Windows defender is configured to regularly scan your system; however, you also want to scan a removable storage device that you just connected to your windows system.
Click the scan option you should use to accomplish this.
Answers
To scan a removable storage device, use the "Custom scan" option in Windows Defender.
In order to scan a removable storage device that you just connected to your Windows system, follow these steps:
1. Open Windows Defender by typing "Windows Defender" in the search bar and clicking on the app.
2. Click on the "Virus & threat protection" tab on the left side of the window.
3. Click on "Quick scan" under the "Current threats" section to reveal more scan options.
4. Select "Custom scan" and then click "Scan now."
5. A new window will open, allowing you to choose the removable storage device you want to scan.
6. Locate the connected device, click on it, and then click "Select Folder."
7. Windows Defender will begin scanning the selected removable storage device for potential threats.
Learn more about scan here:
https://brainly.com/question/31560424
#SPJ11
Related Questions
For what two reasons is it important to add comments to a program?
Answers
Which guidelines should be used to make formatting tasks more efficient?
Use pasted text only; this does not keep the original formatting.
Keep formatting fancy; this makes Word documents look better.
Save styles in the document; this makes working with multiple documents easier.
Avoid pasting text from other documents; this makes formatting easier.
Answers
Answer:
Use pasted text only; this does not keep the original formatting.
Explanation:
bc
Answer:
Use pasted text only; this does not keep the original formatting.
Explanation:
the wireless technology that can be used to transmit data between 2 different network
Answers
Answer:
most probably that's wifi.
this text command defines how text will appear
Answers
In programming, the text command is not a specific command, but rather a term used to refer to a wide range of commands and functions that manipulate or display text.
What is a text command?Text commands may include functions for formatting, searching, replacing, and displaying text within a program or on a screen. These commands may be used in a variety of programming languages, including C, as you mentioned.
In C, for example, there are many standard library functions that can be used to work with text. Some of the most commonly used functions for working with text in C include:
printf(): used to display formatted text on the screen or in a file
scanf(): used to read formatted text from the keyboard or a file
strcpy(): used to copy one string of text to another
strcmp(): used to compare two strings of text to determine if they are equal
strlen(): used to determine the length of a string of text
Overall, text commands are a crucial part of programming and are used extensively in applications that involve working with text data.
Learn more about text on:
https://brainly.com/question/20169296
#SPJ1
What are the four layers of Geert Hofstede's "cultural onion"?
Answers
Answer:
Symbol, hero, ritual, value.
Explanation:
Which of the following types of HDFS nodes stores all the metadata about a file system?
A) Data node
B) Client node
C) Name node
D) Map node
Answers
Name node stores all the metadata about a file system in HDFS. In HDFS, data is stored across multiple nodes in cluster, & metadata about the file system is stored on a dedicated node called the NameNode.
Hadoop Distributed File System (HDFS) is a distributed file system in Hadoop that provides high-throughput access to large data sets. In HDFS, data is stored across multiple nodes in a cluster, and metadata about the file system is stored on a dedicated node called the NameNode.
The NameNode is responsible for managing the file system namespace, including maintaining a record of the files, directories, and blocks in the file system, as well as their locations within the cluster. It also tracks the health of the data nodes and assigns block replicas to them. The NameNode acts as a single point of reference for clients that want to access the data in HDFS.In summary, the NameNode is the central component of HDFS that keeps track of all metadata about the file system, such as the file and directory structure, block locations, and block replicas.
Learn more about Hadoop here:
https://brainly.com/question/30023314
#SPJ4
2 The software needed to send an email is:
+
A presentation software
B web authoring software
C communication software
D graphics software
Answers
Answer:
C communication software
Explanation:
C communication software IS THE ANSWER
What is the relationship between entropy and the second law of thermodynamics, and how does it apply to closed systems in thermodynamics?
Answers
The overall entropy of a system may only ever increase or stay constant during spontaneous processes, according to the second law of thermodynamics.
What is the second law of motion?According to the second rule of thermodynamics, entropy does not decrease in a closed system.
In other words, if the system is originally in an ordered, low-entropy state, its condition will tend to naturally drift toward a maximum-entropy state (disorder).
