Why cannot k-means clustering be used in non euclidean space? Describe one alternative approach for clustering in such scenario
Answers
K-means clustering cannot be used in non euclidean space because in non-Euclidean spaces, such as the spaces defined by discrete data, text data, graphs, and other types of structured data, the concept of distance may not be well-defined or meaningful. One alternative approach for clustering in non-Euclidean spaces is to use other clustering algorithms that can handle non-Euclidean spaces.
K-means clustering is a popular method for clustering data in Euclidean space, where distances between points can be easily calculated using the Pythagorean theorem. However, this method cannot be used in non-Euclidean spaces, such as spherical or hyperbolic spaces, where the distance metric is different.
An alternative approach for clustering in such scenarios is to use other clustering algorithms that can handle non-Euclidean spaces, such as hierarchical clustering, spectral clustering, or density-based clustering. These methods take into account the unique properties of the space being analyzed and use different distance metrics to calculate the distance between points.
For example, in spherical space, one can use the Haversine distance metric, which measures the great-circle distance between two points on a sphere. In hyperbolic space, one can use the Poincaré disk model or the Klein model, which transform the space into a Euclidean space and enable the use of traditional Euclidean distance metrics.
In summary, when dealing with non-Euclidean spaces, k-means clustering cannot be used, and alternative clustering methods that take into account the specific properties of the space should be considered.
To learn more about clustering : https://brainly.com/question/30881716
#SPJ11
Related Questions
The registers are the communication channels inside the computer.( true or false)
Answers
Registers are storage, not channels
A study was undertaken to compare moist and dry storage conditions for their effect on the moisture content(90) of white pine timber. The report on the findings from the study included the following statement: "The study showed a significant difference (observed difference =1.1% : p-value 0.023 ) in the moisture content of the pine timber under different storage conditions. Level of Significance (a) for the test was 5%.
2
Based on this informstion, which of one the following statements is necessarily FAL.SE? The probabaisy that there is no difterence between moist and dry stor fpe conditons is 0.023 Thi observed difference between the mean moisture contents 1.1869 b uniskely to be due to chunce aione Trthis stody was repeated 100 hmess oven then we wehald espect to fincorrectly) conciude there was differense in thet storage methods for approvimatety 5 of the 100 studies ithat l. 5% of the time we would say there wara difference in the storago methods when in fact, there was nonek. A statistically significant difference of 1.18 in the moisture content of the white pine is not necessarily a difference of practical importance A. 95% confidence interval for the mean ( μ of a random variable, based on the t-distribution, is found to be (4.3, 4.9). With minimal further calculations, the p-value for a test of
H
0
:μ=5
H
1
:μ=5
can be ciaimed to be <0.001 can't say without knowing the sample size A significance test was performed to test the null hypothesis H
0
:μ−2 versus the alternative hypothesis H
1
:μ
∗
2. The test statistic is z=1.40. The p-value for this test is approximately 0.16 0.08 0.003 0.92 0.70
Answers
The false statement among the given options is:A statistically significant difference of 1.18 in the moisture content of the white pine is not necessarily a difference of practical importance.
The statement implies that even though the observed difference in moisture content is statistically significant, it may not have practical importance or relevance. However, in reality, statistical significance indicates that there is a meaningful difference between the two storage conditions. The p-value of 0.023 suggests that the observed difference is unlikely to occur by chance alone. Therefore, the statistically significant difference is likely to be practically significant as well.
To know more about moisture click the link below:
brainly.com/question/13724830
#SPJ11
which is true?a.a field can not be initialized in the field declarationb.a default constructor has at least one parameterc.a constructor has no return typed.the java compiler does not initialize fields to their default values
Answers
Java is a high-level programming language that is easy to learn. It is primarily used to create web and mobile applications, but it is also useful for developing other kinds of software. Java has several features that make it unique, such as automatic memory management and platform independence. Java is an object-oriented language, which means that everything in Java is an object. A field can be initialized in the field declaration, and the Java compiler will initialize fields to their default values if they are not explicitly initialized. A default constructor has no parameters, and a constructor has no return type. so, the correct answer is a,b,c and d .
a. A field can be initialized in the field declaration .A field can be initialized in the field declaration. The syntax for declaring a field in Java is:
```
[= ];
```
You can initialize the field in the declaration by providing a value for the initialization. For example, you can declare and initialize a field like this:
``
int count = 0;
```
b. A default constructor has no parameters
A default constructor has no parameters. A constructor is a special method that is used to create objects. A default constructor is a constructor that is provided by the Java compiler if no other constructor is defined. The default constructor has no parameters, and it initializes all fields to their default values.
c. A constructor has no return type
A constructor has no return type. Constructors are used to initialize the object's state. They are called when an object is created using the new keyword. A constructor does not return a value, not even void.
d. The Java compiler will initialize fields to their default values if they are not explicitly initialized
The Java compiler will initialize fields to their default values if they are not explicitly initialized. This is called default initialization. The default value for a numeric field is 0, for a boolean field is false, and for an object field is null.
To know more about java visit:-
https://brainly.com/question/12978370
#SPJ11
identify a protocol that allows data to be privately exchanged over public networks.
Answers
The Virtual Private Network (VPN) protocol allows data to be privately exchanged over public networks.
A Virtual Private Network (VPN) is a technology that provides a secure and private connection to a network over the Internet. It allows a user to connect to a private network through a public network such as the Internet as if they were physically connected to the private network.
It allows for secure and encrypted communication between remote devices. It is commonly used by businesses and individuals who want to protect their online privacy and security.
There are several protocols used for setting up a VPN connection, including:
Point-to-Point Tunneling Protocol (PPTP)
Layer 2 Tunneling Protocol (L2TP)/I
PsecInternet Protocol Security (IPsec)
Secure Sockets Layer (SSL)/Transport Layer Security (TLS)
OpenVPN and more
However, all of these VPN protocols have one thing in common: they encrypt data to provide a secure and private connection over public networks.
Know more about Virtual Private Network (VPN) here:
https://brainly.com/question/14122821
#SPJ11
The water splashed all over the top of the car.
Answers
Answer:
e
Explanation:
Dry the car of i guess
what is the main purpose of the circulatory system
Answers
The network of blood vessels and the heart that carries blood throughout the body. This system helps tissues get the right amount of nutrients, oxygen, and waste disposal.
The most important component of the circulatory system?The primary function of the circulatory system is to carry oxygen, nutrients, and hormones to the muscles, tissues, and organs throughout the body. Another role of the circulatory system is to remove waste from cells and organs so that your body can eliminate it.
What is the primary goal of this quiz about the circulatory system?The circulatory system's job is to provide nutrients and oxygen to body cells while returning carbon dioxide and oxygen-poor blood to the heart and lungs.
To know more about circulatory system visit:-
https://brainly.com/question/29259710
#SPJ4
Which of the following statements are true regarding cognitive impairments? Select 3 options.
Speech input devices help those who are cognitively impaired understand the contents of the screen.
Delivering content in different ways, such as using video, animations, and text, helps promote cognitive accessibility.
To improve cognitive accessibility, the developer should focus on a clear and consistent design.
Even though there are different causes for cognitive impairment, many of the resulting functional issues are similar.
Cognitive issues are learning disabilities caused by genetic disorders.
Answers
Answer:
The correct options are;
Delivering content in different ways, such as using video, animations, and text, helps promote cognitive accessibility
To improve cognitive accessibility, the developer should focus on a clear and consistent design
Even though there are different causes for cognitive impairment, many of the resulting functional issues are similar
Explanation:
Cognitive impairment is the condition of a person having difficulty in concentrating, learning, recalling from memory, or making functional decisions. Depending on the severity, cognitive impairment may be classified as severe or mild
Symptoms includes, loss of memory, asking the same questions or telling the same story frequently, unable to recognize people they already know, or places they have already been to, having problems with vision and being unable to plan or see tasks through
Answer:
The correct options are;
Delivering content in different ways, such as using video, animations, and text, helps promote cognitive accessibility
To improve cognitive accessibility, the developer should focus on a clear and consistent design
Even though there are different causes for cognitive impairment, many of the resulting functional issues are similar
Explanation:
explain why the computer is powerful working tool???
Answers
Answer:
here ya go
Explanation:
A computer is a powerful tool because it is able to perform the information processing cycle operations (input, process, output, and storage) with amazing speed, reliability, and accuracy; store huge amounts of data and information; and communicate with other computers.
why does my wifi keep disconnecting and reconnecting?
Answers
Answer:
get a beter rouour
Explanation:
v
Why we use Social media. Spport your answer with logical reason
Answers
Through social media platforms like Facebiook, Twititer, and Insttagram, we can share updates, photos, and videos with our loved ones, no matter where they are in the world. Social media also provides a platform for networking and professional development.
