specific to the link to which a host is actually connected is known as the link layer.
The link is the logical and physical network component that connects hosts or nodes in the network, and a link protocol is a set of guidelines and rules that only apply to the next-to-next network nodes in a network segment.
The link layer is sometimes described as a combination of the OSI's data link layer (layer 2) and physical layer, despite the fact that the Internet protocol suite and OSI model have different definitions of layering (layer 1).
Learn more about link layer
https://brainly.com/question/29486384
#SPJ4
explain on what you did and give on how problems as such can be avoid inthe future
Answers
you decide you are going to take your internet privacy seriously. which of the following action poses the greatest risk to your internet privacy?a) sharing your email address with those who request it. b) connecting to secured networks using the provided network name and password when visiting hotels. c) encrypting your files and sharing your private key to ensure others who you choose to share files with can read them. d) Using cloud storage to ensure access to your files from all your devices.
Answers
The option that poses the greatest risk to your internet privacy is: c) Encrypting your files and sharing your private key to ensure others who you choose to share files with can read them.
What is internet privacy?Sharing your private key accompanying possible choice compromises the freedom and solitude of your encrypted files. The purpose of encryption search out insulate delicate news and ensure that only approved things can approach it.
By giving your private key, you basically grant approach to one the one acquires it, that defeats the purpose of encryption and exposes your files to potential pirated approach.
Learn more about internet privacy from
https://brainly.com/question/30240651
#SPJ4
When you empty the trash on your computer what happens?
Answers
It is saved from that image or png for lawful usage only after being erased from your recently deleted folder.
What is recently deleted folder?Content that users delete from their accounts now automatically goes to Recently Deleted. The content may then be permanently erased. Or, if users change their minds, they can recover the information from the Recently Deleted folder and add it back to their profile.
The Recently Deleted folder is where files go after you delete them from iCloud Drive or On My [device]. Your files are deleted from Recently Deleted after 30 days. You have 30 days to get a file back if you decide against it or unintentionally erase it.
Photos and movies that you've moved to your Recently Deleted album can be permanently deleted files remain there for 30 days. View here for more information on removing photos.
Thus, It is saved from that image or png for lawful usage
For more information about recently deleted folder, click here:
https://brainly.com/question/1445705
#SPJ5
Anyone who uses search engines should be aware that the content of their searches could become public.
True or false
Answers
The given statement "Anyone who uses search engines should be aware that the content of their searches could become public." is true.
Using search engines does come with the risk that the content of searches could potentially become public. While search engine providers generally prioritize user privacy and take measures to safeguard user data, it is still important for individuals to be aware of the potential risks and exercise caution when conducting searches.
Search engine data collection: Search engines collect data about users' search queries, including the terms they search for, the time and date of the searches, and sometimes the user's IP address or location. This data is typically used to improve search results and provide personalized recommendations.
Data retention: Search engines may retain this search data for varying periods of time, depending on their privacy policies and legal obligations. Even if the data is initially anonymized, there is a possibility that it could be linked back to individual users through other means.
Data breaches: While search engines implement security measures to protect user data, data breaches can still occur. In the event of a breach, search data could potentially be exposed to unauthorized parties, including the content of users' searches.
Legal requests and government surveillance: Search engines may be subject to legal requests or government surveillance, which could lead to the disclosure of user search data. In certain jurisdictions, search engines may be required to comply with court orders or government demands to provide access to user data.
Third-party data sharing: Search engines often have partnerships or advertising networks that may collect user data for targeted advertising purposes. This data sharing could involve sharing search history or search preferences with third parties, potentially exposing the content of searches to external entities.
Given these factors, it is important for individuals to understand that there is a potential risk that the content of their searches could become public. While search engines strive to protect user privacy, it is advisable to exercise caution, be mindful of the information being searched for, and consider using additional privacy-enhancing measures, such as using encrypted search engines or virtual private networks (VPNs), if desired.
For more such questions on search engines, click on:
https://brainly.com/question/512733
#SPJ8
Ethan wants to change the font in his document. He should _____.
delete the text, select a font, and type
select a new font and highlight the text
highlight the text and select a new font
zoom in on the text, click on style, and make a selection
Answers
Answer:
C because it will work. I tried that a lot of time with documents.
Explanation:
Answer:
Ethan wants to change the font in his document. He should _____.
