Which is the most suitable device to use in a classroom or a conference room to deliver presentations?.
Answers
When delivering presentations, it is important to have the right equipment to ensure that your audience can see and hear your message clearly. One of the most suitable devices to use in a classroom or conference room to deliver presentations is a projector.
A projector is a device that projects an image or video onto a screen or wall. It is a popular tool for presenting information because it allows the presenter to display information to a large group of people at once. It is also portable, making it easy to move from one location to another.
When selecting a projector, it is important to consider the brightness, resolution, and contrast. The brightness of a projector is measured in lumens, and the higher the number of lumens, the brighter the image will be. The resolution refers to the number of pixels that make up the image, and the higher the resolution, the sharper and more detailed the image will be.
Finally, the contrast refers to the difference between the lightest and darkest parts of the image, and a high contrast ratio will ensure that the image is clear and easy to see.
To know more about suitable visit:
https://brainly.com/question/27961340
#SPJ11
Related Questions
A ____ of a new design may reveal major flaws without the time, expense, and potential danger of building a prototype.
Answers
The model of a new design may reveal major flaws without the time, expense, and potential danger of building a prototype option (1) is correct.
What is the model?A system is portrayed in a conceptual model. It comprises of ideas that aid in knowing, comprehending, or simulating the subject the model portrays. It is also a collection of ideas.
The question is incomplete.
The complete question is:
A ____ of a new design may reveal major flaws without the time, expense, and potential danger of building a prototype.
ModelBaselineComputationState diagramAs we know, from the definition of the model,
A mathematical and visual approach to solving design issues for intricate control, signal processing, and communication systems is known as model-based design.
Thus, the model of a new design may reveal major flaws without the time, expense, and potential danger of building a prototype option (1) is correct.
Learn more about the model here:
https://brainly.com/question/14281845
#SPJ4
if you want to find a handout, directions for an assignment, important course keys, due dates, where to upload essays to cengage, etc., where should you always look first on the course site?
Answers
You should always look in the course syllabus and/or the course announcements/updates section first on the course site when trying to find handouts, directions for an assignment, important course keys, due dates, and where to upload essays to cengage, etc. The syllabus usually contains all the information about the course and the instructor's contact information, office hours, and the course policies.
The announcements/updates section is where the instructor posts important information and updates about the course, assignments, and exams. It is a good practice to check these two sections frequently throughout the course to stay informed and up-to-date with the course material.
Learn more about course: https://brainly.com/question/3578697
#SPJ4
write a few lines of code or pseudocode that takes a string of zeros and ones and produces the run-length encoding. do not use a prewritten function - please write your own program g
Answers
The approach that takes a string of zeros and one and produces run-length encoding is given below:
Choose the very first letter of the source string. Then,add the chosen character to the string's final destination. Now, add the count to the destination string after counting the character's subsequent occurrences. If the string's end isn't reached, choose the next character and repeat steps 2, 3, and 4.
def encode(message):
encoded_message = ""
i = 0
while (i <= len(message)-1):
count = 1
ch = message[i]
j = i
while (j < len(message)-1):
if (message[j] == message[j+1]):
count = count+1
j = j+1
else:
break
encoded_message=encoded_message+str(count)+ch
i = j+1
return encoded_message
#input the value
encoded_message=encode("11003300")
print(encoded_message)
Output:
21202320
In other words, a single data value describing the repeated block and how many times it appears in the image is kept for sequences that display redundant material using the lossless compression technique known as run-length encoding (RLE). This data can be used to precisely rebuild the image later on during decompression.
To learn more about run-length encoding click here:
brainly.com/question/21876555
#SPJ4
The most significant aspect of the Odessa Steps sequence in Battleship Potemkin is the use of: mise en scene visual analysis of the components of a dramatic event editing to restructure visual elements for heightened effect all of the above none of the above
Answers
The most significant aspect of the Odessa Steps sequence in Battleship Potemkin is the use of editing to restructure visual elements for heightened effect.
