which of the following is not one of the three major components of machine learning systems? group of answer choices a model the learner a function parameters
Answers
The three major components of machine learning systems are a model, the learner, and function parameters. A model refers to the mathematical representation of the problem that the machine learning system is trying to solve.
The learner is the algorithm or method used to adjust the parameters of the model so that it can make accurate predictions or classifications. Function parameters are the values that the learner adjusts in order to optimize the model's performance.
Therefore, the answer to the question is that all three of the options (a model, the learner, and function parameters) are major components of machine learning systems. None of them should be excluded as they all play an important role in building and training machine learning models.
To know more about function visit:-
https://brainly.com/question/28358915
#SPJ11
Related Questions
"please help i have exam
Discuss three phases of social media marketing maturity.
Answers
The three phases of social media marketing maturity are: 1. Foundation Phase 2. Growth Phase 3. Optimization Phase
1. Foundation Phase: In this phase, businesses establish their presence on social media platforms and focus on building a solid foundation for their marketing efforts. They create social media accounts, develop a consistent brand voice, and start engaging with their audience. The primary goal is to increase brand awareness and establish a basic level of social media presence.
2. Growth Phase: During this phase, businesses expand their social media strategies and start leveraging the full potential of social media marketing. They focus on growing their audience, increasing engagement, and driving traffic to their website or physical stores. This phase involves implementing more advanced strategies such as content marketing, influencer partnerships, and targeted advertising campaigns.
3. Optimization Phase: In the optimization phase, businesses refine their social media strategies based on data-driven insights and continuous improvement. They use analytics tools to measure the effectiveness of their campaigns, identify areas for improvement, and optimize their social media content and advertising strategies. This phase emphasizes the importance of data analysis, testing, and ongoing optimization to achieve better results and maximize return on investment.
The three phases of social media marketing maturity represent a progression from establishing a basic presence to achieving strategic growth and continuous optimization. As businesses advance through these phases, they develop a deeper understanding of their target audience, refine their messaging, and refine their tactics to drive meaningful results from their social media marketing efforts.
To learn more about website click here: brainly.com/question/32113821
#SPJ11
I Have a Kodak pixpro camera and I put my memory card in (sandisk) but it keeps on saying "card is not formatted" then it gives me the option of "format" "doing so will clear all data" "yes or no" but i barely bought the memory card and the camera , so What do i do ? I never used the camera or the memory card . (PLEASE HELP )
Answers
If you've never used the camera, and you're fairly certain there aren't any pictures on the memory device, then it's safe to format the disk so that you set up the table of contents properly. That way the computer can read the data in the right sectors and so on. I would choose the option "yes" and follow the instructions on the screen. It should lead you to a blank disk so you can then fill it up with future pictures down the road.
If you think there are pictures on the card and you want to retrieve them, then try putting the card into a different memory reader and see if the same message pops up. Chances are there are slightly different formats that aren't being compatible in some way if this is the case.
What does DOS stand for?
Answers
Answer:
Disk Operating System
Explanation:
"DOS is a platform-independent acronym for Disk Operating System which later became a common shorthand for disk-based operating systems on IBM PC compatibles."
32.
are also known as cyber burglars.
a. Hackers
b. Programmers
c. Software Engineers d. Crackers.
Page 3 of 4
Answers
Answer:
a
Explanation:
hackers access your system unauthorized
Pauline is a manager of a team in a large website design firm. Her team members come from diverse cultural backgrounds. The performance of
her team sometimes suffers due to internal conflicts. As a manager, how can Pauline resolve these conflicts?
Answers
Answer: Pauline is a manager of a team in a large website design firm. Her team members come from diverse cultural backgrounds. The performance of her team sometimes suffers due to internal conflicts. As a manager, how can Pauline resolve these conflicts?
Explanation: Pauline can resolve the conflicts by changing the subject by talking about something else when that happens they tend to forget what they were arguing about.
Can someone tell me how to hit on a link on Brainly to see the answer
Answers
What tag works as a dictionary between text & computer bytes?
