what is the rarest/coolest/most valuable car you have ever seen in person?
Answers
Answer:
A Lamborghini, Tesla Model X, and more!
The Lambo was an Aventador SV
Answer:
Lamborghini Huracan
Explanation:
I seen it before in person, also a 1990 Ferrari and also I've been on and driven my dream car the BMW i8
Related Questions
Part 1: Compare the Websites
You are conducting research for a project about elephant sanctuaries. Compare the two websites using the 5 W’s criteria for reliability and validity. For each website, complete the 5 W’s Checklist.




Answers
Answer:
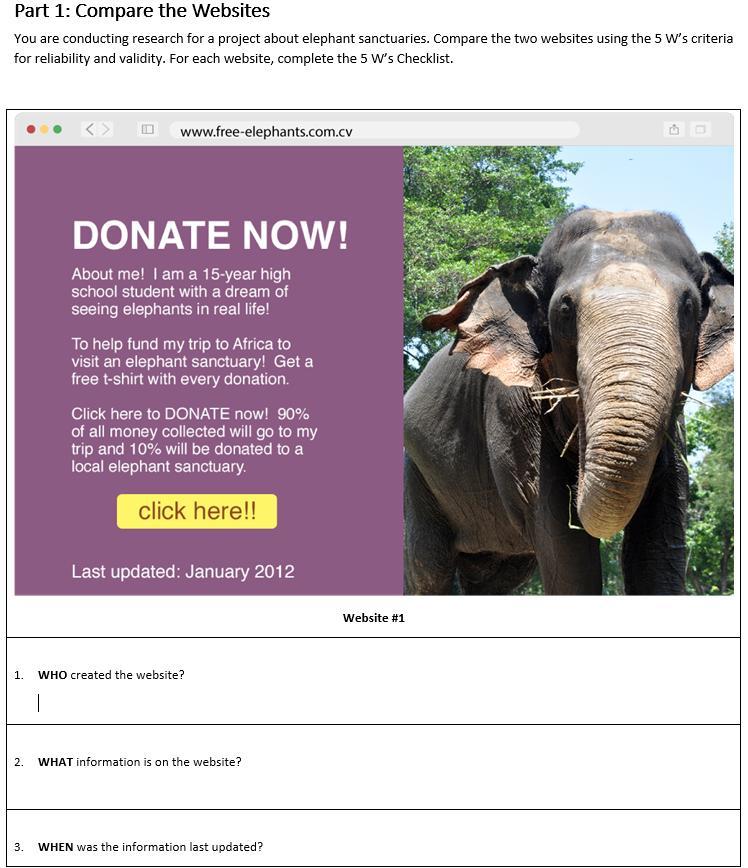
WHO: a 15-year old high school student
WHAT: information about donating to a local elephant sanctuary and a trip
WHEN: January 2012
WHERE: www.free-elephants.com.cv
WHY: To help fund the student's trip to Africa to visit an elephant sanctuary
who: a 15-year-old high school student
what: information about donating to a local elephant sanctuary and a trip
when: January 2012
where: www.free-elephants.com.cv
why: To help fund the student's trip to Africa to visit an elephant sanctuary
Can a syntax error occur in a block-based code? Why or why not?
What are some strategies that you can use when you debug a program?
How would you describe the difference between a syntax error and a logic error?
What are some real-life situations that require a program that is iterative? Include at least three examples in your answer.
How would you describe the relationship between blocks of code and commands?
Answers
If you don’t know the answer, don’t try to answer, *sigh* some people these days...
Can a syntax error occur in a block-based code? Why or why not?
No. Because block code is not actual code, it’s like a simplified version.
What are some strategies that you can use when you debug a program?
When there is a bug, don’t look through the whole code, you should focus on the area that may be causing the bug.
How would you describe the difference between a syntax error and a logic error?
Syntax error is when the rules of the language aren’t followed (like using a variable wrong or forgetting a colon.)
A logic error is a bug within the structure or algorithm of a code.