The sequence is known for its innovative use of montage editing, which creates a powerful emotional impact by juxtaposing shots of different events and characters. The sequence is also notable for its use of striking imagery and visual symbolism, which are part of the mise en scene. However, it is the editing that ties these elements together and creates the sequence's unforgettable impact.
Therefore, the correct answer is "editing to restructure visual elements for heightened effect."
Learn more about Odessa here:
https://brainly.com/question/11818366
#SPJ11
WILL GIVE BRAINLIEST!!!!
Casey overhears two people talking about an amazing new app. What phrase has been abbreviated when they talk about an “app”?
applied computer simulation
application software
appropriate usage format
applied technology
Answers
Answer:
Application Software
Answer:
application software
Explanation:
"Application software" is a common phrase nowadays that is being abbreviated as "app." Casey described the new app as "amazing," which means that the app could be a game, a browser, a photo editor or other programs that are deemed important and mostly exciting for the end users–people who are targeted by the software. In the situation above, they could be talking about a trendy app. New apps are being created by people over the course of years.
What is computer ethics? What are the things that are prohibited by computer ethics?
Answers
Answer:
Computer ethics was set up in 1992. It entails the moral guidelines for computer professionals and users in the usage of the computer. An example is not using the computer to commit any type of fraud etc.
The things prohibited by Computer ethics include
1. Using the computer to commit any type of fraud.
2. Hacking of individual personal and private files.
3. Piracy and usage of pirated softwares etc.
Which of these protocol retrieves email and then deletes the email and its attachments?
O SMTP
O HTTP
O IMAP
OPOP 3
Answers
Answer: POP 3
Explanation: I just did it. It says its POP3
Answer:
POP 3Explanation:
DYou are helping your friend Saanvi with a school project. You notice that she has all of her school files in one big folder, without any organization. Her filenames are mostly just random letters and numbers, so it’s hard for her to find the one she’s looking for. How could you help Saanvi with her file management?
Answers
You could occasionally have problems locating a specific file. If this occurs to you, don't freak out and computer and downloads.
Thus, There are a couple of straightforward ways to locate the file, which is most likely still on your computer. In this lesson, we'll go through several methods for finding your files, such as searching and looking in obvious areas and problems.
Your computer will automatically store downloaded files in a certain folder called the Downloads folder. This is the first place you should search if you're having difficulties locating a file you obtained from the Internet, such as a photo attached to an email message and computer.
Open File Explorer, then find and choose Downloads (located below Favorites on the left side of the window) to display the Downloads folder. Your most recent downloads will be displayed in a list.
Thus, You could occasionally have problems locating a specific file. If this occurs to you, don't freak out and computer and downloads.
Learn more about Downloads, refer to the link:
https://brainly.com/question/26456166
#SPJ1
what is at the top of the stack after the following operations are run? push(4) push(12) pop() push(26)
Answers
20,20,10,10,20 will be at the top of the stack after the given operations are run.
What is stack?A set of related elements is grouped together logically as a stack. In programming and computer memory management, the phrase is frequently used.
Last in first out (LIFO), a type of data abstraction that is frequently used and is composed of the two main operations push and pop, is the foundation of programming stacks. In contrast to the pop operation, which removes elements from the top position, the push operation adds elements to the stack's bottom position.
The top position is tracked using a variable or header pointer, respectively, in arrays and linked lists, which are used to implement the stack concept in software. For the implementation of stacks, many programming languages have built-in features.
Learn more about stack
https://brainly.com/question/14257345
#SPJ4
What term did don norman define as story that puts the operation of the system into context, weaving together all of the essential components, providing a framework, a context, and reasons for understanding?.
Answers
Don Norman defined the phrase "story" as a conceptual model. Conceptual models are ethereal, psychological depictions of proper task execution.
