What marking (banner and footer) acronym (at a minimum) is required on a DoD document containing controlled unclassified information?
A. FOUO
B. IAW
C. Unclassified
D. CUI - Correct Answer
Answers
CUI is required on a DoD document containing controlled unclassified information.
What is DoD document?
The Department of Defense (DoD) document is a document that is issued by the US Department of Defense (DoD). This document is a set of regulations that govern the activities of the Department of Defense and its personnel. The DoD document establishes the authority, responsibility, and oversight for the Department of Defense and its personnel. It also outlines the rules, procedures, and policies for the department's activities. The document is used to ensure the Department of Defense is following its mission and achieving its goals. The document is updated from time to time to reflect changes in the laws and regulations governing the department. The DoD document is an important document that ensures the Department of Defense is meeting its responsibilities and conducting its activities in a professional and responsible manner.
To learn more about DoD document
https://brainly.com/question/27999913
#SPJ1
Related Questions
(Maximum 400 words) Describe how this period of Coronavirus (COVID-19) will influence and affect the STEM (Science, Technology, Engineering, and Mathematics) fields.
Answers
The period of coronavirus will have both negative and positive impacts on STEM fields.
However, the STEM (Science, Technology, Engineering, and Mathematics) fields have shown significant changes and impacts.
Here is how this period of COVID-19 will affect the STEM fields.
1. Technology
The current situation has increased the use of technology in various fields. Remote work and online meetings are becoming more popular, and this has led to increased technology usage. Technological advancements are expected in the future, leading to new business models that are more efficient.
2. Biomedical research
The COVID-19 pandemic has sparked the need for more biomedical research and led to an increase in research funding. Scientists are researching vaccines, treatments, and diagnostic tools, which is expected to lead to a better understanding of viruses and other infectious diseases.
3. Education
The pandemic has affected the education system globally, with many institutions closing and students learning from home. Teachers and educators are now incorporating technology in teaching, and the pandemic has accelerated the adoption of e-learning platforms. This has led to the development of new ways to learn and teach, and new online learning platforms are expected to emerge in the future.
4. Engineering
The pandemic has led to an increase in demand for essential supplies such as ventilators, personal protective equipment (PPE), and other medical devices. This has led to the development of new designs and manufacturing processes that are more efficient. The need for innovation has also led to the development of new solutions, such as 3D printing of medical supplies.
5. Mathematics
Mathematical models are used to understand the transmission of diseases, and the COVID-19 pandemic has led to the development of new models to understand the spread of the virus. These models help policymakers and public health officials make decisions to control the pandemic.
In conclusion, the COVID-19 pandemic has impacted STEM fields significantly, leading to new developments and innovations. With increased technology adoption, biomedical research, e-learning platforms, and engineering, the STEM fields are expected to change and adapt to the new normal. It is crucial to keep up with these changes and find ways to take advantage of the opportunities presented by the pandemic.
learn more about STEM fields here:
https://brainly.com/question/30082530
#SPJ11
Here is a CPM network with activity times in weeks:
b. How many weeks will the project take to complete? c. Suppose F could be shortened by two weeks and B by one week. By how many weeks would this r
Answers
a) The Critical Path Method (CPM) network provided consists of several activities with their respective duration in weeks.
b) The sum of the durations of activities along the critical path gives us the total duration of the project.
c) If they have slack time, the project duration may not change as the reduced duration will still fall within the slack time.
a) The CPM network provided is not visible in the given prompt. To determine the project duration, it is necessary to have a visual representation of the network with activity relationships and durations.
b) The project duration can be determined by finding the critical path. The critical path is the longest path through the network and consists of activities with zero slack time. By summing the durations of activities along the critical path, we obtain the total duration of the project.
c) If activities F and B can be shortened by two weeks and one week, respectively, the impact on the project duration depends on their position in the network. If both activities are on the critical path, reducing their durations will directly reduce the project duration by the corresponding time reductions. However, if F and B have slack time, the project duration may not change significantly, as the reduced durations will still fall within the available slack time. It is essential to evaluate the new critical path and any potential changes in activity dependencies to determine the precise impact on the project duration.