What are some real-life situations that require a program that is iterative? Include at least three examples in your answer.
Apple releases different version of the iPhone to make it work better.
Coke uses different formulations of Coca Cola to get the best tasing version.
A cook may change a recipe to make it taste better.
How would you describe the relationship between blocks of code and commands?
Code makes the block, commands run the blocks.
Answer:
1. A syntax error cannot occur in a block based code because block based code isn’t actual code, it is a version of it.
2. When there is a bug, you should go to the place where something wrong happened and fix that.
3. A syntax error is when we type something that is not in the computer language. A logic error is in the algorithm of a code.
4. The Tesla company releases new models of teslas. An author publishes a new book. A person changing their furniture.
Explanation:
What does the alternate letter code YUOYU FWOSUFNCD CIET!
In real words?
Answers
Answer:YOU FOUND IT
Explanation:
remove every other letter
Select the correct text in the passage.
Which phrases/sentences correctly define a project proposal document?
Carrie has the responsibility of preparing documents in the project initiation phase.She [recorded the project type, scope, time, cost, and classification in a document.] She thinks this document will [help to determine whether the project needs match the business needs.] Carrie also participated in a meeting with the project manager and key stakeholders. Together, they worked on a document to [define project scope and assumptions, estimate cost, create project feature requirements, and note risks. They also built a preliminary timeline of the project in the document]
Answer choices are in brackets: [ ]
Answers
Answer:
The last bracket "define project scope and assumptions, estimate cost, create project feature requirements, and note risks."
Explanation:
Project proposals are showing the audience what the project is, how much it will cost them, necessary requirements to achieve, and risks (financial, physical, etc..). That sentence covers all of that.
public class Main {
public static void main(String[] args) {
String firstName = "John ";
String lastName = "Doe";
String fullName = firstName + lastName;
System.out.println(fullName);
}
}
From this example copy and paste code that when run would say your name. in javascript with my first name being Ryan and my last name being Smith
Answers
Answer:
const firstName = "Ryan ";
const lastName = "Smith";
const fullName = firstName + lastName;
console.log(fullName);
Explanation:
public static void main(String[] args) {
String firstName = "Ryan";
String lastName = "Smith";
String fullName = firstName + lastName;
System.out.println(fullName);
}
Dr. Kim divides a programming class into groups. Each group will create a large program as their
final exam. To make this big project more manageable, which of these should the group use?
an algorithm creator
a binary translator
a text editor
top-down programming
Answers
ANSWER AS FAST AS U CAN ITS DUE IN LIKE 5 MINUTES-
What must a new object have in Turtle Graphics?
Export
Name
Title
Rank
Answers
how do you set up a go ogle account on a school computer?
Answers
Explanation: Click sign in, then Click use another account, after that put in the email and password for that account. You should now have a new account.
What is the name given to the parts of a computer that you can actually
touch?
Software
Computer Parts
Computer Case
Hardware
Answers
Answer:
Hardware
Explanation:
Hardware, is the parts of the computer that you can physically touch. Examples include, the keyboard and mouse.
Hope this helps. <3
Hardware is the name given to the parts of a computer that you can actually touch.
What is Hardware?
The physical components of a computer, such as its chassis, CPU, RAM, monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers, and motherboard, are referred to as computer hardware.
Software, on the other hand, is a collection of instructions that may be stored and executed by hardware. Software is referred to as "soft" because it is flexible, but hardware is referred to as "hard" because it is rigid in terms of modifications.
Software often instructs hardware to carry out any command or instruction. A useful computer system is one that combines hardware and software, while there are also systems that use simply hardware.
Therefore, Hardware is the name given to the parts of a computer that you can actually touch.
To learn more about Hardware, refer to the link:
https://brainly.com/question/15232088
#SPJ5
List the different computer industries, and what they do.