In order to systematize processes, people use conceptual models subconsciously and intuitively. For instance, using calendars and diaries to make appointments is a common mental model. Knowing how common and effective conceptual models are helps developers create software that is matched to users' conceptual frameworks.
Designers build on preexisting frameworks and knowledge by producing interfaces and applications that mirror conceptual models, which makes it simpler for users to learn how to use the new product.
Learn more about conceptual models https://brainly.com/question/11274859
#SPJ4
Amal wants to store a list of the average temperatures for the past month (for example 14.2, 14. 12.6). What data type can he use to store all these values?
A. Floating point number
B. Integer
C. Array
D. String
Answers
Answer: the correct answer is C
Explanation: array is 100% correct
I got the question right
consider the following sequence of page references: 0, 1, 2, 3, 4, 2, 1, 5, 6, 2, 1, 2, 3, 7, 6, 3, 2, 1 assuming four initially empty frames in the physical memory, how many page faults would occur using the optimal page replacement algorithm?
Answers
The page that was brought in initially gets replaced first because to the FIFO (initially In First Out) process, which replaces the oldest page in the frame. Optimal replacement:With three frames: 6-page faults, With four frames: 5-page faults.
The FIFO approach would generate the most page faults for the given page reference string when using three frames, whereas the Optimal algorithm would generate the fewest page faults when using four frames.
For the other techniques, the page fault count would be somewhere in the middle of these two extremes.
Learn more about FIFO, here:
https://brainly.com/question/17236535
#SPJ1
What are the missing whole numbers on this number line? Enter your answers in the boxes. plz show work I'm I need answer 3rd grade

Answers
yo can someone hook me up with some uranium
Answers
Answer:
now how we gon do dat
Explanation:
...
can someone give me an window blur code in javascript like i mean full coding
Answers
Answer:
uh wha- what?!?!
Explanation:
no
find it urself
:P
jekqfjewil bored anyways
Kareem wants to include line drawings of abstract shapes on his personal website. What should he use to acquire the graphics
Answers
To acquire the graphics, Kareem should use: A drawing Software.
What is a Drawing Software?Drawing software is simply a computer program that allows users to sketch diagrams online. Graphic designers can use this software to create artworks that can be attached to websites or any other online platform.
So, for Kareem to include the line drawings on his personal website, he should use drawing software.
Learn more about the drawing software here:
https://brainly.com/question/25236672
public interface Shape { void draw ();} public abstract class ComplexShape implements Shape\{ List> shapes = new ArrayList <(); \} public class Triangle implements Shape\{ void draw() { System.out.println("drawing triangle"); } 1. Shape shape = new Shape(); 2. ComplexShape shape 2= new Triangle(); 3. ComplexShape shape3 = new ComplexShape(); 4. shape3.draw(); 5. Triangle shape4 = new Triangle(); shape4 ⋅ draw () ; Q47) Only one line in the code above will work. Which one?
Answers
The only line that will work in the code above is line 5, which calls the draw( ) method on an instance of the Triangle class. Triangle shape4 = new Triangle(); shape4.draw( );
1. Shape shape = new Shape(); - This line will not work because Shape is an interface and cannot be instantiated.
2. ComplexShape shape2 = new Triangle(); - This line will work, but only if the ComplexShape class has a constructor that takes a Triangle as a parameter. Since the given code does not have such a constructor, this line will not work.
3. ComplexShape shape3 = new ComplexShape(); - This line will work, but it does not create an instance of a shape that can be drawn. It only creates an empty ArrayList within the ComplexShape class.
4. shape3.draw( ); - This line will not work because shape3 is a ComplexShape object, which does not have a draw( ) method.
5. Triangle shape4 = new Triangle( ); shape4.draw( ); - This line will work because it creates an instance of the Triangle class, which implements the Shape interface and has a draw( ) method. The draw( ) method will print a "drawing triangle" to the console.
Read more about interfaces in Java: https://brainly.com/question/30390717
#SPJ11
PLEASE HELP!!!!
