What is the maximum number of worksheets that can be undeleted using the Undo command?
Answers
Answer:
100
Explanation:
The default value is 100 although this can be altered by changing the windows registry.
Related Questions
Cristina works in the sales department of a company that provides security services to businesses. She is writing a proposal to persuade a shopping mall to hire her company. She is using the most recent version of Microsoft word but just learned that the customer has an older version. What word-processing function will let her provide a document her customer's software can read?
Answers
In such a situation, Cristina must save the document in a format that the customer's software can read.To ensure compatibility, Cristina can use the "Save As" function to save the document in an earlier version of Microsoft Word format. When using this function, she must choose the earliest version that is compatible with the customer's software.
When writing a proposal to persuade a shopping mall to hire a company that provides security services to businesses, the writer must ensure that the proposal is compatible with the software the customer uses. Cristina works in the sales department of such a company, and she is using the most recent version of Microsoft Word. However, she just learned that the customer has an older version.
In such a situation, Cristina must save the document in a format that the customer's software can read.To ensure compatibility, Cristina can use the "Save As" function to save the document in an earlier version of Microsoft Word format. When using this function, she must choose the earliest version that is compatible with the customer's software.
In this case, she must save the document in a format that is compatible with the older version of Word used by the customer.The "Save As" function in Microsoft Word is used to create a new version of the same document with a different name and file format. It is used to save the document in a different location and to save it in a different format from the original. The function is useful when a document must be saved in a different file format to be compatible with other software programs.
For more such questions on Microsoft Word, click on:
https://brainly.com/question/25813601
#SPJ8
Can video games provide simulations for world problems?
Answers
Answer:
Yes
Explanation:
Yes, we absolutely use simulations for world problems. Some of the highly trained and specialized pilots, doctors, surgeons etc. had some form of simulations in the form of video games or other simulation software to help them become better at what they do.
Video games are not tangible so whatever happens in the game does not affect the real world, but the lessons we learn from playing simulation video games not only prepares us for the real world but we get better at our skills as well.
Edit: have used such software myself in medicine such as to learn different surgical skills and patient diagnosis :D
Answer:
Yes
Explanation:
"Video game" is the wrong term to describe this. There are simulations created with the same technology as games, but for a purpose other than entertainment.
Spreadsheet software enables you to organize, calculate, and present numerical data. Numerical entries are called values, and the
instructions for calculating them are called.
Answers
Answer:
It's called coding frame
How much water does the Hill family use per week?
Answers
Answer:
The Hill family uses69 pints
Explanation:
bc why not
Write a code snippet Now write your own code snippet that asks the user to enter two numbers of integer type (one at a time) and prints their sum. >>>your code starts here HTML Editor B
Answers
Explanation:
num1= print("Enter a number :")
num2 = print("Enter a number :")
sum = num1 + num2
print(sum)
Kile is assigned a role as a grey box penetration tester in the financial sector. He has to conduct a pen testing attack on all the application servers in the network. Which of the following tasks should he perform first while conducting a penetration testing attack on a network?
Tailgating
Phishing
Vishing
Footprinting
Answers
In the banking industry, Kile is given a job as a grey box penetration tester. All of the application servers must be the target of a pen testing attack by him.
What is networking ?The process of connecting and establishing relationships is known as networking. You may receive guidance and contacts from these connections, which can assist you in making wise career selections. You can also locate unlisted jobs and internships through networking. One-on-one or in a group context, networking is possible. Although the definition of networking is broad, we can limit it to the connection of a number of networks that are located in various locations. The main objectives of networking computers are to increase management, security, efficiency, or cost-effectiveness in comparison to non-networked systems. We might also concentrate on the various computers. A network is a collection of connected computers that allow one computer to speak with another and share resources.
To know more about networking visit:
https://brainly.com/question/30456221
#SPJ4
Write a script called pow.sh that is located in your workspace directory to calculate the power of two integer numbers (e.g. a ^ b); where a and b are passed as parameters from the command line (e.g. ./pow.sh 2 3). The result should be echoed to the screen as a single integer (e.g. 8).
Answers
Answer:
#! /usr/bin/bash
echo $[$1**$2]
Explanation:
(a) The first line of the code is very important as it tells the interpreter where the bash shell is located on the executing computer.
To get this on your computer, simply:
1. open your command line
2. type the following command: which bash
This will return the location where the bash shell is. In this case, it returned
/usr/bin/bash
(b) The second line is where the actual arithmetic takes place.
The variables $1 and $2 in the square bracket are the first and second arguments passed from the command line. The ** operator raises the left operand (in this case $1) to the power of the second operand (in this case $2).
