which type of number would a scripting language consider the value 3.5?
Answers
The scripting language would consider the value 3.5 as a floating-point number.
Floating-point numbers are a type of data that is used to represent real numbers with decimal points. In many programming languages, including scripting languages, floating-point numbers are represented as either single-precision or double-precision numbers, depending on the amount of memory that is allocated to store them.
Single-precision floating-point numbers have a precision of about 7 digits and are represented with the letter "f" or "F" at the end of the number, while double-precision floating-point numbers have a precision of about 15 digits and are represented with the letter "d" or "D" at the end of the number.
You can learn more about scripting language at
https://brainly.com/question/31602599
#SPJ11
Related Questions
Suppose+you+run+a+parallel+program+on+a+parallel+computer.+if+10%+of+the+execution+of+the+program+is+sequential,+what+is+the+maximum+speedup+of+the+program+if+it+runs+on+25+processors?
Answers
The maximum speedup of the program when running on 25 processors is 7.35.
The maximum speedup of a parallel program on a parallel computer can be calculated using Amdahl's law. In this case, if 10% of the program's execution is sequential, the remaining 90% can be executed in parallel.
To calculate the maximum speedup, we use the formula:
Speedup = 1 / ((1 - P) + (P / N))
Where P is the portion of the program that can be executed in parallel (90% in this case) and N is the number of processors (25 in this case).
Substituting the values, we get:
Speedup = 1 / ((1 - 0.9) + (0.9 / 25))
= 1 / (0.1 + 0.036)
= 1 / 0.136
= 7.35
Therefore, the maximum speedup of the program when running on 25 processors is 7.35.
To know more about program visit:
https://brainly.com/question/30613605
#SPJ11
Rafe is transportation engineer working on a light rai, system. Who are the other two
specialized civil engineers Rafe is LIKELY working with?
(1point)
Answers
The other two specialized civil engineers Rafe is LIKELY working with are: Structural Engineers and geotechnical engineer
The specialized civil engineersThe second engineer is a geotechnical engineer who deals with the challenges related to ground conditions and provides recommendations for foundation design and slope stability.
Together, these specialized civil engineers collaborate with Ra e to address different engineering aspects of the project, ensuring the construction of a safe and efficient light rail system.
In summary Rafe would work with Structural Engineers and geotechnical engineer.
Read more on civil engineers
https://brainly.com/question/14559197
#SPJ1
Which methods can you use to move text from one part of the document to another?.
Answers
Answer:
-Cut using Ctrl+X, move your cursor to the new location of the text, then paste to the new location with Ctrl+V.
-Copy using Ctrl+C, move your cursor to the new location of the text, then paste to the new location with Ctrl+V.
Explanation:
what is the biggest benefit to using a dhcp server in a large network?
Answers
The biggest benefit to using a DHCP server in a large network is efficiency.
What is DHCP server ?DHCP (Dynamic Host Configuration Protocol) is a server/client networking protocol used to dynamically assign IP addresses to devices on a network. DHCP is used to provide a device with information such as its IP address, subnet mask, gateway address and DNS server address. The DHCP server maintains a pool of available IP addresses and assigns one to a device when it is connected to the network.
By having a DHCP server, the network administrator can easily set up and manage IP addresses, as well as other network settings, for all the devices on the network. This eliminates the need to manually configure each device, which can be time consuming and error-prone. DHCP also enables the network to automatically assign new devices an available IP address, reducing the amount of time needed for new device setup and configuration.
To learn more about DHCP server
https://brainly.com/question/14407739
#SPJ4
_____ oversee the work of various types of computer professionals and must be able to communicate with people in technical and nontechnical terms.
Answers
Systems analysts oversee the work of various types of computer professionals and communicate with people in technical and nontechnical terms.
Who works in an information systems?The information systems field is known to be made up of people in a firm who set up and build information systems, the individuals who use those systems, and the people who are known to managing them.
Note that there is high demand for IT staff whose common example includes programmers, business analysts, systems analysts, etc.