Which of the following statements about content-based filtering is TRUE?
A. With content-based filtering, users receive recommendations for items liked by similar users.
B. With content-based filtering, users receive recommendations for items that are similar in type to ones they already like.
C. Both A and B are true
D.Neither A nor Bare true
Answers
Answer:
D
Explanation:
It means its based on things similar to what you are reading or looking at.
The statement that is true about content-based filtering is; A. With content-based filtering, users receive recommendations for items liked by similar users.
What is Content based Filtering?
Content-based filtering is defined as a type of recommender system that attempts to guess what a user may like based on that user's activity.
Now, from the given options we can say that option A is correct because it matches the description we have above about Content based filtering.
Read more about Content based filtering at; https://brainly.com/question/10043488
#SPJ9
Lets do a who know me better! 5 questions! if you get 4\5 you get brainliest or a 3\5 but anything below u dont get it!
How old am I?
Do I like Summer or Winter?
Whats my name? (You guys should get this.)
What grade am I in? (Its between 4th and 8th).
How many siblings do I have? ( its between 2 and 5)
Good Luck!
Answers
Answer:your 13
you enjoy winter but still like summer
Skylar
either 7 or 8th
3 siblings
Explanation:
The user will input a three digit number
if they input 678 I need to output 876
I have 8 and 6 but I can't get 7
help me
/* Unit 1 - Lesson 5 - Coding Activity Question 1 */
import java.util.Scanner;
class U1_L5_Activity_One {
public static void main(String[] args) {
Scanner scan = new Scanner(System.in);
System.out.print("Please enter a two digit number: ");
int x = scan.nextInt();
System.out.println("Here are the digits:");
System.out.println(x/100);
System.out.println(x/10);
System.out.println(x%10);
}
}
Answers
import java.util.Scanner;
public class U1_L5_Activity_One {
public static void main(String[] args) {
Scanner scan = new Scanner(System.in);
System.out.print("Please enter a two digit number: ");
int x = scan.nextInt();
System.out.println("Here are the digits:");
System.out.println(x/100);
System.out.println((x/10)%10); //Just divide the result by 10 and find the remainder
System.out.println(x%10);
}
}
//Or, you can do that way:
import java.util.Scanner;
public class U1_L5_Activity_One {
public static void main(String[] args) {
Scanner scan = new Scanner(System.in);
System.out.print("Please enter a two digit number: ");
String[] x = scan.nextLine().split(""); //We need it to be a string array, to split the values after "", that is, after each symbol(number)
System.out.println("Here are the digits:");
for(int i = 0; i<x.length; i++) {
System.out.println(Integer.parseInt(x[i])); //Converting the string into int, as you want
}
}
}
A typical IT infrastructure has seven domains: User Domain, Workstation Domain, LAN Domain, LAN-to-WAN Domain, WAN Domain, Remote Access Domain, and System/Application Domain. Each domain requires proper security controls that must meet the requirements of confidentiality, integrity, and availability.
Question 1
In your opinion, which domain is the most difficult to monitor for malicious activity? Why? and which domain is the most difficult to protect? Why?
Answers
The most difficult domain to monitor for malicious activity in an IT infrastructure is the Remote Access Domain, while the most difficult domain to protect is the System/Application Domain.
The Remote Access Domain is challenging to monitor due to the nature of remote connections. It involves users accessing the network and systems from outside the organization's physical boundaries, often through virtual private networks (VPNs) or other remote access methods.
The distributed nature of remote access makes it harder to track and detect potential malicious activity, as it may originate from various locations and devices. Monitoring user behavior, network traffic, and authentication attempts becomes complex in this domain.
On the other hand, the System/Application Domain is the most challenging to protect. It encompasses the critical systems, applications, and data within the infrastructure. Protecting this domain involves securing sensitive information, implementing access controls, and ensuring the availability and integrity of systems and applications.