Then, the echo statement prints out the result.
(c) Save this code in a file named as pow.sh then run it on the command line.
For example, if the following is run on the command line: ./pow.sh 2 3
Then,
the first argument which is 2 is stored in $1 and;
the second argument which is 3 is stored in $2.
The arithmetic operator (**) then performs the arithmetic 2^3 which gives 8.
what is information technology
Answers
Explanation:
The study or use of electronic equipment, especially computers, for collecting, storing and send out information.Information technology is the use of computers to store, retrieve transmit, and manipulate data, or information.
What type of hard disk is recommended for a Windows 10 VM?
IDE
SCSI
SATA
NVMe
Answers
Answer:
c
Explanation:
iv'e done this before
The type of hard disk is recommended for a Windows 10 VM is SATA. Therefore, option C is correct.
What is the virtual hard disk type of VM?A virtual hard disk (VHD) is a file format that stores the entire contents of a computer's hard drive. A disk image, also known as a virtual machine (VM), is a copy of an existing hard drive that includes all data and structural elements.
The VHDX format is more durable. VHDX provides improved performance and capacity of up to 64 TB. Converting a VHD to VHDX format is simple with tools like Hyper-V Manager or PowerShell.
The SATA controller is typically used by default for a VM's CD/DVD drive. Compatibility: Virtual hardware compatibility with ESXi 5.5 or later. A maximum of four SATA controllers are supported per VM.
Thus, option C is correct.
To learn more about the virtual hard disk, follow the link;
https://brainly.com/question/30262846
#SPJ2
Your data set is total sales per month. What does the value $500.0 in this image of the Status Bar tell you? Profits Average: $346.7 Count: 3 Numerical Count: 3 Min: $240.0 Max: $500.0 Sum: $1,040.0
Answers
Note that where the Status Bar in Microsoft Excel indicates $500, this refers "the largest dollar amount of sales across all 12 months" in the referenced data set.
What is the rationale for the above response?Note that $500 refers to the highest numerical value in the currently selected range of cells. It is a quick way to obtain the maximum value without having to use a formula or function. This can be useful in data analysis to quickly identify the highest value in a set of data.
The status bar in software applications such as Microsoft Excel, Word, and other productivity tools is important because it provides users with real-time information and quick access to certain features and settings.
For example, in Microsoft Excel, the status bar provides users with important information such as the current cell mode, whether the num lock is on or off, the average, count, and sum of selected cells, and the maximum and minimum values of selected cells.
Learn more about Data Set:
https://brainly.com/question/16300950
#SPJ1

Is it possible to beat the final level of Halo Reach?
Answers
what are the earliest invention in human history
Answers
Answer: Tools, Boats, Hand made bricks.
Explanation: The tools were the first technological advancement, the boats were the next, them hand made bricks for construction.
1608:telescope
1620:Compound microscope
1630:Slide rule
1642:mechanical calculator 1643:barometer
1650:vacuum pump
1656:pendulum clock
Hope this is enough
Your company has been assigned the 194.10.0.0/24 network for use at one of its sites. You need to calculate a subnet mask that will accommodate 60 hosts per subnet while maximizing the number of available subnets. What subnet mask will you use in CIDR notation?
Answers
To accommodate 60 hosts per subnet while maximizing the number of available subnets, we need to use a subnet mask that provides enough host bits and subnet bits.
How to calculateTo calculate the subnet mask, we determine the number of host bits required to accommodate 60 hosts: 2^6 = 64. Therefore, we need 6 host bits.
Subsequently, we determine the optimal quantity of subnet bits needed to increase the quantity of accessible subnets: the formula 2^n >= the amount of subnets is used. To account for multiple subnets, the value of n is set to 2, resulting in a total of 4 subnets.
Therefore, we need 2 subnet bits.
Combining the host bits (6) and subnet bits (2), we get a subnet mask of /28 in CIDR notation.
Read more about subnet mask here:
https://brainly.com/question/28390252
#SPJ1
Name:
Sup-R Game Desktop – Model EEXL
Inteel® Core i7
6GB Tri-Channel DDR3
500GB SATA-II (7200 rpm)
16x CD/DVD burner
21.5” HD widescreen monitor
NVIDIA® GeForce
Creative Sound Blaster® X-Fi Titanium
Altec Lansing speakers
Gigabit Ethernet port
3 – year limited warranty
Windows 10
1. Suppose you are reading a computer magazine and you come across the ad pictured above. By looking at the specs, you can see that: (2 Points)
The amount of RAM is ___________.
The microprocessor manufacturer is __________.
The amount of disk storage is _______________.
