Which automated method for VPN connection deployment would work best in combination with Microsoft Intune or Microsoft Endpoint Configuration Manager
Answers
There are different kinds of automated method for VPN connection deployment. The automated method for VPN connection deployment would work best is ProfileXML
ProfileXML is known to be often used as a delivery methods in Windows PowerShell, Microsoft Endpoint Configuration Manager, and Intune. For an individual to be able to use the ProfileXML VPNv2 CSP setting, one have to construct XML by using the ProfileXML schema.An individual can configure the Always On VPN client by using the PowerShell, Microsoft Endpoint Configuration Manager, or Intune. They all need an XML VPN profile to configure the appropriate VPN settings.
Learn more from
https://brainly.com/question/25554117
Related Questions
A rectangle has an area of 368. 4 in2, and its height is 15 in. Find the base of the rectangle.
A/24. 56 in
B/25. 64 in
C/26. 45 in
D/ 24. 56 cm
Answers
The correct answer is B/25. 64 in. The formula for the area of a rectangle is A = base × height. Given the area A = 368.4 in² and the height h = 15 in, we can rearrange the formula to solve for the base b. Dividing the area by the height, we get b = A / h = 368.4 in² / 15 in = 24.56 in. Rounded to the nearest whole number, the base is 25 in.
The area of a rectangle is determined by multiplying its base by its height. To find the base, we rearrange the formula: A = base × height. We substitute the given values, A = 368.4 in² and h = 15 in. Solving for the base, we divide the area by the height: b = A / h = 368.4 in² / 15 in = 24.56 in. Finally, rounding to the nearest whole number, we conclude that the base of the rectangle is 25 in. Therefore, the correct answer is B/25. 64 in.
Learn more about rectangle is determined here:
https://brainly.com/question/14812693
#SPJ11
After a group sets a project schedule, members should be prepared to
O make periodic adjustments on an as-needed basis.
make changes when some members fall behind.
drop other activities so they can complete their job on time.
complete a study-time survey to prove they can do the work.
Answers
After a group sets a project schedule, members should be prepared to complete a study-time survey to prove they can do the work.
What is a group project?A group project is a project in which more than one person work together. Group projects are given to improve the work, as various minds can bring out various implements for the project.
Thus, the correct option is D. complete a study-time survey to prove they can do the work.
Learn more about group project
https://brainly.com/question/14488746
#SPJ1
Answer:
A on edge
Explanation:
Why should even small-sized companies be vigilant about security?
Answers
Answer:businesses systems and data are constantly in danger from hackers,malware,rogue employees, system failure and much more
Explanation:
the siri personal assistant application on apple's iphone 5s is an example of a ________.
Answers
The Siri personal assistant application on apple's iPhone 5s is an example of a natural language processing (NPL) system.
What is a natural language processing system?
Scaling other language-related jobs is accomplished through the use of natural language processing, which enables computers to speak with people in their own language. As an illustration, NPL enables computers to read text, hear the voice, understand it, gauge sentiment, and identify the key points.
While the science of natural language processing(NPL) is not new, the technology is growing quickly as a result of a rise in interest in human-to-machine communication, as well as the availability of massive data, powerful computation, and improved algorithms.
To learn more about natural language processing system, use the link given
https://brainly.com/question/14222695
#SPJ1
What documents are needed for real id in california.
Answers
When applying for a REAL ID, the document needed are:
A Proof of your identity (such as U.S. birth certificate, valid U.S. passport, permanent resident card, etc.An evidence of Social Security number ( such as Social Security card, W-2 form, etc.).What is an ID?An Id is known to be a tool or something that is often used in the identification of a person.
Therefore, When applying for a REAL ID, the document needed are:
A Proof of your identity (such as U.S. birth certificate, valid U.S. passport, permanent resident card, etc.An evidence of Social Security number ( such as Social Security card, W-2 form, etc.).Learn more about ID from
https://brainly.com/question/16045720
#SPJ1
O B. the bulk of a person's income.
a
C. a person's excess income.
Those taking illegal drugs, or using a prescription drug without a medical need, are likely ...
A. to be making a calci
Answers
im confused by the formatting of this- maybe type it again ;-;
Question 1 (2 points)
What happens to an object's acceleration as mass of the object increases but the
force stays the same?
The acceleration is zero
The acceleration stays the same
The acceleration increases
The acceleration decreases

Answers
Answer:
it would stay the same
Explanation:
am using a Visual Studio toolchain with the vscode-cpptools extension for VS Code and getting the following error:cl.exe build and debug is only usable when VS Code is run from the Developer Command Prompt for VS.What is the cause of the error and how can it be resolved?