A. delete the text, select a font, and type
B. select a new font and highlight the text
C. highlight the text and select a new font
D. zoom in on the text, click on style, and make a selection
It is highlight the text and select a new font
Explanation:
compute the distance between the positions of the first and last zero element in the given array. for example, if the array is 3 0 1 0 4 9 5 0 6 your algorithm should yield 7 - 1
Answers
The distance between the first and last zero elements in the given array {`3 0 1 0 4 9 5 0 6`} is `7`.
To compute the distance between the positions of the first and last zero elements in the given array, we can follow the below approach.
1. Initialize two integer variables `first_zero` and `last_zero` to -1.
2. Iterate through the array of elements from start to end.
3. If the current element is zero and `first_zero` is still -1, then assign the index of the current element to the variable `first_zero`.
4. If the current element is zero and `first_zero` is not -1, then assign the index of the current element to the variable `last_zero`.
5. Once the iteration is done, compute the distance between the `first_zero` and `last_zero` by subtracting the index of `first_zero` from the index of `last_zero`.
6. The result obtained from step 5 is the distance between the positions of the first and last zero elements.
Let's apply the above approach to the given array.
Array Elements: `3 0 1 0 4 9 5 0 6`
Index: `0 1 2 3 4 5 6 7 8`
1. `first_zero` and `last_zero` are both initialized to -1.
2. Index 0: `3` is a non-zero element.
3. Index 1: `0` is a zero element, so assign the index 1 to `first_zero`.
4. Index 2: `1` is a non-zero element.
5. Index 3: `0` is a zero element, so assign index 3 to `last_zero`.
6. Index 4 to 8: All elements are non-zero.
7. Now, we have the `first_zero` index as 1 and the `last_zero` index as 3.
8. Therefore, the distance between the positions of the first and last zero elements is `last_zero - first_zero = 3 - 1 = 2`.
In conclusion, the distance between the positions of the first and last zero elements in the given array {`3 0 1 0 4 9 5 0 6`} is `7`. We achieved this by iterating through the array and finding the index positions of the first and last zero elements and then computing the distance.
To know more about array, visit:
https://brainly.com/question/16283725
#SPJ11
The distance between the positions of the first and last zero elements in the given array is 6.
Given an array 3, 0, 1, 0, 4, 9, 5, 0, 6. We need to compute the distance between the positions of the first and last zero element. The algorithm for the same will be as follows: Step-by-step solution:
We are given an array3 0 1 0 4 9 5 0 6
The first step is to find the index of the first occurrence of the zero elements in the array. Here, the first occurrence of the zero element is at index 1. So, the index of the first zero elements is 1. Next, we need to find the index of the last occurrence of the zero element in the array. Here, the last occurrence of the zero elements is at index 7. So, the index of the last zero element is 7. Now, we can compute the distance between the positions of the first and last zero element by taking the difference of their indices.
Thus, the distance between the positions of the first and last zero element is given by:
Distance = Index of last zero element - Index of first zero elementDistance = 7 - 1 = 6
Therefore, the distance between the positions of the first and last zero element in the given array is 6.
To know more about array refer for :
https://brainly.com/question/28061186
#SPJ11
Jordan just wrote a secret message program in Python that converts the number 7,095 to 1s and 0s. Which number system is Jordan converting to?
A Binary
B Decimal
C Digital
D Hexadecimal
Answers
Answer:
binary
Explanation:
bi-two numbers doesnt meet reqiurments automatically considered 0
Answer:
Binary
Explanation:
i took the test
what is the password for the root of the mysql server
Answers
Answer:
The default user for MySQL is root and by default, it has no password.
in this clip, the filmmakers connect each shot using a technique called – . these editing choices are intended to maintain cinematic – and hide the edit.
Answers
The filmmakers connect each shot using a technique called Cutting on action.
These editing choices are intended to maintain cinematic hides the shift from one shot to the next and hide the edit.What is meant by cutting on action?Cutting on Action is known to be a term that is said to be used by editor and it is one that implies the cuts in the middle of a given action to another shot that tends to matches the first shot's said action.
Note that it is seen as a common editing method that tends to hides the shift from one shot angle to another shot angle and this is often done by stopping the first shot in the middle of another continuing action and then beginning the next shot at some distance along in the similar action.
Therefore, The filmmakers connect each shot using a technique called Cutting on action. These editing choices are intended to maintain cinematic hides the shift from one shot to the next and hide the edit.