The amount of Solid State Drive storage is ______________
2. In the table below, list the hardware/peripheral components in the ad and check which function the component performs. (Add additional rows to the table if needed). (5 Points)
Component
Processor
Memory
Storage
Input
Output
Other
3. In the table below, list 5 functions/features you would look for in purchasing a computer and explain why each is important to you. (3 Points)
Function/Feature
Explanation as to why and size, capacity, etc. you need this feature/function
5. List and describe the factors that affect the performance of a microprocessor. Name two manufacturers of central processing units (CPUs) and some for the different models of processors that they manufacture. (5 points)
6. At the beginning of an update for your smart phone, you notice a warning that says “Make sure your device is connected to a wall outlet and do not turn the device off until the update is complete.” You suspect that the update is going to _______________ the ROM boot loader to fix a security vulnerability. (2 Points)
7. You are working on a group project and you suggest to your team that they use a ______________ storage service where members can access a shared folder. (2 Points)
8. One of the ports on your laptop is rectangular and the inside of it is blue. It is a(n) _________ port. (2 Points)
9. You need an external keyboard for your Android device, and thankfully you can add a wireless one because it has ________________ capability. (2 Points)
10. You volunteer to produce a large quantity of black-and-white leaflets for a charity organization. It is fortunate that you have access to a(n) _____________________ printer with a high duty cycle and low operating costs.
Answers
inteel
500gb
500gb
What is cybersecurity? Cybersecurity refers to the protection of hardware?

Answers
Cybersecurity is the practice of safeguarding computer systems, networks, and mathematical data from unauthorized approach, theft, damage, or additional malicious attacks.
What is cybersecurity?It involves the use of differing technologies, processes, and practices to secure digital maneuvers, networks, and data from a wide range of dangers, including cybercrime, cyber-spying, cyber-terrorism, and different forms of malicious endeavor.
While cybersecurity does involve protecting fittings, it also involves looking after software, networks, and digital dossier. In addition to protecting against external warnings, etc.
Learn more about cybersecurity from
https://brainly.com/question/28004913
#SPJ1
What feature allows a person to key on the new lines without tapping the return or enter key
Answers
The feature that allows a person to key on new lines without tapping the return or enter key is called word wrap
How to determine the featureWhen the current line is full with text, word wrap automatically shifts the pointer to a new line, removing the need to manually press the return or enter key.
In apps like word processors, text editors, and messaging services, it makes sure that text flows naturally within the available space.
This function allows for continued typing without the interruption of line breaks, which is very helpful when writing large paragraphs or dealing with a little amount of screen space.
Learn more about word wrap at: https://brainly.com/question/26721412
#SPJ1
Draw raw a program Flowchart that will be use to solve the value ofx im a quadratic equation +(x) = ax²tbxtc.
Answers
A program Flowchart that will be use to solve the value of x in a quadratic equation f(x) = ax²+bx+c.
Sure! Here's a basic flowchart to solve the value of x in a quadratic equation:
```Start
|
v
Input values of a, b, and c
|
v
Calculate discriminant (D) = b² - 4ac
|
v
If D < 0, No real solutions
|
v
If D = 0, x = -b / (2a)
|
v
If D > 0,
|
v
Calculate x1 = (-b + √D) / (2a)
|
v
Calculate x2 = (-b - √D) / (2a)
|
v
Output x1 and x2 as solutions
|
v
Stop
```In this flowchart, the program starts by taking input values of the coefficients a, b, and c. Then, it calculates the discriminant (D) using the formula D = b² - 4ac.
Next, it checks the value of the discriminant:
- If D is less than 0, it means there are no real solutions to the quadratic equation.
- If D is equal to 0, it means there is a single real solution, which can be calculated using the formula x = -b / (2a).
- If D is greater than 0, it means there are two distinct real solutions. The program calculates both solutions using the quadratic formula: x1 = (-b + √D) / (2a) and x2 = (-b - √D) / (2a).
Finally, the program outputs the solutions x1 and x2 as the result.
For more such questions on Flowchart,click on
https://brainly.com/question/6532130
#SPJ8
The Probable question may be:
Draw a program Flowchart that will be use to solve the value of x in a quadratic equation f(x) = ax²+bx+c.
How many subnets and host per subnet are available from network 192.168.43.0 255.255.255.224?
Answers
It should be noted that the number of subnets and hosts available from network 192.168.43.0 255.255.255.224 is 8 and 32, respectively. Only 30 of the 32 hosts are generally functional.
What is a host in computer networking?A network host is a computer or other device that is connected to a computer network. A host can serve as a server, supplying network users and other hosts with information resources, services, and applications. Each host is given at least one network address.