(Like the part makers, people who assemble it and stuff not the companies)
Answers
Answer:
There are several different industries that are involved in the production and use of computers. These industries include:
Hardware manufacturers: These companies design and produce the physical components of computers, such as the motherboard, processor, memory, storage, and other peripherals.Software developers: These companies create the operating systems, applications, and other programs that run on computers.System integrators: These companies assemble and configure computers, often using components from multiple manufacturers, and sell them to consumers or businesses.Service providers: These companies provide support and maintenance services for computers, including repair, installation, and training.Data centers: These companies operate large facilities that host and manage the data and computing resources of other companies.Internet service providers: These companies provide access to the internet for businesses and consumers.Cloud computing providers: These companies offer computing services, such as storage, networking, and software, over the internet.Consulting firms: These companies provide advice and expertise on the use of computers and technology for business and organizational goals.Answer:
Hardware Manufacturers
Software Developers
System Integrators
Service Providers
Data Providers
ISP
Cloud Computing Providers
Consulting Firms
Explanation:
It is in order..
aaaaaaaaaaaaaaaaplssssssssssssssssssssssssssssshelpppppppppppppppppppppppp

Answers
Answer:
Voltage=50
Explanation:
V = I × R
V= I × 50
V = 50
V = Potential difference in volts
R = Resistance in ohms
I = Current in amps (amperes)
In your own words, how are sources of income and expenses related to
budgets?
I NEED HELPPP
Answers
Answer:
They are related because...
Explanation:
Your income becomes your budget and depending on how high your budget is it shows how much can you spend and the amount of money you spend is your expenses
Will the following boolean expression return True or False?

Answers
Answer:
the boolean expression returns false
Explanation:
because 10!==100
What do the stapedius and gluteus maximus have in common?
this is a science question
Answers
Answer:
What do the stapedius and gluteus maximus have in common? They move the hips and thighs. They are attached to bones. They are the largest muscles.
Explanation:
Answer:
Explanation:
......lo siento, no sé esto
write a script for a difficult talk with your boss. Write down what you would say to share the facts or to tell your story. Don’t forget to write down how you would ask for your boss’s viewpoint or input.
Answers
Answer:
1st. Im sorry but i think I sincerely don't get viewed
Explanation:
Name three computer company's.
Answers
True/False: Software is needed in order for hardware to operate.
Answers
Answer:
I think it is true sorry if it's wrong
Answer:
the answer is true
Explanation:
hope this helps
A networking mode that allows traffic from a virtual machine to pass through unchanged to the physical network as though it were directly attached. Group of answer choices bridged mode NAT mode switch mode horse mode
Answers
Answer:
The answer is bridged mode.
Explanation:
Solution
A bridged mode enables a traffic from a virtual machine to pass through unchanged to the physical network as though it were directly attached
Bridged mode: It refers to a configuration that disables the NAT attribute on the modem and permits a router to act as a DHCP server without an IP Address conflict.
Bridged networking connects a virtual machine to a network by making use of the network adapter on the host system.
How do the text feature help on the text?
Answers
Answer:
Text features help you locate important information in a text. Knowing the purpose of the text feature helps you decide at which text feature to look when you want to understand your text better. Organized by purpose, the chart identifies text features and how they help the reader.
Explanation:

Be sure to answer the following in complete and detailed sentences.
1. What might be a benefit of wirelessly connecting smart devices in a physical computing project?
2. How might you connect more than two micro:bits to activate multiple outputs triggered by one micro:bit?
3. How do batteries and other types of power sources make physical computing systems more mobile? Why is that helpful?
Answers
Answer: 1, 3
Explanation:
1: It can not just cause less of a wire mess. It can also cause easy travel if you want to do something from somewhere else!
3: It can make it easier to power up a device quickly when you CAN replace the batteries. It can also make charging more efficient overall.
Answer:1: It can not just cause less of a wire mess. It can also cause easy travel if you want to do something from somewhere else!
3: It can make it easier to power up a device quickly when you CAN replace the batteries. It can also make charging more efficient overall.