Answers
Answer:
Here is some python code
Explanation

please help me with this this is Computer chapter Advanced HTML of class 8th
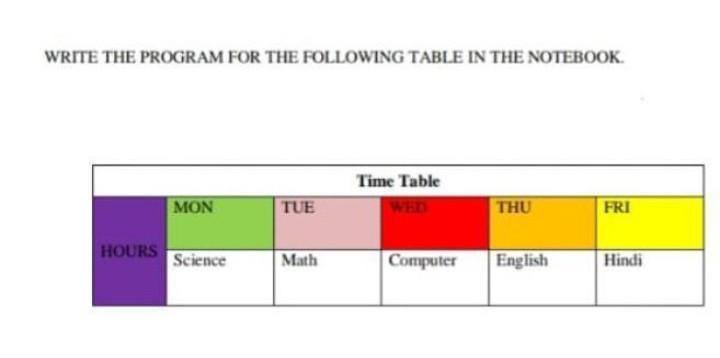
Answers
Answer:
ok let me try
It stands for
Hypertext Markup Language
Image result for html stands for
HTML (the Hypertext Markup Language) and CSS (Cascading Style Sheets) are two of the core technologies for building Web pages. HTML provides the structure of the page, CSS the (visual and aural) layout, for a variety of devices.
Consider a pipelined processor with just one level of cache. assume that in the absence of memory delays, the baseline cpi of this processor is 2. now assume that the percentage of memory instructions in a typical program executed on this cpu is 50% and the memory access latency is 150 cycles. assuming that the i-cache delays are already accounted for in the baseline cpi, consider the following two alternatives for the d-cache design:
alternative 1: a small d-cache with a hit rate of 94% and a hit access time of 1 cycle (assume that no additional cycles on top of the baseline cpi are added to the execution on a cache hit in this case).
alter tive 2: a larger d-cache with a hit rate of 98% and the hit access time of 2 cycles (assume that every memory instruction that hits into the cache adds one additional cycle on top of the baseline cpi).
a) [5%] estimate the cpi metric for both of these designs and determine which of these two designs provides better performance. explain your answers
b) [5%] repeat part (a), but now assume that the memory access latency is reduced to 50 cycles.
c) [5%] repeat part (b), but now assume that the l2 cache is also added to the system with the hit rate of 75% and access latency of 10 cycles.
Answers
Alternative 1:A small D-cache with a hit rate of 94% and a hit access time of 1 cycle (assume that no additional cycles on top of the baseline CPI are added to the execution on a cache hit in this case).Alternative 2: A larger D-cache with a hit rate of 98% and the hit access time of 2 cycles (assume that every memory instruction that hits into the cache adds one additional cycle on top of the baseline CPI). a)[10%] Estimate the CPI metric for both of these designs and determine which of these two designsprovides better performance. Explain your answers!CPI = # Cycles / # InsnLet X = # InsnCPI = # Cycles / XAlternative 1:# Cycles = 0.50*X*2 + 0.50*X(0.94*2 + 0.06*150)CPI= 0.50*X*2 + 0.50*X(0.94*2 + 0.06*150) / X1= X(0.50*2 + 0.50(0.94*2 + 0.06*150) ) / X= 0.50*2 + 0.50(0.94*2 + 0.06*150)= 6.44Alternative 2:# Cycles = 0.50*X*2 + 0.50*X(0.98*(2+1) + 0.02*150)CPI= 0.50*X*2 + 0.50*X(0.98*(2+1) + 0.02*150) / X2= X(0.50*2 + 0.50(0.98*(2+1) + 0.02*150)) / X= 0.50*2 + 0.50(0.98*(2+1) + 0.02*150)= 3.97Alternative 2 has a lower CPI, therefore Alternative 2 provides better performance.
HURRY!!!!!!!!!!!!!
Suppose you have a pictorial drawing of a playground design. How would you represent the length of a slide that is 12 feet long?
Answers
Answer:
You make use of a scale (See Explanation)
Explanation:
Given
Length = 12 feet
Required
How would you represent this on drawing.
Knowing that a length of 12 feet can't be drawn on drawing, the best way to do this is to make use of a scale measurement.
The scale to use depends on you and the size of paper at your disposal.
Assume you adopt a scale of 1 inch: 1 feet
This means that a length of 12 feet will be represented by 12 inches in drawings
import the text-boydair10.txt file from your downloaded from the resources link. use the first row as column headers.
Answers
To import the text-boydair10.txt file
URL resource = getClass().getClassLoader().getResource("text-boydair10.txt");
This is how we can import a text file from our downloaded from the resources link.
What is resource link?An object in the Data Catalog known as a resource link is a connection to a database or table that is either private or public. The name of the resource link that you create to a database or table can be used in place of the database or table name after you create the resource link.
Table resource links are returned by glue:GetTables() and show up as entries on the Lake Formation console's Tables page in addition to any tables that you own or have access to. Similar behavior is displayed by resource links to databases.
A database or table in your Data Catalog may be given a different name. This is particularly helpful if multiple databases in your account contain tables with the same name from different AWS accounts, or if those databases are shared by other AWS accounts.
Learn more about resource link
https://brainly.com/question/26211894
#SPJ4
PLEASE ASAP!!
Today, most film editors manually cut and splice the actual film footage once it arrives.
O True
O False
Answers
Answer:
True
Explanation:
edg2021
The film editor is such an important person on a film that he is often hired before the cast and other crew. This editor is responsible for revising the filmed footage until it becomes the finished film. The editor begins by reading the script to get familiar with the story. It is important for the editor to know the script because film scenes are generally shot and edited out of sequence. When footage begins to come in, the editor reviews the footage and production notes provided by the director and production team. These notes contain details about the footage and the director’s comments about the footage. The editor then uploads or transfers the footage to computers in the editing bay and begins editing the footage into finished scenes. The editing bay is the control room with editing equipment, computers, monitors, and sound system where film editors manipulate plot, sound, graphics, and score to produce a well-constructed scene. This is a painstakingly detailed and time-consuming task
A running back with a mass of 78 kg and a speed of 6 m/s collides with, and is held by, a 117-kg defensive tackle going in the opposite direction. How fast must the tackle be going before the collision for their speed afterward to be zero
Answers
The tackle must be moving at a speed of 4 m/s in the opposite direction before the collision for both players to come to a stop afterward.
This problem can be solved using the principle of conservation of momentum. The total momentum before the collision is zero since the running back and the tackle are moving in opposite directions. After the collision, their combined momentum must also be zero for both players to come to a stop. By setting up an equation using the conservation of momentum, we can solve for the velocity of the tackle. The equation is as follows:
(mass of running back × velocity of running back) + (mass of tackle × velocity of tackle) = 0
Plugging in the given values, we get:
(78 kg × 6 m/s) + (117 kg × velocity of tackle) = 0
By solving this equation, we find that the velocity of the tackle must be -4 m/s, indicating that the tackle is moving in the opposite direction at a speed of 4 m/s before the collision for both players to come to a stop afterward.
Learn more about collision here:
https://brainly.com/question/13138178
#SPJ11
an externally facing web server in your organization keeps crashing. looking at the server after a reboot, you notice cpu usage is pegged and memory usage is rapidly climbing. the traffic logs show a massive amount of incoming http and https requests to the server. which type of attack is this web server experiencing?
Answers
Memory usage seems to climb every day until the server runs out of memory ,the application is most likely suffering from Memory Leak.
Memory is a system or device used in computing to store data for immediate use in a computer, associated computer hardware, or digital electronic devices. Primary storage and main memory are frequently used interchangeably when referring to one another. Store is a dated word that describes memory.
The computer memory is split up into a great deal of little pieces called cells. An individual address for each cell ranges from 0 to memory size minus one. Volatile (RAM) and non-volatile are the two types of computer memory (ROM). Hard discs used as auxiliary memory are referred to as storage rather than memory.
To learn more about Memory refer to:
brainly.com/question/24688176
#SPJ4
pls help
Question 2 (1 point)
True or false: when you use someone's copyrighted work in something you are
selling, you only have to cite them.
Answers
The given statement of copyrighted work is false.
What do you mean by copyright?
A copyright is a type of intellectual property that grants the owner the exclusive right to copy, distribute, adapt, display, and perform a creative work for a specific period of time. The creative work could be literary, artistic, educational, or musical in nature. The purpose of copyright is to protect the original expression of an idea in the form of a creative work, not the idea itself. A copyright is subject to public interest limitations, such as the fair use doctrine in the United States.
When you use someone's copyrighted work in something you are selling, you must get their permission first.
To learn more about copyright
https://brainly.com/question/357686
#SPJ13
Write a program in java to input N numbers from the user in a Single Dimensional Array .Now, display only those numbers that are palindrome
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that input N numbers from the user in a Single Dimensional Array .
Writting the code:class GFG {
// Function to reverse a number n
static int reverse(int n)
{
int d = 0, s = 0;
while (n > 0) {
d = n % 10;
s = s * 10 + d;
n = n / 10;
}
return s;
}
// Function to check if a number n is
// palindrome
static boolean isPalin(int n)
{
// If n is equal to the reverse of n
// it is a palindrome
return n == reverse(n);
}
// Function to calculate sum of all array
// elements which are palindrome
static int sumOfArray(int[] arr, int n)
{
int s = 0;
for (int i = 0; i < n; i++) {
if ((arr[i] > 10) && isPalin(arr[i])) {
// summation of all palindrome numbers
// present in array
s += arr[i];
}
}
return s;
}
// Driver Code
public static void main(String[] args)
{
int n = 6;
int[] arr = { 12, 313, 11, 44, 9, 1 };
System.out.println(sumOfArray(arr, n));
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Which internet communication service can you use to speak to other users over the internet?.
Answers
Answer: VOIP or Voice over IP
Explanation: It uses internet protocols and your IP address to make video or voice calls, depending on the service, it might also use WebRTC
write a loop that counts the number of lowercase characters in the string referenced by my_string
write in python
Answers
Answer:
Here's an example Python code that uses a loop to count the number of lowercase characters in a string:
my_string = "The quick BROWN fox JUMPS over the lazy dog"
# Initialize a count variable to keep track of lowercase characters
count = 0
# Loop through each character in the string
for char in my_string:
# Check if the character is lowercase
if char.islower():
# Increment the count if it is lowercase
count += 1
# Print the total count of lowercase characters
print("The number of lowercase characters in the string is:", count)
In this example, we start with a string "The quick BROWN fox JUMPS over the lazy dog" and we want to count the number of lowercase characters in the string. We initialize a count variable to zero and then loop through each character in the string. For each character, we check if it is lowercase using the islower() method. If the character is lowercase, we increment the count by 1. Finally, we print out the total count of lowercase characters in the string, which is 20 in this case.
What web browser feature would be particularly useful when using public computers?
Answers
A web browser feature which would be particularly useful when using public computers is: C. Privacy browsing.
What is a web browser?A web browser can be defined as a type of software application (program) that is designed and developed to enable an end user view, access and perform certain tasks on a website, especially when connected to the Internet.
What are public computers?Public computers can be defined as the type of computers that are typically used by the general public and as such are less secured than personal computers.
In this context, we can infer and logically deduce that privacy browsing is a web browser feature which would be particularly useful when using public computers.
Read more on privacy browsing here: https://brainly.com/question/6970507
#SPJ1
Complete Question:
What web browser feature would be particularly useful when using public computers?
A. Session restore
B. Pinned tabs
C. Privacy browsing
D. All of the above
Select the correct navigational path to freeze the top row of your worksheet. Select the panes you wish to freeze. Click the tab on the ribbon to enter the gallery. Then, select the drop-down menu to freeze the panes.
Answers
Yeah, Your steps ar correct. Let's analyse those steps more easily by the following steps:
\( \Large{ \boxed{ \bf{ \color{aqua}{Freeze \: panes:}}}}\)
Freeze panes is a feature in spreadsheet applications, such as Microsoft Excel, LibreOffice Calc, and Google Sheets. It "freezes" a row or column, so that it is always displayed, even as you navigate the spreadsheet.
❍ Freezing panes is especially useful if your spreadsheet has a header row, that you want to always be visible.
Select the row below the row(s) you want to freeze. In our example, we want to freeze rows 1 and 2, so we'll select row.Click the View tab on the Ribbon.Select the Freeze Panes command, then choose Freeze Panes from the drop-down menu. ...The rows will be frozen in place, as indicated by the gray line.━━━━━━━━━━━━━━━━━━━━

Answer:
Select the correct navigational path to freeze the top row of your worksheet.
Select the panes you wish to freeze.
Click the ✔ View tab on the ribbon to enter the ✔ Window gallery.
Then, select the drop-down menu ✔ Freeze Panes
to freeze the panes.
Explanation:
which is the right answer

Answers
Answer:
B
Explanation:
I think.
Answer:
answer a
Explanation:
as my name starts with a
What is the primary purpose of the destination address?
Choose 1 answer:
It helps the router know where to send the packet.
B
It helps the receiving computer reassemble the packets.
It tells the router where the packet came from.
D
It helps the sending computer know how long to wait before retrying.
It prevents the packet from being intercepted by cybercriminals.
Answers
Answer:
The answer to this question is given below is the explanation section.
Explanation:
"A" option is correct
It helps the router know where to send the packet.
Across revisions of the Diagnostic and Statistical Manual, _____ has been removed entirely, while _____ has been renamed.
Answers
that homosexuality has been removed entirely from the Diagnostic and Statistical Manual (DSM), while gender identity disorder has been renamed to gender dysphoria.
this is that homosexuality was once considered a mental disorder, but it was removed in 1973 due to increasing pressure from the LGBTQ+ community and scientific evidence showing that it is not a mental illness. In contrast, gender identity disorder was renamed to gender dysphoria in the DSM-5 in 2013 to reflect a shift in understanding of the condition as a distress related to incongruence between one's gender identity and sex assigned at birth, rather than a disorder in and of itself. In conclusion, the DSM has undergone revisions that reflect changing societal attitudes and scientific understanding of mental health conditions.
In the revisions of the Diagnostic and Statistical Manual of Mental Disorders (DSM), homosexuality was removed entirely as a mental disorder in 1973, during the publication of the DSM-III. On the other hand, Gender Identity Disorder, which was included in previous versions, was renamed to Gender Dysphoria in the DSM-5, published in 2013, to better reflect the condition and reduce stigma.
Across the DSM revisions, homosexuality has been removed, while Gender Identity Disorder has been renamed to Gender Dysphoria.
For more information on homosexuality kindly visit to
https://brainly.com/question/28145496
#SPJ11
Explain the process to keep the dropdown list in the e-form.
Answers
Answer:
To keep a dropdown list in an e-form, you need to ensure that the list items are entered as options in the form field properties. Here are the general steps:
1) Open the e-form in the appropriate software or application, such as Adobe Acrobat or Microsoft Word.
2) Select the form field that you want to turn into a dropdown list.
3) Open the form field properties window.
4) In the form field properties window, select the "Options" or "Dropdown List" tab.
5) Enter the list items that you want to include in the dropdown list, one per line. You can also use the "Add" and "Remove" buttons to add or remove items from the list.
6) If you want to allow users to enter their own text in addition to the predefined list items, check the "Allow custom text entry" option.
7) Save the changes to the form field properties and save the e-form document.
By following these steps, you should be able to create a dropdown list in your e-form that stays in place and allows users to select from a list of predefined options.
In a new worksheet, type the entries you want to appear in your drop-down list. · Select the cell in the worksheet where you want the drop-down list.
We know Infrared waves operates in frequencies between 300 GHz to 400 THz with wavelength
ranging between 1 mm to 770 mm. And The initial 6G networks are proposing a THz frequencies
for smooth operation, best speed and also ultra-low latency. Explain why Infrared frequencies are
not preferred for 6G networks with very detailed and technical reasons to back your answer?
Answers
Infrared frequencies are not preferred for 6G networks due to limited range, susceptibility to interference, and inability to penetrate obstacles. Due to its inherent limitations, infrared frequencies are not the ideal choice for 6G networks, which require wider coverage, higher reliability, and the ability to handle massive amounts of data traffic.
Explanation:
Infrared frequencies are not preferred for 6G networks due to limited range, susceptibility to interference, and inability to penetrate obstacles.
1. Limited Range: Infrared waves have a shorter range compared to radio waves used in wireless communication networks. Infrared communication requires a direct line-of-sight between the transmitter and receiver, which limits its effectiveness in covering large areas and connecting multiple devices in a network.
2. Susceptibility to Interference: Infrared communication can be easily disrupted by environmental factors such as sunlight, heat, and other electromagnetic radiation sources. This makes it less reliable for outdoor use and in environments with high levels of interference.
3. Inability to Penetrate Obstacles: Infrared waves cannot penetrate solid objects like walls and other barriers, making it impractical for use in building and urban environments. Radio waves, on the other hand, can pass through obstacles, making them more suitable for 6G networks.
4. Limited Bandwidth: Although infrared frequencies offer a high bandwidth, they are still not sufficient to support the data rates and capacity requirements of 6G networks, which are expected to provide enhanced mobile broadband, massive machine-type communications, and ultra-reliable low-latency communications.
5. Scalability Issues: 6G networks aim to support a massive number of connected devices, including IoT devices and autonomous vehicles. Infrared technology's imitation's in range, interference, and obstacle penetration make it difficult to scale and meet these demands.
In summary, due to its inherent limitations, infrared frequencies are not the ideal choice for 6G networks, which require wider coverage, higher reliability, and the ability to handle massive amounts of data traffic.
Know more about the data traffic click here:
https://brainly.com/question/11590079
#SPJ11
joann turned on her windows 10 computer today, and while the computer was booting up, it shut down. she restarted the computer and it booted fine but ran slowly. she opened task manager and noticed that her cpu was running at 98% capacity and her network at 75% capacity. when she checked to see what process was using so much network connectivity, she received a message saying that access to the process was denied.
Answers
Based on these indicators, the clear actions which Joann should do with her computer are:
Run antivirus software.Disconnect from the network.Check the file permissions.What is System Security?This refers to the precautions or measures that are taken in order to safeguard or protect a computer system or network from unauthorized usage through the use of things like firewalls, etc.
Hence, we can see that based on the given question, we are told that Joann turned on her windows 10 computer today, and while the computer was booting up, it shut down and when she re-booted it, she found out that her CPU was running at 98% capacity and her network at 75% capacity.
The best actions that she has to take in order to address these issues and also the issue of network connectivity are listed above which are using an antivirus to scan, disconnect from the network, and check file permissions.
Read more about system security here:
https://brainly.com/question/25720881
#SPJ1
The complete question is:
Joann turned on her Windows 10 computer today, and while the computer was booting up, it shut down. She restarted the computer and it booted fine but ran slowly. She opened Task Manager and noticed that her CPU was running at 98% capacity and her network at 75% capacity. When she checked to see what process was using so much network connectivity, she received a message saying that access to the process was denied.
Based on these indicators, what should Joann do with her computer? (Select all that apply.)
Who's ur favorite YTber?
Answers
Answer:
Explanation:
my favorite ytuber is Deestroying
Answer:
Laurenzside is one of my faves ig
Explanation:
How do you get information from a form that is submitted using the "get" method in PHP?
A. $_POST[];
B. $_GET[];
C. Request.Form;
D. Request.QueryString;
Answers
In PHP, to get information from a form that is submitted using the "get" method, you would use the superglobal variable $_GET[]. The correct option is B.
The form data is added to the URL as query parameters when a form is submitted using the "get" method.
These query parameters are automatically added to the $_GET[] superglobal array by PHP. By designating the input name as the array's key in the $_GET[] structure, you can obtain the values of form inputs.
The value given by the user can be retrieved using $_GET['username'] if your form, for instance, has an input field named "username" and is submitted using the "get" method.
Thus, the correct option is B.
For more details regarding PHP, visit:
https://brainly.com/question/25666510
#SPJ4
Job opportunities in the computer science field are expected to (5 points)
A. increase
B. stay the same
C. decrease
D. be limited
Answers
Answer:
A) increase
Explanation:
Computer science is a high-demand job and is one of the crucial components needed to run future technology.
Answer:
(C) decrease
Explanation:
Because Artificial intelligence is coming ♕︎ first increase for few years but when it dec decrease then never will increase again.What are examples of object dependencies? Check all that apply.
O a button with an anchor property
Oa report that is based on a query
Oa macro with conditional formatting
Oa query that uses data from a table
Oa table that underlies the report information
Oa text box control aligned to the edge of a report
Answers
The examples of object dependencies are:
A report that is based on a query.A query that uses data from a table.A table that underlies the report information.What is an object dependency?An object dependency is known to be a term that connote the order in which an object do work or operate in.
Note that the object that is said to be operated on will have to have a reference metadata for itself and an example of object are tables, query, etc.
Learn more about object dependencies from
https://brainly.com/question/25624254
#SPJ1