A computer network is a group of computers that share resources on or provided by network nodes. To communicate with one another, computers use common communication protocols over digital links.
So, in respect to the above response, bear in mind that we may compute the total number of: by putting the information into an online IPv4 subnet calculator.
8 subnets; and30 hosts available for 192.168.43.0 (IP Address) and 255.255.255.224 (Subnet)
Learn more about hosts:
https://brainly.com/question/14258036
#SPJ1
What is an OS? Explain the objectives of an OS.
Answers
Answer:
operating systems is a group of computer programs that is responsible for the management and coordination of activities and the sharing of the resources of that computer.
objective
1 to make the computer system convenient and easy to use for the user.
2 to use the computer hardware is a efficient way by handling the details of the operations of the hardware
Jerome falls sick after eating a burger at a restaurant. After a visit to the doctor, he finds out he has a foodborne illness. One of the symptoms of foodborne illness Jerome has is .
Jerome likely got the illness after eating food.
Answers
Answer: food poisning
Explanation:
either the food wasnt
cooked properly or the food was out of date and went bad
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Think about that the C, B and S parameters of a Cache. Think about what happens to compulsory, capacity, conflict misses, if only each of the following parameter changed (the other two are kept the same)?
(i) C is increased (S, B same)
(ii) S is increased (C, B Same)
(iii) B is increased (C, S Same)
Answers
Answer:
(i) C is increased (S, B same)
Explanation:
Cache are items which are stored in the computer at a hidden place. These are sometimes unwanted and they may hinder the speed and performance of the device. They exist to bridge speed gap.
Look at the attached photos! I need urgent help! Please answer each of the questions. If you have any, I will take them!


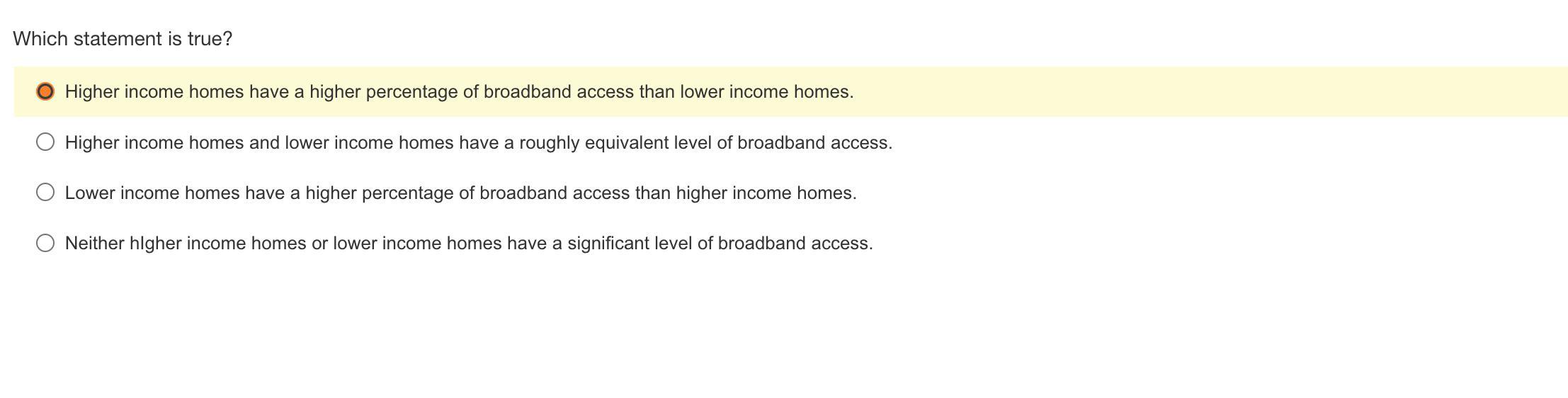
Answers
The greatest challenge the analyst is likely to face in solving this problem is A. Making sure the price and volume numbers are accurate
The skill practiced is Consensus building.
The true statement is that A. Higher income homes have a higher percentage of broadband access than lower income homes
How to convey the informationThe greatest challenge the analyst is likely to face in solving this problem is likely to be finding meaningful patterns in the stock market data that can accurately predict future behavior.
Higher income homes have a higher percentage of broadband access than lower income homes. This disparity in broadband access is commonly referred to as the "digital divide".
Learn more about market on:
https://brainly.com/question/25369230
#SPJ1
1. Which of the following is used to operate computers and execute tasks?
A. Software
C. Update
B. Application
D. Upgrade
Answers
Answer:
a.software
I hope it hel
In c++, make the output exactly as shown in the example.