Therefore, the second law of thermodynamics states that the total entropy of a system may only ever increase or remain constant during spontaneous processes.
To learn more about the second law of motion, refer to the link:
https://brainly.com/question/28010409
#SPJ9
Whales thrive in the benthic zone because it is full of plankton.
Is it true or false
Answers
Answer:
true
Explanation:
False. I answered true on the quiz and got it wrong.
a wrapper is a specialized tool used by hackers to build trojan horses. true or false?
Answers
False. A wrapper is not a specialized tool used by hackers to build trojan horses.
In computer programming, a wrapper is a software component that provides a simplified interface or functionality to another component or system. It is commonly used to encapsulate complex or low-level operations, making them easier to use for other programs or developers. While hackers may use various tools and techniques to create malicious software like trojan horses, the term "wrapper" itself does not imply any specific malicious intent. Wrappers are widely used in legitimate software development for purposes such as abstraction, integration, or simplification of code.
learn more about hackers here:
https://brainly.com/question/32413644
#SPJ11
write a program to calculate sum of first ten natural numbers
Answers
Answer:
Explanation:
total = 0
i = 0
while i<=10:
total = i +total
print(total)
What is the significance of being able to harvest stem
cells that can specialize into any type of cell?
Answers
Answer:
wassup the answer is F
Explanation:
hope this helps:)))))
The significance of being able to harvest stem cells is that it gives one room for embryonic stem cells to be employed in the regeneration or the repair of any kind of faulty tissue or organs.
What are Stem cells?These are known to be any kind of cells that can be able to recreate or develop into a lot of different types of cells in any body.
Conclusively, The importance of being able to harvest stem cells is that it gives one room for embryonic stem cells to be used in the recreating or the repair of any kind of faulty tissue or organs.
Learn more about stem cells from
https://brainly.com/question/18243320
memory has four essential processes—encoding, storage, retrieval, and consolidation. true or false
Answers
False. The statement is incorrect. While memory does involve encoding, storage, retrieval, and consolidation processes, there are typically three main processes recognized in memory psychology: encoding, storage, and retrieval.
The process of memory involves several interconnected stages, but the commonly recognized ones are encoding, storage, and retrieval. Encoding refers to the initial process of transforming information into a format that can be stored in memory. It involves converting sensory input into meaningful representations that can be processed and retained. For example, when we encounter new information, our brain encodes it through various mechanisms such as semantic encoding (based on meaning) or visual encoding (based on visual features).
Once encoded, the information enters the storage phase. Storage involves maintaining and organizing the encoded information over time. It is often conceptualized as a three-stage model comprising sensory memory, short-term memory, and long-term memory. Sensory memory holds sensory information for a brief duration, while short-term memory, also known as working memory, holds information temporarily for immediate processing. Long-term memory is the more permanent storehouse where encoded information can be stored for an extended period, potentially lasting a lifetime.
Retrieval is the process of accessing and recalling stored information from memory. It involves locating and bringing forth the desired information when needed. Retrieval can occur consciously, such as when we actively try to recall a specific memory or piece of information, or it can happen unconsciously, with memories being triggered by cues or associations in our environment.
While consolidation is an important aspect of memory, it is not typically considered one of the core processes. Consolidation refers to the process by which memories become stable and strengthened over time. It involves the transfer of information from short-term memory to long-term memory, making the memories more resistant to forgetting. Consolidation is thought to occur through various physiological and neural processes that allow memories to become more firmly established.
In summary, memory involves the stages of encoding, storage, and retrieval. Encoding allows information to be transformed into a suitable form for storage, storage involves maintaining and organizing the information, and retrieval allows for the access and recall of stored information. While consolidation is significant for memory stability, it is not generally included as one of the essential processes of memory.
To know more about Encoding, visit
https://brainly.com/question/13963375
#SPJ11
RIGHT ANSWER GETS BRAINLEST
Complete the code.
You are writing a loop to allow the user to enter data until they enter a "Q". You want to allow them to enter an upper- or lowercase "Q".
if yourTeam.
() == "q":
break
The options they give are:
Upper
Compare
lower
Answers
Answer:
sir i beleive lower is your answer, i know it isnt upper.