Answers
The error "cl.exe build and debug is only usable when VS Code is run from the Developer Command Prompt for VS" occurs because the cppTools extension requires certain environment variables to be set up for the Visual Studio toolchain to work correctly.
These environment variables are set up automatically when Visual Studio is launched from the Developer Command Prompt, but not when VS Code is launched directly.
To resolve this error, you can launch VS Code from the Developer Command Prompt for VS instead of launching it directly. Alternatively, you can manually set up the required environment variables by adding them to your system's environment variables. You can find the required environment variables and their values in the documentation for your Visual Studio toolchain. Once the environment variables are set up correctly, you should be able to build and debug your code using the cppTools extension in VS Code.
To know more about Command Prompt click here:
brainly.com/question/27986533
#SPJ4
Colby works as a shipping clerk for a major package delivery service. Some of his daily tasks include tracking shipments and entering orders. Which aspect of the Information Technology cluster would he most likely be trained in?
Answers
Answer: databases
Explanation:
The options include:
A. networking
B. databases
C. hardware
D. software
The aspect of the Information Technology cluster that he would most likely be trained in is the databases.
Database simply refers to a structured set of data which is being held in a computer. It helps in the storage of organized information.
Since some of his daily tasks include tracking shipments and entering orders, he'll be trained in database.
Answer:
I know that the answer would be Databases
Explanation:
If I am wrong I am sorry BTW this is for (EDGE 2021)
photo editing software, desktop publishing, email and word processing software is most likely to be used by:
a) law enforcement officers
b) musicians
c)mass media personnel
d)medical personnel
Answers
Answer:
c) mass media personnel
Explanation:
A software can be defined as a set of executable instructions (codes) or collection of data that is used typically to instruct a computer how to perform a specific task and to solve a particular problem.
Basically, softwares are categorized into two (2) main categories and these are;
I. System softwares.
II. Utility softwares.
Photo editing software, desktop publishing, email and word processing software is most likely to be used by a mass media personnel because he or she deals with the creation of various documents such as images, texts, multimedia files etc.
The algorithm below is used to find the largest element in a list of numbers.
By modifying one of the lines in the program it is possible to make the algorithm find the SMALLEST element. Which line would need to be modified and how?

Answers
The line that can be modified in the algorithm to return the smallest of the list is line 04
From the question, we understand that:
The algorithm returns the largest of all elements in a listThe above action is executed on line 04
To change the function of the algorithm to return the smallest, line 04 must be modified as follows:
IF (num < target)
Hence, the line that can be modified in the algorithm to return the smallest of the list is line 04
Read more about algorithms at:
https://brainly.com/question/24793921
What advantage does PNG offer over JPEG?
PNG files can have multiple layers for easy editing.
PNG images can have transparency.
PNG images can have brighter colors.
Answers
Answer:
In addition to those, PNG is also saved as a vector image and is saved as shapes, rather than as a raster, where it is saved as pixels
Explanation:
This is especially useful in graphic design and other applications, where PNG is able to have an infinite resolution because it is not composed of pixels.
PROJECT RISK MANAGEMENT: CASE STUDY Roy and his team identified some risks during the first month of the My R & R Intranet Project. However, all they did was document the risks in a list. They never ranked the risks or developed any response strategies. Because the project has had several problems, such as key team members leaving the company, users being uncooperative, and team members not providing good status information, Roy has decided to be more proactive in managing risks. He also wants to address positive risks as well as negative risks ASSIGNMENT INSTRUCTIONS 1. Read the Case Study 2. Create a risk register for the project using the Risk Register Excel template attached. Identify six potential risks, including risks related to the problems described in the Case above. Include both negative and positive risks. 3. Plot the six risks on a probability/impact matrix using the template attached. Also, assign a numeric value for the probability and impact of each risk on meeting the main project objective. Use a scale of 1 to 10 in assigning the values, with 1 representing the lowest values. For a simple risk factor calculation, multiply the probability score and the impact score. Add a column called Risk Score to your risk register to the right of the impact column. Enter the new data in the risk register. Copy your impact matrix and new risk register to a word document and write your rationale for how you determined the scores for one of the negative risks and one of the positive risks. 4. Develop a response strategy for one of the negative risks and one of the positive risks. Enter the information in the risk register. Copy your risk register and impact matrix to your word document with your rationale, response strategy, and a separate paragraph describing what specific tasks would be required to implement the strategy. Include time and cost estimates for each strategy as well
Answers
A risk response strategy for negative risks typically involves mitigating, avoiding, transferring, or accepting the risk, while for positive risks, strategies often include exploiting, enhancing, sharing, or accepting the risk.