Learn more about filmmakers from
https://brainly.com/question/28110104
#SPJ1
The following algorithm accepts 3 integer values from the user, and then prints the maximum value entered. Some lines are missing.
Complete the program by inserting instructions after Line 4
1. OUTPUT (“Please enter 3 values. “)
2. Input (x, y, z)
3. MaxValue x
4. IF y > MaxValue THEN
MaxValue y
Answers
Answer:
1. OUTPUT (“Please enter 3 values. “)
2. Input (x, y, z)
3. MaxValue = x
4. IF y > MaxValue THEN
5. MaxValue = y
6. IF z > MaxValue THEN
7. MaxValue = z
8. OUTPUT("Maximum value is: ", MaxValue)
Mr. Prasad is a high school English teacher. He weighs different essays and assignments differently while calculating final grades. Therefore, he has made an Excel worksheet showing how different classwork weighs into a final grade. He would like to distribute an electronic file to his students, but he wants everyone to be able to read it regardless of whether or not they have Microsoft Office Suite.
What can Mr. Prasad do to best distribute the file?
use “Save As” to save it as an Adobe PDF file
use “Save As” to save it as an Excel 97-2003 workbook
paste the material into an Adobe PDF file
paste material into an Excel 97-2003 workbook
Answers
Mr. Prasad should use “Save As” to save it as an Adobe PDF file. The correct option is A.
What is pdf?The abbreviation PDF stands for Portable Document Format. It's a versatile file format developed by Adobe that allows people to easily present and exchange documents.
It is basically regardless of the software, hardware, or operating systems used by anyone who views the document.
As Mr. Prasad wants to distribute the files regardless of the students having Microsoft Office or not, he can save it as pdf, so it can be readable with all.
Thus, the correct option is A.
For more details regarding pdf, visit:
https://brainly.com/question/13300718
#SPJ1
remove the cover or chassis or case
Answers
Answer:
Case. Under that, there is the motherboard which has all the connections to all the hardware
Explanation:
which of the following types of software is for organizing analyzing and storing data in a table A spreadsheet software B database software C desktop publishing software D multimedia software
Answers
Answer:
spreadsheet software
Explanation:
Caden, Jacob, Lucas, and Michael, whose last names are Armstrong, Boothe, Gardner, and Robinson, live in four houses in a row.
From the clues below, find each person’s full name and house position (with house number 1 at the left).
1. Michael doesn’t live next door to Lucas.
2. Robinson’s house is after Gardner’s and before Michael’s.
3. Boothe’s house is just before Armstrong’s.
4. Lucas’ house, which is not first, is somewhere to the left of Caden’s.
Answers
Answer:
Jacob Gardner - Lucas Robinson - Caden Boothe - Michael Armstrong
Explanation:
According to clue 4, Lucas's house is not the first, and he has a house on his right, so it can only be house 2 or house 3. Therefore, Caden's house (which is on the right right of Lucas's), it can only be house 3 or house 4.
In turn, track 1 says that Michael's house is not next to Lucas's, so it can be 1 (if Lucas's house is 3) or 4 (if Lucas's house is in 2).
Track 2 says that there is a house before Michael's, which eliminates the possibility that Michael's house is number 1 (there would be no previous house). Thus, in addition, Lucas's house turns out to be 2 (Michael's house is not next door) and Caden's is 3, while Jacon's is house 1.
Jacob - Lucas - Caden - Michael
In turn, regarding surnames, clue 2 says that Robinson's house is after Gardner's and before Michael's. Thus, Robinson can be the last name of Jacob or Lucas, and Gardner that of Lucas or Caden. Now, since Boothe's house is just before Armstrong's, the order would be as follows:
Jacob Gardner - Lucas Robinson - Caden Boothe - Michael Armstrong
PRACTICE
.
3. Write a program asks the user to enter their first name and their last name, separated by a space.
Break the input string up into two strings, one containing the first name and one containing the last
name. You can do that by using the indexOf() subroutine to find the position of the space, and then
using substring0 to extract each of the two names. (should save each into its own variable)
• A sample run of the program should look something like this:
Please enter your first name and last name, separated by a space. ?
Mary Smith
Your first name is Mary.
Your last name is Smith.