We use social media for various reasons. One reason is that it allows us to connect with others and stay in touch with friends, family, and colleagues. LinnkedIn, for example, allows professionals to connect with others in their field, share expertise, and discover job opportunities.
Another reason for using social media is its ability to provide information and entertainment. We can follow news outlets, blogs, and influencers to stay informed and engaged. Additionally, social media enables us to join communities of like-minded individuals and participate in discussions on various topics. Overall, social media offers a convenient and accessible way to connect, learn, and be entertained.
To know more about social media platforms visit :-
https://brainly.com/question/32908918
#SPJ11
6. (01.02 LC)
The programming language C: uses a series of 1s and Os to communicate with the computer. (5 points)
O True
False
Answers
Answer:
False
Explanation:
Which process converts a high-level language such as Python into machine language?
compiling
debugging
processing
analyzing
Answers
The process that converts a high-level language such as Python into machine language is known as Compiling. Thus, the correct option for this question is A.
What is Compilation?Compilation may be defined as a process that significantly involves the conversion of high-level programming language into a machine language that a computer can easily understand and responds to it.
According to the context of this question, machine languages are those languages that are utilized by computers in which instructions are represented in the form of numbers. This assists the computer to understand the instruction and act on them.
While high-level languages refer to any programming language that enables the development of programs.
Therefore, compilation is the process that converts a high-level language such as Python into machine language.
To learn more about Compilation, refer to the link:
https://brainly.com/question/885133
#SPJ5
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
discuss what is a trigger in database, and what is its purpose? discuss real-word application example of triggers. please do not write the sql command. provide a scenario of real-world application that you will use triggers.
Answers
A trigger is a special type of stored procedure in a database that automatically executes when an event occurs in the database.
Example of trigger :
A real-world application example of triggers is an order management system. For example, when an order is placed, a trigger can be used to automatically check if there is enough stock to fulfill the order. If there is sufficient stock, the trigger can update the inventory in the database and send a notification to the customer that the order has been successfully processed. If there is insufficient stock, the trigger can update the customer with the new delivery date. This helps to ensure that orders are fulfilled quickly and efficiently, while maintaining data integrity.
To know more about trigger
https://brainly.com/question/13384276
#SPJ4
Jeremiah needs to see data in two different table views from two regions without creating two tables. Which two features would he use to create this?
Answers
Answer:
Tables & Filter
Explanation:
That correct
Answer:
D. Tables and filter
Explanation:
1. .……............. can be considered as raw data.
(a) Sithum’s G.C.E. (O/L) examination results
(b) Z-Score of G.C.E. (O/L) examination results
(c) The average marks of students of G.C.E. (O/L) examination
(d) The top ten total marks of students of G.C.E. (O/L) examination
Answers
Answer:
(a) Sithum's G.C.E. (O/L) examination results
Explanation:
Raw data which is also known as primary data, are the data collected when performing a research, investigation or study, which are obtained through a survey, experiment, or observation and from which correlations and distributions can be calculated, only when the data is complete
Therefore, raw data is unprocessed data, and the option which can be considered as raw data is the option which is not processed, which is Sithum's G.C.E. (O/L) examination results.
How do you delete data from a cell?
O press the delete key
O the d key
O the enter key
O F5 key

Answers
Answer:
press the delete key is the way to delete the data from a cell
What is Utility Software ? Name any two utility programs.
Answers
Answer:
Utility software is any software that gives pleasure and two utility programs could be linux and unix uwu
Explanation:
WinRar, Winzip, is a type of program that provides configuration services
An employee sets up Apache HTTP Server. He types 127.0.0.1 in the browser to check that the content is there. What is the next step in the setup process?
Answers
Answer:
Set up DNS so the server can be accessed through the Internet
Explanation:
If an employee establishes the HTTP server for Apache. In the browser, he types 127.0.0.1 to verify whether the content is visible or not
So by considering this, the next step in the setup process is to establish the DNS as after that, employees will need to provide the server name to the IP address, i.e. where the server exists on the internet. In addition, to do so, the server name must be in DNS.
Hence, the first option is correct
Your question is lacking the necessary answer options, so I will be adding them here:
A. Set up DNS so the server can be accessed through the Internet.
B. Install CUPS.
C. Assign a static IP address.
D. Nothing. The web server is good to go.
So, given your question, what is the next step in the setup process when setting up an Apache HTTP Server, the best option to answer it would be: A. Set up DNS so the server can be accessed through the Internet.
A server can be defined as a specialized computer system that is designed and configured to provide specific services for its end users (clients) on a request basis. A typical example of a server is a web server.