The complexity lies in the constant evolution of threats targeting vulnerabilities in applications and the need to balance security measures with usability and functionality.
To learn more about Remote Access Domain, visit:
https://brainly.com/question/14526040
#SPJ11
pls help
Question 2 (1 point)
True or false: when you use someone's copyrighted work in something you are
selling, you only have to cite them.
Answers
The given statement of copyrighted work is false.
What do you mean by copyright?
A copyright is a type of intellectual property that grants the owner the exclusive right to copy, distribute, adapt, display, and perform a creative work for a specific period of time. The creative work could be literary, artistic, educational, or musical in nature. The purpose of copyright is to protect the original expression of an idea in the form of a creative work, not the idea itself. A copyright is subject to public interest limitations, such as the fair use doctrine in the United States.
When you use someone's copyrighted work in something you are selling, you must get their permission first.
To learn more about copyright
https://brainly.com/question/357686
#SPJ13
7.2 code practice edhesive. I need help!!
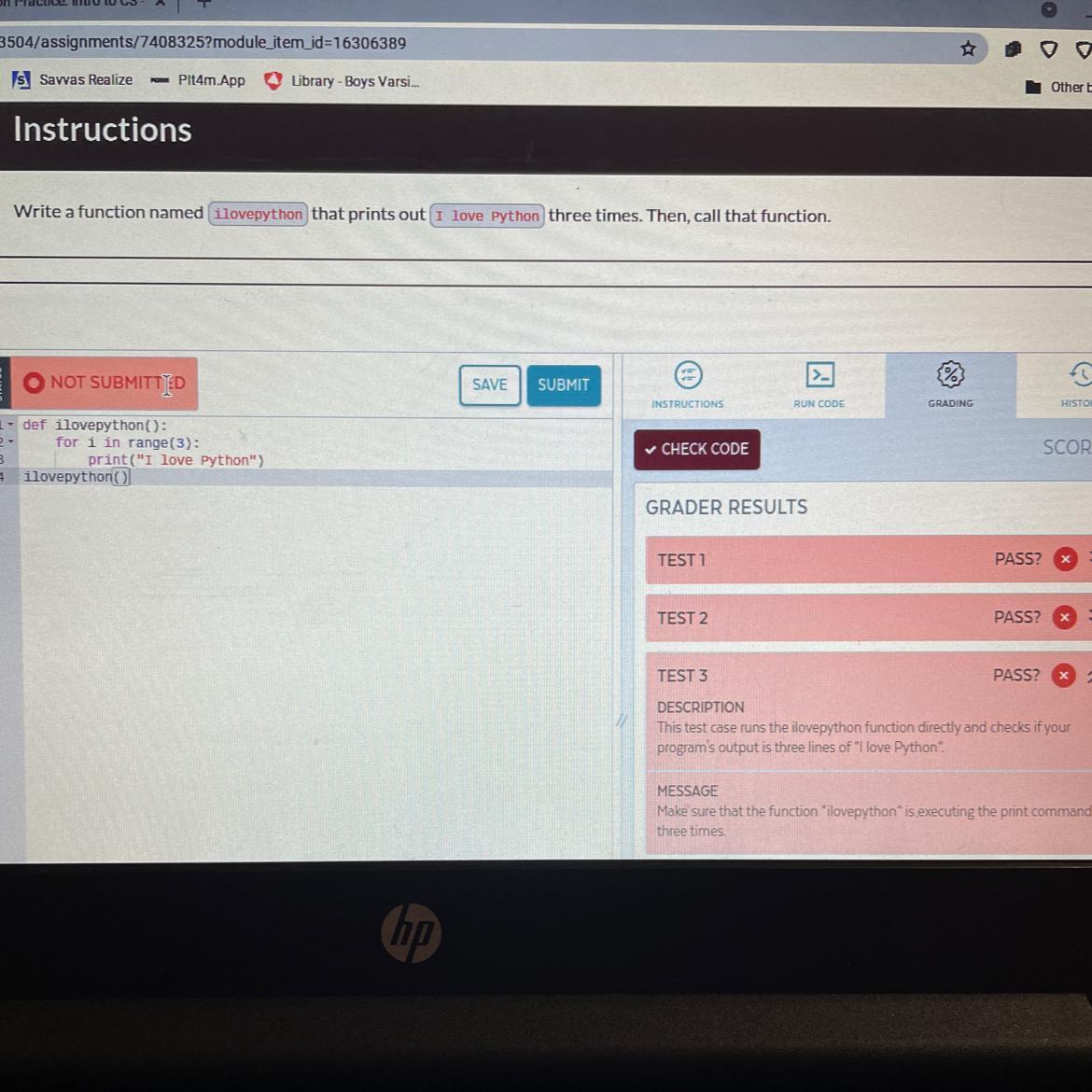
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
When we are talking about personal privacy. Some online activities carry more risk than others. Listed below are several popular online activities. Choose the one that carries the greatest risk.
