Which term means "the act or process of acquiring knowledge or skills?"
learning strategy
metacognitive learning
learning
cognitive theory of learning
Answers
Answer:
Learning is the term that means, "the act or process of acquiring knowledge or skills"
Answer:
the term you are looking for is learning
Explanation:
learning something means to acquire knowledge
Related Questions
Rank the order of venders keeping Amazon’s goals in mind

Answers
Rankings are determined for several reasons. The vendors that best satisfy Amazon's objectives are listed in Rank order as follows:
Vendor E - FirstVendor R - SecondVendor K -Third Vendor F - FourthWhat is the vendor ranking about?When evaluating vendors, companies typically have a set of parameters or criteria that they use to determine which vendor is the best fit for their needs. These parameters can include things like cost, quantity, shipping time, and cost to the company.
In this scenario, Vendor E is ranking first because it is meeting the majority of the company's parameters. The low cost issues, low quantity, high shipped on time, and low cost to Amazon all indicate that Vendor E is providing a high level of service and is a cost-effective choice for the company.
On the other hand, Vendor K is ranking lower because it is not meeting some of the company's parameters as well as Vendor E. Vendor K has low cost issues, moderate quantity shipped, high quantity shipped and high cost to Amazon, indicating that it may not be as cost-effective or reliable as Vendor E.
In all, Vendor E is ranking first because it is meeting the majority of the company's parameters, indicating that it is a good fit for the company's needs and it is a cost-effective choice.
Learn more about Amazon from
https://brainly.com/question/26188227
#SPJ1
What are some societal and technological similarities or differences between now and the mid- 1400s in Print media? Discuss (10 marks)
Answers
There are several similarities and differences between the print media of the mid-1400s and the present day in terms of societal and technological aspects.
What are the technological similarities or differences?Here are some of the key points:
Similarities:
The role of print media in disseminating information: In the mid-1400s, the printing press revolutionized the way information was spread, making books and pamphlets more widely available. Similarly, today, print media continues to play a crucial role in disseminating information and shaping public opinion.The importance of literacy: In the mid-1400s, the spread of the printing press led to a greater emphasis on literacy, as people needed to be able to read in order to access the printed materials. Today, literacy remains an essential skill for accessing and understanding print media.Lastly, the Differences:
The speed and reach of information: Today, print media is able to reach a much wider audience much more quickly than it was in the mid-1400s. With the advent of the internet, news and information can be disseminated instantly to a global audience.The diversity of voices: In the mid-1400s, the printing press was controlled by a relatively small number of publishers, who had a great deal of influence over what was printed. Today, there is a much greater diversity of voices in print media, with a wide range of publications catering to different interests and perspectives.Learn more about Print media from
https://brainly.com/question/23902078
#SPJ1
Which function of NOS involves switching the CPU time between different programs?
Answers
The capacity to run many processes or processes at once is known as multitasking in a network operating system. While only one program is actually being run at a time, multitasking gives the impression that several are.
What is multitasking?The simultaneous execution of several tasks for a set amount of time is known as multitasking in computers. As opposed to waiting for them to finish, new tasks might begin and interrupt others that have already begun. An operating system that supports multitasking enables a user to do multiple computer tasks at once, such as running an application software. The operating system can keep track of your progress in various tasks and switch between them without losing data.In a human context, multitasking refers to the act of performing several tasks at once. Examples include updating a document or replying to emails while participating in a teleconference. Computing was where the idea of multitasking first emerged.To learn more about multitasking refer to:
https://brainly.com/question/8367506
#SPJ1
Two negative reviews and no positive reviews is enough to consider the website to have a negative reputation.
Answers
Two negative reviews and no positive reviews is enough to consider the website to have a negative reputation: False.
What is reputation?In Computer technology, reputation can be defined as a metric which is used to determine the quality of a particular website, especially based on the opinions and ratings by its end users.
In this context, we can infer that two negative reviews and no positive reviews isn't an enough metric to consider a website as having a negative reputation.
Read more on negative reputation here: https://brainly.com/question/2343924
#SPJ1
what will allow you to immediately exit the program without rebooting the computer, when you realize your browser is not responding
Answers
Answer:
the exit button on top right or x out of that certain tab
Explanation:
**GIVING ALL POINTS** 4.02 Coding With Loops
I NEED THIS TO BE DONE FOR ME AS I DONT UNDERSTAND HOW TO DO IT. THANK YOU
Output: Your goal
You will complete a program that asks a user to guess a number.
Part 1: Review the Code
Review the code and locate the comments with missing lines (# Fill in missing code). Copy and paste the code into the Python IDLE. Use the IDLE to fill in the missing lines of code.
On the surface this program seems simple. Allow the player to keep guessing until he/she finds the secret number. But stop and think for a moment. You need a loop to keep running until the player gets the right answer.
Some things to think about as you write your loop:
The loop will only run if the comparison is true.
(e.g., 1 < 0 would not run as it is false but 5 != 10 would run as it is true)
What variables will you need to compare?
What comparison operator will you need to use?
# Heading (name, date, and short description) feel free to use multiple lines
def main():
# Initialize variables
numGuesses = 0
userGuess = -1
secretNum = 5
name = input("Hello! What is your name?")
# Fill in the missing LOOP here.
# This loop will need run until the player has guessed the secret number.
userGuess = int(input("Guess a number between 1 and 20: "))
numGuesses = numGuesses + 1
if (userGuess < secretNum):
print("You guessed " + str(userGuess) + ". Too low.")
if (userGuess > secretNum):
print("You guessed " + str(userGuess) + ". Too high.")
# Fill in missing PRINT statement here.
# Print a single message telling the player:
# That he/she guessed the secret number
# What the secret number was
# How many guesses it took
main()
Part 2: Test Your Code
Use the Python IDLE to test the program.
Using comments, type a heading that includes your name, today’s date, and a short description.
Run your program to ensure it is working properly. Fix any errors you observe.
Example of expected output: The output below is an example of the output from the Guess the Number game. Your specific results will vary based on the input you enter.
Output
Your guessed 10. Too high.
Your guessed 1. Too low.
Your guessed 3. Too low.
Good job, Jax! You guessed my number (5) in 3 tries!
When you've completed filling in your program code, save your work by selecting 'Save' in the Python IDLE.
When you submit your assignment, you will attach this Python file separately.
Part 3: Post Mortem Review (PMR)
Using complete sentences, respond to all the questions in the PMR chart.
Review Question Response
What was the purpose of your program?
How could your program be useful in the real world?
What is a problem you ran into, and how did you fix it?
Describe one thing you would do differently the next time you write a program.
Answers
Answer:
sorry man
Explanation:
Describe two reasons to use the Internet responsibly. Explain what might happen if the Internet use policies were broken at
your school.
Answers
Answer: You don't want to download any virus and Chat rooms with stranger can be harmful
Explanation: You can get a virus on your school device, get yourself in harmful situations and your passwords might not be safe
A text that is arranged in a one letter column is called a?
Answers
A text that is arranged in a one-letter column is called a "one-letter-per-line" format.
It is a style of formatting where every letter or word in a text is written on a separate line, usually used for emphasis or aesthetics in writing. One-letter-per-line formatting is a writing style that has been used throughout history and has become more popular in modern times, particularly with the rise of the internet and social media.
One-letter-per-line format can be used to create a variety of effects in writing. For example, it can be used to create a sense of emphasis or to draw attention to a particular word or phrase. It can also be used to create a sense of rhythm or to give a text a more visual or artistic quality. One-letter-per-line formatting can be used in poetry, prose, or any other type of writing, and it can be used to create a wide range of effects.
In conclusion, one-letter-per-line formatting is a writing style that is used to create emphasis, rhythm, or visual effects in writing. It can be used in a wide range of contexts, including poetry, prose, and social media, and it can be used to create a variety of effects depending on the writer's intentions.
For more such questions on one-letter, click on:
https://brainly.com/question/12435728
#SPJ8
Print air_temperature with 1 decimal point followed by C.
Sample output with input: 36.4158102
36.4C
Answers
Answer:
printf("%.1f", air_temperature);
Explanation:
PLEASE HELP I REALLY NEED IT ASAP
Select the correct answer. Layla and her team have installed a fire alarm system in an office. The alarm system connects to a wireless network, so it can be monitored using smartphones and computers connected to the same network. Which wireless technology does the fire alarm system use?
OA satellite
OB. Bluetooth
O C. infrared
OD. WI-FI
Answers
Answer:
wifi
Explanation:
if it's running on the same network that's wifi
Answer:
The correct answer is D. Wi-Fi.
Explanation:
I got it right on the Edmentum test.
Select the correct answer from each drop-down menu.
Select the correct option to complete the algorithm that generates the first 100 even numbers (even numbers are divisible by 2)?


Answers
The correct option to complete the algorithm that generates the first 100 even numbers (even numbers are divisible by 2) include the following:
3. if x is less than or equal to 100, then go to step 4, else go to step 7.
4. if x is divisible by 2, then display x.