1. Risk Register:
- Create a table with columns such as Risk ID, Risk Description, Risk Category, Probability, Impact, Risk Score, and Response Strategy.
- Identify six potential risks related to the problems mentioned in the case study. Consider risks such as key team members leaving, uncooperative users, lack of status information, etc. Make sure to include both negative and positive risks.
- Fill in the risk register with the identified risks and their respective details.
2. Probability/Impact Matrix:
- Create a 2x2 matrix with the X-axis representing the probability and the Y-axis representing the impact.
- Assign a numeric value (ranging from 1 to 10) for the probability and impact of each risk. The higher the value, the greater the probability or impact.
- Multiply the probability score by the impact score to calculate the Risk Score. Enter this value in the Risk Score column of the risk register.
- Copy the impact matrix and the updated risk register to a Word document.
3. Rationale:
- Select one negative risk and one positive risk from your risk register for which you'll provide the rationale.
- In your Word document, explain how you determined the scores for the selected risks. Consider factors such as the likelihood of occurrence, potential consequences, historical data, expert judgment, etc.
4. Response Strategy:
- Choose one negative risk and one positive risk to develop response strategies.
- In the risk register, add a column for Response Strategy and fill in the appropriate response for each risk.
- In your Word document, describe the response strategies chosen and explain why they are appropriate for mitigating the risks.
- Additionally, outline the specific tasks required to implement each strategy, along with time and cost estimates for each task.
Remember, a risk response strategy for negative risks typically involves mitigating, avoiding, transferring, or accepting the risk, while for positive risks, strategies often include exploiting, enhancing, sharing, or accepting the risk.
Learn more about Risk Register here:
https://brainly.com/question/31942299
#SPJ11
Before a new email application could be released to the public, it was released for a few days to some account holders of a website. The project team then collected feedback from this limited number of users and later made the email application available for public use. What type of testing did the project team use?
The project team used __ testing for the email application.
Answers
Answer:
closed
Explanation:
closed beta testing
Answer:
beta
Explanation:
Would X-ray waves carry a lot of energy? And do they have a high frequency?
Answers
Answer:
X-rays are very high frequency waves, and carry a lot of energy. They will pass through most substances, and this makes them useful in medicine and industry to see inside things.
Companies such as ORACLE, Amazon Web Services, and Microsoft offer courses to
learn about their technologies.
True
False
Answers
Companies such as ORACLE, Amazon Web Services, and Microsoft offer courses to learn about their technologies is a true statement.
What are Microsoft courses?The world of Microsoft technology is known to be one that is made of a lot of courses that people cab be able to choose a path and learn. They include:
Microsoft Cloud.Microsoft Security.Dynamics 365.Therefore, Companies such as ORACLE, Amazon Web Services, and Microsoft offer courses to learn about their technologies is a true statement.
Learn more about Microsoft from
https://brainly.com/question/20659068
#SPJ1
please help me out with answering the questions

Answers
10.
if "h" in letter:
#do something
11.
if value >= 13.6:
#do something
12.
if 5 < y < 11:
#do something
13.
if num1 == num2:
print("equal")
14.
num1 = int(input("Enter a number: "))
num2 = int(input("Enter a number: "))
if num1 > num2:
print(num1)
else:
print(num2)
15.
if number == 89 or number == 78:
print("Your number is equal to 89 or 78")
I hope this helps! If you have any other questions, I'll do my best to answer them.
please help, CodeHS nitro u7 frq
in java script!
Consider this implementation of the class Card, that stores information related to a cards monetary value, name, condition, and number in a set of collectible cards:
public class Card
{
private double value;
private String name;
private int setNum;
private String condition;
public Card (String Name, String Condition, double Value, int numSet){
name = Name;
condition = Condition;
value = Value;
setNum = numSet;
}
public String getName(){
return name;
}
public String getCondition(){
return condition;
}
public double getValue(){
return value;
}
public int getSetNum(){
return setNum;
}
}
A subsequent class CardCollection has been created with the instance variable ArrayList collection that stores a collection of cards. When instantiated, the CardCollection class takes an ArrayList as a parameter, and copies that ArrayList to the Collection instance variable. In this question, you will write three methods in the CardCollection class.
