When does a Developer become the sole owner of a Sprint Backlog item? A) Never. All Sprint Backlog items are "owned" by the Developers on the Scrum Team even though each item may be implemented by an individual Developer.
Answers
According to the Scrum framework, all Sprint Backlog items are owned by the Developers on the Scrum Team. This means that there is no point at which a single Developer becomes the sole owner of a Sprint Backlog item.
This is an important aspect of the Scrum framework because it encourages collaboration and collective ownership of the work being done. It helps to ensure that the team is working together towards a common goal, rather than working independently on separate tasks.
In practical terms, this means that each Sprint Backlog item is assigned to the entire team during Sprint Planning. The team then works together to determine how best to implement each item, with individual Developers taking on specific tasks as needed. Throughout the Sprint, the team works together to ensure that all Sprint Backlog items are completed on time and to the required standard.
To know more about framework visit:-
https://brainly.com/question/28142262
#SPJ11
Related Questions
Which Annotation tool provides the ability to convert the mouse icon when giving a presentation to better focus the audience attention?
1. Arrow
2. Ink Color
3. Eraser
4. Laser Pointer
Answers
Describe, with examples, the way in which a defect in software can cause harm to a person, to the environment, or to a company
Answers
Answer:
Losing jobs. Fire. Destruction of property.
Explanation:
Having a company shut down due to lack of protection and having people testify products unsafe. If software blows up it could cause desturction of property therefore causing the effect of many people losing their jobs.
Can able to Computer decide its input by itself? How ?
Answers
john walls ride the bus with no hand's person is right
Select the correct answer.
Jack is part of the software quality assurance team in a company. Which activity should Jack perform as a part of software quality assurance?
O A.
billing
ОВ.
recruiting
OC.
testing
OD
installing
O E.
accounting
Answers
Answer:
E
Explanation:
Research the CCMA and answer the following questions (worth 7.5 points each): 1. What is the cost to renew? 2. What is the website to renew through? 3. What is the duration of certification? 4. What is the process to renew?
Answers
The specific organization or context of CCMA is not mentioned in the question. Without further information, it is challenging to provide accurate answers regarding the cost to renew, the website to renew through, the duration of certification, and the process to renew.
To obtain the required information, it is recommended to research the specific CCMA organization or certification program in question and refer to their official website, documentation, or contact their relevant authorities for accurate and up-to-date information regarding renewal costs, duration, website, and renewal process.
CCMA stands for different organizations or programs in various fields, such as the Contact Centre Management Association, Canadian Construction Materials Centre, California Certified Medical Assistant, etc. Each organization or program may have different renewal procedures, costs, and websites. To find the accurate answers, it is necessary to identify the specific CCMA context and conduct research accordingly. Visiting the official website, reviewing certification guidelines, FAQs, or contacting the relevant authorities associated with the CCMA program will provide the most accurate and up-to-date information regarding the cost to renew, the website to renew through, the duration of certification, and the process to renew.
Learn more about website here :
https://brainly.com/question/19459381
#SPJ11
which vpc component is useful when you need to allow the instances in a private subnet of an amazon vpc to connect to the internet to perform tasks like downloading patches and updates, while still preventing any inbound connections from being initiated to these instances via the internet? select one answer internet gateway nat gateway vpc peering connections transit gateway
Answers
The VPC component that is useful when you need to allow the instances in a private subnet of an amazon VPC to connect to the internet to perform tasks like downloading patches and updates, while still preventing any inbound connections from being initiated to these instances via the internet is a NAT gateway.
What is internet?The internet is a global network of interconnected computers and devices that allows communication, information sharing, and access to resources over vast geographical distances.
It is a decentralized network, meaning there is no central authority controlling it. Instead, it is made up of numerous interconnected networks operated by different organizations and individuals.
Learn more about internet on https://brainly.com/question/21527655
#SPJ4
What is a nontechnical method that a cybercriminal would use to gather sensitive information from an organization?.
Answers
A non-technical method that a cybercriminal may use to gather sensitive information from an organization is social engineering.
Social engineering involves manipulating people into divulging confidential information or performing certain actions. Here's how it works in a few steps:
1. Research: The cybercriminal gathers information about the targeted organization, such as its employees, hierarchy, and public information.
2. Pretexting: The cybercriminal creates a believable pretext or story to gain the trust of employees. They might pretend to be a co-worker, vendor, or customer.
3. Building rapport: The cybercriminal establishes a rapport with the targeted individual to create a sense of familiarity and trust.
4. Exploitation: Using the trust they've gained, the cybercriminal persuades the target to provide sensitive information, such as login credentials or customer data.
5. Information gathering: Once the cybercriminal obtains the desired information, they can use it for malicious purposes, such as identity theft or unauthorized access.
In summary, social engineering is a non-technical method that cybercriminals use to manipulate people and gather sensitive information from an organization.
Learn more about a cybercriminal: https://brainly.com/question/19819005
#SPJ11
If you had a circuit with a voltage of 228 and a resistance of 13,the current would be ____ amps. (ROUND TO TWO DECIMALS PLACES) hint....using V=IR Rewrite the question to solve for I.
Answers
You have been trying all day to check your direct messages on social media. The site is really slow to load and sometimes you can't even get to it at all. Your friends seem to be having the same problem. What could be happening? It might be getting hit with a DDoS attack. You might have malware preventing you from getting to the site. Your firewall is blocking the site. The site is undergoing upgrades and will be back soon.
Answers
Answer:
You might be geting hit by a DDoS
Explanation:

Lexicographic Comparison • Using the same name from the previous problem, tell the user whether their name comes before or after your name in the dictionary. Indexes • Test whether or not the name contains the letter ‘e’ in the first 3 letters
I have the project in a downloadable pdf.
I can't seem to be able to do "Lexicographic Comparison", with no clue how.
And "Starts With…", I am only able to print if their input is that 1 letter, not the first letter in a word.
Answers
You can also find this code on the repl.it platform. Due to Brainly's policy I can't copy it, I've attached it as a photo and file and you can check it in the comments. Good luck!

2.12.6 right vs left square
Answers
The terms "right" and "left" square refer to the orientation of a square shape. A square is considered "right" if its sides are perpendicular to each other and its corners form right angles of 90 degrees. Conversely, a square is considered "left" if its sides are not perpendicular to each other and its corners do not form right angles.
The difference between right and left squares may seem minor, but it can have significant consequences in various fields such as engineering, construction, and design. For example, in construction, right squares are essential for ensuring that walls and other structures are built at perfect right angles to each other. In graphic design, left squares can be used to create more dynamic and visually interesting compositions by breaking away from the rigid constraints of right angles.
Overall, the choice between using a right or left square depends on the specific application and the desired outcome. Both orientations have their own advantages and limitations, and it is up to the user to determine which one is appropriate for their needs. Understanding the difference between right and left squares is an important aspect of geometry and can be useful in many different contexts.
For such more question on right angles
https://brainly.com/question/64787
#SPJ11
Which threat actor will have prior knowledge of the network layout to perform a malicious attack?.
Answers
The threat actor will have prior knowledge of the network layout to perform a malicious attack is Organized cybercriminals.
Which of the following threats has a financial incentive?The most obvious threat actor is a cybercriminal. They primarily target companies in order to profit financially. Although cybercrime gangs are becoming more prevalent, individuals can also be a serious menace. Cybercriminals have a wide range of abilities when it comes to their attack kinds and skill sets.
Note that Profit is the driving force behind organized cybercriminals, thus it seems to reason that they would take advantage of the business prospects that hacking offers. Individually identifiable information (PII) like credit card numbers, login credentials for accounts, and Social Security numbers is what cybercriminal actors are most interested in collecting.
Learn more about cybercriminals from
https://brainly.com/question/25157310
#SPJ1
2 features of mark i
Answers
Answer:
Mark I was enourmous in size, measuring 8 feet high, 51 feet long and three feet deep. It weighed 5 tons, used 530 miles of wire and 730,000 separate parts. The operation of these parts was powered and synchronized by a long horizontal rotating shaft. A four horsepower engine drives the mechanical parts.
Which of the following is an advantage of using variables?
A.It reduces the number of functions that are necessary in the program.
B.It increases the number of values that are used in a program.
C.It erases the default values.
D.It makes it less likely that an error will be introduced into the code.
Answers
Answer:
D. It makes it less likely that an error will be introduced into the code.
Explanation:
Write a python function that will return true if the two given integer values are equal or their sum or difference is 5
Answers
Here's a Python function that checks if two given integer values are equal or if their sum or difference is 5.
def check_integer_values(a, b):
if a == b or a + b == 5 or abs(a - b) == 5:
return True
else:
return False
In this function, a and b are the two integer values being compared. The function checks if a is equal to b (a == b), if their sum is 5 (a + b == 5), or if their absolute difference is 5 (abs(a - b) == 5).
If any of these conditions are true, the function returns True. Otherwise, it returns False.
You can call this function and pass your integer values to check if they satisfy the conditions. For example:
print(check_integer_values(3, 8)) # False
print(check_integer_values(2, 3)) # True
print(check_integer_values(7, 2)) # True
Learn more about Python here:
brainly.com/question/30391554
#SPJ11
what do i do for this not to stop me from trying to ask a question. / What phrases are / could be hurtful to brainly? - Don't use such phrases here, not cool! It hurts our feelings :(
Answers
Some one help pls will mark brainless !!!!!
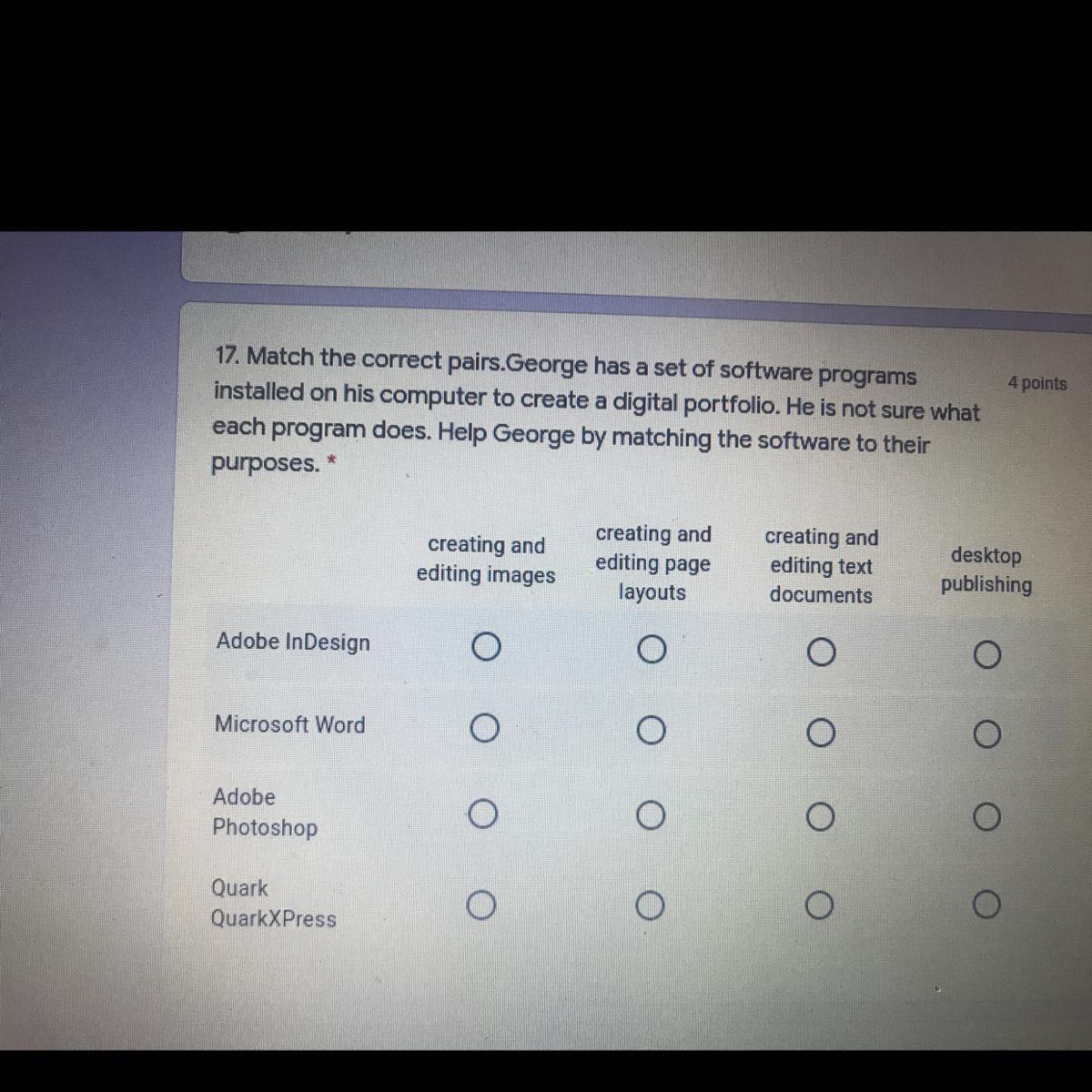
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
Show an example of a DHCP packet with a padding option.