Learn more about CPM network here : brainly.com/question/14992192
#SPJ11
Write a program that computes the sum of all integers that exist within the range 611 to 1742 (inclusive on both ends) that have the value 6 in their ONES place. For example, 6, 76 and 926 all have the value 6 in their ONES place. When you are finished enter the sum you computed as the answer to this question.
Answers
When the loop finishes, the program prints out the final value of `sum`, which represents the sum of all the integers between 611 and 1742 (inclusive) that have a 6 in their one's place.
Running this program gives us a final answer of 159636.
Here's a Python program that calculates the sum of all integers between 611 and 1742 (inclusive) that have a 6 in their ones place:
```
sum = 0
for i in range(611, 1743):
if i % 10 == 6:
sum += i
print(sum)
```
The program initializes a variable `sum` to zero, and then loops over all the integers in the range from 611 to 1742 (inclusive) using a `for` loop. For each integer in that range, it checks whether its ones place (the last digit) is a 6, by using the modulo operator `%` to check whether the integer is evenly divisible by 10 (since the remainder when dividing by 10 gives you the ones place digit). If the ones place digit is 6, the program adds that integer to the running total stored in `sum`.
When the loop finishes, the program prints out the final value of `sum`, which represents the sum of all the integers between 611 and 1742 (inclusive) that have a 6 in their one's place.
Running this program gives us a final answer of 159636.
learn more about Python program
https://brainly.com/question/28691290
#SPJ11
The most common types of chart are pie, column, bar, line, and area
true or false
Answers
Answer:
true
Explanation:
i think its true
What menu allows you to add different features to your document?
Answers
Answer:
The Insert Menu. The insert menu is used to place various objects into your document, such as page numbers, pictures, symbols, comments and other objects. Commands include break, date and time, field, symbol, reference, web component, text box, file and hyperlink.hope it helps ya mate!ت︎what is a example of a static web page. A. the about us page
B. the current affairs page
C. the ads in a website
D. the weather ticker
Answers
Answer:
A. the about us page
Explanation:
The about us page usually never changes, so it is a static web page.
what human-readable data
Answers
Explanation:
what?? there is no question
Answer: A human-readable medium or human-readable format is any encoding of data or information that can be naturally read by humans.
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
Pick all the correct answers

Answers
Before you could train as a physician, you first had to become _____.
Answers
Mike decides to humiliate a former friend by posting embarrassing photos on social media Which ethical standard did he violate?

Answers
Answer:
The answer is "Human dignity "
Explanation:
It is the basic human nature, in which it is the recognition of the importance of humans, and it is inherent, and also that they deserve respect for just being humans, and the wrong choice can be defined as follows:
Property rights are the wrong choice because it is used to determine the use and possession of a resource or economic good. Confidentiality is also a wrong choice because it is a detail that provides verbally or in writing. The term civility also was wrong because it relates to politeness.Plaintext is transformed into ciphertext using two keys and a decryption algorithm. true false
Answers
False. Plaintext is transformed into ciphertext using a single key and an encryption algorithm, not two keys and a decryption algorithm.
The encryption algorithm applies various mathematical operations to the plaintext using the key to produce the ciphertext. The resulting ciphertext is unreadable and unintelligible without the corresponding decryption key and the decryption algorithm.
In symmetric encryption, the same key is used for both encryption and decryption. This means that the sender and the receiver must share the same key. In asymmetric encryption, also known as public key encryption, there are two separate keys: a public key used for encryption and a private key used for decryption. The public key can be freely shared, while the private key is kept secret.
To summarize, plaintext is transformed into ciphertext using a single key and an encryption algorithm, not two keys and a decryption algorithm.
Learn more about encryption algorithm: https://brainly.com/question/31807283
#SPJ11
When you add a zero to the right of a decimal number, it multiplies its value by 10 (For example, "15" becomes "150"). What similar result happens to the value of a binary number when you add a zero on the right? (For example, "11" would become "110").
Answers
Hope this helps ʕ•ᴥ•ʔ
When you you add zero to the right hand side of a binary number such as 11, This binary number is going to become twice its value.