Explanation:
Why isn't my brainly post being answered?
Answers
Try deleting then reposting, it may not always pop up in new questions, I will have a look at the question anyway.
Hope this helps!
C programming 3.26 LAB: Leap year
A year in the modern Gregorian Calendar consists of 365 days. In reality, the earth takes longer to rotate around the sun. To account for the difference in time, every 4 years, a leap year takes place. A leap year is when a year has 366 days: An extra day, February 29th. The requirements for a given year to be a leap year are:
1) The year must be divisible by 4
2) If the year is a century year (1700, 1800, etc.), the year must be evenly divisible by 400; therefore, both 1700 and 1800 are not leap years
Some example leap years are 1600, 1712, and 2016.
Write a program that takes in a year and determines whether that year is a leap year.
Ex: If the input is 1712, the output is:
1712 - leap year
Answers
if year mod 100 equals 0
Check if year mod 400 equals 0 (if true, leap year, if not, not a leap year)
And if year mod 100 doesn’t equal 0
Check if year mod 4 equals 0 (if true, leap year, if not, not a leap year)
Sorry if this is a bit janky, if you need any further explanation please let me know.
The page that appears when you first open your Internet browser is the _____.
Answers
Answer:
Home page
I think this is straight forward
My brother is having troubles trading a fly ride king bee.
1) Have an offer comment your username and the offer.
2) If your gonna be rude CLICK OFF OR IM REPORTING
3) Brainliest for the person that answer's true-fully
4) Are you sure yo wanna do the trade?
Answers
i will trade a magic door!!!
user: lrlau102
While Lucas was shopping online, a new window opened to show similar products from a different store. Which of the following practices will prevent unauthorized access to his system when browsing the internet? (5 points) Enable pop-up blockers. Install antivirus software. Protect passwords. Use spam filters.
Answers
To prevent unauthorized access when browsing the internet, Lucas should enable pop-up blockers and install antivirus software.
How can Lucas enhance his online security while browsing?Enabling pop-up blockers and installing antivirus software are essential steps to enhance Lucas's online security. Pop-up blockers help prevent malicious or unwanted windows from opening unexpectedly, reducing the risk of unauthorized access through deceptive pop-ups.
The antivirus software scans for and detects potential threats, such as malware or viruses, safeguarding Lucas's system from unauthorized intrusions while he explores the web. By employing these measures, Lucas will reduce the chances of unauthorized access to his system during his online shopping activities.
Read more about unauthorized access
brainly.com/question/14925927
#SPJ2
(I made this up teehee) what anime is katski bakugo from
Answers
You can find this out on Brainly! Recycling one glass jar saves enough energy to watch television for _ hours It's one of the fun facts!
Answers
Recycling one glass jar saves enough energy to watch television for 3 hours.
explain the history of computing of mechanical era
Answers
Answer:The Mechanical Era
Created a machine that could add and subtract numbers. Dials were used to enter the numbers. ... Designed a machine called the Analytical Engine. The design had all the basic components of a modern day computer. In addition, it was designed to be programmable using punched cards.
Explanation:Hope this helped
HELP!!!! PLEASE WILL MARK BRAINLIEST
When you provide personal information, such as your name, age, and hometown sites like Amazon, yoitube, spotify, and pandora you are creating the following.
Check all that apply:
A) partial identity
B) persona
C) super identity
D) incognito shield
Answers
Answer:
super identity
Explanation: hope this helps im pretty sure its that
Jackie is planning a birthday party for her little brother and is researching different trampoline parks. She receives a pop-up asking for her name, address, and date of birth so she can receive a special promotion from the trampoline park. What should Jackie do?
a
Ignore the request and not enter any personal information.
b
Provide only her name and date of birth.
c
Provide only her name and address.
d
Provide the requested information to receive the discount.
Answers
Answer:
a
Explanation:
sis is gonna get scammed
Answer:
a
Explanation:
You dont know who is getting your information and it is not someone you know. STRANGER DANGER!