(I am using Notepad)
Answers
class Name
{
public static void main(String args[])
{
String name, firstName,lastName;
int blankIndex,fchar,lchar;
System.out.println("Enter your name having space between first name and last name");
Scanner in = new Scanner(System.in);
name= in.nextLine();
blankIndex = name.indexOf(' ');
firstName = name.substring(0,blankIndex-1);
lastName = name.substring(blankIndex+1, name.length()-1);
fchar = firstName.length();
lchar = lastName.lenght();
System.out.println("You entered the name"+name); Â Â
System.out.println("Your firstname is"+firstName+"has"+fchar+"characters" );
System.out.println("Your lastname is"+lastName+"has"+lchar+"characters" );
}
}
Identify the programming language released by
the Department of Defense in the 1980s.
Pascal
O
Ada
C++
BASIC
Answers
Answer:
the answer is ADA
Explanation:
got it right
ADA 83,
(Context on ADA)
It was recognized as a powerful, modern programming language that addressed DOD's stated requirements for embedded systems.
A microcontroller with 8-bit memory cells has a 30-bit address bus. How many bytes of data can be individually addressed
Answers
A microcontroller with 8-bit memory cells and 30-bit address bus can individually address 2^30 bytes of data or 1 GB of data. Therefore, the answer is 1 GB of data can be individually addressed.
A microcontroller is a small computer on a single chip. It includes a processor, memory, and input/output peripherals. The number of bits in a microcontroller determines how many bytes of data the memory can address. In this case, the microcontroller has 8-bit memory cells, which means each memory cell can store 8 bits of data. The address bus of the microcontroller is 30-bit, which determines the number of memory cells that can be individually addressed. 2^30 bytes of data or 1 GB of data can be addressed. Therefore, a microcontroller with 8-bit memory cells and 30-bit address bus can address 1 GB of data.
A microcontroller with 8-bit memory cells and 30-bit address bus can address 1 GB of data.
To know more about microcontroller visit:
https://brainly.com/question/31856333
#SPJ11
Why is online etiquette important for digital communication in an educational setting? (Choose all that apply)
•It allows you to communicate clearly.
•Writing that is informal and full of errors is a security risk.
•It makes a good virtual impression.
•Teachers and parents don't understand modern slang and emojis.
Answers
Answer:
~Senpi Boi here~
Explanation:
The main ones that apply are: •It allows you to communicate clearly.
•It makes a good virtual impression.
(I would belive those will mostly apply to the qestion)
(Hope this helps!)
NEED THIS ASAP!!) What makes open source software different from closed source software? A It is made specifically for the Linux operating system. B It allows users to view the underlying code. C It is always developed by teams of professional programmers. D It is programmed directly in 1s and 0s instead of using a programming language.
Answers
Answer: B
Explanation: Open Source software is "open" by nature, meaning collaborative. Developers share code, knowledge, and related insight in order to for others to use it and innovate together over time. It is differentiated from commercial software, which is not "open" or generally free to use.
T/F. a comment in excel can capture an ongoing text conversation.
Answers
It is accurate to say that an excel comment can record a text dialogue in progress.
Can Excel threaded chats incorporate comments?The way comments function has changed in Excel for Microsoft 365. Now that comments are threaded, you can discuss the data with other readers. Notes function similarly to comments did in older iterations of Excel and are used for creating notes or remarks regarding the data.
What is a comment and how is it used?Comments are text notes that are included into programs to provide explanations of the source code. In a programming language, they are used to describe the program, remind programmers of the tough things they recently accomplished with the code, and assist the following generation.
To know more about comments visit:-
https://brainly.com/question/30318947
#SPJ1
Using Internet resources, find at least five organizations that offer Software as a Service (SaaS). How do their services benefit their users?
Answers
Answer:
1. Antenna Software
2. Cloud9 Analytics
3. CVM Solutions
4. Exoprise Systems
5. GageIn
Explanation:
1. Antenna Software - It has five gateways to routes and manages all transactions between the mobile applications and backend systems
2. Cloud9 Analytics - manages the warehouse separately from the solutions
3. CVM Solutions - Enables users to "clean" supplier information and to centralize and standardize information
4. Exoprise Systems - It avoid use of complex database and Web servers
5. GageIn - It uses Networking and social tools to connect users and facilitate communications
Answer:
1. Antenna Software
2. Cloud9 Analytics
3. CVM Solutions
4. Exoprise Systems
5. GageIn
Explanation: