Which of the followings are true or false?
a. RISC tends to execute more instructions than CISC to complete the same task.
b. In the von Neumann Architecture, data and instructions are stored in different memories.
c. Assume an ISA where all the instructions are 16 bits and which has 8 general purpose registers. If the instruction set only consists of instructions using two source registers and one destination. The ISA can support 2^7 different opcodes at most.
d. When designing the processor, the only thing we need to consider is speed.
e. LC2K is byte addressable.
Answers
Falseb. Falsec. True d. Falsed. Falsee. Truea. FalseRISC (Reduced Instruction Set Computing) executes fewer instructions than CISC (Complex Instruction Set Computing) to complete the same task.
FalseIn the von Neumann Architecture, data and instructions are stored in the same memory.c. TrueIf an ISA includes all the instructions that are 16 bits in length and has 8 general-purpose registers. If the instruction set only includes instructions with two source registers and one destination,.
the ISA can support up to 2^7 different opcodes.d. FalseWhen designing the processor, we need to consider power consumption, heat dissipation, reliability, and other factors in addition to speed.e. TrueLC2K is byte-addressable.
To know more about Reduced Instruction Set Computing visit:
https://brainly.com/question/29453640
#SPJ11
Related Questions
Which of the following is an object-oriented programming language?
- Ada
- COBOL
- Pascal
- Python
Answers
Explanation:
This is the correct answer
pythonAnswer:
[D] Python
Explanation:
With the exception of control flow, everything in Python is an object.
Thus, python is an object-oriented programming language.
~Learn with Lenvy~
to extract a range of bits from bit 5 to bit 3 on a 10 bit unsigned number, we have (x << a) >> b. what b should be?
Answers
To extract a range of bits from bit 5 to bit 3 on a 10-bit unsigned number using the expression (x << a) >> b, you should set a = 6 and b = 7. This will shift the bits to the left by 6 positions, then shift them back to the right by 7 positions, effectively isolating bits 5 to 3.
To extract a range of bits from an unsigned number, we need to shift the bits to the right and then perform a bitwise AND operation with a mask that has ones in the positions of the bits we want to extract. In this case, we want to extract bits 5 to 3, which means we need to shift the bits to the left by 6 positions (a = 6) so that bits 5 to 3 are in positions 9 to 7. Then, we shift the bits back to the right by 7 positions (b = 7) to isolate the bits we want. Finally, we can apply a bitwise AND operation with the mask 0b111 to extract the desired bits.
Learn more about bits here;
https://brainly.com/question/30791648
#SPJ11
You are concerned about attacks directed against the firewall on your network. You want to be able to identify attacks and be notified of attacks. In addition, you want the system to take immediate action when possible to stop ore prevent the attack.
Which tool should you use?
- Packet sniffer
- IPS
- Port scanner
- IDS
Answers
The tool that you should use is an IPS (Intrusion Prevention System). An IPS can identify attacks directed against the firewall on your network and can notify you of these attacks. In addition, an IPS can take immediate action when possible to stop or prevent the attack.
A packet sniffer and a port scanner can help you identify potential vulnerabilities in your network, but they do not have the ability to prevent or stop attacks. An IDS (Intrusion Detection System) can identify attacks, but it does not have the ability to take immediate action to prevent or stop the attack.
An intrusion detection system is a piece of hardware or software that looks for malicious activity or policy violations in a system or network. Any interruption action or infringement is commonly detailed either to a head or gathered halfway utilizing a security data and occasion the board framework.
Know more about Intrusion Prevention System, here:
https://brainly.com/question/31451453
#SPJ11
2.32 LAB: Musical note frequencies On a piano, a key has a frequency, say f0. Each higher key (black or white) has a frequency of f0 * rn, where n is the distance (number of keys) from that key, and r is 2(1/12). Given an initial key frequency, output that frequency and the next 4 higher key frequencies. Output each floating-point value with two digits after the decimal point, which can be achieved by executing cout << fixed << setprecision(2); once before all other cout statements. Ex: If the input is: 440.0 (which is the A key near the middle of a piano keyboard), the output is: 440.00 466.16 493.88 523.25 554.37
Answers
Answer:
Explanation:
\(\text{This is a python code:}\)
\(\text{import math}\)
\(your {\_} {value 1 }= float(inpu \ t ())\)
\(your{\_}value 2 = your{\_}value1*math.exp(1 * math.log(2) / 12)\)
\(your{\_}value 3 = your{\_}value1*math.exp(2 * math.log(2) / 12)\)
\(your{\_}value 4 = your{\_}value1*math.exp(3 * math.log(2) / 12)\)
\(your{\_}value 5 = your{\_}value1*math.exp(4 * math.log(2) / 12)\)
\(print('\{:.2f\} \{:.2f\} \{:.2f\} \{:.2f\} \{:.2f\}'.format(your\_value1, \ your\_value2, \ your\_value3,\)\(\ your\_value4, \ \ your\_value5))\)
\(\mathbf{OUTPU \ T :}\)
\(\mathbf{440.00 \ 466.16 \ 493.88 \ 523.25 \ 554.37}\)
The code for musical note frequencies On a piano, a key has a frequency, say f0 is in the explanation part below.
Here is a C++ program to the stated problem:
#include <iostream>
#include <iomanip>
#include <cmath>
int main() {
double frequency;
std::cout << "Enter the initial key frequency: ";
std::cin >> frequency;
std::cout << std::fixed << std::setprecision(2); // Set output precision to 2 decimal places
std::cout << frequency << " ";
for (int i = 1; i <= 4; ++i) {
frequency *= std::pow(2, 1.0 / 12); // Calculate the next frequency
std::cout << frequency << " ";
}
return 0;
}
Thus, in this program, we use the user's original key frequency as input. The starting frequency and the following four higher key frequencies are then calculated and produced using a loop.
For more details regarding C++ program, visit:
https://brainly.com/question/33180199
#SPJ6
Cryptocurrency is a form of payment that:
• A. can be used for digital or face-to-face transactions.
•
B. can only be exchanged for specific things.
®
C. exists online and in local banks.
•
D. can be exchanged online for goods and services.
Answers
Cryptocurrency is a form of payment that can be used for digital or face-to-face transactions. Option A is the correct answer.
Cryptocurrencies is a decentralized digital currency that is secured through cryptography, and it exists solely online. Cryptocurrencies are not backed by any government or financial institution and can be used to purchase goods and services, as well as exchanged for other currencies. Transactions made using cryptocurrency are recorded in a decentralized public ledger called a blockchain.
Cryptocurrency can be stored in digital wallets and can be bought and sold on various online exchanges. As it is not bound by traditional banking regulations, cryptocurrency has the potential to offer a more secure and efficient way to make payments.
Option A is the correct answer.
You can learn more about Cryptocurrency at
https://brainly.com/question/26103103
#SPJ11
What are the major development that took place in the fourth generation of computer
Answers
Answer:
I'm going to assume they're talking about VLSI circuits. It allowed more transistors and circuits on a single chip. Made computers better in every way.
Answer:
Computers of fourth generation used Very Large Scale Integrated (VLSI) circuits. VLSI circuits having about 5000 transistors and other circuit elements with their associated circuits on a single chip made it possible to have microcomputers of fourth generation.
PLS MARK ME BRAINLIEST
Explanation:
write a function named wordcount that reads words from a text file whose name is passed as a parameter to the function, and counts the frequency of each acceptable word. the function should return a list of tuples of word and frequency count.
Answers
The same function can be used to determine how frequently a certain word appears.
While you type, Word keeps track of the words in the document. Pages, paragraphs, lines, and characters are all counted by Word. Check the status bar to see how many words, pages, characters, paragraphs, or lines are in a document. Choose the words you want to count to get a partial word count. Get the number of entries in a number field that is part of a range or array of numbers by using the COUNT function. To count the numbers in the range A1:A20, for instance, enter the formula =COUNT (A1:A20). In this case, if five of the range's cells are made up of numbers, the answer is 5.
Learn more about word here-
https://brainly.com/question/24991315
#SPJ4
Give the first in first out queue java example!
Answers
Queue<String> queue = new LinkedList<>();
Explanation: This code creates a FIFO queue using the LinkedList class in Java.
How to implement a FIFO queue in Java?Here's an example of a First-In-First-Out (FIFO) queue implementation in Java using the LinkedList class:
import java.util.LinkedList;
import java.util.Queue;
public class FIFOQueueExample {
public static void main(String[] args) {
Queue<String> queue = new LinkedList<>();
// Enqueue elements
queue.offer("First");
queue.offer("Second");
queue.offer("Third");
// Dequeue elements
while (!queue.isEmpty()) {
String element = queue.poll();
System.out.println("Dequeued: " + element);
}
}
}
In this example, we use the LinkedList class from the java.util package, which provides an implementation of the Queue interface.
We create a Queue object named queue using the LinkedList class.We enqueue elements into the queue using the offer method, which adds elements to the end of the queue.We dequeue elements from the queue using the poll method, which retrieves and removes the element at the front of the queue.We repeat the dequeue process until the queue becomes empty, checking with the isEmpty method.The output of this code will be:
Dequeued: First
Dequeued: Second
Dequeued: Third
This demonstrates the FIFO behavior of the queue, where the elements are dequeued in the same order they were enqueued.
Learn more about Java
brainly.com/question/12978370
#SPJ11
Complete the sentence.
A__
certificate
Internal Server Error
File Not Found
___error might appear when you are attempting to view a secure web page.
Answers
A intermediate certificate Internal Server Error File Not Found Windows server error might appear when you are attempting to view a secure web page.
What is Intermediate Certificate Issues?The most frequent reason for a "certificate not trusted" problem is because the certificate installation on the server (or servers) hosting the site was not correctly finished. Check for this problem by utilizing our SSL Certificate checker. One certificate file and a broken red chain are indicators of an incomplete installation in the tester.Install the intermediate certificate (or chain certificate) file on the server hosting your website to remedy this issue. Log into your DigiCert Management Console, click the order number, and then choose the link for the certificate download to accomplish this. The correct filename for this is DigiCertCA.crt. Installing the intermediate certificate file then requires that you adhere to your server's specific installation guidelines.Use the SSL Certificate tester to recheck the installation after importing the intermediate certificate. Multiple certificate files connected by an uninterrupted blue chain are displayed in the tester as having an incomplete installation.Please refer to this article for instructions on how to resolve an SSL installation error if you are using a Windows server, receiving an error when using our SSL Certificate tester, and DigiCert High Assurance EV CA-3 is listed as the issuer of your certificate.To Learn more About intermediate certificate Refer To :
https://brainly.com/question/10210317
#SPJ1
What are the local, state, and national opportunities that may be available to those who participate in CTSOs?
Answers
Answer: Students
Explanation:
The National Coordinating Council for Career and Technical Student Organizations (CTSO) advocate for the values that the Career and Technical Education (CTE) curriculum instills in students.
In association with the Association for Career and Technical Education (ACTE), the CTSO work to instill career skills to students in middle school, high school, and post-secondary institutions such as Business, Health science, Information Technology and Finance amongst others.
CTSOs such as Educators Rising and Business Professionals of America encourage and support CTE programs for their members which also has a Federal Support of $1.1 billion.
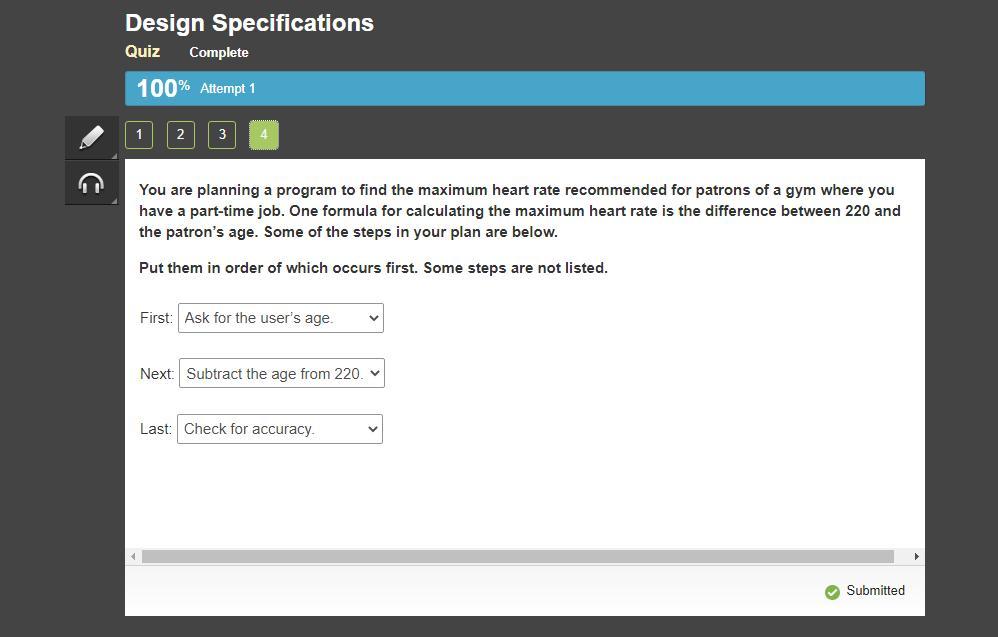
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
Assembly Program
⦁ Store the two 8 bit numbers in registers
⦁ compare them both
⦁ check if the value in the first register is greater than the other
⦁ if true print their sum
⦁ else subtract them
Answers
This program first stores two 8-bit numbers (42 and 23) in registers A and B, respectively. It then compares the values in registers A and B using the CMP instruction.