Question 1 options:
Social Networking
Online gaming
Online purchases
Cyberbullying
PLEASE RESPOND QUICK ILL GIVE 50 POINTS
Answers
Answer:
I think it's cyberbullying ...
bcoz online gaming is ok.. purchases is also ok network is also but cyberbullying is not ok... it's carries a risk.. sometimes u also caught in a situation which u can't avoid...
Answer: Social Networking
Explanation: bc
At least 3 facts I learned about our Amazon Volunteer or their career experience:
Answers
Answer:
Amazon's Global Month of Volunteering includes hundreds of partners. Tens of thousands of employees around the world are coming together to support over 400 organizations in their local communities.
Please help with this code!

Answers
import random
months = ["jan", "feb", "mar", "apr", "may", "june", "july", "aug", "sept", "oct", "nov", "dec"]
pick1 = random.choice(months)
pick2 = random.choice(months)
if months.index(pick1) < months.index(pick2):
print(pick1)
print(pick2)
else:
print(pick2)
print(pick1)
Since the months are already in chronological order in the list, we can compare their index and print the string with the smaller index first. I wrote my code in python 3.8. I hope this helps.
Help please this is my last assignment of the year

Answers
Answer:
the answer is in the website that are there
Which of these features is an orientation feature?
A.
letting users know where they are
B.
letting users know how to get to the next node
C.
letting users know where all the hyperlinks are
D.
letting users know how far they are from a node
E.
letting users know how far from the homepage they are
Answers
Answer:
e
Explanation:
Answer:
letting users know how far from the homepage they are
Explanation:
What kind of sharpener can be described as having sharpening wheels that are powered to spin against the blade,meaning that it takes very little effort to use?
A.a limestone sharpener
B.a metal rod
C.a manual sharpener
D.an electric sharpener
Answers
The kind of sharpener that can be described as having sharpening wheels that are powered to spin against the blade, meaning that it takes very little effort to use, is an electric sharpener.
This type of sharpener uses a motor to power the sharpening wheels, allowing them to spin rapidly against the blade. This makes the sharpening process much faster and more efficient than with a manual sharpener or a metal rod. Additionally, the electric sharpener's ease of use and convenience make it a popular choice for those who want to sharpen their knives and tools quickly and easily.
learn more about sharpening wheels here:
https://brainly.com/question/21985897
#SPJ11
what was the first computer ever to co me out
Answers
Answer:
The first mechanical computer, The Babbage Difference Engine, was designed by Charles Babbage in 1822. The ABC was the basis for the modern computer we all use today. The ABC weighed over 700 pounds and used vacuum tubes
Explanation:
The first mechanical computer, The Babbage Difference Engine, was designed by Charles Babbage in 1822. The ABC was the basis for the modern computer we all use today. The ABC weighed over 700 pounds and used vacuum tubes