What is an algorithm?In Computer technology, an algorithm can be defined as a standard formula (procedures) which is made up of a set of finite steps and instructions that are executed on a computer system, in order to enable a software proffer a solution to a particular problem under appropriate conditions.
Additionally, the three (3) main traits of an algorithm include the following:
An input.Logical steps.An output.Based on the given algorithm for the first 100 even numbers (even numbers are divisible by 2), the missing steps should be completed with the information provided above.
Read more on algorithm here: brainly.com/question/24793921
#SPJ1
write pseudocode to represent the logic of a program that allows the user to enter two values. The program outputs the sum of and the difference between the two values.
Answers
The pseudocode representing the above described logic of a program is:
start
input num1
input num2
set product = num1*num2
output product
stop
See the related flow chart is attached.
What is a pseudocode?Pseudocode is a precise yet comprehensible explanation of what a computer program or algorithm must perform, written in normal language rather than programming language.
Pseudocode is occasionally used as a detailed phase in the development of a program.
Learn more about Pseudocode:
https://brainly.com/question/24953880
#SPJ1

Pls help I will mark brainliest

Answers
Answer:
connection-oreented
Explanation:
Digital photography 1b quiz 8 anyone have the answers?
Answers
The answers related to metering in photography are given as follows.
What is the explanation for the above response?In center-weighted metering, the center of the picture is used to determine exposure. If your subject was in the middle of the frame, you would employ this kind of metering.
Note that a metering setting that only collects data from a tiny portion of the center of the frame, often around 10%.
Instead of altering exposure to account for the significantly stronger light around the hairline, spot metering enables the camera to measure the light reflected off the subject's face and expose appropriately for it.
Learn more about Digital photography at:
https://brainly.com/question/7519393
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
1) What is center-weighted metering?
2) What is partial metering?
1. a printed portfolio
2. sheet protectors.
3. Shutterfly
4. forensic photographer
5. managing cash flow.
6. Annie Leibowitz
7. freewriting
8. provenance.
9. poetry or folksy sayings
10. fashion
11. Mike Brodie
12. focus and depth and field
13. to generate ideas that will help you to compose an original and creative artist’s statement
14. write her artist’s statement
15. ethnography
Explanation: All of these answers are correct :)
Assignment
Write the algorithm for solving the
f problems
1. Perimeter of a rectangle
2 Average of five (5) numbers
Answers
B.Add both lengths
C.Add both widths
D.sum up the value had on both length and width
what is data abstraction and data independence?
Answers
Data abstraction and data independence are two key concepts in computer science and database management systems. They are closely related and aim to improve the efficiency, flexibility, and maintainability of data management.
What is data abstraction and data independence?The definitions of these two are:
Data Abstraction:
Data abstraction refers to the process of hiding the implementation details of data and providing a simplified view or interface to interact with it. It allows users to focus on the essential aspects of data without being concerned about the underlying complexities. In programming languages, data abstraction is often achieved through the use of abstract data types (ADTs) or classes.
By abstracting data, programmers can create high-level representations of data entities, defining their properties and operations.
Data Independence:
Data independence refers to the ability to modify the data storage structures and organization without affecting the higher-level applications or programs that use the data. It allows for changes to be made to the database system without requiring corresponding modifications to the applications that rely on that data. Data independence provides flexibility, scalability, and ease of maintenance in database systems.
Learn more about data at:
https://brainly.com/question/179886
#SPJ1
What are two examples of ways an electronic record may be distributed to others
Answers
Explanation:
Two ways an electronic record may be distributed are e-mail or printing and publishing to others.
How is LUA different from Python?
Give an example.
Answers
This is the answer I couldn't write it here since brainly said it contained some bad word whatever.
Answer:
good old brainly think stuff is bad word even tho it is not had to use txt file since brainly think code or rblx is bad word
A trucking company is expanding its business and recently added 50 new trucks to its fleet delivering to numerous locations. The company is facing some challenges managing the new additions. Which of the company's problems could be solved more easily using quantum computing
Answers
The company's problems that could be solved more easily using quantum computing is commute optimization task.
What is optimization task?
The level or rate of hardness of of the commute optimization task is known to be in the areas
Components processing waiting commuting timeIn the case above, Quantum-assistance is one that can helps firms to be able to handle the time issues and to find solutions for the problem above.
Learn more about quantum computing from
https://brainly.com/question/25513082
#SPJ1
Joe just joined a new team at his marketing firm, which has been working on a campaign ad for the new Elmo doll. Everyone in the group has children except for Joe, and thus they are familiar with the doll. Joe has never seen an Elmo doll before. How should he deal with the situation?
Answers
Answer: ask someone to show or explain the doll to him
Explanation:
edmentum
Answer: ask someone to show or explain the doll to him
Explanation:
If Joe asks his teammates to show or explain the doll to him, he too can contribute ideas for the successful completion of the project.
Cora is a network engineer for a large company and has been given instructions on how to configure a private fiber connection between her company's data center and the cloud service provider her company uses. She needs to configure an ASN on one of the core routers in the data center as part of the connection. Which of the following protocols is she most likely being instructed to configure for use with the CSP?
Answers
Answer: Cora is most likely being instructed to configure the Border Gateway Protocol (BGP) for use with the cloud service provider (CSP).
Explanation:
Cora is most likely being instructed to configure the Border Gateway Protocol (BGP) for use with the cloud service provider (CSP). BGP is a routing protocol that is commonly used in large networks, including those that connect data centers to cloud service providers. It allows for the exchange of routing information between different networks and helps to ensure that data is routed efficiently and reliably. BGP uses Autonomous System Numbers (ASNs) to identify different networks and to facilitate routing between them, which is why Cora needs to configure an ASN on one of the core routers in the data center.
Different types of users in a managed network, what they do, their classification based on tasks
Answers
In a managed network,, skilled can be miscellaneous types of consumers accompanying various roles and blames.
What is the network?Administrators are being the reason for directing and upholding the network infrastructure. Their tasks involve network arrangement, freedom management, consumer approach control, listening network performance, and mechanically alter issues.
Administrators have high-ranking approach and control over the network. Network Engineers: Network engineers devote effort to something designing, achieving, and claiming the network foundation.
Learn more about network from
https://brainly.com/question/1326000
#SPJ1
HELP ASAP PLZ PLZ PLZTegan is playing a computer game on her smartphone and the battery is getting low. When she goes to charge her phone, she notices that the cord is broken. What can Tegan do to solve her problem?
Plug in the smartphone to charge.
Put tape around the broken part of the cord.
Ask a trusted adult for help replacing the cord.
Use the laptop charger instead.
Answers
Answer:
3rd choice
Explanation:
The given program reads a list of single-word first names and ages (ending with -1), and outputs that list with the age incremented. The program fails and throws an exception if the second input on a line is a string rather than an int. At FIXME in the code, add a try/catch statement to catch ios_base::failure and output 0 for the age.
Ex: If the input is:
Lee 18
Lua 21
Mary Beth 19
Stu 33
-1
then the output is:
Lee 19
Lua 22
Mary 0
Stu 34
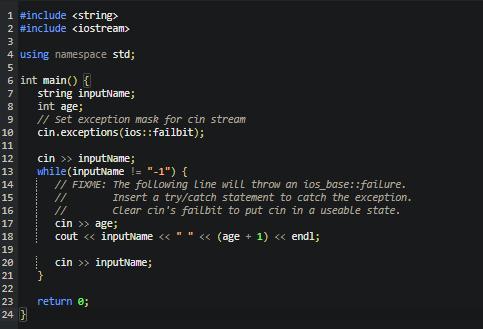
Answers
Note that the code for the above instructions is given as follows:
#include <iostream>
#include <string>
#include <ios>
using namespace std;
int main() {
string name;
int age;
while (cin >> name && name != "-1") {
try {
cin >> age;
age++;
cout << name << " " << age << endl;
} catch (ios_base::failure& e) {
cout << name << " " << 0 << endl;
}
}
return 0;
}
What is the rationale for the above response?The try/catch statement is used to catch the exception ios_base::failure that is thrown when the second input on a line is not an integer.
If an exception is thrown, the code inside the catch block is executed, which outputs the name and 0 as the age. If no exception is thrown, the code inside the try block is executed, incrementing the age by 1 and outputting the name and the incremented age.
Learn more about code:
https://brainly.com/question/14892473
#SPJ1
Within the creditcard selection list add the following options and values: Credit Card Type (leave the value as an empty text string), American Express (value="amex"), Discover (value="disc"), MasterCard (value="master"), and Visa (value="visa").
Make the selection list and cardname field required.
Answers
The credit card issuer may additionally provide cardholders with a separate cash line of credit (LOC) in addition to the usual credit line.
Thus, A credit card is a small, rectangular piece of plastic or metal that is issued by a bank or other financial institution and enables its holder to borrow money to pay for products and services at businesses that accept credit cards.
Credit cards impose the need that cardholders repay the borrowed funds, plus any applicable interest and any other agreed-upon charges, in full or over time, either by the billing date or at a later date.
It will allow them to borrow money in the form of cash advances that can be accessed by bank teller machines, abms, or credit card convenience checks.
Thus, The credit card issuer may additionally provide cardholders with a separate cash line of credit (LOC) in addition to the usual credit line.
Learn more about Credit card, refer to the link:
https://brainly.com/question/31598744
#SPJ1
Perform a bubble sort on the following unsorted list:
3 2 5 6 4 1
In each blank, enter the list after the given iteration. Put one space between each pair of numbers. Do not put commas or any other character in your response besides the numbers and spaces. Do not put a space at the beginning or end of your response.
1. What will the list be after the first iteration of bubble sort?
2. What will the list be after the second iteration of bubble sort?
3. What will the list be after the third iteration of bubble sort?
4. What will the list be after the fourth iteration of bubble sort?
5. What will the list be after the fifth iteration of bubble sort?
Answers
Answer:
3 2 5 6 4 1
2 3 5 4 1 6
2 3 4 1 5 6
2 3 1 4 5 6
2 1 3 4 5 6
1 2 3 4 5 6
Explanation:
After each iteration, one more element at the end of the list is at its final position.
The bubble sort of the unsorted list after one iteration each is:
3 2 5 6 4 12 3 5 4 1 62 3 4 1 5 62 3 1 4 5 6What is a Bubble Sort?This refers to the simple sort algorithm that makes a sweep through a list to properly sort elements that are in improper order and loops until the list is sorted.
Hence, because one iteration is needed, there would be a new element added until the end of the list when they are all in their final position and no commas are used.
The complete answer is:
5. 2 1 3 4 5 66. 1 2 3 4 5 6Read more about bubble sort here:
https://brainly.com/question/14944048
#SPJ2
Write a statement that inserts the value 'wash dog' into the list activities so that it becomes the element at index 2.
Answers
I don't have much context on it or what programming language you want so...
activities[2] = 'wash dog'
Can someone help me with the following logical circuit, perform two actions. FIRST, convert the circuit into a logical
statement. SECOND, create a truth table based on the circuit/statement. (20 pts. each for statement and
truth table.

Answers
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
Given the logical circuit, we are required to perform two actions on it. Firstly, convert the circuit into a logical statement. Secondly, create a truth table based on the circuit/statement. Let's understand how to do these actions one by one:Conversion of Circuit into Logical Statement.
The given circuit contains three components: NOT gate, AND gate and OR gate. Let's analyze the working of this circuit. The two input variables A and B are first passed through the NOT gate, which gives the opposite of the input signal.
Then the NOT gate output is passed through the AND gate along with the input variable B. The output of the AND gate is then passed through the OR gate along with the input variable A.We can create a logical statement based on this working as: (not A) and B or A. This can also be represented as A or (not A) and B. Either of these statements is correct and can be used to construct the truth table.
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
In the truth table, we have all possible combinations of input variables A and B and their corresponding outputs for each component of the circuit.
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
For more such questions on Truth Table, click on:
https://brainly.com/question/13425324
#SPJ8
A virus that loads itself onto the target system's memory, infects other files, and then unloads itself is called a:
Answers
Answer:
True. A virus that loads itself onto the target system's memory, infects other files, and then unloads itself is called a: Direct-action virus.
Explanation:
A virus that loads itself onto the target system's memory, infects other files, and then unloads itself is called a Direct-action virus.
What is Direct-action virus?A direct action computer virus is known to be a virus class that is said to be self-multiplying malware that is known to be attached to any executable file.
Therefore, Note that A virus that loads itself onto the target system's memory, infects other files, and then unloads itself is called a Direct-action virus.
Learn more about virus from
https://brainly.com/question/26128220
#SPJ2
One of the first things authoritarian governments do is shut down the media so that _____. Select 3 options.
information can be controlled
information can be controlled
they can protect the public
they can protect the public
everyone is represented equally
everyone is represented equally
public knowledge can be manipulated
public knowledge can be manipulated
they can hide injustice and corruption
they can hide injustice and corruption
Answers
One of the first things authoritarian governments do is shut down the media so that:
information can be controlled (Option A)Public knowledge can be manipulated (Option D)they can hide injustice and corruption (Option E)What is an authoritarian government?An authoritarian regime has "a power concentrated in a leader or an elite not constitutionally answerable to the people". Unlike totalitarian nations, they will enable non-governmental social and economic organizations and rely on passive mass acquiescence rather than active popular backing.
Because autocratic leaders make choices without discussing the group, members may be dissatisfied with their inability to provide suggestions. Researchers have also discovered that authoritarian leadership frequently results in a lack of innovative problem-solving ideas, which can eventually harm the group's performance.
Learn more about authoritarian governments:
https://brainly.com/question/16940043
#SPJ1