All the number that were 1 are now two times of what they were. We would have a solution like this:
(11)₂ = (1x2)¹ + (1x2)⁰
= 2 + 1
= 3
(110)₂ = (1x2)² + (1x2)¹ + (0x2)⁰
= 1x4 + 1x2 + 0x1
= 4+2+0
= 6
In conclusion, adding 0 to the right hand side of a binary number increases the number by 2. From the solution above, we can see 11 = 3, but after 0 was added, 110 = 6
Read more at https://brainly.com/question/14789125?referrer=searchResults
in a basic program with 3 IF statements, there will always be _________ END IIF's.
a)2
b)3
c)4
Answers
Answer:
c)4
Explanation:
Hope it could helps you
Which cisco ios command can be used to display the roas configuration on a router?
Answers
The cisco ios command can be utilized to display the roas configuration on a router is show interfaces VLAN.
What is the show VLAN command?Open Network Adapters in Device Manager. Choose Properties by doing a right-click on the NIC. On the Advanced tab, click. To find the VLAN ID, scroll down.
The switch's active VLANs are listed with their VID, name, and status using the show VLANs command. Only when the switch is operating with GVRP enabled and one or more ports have dynamically joined an advertised VLAN do dynamic VLANs show.
What is ROAS in the network?You can split up a router's single physical interface into logical interfaces that will be set up as trunk interfaces to enable interVLAN connectivity. All VLANs are able to connect with each other through a single physical interface using the router on a stick (ROAS) interVLAN communication technique.
Therefore, the correct answer is A) show interfaces VLAN.
The complete question is:
Which Cisco IOS command can be used to display the ROAS configuration on a router?
A) show interfaces VLAN.
B) show VLANs.
C) show VLAN.
D) show roas.
To learn more about show interfaces VLAN refers to:
https://brainly.com/question/9356255
#SPJ4
it is used to replace numeric number of a website
Answers
greatflombles or gr8flombles or go2flombles
A predefined formula that performs calculations by using specific values in a particular order or structure.
Answers
Using specified values in a predetermined order or structure, a function is a formula that already exists and executes calculations.
A function is a predefined formula in mathematics, engineering, computer science, and other fields that performs a specific task by using a set of inputs, known as arguments or parameters, and returns a result. Functions are used to simplify complex calculations or operations, and they typically follow a specific syntax or structure that determines how the inputs and outputs are processed.
Functions can perform a wide range of tasks, from basic arithmetic operations like addition and subtraction to complex statistical analysis, data processing, and machine learning algorithms. They can take any number of inputs and return any type of output, depending on their specific purpose and implementation.
Functions are widely used in programming languages like Python, Java, and C++, as well as in spreadsheet applications like Ms Excel and Sheets, where they provide a powerful tool for performing calculations and automating tasks.
Learn more about function here:
https://brainly.com/question/29796477
#SPJ4
Atomic integers in Linux are useful when A) several variables are involved in a race condition. B) a single process access several variable involved in a race condition. C) an integer variable needs to be updated. D) All of the above.
Answers
Atomic integers in Linux are useful when an integer variable needs to be updated.
What is an Atomic Integer?This is known to be an applications that is said to be a form of an atomically incremented counters, and it is one which cannot be used as a kind of replacement for any Integer.
Therefore, Atomic integers in Linux are useful when an integer variable needs to be updated.
Learn more about Atomic integers from
https://brainly.com/question/20515314
#SPJ1
A user is redesigning a network for a small company and wants to ensure security at a reasonable price. The user deploys a new application-aware firewall with intrusion detection capabilities on the ISP connection. The user installs a second firewall to separate the company network from the public network. Additionally, the user installs an IPS on the internal network of the company. What approach is the user implementing
Answers
"Layered approach" will be the appropriate response.
The method that divides the OS into multiple layers, is a layered approach. The latter empowers application developers to modify their internal functions as well as enhances adaptability.The network idea throughout this method is generally separated into multiple levels and a certain responsibility or activity is delegated to every other layer.
Thus the above is the right answer.
Learn more layered approaches here:
https://brainly.com/question/10105615
How would you describe the relationship between blocks of code and commands?
Answers
Click this link to view O*NET’s Work Activities section for Chefs and Head Cooks.
Note that common activities are listed toward the top, and less common activities are listed toward the bottom.