Explanation:
:D
Answer:
lower
Explanation:
i just did the quiz and got it right :)
The purpose of a function that does not return a value is Group of answer choices to insert a temporary implementation of a function that can be refined later only used when the function needs to produce output to package a repeated task as a function even though the task does not yield a value to provide a function that can only be included in an assignment statement
Answers
Answer:
to package a repeated task as a function even though the task does not yield a value.
Explanation:
In Computer programming, a function can be defined as a group of organized, reusable sets of code that is used to perform a specific task i.e a single but related action. Thus, a function accepts data as an input, process the data and return a single result or a set of results.
Some of the notable characteristics of a function includes;
I. The name and arguments of the function must be specified by a function.
II. The implementation of a function is usually designed to be hidden from the caller.
IIII. A function define specific tasks that reusable at many points in a program.
A function that does not return a value after it executes is generally referred to as a void function. Thus, a void function uses the keyword "void" and has no explicit return statement in its body, with respect to a data type.
The purpose of a void function is to control returns back to the caller or package a repeated task as a function but, it doesn't yield a value.
Which slide should you change so that it reflects on all the slides?
Any change you can make to a slide in Normal view can be made to the slide master so the change will be reflected on all slides in the presentation.
Answers
A presentation's theme and slide layouts, including the background color, typefaces, effects, placeholder sizes, and positioning, are stored on the top slide, known as the "slide master."
To save the image you wish to add to your computer, click it with your right mouse button. After selecting the View tab, choose the Slide Master command. Any modification you make to a slide in the presentation's Normal view also affects the slide master, which updates all other slides.
The slide whose arrangement you want to change should be selected. Select Home > Layout. A preferred configuration should be chosen. The layouts can contain text, video, pictures, charts, shapes, clip art, backgrounds, and other elements.
To learn more about Slide Master click here:
brainly.com/question/7868891
#SPJ4
what advantage is there in having different time-quantum sizes at different levels of a multilevel queueing system?
Answers
Answer :
The benefit of having different time-quantum sizes at different levels of a multilevel queueing system is that it enables the use of system resources in the most efficient manner possible.A multilevel queueing system is a kind of queueing system that employs multiple job queues at the same time. The processes are split into several separate queues depending on their requirements and how they should be handled.Each queue might have its own specific requirements for scheduling and resource allocation.
Explanation :
In general, the system can be split into different levels based on how critical the tasks are and how quickly they should be processed.Each level of the queueing system will have its own unique time-quantum value. The time-quantum size varies according to the level's priority. The priority will be decided by the task's level in the system, which is determined by its significance to the program.The main advantage of having different time-quantum sizes at different levels of a multilevel queueing system is that it enables the use of system resources in the most efficient manner possible. By providing the most priority to the most critical and significant tasks, system resources can be allocated to the most important tasks first.This ensures that the most essential and critical tasks are completed first, and that the system's output is optimised. As a result, the multilevel queueing system becomes more efficient and productive.
Learn more about "Cyber attacks" : https://brainly.in/question/2412100
#SPJ11
If network administrators want to be informed when an attempt has been made to compromise the network, what should they use?a. VPNb. AESc. IDSd. EFS
Answers
The network administrators should use an Intrusion Detection System (IDS) to be informed when an attempt has been made to compromise the network.
What's IDSAn IDS is a type of security system that is designed to detect malicious activities or policy violations on a network. It monitors network traffic and monitors for suspicious activities that could indicate a security breach.
Network administrators should use an IDS (Intrusion Detection System) if they want to be informed when an attempt has been made to compromise the network. An IDS is a software application that monitors a network or systems for malicious activity or policy violations.
It can detect unauthorized access attempts, malicious code, or policy violations and alert the administrator to take action.
Therefore, the correct answer is option c. IDS.
Learn more about IDS at
https://brainly.com/question/29038449
#SPJ11
Design an algorithm for a function that accepts an Integer array as an argument
and returns the total of the values in the array.
In bash or pseudocode, please. Use a counted For loop, not a For Each or For..In loop
Answers
Below is an algorithm in pseudocode for a function that accepts an integer array as an argument and returns the total of the values in the array using a counted for loop.