If A is greater than or equal to B, it jumps to the ADD label, where it adds the values in registers A and B, stores the result in register C, and calls the PRINT_SUM subroutine to print the sum to the console. If A is less than B, it subtracts the value in register B from the value in register A, stores the result in register C, and calls the PRINT_DIFF subroutine to print the difference to the console.
The PRINT_NUM subroutine is used to convert the sum or difference in register C to ASCII code and output it to the console. It uses the DIV instruction to divide the number in register A by 10, which stores the quotient in A and the remainder in B. It then converts the remainder and quotient to ASCII code by adding 48 to their values (since the ASCII code for '0' is 48) and outputs them to the console using the 0EH output port. Finally, it swaps the values in registers A and B so that the quotient is in A and the remainder is in B, and repeats the process to output the second digit of the number.
To know more about program visit :
https://brainly.com/question/11023419
#SPJ11
Who watches Riverdale ? if you do can we be friends(pLEASE DON'T DELETE) and also who is your fav character from Riverdale





Answers
Answer:
I have watched it before
Answer:
my fav is veronica lol
Explanation:
which monitor will you prefer in your school crt or fpd and why?
Answers
Answer: CRT
Explanation: because just because
Take an example of old communication technology and compare it with the new communication technology which is solving the same use case and describe how new communication technology has changed the future of communication
Answers
Any digital gadget that can be used to convey and receive information is referred to as communication technology.
Thus, Software, computer programs, gadgets, and message systems are examples of this technology. Technologies for effective communication are quick, effective, practical, and simple to use. They frequently make it possible for people to connect with one another from anywhere in the world.
Before communication technology, delivering even the most straightforward information took more time and effort than is possible to convey in 140 characters or less.
Information sharing is now simpler than ever because to the integration of technology into many forms of communication. Despite the huge number of devices, programs, and tools used in communication technology.
Thus, Any digital gadget that can be used to convey and receive information is referred to as communication technology.
Learn more about Communication technology, refer to the link:
https://brainly.com/question/1150014
#SPJ4
the task of monitoring file systems for unauthorized change is best performed by using a(n) ____.
Answers
The task of monitoring file systems for unauthorized changes is best performed by using an Intrusion Detection System (IDS) or an "Integrity Monitoring System" (IMS).
An Intrusion Detection System is a security tool designed to monitor network traffic or system activity for signs of unauthorized access, malicious activities, or policy violations.
It can also include file integrity monitoring capabilities to detect unauthorized changes to files and directories.
Integrity Monitoring Systems, on the other hand, specifically focus on monitoring and detecting unauthorized changes to files, configurations, or critical system components.
They compare the current state of the file system with a known baseline or reference state to identify any alterations or modifications.
Both IDS and IMS solutions are valuable for monitoring file systems to ensure the integrity and security of critical files and data. They help identify unauthorized changes, malware infections, or potential compromises, allowing organizations to take timely action to mitigate risks and maintain the security of their systems.
To learn more about unauthorized: https://brainly.com/question/29037358
#SPJ11
pls tell me which app or how they animated this spams will be reported.

Answers
How do you check to see if the user entered more than one character? Complete the code.
letter = input("Enter a letter: ")
if _____ > 1:
print("\nPlease guess a single letter.\n")
letter.len()
length(letter)
letter.length()
len(letter)
Answers
Answer:
1len(letter)
Explanation:
JUST GOT IT RIGHT
The code is letter = input("Enter a letter: ") if len(letter) > 1:print("\nPlease guess a single letter.\n")
What is code?There are four kinds of coding:
Data compression (or source coding)Error control (or channel coding)Cryptographic coding.Line coding.The description of a code is a set of rules or a method of communication, often with erratically assigned numbers and letters given specific definitions.
An illustration of code is the state's vehicle laws. An example of code is a made-up vocabulary that two children use to articulate to each other.The total numeral of computer languages to exist is approximately 9,000, though there are 50 that are the most famous programming languages in use today.To learn more about code, refer to:
https://brainly.com/question/25605883
#SPJ2
Lynn would like to compare the tuition cost of three different colleges. Which type of chart would best display this data? Analogous Bar Diagram Scatter
Answers
Answer:
Bar chart
Explanation:
A bar chart or bar graph is used to present the data according to the categories in the form of rectangular bars. The data of each constituent is presented either vertically or horizontally. There are two axes on the bar chart. One of them represents one category while the other represents the value to be measured. The comparison among the data given can be easily found and analyzed using a bar chart.
The tuition cost of the three different colleges can be easily compared when the data can be presented in the bar chart.
Answer:
bar graph
Explanation:
Assume you need to create a presentation on the effects of global warming. Keeping the topic in mind, you need to
focus on certain key guidelines while creating the presentation. In a table, list those appropriate guidelines that you
would follow to create an effective presentation. Your table should have guidelines related to image choices, font
size for the heading and body text, background and text color for the slide, number of bullet points you will use,
and number of words per line. Also, provide your rationale about the choices for these elements.
Answers
Answer:
................................................................................................
Explanation:

what is graphical symbols
Answers
Explanation:
A graphical symbol is a visually perceptible figure with a particular meaning used to transmit information independently of language.
if this helps you please mark me brainliest
have a nice day :)
Which of the following is considered information? a. A single keystroke b. All the characters on a keyboard c. An individual test score d. Average of a series of test scores
Answers
Answer:
The correct option is;
d. Average of a series of test scores
Explanation:
Information is defined as the knowledge or news which has been sent by one person and received by another such as the reply for a request for the current weather at a specific geographical location
Information is data that has been interpreted, processed, organised, put into a structured and presented within a given context that can be intelligible, meaningful and useful to people.
4.3 Code Practice: Question 1
Answers
There are about four issues with the code. The most important is the while loop which has been removed. The modified code is given below.
What are the issues with the code ?A) The variable i is not initialized before it is used in the while loop. Therefore, it may cause a NameError.
B) The comparison in the while loop i <= "aqe" compares a variable i which is an integer to a string "aqe". This would cause a TypeError.
C) There is no update statement in the while loop, so i will always be the same and the loop will run indefinitely.
The corrected code is:
age = input("How old are you turning? ")
print("**HUG**") if age.isdigit() else None
Here the code prints "HUG" only once. This is achieved by removing the "while" loop.
Learn more about codes in programming at:
https://brainly.com/question/28848004
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
'In my 4.3 Code practice: Question 1. Every time I enter an age, it just continues to print **HUG**
What is wrong with my code?
aqe int(Input( "How old are you turning?))
While (i <="aqe") :
print(("**HUG**") )'
i = i+i
6.3.6: Create your own Encoding on codehs be confusing.


Answers
A general example of an encoding scheme that contains A-Z and space is given below.
How to illustrate the informationIn this example, we can assign the following binary codes to each character:
A: 00
B: 01
C: 10
...
Z: 10101
Space: 10110
Using this encoding scheme, the phrase "HELLO WORLD" would be represented as:
00010101100101100110000010101011001010000001101
As you can see, this encoding scheme requires a varying number of bits to represent each character, with shorter codes assigned to more commonly used letters and longer codes assigned to less commonly used letters. This can help to minimize the total number of bits required to encode a message.
Learn more about encoding on
https://brainly.com/question/3926211
#SPJ1
What should you look for if you want to know if your web browser session is secure?
Answers
To determine if your web browser session is secure, you should look for a few indicators.
The times to be look forHTTPS - Check if the website URL begins with "https -//" instead of "http -//". The "s" indicates a secure connection.
Padlock Icon - Look for a padlock symbol in the address bar. It signifies that the connection is encrypted.
Security Warnings - Ensure there are no warning messages or alerts indicating potential security risks.
Extended Validation Certificate - Some secure websites display an extended validation certificate, which provides additional verification of the website's authenticity.
Browser Security Settings - Make sure your browser settings prioritize security and warn about insecure connections or websites.
Learn more about secure browsing:
https://brainly.com/question/13354554
#SPJ4
a cnf grammar can generate (the empty string) if the original grammar generates . group of answer choices true false
Answers
The statement " a cnf grammar can generate (the empty string) if the original grammar generates" is False.