1. Write a method totalValue() which returns the total value of all cards in a card collection.
2. Write a method checkPerfect() that prints the name of the Cards in a collection that are in "perfect" condition.
3.Write a method orderNumerically() that reorders the ArrayList collection in numerical order by set number. Assume that the set includes 151 cards.
Answers
Here's a possible implementation of the three methods in the CardCollection class:
import java.util.ArrayList;
import java.util.Collections;
public class CardCollection {
private ArrayList<Card> collection;
public CardCollection(ArrayList<Card> cards) {
collection = new ArrayList<Card>(cards);
}
public double totalValue() {
double sum = 0.0;
for (Card card : collection) {
sum += card.getValue();
}
return sum;
}
public void checkPerfect() {
for (Card card : collection) {
if (card.getCondition().equals("perfect")) {
System.out.println(card.getName());
}
}
}
public void orderNumerically() {
Collections.sort(collection, (card1, card2) -> card1.getSetNum() - card2.getSetNum());
}
}
The totalValue() method calculates the sum of the values of all cards in the collection by iterating over the collection instance variable and adding up the value of each Card object.The checkPerfect() method prints the name of each Card in the collection that has a condition of "perfect". It does this by iterating over the collection and checking the condition of each Card object. If the condition is "perfect", it prints the name of the Card.To know more about Java visit:
https://brainly.com/question/26754476
#SPJ1
explain how you would redesign the dataviz class using the adapter pattern so that dataviz can be configured at runtime to use either superstats or uberstats.
Answers
The adapter pattern should be used to allow dataviz to be configured at runtime to use either superstats or uberstats. You can use this pattern to create a class that adapts the interface of dataviz to the interface of superstats or uberstats.
What is the adapter patternThe adapter pattern is a software design pattern that enables the interface of an existing class to be used by another class. This pattern is used to make two incompatible interfaces compatible with one another by converting the interface of one class into another interface that the other class requires.
How to redesign the dataviz class ?To redesign the dataviz class using the adapter pattern, follow these steps:
1: Determine the interface of dataviz
The first step in redesigning the dataviz class using the adapter pattern is to determine the interface of dataviz. This interface will be used to create an adapter that adapts dataviz's interface to the interface of either superstats or uberstats.
2: Determine the interface of superstats or uberstats
The second step in redesigning the dataviz class using the adapter pattern is to determine the interface of either superstats or uberstats. This interface will be used to create an adapter that adapts dataviz's interface to the interface of either superstats or uberstats.
3: Create an adapter class
The third step in redesigning the dataviz class using the adapter pattern is to create an adapter class. This adapter class should implement the interface of superstats or uberstats and should take an instance of dataviz as a constructor parameter.
4: Implement the adapter's interface methods
The fourth step in redesigning the dataviz class using the adapter pattern is to implement the interface methods of the adapter. These methods should call the corresponding methods of dataviz.
5: Use the adapter at runtime
The final step in redesigning the dataviz class using the adapter pattern is to use the adapter at runtime. You should create an instance of the adapter class and pass it to the code that requires either superstats or uberstats.
Learn more about adapter pattern at
https://brainly.com/question/14151686
#SPJ11
the security rules requirements are organized into which of the following three categories
Answers
The security rules requirements are categorized into three main categories, which are administrative, physical, and technical safeguards.
Administrative safeguards involve policies and procedures that are put in place to manage and maintain the security and confidentiality of electronic health information. This includes assigning security roles and responsibilities, conducting risk assessments, and implementing workforce security training programs. Physical safeguards, on the other hand, involve physical measures that are put in place to protect the physical hardware, software, and data centers that store electronic health information. This includes facility access controls, workstation use policies, and device and media controls. Technical safeguards refer to technology-based measures that are put in place to protect electronic health information and control access to it. This includes access control mechanisms, audit controls, and encryption and decryption mechanisms. All three categories of security rules requirements are important in ensuring the confidentiality, integrity, and availability of electronic health information.
To know more about requirements visit :
https://brainly.com/question/2929431
#SPJ11
Can anyone help with this

Answers
b) Hard Disk
c) Solid state drives (SSD)
Information stored on CD-ROM disc must be read and then erased.True or false?