4. Show an example of a DHCP packet with an end-of-list option.
5. What is the maximum number of seconds that can be stored in the Number of Seconds field of a DHCP packet?
Answers
The above looks at an example of a DHCP packet with a padding option among other related concepts.
How is this so?Example of a DHCP packet with a padding option
DHCP Packet -
- Message Type - Discover
- Client IP Address - 0.0.0.0
- Options -
- Option 53 - DHCP Message Type (Discover)
- Option 0 - Padding (0x00)
Example of a DHCP packet with an end-of-list option -
DHCP Packet -
- Message Type - Offer
- Client IP Address - 192.168.1.10
- Options -
- Option 53 - DHCP Message Type (Offer)
- Option 255 - End-of-List (0xFF)
The maximum number of seconds that can be stored in the Number of Seconds field of a DHCP packet is 65535 seconds.
Learn more about DHCP at:
https://brainly.com/question/10097408
#SPJ4
ternary operators of computer
please explain.
Answers
Answer:
It's a compact way of doing an if-else statement.
General Format is
<condition> ? <if condition is true> : <else>;
Example:
I could rewrite:
if(a==1) temp = 1;
else temp = 999;
as
temp = (a==1) ? 1 : 999;
Which task can be completed using both the Shape Fill and Shape Outline panes of PowerPoint?
O adding color
O adding weight
O adding texture
O adding a picture
Answers
Answer:
A.) adding color
Explanation:
just did it on edg 2021
Answer:
A. Adding color
Explanation: Just did it and got it right on Edg 2021
What is the force that resists the motion of an object through a fluid?
Answers
Answer:
Friction (drag)
Explanation:
The force resisting motion through a fluid is a type of friction, that is called drag.
your friend is setting up a computer and plans to use windows raid striping. he asks you howmany hard drives he should install in the system. what do you tell him?
Answers
For setting up a computer with Windows RAID striping, your friend should install a minimum of two hard drives in the system.
If your friend plans to use Windows RAID striping, he should install at least two hard drives in the system.
RAID striping requires a minimum of two drives, which are then combined to act as one logical drive with increased performance and storage capacity. However, it is recommended to use an even number of drives to get the best performance and avoid potential data loss. So, your friend can install two, four, six, or more drives, depending on his storage and performance needs.Thus, For setting up a computer with Windows RAID striping, your friend should install a minimum of two hard drives in the system. RAID striping (RAID 0) requires at least two drives to distribute data across them for improved performance.Know more about the Windows RAID striping,
https://brainly.com/question/29039401
#SPJ11
A user plans to travel and needs to remotely connect to the corporate network. What technology can be used to accomplish this
Answers
Virtual Private Network (VPN) can be used to remotely connect to the corporate network while traveling.
A VPN creates a secure, encrypted tunnel between the user's device and the corporate network, allowing the user to access company resources as if they were on the same local network.
VPN technology ensures that all data transmitted between the user's device and the corporate network is encrypted and protected from interception, ensuring confidentiality and integrity.
VPNs are widely used by organizations to provide secure remote access to their employees, contractors, and partners who need to connect to corporate resources from outside the office or while traveling. Different types of VPNs are available, including SSL VPN, IPsec VPN, and PPTP VPN, with varying levels of security and ease of use.
For more questions like Network click the link below:
https://brainly.com/question/28590616
#SPJ11
What is the final value for X ?
x= 1
x=13
x= x+3
x=0
Answers
Answer:
60
Explanation:
Question 1 of 10
What is one reason why a business may want to move entirely online?
A. To focus on a global market
B. To limit the number of items in its inventory
C. To avoid paying state and local taxes
O D. To double the number of employees
Answers
I think it is A because the moving online for businesses would only affect the global market. B,C, and D are not affected by moving online. The best answer is A
import java.util.Scanner;
public class PigLatin {
public static void main(String args[]) {
Scanner console =new Scanner(System.in);
System.out.println("Please enter a word");
String phrase=console.nextLine();
System.out.println(eachWord(phrase));
}
public static String eachWord(String phrase) {
String help[]=phrase.split(" ");
for(int i=0; i
if (help[i].charAt(0) == 'a'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'e'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'i'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'o'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'u'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'A'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'E'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'I'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'O'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'U'){
return help[i] + "-ay";
}
else {
return help[i].substring(1)+"-"+help[i].charAt(0)+"ay";
}
}
return "aoujbfgaiubsgasdfasd";
}
I need help with this Pig Latin Program. I want to split the string so each word can run through the method eachWord. I don't know how to revamp this!
Answers
Answer:b
Explanation:
I took quiz
Answer:
uuuuuuuuuuhhm
Explanation:
CODE!
where to buy a ps5
I really want one please help meh
Answers
Answer:
You can buy one at gamestop, target, walmart, best buy and probably more stores
Answer:
Amazon, walmart, target, gamestop?
Explanation:
I'm sure a quick go ogle search will get u what u want to see, have a nice day and I hope u get what u want!
Which of the following is NOT an important factor when choosing an insurance company?
Licensing
Price
Financial solidity
Location
Answers
Answer:
financial solidity
Explanation:
it will be always be ready while sound or not
A factor which isn't important when choosing an insurance company is: D. location.
What is an insurance company?An insurance company is a business firm that is establish to collect premium from all of their customers (insured) for losses which may or may not occur, so they can easily use this cash to compensate or indemnify for losses incurred by those having high risk.
Generally, it is important to consider the following factors when choosing an insurance company:
LicensingPriceFinancial solidityHowever, location is a factor which isn't important when choosing an insurance company.
Read more on insurance here: https://brainly.com/question/16789837
suppose that you know a mac value x and the key k that was used to compute the mac, but you do not know the original message
(a) (8pt) Show that you can construct a message M that also has its MAC equal to X. Note that we are assuming that you know the key K and the same key is used for both MAC computations.?
(b) (2pt) How much of the message M are you free to choose?
Answers
(a) To construct a message M that has the same MAC value as X, you can use a technique called a "length extension attack".
Essentially, you can take the MAC value X and the key K, and use them to compute a new MAC value for a message M' that is an extension of the unknown original message. Specifically, you can choose M' to be the concatenation of the original message with some additional data, such as padding or a new message suffix.
Then, you can use the MAC algorithm and key K to compute the MAC value of M', which will be equal to X. This works because the MAC algorithm is deterministic - given the same key and message, it always produces the same MAC value - so as long as you know the key and the MAC value, you can compute a valid MAC for any message that extends the original message.
(b) You are free to choose any extension to the original message that produces the same MAC value as X. However, you must be careful to ensure that the extension does not introduce any security vulnerabilities or allow an attacker to exploit the system.
In general, it is best to use a standard padding scheme or other well-established method for message extension, rather than inventing your own. Additionally, you should consider the potential impact of the message extension on the overall security of the system, and consult with a security expert if necessary.
Learn more about Concatenation here:
https://brainly.com/question/30402466
#SPJ11
Which option is used in Access to locate and retrieve data that may be present in multiple database tables within the database?
queries
forms
procedures
subroutines
Answers
Answer:
Subroutines
Explanation:
Answer:
queries
Explanation:
I just took the test.