A web server is a type of computer that run websites and distribute web pages as they are being requested over the Internet by end users (clients).
Basically, when an end user (client) request for a website by adding or typing the uniform resource locator (URL) on the address bar of a web browser; a request is sent to the Internet to view the corresponding web pages (website) associated with that particular address (domain name).
An Apache HTTP Server is a freely-available and open source web server software designed and developed to avail end users the ability to deploy their websites on the world wide web (WWW) or Internet.
In this scenario, an employee sets up an Apache HTTP Server and types 127.0.0.1 in the web browser to check that the content is there. Thus, the next step in the setup process would be to set up a domain name system (DNS) so the server can be accessed by its users through the Internet.
In conclusion, the employee should set up a domain name system (DNS) in order to make the Apache HTTP Server accessible to end users through the Internet.
Find more information here: https://brainly.com/question/19341088
a file that serves as a starting point for a new document
Answers
Answer:
The appropriate response is "Template".
Explanation:
A template would be a document that might open new opportunities for such a new folder. Because once you launch a framework, that's already pre-formatted sometimes in a manner. This same template will indeed presumably have such identification and phone number environment throughout the upper left, a person receiving identify location somewhat below something on the opposite side, a response body location further below, as well as a signature, identify at either the lower part.Part 1
Find a public, free, supervised (i.e., it must have features and labels), machine learning dataset from somewhere *other than* The UCI Machine Learning Repository or Kaggle.com. Provide the following information:
The name of the data set.
Where the data can be obtained.
A brief (i.e. 1-2 sentences) description of the data set including what the features are and what is being predicted.
The number of examples in the data set.
The number of features for each example. If this isn’t concrete, describe it as best as possible.
Extra credit will be given for: (1) the most unique, (2) the data set with the largest number of examples and (3) the data set with the largest number of features.
Part 2
Two datasets have been provided and the descriptions can be found below.
Datasets
TitanicPreview the document: Predict whether the passenger survived (last column) based on:
First class (whether the passenger was in first class or not)
Sex (0 = Male, 1 = Female)
Age (0 = <25, 1 = 25+)
SibSp (had siblings/spouses aboard?)
ParCh (had parents/children aboard?)
Embarked (Left from Southampton?)
Breast CancerPreview the document: Predict the recurrence of breast cancer (last column) based on:
age: 10-19, 20-29, 30-39, 40-49, 50-59, 60-69, 70-79, 80-89, 90-99.
menopause: lt40, ge40, premeno.
tumor-size: 0-4, 5-9, 10-14, 15-19, 20-24, 25-29, 30-34, 35-39, 40-44, 45-49, 50-54, 55-59.
inv-nodes: 0-2, 3-5, 6-8, 9-11, 12-14, 15-17, 18-20, 21-23, 24-26, 27-29, 30-32, 33-35, 36-39.
node-caps: yes, no.
deg-malig: 1, 2, 3.
breast: left, right.
breast-quad: left-up, left-low, right-up, right-low, central.
irradiat: yes, no.
Questions
For each dataset, your program should output multiple training error rates, one for each feature. For each of the features, calculate the training error rate if you use only that feature to classify the data. (Namely, we are building a 1-level decision tree. Do not use any existing implementation of the decision tree model for this question.)
For each dataset, use some library (e.g., sklearn) to build a full decision tree and report the training error rate. (One might use an existing implementation of the decision tree model for this question.)
Can we directly use the kNN or the Perceptron model to train a classifier on these two datasets? A brief and reasonable explanation would be good enough. (Hint: compared to the dataset in PA 1, is there any trouble on how to compute the distances or how to compute the inner-products? Optionally, one might come up with some ideas so that these issues are resolved.)
Answers
Part 1
For a public, free, supervised machine learning dataset from somewhere other than The UCI Machine Learning Repository or Kaggle.com, the following is the information:
The name of the data set: "COVID-19 Vaccination Progress Data".Where the data can be obtained: The data set can be found on Our World in Data’s website.A brief (i.e. 1-2 sentences) description of the data set including what the features are and what is being predicted:
The COVID-19 Vaccination Progress Data set includes data about the progress of vaccinations all around the world. The features of this dataset are the location, date, total vaccines administered, and total people vaccinated. The number of examples in the data set is 6,117.The number of features for each example:
he data set has four features for each example.Part 2Titanic Data SetTraining Error Rate of a single feature:
First class: 0.23883
Sex: 0.19057
Age: 0.40668
SibSp: 0.28952
ParCh: 0.28807
Embarked: 0.30625
Training error rate after building a full decision tree: 0.17532
Breast Cancer Data SetTraining Error Rate of a single feature:
age: 0.28683menopause: 0.34581
tumor-size: 0.34241inv-nodes: 0.26491
node-caps: 0.24038deg-malig: 0.35058
breast: 0.34581
breast-quad: 0.35960
irradiat: 0.28335
Training error rate after building a full decision tree: 0.05186
Can we directly use the kNN or the Perceptron model to train a classifier on these two datasets?
For these two datasets, we cannot directly use the kNN or the Perceptron model to train a classifier since both of these models require calculating the distance or the inner product between different data points. However, in the case of the Titanic dataset, the features are already numerical, so it would be possible to use kNN or Perceptron after normalizing the data. In contrast, the Breast Cancer dataset is not numerical, and we would need to convert the features into numbers, which could cause problems when training the model.
Therefore, it is best to use other models like decision trees, SVM, or logistic regression on the Breast Cancer dataset.
To know more about the machine learning, click here;
https://brainly.com/question/31908143
#SPJ11
what type of printer is most suitable for multi-part forms?
Answers
The type of printer that is most suitable for multi-part forms is a dot-matrix printer.
Dot-matrix printers use a series of small pins to strike an inked ribbon against a paper to create an image or text. They are known for their ability to print on multi-part forms, such as carbon copies, triplicates, or quadruplicates, which are commonly used in industries such as finance, healthcare, and manufacturing.
One of the advantages of dot-matrix printers is that they can create multiple copies of a document at the same time without the need for additional hardware, as the impact of the pins transfers the ink onto all copies. Additionally, dot-matrix printers are durable and reliable, making them suitable for printing high volumes of multi-part forms.
While dot-matrix printers may not offer the same print quality or speed as other types of printers, such as inkjet or laser printers, they remain a popular choice for industries that require multi-part forms.
Learn more about dot-matrix here:
https://brainly.com/question/30885094
#SPJ11
Which best describes the Quick Access toolbar and the ribbon tabs?
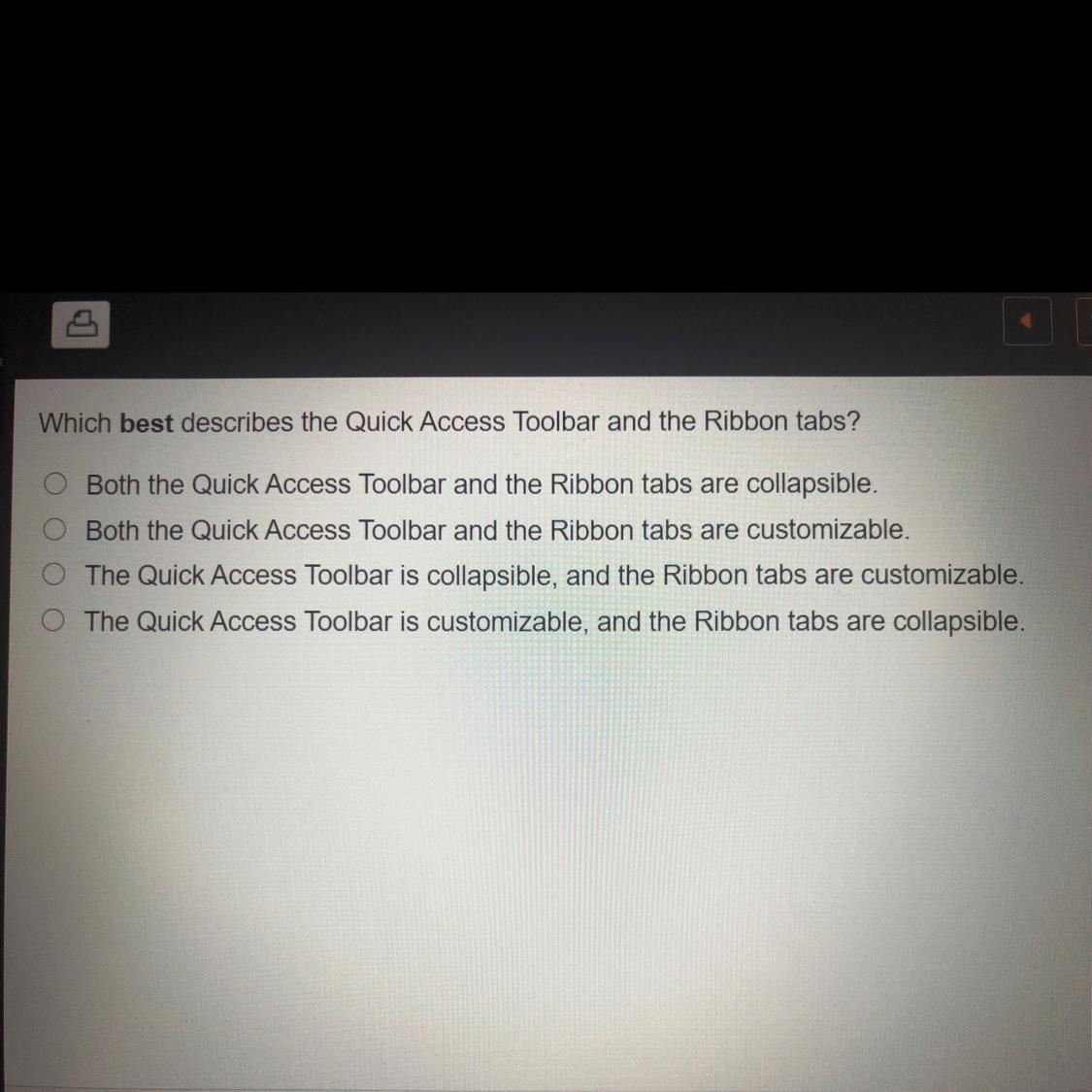
Answers
Answer: D
Explanation: The Quick Access Toolbar is customizable, and the Ribbon tabs are collapsible.
Answer:
d
Explanation:
an obstacle or barrier that may prevent you from accomplishing your goal is called
Answers
Answer:
a roadblock
Explanation:
What should you remember about typography while creating your résumé?
It is advisable to avoid using [blank] font when creating your résumé. To facilitate readability, your font should not be smaller than [blank]
points.
Answers
Answer:
Your font should not be smaller than 0.5
Explanation:
Jason is creating a web page on the basic parts of a camera. He has to use a mix of both images and content for the web page to help identify different parts of a camera. What screen design techniques should he apply to maintain consistency in the content and images? A. balance and symmetry B. balance and color palette C. balance and screen navigation D. balance and screen focus
Answers
A. Balance and symmetry would be the most appropriate screen design techniques to maintain consistency in the content and images on the web page about the basic parts of a camera. Balance refers to the even distribution of elements on the screen, and symmetry is a specific type of balance that involves creating a mirror image effect. By applying balance and symmetry, Jason can ensure that the content and images are evenly distributed and aligned, which can make the web page more visually appealing and easier to understand.
You have the following code:
----------------------------------------------------------------------------------------------
fruit_list = ["strawberries", "bananas", "apples", "grapes"]
total_cost = 0
for fruit in fruit_list:
if fruit in ["apples","bananas"]:
total_cost += 3
elif fruit == "cantaloupe":
total_cost += 5
elif fruit in ["raspberries","strawberries","grapes"]:
total_cost += 4
-------------------------------------------------------------------------------------------------
What will be the value of total_cost?
A.13
B.14
C.15
D.7
Answers
Answer:
7
Explanation:
We already have the functions that tells us how much to add. If you add all this, you will get 12. HOWEVER because cantaloupe is in the list, the computer does not count that. So if we add that again without 5(how much the cantaloupe costs), we get 7.
What does CRUD programming means and why do we need to learn it?
Answers
Answer:
CRUD Meaning : CRUD is an acronym that comes from the world of computer programming and refers to the four functions that are considered necessary to implement a persistent storage application: create, read, update and delete.
Why we need to learn it? : The ability to create, read, update and delete items in a web application is crucial to most full stack projects. CRUD is too important to be ignored, so learning it first can really improve confidence within unfamiliar stacks.
Cache hit occurs when requested data is found in cache. For cache hit, data in main memory is loaded again to cache.
Answers
Answer:
TRUE
Explanation:
In the field of computing, cache is defined as the software or hardware component which stores the data and information for future use. It is a place in the computer software or hardware where the data are stored for their future use so that it can be retrieved faster when the data or the information is requested by the user.
A cache hit occurs when the data that is requested by the user is found in the cache memory. It is meant to deliver the data faster to the processor. And for the cache hit, the data in the memory is again loaded in the cache when the data is used.
Any Suggestions on what to do here? I already restarted my PC twice, cleared my browsing data, and rebooted the wifi network....

Answers
Answer:
if u r at school, then it might be blocked.
if not, get a vpn proxy.