Answers
Answer:
False
Explanation:
Cadillac Desert Chapter 10 Questions Chapter 10 "Chinatown" in Cadillac Desert begins by explaining the many small irrigation projects that existed before the large-scale Central Valley Project (CVP) and State Water Project (SWP, also called the Califomia Water Project) were created. The chapter goes into detail how the large water projects were conceived, lobbied and implemented, along with the various players, beneficiaries, and losers of the project. While reading Chapter 10 answer the questions below: 1. In 4-5 sentences, summarize the conception, hurdles, and implementation of the Central Valley Project 2. Did companies or individual farmers end up recelving the CVP water? How did they get around the problem of divestiture? Did the Bureau know about illegal landholdings? 3. In 4-5 sentences, summarize the conception, hurdies, and implementation of the State Water Project. Who were the champions of the SWP? Who opposed it? What tactics did Pat Brown use to sway voters? What challenges did Jeny Brown face? 4. What role did ground water play in the CVP and SWP? What are some of the problems with pumping groundwater out of the ground?
Answers
The conception of the Central Valley Project (CVP) involved the efforts of politicians, engineers, and landowners who saw it as a solution to water scarcity in California's Central Valley.
The conception of the Central Valley Project (CVP) began with the recognition of water scarcity in California's Central Valley, leading politicians, engineers, and landowners to advocate for a large-scale solution. However, the project faced significant hurdles. One challenge was securing funding, which was accomplished through a combination of federal financing and bond measures. Environmental concerns and opposition from farmers who feared losing their water rights also posed obstacles. To address the issue of divestiture, water districts were created, allowing both companies and individual farmers to receive CVP water. These districts entered into long-term contracts with the government, ensuring a steady water supply.
While the Bureau of Reclamation was aware of illegal landholdings within the CVP project area, they chose not to intervene. This was primarily due to political pressure and the desire to move the project forward. The focus was on completing the infrastructure and delivering water, rather than investigating and addressing illegal landholdings. Consequently, the issue of illegal land ownership remained largely unaddressed.
Despite these obstacles, the CVP was implemented through a combination of government funding, construction of dams and canals, and the formation of water districts. Companies and individual farmers eventually received CVP water, bypassing the problem of divestiture by forming water districts and entering into long-term contracts with the government. The Bureau of Reclamation was aware of illegal landholdings but turned a blind eye to them.
Learn more about engineers here:
https://brainly.com/question/31592475
#SPJ11
he following characteristics of disks make them convenient for being the secondary storage: a. it is possible to read a block from the disk, modify the block, and write it back into the same place b. a disk can access directly any block of information it contains c. all of the above d. none of the above
Answers
The characteristics of disks that make them convenient for being secondary storage are as follows:
It is possible to read a block from the disk, modify the block, and write it back into the same place.A disk can access directly any block of information it contains.Thus, the correct option for this question is C, i.e. all of the above.
What is Secondary storage?Secondary storage may be defined as a type of storage that is commonly utilized in order to store backup data that comes from primary storage.
The data is significantly get copied from the primary storage system to the secondary storage system through the use of replication or other data protection and recovery techniques.
Therefore, the correct option for this question is C, i.e. all of the above.
To learn more about Secondary storage, refer to the link:
https://brainly.com/question/86807
#SPJ1
Complete the following sentences by choosing the best answer from the drop-down menus. A/an _______ is a device used to protect computer against surges and spikes in power. Sleep and Hibernate are examples of _______. Regular maintenance on a computer is good for _______. Bad sectors are sections of the _______ that are physically damaged. To protect some devices such as flash drives and external hard drives from corruption, it’s best to _______ the devices.