Learn more about computer from
https://brainly.com/question/24540334
Choose one answer for each statement, whether it is True or False:
a) CPU stands for Computer Processing Unit
b) The CPU processes all of the data and instructions that make a computer system work
c) The CPU carries out the fetch-decode-execute cycle
d) The clock speed, number of processor cores and cache size all affect CPU performance
Answers
b) true
c) true
d) true
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
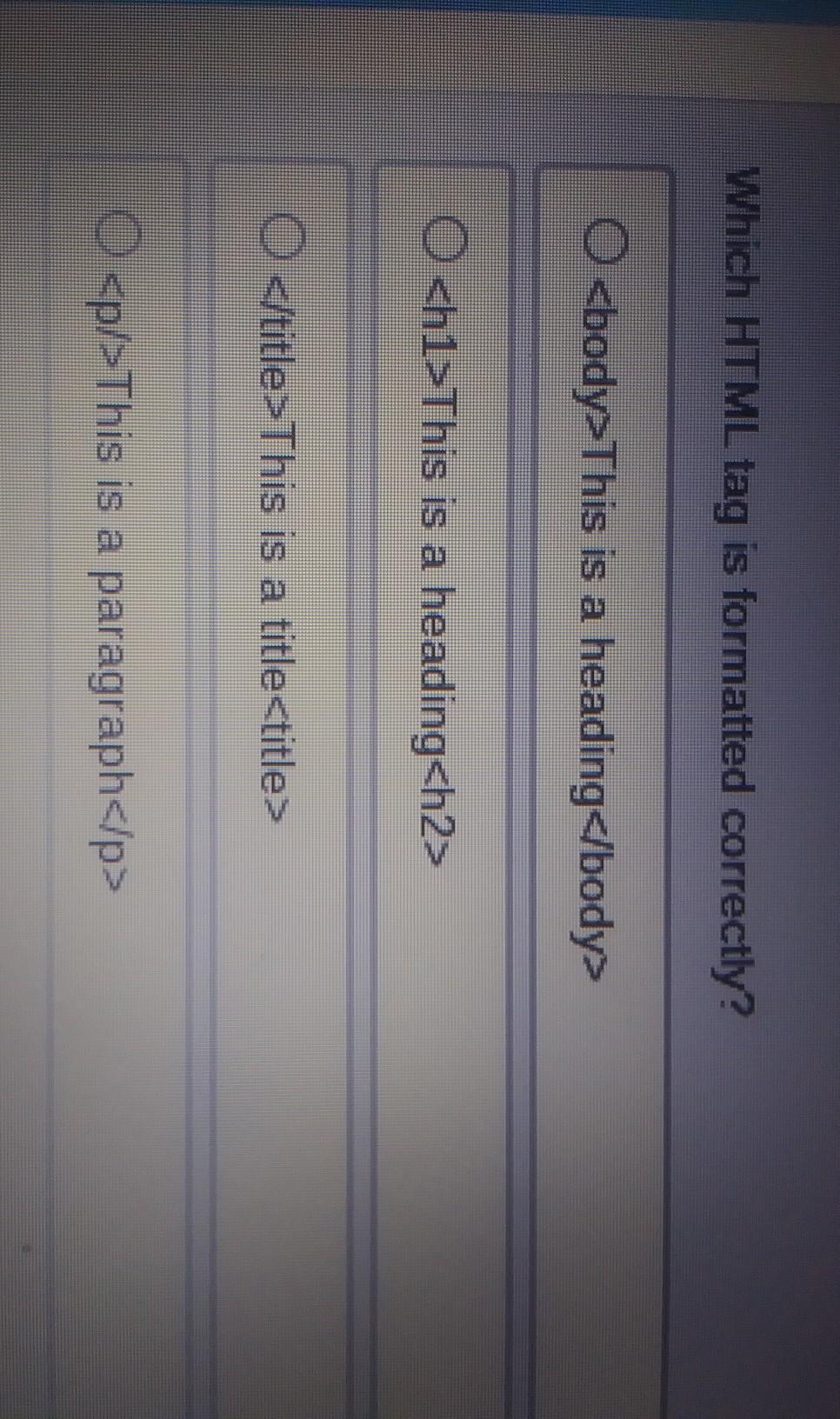
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
Provide a description of cloud computing. Include the advantages
and disadvantages and business drivers for using cloud
computing.