What is the algorithm?sql
function calculateTotal(arr: integer[]): integer
total = 0 // Initialize total to zero
length = length of arr // Get length of the array
for i = 0 to length - 1 // Loop through each element in the array
total = total + arr[i] // Add the current element to the total
end for
return total // Return the total
end function
Note, could not finish it since it showing inappropraite words.
Read more about algorithm here:
https://brainly.com/question/24953880
#SPJ1
consider sending a 2900-bytes datagram into a link that has an mtu of 700 bytes. how many fragments are generated assuming that ip header is 20 bytes?
Answers
There would be 5 fragments generated. The first fragment would be 700 bytes (MTU) + 20 bytes (IP Header) = 720 bytes. The remaining 2880 bytes would be divided into 4 fragments of 700 bytes each.
What is Bytes?
Bytes are the smallest unit of measurement used to measure digital information. Bytes are typically used to measure the size of a file, the amount of memory on a computer, the size of a document, or the amount of data that can be transmitted over a network. A single byte contains 8 bits, which is the smallest unit of memory a computer can access. A byte is large enough to represent one character of text, such as a letter or number. A kilobyte (KB) is equal to 1,024 bytes, a megabyte (MB) is equal to 1,048,576 bytes, and a gigabyte (GB) is equal to 1,073,741,824 bytes.
To know more about Bytes
https://brainly.com/question/14927057
#SPJ4
How to fix unable to verify that you have access to this experience. please try again later.?
Answers
If you receive the warning "Unable to verify that you have access to this experience," this means that you do. You can attempt the following to resolve the problem: Your internet connection should be checked.
An individual's participation in or living through an event or activity is referred to as having a "experience." In a broad sense, experiences might range from individual activities and adventures to possibilities for learning or employment. A person's views, perceptions, and values might change as a result of experiences. They can have either positive or negative impacts, and they can teach us important lessons that we can apply to our future undertakings. Experiences in the context of contemporary technology can include virtual or augmented reality simulations, games, or applications that provide the user with an interactive and immersive world. Such experiences are redefining how individuals interact with their environment and are becoming more and more common in a variety of disciplines, from education to entertainment.
Learn more about experience here:
https://brainly.com/question/11256472
#SPJ4
Suppose you are packing for a backpacking trip and trying to decide which snacks to bring. your home pantry contains m snack items, each of which has a certain weight wi and a calorie value vi. your backpack can only hold a maximum weight of w , and for your journey you need a minimum of v calories. therefore, you need to answer the question: is there is some set s of items from your pantry such that the sum of the weights of the items in s is less than or equal to w , while the sum of the calorie values of the items in s is greater than or equal to v.
required:
a. describe a (deterministic) algorithm for answering the question. is it a polynomial-time algorithm? explain your answer.
b. describe a non-deterministic algorithm for deciding the question. is it a nondeterministic polynomial-time algorithm?
Answers
A deterministic algorithm is required to compute an optimal solution in exponential time.
a. A deterministic algorithm to answer the question
If we want to check whether there is a set of items that satisfy our requirements, we can use a brute-force approach where we try out all possible combinations of items and check if they satisfy the constraints. This is done by following these steps:Generate all possible subsets of the m itemsCheck if the weight of each subset is less than or equal to wCheck if the calorie value of each subset is greater than or equal to vIf a subset is found that satisfies both conditions, then output “Yes” and the set of items that satisfy the conditions Else, output “No” if no such subset is found.The time complexity of the above algorithm is O(2^m) since we need to generate all possible subsets, and there are 2^m subsets for m items.
Hence, it is an exponential-time algorithm. It is not a polynomial-time algorithm since the time complexity does not grow as a polynomial function of the input size.b. A non-deterministic algorithm to decide the questionA non-deterministic algorithm can be used to guess a solution to the problem in polynomial time and verify it in polynomial time. Hence, we can guess a subset of items and verify if it satisfies the constraints as follows:Guess a subset of items from the pantry
Check if the weight of the subset is less than or equal to wCheck if the calorie value of the subset is greater than or equal to vIf both conditions are satisfied, then output “Yes” and the subset of items as the solutionElse, output “No” if no such subset is found.The time complexity of the above algorithm is O(m), which is polynomial in the input size. However, the non-deterministic algorithm cannot be used to compute an optimal solution since it does not guarantee that the guessed subset is the optimal solution. Hence, a deterministic algorithm is required to compute an optimal solution in exponential time.
Learn more about algorithm :
https://brainly.com/question/21172316
#SPJ11
what is a bookmark hyperlink?
Answers
A Bookmark is an object used to record a location in a Word document. You can define a bookmark programmatically with the BookmarkStart and BookmarkEnd pair of elements. A Hyperlink is a document element used to jump to a Bookmark in the same document or to an external resource
Which office setup would be difficult to host on a LAN?
hardware.
RAM.
storage.
software.
Answers
The office setup would be difficult to host on a LAN is option C: storage.
What is the office LAN setup like?A local area network (LAN) is a network made up of a number of computers that are connected in a certain area. TCP/IP ethernet or Wi-Fi is used in a LAN to link the computers to one another. A LAN is typically only used by one particular establishment, like a school, office, group, or church.
Therefore, LANs are frequently used in offices to give internal staff members shared access to servers or printers that are linked to the network.
Learn more about LAN from
https://brainly.com/question/8118353
#SPJ1
which protocol range you should specify to allow inbound rdp traffic
Answers
To allow inbound RDP (Remote Desktop Protocol) traffic, the protocol range you should specify is TCP port range 3389.
RDP (Remote Desktop Protocol) is a protocol developed by Microsoft for remote access to Windows machines.
It is an application that allows you to connect to a remote computer over the internet or on the same network and interact with it as if you were physically present.
A port range is a collection of ports in a TCP/IP network that is used to identify a specific service or application.
Each port has a unique number assigned to it that is used to identify a specific service or application.
RDP uses TCP port 3389 as its default port, so to allow inbound RDP traffic, you must open up that specific port on the firewall.
A firewall is a security system that is used to control access to a computer or network.
It is a barrier that prevents unauthorized access to your system by monitoring and controlling the traffic that flows between your computer and the internet or another network.
The firewall can be configured to block all traffic by default, allowing only authorized traffic to pass through.
Know more about RDP here:
https://brainly.com/question/14719354
#SPJ11
What is the File Transfer Protocol (FTP)?
Answers
The File Transfer Protocol (FTP) is a standard network protocol used for transferring files from one computer to another over a TCP/IP network, such as the internet.
What is network protocol?Network protocol is a set of rules and regulations that governs communication between two or more computing devices over a computer network, allowing them to exchange data.
It is used for uploading and downloading files, as well as for managing files on remote computers. FTP uses a client-server architecture, where an FTP client is used to establish a connection to an FTP server. Once connected, users can upload, download, delete, or modify files on the remote computer.
To learn more about network protocol
https://brainly.com/question/28811877
#SPJ4
Helppp meee e e e e e e
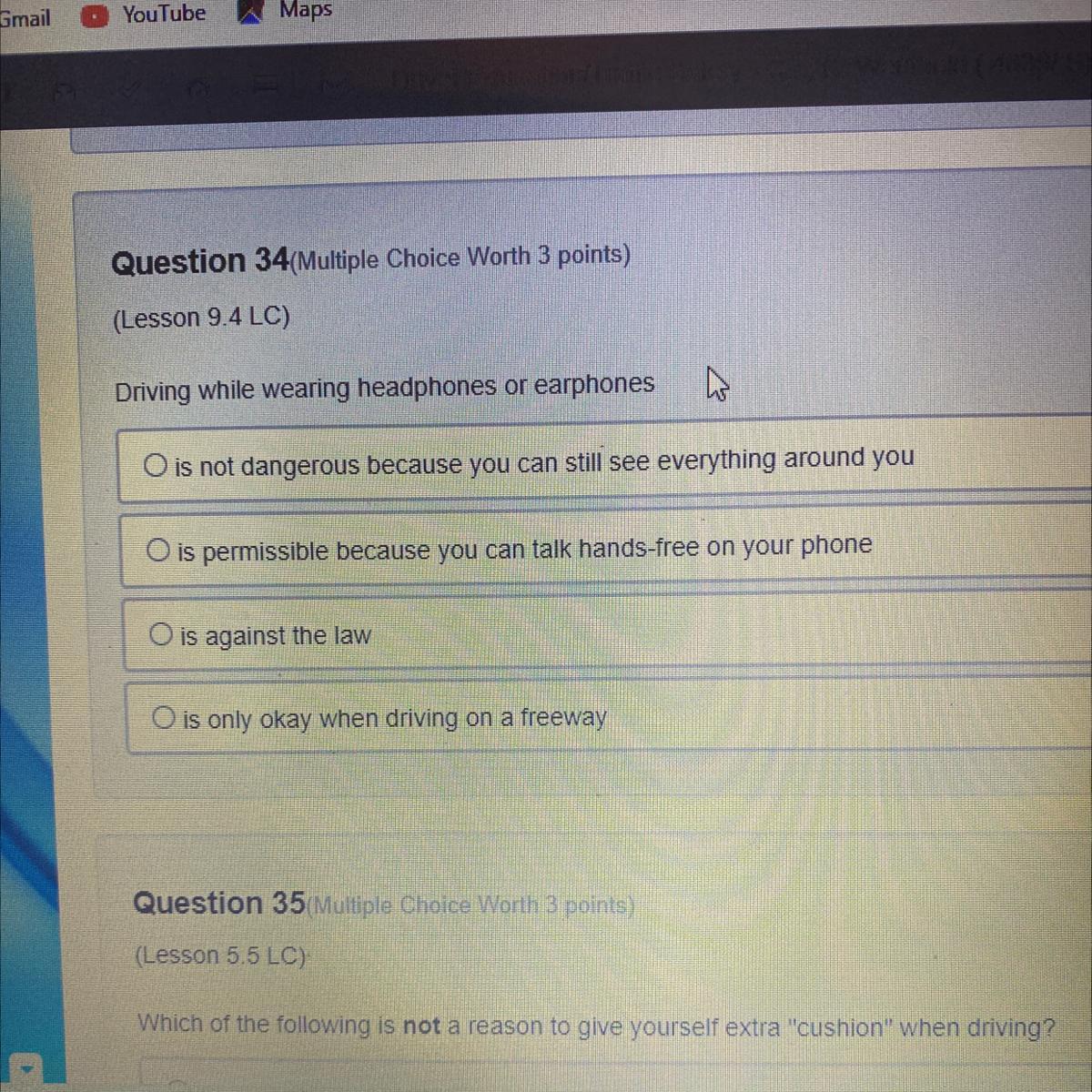
Answers
Answer:
C) Its against the law
Explanation:
Wearing headphones or earphones in both ears simultaneously for the purposes of receiving or listening to broadcasts or reproductions from radios, tape decks, or other sound-producing or transmitting devices, is not permitted while driving. Exempts the use of hearing aid devices.
7.4 Code Practice: Question 2
Adjust the code you wrote for the last problem to allow for weighted classes. Add a parameter weighted ( 1 = yes, 0 = no) and then return the correct number for the GPA. Weighted classes get one extra point on the GPA value.
I could really use some help on this and 7.5 (I’ll ask that question for 7.5 later)

Answers
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
if weighted == 1 and grade in dictionary:
return "Your GPA score is: "+str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
return "Your GPA score is : "+str(dictionary[grade])
else:
return "Invalid"
print(GPAcalc(input("Input a letter grade: "), int(input("Is it weigthed? (1= yes, 0= no)"))))
I modified the code a bit to cut down on the use of if and elif statements. If you need me to change it, I will. Best of luck.
The program is an illustration of conditional statements.
Conditional statements are statements whose execution is dependent on its truth value.
The program in Python, where comments are used to explain each line is as follows:
#This initializes the dictionary
dict = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
#This gets input for grade
grade = input().lower()
#This gets input for the weighted average
weighted = int(input())
#If the weighted average is 1, and the grade is in the dictionary
if weighted == 1 and grade in dictionary:
#This prints the GPA score
print("Your GPA score is: "+str(dict[grade] + 1))
#If the weighted average is 0, and the grade is in the dictionary
elif weighted == 0 and grade in dictionary:
#This prints the GPA score
print("Your GPA score is : "+str(dict[grade]))
#Otherwise
else:
#The grade is invalid
print("Invalid")
Read more about similar programs at:
https://brainly.com/question/19241597
4. 8. 5: Calendar code hs
Using an HTML table, make your own calendar for this month.
The table headers should have the name of each day of the week.
Inside the table, write the date of each day in the month.
For example, the calendar for the month of November 2016 would look like this:
November Calendar
BONUS CHALLENGE:
Add events to your calendar by adding lists to specific days in the table. Add friend and family birthdays, holidays, or any other events you can think of!
Answers
Answer:
Here is an HTML code you can use.
If you go to any HTML editor. You will see this clearly works. Hope this helps lad. This also includes your bonus challenge.
<!DOCTYPE html>
<html>
<head>
<title>March Calendar</title>
<style>
table {
border-collapse: collapse;
}
td, th {
border: 1px solid black;
padding: 10px;
text-align: center;
font-size: 20px;
font-weight: bold;
}
th {
background-color: #ddd;
}
td {
height: 100px;
vertical-align: top;
}
</style>
</head>
<body>
<h1>March Calendar</h1>
<table>
<thead>
<tr>
<th>Sun</th>
<th>Mon</th>
<th>Tue</th>
<th>Wed</th>
<th>Thu</th>
<th>Fri</th>
<th>Sat</th>
</tr>
</thead>
<tbody>
<tr>
<td></td>
<td></td>
<td></td>
<td></td>
<td></td>
<td>1</td>
<td>2</td>
</tr>
<tr>
<td>3</td>
<td>4</td>
<td>5</td>
<td>6</td>
<td>7</td>
<td>8</td>
<td>9</td>
</tr>
<tr>
<td>10</td>
<td>11</td>
<td>12</td>
<td>13</td>
<td>14</td>
<td>15</td>
<td>16</td>
</tr>
<tr>
<td>17</td>
<td>18</td>
<td>19</td>
<td>20</td>
<td>21</td>
<td>22</td>
<td>23</td>
</tr>
<tr>
<td>24</td>
<td>25</td>
<td>26</td>
<td>27</td>
<td>28</td>
<td>29</td>
<td>30</td>
</tr>
<tr>
<td>31</td>
<td></td>
<td></td>
<td></td>
<td></td>
<td></td>
<td></td>
</tr>
</tbody>
</table>
<h2>Events:</h2>
<ul>
<li>March 17 - St. Patrick's Day</li>
<li>March 20 - First day of Spring</li>
</ul>
</body>
</html>
The calendar for this month using HTML is mentioned below:
<!DOCTYPE html>
<html>
<head>
<title>Calendar</title>
<style>
table {
border-collapse: collapse;
width: 100%;
}
th, td {
border: 1px solid black;
text-align: center;
padding: 8px;
}
th {
background-color: #ccc;
}
</style>
</head>
<body>
<h2>Calendar</h2>
<table>
<tr>
<th>Sunday</th>
<th>Monday</th>
<th>Tuesday</th>
<th>Wednesday</th>
<th>Thursday</th>
<th>Friday</th>
<th>Saturday</th>
</tr>
<tr>
<td></td>
<td></td>
<td></td>
<td></td>
<td>1</td>
<td>2</td>
<td>3</td>
</tr>
<tr>
<td>4</td>
<td>5</td>
<td>6</td>
<td>7</td>
<td>8</td>
<td>9</td>
<td>10</td>
</tr>
<tr>
<td>11</td>
<td>12</td>
<td>13</td>
<td>14</td>
<td>15</td>
<td>16</td>
<td>17</td>
</tr>
<tr>
<td>18</td>
<td>19</td>
<td>20</td>
<td>21</td>
<td>22</td>
<td>23</td>
<td>24</td>
</tr>
<tr>
<td>25</td>
<td>26</td>
<td>27</td>
<td>28</td>
<td>29</td>
<td>30</td>
<td>31</td>
</tr>
</table>
</body>
</html>
Learn more about HTML, here:
https://brainly.com/question/24065854
#SPJ2
what class of arthropods is mainly involved in the pollination process?
Answers
Answer:
Insects
Explanation:
insects are the most pollinating arthropods.