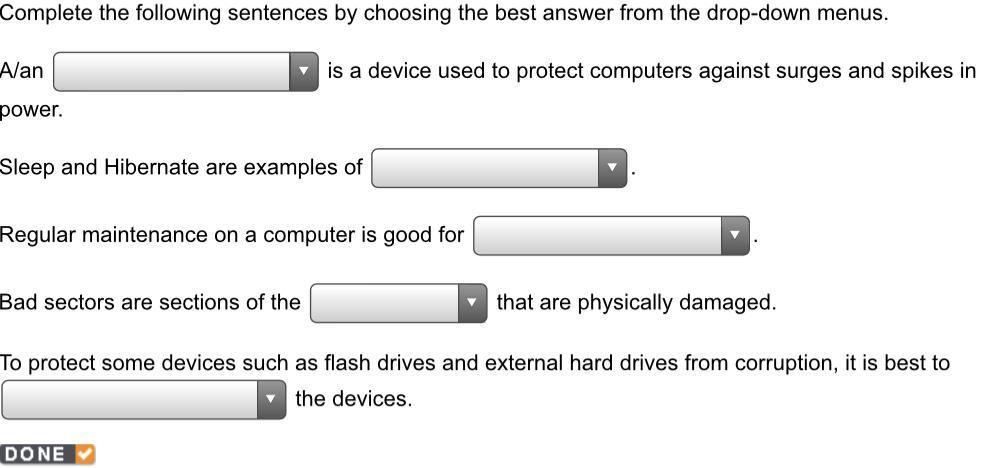
Answers
Answer:
1. Surge protector
2. Power-saving mode
3. Hardware and software
4. Hard disk
5. Eject
Explanation:
sadly my answer has deleted here so i have to start all over again
which of these properties describe the molecular level structure of ionic compounds? [select all that apply.] infinite crystal latticedistinct +/− ionssoluble only in polar solvents (i.e. water)strong omnidirectional electrostatic bondsvery high melting and boiling pointshard but brittle
Answers
The properties that describe the molecular level structure of ionic compounds are:
Infinite crystal latticeDistinct +/− ionsStrong omnidirectional electrostatic bondsVery high melting and boiling pointsHard but brittleThese properties are a result of the strong electrostatic forces that hold the ions together in an ionic compound. The infinite crystal lattice and distinct +/− ions are a result of the regular arrangement of ions in an ionic compound. The strong omnidirectional electrostatic bonds are responsible for the high melting and boiling points of ionic compounds. Finally, the hardness and brittleness of ionic compounds are a result of the strong electrostatic forces and the regular arrangement of ions.
Learn more about the molecular level structure of ionic compounds:https://brainly.com/question/19372330
#SPJ11
the binarysearchtree.cpp program is partially completed. it contains empty methods representing the programming interface used to interact with a binary search tree. you will need to add logic to the methods to implement the necessary behavior. here is the public api for binarysearchtree.cpp that you have to complete:
Answers
The binarysearchtree.cpp program is incomplete and needs logic to be added to the methods to implement the necessary behavior. This involves adding code to the public API methods outlined in the program.
The binarysearchtree.cpp program is not completely finished and requires further work. The program provides a public API, which outlines the methods used to interact with a binary search tree. To complete this program, code needs to be added to the methods to implement the desired behavior. This includes adding logic to the methods to ensure that the tree is correctly constructed and that data can be added, removed, and searched for. Additionally, the methods will need to be tested to make sure that the desired behavior is achieved. Finally, the program can be refactored to ensure that it is optimized for performance and is written in a clear and concise manner.
Learn more about code here:
https://brainly.com/question/25774782
#SPJ4
Can someone please help me with this .

Answers
Answer:
whether or not it is raining outside
if the first letter of your name starts with A
whether or not you were on time to school today
the answer to a yes or no question
whether or not it is monday
Explanation:
notice how all of them are "Whether" or "if" or "yes or no" or "1 or 0"
1.What do diamonds, NFL players, and antique corvettes have in common?
2. What are two hidden costs of employment?
3. What were the Chocolate Wars about?
Answers
The thing that diamonds, NFL players, and antique corvettes have in common is that the NFL players loves buying them and showing off with them because it is a great assets that they can still sell at higher price in the future.
The two hidden costs of employment are:
Uncompensated Training. Relocation CostsWhat were the Chocolate Wars about?The Chocolate War, which Robert Cormier initially published in 1974, is still a go-to novel for book banners and censors. The Vigils, a secret club whose members coerce and threaten most pupils into adhering to their rules, are the subject of the book.
Jerry's refusal to participate in the school's chocolate sale has caused a lot of conflict. rising action Jerry's rejection after the first ten days and the penalty that followed for that decision from The Vigils.
Therefore, one can say that opportunity costs are hidden expenses that result from using resources that the company owns but may be put to better use. These expenses frequently go unnoticed and are hidden from view.
Learn more about employment from
https://brainly.com/question/1446509
#SPJ1
What are the flowchart symbols?
Answers
Answer:Flowchart use to represent different types of action and steps in the process.These are known as flowchart symbol.
Explanation:The flowchart symbols are lines and arrows show the step and relations, these are known as flowchart symbol.
Diamond shape: This types of flow chart symbols represent a decision.
Rectangle shape:This types of flow chart symbols represent a process.
Start/End : it represent that start or end point.
Arrows: it represent that representative shapes.
Input/output: it represent that input or output.