Answers
Cloud computing is a paradigm that enables convenient, on-demand access to a shared pool of configurable computing resources over the internet. It offers numerous advantages such as scalability, cost-effectiveness, flexibility, and reliability. However, there are also disadvantages, including security concerns, dependency on internet connectivity, and potential vendor lock-in.
Cloud computing refers to the delivery of computing resources, including servers, storage, databases, software, and networking, over the internet. It allows users to access and utilize these resources on-demand, without the need for extensive local infrastructure. One of the key advantages of cloud computing is scalability, as businesses can easily scale their resources up or down based on their needs, thereby optimizing costs and improving efficiency. Additionally, cloud services are typically offered on a pay-as-you-go basis, allowing organizations to save on upfront infrastructure costs and only pay for what they use.
Another advantage is flexibility, as cloud computing enables remote access to resources from anywhere with an internet connection. This facilitates remote work, collaboration, and global accessibility, promoting efficiency and productivity. Moreover, cloud providers often offer high levels of reliability and uptime through redundant systems and data backups, minimizing the risk of data loss or downtime.
However, there are also disadvantages to consider. Security is a major concern, as sensitive data may be stored in the cloud and exposed to potential breaches. Organizations must implement robust security measures and trust the cloud provider's security practices. Furthermore, reliance on internet connectivity becomes crucial, as any disruption in connectivity can affect access to cloud services and impact operations. Additionally, adopting a particular cloud provider's services may result in vendor lock-in, making it difficult to switch providers or migrate to alternative solutions.
From a business perspective, several drivers motivate the adoption of cloud computing. Cloud services enable organizations to be more agile by quickly provisioning resources to meet changing demands. This agility supports innovation, faster time to market, and the ability to scale operations as required. Cloud computing also allows businesses to optimize resource utilization by dynamically allocating and de-allocating resources based on workload fluctuations, thereby maximizing efficiency and cost-effectiveness. Moreover, by moving to the cloud, companies can reduce capital expenditures associated with building and maintaining physical infrastructure, shifting to a more predictable and flexible operational expenditure model.
Furthermore, cloud computing provides access to advanced technologies and services that might otherwise be costly or difficult to implement in-house. This includes machine learning, artificial intelligence, big data analytics, and high-performance computing capabilities, enabling organizations to leverage these technologies for competitive advantage and business growth.
In conclusion, cloud computing offers significant advantages in terms of scalability, cost-effectiveness, flexibility, and reliability. However, it also presents challenges related to security, connectivity, and vendor lock-in. Businesses are driven to adopt cloud computing for its ability to enhance agility, improve resource utilization, reduce infrastructure costs, and access advanced technologies and services. Careful consideration of these factors is essential for organizations seeking to harness the benefits of cloud computing while mitigating associated risks.
Learn more about computing here:
https://brainly.com/question/8645052
#SPJ11
which of these is a requirement for a computer to access the internet? i istart text, i, end text. a wired connection using either an ethernet or fiber optic cable ii iistart text, i, i, end text. a monthly payment to the internet engineering task force iii iiistart text, i, i, i, end text. the ability to connect that computer to another internet-connected device
Answers
Among the three options, the requirement for a computer to access the internet is a wired connection using either an ethernet or fiber optic cable (option i).
Why is this so?This is because a wired connection allows the computer to connect to a modem or router, which then connects to the internet service provider (ISP) and provides access to the internet.
A monthly payment to the Internet Engineering Task Force (option ii) is not a requirement for accessing the internet. The Internet Engineering Task Force (IETF) is a standards organization that develops and promotes internet standards, but it does not provide internet access.