Answers
Answer:
Here's a C++ program that takes a positive integer as input, and outputs a string of 1's and 0's representing the integer in reverse binary:
#include <iostream>
#include <string>
std::string reverse_binary(int x) {
std::string result = "";
while (x > 0) {
result += std::to_string(x % 2);
x /= 2;
}
return result;
}
int main() {
int x;
std::cin >> x;
std::cout << reverse_binary(x) << std::endl;
return 0;
}
The reverse_binary function takes an integer x as input, and returns a string of 1's and 0's representing x in reverse binary. The function uses a while loop to repeatedly divide x by 2 and append the remainder (either 0 or 1) to the result string. Once x is zero, the function returns the result string.
In the main function, we simply read in an integer from std::cin, call reverse_binary to get the reverse binary representation as a string, and then output the string to std::cout.
For example, if the user inputs 6, the output will be "011".
Hope this helps!
Imani works on computer systems and telecommunication devices that are used to manage and send information. What specific field of technology is she working in?
Answers
Imani is working in the field of "telecommunications" or "networking" technology.
Why is Networking Technology Important?It not only allows employees to easily exchange information, enhancing productivity and efficiency, but it also provides cost-effectiveness, storage efficiency, flexibility, and data security.
Client/server computing, packet switching, and the creation of communication standards are the three major digital technologies. TCP/IP (Transmission Control Protocol/Internet Protocol)
Learn more about Networking at:
https://brainly.com/question/1027666
#SPJ1
hat characteristic of Python subprograms sets them apart from those of other languages?
One characteristic of Python functions that sets them apart from the functions of other common programming languages is that function def statements are executable. When a def statement is executed, it assigns the given name to the given function body. Until a function's def has been executed, the function cannot be called. Consider the following skeletal example:
if . . .
def fun(. . .):
. . .
else
def fun(. . .):
. . .
Answers
The statement for the characteristics of Python subprograms sets them apart from those of other languages is true.
What is def statement?Python subprograms can be written with def statement to define a function. Def statement is a user-defined function and this function is provided by the user.
Def statement is a function of code that contains the logical unit of the sequence of statements. Difference from the other language, def statement function will execute before the function can be available to be called.
Thus the given statement about subprograms sets of python is true.
Your question is incomplete, but most probably your full question was
True/false. One characteristic of Python functions that sets them apart from the functions of other common programming languages is that function def statements are executable. When a def statement is executed, it assigns the given name to the given function body. Until a function def has been executed, the function cannot be called. Consider the following skeletal example:
if . . .
def fun(. . .):
. . .
else
def fun(. . .):
. . .
Learn more about def statement here:
brainly.com/question/13259727
#SPJ4
underfloor, cellular concrete floor, cellular metal floor, surface, wireway and busway are all kind of
A. raceways
B. conduit
C. wiring
D.NEC rules
Answers
Answer:
Option C
Explanation:
Underfloor, cellular concrete floor, cellular metal floor, surface, wireway and busway are all kind of wiring.
In these wiring method, a conduit body or a box is installed at conductor splice, outlet, switch, junction, termination or pull point.
Hence, option C is correct
32. The broadcast address is a special address in which the host bits in the network address are all set to 1, and it can also be used as a host address.
A.True
B.False
Answers
Some host addresses are reserved for special uses. On all networks, host numbers 0 and 255 are reserved. An IP address with all host bits set to 1 is False.
How can I find a network's broadcast address?Any device connected to a multiple-access communications network can receive data from a broadcast address. Any host with a network connection could receive a message delivered to a broadcast address.All hosts on the local subnet are reached by using this address to send data. The Routing Information Protocol (RIP), among other protocols that must communicate data before they are aware of the local subnet mask, uses the broadcast address.The use of some host addresses is reserved. Host numbers 0 and 255 are set aside for use only on reserved networks. When all host bits are set to 1, an IP address is considered false.To learn more about Broadcast address refer to:
https://brainly.com/question/28901647
#SPJ1
all foreign language results should be rated as fails to meet. True or false?
Answers
All foreign language results should be rated as fails to meet. This statement is true. Thus, option (a) is correct.
What is languages?
The term language refers to the spoken and written. The language is the structure of the communication. The language are the easily readability and understandability. The language are the component are the vocabulary. The language is the important phenomenon of the culture.
According to the languages are to explain the all the foreign languages are to learn in the study in the learning habits. But there is not the easy to learn. There are the must easy to the interest of to learn foreign languages.
As a result, the foreign language results should be rated as fails to meet. This statement is true. Therefore, option (a) is correct.
Learn more about on language, here:
https://brainly.com/question/20921887
#SPJ1