What is context-free grammar?
A context-free grammar is one whose production rules take the form A to alpha, where A is a single nonterminal symbol and alpha is a string of terminals and/or nonterminals.
In order to produce every feasible pattern of strings in a given formal language, context-free grammar (CFG) is used. G is a grammar made up of a collection of production rules. It is employed to produce linguistic strings. The terminal symbols ending with T are the last set.
Chomsky's normal form is known as CNF. When all production rules meet one of the following criteria, context-free grammar is said to be in Chomsky's normal form (CNF). begin creating symbols.
To learn more about contex-free, use the link given
https://brainly.com/question/15000259
#SPJ4
what statistics in the output do you compare to determine which model to use? group of answer choices r2 of .8305 to r2 of .885
Answers
The model with an R-squared value of 0.885 should be used instead of the other model.
When comparing models to determine which one to use, the statistics to be compared in the output are R-squared values. R-squared values are used to determine the proportion of the variation in the dependent variable that is explained by the independent variables in a linear regression model. Higher R-squared values indicate that the model is a better fit for the data than a model with a lower R-squared value. In this case, the two R-squared values being compared are 0.8305 and 0.885. The model with the higher R-squared value of 0.885 is a better fit for the data than the model with the lower R-squared value of 0.8305. Therefore, the model with an R-squared value of 0.885 should be used instead of the other model.
Learn more about R-squared value visit:
https://brainly.com/question/29844785
#SPJ11
Which file attribute identifies the file as having been modified since the last backup?.
Answers
Archive file identifies the file as having been modified since the last backup.
Archive file understanding
The meaning of the word Archive in the Online Computer Dictionary is used to make a copy of a backup file with the aim of protecting the original copy from damage.
How to Archive Files Into 1 File
If you want to send a large number of files, you can make the file into 1 archive file format with .zip, .tar, or .rar format first. This method is also quite easy and fast.
• First, make sure your computer has programs such as winzip, winrar. This program is needed to archive files.
• Second, you can select the file you want to archive, then right-click on the file. The example below shows 2 files to be archived
• The third step, you can directly select Add to “folder name.rar” to directly create archive files automatically. If you want to do some settings, it can be done by selecting the Add to archive option.
The Add to archive option allows you to choose the save format of the file, divide or create the archive into several parts (part 1, part 2, etc.), to create a password. With the password, before the file can be extracted, it is necessary to enter the password first.
In addition to files, you can also archive folders directly along with the contents of the files in it. Keep in mind, how fast the process of archiving this file will depend on how many or large files to be archived.
Learn more about archive files at https://brainly.com/question/15355917.
#SPJ4
Instructions
Click the links to open the resources below. These resources will help you complete the assignment. Once you have created your
file(s) and are ready to upload your assignment, click the Add Files button below and select each file from your desktop or network
folder. Upload each file separately.
Your work will not be submitted to your teacher until you click Submit.
Documents
Ways to Organize Text - Student Guide
Creation and Management of Lists - Student Guide
Insertion of Symbols Special Characters, and Images - Student Guide
File Upload
Accepted file types: .ppt, .pptx, xls, xlsx, doc, .docx, zip, pdf, .accdb, msg
Add Files
*
Delete All
Answers
explanation:
whats the question?
which two are available in ads? (choose two.) select 2 correct responses device targeting, which allows you to serve your ads to users on desktops, smartphones, and tablets. variable targeting, which allows ads to be served to a subset of users on specified dates for a set ad price. heritage targeting, which allows advertisers to serve ads only to users who have a specified family history. company targeting, which allows you to serve ads to the people who work for a specific company you choose. language targeting, which lets you reach people with your selected language as their browser's language setting.
Answers
The two options available in ads are A: device targeting allows advertisers to serve ads to users on desktops, smartphones, and tablets AND E: Language targeting which lets advertisers reach people who have selected the advertiser's chosen language as their browser's language setting.
The two available targeting options in ads are device targeting and language targeting. Device targeting allows advertisers to serve ads to users on desktops, smartphones, and tablets. This enables ads to reach a broader audience and ensures that the ads are displayed properly on all devices. Language targeting lets advertisers reach people who have selected the language they want to use on their browser. This enables advertisers to serve ads to people who are more likely to understand and engage with the content in their language.
You can learn more about ads at
https://brainly.com/question/1658517
#SPJ11