The ability to connect that computer to another internet-connected device (option iii) is also not a requirement for accessing the internet, although it may be necessary for some specific applications or scenarios.
Read more about internet access here:
https://brainly.com/question/529836
#SPJ1
Answer:
lll only
Explanation:
i got it right
PLEASE HELP!!! THIS IS DUE TODAY!! WILL MARK BRAINLIEST!!
Two examples of good digital citizenship, and provide your reasoning as to why they are good.
Answers
Answer:
1. Respecting rules and cookies while browsing a website.
2. Being kind and properly following the requirements the owner asks you to follow. Reporting any sort of comment or image that is hurtful/harmful.
Explanation:
1. By the rules and cookies for a website, you ensure the safety of your device and are not putting any information at risk.
2. Cyberbullying is a huge issue and you can reduce cyberbullying with the simple steps of being kind and respecting others.
Conclusion:
These rules are examples of good digital citizenship and following them will benefit you and your peers greatly.
Example 1. Learning to type, use a mouse, and other computer skills.
Explanation: This is a good example of digital citizenship because by learning these skills it allows you to actively engage with others digitally and even give them pointers with their own learning.
Example 2. Avoiding harassment or hateful speech while conversing with others online.
Explanation: This is a good example of digital citizenship because by avoiding harassment or hateful speech you are contributing to making the digital world a safer place for everyone.
hopefully this deserves brainliest :)
Research the CCMA and answer the following questions (worth 7.5 points each): 1. What is the cost to renew? 2. What is the website to renew through? 3. What is the duration of certification? 4. What is the process to renew?
Answers
The specific organization or context of CCMA is not mentioned in the question. Without further information, it is challenging to provide accurate answers regarding the cost to renew, the website to renew through, the duration of certification, and the process to renew.
To obtain the required information, it is recommended to research the specific CCMA organization or certification program in question and refer to their official website, documentation, or contact their relevant authorities for accurate and up-to-date information regarding renewal costs, duration, website, and renewal process.
CCMA stands for different organizations or programs in various fields, such as the Contact Centre Management Association, Canadian Construction Materials Centre, California Certified Medical Assistant, etc. Each organization or program may have different renewal procedures, costs, and websites. To find the accurate answers, it is necessary to identify the specific CCMA context and conduct research accordingly. Visiting the official website, reviewing certification guidelines, FAQs, or contacting the relevant authorities associated with the CCMA program will provide the most accurate and up-to-date information regarding the cost to renew, the website to renew through, the duration of certification, and the process to renew.
Learn more about website here :
https://brainly.com/question/19459381
#SPJ11
write a paragraph on plastic and pollution within 100 words
Answers
Plastic is everywhere nowadays. People are using it endlessly just for their comfort. However, no one realizes how it is harming our planet. We need to become aware of the consequences so that we can stop plastic pollution. Kids should be taught from their childhood to avoid using plastic. Similarly, adults must check each other on the same. In addition, the government must take stringent measures to stop plastic pollution before it gets too late.
Plastic has become one of the most used substances. It is seen everywhere these days, from supermarkets to common households. Why is that? Why is the use of plastic on the rise instead of diminishing? The main reason is that plastic is very cheap. It costs lesser than other alternatives like paper and cloth. This is why it is so common.
Secondly, it is very easy to use. Plastic can be used for almost anything either liquid or solid. Moreover, it comes in different forms which we can easily mold.
Furthermore, we see that plastic is a non-biodegradable material. It does not leave the face of the Earth. We cannot dissolve plastic in land or water, it remains forever. Thus, more and more use of plastic means more plastic which won’t get dissolved. Thus, the uprise of plastic pollution is happening at a very rapid rate.
Most importantly, plastic pollution harms the Marine life. The plastic litter in the water is mistaken for food by the aquatic animals. They eat it and die eventually. For instance, a dolphin died due to a plastic ring stuck in its mouth. It couldn’t open its mouth due to that and died of starvation. Thus, we see how innocent animals are dying because of plastic pollution.