According to O*NET, what are common work activities performed by Chefs and Head Cooks? Check all that apply.
making decisions and solving problems
repairing electronic equipment
coordinating the work and activities of others
maintaining interpersonal relationships
taking payments from customers
inspecting equipment
Answers
Answer:
A, C, D, and F
Explanation:
I just did it
Answer:
1, 2, 3 and 5
Explanation:
Leana was correct
I=5
While I <=20
TextWindow.Write (A + " " )
I = I + 6
EndWhile
Answers
The code provided is a simple example of a while loop written in the BASIC programming language. The loop uses a counter variable 'I' to execute a block of code repeatedly until a specific condition is met.
In this particular example, the loop initializes the variable 'I' to 5, and then executes a block of code that writes the value of a variable 'A' to the console using the TextWindow.Write method. After writing the value to the console, the loop increments the value of 'I' by 6.The loop continues to execute the code block and increment the value of 'I' until the condition 'I <= 20' is no longer true. This means that the loop will execute as long as the value of 'I' is less than or equal to 20. Once the value of 'I' becomes greater than 20, the loop terminates, and the program moves on to the next line of code.
To learn more about while loop click the link below:
brainly.com/question/15091477
#SPJ1
Can a computer evaluate an expression to something between true and false? Can you write an expression to deal with a "maybe" answer?
Answers
Answer:
yes it can
Explanation:
Computers cannot evaluate an expression to be between true or false.
Expressions in computers are represented in boolean values; i.e. they can only take one of two values (either true or false, yes or no, 1 or 0, etc.)
Take for instance, the following expressions will be evaluated to true, because the expressions are true.
\(\mathbf{1 + 2 = 3}\).\(\mathbf{5>4}\).\(\mathbf{4 + 4 <10}\)The following expressions will be evaluated to false, because the expressions are false.
\(\mathbf{1 + 2 > 3}\).\(\mathbf{5=4}\).\(\mathbf{4 + 4 >10}\)The above highlights show that, a computer cannot evaluate expressions to another value other than true or false
Read more about computer expressions at:
https://brainly.com/question/17500565
how do i give brainliest? if what you say works i'll give de brain
Answers
two people have to answer the question and at the bottom of the question you'll see a crown and you just click on that to give them brainliest
Answer:
When Two people answer a question A crown should appear at the bottom where you find the buttons like and rat/e so once you click it the crown will go to the top of the question of the question that you think is the best.
Explanation:
(d) What other services beside cloud-based software may be provided by Internet hosts?[1]
Answers
Answer:
Internet
(Some have Cable TV)
what does a CPU use to temporarily store data
a) buffer
b) track
c) sector
d) cylinder
Answers
Answer:
a) buffer is the right answer
The ? bar gives you information related to the document such as slide number, theme and whether or not the computer has found an error in the text
Answers
Answer:
Status bar
Explanation:
The status bar is a horizontal bar usually located at the bottom of the screen or window, showing information related to a document being edited such as slide number, current theme template, spelling and grammar, language, zoom, notes, comments, permissions, signatures e.t.c.
It can be used to group information by dividing into sections and also provides several View options.
WILL GIVE BRAILIST IF ANSWER RIGHT

Answers
Answer:
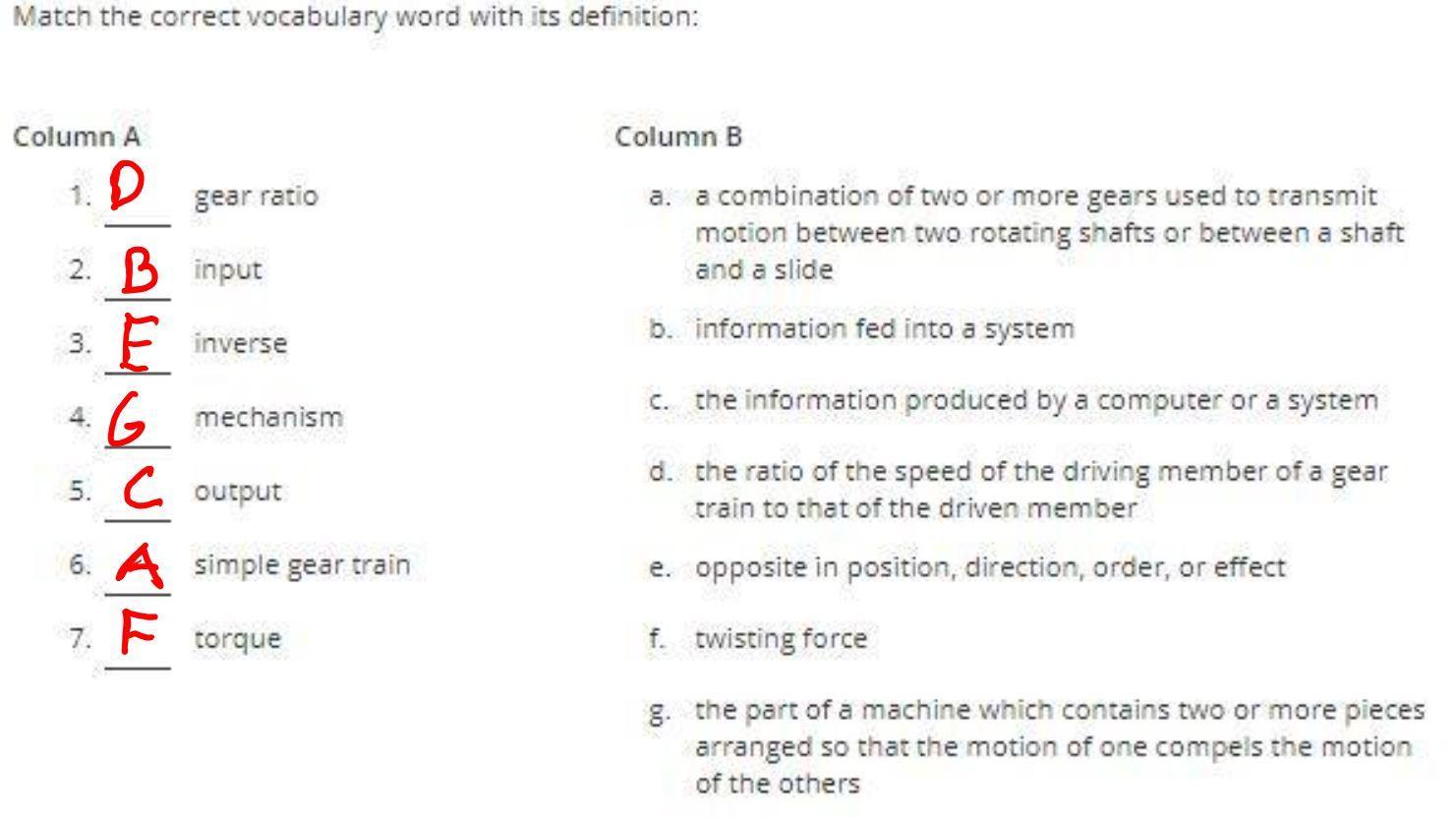
See Photo For Matching.
Which statement about intellectual property is true? (CSI-7.6) Group of answer choices It is okay to use code you find on the internet, since it is searchable. Since intellectual property is about your ideas, they aren't covered by any laws. Documentation of your ideas isn't important to prove intellectual property. Laws are in place to cover your creative work, which includes code you have written.
Answers
Answer:
Laws are in place to cover your creative work, which includes code you have written.
Explanation:
Copyright law can be defined as a set of formal rules granted by a government to protect an intellectual property by giving the owner an exclusive right to use while preventing any unauthorized access, use or duplication by others.
A copyright can be defined as an exclusive legal right granted to the owner of a creative work (intellectual property) to perform, print, record, and publish his or her work. Also, the owner is granted the sole right to authorize any other person to use the creative work.
For instance, copyright law which protects the sharing and downloading rights of music is known as the Digital Millennium Copyright Act (DMCA).
An intellectual property can be defined as an intangible and innovative creation of the mind that solely depends on human intellect.
Simply stated, an intellectual property is an intangible creation of the human mind, ideas, thoughts or intelligence. They include intellectual and artistic creations such as name, symbol, literary work, songs, graphic design, computer codes, inventions, etc.
Hence, laws are in place to cover a person's creative work, and it includes code he or she have written.
why over the course of time have more programming language been developed