In short, we see how plastic pollution is ruining everyone’s life on earth. We must take major steps to prevent it. We must use alternatives like cloth bags and paper bags instead of plastic bags. If we are purchasing plastic, we must reuse it. We must avoid drinking bottled water which contributes largely to plastic pollution. The government must put a plastic ban on the use of plastic. All this can prevent plastic pollution to a large extent.
Answer:
Plastic is everywhere nowadays. People are using it endlessly just for their comfort. However, no one realizes how it is harming our planet. We need to become aware of the consequences so that we can stop plastic pollution. Kids should be taught from their childhood to avoid using plastic. Similarly, adults must check each other on the same. In addition, the government must take stringent measures to stop plastic pollution before it gets too late.
Uprise of Plastic Pollution
Plastic has become one of the most used substances. It is seen everywhere these days, from supermarkets to common households. Why is that? Why is the use of plastic on the rise instead of diminishing? The main reason is that plastic is very cheap. It costs lesser than other alternatives like paper and cloth. This is why it is so common.
Secondly, it is very easy to use. Plastic can be used for almost anything either liquid or solid. Moreover, it comes in different forms which we can easily mold.
Furthermore, we see that plastic is a non-biodegradable material. It does not leave the face of the Earth. We cannot dissolve plastic in land or water, it remains forever. Thus, more and more use of plastic means more plastic which won’t get dissolved. Thus, the uprise of plastic pollution is happening at a very rapid rate.
Which of the following gives the manufacturer
of a device with MAC address
6A:BB:17:5D:33:8F?
BB:17:5D
5D:33:8F
17:5D:33
6A:BB:17

Answers
When looking for MAC address prefixes, MACLookup makes the process simple by matching them to the company that made the chipset. The IEEE database is utilized.
What area of a MAC address represents the manufacturer?The 12 hexadecimal digits that make up a MAC address are typically organized into six pairs and separated by hyphens. The range of MAC addresses is 00-00-00-00-00-00 to FF-FF-FF-FF-FF. The number's first digit is often used as a manufacturer ID, and its second digit serves as a device identifier.
How can I locate manufacturer information?If you're using professional directories, it may be possible for manufacturers and suppliers to list their items according to the NAICS code, which will make it simpler for you to locate the companies that make and supply your products. You can access the NAICS directory online or in your local library.
to know more about MAC address here:
brainly.com/question/27960072
#SPJ1
5.4.7 Teenagers Code HS
Can someone help me with this? i currently have
if (age = 13){
println("Yes, you are a teenager.");
}else{
if (age <= 19){
println ("No, you are not a teenager.");
}
and anytime I type anything it always says yes so I'm confused.

Answers
Answer:
var teen = readInt("Are you a teen, if so what is your age? " );
if(teen >= 13 &&(teen < 19)){
println("Yes, you are a teenager.");
}else{
println("No, you are not a teenager.");
}
Explanation:
Hopefully this helps you :)
x = int ( input("what is your age ? "))
if x >= 13 and x <= 19:
print("yes you are a teenager")
else:
print("No, you are not a teenager")
The variable x is used to store the user input. it prompts the user to input his/her age.
The if/else statement is used to check if the user is a teenager or not. If the user's age is between 13 and 19, both inclusive the use will get a message "yes you are a teenager " and if otherwise the user will gets a message "No, you are not a teenager"
The bolded word in the codes are key words in python. Pay attention to indentation.
read more: https://brainly.com/question/12089897?referrer=searchResults
The process of repeatedly increasing a value by some amount is known as
O a. adding
O b. containing
O C. checking
O d. accumulating
Answers
What can you do in Microsoft Word 2016?
Answers
Answer:
write ?
Explanation:
Please answer the question no. 3 in the photo. I have exams. It's related to HTML.

Answers
Answer:
<p style="font-size: x-large; color: blue;">SILK FAB</p>
<p style="font-size: normal; color: red;">SILK FAB</p>
<p style="text-decoration: underline;">SILK FAB</p>
<p>Come to the silk fab organised by Govt. of India and get all the following text - "Come to weavers of all the states. <span style="color: green;">Encourage handloom</span> and give your support to hardworking weavers". The words "Encourage handloom" should be in green colour.</p>
Explanation:
Here is a code snippet in HTML that should accomplish what you described:
This code will print "SILK FAB" in the largest size in blue, followed by "SILK FAB" in normal size and red, and then "SILK FAB" in normal size and underlined. The final paragraph will contain the rest of the text, with the words "Encourage handloom" in green.
1. A two-dimensional array of ints with 4 rows, has been created and assigned to a2d. Write an expression whose value is the total number of ints that could be stored in the entire array.
2. A two-dimensional array of ints, has been created and assigned to a2d. Write an expression whose value is the number of elements in the last row. (Assume the array is not empty.)
Answers
1. A two-dimensional array, also known as a matrix, is a data structure that contains elements arranged in rows and columns. In this case, you have a two-dimensional array of ints named "a2d" with 4 rows.
To find the total number of ints that could be stored in the entire array, you need to multiply the number of rows by the number of columns. Let's assume there are 'n' columns in this array. The expression to calculate the total number of ints in the array would be:
Total number of ints = number of rows * number of columns
Total number of ints = 4 * n
2. To find the number of elements in the last row of a two-dimensional array, you need to determine the length of that row. In the array "a2d", you can do this by using the length property of the last row. Since the array is not empty and has at least one row, you can use the following expression to find the number of elements in the last row:
Number of elements in the last row = a2d[a2d.length - 1].length
This expression calculates the length of the last row by subtracting 1 from the total number of rows in "a2d" (since arrays use zero-based indexing) and then obtaining the length of that row.
Learn more about zero-based indexing here:
https://brainly.com/question/16235818
#SPJ11
Name six (6) password policies you could enable in a Windows Domain
5. What are some of the options that you can exercise to configure the MBSA scan?
Answers
Password policies that can be enabled in a Windows Domain are Password length: minimum Password length and maximum Password length, Password history: Minimum password age and Maximum password age, Password complexity.
Remember that password policy should be easy for users to remember and type, but difficult for others to guess or crack, it should contain uppercase, lowercase, numbers, and special characters. Password policies are used to enforce a strong password policy across the domain. Doing so strengthens security within the domain by making it harder for passwords to be cracked. In the introduction part, we introduce the password policies that are used to enforce a strong password policy across the domain and provide a brief explanation of password policies.In the body part, we explained all six password policies that can be enabled in a Windows Domain, password length minimum, password length maximum, password history, minimum password age, maximum password age, and password complexity.In conclusion, we can summarize that by implementing these password policies, we can enforce a strong password policy across the domain and strengthen security within the domain.
To learn more about Password, visit:
https://brainly.com/question/32669918
#SPJ11
How do you create an array in data structure?
Answers
To create an array in a data structure, you first need to determine the size of the array and the type of data that it will hold.
Once you have this information, you can declare the array and initialize it with values. The syntax for creating an array can vary depending on the programming language, but generally involves using square brackets [] to denote the array and specifying the size and data type within the brackets. For example, in Java, you would declare an array of integers with a size of 10 as follows:
int[] myArray = new int[10];
This creates an integer array called myArray with 10 elements. You can then populate the array with values by assigning values to specific elements, such as myArray[0] = 5; or by using a loop to iterate through the array and set each element to a value. Arrays are a fundamental data structure used in programming to store and manipulate collections of data.
To learn more about array in a data structure, click here:
https://brainly.com/question/30614560
#SPJ11
Text books are not a good source for finding ideas about what to study because the teachers make up the test questions. Please select the best answer from the choices provided T F
Answers
Answer:
Text books are not a good source for finding ideas about what to study because the teachers make up the test questions. False- most teachers use the textbooks as guides. Visiting the library to seek books on your current topic will not help you in determining what to study.
Explanation:
Text books are not a good source for finding ideas about what to study because the teachers make up the test questions. False- most teachers use the textbooks as guides. Visiting the library to seek books on your current topic will not help you in determining what to study.
Answer:
False
Explanation: I took the test and passed!!
Prove that any two triangulations of a convex polygon can be transformed into each other by a sequence of edge flips.
Answers
We may use the following procedures to demonstrate that any two triangulations of a convex polygon can be turned into each other by a series of edge flips:
1. Begin with two triangulations of the same convex polygon.
2. Choose an edge in one of the triangulations that are not present in the other.
3. Flip an edge on the specified edge. An edge flip entails deleting the selected edge and replacing it with a new edge that links the two vertices that were not previously connected by the selected edge. As a consequence, a new triangulation will be formed.
4. Keep in mind that the edge flip operation preserves the polygon's convexity.
5. Steps 2-4 should be repeated until the two triangulations are the same.
This process ensures that a sequence of edge flips can be used to transform any two triangulations of a convex polygon into each other.
Learn more about edge flips:
https://brainly.com/question/17174293
#SPJ11
what is a bookmark hyperlink?
Answers
A Bookmark is an object used to record a location in a Word document. You can define a bookmark programmatically with the BookmarkStart and BookmarkEnd pair of elements. A Hyperlink is a document element used to jump to a Bookmark in the same document or to an external resource
In an object-oriented database, an extent is the equivalent to a(n) _____ in a relational database.
Answers
Therefore, an extent in an object-oriented database and a table in a relational database serve a similar purpose of organizing and storing data.
In an object-oriented database, an extent is the equivalent to a table in a relational database.
In an object-oriented database, data is organized into classes or object types, and each class corresponds to a table in a relational database. An extent represents a collection of instances or objects belonging to a particular class or object type. It can be seen as a logical grouping of similar objects within a class.
Similarly, in a relational database, a table consists of rows and columns, where each row represents a record or instance, and each column represents a field or attribute. The table structure defines the schema or structure of the data stored in the database.
Learn more about database here
https://brainly.com/question/30163202
#SPJ11
Where would you find the Create Table Dialog box ?
Answers
Hope it’s right
Best luck with your studying
Answer:
From the Insert command tab, in the Tables group, click Table. NOTES: The Create Table dialog box appears, displaying the selected cell range.
Explanation:
3 disadvantage of bus topology
Answers
Answer:
Entire network fail is there any problem in a central cable.It does not support very large networks.Maintenance cost may be much higher in the long run.A box has a mass of 5 kg. What is the weight of the box on Earth?
Show your work
Answers
Answer:
5 kg
Explanation:
5 kg
Which data format type will increase the cell width instead of overlapping into empty cells?
a. number
b. general
c. text
d. date
Answers
Number is a data format type that will widen the cell rather than encroaching into empty ones.
How can I adjust a cell's size without altering the entire column?Combine several cells. One choice is to merge multiple cells if you want to increase the size of a cell without changing the row or column as a whole. By combining two or more cells into one that spans several rows or columns, you can merge cells.
How can I make Excel's cell sizes larger?Under the Home tab, in the Cells group, select Format. Simply choose Default Width from the Cell Size menu. Click OK after entering a new value in the Standard column width box.
To know more about data format type visit:-
https://brainly.com/question/30019805
#SPJ4
PLEASE HELP!! FIRST ANSWER WILL MARK AS BRAINLIEST!!!
What is the most efficient way to control the type of information that is included in the .msg file when a user forwards a contact to another user?
Use the "As an Outlook Contact" option.
Create an additional contact with limited information.
Use the Business Card option.
Create the contact using the XML format.
Answers
Answer:
A on edge
Explanation:
How is the author's point of view
different from the officials' point of
view?
The officials' position is that freedom
to
is
guaranteed by the Constitution. The
author thinks the Constitution also
protects the rights of people who
.So
her position is that we need
Answers
Answer: The authors point of view is different because they could be describing themselves or something but the " Reader" might not understand what is happening because they may not get it
Explanation: